What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2021-02-04 14:00:00 | The Security Value of Exploit Protection (lien direct) |
 An exploit attack occurs when a malicious actor takes advantage of a software vulnerability to penetrate and then damage or steal information from a computer system. One feature that Cybereason provides to protect users from exploit attacks is our Exploit Protection. The following is a quick rundown of some of the key terms for understanding exploit attacks.
An exploit attack occurs when a malicious actor takes advantage of a software vulnerability to penetrate and then damage or steal information from a computer system. One feature that Cybereason provides to protect users from exploit attacks is our Exploit Protection. The following is a quick rundown of some of the key terms for understanding exploit attacks. |
Vulnerability | |||
| 2021-02-04 13:05:00 | Cybereason XDR Dubbed Hottest New Cybersecurity Product by CRN (lien direct) |
 Cybereason is pleased to announce that Cybereason XDR was named one of the hottest new cybersecurity products of 2020 by CRN. With Cybereason XDR, defenders can pinpoint, understand and end any Malop™ (malicious operation) across the entire IT stack whether on-premises, mobile or in the cloud.
Cybereason is pleased to announce that Cybereason XDR was named one of the hottest new cybersecurity products of 2020 by CRN. With Cybereason XDR, defenders can pinpoint, understand and end any Malop™ (malicious operation) across the entire IT stack whether on-premises, mobile or in the cloud. |
||||
| 2021-02-03 16:08:52 | Malicious Life Podcast: Inside Clearview AI Facial Recognition (lien direct) |
 Clearview AI scrapes billions of images off social media and the open web, applies facial recognition algorithms on them, and sells that data to law enforcement agencies all over the world. But who are the people behind this secretive company, and what did a breach into its databases reveal?
Clearview AI scrapes billions of images off social media and the open web, applies facial recognition algorithms on them, and sells that data to law enforcement agencies all over the world. But who are the people behind this secretive company, and what did a breach into its databases reveal? |
||||
| 2021-02-03 14:42:59 | Nearly One-Third of Attack Targets Weren\'t Running SolarWinds (lien direct) |
 Approximately one-third of organizations affected by the SolarWinds supply chain attacks weren't actually running the IT management company's affected software.
Approximately one-third of organizations affected by the SolarWinds supply chain attacks weren't actually running the IT management company's affected software. |
||||
| 2021-02-02 21:07:01 | Krebs, Curry and Cyber Security (lien direct) |
 The daily drumbeat of data spills, breaches, and thefts can foster breach fatigue, apathy, and cynicism among even the hardiest security professionals. What sets in is a suspicion that all our efforts are for naught, and that we are perpetually a step behind the bad guys.
The daily drumbeat of data spills, breaches, and thefts can foster breach fatigue, apathy, and cynicism among even the hardiest security professionals. What sets in is a suspicion that all our efforts are for naught, and that we are perpetually a step behind the bad guys. |
||||
| 2021-02-01 14:00:00 | NHS Warns of New COVID-19 Vaccine-Related Phishing Campaigns (lien direct) |
 The United Kingdom's National Health Service (NHS) warned that scammers are in the process of sending out fake COVID-19 vaccine invitations. On January 25th, Urology Cancer Research & Education (UCARE) Oxford reached out to the NHS on Twitter and shared an image of one such fake invitation that it had received.
The United Kingdom's National Health Service (NHS) warned that scammers are in the process of sending out fake COVID-19 vaccine invitations. On January 25th, Urology Cancer Research & Education (UCARE) Oxford reached out to the NHS on Twitter and shared an image of one such fake invitation that it had received. |
||||
| 2021-01-28 17:55:04 | Emotet Botnet Infrastructure Disrupted in International Takedown (lien direct) |
 Law enforcement entities and judicial authorities located around the world succeeded in disrupting the Emotet botnet's infrastructure through a coordinated takedown effort.
