What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-10-03 13:00:00 | L'épidémie silencieuse: découvrir les dangers de la fatigue alerte et comment le surmonter The Silent Epidemic: Uncovering the Dangers of Alert Fatigue and How to Overcome It (lien direct) |
 À l'ère numérique d'aujourd'hui, les cyberattaques sont devenues une menace commune et constante pour les individus et les organisations.Des escroqueries à phishing aux attaques de logiciels malveillants, les cybercriminels trouvent constamment de nouvelles façons d'exploiter les vulnérabilités et de voler des informations sensibles.Les ransomwares sont de plus en plus répandus, avec des attaques de haut niveau ciblant les grandes organisations, les agences gouvernementales et les systèmes de santé.Les conséquences d'une attaque de ransomware peuvent être dévastatrices, entraînant une perte financière, des dommages de réputation et même le compromis de données sensibles.
À l'ère numérique d'aujourd'hui, les cyberattaques sont devenues une menace commune et constante pour les individus et les organisations.Des escroqueries à phishing aux attaques de logiciels malveillants, les cybercriminels trouvent constamment de nouvelles façons d'exploiter les vulnérabilités et de voler des informations sensibles.Les ransomwares sont de plus en plus répandus, avec des attaques de haut niveau ciblant les grandes organisations, les agences gouvernementales et les systèmes de santé.Les conséquences d'une attaque de ransomware peuvent être dévastatrices, entraînant une perte financière, des dommages de réputation et même le compromis de données sensibles.
 In today\'s digital age, cyberattacks have become a common and constant threat to individuals and organizations alike. From phishing scams to malware attacks, cybercriminals are constantly finding new ways to exploit vulnerabilities and steal sensitive information. Ransomware is increasingly prevalent, with high-profile attacks targeting large organizations, government agencies, and healthcare systems. The consequences of a ransomware attack can be devastating, resulting in financial loss, reputational damage, and even the compromise of sensitive data.
In today\'s digital age, cyberattacks have become a common and constant threat to individuals and organizations alike. From phishing scams to malware attacks, cybercriminals are constantly finding new ways to exploit vulnerabilities and steal sensitive information. Ransomware is increasingly prevalent, with high-profile attacks targeting large organizations, government agencies, and healthcare systems. The consequences of a ransomware attack can be devastating, resulting in financial loss, reputational damage, and even the compromise of sensitive data. |
Ransomware Malware Vulnerability Threat Medical | ★★ | ||
| 2024-07-15 19:33:45 | Podcast MALICICE Life: Pourquoi les gens ont-ils écrit des virus dans les années 80 et 90? Malicious Life Podcast: Why Did People Write Viruses In The 80s & 90s? (lien direct) |
Malware | ★★ | |||
| 2024-02-12 16:37:24 | De Cracked à piraté: les logiciels malveillants se propagent via des vidéos YouTube From Cracked to Hacked: Malware Spread via YouTube Videos (lien direct) |
 Ce rapport d'analyse des menaces se plongera dans les comptes YouTube compromis utilisés comme vecteur pour la propagation des logiciels malveillants.Il décrira comment ce vecteur d'attaque est exploité pour les campagnes à faible combustion et à faible coût, mettant en évidence les stratégies utilisées par les acteurs de la menace et comment les défenseurs peuvent détecter et prévenir ces attaques. & NBSP;
Ce rapport d'analyse des menaces se plongera dans les comptes YouTube compromis utilisés comme vecteur pour la propagation des logiciels malveillants.Il décrira comment ce vecteur d'attaque est exploité pour les campagnes à faible combustion et à faible coût, mettant en évidence les stratégies utilisées par les acteurs de la menace et comment les défenseurs peuvent détecter et prévenir ces attaques. & NBSP;
 This Threat Analysis Report will delve into compromised YouTube accounts being used as a vector for the spread of malware. It will outline how this attack vector is exploited for low-burn, low-cost campaigns, highlighting strategies used by threat actors and how defenders can detect and prevent these attacks.
This Threat Analysis Report will delve into compromised YouTube accounts being used as a vector for the spread of malware. It will outline how this attack vector is exploited for low-burn, low-cost campaigns, highlighting strategies used by threat actors and how defenders can detect and prevent these attacks. |
Malware Threat | ★★★ | ||
| 2022-07-20 13:49:40 | Ransomware Attacks by the Numbers - and How to Defend Against Them (lien direct) |
 Ransomware is an ever-evolving type of malware that has been around for more than two decades. First appearing in the late 1980s and growing in popularity and complexity in the early 2010s, Ransomware has risen to an unprecedented level with multi-million dollar ransom demands in attacks against companies like Colonial Pipeline, JBS Foods and other critical infrastructure providers.
