What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2021-09-01 13:02:03 | The Value Drivers for an XDR Investment (lien direct) |
 We have a pretty good idea by now of what Extended Detection and Response (XDR) is. As we noted in an earlier article, titled XDR: The Next Step in Threat Detection and Response, XDR is a security approach that builds on the successes of Endpoint Detection and Response (EDR).
We have a pretty good idea by now of what Extended Detection and Response (XDR) is. As we noted in an earlier article, titled XDR: The Next Step in Threat Detection and Response, XDR is a security approach that builds on the successes of Endpoint Detection and Response (EDR). |
Threat | |||
| 2021-08-31 12:01:26 | Evolving Ransomware Tactics Include Recruiting Insiders and DDoS Attacks (lien direct) |
 The attention generated by the DarkSide ransomware attack against Colonial Pipeline in May has helped to reshape the ransomware threat landscape. One of the most important modifications came when the digital crime forum XSS announced that members could no longer post about ransomware topics. The Exploit forum followed suit not long after, as reported by Bleeping Computer.
The attention generated by the DarkSide ransomware attack against Colonial Pipeline in May has helped to reshape the ransomware threat landscape. One of the most important modifications came when the digital crime forum XSS announced that members could no longer post about ransomware topics. The Exploit forum followed suit not long after, as reported by Bleeping Computer. |
Ransomware Threat | |||
| 2021-08-17 12:51:03 | XDR: The Key to Solving SIEM Shortcomings (lien direct) |
 One of the mainstays of organizations' digital security postures is a Security Information and Event Management (SIEM) platform. According to CSO Online, SIEMs augment threat monitoring and incident response with log analysis.
One of the mainstays of organizations' digital security postures is a Security Information and Event Management (SIEM) platform. According to CSO Online, SIEMs augment threat monitoring and incident response with log analysis. |
Threat | |||
| 2021-08-16 12:04:08 | (Déjà vu) Malicious Life Podcast: DeadRinger - Exposing Chinese APTs Targeting Major Telcos (lien direct) |
 Cybereason recently discovered several previously unidentified attack campaigns targeting the telecoms industry across Southeast Asia that are assessed to be the work of multiple Chinese APT groups. The attacks are detailed in the threat intelligence report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos.
Cybereason recently discovered several previously unidentified attack campaigns targeting the telecoms industry across Southeast Asia that are assessed to be the work of multiple Chinese APT groups. The attacks are detailed in the threat intelligence report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos. |
Threat | |||
| 2021-08-11 14:45:48 | The Rising Threat from LockBit Ransomware (lien direct) |
 LockBit ransomware is the latest threat posing an increased risk for organizations. The ransomware gang has been making headlines recently. LockBit has also reportedly compromised Accenture.
The group reportedly revealed the attack on their site on the DarkWeb, noting, “these people are beyond privacy and security. Hope their services are better than what I have seen inside. If you are interested in purchasing data sets, contact us.”
LockBit ransomware is the latest threat posing an increased risk for organizations. The ransomware gang has been making headlines recently. LockBit has also reportedly compromised Accenture.
The group reportedly revealed the attack on their site on the DarkWeb, noting, “these people are beyond privacy and security. Hope their services are better than what I have seen inside. If you are interested in purchasing data sets, contact us.” |
Ransomware Threat | |||
| 2021-08-09 12:18:15 | XDR: The Next Step in Threat Detection and Response (lien direct) |
 The global EDR market (Endpoint Detection and Response) is growing rapidly. The Transparency Market Research team predicted that this market will increase at a CAGR of about 21% in the next decade, reported Help Net Security. If it happens, this growth will help the global EDR market surpass a valuation of $13.8 billion by 2030.
The global EDR market (Endpoint Detection and Response) is growing rapidly. The Transparency Market Research team predicted that this market will increase at a CAGR of about 21% in the next decade, reported Help Net Security. If it happens, this growth will help the global EDR market surpass a valuation of $13.8 billion by 2030. |
Threat | |||
| 2021-08-03 04:03:00 | DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos (lien direct) |
 Following the discovery of Hafnium attacks targeting Microsoft Exchange vulnerabilities, the Cybereason Nocturnus and Incident Response teams proactively hunted for various threat actors trying to leverage similar techniques in-the-wild. In the beginning of 2021, the Cybereason Nocturnus Team investigated clusters of intrusions detected targeting the telecommunications industry across Southeast Asia. During the investigation, three clusters of activity were identified and showed significant connections to known threat actors, all suspected to be operating on behalf of Chinese state interests.