Law enforcement entities and judicial authorities located around the world succeeded in disrupting the Emotet botnet's infrastructure through a coordinated takedown effort. |
||||
| 2021-01-28 14:00:00 | Sam Curry on the \'Real Privacy Mandate\' (lien direct) |
 National Privacy Day is a time to look at the current state of privacy and to set the direction and tone for the future. On January 28, 2021, let's stop and think not just about the minimum requirements of privacy legislation but rather about the world we're building and handing to our children.
National Privacy Day is a time to look at the current state of privacy and to set the direction and tone for the future. On January 28, 2021, let's stop and think not just about the minimum requirements of privacy legislation but rather about the world we're building and handing to our children. |
||||
| 2021-01-28 13:05:00 | Cybereason Partners with Ensign to Provide Managed Detection and Response Services in APAC (lien direct) |
 Cybereason, the leader in future ready attack protection, is pleased to announce a partnership with Ensign InfoSecurity , one of the Asia Pacific's largest pure-play cybersecurity firms, to expand the suite of cybersecurity solutions and services that Ensign offers to protect its Asia Pacific customers from the evolving cyber threats.
Cybereason, the leader in future ready attack protection, is pleased to announce a partnership with Ensign InfoSecurity , one of the Asia Pacific's largest pure-play cybersecurity firms, to expand the suite of cybersecurity solutions and services that Ensign offers to protect its Asia Pacific customers from the evolving cyber threats. |
Guideline | ★★★★★ | ||
| 2021-01-27 14:30:00 | SolarWinds Attacks Highlight Advantage of Indicators of Behavior for Early Detection (lien direct) |
 I've talked about the SolarWinds Supply Chain Attacks recently more than you'd care to know over the past month or so (just ask anyone who knows me), with key points from a few of the discussions making their way into the public sphere here and here.
I've talked about the SolarWinds Supply Chain Attacks recently more than you'd care to know over the past month or so (just ask anyone who knows me), with key points from a few of the discussions making their way into the public sphere here and here. |
||||
| 2021-01-26 14:00:00 | (Déjà vu) Cybereason vs. RansomEXX Ransomware (lien direct) |
 Research by: Daniel Frank
Research by: Daniel Frank |
Ransomware | |||
| 2021-01-25 14:44:34 | Wipro\'s State of Cybersecurity Report Reveals Valuable Insights (lien direct) |
 It is true in general that technology is always changing, and the threat landscape is constantly evolving, but 2020 has amplified the cybersecurity challenge. Organizations of all sizes and across all industries already struggled to effectively manage risk and cyber resilience, but the global pandemic of COVID-19 has introduced a sudden and dramatic shift that tips the playing field in favor of attackers and exacerbates the task.
It is true in general that technology is always changing, and the threat landscape is constantly evolving, but 2020 has amplified the cybersecurity challenge. Organizations of all sizes and across all industries already struggled to effectively manage risk and cyber resilience, but the global pandemic of COVID-19 has introduced a sudden and dramatic shift that tips the playing field in favor of attackers and exacerbates the task. |
Threat | |||
| 2021-01-22 14:00:00 | Last Hurrah: Executive Order to Protect IaaS Platforms from Malicious Actors (lien direct) |
 President Donald Trump signed an executive order to prevent foreign malicious cyber actors from misusing United States Infrastructure as a Service (IaaS) products. In the executive order, dated January 19, President Trump explained that foreign malicious cyber actors were using IaaS products made in the United States to aid their efforts in stealing sensitive information as well as targeting U.S. critical infrastructure:
President Donald Trump signed an executive order to prevent foreign malicious cyber actors from misusing United States Infrastructure as a Service (IaaS) products. In the executive order, dated January 19, President Trump explained that foreign malicious cyber actors were using IaaS products made in the United States to aid their efforts in stealing sensitive information as well as targeting U.S. critical infrastructure: |
||||
| 2021-01-21 14:08:16 | SolarWinds Attacks Highlight Importance of Operation-Centric Approach (lien direct) |
 We're still learning the full extent of the SolarWinds supply chain attacks. On January 11, for instance, researchers published a technical breakdown of a malicious tool detected as SUNSPOT that was employed as part of the infection chain involving the IT management software provider's Orion platform.