Ransomware is an ever-evolving type of malware that has been around for more than two decades. First appearing in the late 1980s and growing in popularity and complexity in the early 2010s, Ransomware has risen to an unprecedented level with multi-million dollar ransom demands in attacks against companies like Colonial Pipeline, JBS Foods and other critical infrastructure providers. |
Ransomware Malware | |||
| 2022-05-04 04:02:00 | Operation CuckooBees: Cybereason Uncovers Massive Chinese Intellectual Property Theft Operation (lien direct) |
 Cybersecurity often focuses on malware campaigns or the latest zero-day exploit. Surveys and reports reveal the average cost of a data breach or how much it typically costs to recover from a ransomware attack. Those are the attacks that make noise and capture attention, though. The attacks that fly under the radar are often more insidious and much more costly.
Cybersecurity often focuses on malware campaigns or the latest zero-day exploit. Surveys and reports reveal the average cost of a data breach or how much it typically costs to recover from a ransomware attack. Those are the attacks that make noise and capture attention, though. The attacks that fly under the radar are often more insidious and much more costly. |
Ransomware Data Breach Malware | |||
| 2022-05-04 04:00:00 | Operation CuckooBees: A Winnti Malware Arsenal Deep-Dive (lien direct) |
 In part one of this research, the Cybereason Nocturnus Incident Response Team provided a unique glimpse into the Wintti intrusion playbook, covering the techniques that were used by the group from initial compromise to stealing the data, as observed and analyzed by the Cybereason Incident Response team.
In part one of this research, the Cybereason Nocturnus Incident Response Team provided a unique glimpse into the Wintti intrusion playbook, covering the techniques that were used by the group from initial compromise to stealing the data, as observed and analyzed by the Cybereason Incident Response team. |
Malware | APT 41 | ||
| 2021-10-28 13:00:12 | (Déjà vu) THREAT ANALYSIS REPORT: Snake Infostealer Malware (lien direct) |
 The Cybereason Global Security Operations Center (GSOC) issues Cybereason Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them.
The Cybereason Global Security Operations Center (GSOC) issues Cybereason Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them. |
Malware Threat | |||
| 2021-10-22 19:31:06 | Microsoft OneDrive Used for Ransom Operations (lien direct) |
 Microsoft was called out recently after it was discovered that hundreds of malware files commonly used to launch Conti ransomware attacks are being hosted from their OneDrive cloud storage service. The news highlights once again that Microsoft needs to invest significant time and resources just to get its own security house in order-and why they have no business trying to sell customers cybersecurity solutions to problems they created.
Microsoft was called out recently after it was discovered that hundreds of malware files commonly used to launch Conti ransomware attacks are being hosted from their OneDrive cloud storage service. The news highlights once again that Microsoft needs to invest significant time and resources just to get its own security house in order-and why they have no business trying to sell customers cybersecurity solutions to problems they created. |
Ransomware Malware | |||
| 2021-04-27 14:52:51 | Cybereason vs. Avaddon Ransomware (lien direct) |
 Over the last few months, the Cybereason Nocturnus Team has been tracking the activity of the Avaddon Ransomware. It has been active since June 2020 and is operating with the Ransomware-as-a-Service (RaaS) and double extortion models, targeting sectors such as healthcare. Avaddon is distributed via malspam campaigns, where the victim is being lured to download the malware loader.
Over the last few months, the Cybereason Nocturnus Team has been tracking the activity of the Avaddon Ransomware. It has been active since June 2020 and is operating with the Ransomware-as-a-Service (RaaS) and double extortion models, targeting sectors such as healthcare. Avaddon is distributed via malspam campaigns, where the victim is being lured to download the malware loader. |
Ransomware Malware | |||
| 2021-04-22 19:27:46 | HAFNIUM Exploits Live On (lien direct) |
 The Prometei Botnet is not new. Like most malware and exploits, it continues to adapt and change over time. What is concerning is what is happening now. Our latest research demonstrates how Prometei has evolved and reveals that current versions of Prometei are now exploiting some of the vulnerabilities in Microsoft Exchange that were part of the recent HAFNIUM attacks. We will continue to deal with lingering effects from these specific Microsoft Exchange vulnerabilities, but-more importantly-we will continue to deal with vulnerabilities in general and that requires a better approach to cybersecurity.