The report comes on the heels of the Biden administration's public rebuke of China's Ministry of State Security for the recent HAFNIUM attacks that exploited vulnerabilities in unpatched Microsoft Exchange Servers and put thousands of organizations worldwide at risk. Exploitation of these same vulnerabilities were central to the success of the attacks detailed in this research.
Following the discovery of Hafnium attacks targeting Microsoft Exchange vulnerabilities, the Cybereason Nocturnus and Incident Response teams proactively hunted for various threat actors trying to leverage similar techniques in-the-wild. In the beginning of 2021, the Cybereason Nocturnus Team investigated clusters of intrusions detected targeting the telecommunications industry across Southeast Asia. During the investigation, three clusters of activity were identified and showed significant connections to known threat actors, all suspected to be operating on behalf of Chinese state interests.
The report comes on the heels of the Biden administration's public rebuke of China's Ministry of State Security for the recent HAFNIUM attacks that exploited vulnerabilities in unpatched Microsoft Exchange Servers and put thousands of organizations worldwide at risk. Exploitation of these same vulnerabilities were central to the success of the attacks detailed in this research. |
Threat | |||
| 2021-08-03 04:00:17 | Webinar: DeadRinger - Exposing Chinese Threat Actors Targeting Major Telcos (lien direct) |
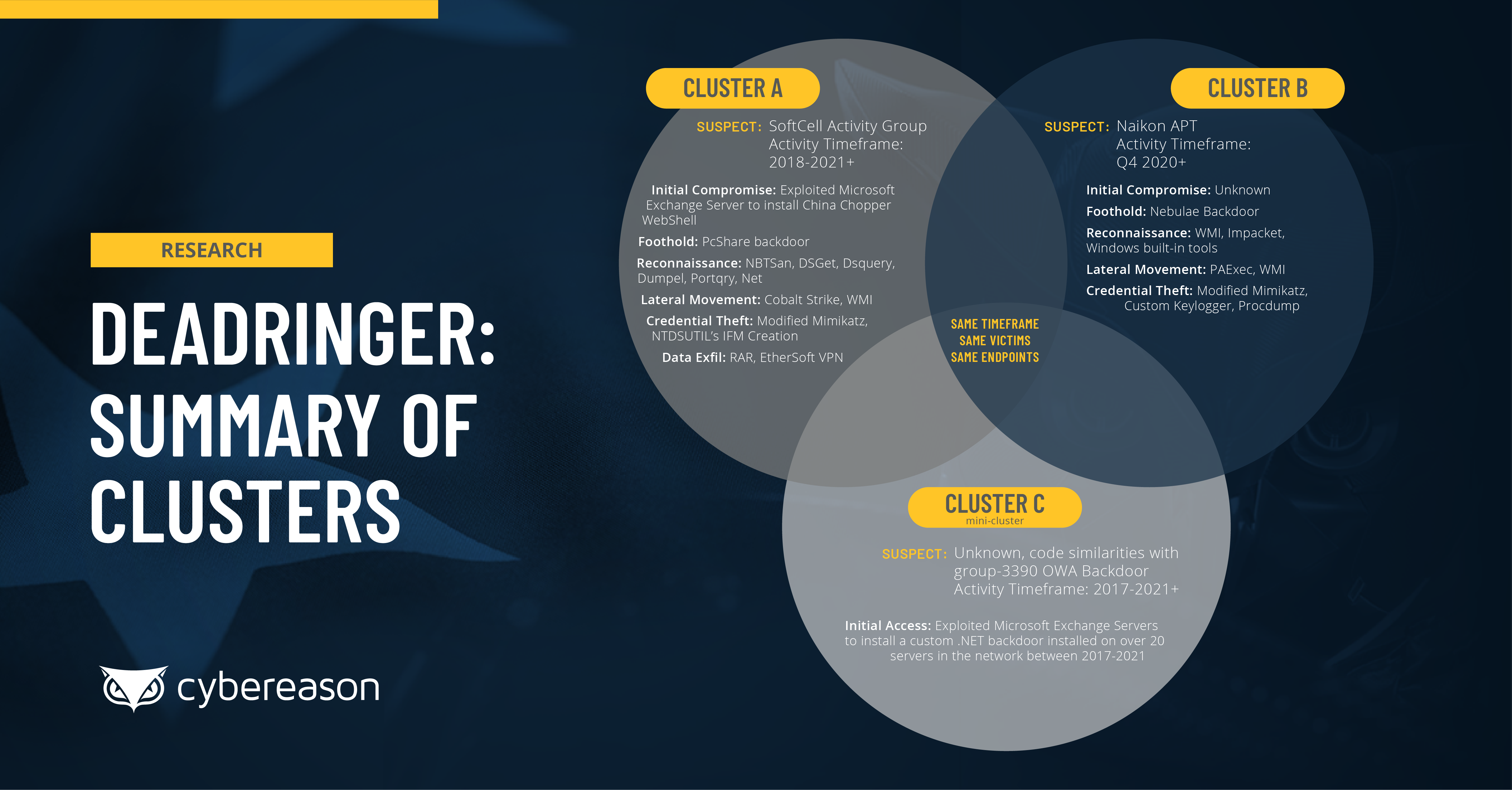 The Cybereason Nocturnus Research Team recently released a major threat intelligence research report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos, which details the discovery of several previously unidentified attack campaigns targeting the telecommunications industry across Southeast Asia, where several clusters of attack activity were identified and assessed to be the work of several prominent APT groups who are known to conduct operations aligned with the interests of the Chinese government.