We're still learning the full extent of the SolarWinds supply chain attacks. On January 11, for instance, researchers published a technical breakdown of a malicious tool detected as SUNSPOT that was employed as part of the infection chain involving the IT management software provider's Orion platform. |
Tool | Solardwinds Solardwinds | ||
| 2021-01-13 14:00:00 | Cybereason and SYNNEX Corporation Partner to End Cyber Attacks (lien direct) |
 Cybereason and SYNNEX Corporation are pleased to announce a strategic agreement that enables SMBs and Enterprises to detect and end cyber attacks on endpoints anywhere on their networks.
Cybereason and SYNNEX Corporation are pleased to announce a strategic agreement that enables SMBs and Enterprises to detect and end cyber attacks on endpoints anywhere on their networks. |
||||
| 2021-01-12 14:03:32 | (Déjà vu) Cybereason vs. Conti Ransomware (lien direct) |
 Research by: Lior Rochberger
Research by: Lior Rochberger |
Ransomware | |||
| 2021-01-11 21:35:00 | Cybereason and Intel Introduce Hardware-Enabled Ransomware Protections for Businesses (lien direct) |
 Ransomware can literally put organizations and lives at risk, as witnessed in 2020 with the continuous onslaught of attacks against the healthcare industry, research organizations working on COVID-19 vaccines, telecommunication centers, financial institutions, the public sector and companies across every industry vertical.
Ransomware can literally put organizations and lives at risk, as witnessed in 2020 with the continuous onslaught of attacks against the healthcare industry, research organizations working on COVID-19 vaccines, telecommunication centers, financial institutions, the public sector and companies across every industry vertical. |
Ransomware | |||
| 2021-01-05 19:42:44 | Contextualizing Microsoft\'s Source Code Exposure in the SolarWinds Attacks (lien direct) |
 In the middle of December, IT management software provider SolarWinds revealed in a security advisory that it had fallen victim to a sophisticated supply chain attack. The offensive involved the placement of a backdoor known as SUNBURST into versions 2019.4 HF 5, 2020.2 with no hotfix installed and 2020.2 HF 1 of the company's Orion Platform software. If executed, SUNBURST allowed an attacker to compromise the server running the Orion build.
In the middle of December, IT management software provider SolarWinds revealed in a security advisory that it had fallen victim to a sophisticated supply chain attack. The offensive involved the placement of a backdoor known as SUNBURST into versions 2019.4 HF 5, 2020.2 with no hotfix installed and 2020.2 HF 1 of the company's Orion Platform software. If executed, SUNBURST allowed an attacker to compromise the server running the Orion build. |
Solardwinds Solardwinds | |||
| 2021-01-04 13:30:00 | Ever Evolving: Israel Barak on Running Remote SOC Ops (lien direct) |
 We spent some time with Israel Barak, Chief Information Security Officer at Cybereason, who discussed some of the challenges of running a world-wide SOC remotely during the pandemic - check it out...
We spent some time with Israel Barak, Chief Information Security Officer at Cybereason, who discussed some of the challenges of running a world-wide SOC remotely during the pandemic - check it out... |
||||
| 2020-12-24 13:00:00 | Amazon Gift Card Offer Serves Up Dridex Banking Trojan (lien direct) |
 Research by: Daniel Frank
Research by: Daniel Frank |
★★★★ | |||
| 2020-12-23 14:00:00 | Cybereason vs. Clop Ransomware (lien direct) |
 Research by: Daniel Frank
Research by: Daniel Frank |
Ransomware | |||
| 2020-12-22 21:14:06 | Cybereason vs. SolarWinds Supply Chain Attack (lien direct) |
 On December 13, 2020, IT infrastructure management provider SolarWinds issued a Security Advisory regarding their SolarWinds Orion Platform after experiencing a “highly sophisticated” supply chain attack. The activity is reported to have begun as early as Spring 2020, as reported by researchers from security firm FireEye.