The Prometei Botnet is not new. Like most malware and exploits, it continues to adapt and change over time. What is concerning is what is happening now. Our latest research demonstrates how Prometei has evolved and reveals that current versions of Prometei are now exploiting some of the vulnerabilities in Microsoft Exchange that were part of the recent HAFNIUM attacks. We will continue to deal with lingering effects from these specific Microsoft Exchange vulnerabilities, but-more importantly-we will continue to deal with vulnerabilities in general and that requires a better approach to cybersecurity. |
Malware | |||
| 2021-04-19 13:25:54 | Ransomware Decoded: Preventing Modern Ransomware Attacks (lien direct) |
 Many types of malware silently persist on the network, move laterally, communicate with their C2, or obfuscate their behaviors to prevent detection. In contrast to this, traditional ransomware was all about coming in with a big splash and causing immediate damage.
Many types of malware silently persist on the network, move laterally, communicate with their C2, or obfuscate their behaviors to prevent detection. In contrast to this, traditional ransomware was all about coming in with a big splash and causing immediate damage. |
Ransomware Malware | |||
| 2021-04-12 02:50:19 | Five Clear Steps to Enhance SecOps with MITRE ATT@CK (lien direct) |
 A skyrocketing number of alerts, limited security talent, and millions of new malware strains daily have made security a seemingly insurmountable task.
A skyrocketing number of alerts, limited security talent, and millions of new malware strains daily have made security a seemingly insurmountable task. |
Malware | |||
| 2021-03-18 10:04:34 | Cybereason Exposes Campaign Targeting US Taxpayers with NetWire and Remcos Malware (lien direct) |
 Over the past year, the Cybereason Nocturnus Team has observed various trends among cyber criminals and nation-state groups leveraging various global events such as COVID-19 and other topical themes and trending issues as phishing content to lure their victims into installing their malware of choice.
Over the past year, the Cybereason Nocturnus Team has observed various trends among cyber criminals and nation-state groups leveraging various global events such as COVID-19 and other topical themes and trending issues as phishing content to lure their victims into installing their malware of choice. |
Malware | |||
| 2020-12-15 18:11:05 | Molerats APT: New Malware and Techniques in Middle East Espionage Campaign (lien direct) |
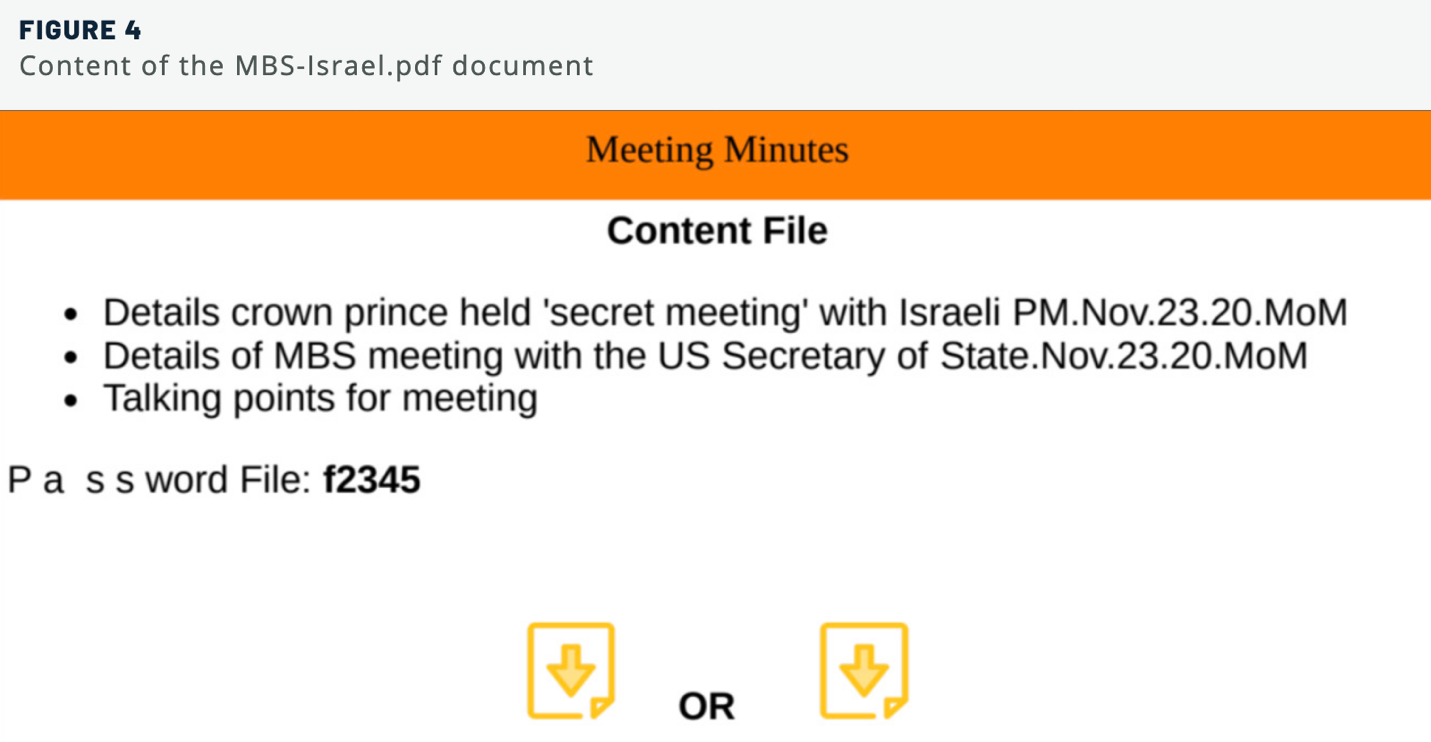 Security researchers observed a politically motivated APT called “Molerats” using three new malware variants to conduct espionage in the Middle East.
Security researchers observed a politically motivated APT called “Molerats” using three new malware variants to conduct espionage in the Middle East. |
Malware | |||
| 2020-12-09 02:00:00 | New Malware Arsenal Abusing Cloud Platforms in Middle East Espionage Campaign (lien direct) |