The Cybereason Nocturnus Research Team recently released a major threat intelligence research report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos, which details the discovery of several previously unidentified attack campaigns targeting the telecommunications industry across Southeast Asia, where several clusters of attack activity were identified and assessed to be the work of several prominent APT groups who are known to conduct operations aligned with the interests of the Chinese government. |
Threat | |||
| 2021-06-17 12:32:14 | Biden-Putin Summit and Why Threat Actors Just Won\'t Give it a Rest (lien direct) |
 On June 11, McDonald's said in a message to its U.S. employees that it had discovered unauthorized activity on an internal security system. The burger chain responded by bringing on some external consultants to investigate what had happened, reported the Wall Street Journal.
On June 11, McDonald's said in a message to its U.S. employees that it had discovered unauthorized activity on an internal security system. The burger chain responded by bringing on some external consultants to investigate what had happened, reported the Wall Street Journal. |
Threat | |||
| 2021-06-14 11:59:48 | Ransomware Attacks are Evolving: What You Need to Know (lien direct) |
 One look at all the ransomware attacks from the past few years, and it's clear that crypto-malware actors are attempting to maximize their financial gain. We've observed these threat groups using multiple techniques to profit even more off their victims than in years past. Here are a few tactics that stood out to us.
One look at all the ransomware attacks from the past few years, and it's clear that crypto-malware actors are attempting to maximize their financial gain. We've observed these threat groups using multiple techniques to profit even more off their victims than in years past. Here are a few tactics that stood out to us.
|
Ransomware Threat | |||
| 2021-06-01 16:53:30 | SolarWinds Threat Actors Behind New Email Attack Campaign (lien direct) |
 The threat actors behind last year's SolarWinds supply chain attack have launched a new email attack campaign aimed at organizations around the world. This attack wave attracted the attention of the Microsoft Threat Intelligence Center (MSTIC) on May 25.
The threat actors behind last year's SolarWinds supply chain attack have launched a new email attack campaign aimed at organizations around the world. This attack wave attracted the attention of the Microsoft Threat Intelligence Center (MSTIC) on May 25. |
Threat | |||
| 2021-05-25 12:23:45 | New Cybersecurity Executive Order: Will It Have Impact? (lien direct) |
 The state of the threat landscape in general, and incidents like the recent ransomware attack against Colonial Pipeline demand that we take immediate action to improve cybersecurity defenses. The recent executive order (EO) on cybersecurity from President Biden is a bold step in the right direction.
The state of the threat landscape in general, and incidents like the recent ransomware attack against Colonial Pipeline demand that we take immediate action to improve cybersecurity defenses. The recent executive order (EO) on cybersecurity from President Biden is a bold step in the right direction. |
Threat | |||
| 2021-04-30 12:20:47 | 100 Days Down, 1,360 Days of Nation-State Cybersecurity Threats to Go (lien direct) |
 This week marks the milestone of the Biden Administration's first 100 days. It is somewhat arbitrary to expect an incoming president to achieve significant progress in just 100 days, or to judge success or failure based on such a small span of time.