On December 13, 2020, IT infrastructure management provider SolarWinds issued a Security Advisory regarding their SolarWinds Orion Platform after experiencing a “highly sophisticated” supply chain attack. The activity is reported to have begun as early as Spring 2020, as reported by researchers from security firm FireEye. |
Solardwinds | |||
| 2020-12-22 14:00:00 | 2021 Security Crystal Ball: Trends and Predictions for the Year Ahead (lien direct) |
 2020 kicked off with a bang, literally, as General Soleimani was killed less than a week into the year. This had immediate repercussions with simple website defacements by minor actors ideologically aligned with Iran and concerns of cyber escalations.
2020 kicked off with a bang, literally, as General Soleimani was killed less than a week into the year. This had immediate repercussions with simple website defacements by minor actors ideologically aligned with Iran and concerns of cyber escalations. |
||||
| 2020-12-21 04:08:43 | Cybereason and Oracle Team Up for Security at Scale from the Endpoint to the Cloud (lien direct) |
 The sudden transition to remote work brought on by the pandemic resulted in many companies ensuring employees had the necessary tools to work remotely. However, that left little focus on the rising security risks that come with home networks and endpoints.
The sudden transition to remote work brought on by the pandemic resulted in many companies ensuring employees had the necessary tools to work remotely. However, that left little focus on the rising security risks that come with home networks and endpoints. |
||||
| 2020-12-18 18:16:30 | Impact of XDR on the Modern SOC: New ESG Report (lien direct) |
 As we hurtle towards the end of 2020, the only constant we can come to expect is change itself. We're pressed on two sides: our corporate IT environments continue to change, and attackers are more persistent and explosive than ever. While it is possible to secure a modern, distributed, multi-cloud environment, it feels out of reach for most security teams. Between data lake management, detection and rules tuning, and repetitive response actions, it's challenging to architect, build, and maintain -- and of course prove that it's making the business safer.
As we hurtle towards the end of 2020, the only constant we can come to expect is change itself. We're pressed on two sides: our corporate IT environments continue to change, and attackers are more persistent and explosive than ever. While it is possible to secure a modern, distributed, multi-cloud environment, it feels out of reach for most security teams. Between data lake management, detection and rules tuning, and repetitive response actions, it's challenging to architect, build, and maintain -- and of course prove that it's making the business safer. |
||||
| 2020-12-15 18:11:05 | Molerats APT: New Malware and Techniques in Middle East Espionage Campaign (lien direct) |
 Security researchers observed a politically motivated APT called “Molerats” using three new malware variants to conduct espionage in the Middle East.
Security researchers observed a politically motivated APT called “Molerats” using three new malware variants to conduct espionage in the Middle East. |
Malware | |||
| 2020-12-14 21:47:12 | The SolarWinds Supply Chain Attack and the Limits of Cyber Hygiene (lien direct) |
 By now, you've probably heard: On December 13, Reuters reported that malicious actors had gone after both the U.S. Department of Treasury and the U.S. Department of Commerce. The National Security Council met at the White House on December 12 to talk things over. A day later, U.S. officials indicated that they had asked CISA and the FBI to look into what had happened.
By now, you've probably heard: On December 13, Reuters reported that malicious actors had gone after both the U.S. Department of Treasury and the U.S. Department of Commerce. The National Security Council met at the White House on December 12 to talk things over. A day later, U.S. officials indicated that they had asked CISA and the FBI to look into what had happened. |
||||
| 2020-12-14 14:30:00 | Ever Evolving: Jake Williams on Running an Infosec Consultancy Remotely (lien direct) |
 We spent some time with Jake Williams - founder and President at Rendition Infosec and SANS Instructor - discusses some of the challenges in remotely running a successful infosec consultancy - check it out...