 The Cybereason Nocturnus Team has identified an active espionage campaign employing three previously unidentified malware variants that use Facebook, Dropbox, Google Docs and Simplenote for command & control and the exfiltration of data from targets across the Middle East. The full report can be downloaded here (ungated).
The Cybereason Nocturnus Team has identified an active espionage campaign employing three previously unidentified malware variants that use Facebook, Dropbox, Google Docs and Simplenote for command & control and the exfiltration of data from targets across the Middle East. The full report can be downloaded here (ungated). |
Malware | |||
| 2020-11-18 04:15:00 | Novel Chaes Malware Underscores Heightened E-Commerce Risk This Holiday Season (lien direct) |
 The Cybereason Nocturnus Team has identified an active campaign targeting customers of a larger e-commerce platform with newly identified multi-stage malware that evades antivirus tools dubbed Chaes.
The Cybereason Nocturnus Team has identified an active campaign targeting customers of a larger e-commerce platform with newly identified multi-stage malware that evades antivirus tools dubbed Chaes. |
Malware | |||
| 2020-10-30 19:55:19 | Law Enforcement Warns of Imminent Ransomware Threat to U.S. Hospitals (lien direct) |
 On October 29, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) published a joint alert with the Federal Bureau of Investigations (FBI) and the Department of Health and Human Services (HHS). In it, the organizations claimed to “have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” CISA, the FBI and HHS attributed the threat to the digital criminal enterprise behind TrickBot, malware which is capable of targeting victims with ransomware.
On October 29, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) published a joint alert with the Federal Bureau of Investigations (FBI) and the Department of Health and Human Services (HHS). In it, the organizations claimed to “have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” CISA, the FBI and HHS attributed the threat to the digital criminal enterprise behind TrickBot, malware which is capable of targeting victims with ransomware. |
Ransomware Malware Threat | |||
| 2020-06-23 17:06:55 | Next-generation Antivirus 101: Layers of Prevention (lien direct) |
 The foundation of the antivirus industry was built in the 1980s, with companies like McAfee and Avast releasing their first antivirus products. At that time, the terms “malware” and “computer virus” were just being born. Over the course of the next forty years, attackers would develop malware into the broad mix of crude and sophisticated software we see today. Now, there are over 1000M new malware samples classified every year.
The foundation of the antivirus industry was built in the 1980s, with companies like McAfee and Avast releasing their first antivirus products. At that time, the terms “malware” and “computer virus” were just being born. Over the course of the next forty years, attackers would develop malware into the broad mix of crude and sophisticated software we see today. Now, there are over 1000M new malware samples classified every year. |
Malware |
1
We have: 18 articles.
We have: 18 articles.
To see everything:
Our RSS (filtrered)