However, it does provide a glimpse into the vision and direction of the administration, and so far it seems like President Biden is preparing to address the growing cybersecurity threat from our adversaries.
This week marks the milestone of the Biden Administration's first 100 days. It is somewhat arbitrary to expect an incoming president to achieve significant progress in just 100 days, or to judge success or failure based on such a small span of time.
However, it does provide a glimpse into the vision and direction of the administration, and so far it seems like President Biden is preparing to address the growing cybersecurity threat from our adversaries. |
Threat | |||
| 2021-04-30 12:11:34 | PortDoor: New Chinese APT Backdoor Attack Targets Russian Defense Sector (lien direct) |
 The Cybereason Nocturnus Team has been tracking recent developments in the RoyalRoad weaponizer, also known as the 8.t Dropper/RTF exploit builder. Over the years, this tool has become a part of the arsenal of several Chinese-related threat actors such as Tick, Tonto Team and TA428, all of which employ RoyalRoad regularly for spear-phishing in targeted attacks against high-value targets.
The Cybereason Nocturnus Team has been tracking recent developments in the RoyalRoad weaponizer, also known as the 8.t Dropper/RTF exploit builder. Over the years, this tool has become a part of the arsenal of several Chinese-related threat actors such as Tick, Tonto Team and TA428, all of which employ RoyalRoad regularly for spear-phishing in targeted attacks against high-value targets. |
Tool Threat | |||
| 2021-04-28 12:59:38 | Five Things You Need to Know About Ransomware Attacks (lien direct) |
 The digital threat landscape as a whole is constantly changing and evolving. That can make it difficult to keep track of new developments for specific threats like ransomware. Don't worry though, Cybereason has got you covered.
The digital threat landscape as a whole is constantly changing and evolving. That can make it difficult to keep track of new developments for specific threats like ransomware. Don't worry though, Cybereason has got you covered. |
Ransomware Threat | |||
| 2021-04-15 18:02:25 | MITRE ATT&CK Evaluations - Unpacking the Emulation (lien direct) |
 If you've been researching MITRE ATT&CK and aligning your security program maturity measurement to it, you're likely excited for this year's ATT&CK evaluation from MITRE Engenuity, which tests security vendors' ability to quickly detect and stop tactics and techniques used by today's threat actors.
If you've been researching MITRE ATT&CK and aligning your security program maturity measurement to it, you're likely excited for this year's ATT&CK evaluation from MITRE Engenuity, which tests security vendors' ability to quickly detect and stop tactics and techniques used by today's threat actors. |
Threat | |||
| 2021-03-23 18:00:09 | Malicious Life Podcast: Inside the HAFNIUM Microsoft Exchange Attacks (lien direct) |
 The recent HAFNIUM attacks hit tens of thousands of organizations' Microsoft Exchange servers around the globe. Now, an array of other threat actors are leveraging the residual webshells on victim systems to launch new attacks against organizations who thought patching the Microsoft vulnerabilities would have been enough to be protected.
The recent HAFNIUM attacks hit tens of thousands of organizations' Microsoft Exchange servers around the globe. Now, an array of other threat actors are leveraging the residual webshells on victim systems to launch new attacks against organizations who thought patching the Microsoft vulnerabilities would have been enough to be protected. |
Threat Patching | |||
| 2021-03-18 15:27:30 | HAFNIUM Response: Cybereason is Dedicated to Defending Our Customers (lien direct) |
 It was recently disclosed that Microsoft Exchange offerings were severely compromised in nation-state sponsored operations by the threat group known as HAFNIUM. This incident has potentially affected tens-of-thousands of public and private organizations across the globe.
It was recently disclosed that Microsoft Exchange offerings were severely compromised in nation-state sponsored operations by the threat group known as HAFNIUM. This incident has potentially affected tens-of-thousands of public and private organizations across the globe. |
Threat | |||
| 2021-03-11 17:36:05 | Live Feeds of 150K Surveillance Cameras Compromised in Verkada Breach (lien direct) |
 Digital attackers compromised the live feeds of 150,000 surveillance cameras made by enterprise security camera system manufacturer Verkada. According to Bloomberg News, a hacking collective that calls itself “Advanced Persistent Threat 69420” gained access to Verkada by misusing a “Super Admin” account at the company.