We spent some time with Jake Williams - founder and President at Rendition Infosec and SANS Instructor - discusses some of the challenges in remotely running a successful infosec consultancy - check it out... |
||||
| 2020-12-10 16:00:31 | Cybereason vs. Ryuk Ransomware (lien direct) |
 Ryuk ransomware has been infecting victims since around 2018, and is believed to be based on the source code of Hermes ransomware, which was sold on an internet hacking forum back in 2017. Since its inception, Ryuk has been used to target large organizations to great effect, having accumulated as much as $61.26 million (as of Feb 2020) in ransom payments according to federal investigations.
Ryuk ransomware has been infecting victims since around 2018, and is believed to be based on the source code of Hermes ransomware, which was sold on an internet hacking forum back in 2017. Since its inception, Ryuk has been used to target large organizations to great effect, having accumulated as much as $61.26 million (as of Feb 2020) in ransom payments according to federal investigations. |
Ransomware | |||
| 2020-12-09 02:00:00 | New Malware Arsenal Abusing Cloud Platforms in Middle East Espionage Campaign (lien direct) |
 The Cybereason Nocturnus Team has identified an active espionage campaign employing three previously unidentified malware variants that use Facebook, Dropbox, Google Docs and Simplenote for command & control and the exfiltration of data from targets across the Middle East. The full report can be downloaded here (ungated).
The Cybereason Nocturnus Team has identified an active espionage campaign employing three previously unidentified malware variants that use Facebook, Dropbox, Google Docs and Simplenote for command & control and the exfiltration of data from targets across the Middle East. The full report can be downloaded here (ungated). |
Malware | |||
| 2020-12-07 20:46:46 | Ever Evolving: Katie Nickels on Incident Response in a Remote World (lien direct) |
 We spent some time with Katie Nickels - current Director of Intelligence at Red Canary and formerly MITRE ATT&CK Threat Intelligence Lead - to discuss applied threat intelligence, prioritizing threats for impact, and working incident response in remote environments - check it out...
We spent some time with Katie Nickels - current Director of Intelligence at Red Canary and formerly MITRE ATT&CK Threat Intelligence Lead - to discuss applied threat intelligence, prioritizing threats for impact, and working incident response in remote environments - check it out... |
Threat Guideline | APT 15 | ||
| 2020-12-04 18:23:59 | Is XDR the Next Silver Bullet? (lien direct) |
 Join us for an hour-long panel on the intricacies of XDR and how it will affect the security industry. Learn what XDR is, specific use cases, and how security practitioners can easily integrate this new technology into their security stack.
Join us for an hour-long panel on the intricacies of XDR and how it will affect the security industry. Learn what XDR is, specific use cases, and how security practitioners can easily integrate this new technology into their security stack. |
||||
| 2020-12-04 10:00:00 | Meet the League of Defenders (lien direct) |
 When I chose a career in B2B marketing I'm not sure I ever imagined I'd be a part of a team that spent weeks architecting intricate owl wings and razor-sharp talons, but here we are. While 2020 has been filled with many challenging surprises, this was a great one for me. And because we are driven by the mission of defending together, today we released a video of what it took to bring our new league of animated owls to life. But first, some history of the owl + Cybereason.
When I chose a career in B2B marketing I'm not sure I ever imagined I'd be a part of a team that spent weeks architecting intricate owl wings and razor-sharp talons, but here we are. While 2020 has been filled with many challenging surprises, this was a great one for me. And because we are driven by the mission of defending together, today we released a video of what it took to bring our new league of animated owls to life. But first, some history of the owl + Cybereason. |
||||
| 2020-12-02 14:30:00 | Ensuring Digital Safety and Security This Holiday Season (lien direct) |
 In mid-2020, the Cybereason Research Team detected an active campaign that targeted Brazilian customers of MercadoLivre, one of the largest e-commerce platforms in Latin America.
In mid-2020, the Cybereason Research Team detected an active campaign that targeted Brazilian customers of MercadoLivre, one of the largest e-commerce platforms in Latin America. |
||||
| 2020-11-30 14:30:00 | Ever Evolving: Rachel Tobac Talks Social Engineering (lien direct) |
 We spent some time with Rachel Tobac discussing techniques, awareness and training for organizations seeking to limit the risk from one of the most difficult security threats to counter - social engineering attacks - check it out...
We spent some time with Rachel Tobac discussing techniques, awareness and training for organizations seeking to limit the risk from one of the most difficult security threats to counter - social engineering attacks - check it out... |
||||
| 2020-11-26 01:51:59 | Cybereason vs. Egregor Ransomware (lien direct) |
 Research by: Lior Rochberger
Research by: Lior Rochberger |
Ransomware | |||
| 2020-11-23 19:15:34 | The Boston Globe Recognizes Cybereason as a Top Place to Work in 2020 (lien direct) |
 Cybereason is pleased to announce we were named one of the Top Places to Work in 2020 by The Boston Globe, which recognizes the most admired workplaces in the state voted on by the people who know them best-their employees. The survey measures employee opinions about their company's direction, execution, connection, management, work, pay and benefits, and engagement.
Cybereason is pleased to announce we were named one of the Top Places to Work in 2020 by The Boston Globe, which recognizes the most admired workplaces in the state voted on by the people who know them best-their employees. The survey measures employee opinions about their company's direction, execution, connection, management, work, pay and benefits, and engagement. |
||||
| 2020-11-23 17:57:58 | Ever Evolving: Cybereason CSO Sam Curry on Security and Leadership (lien direct) |
 Cybereason CSO Sam Curry shares insights on tackling tough security challenges from a strategic perspective as well as from the point of view of a leader of security operations teams working tirelessly to reverse the adversary advantage and return the high ground to the defenders.
Cybereason CSO Sam Curry shares insights on tackling tough security challenges from a strategic perspective as well as from the point of view of a leader of security operations teams working tirelessly to reverse the adversary advantage and return the high ground to the defenders. |
Guideline | |||
| 2020-11-19 16:19:51 | Cybereason vs. MedusaLocker Ransomware (lien direct) |
 Research by: Tom Fakterman and Assaf Dahan
Research by: Tom Fakterman and Assaf Dahan |
Ransomware | |||
| 2020-11-18 19:59:10 | Buyer Beware: Tips for Secure Online Shopping During the Holidays (lien direct) |
 If 2020 has taught us anything, it is to expect the unexpected. The global pandemic has shown that people have heart and are very resilient in the face of adversity. For cyber criminals, 2020 year has been one of the most profitable in history, as we have seen a massive uptick in cyber-related criminal activity, scams and fraud.
If 2020 has taught us anything, it is to expect the unexpected. The global pandemic has shown that people have heart and are very resilient in the face of adversity. For cyber criminals, 2020 year has been one of the most profitable in history, as we have seen a massive uptick in cyber-related criminal activity, scams and fraud. |
||||
| 2020-11-18 04:15:00 | Novel Chaes Malware Underscores Heightened E-Commerce Risk This Holiday Season (lien direct) |
 The Cybereason Nocturnus Team has identified an active campaign targeting customers of a larger e-commerce platform with newly identified multi-stage malware that evades antivirus tools dubbed Chaes.
The Cybereason Nocturnus Team has identified an active campaign targeting customers of a larger e-commerce platform with newly identified multi-stage malware that evades antivirus tools dubbed Chaes. |
Malware | |||
| 2020-11-16 13:30:00 | Ever Evolving: Stephanie Ihezukwu on Managing Security Remotely (lien direct) |
 Not long ago we were fortunate to grab some time with Steph Ihezukwu who shared her insights and observation on everything from diversity in tech to how to collaborate with teams in the age of remote work and heightened security concerns - check it out...
Not long ago we were fortunate to grab some time with Steph Ihezukwu who shared her insights and observation on everything from diversity in tech to how to collaborate with teams in the age of remote work and heightened security concerns - check it out... |
||||
| 2020-11-11 04:30:00 | Cybereason XDR: Delivering Future-Ready Attack Protection Beyond the Endpoint (lien direct) |
 Today's targeted attacks increasingly take aim at multiple devices and users simultaneously while employing a range of tactics, techniques and procedures (TTPs). Defenders are forced to work in silos, employing disparate tools on each type of asset -- one solution for endpoint, another for cloud, a third for mobile and fourth to look at cloud identities.