Digital attackers compromised the live feeds of 150,000 surveillance cameras made by enterprise security camera system manufacturer Verkada. According to Bloomberg News, a hacking collective that calls itself “Advanced Persistent Threat 69420” gained access to Verkada by misusing a “Super Admin” account at the company. |
Threat | |||
| 2021-02-17 18:35:26 | Global Law Firm Attributes Data Breach to Compromise at File Sharing Provider (lien direct) |
 An international law firm attributed a data breach to a compromise at a cloud solutions company that provides file-sharing services. According to the Wall Street Journal, a threat actor claimed to have stolen data from global law firm Jones Day and published that information on the dark web.
An international law firm attributed a data breach to a compromise at a cloud solutions company that provides file-sharing services. According to the Wall Street Journal, a threat actor claimed to have stolen data from global law firm Jones Day and published that information on the dark web. |
Data Breach Threat | |||
| 2021-02-16 13:00:00 | Cybereason vs. NetWalker Ransomware (lien direct) |
 The NetWalker ransomware has been one of the most notorious ransomware families over the course of the past year, targeting organizations in the US and Europe including several healthcare organizations, despite several known threat actors publicly claiming to abstain from targeting such organizations due to COVID-19.
The NetWalker ransomware has been one of the most notorious ransomware families over the course of the past year, targeting organizations in the US and Europe including several healthcare organizations, despite several known threat actors publicly claiming to abstain from targeting such organizations due to COVID-19. |
Ransomware Threat | |||
| 2021-01-25 14:44:34 | Wipro\'s State of Cybersecurity Report Reveals Valuable Insights (lien direct) |
 It is true in general that technology is always changing, and the threat landscape is constantly evolving, but 2020 has amplified the cybersecurity challenge. Organizations of all sizes and across all industries already struggled to effectively manage risk and cyber resilience, but the global pandemic of COVID-19 has introduced a sudden and dramatic shift that tips the playing field in favor of attackers and exacerbates the task.
It is true in general that technology is always changing, and the threat landscape is constantly evolving, but 2020 has amplified the cybersecurity challenge. Organizations of all sizes and across all industries already struggled to effectively manage risk and cyber resilience, but the global pandemic of COVID-19 has introduced a sudden and dramatic shift that tips the playing field in favor of attackers and exacerbates the task. |
Threat | |||
| 2020-12-07 20:46:46 | Ever Evolving: Katie Nickels on Incident Response in a Remote World (lien direct) |
 We spent some time with Katie Nickels - current Director of Intelligence at Red Canary and formerly MITRE ATT&CK Threat Intelligence Lead - to discuss applied threat intelligence, prioritizing threats for impact, and working incident response in remote environments - check it out...
We spent some time with Katie Nickels - current Director of Intelligence at Red Canary and formerly MITRE ATT&CK Threat Intelligence Lead - to discuss applied threat intelligence, prioritizing threats for impact, and working incident response in remote environments - check it out... |
Threat Guideline | APT 15 | ||
| 2020-10-30 19:55:19 | Law Enforcement Warns of Imminent Ransomware Threat to U.S. Hospitals (lien direct) |
 On October 29, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) published a joint alert with the Federal Bureau of Investigations (FBI) and the Department of Health and Human Services (HHS). In it, the organizations claimed to “have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” CISA, the FBI and HHS attributed the threat to the digital criminal enterprise behind TrickBot, malware which is capable of targeting victims with ransomware.
On October 29, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) published a joint alert with the Federal Bureau of Investigations (FBI) and the Department of Health and Human Services (HHS). In it, the organizations claimed to “have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” CISA, the FBI and HHS attributed the threat to the digital criminal enterprise behind TrickBot, malware which is capable of targeting victims with ransomware. |
Ransomware Malware Threat | |||
| 2020-09-22 17:23:19 | VB2020: Anchor, Bazar, and the Trickbot Connection (lien direct) |
 VB2020, the annual Virus Bulletin international conference “featuring the latest and best research on malware, malicious actors and threat intelligence,” has gone virtual this year and will be live-streamed 30 Sept - 2 Oct, 2020. The conference is free of charge, and offers a wide selection of presentations for on-demand viewing in addition to the live sessions.
VB2020, the annual Virus Bulletin international conference “featuring the latest and best research on malware, malicious actors and threat intelligence,” has gone virtual this year and will be live-streamed 30 Sept - 2 Oct, 2020. The conference is free of charge, and offers a wide selection of presentations for on-demand viewing in addition to the live sessions. |
Threat |
To see everything:
Our RSS (filtrered)