Today's targeted attacks increasingly take aim at multiple devices and users simultaneously while employing a range of tactics, techniques and procedures (TTPs). Defenders are forced to work in silos, employing disparate tools on each type of asset -- one solution for endpoint, another for cloud, a third for mobile and fourth to look at cloud identities. |
||||
| 2020-11-09 18:19:07 | Ever Evolving: Yonatan Striem-Amit on Handling Breaches While Remote (lien direct) |
 Cybereason was established with an offensive mindset as the foundation of the company's approach to developing future-ready defensive products and solutions because it takes a deeper understanding of the attacker's perspective to create game changing technologies that work to reverse the adversary advantage and return the high ground to the defenders.
Cybereason was established with an offensive mindset as the foundation of the company's approach to developing future-ready defensive products and solutions because it takes a deeper understanding of the attacker's perspective to create game changing technologies that work to reverse the adversary advantage and return the high ground to the defenders. |
||||
| 2020-11-02 14:00:00 | Ever Evolving: Tanya Janca on Application Security Challenges (lien direct) |
 A few months ago, we were lucky enough to grab some time with Tanya Janca to discuss some key issues around security in times of crisis. Tanya has more than twenty years of experience in the security industry, and we're so fortunate to have her join us for the series - check it out...
A few months ago, we were lucky enough to grab some time with Tanya Janca to discuss some key issues around security in times of crisis. Tanya has more than twenty years of experience in the security industry, and we're so fortunate to have her join us for the series - check it out... |
||||
| 2020-11-02 05:00:00 | Back to the Future: Inside the Kimsuky KGH Spyware Suite (lien direct) |
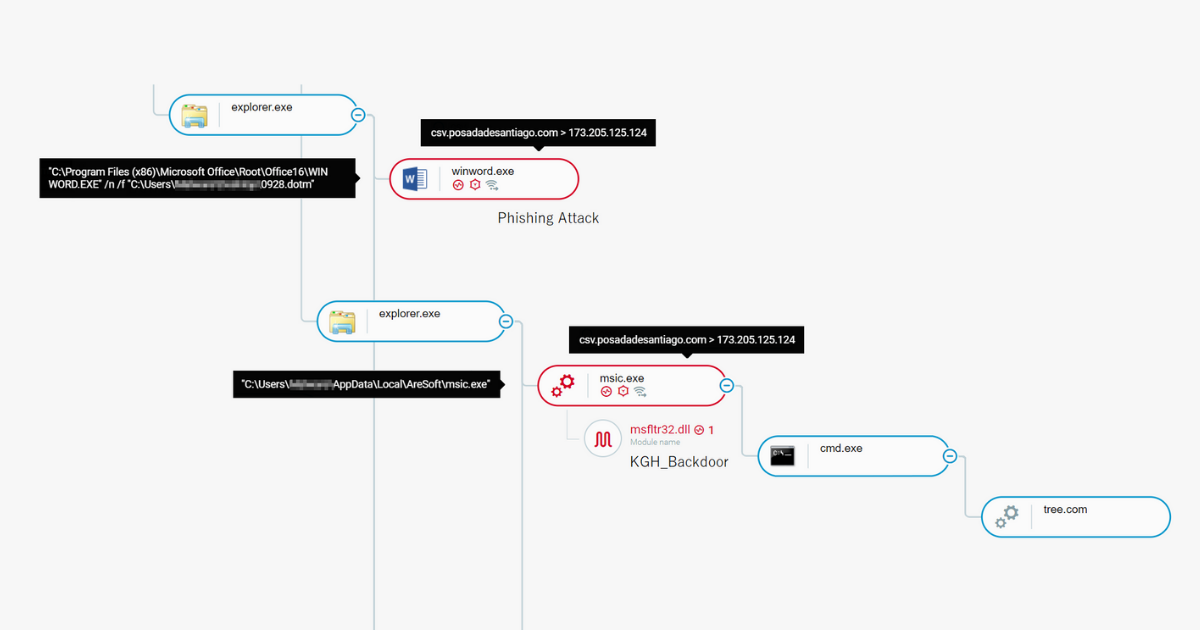 Research by: Assaf Dahan, Lior Rochberger, Daniel Frank and Tom Fakterman
Research by: Assaf Dahan, Lior Rochberger, Daniel Frank and Tom Fakterman |
||||
| 2020-10-30 19:55:19 | Law Enforcement Warns of Imminent Ransomware Threat to U.S. Hospitals (lien direct) |
 On October 29, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) published a joint alert with the Federal Bureau of Investigations (FBI) and the Department of Health and Human Services (HHS). In it, the organizations claimed to “have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” CISA, the FBI and HHS attributed the threat to the digital criminal enterprise behind TrickBot, malware which is capable of targeting victims with ransomware.
On October 29, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) published a joint alert with the Federal Bureau of Investigations (FBI) and the Department of Health and Human Services (HHS). In it, the organizations claimed to “have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” CISA, the FBI and HHS attributed the threat to the digital criminal enterprise behind TrickBot, malware which is capable of targeting victims with ransomware. |
Ransomware Malware Threat | |||
| 2020-10-30 10:54:33 | Ryuk Ransomware: Mitigation and Defense Action Items (lien direct) |
 The FBI, DHS, and HHS are warning of imminent Ryuk ransomware attacks targeting hospitals in the US. The story is being covered broadly by the industry media, including Krebs and various media outlets.
The FBI, DHS, and HHS are warning of imminent Ryuk ransomware attacks targeting hospitals in the US. The story is being covered broadly by the industry media, including Krebs and various media outlets. |
Ransomware | |||
| 2020-10-29 18:09:04 | Heart of Cyber Darkness: How I Became a Defender (lien direct) |
 When I went back into the workforce after my last degree in 1996, I made a big leap and returned to Canada to join a small team of passionate people in a brand new company called Signal 9 Solutions. I packed my bags and headed to the village of Ashton, Station Ontario not far from Ottawa, where thanks to my friend (and boss) Phil Attfield, I had a bed in Phil's basement, which had just flooded to due a thaw and snap freeze; I drove a green-minded, propane power Chrysler K-car with AM-only radio. This was the dream if you can believe it a quarter century later.
When I went back into the workforce after my last degree in 1996, I made a big leap and returned to Canada to join a small team of passionate people in a brand new company called Signal 9 Solutions. I packed my bags and headed to the village of Ashton, Station Ontario not far from Ottawa, where thanks to my friend (and boss) Phil Attfield, I had a bed in Phil's basement, which had just flooded to due a thaw and snap freeze; I drove a green-minded, propane power Chrysler K-car with AM-only radio. This was the dream if you can believe it a quarter century later. |
||||
| 2020-10-28 03:24:21 | Cybereason\'s Commitment to Defenders Now Backed by $1 Million Breach Protection Warranty (lien direct) |
 At Cybereason, we ask defenders to place their trust in us to protect their valuable assets, and in return we believe we owe them a level of accountability worthy of that trust. As an affirmation of our commitment to our customers and the confidence we have in the effectiveness of our platform, we are pleased to announce the Cybereason Breach Protection Warranty (PDF), which provides up to $1 Million in coverage in the event of a breach.
At Cybereason, we ask defenders to place their trust in us to protect their valuable assets, and in return we believe we owe them a level of accountability worthy of that trust. As an affirmation of our commitment to our customers and the confidence we have in the effectiveness of our platform, we are pleased to announce the Cybereason Breach Protection Warranty (PDF), which provides up to $1 Million in coverage in the event of a breach. |
To see everything:
Our RSS (filtrered)
