What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-06-13 13:00:00 | CyberheistNews Vol 13 # 24 [Le biais de l'esprit \\] le prétexage dépasse désormais le phishing dans les attaques d'ingénierie sociale CyberheistNews Vol 13 #24 [The Mind\\'s Bias] Pretexting Now Tops Phishing in Social Engineering Attacks (lien direct) |
 CyberheistNews Vol 13 #24 | June 13th, 2023
[The Mind\'s Bias] Pretexting Now Tops Phishing in Social Engineering Attacks
The New Verizon DBIR is a treasure trove of data. As we will cover a bit below, Verizon reported that 74% of data breaches Involve the "Human Element," so people are one of the most common factors contributing to successful data breaches. Let\'s drill down a bit more in the social engineering section.
They explained: "Now, who has received an email or a direct message on social media from a friend or family member who desperately needs money? Probably fewer of you. This is social engineering (pretexting specifically) and it takes more skill.
"The most convincing social engineers can get into your head and convince you that someone you love is in danger. They use information they have learned about you and your loved ones to trick you into believing the message is truly from someone you know, and they use this invented scenario to play on your emotions and create a sense of urgency. The DBIR Figure 35 shows that Pretexting is now more prevalent than Phishing in Social Engineering incidents. However, when we look at confirmed breaches, Phishing is still on top."
A social attack known as BEC, or business email compromise, can be quite intricate. In this type of attack, the perpetrator uses existing email communications and information to deceive the recipient into carrying out a seemingly ordinary task, like changing a vendor\'s bank account details. But what makes this attack dangerous is that the new bank account provided belongs to the attacker. As a result, any payments the recipient makes to that account will simply disappear.
BEC Attacks Have Nearly Doubled
It can be difficult to spot these attacks as the attackers do a lot of preparation beforehand. They may create a domain doppelganger that looks almost identical to the real one and modify the signature block to show their own number instead of the legitimate vendor.
Attackers can make many subtle changes to trick their targets, especially if they are receiving many similar legitimate requests. This could be one reason why BEC attacks have nearly doubled across the DBIR entire incident dataset, as shown in Figure 36, and now make up over 50% of incidents in this category.
Financially Motivated External Attackers Double Down on Social Engineering
Timely detection and response is crucial when dealing with social engineering attacks, as well as most other attacks. Figure 38 shows a steady increase in the median cost of BECs since 2018, now averaging around $50,000, emphasizing the significance of quick detection.
However, unlike the times we live in, this section isn\'t all doom and
CyberheistNews Vol 13 #24 | June 13th, 2023
[The Mind\'s Bias] Pretexting Now Tops Phishing in Social Engineering Attacks
The New Verizon DBIR is a treasure trove of data. As we will cover a bit below, Verizon reported that 74% of data breaches Involve the "Human Element," so people are one of the most common factors contributing to successful data breaches. Let\'s drill down a bit more in the social engineering section.
They explained: "Now, who has received an email or a direct message on social media from a friend or family member who desperately needs money? Probably fewer of you. This is social engineering (pretexting specifically) and it takes more skill.
"The most convincing social engineers can get into your head and convince you that someone you love is in danger. They use information they have learned about you and your loved ones to trick you into believing the message is truly from someone you know, and they use this invented scenario to play on your emotions and create a sense of urgency. The DBIR Figure 35 shows that Pretexting is now more prevalent than Phishing in Social Engineering incidents. However, when we look at confirmed breaches, Phishing is still on top."
A social attack known as BEC, or business email compromise, can be quite intricate. In this type of attack, the perpetrator uses existing email communications and information to deceive the recipient into carrying out a seemingly ordinary task, like changing a vendor\'s bank account details. But what makes this attack dangerous is that the new bank account provided belongs to the attacker. As a result, any payments the recipient makes to that account will simply disappear.
BEC Attacks Have Nearly Doubled
It can be difficult to spot these attacks as the attackers do a lot of preparation beforehand. They may create a domain doppelganger that looks almost identical to the real one and modify the signature block to show their own number instead of the legitimate vendor.
Attackers can make many subtle changes to trick their targets, especially if they are receiving many similar legitimate requests. This could be one reason why BEC attacks have nearly doubled across the DBIR entire incident dataset, as shown in Figure 36, and now make up over 50% of incidents in this category.
Financially Motivated External Attackers Double Down on Social Engineering
Timely detection and response is crucial when dealing with social engineering attacks, as well as most other attacks. Figure 38 shows a steady increase in the median cost of BECs since 2018, now averaging around $50,000, emphasizing the significance of quick detection.
However, unlike the times we live in, this section isn\'t all doom and |
Spam Malware Vulnerability Threat Patching | Uber APT 37 ChatGPT ChatGPT APT 43 | ★★ | |
| 2023-05-31 13:00:00 | Cyberheistnews Vol 13 # 22 [Eye on Fraud] Un examen plus approfondi de la hausse massive de 72% des attaques de phishing financier CyberheistNews Vol 13 #22 [Eye on Fraud] A Closer Look at the Massive 72% Spike in Financial Phishing Attacks (lien direct) |
 CyberheistNews Vol 13 #22 | May 31st, 2023
[Eye on Fraud] A Closer Look at the Massive 72% Spike in Financial Phishing Attacks
With attackers knowing financial fraud-based phishing attacks are best suited for the one industry where the money is, this massive spike in attacks should both surprise you and not surprise you at all.
When you want tires, where do you go? Right – to the tire store. Shoes? Yup – shoe store. The most money you can scam from a single attack? That\'s right – the financial services industry, at least according to cybersecurity vendor Armorblox\'s 2023 Email Security Threat Report.
According to the report, the financial services industry as a target has increased by 72% over 2022 and was the single largest target of financial fraud attacks, representing 49% of all such attacks. When breaking down the specific types of financial fraud, it doesn\'t get any better for the financial industry:
51% of invoice fraud attacks targeted the financial services industry
42% were payroll fraud attacks
63% were payment fraud
To make matters worse, nearly one-quarter (22%) of financial fraud attacks successfully bypassed native email security controls, according to Armorblox. That means one in five email-based attacks made it all the way to the Inbox.
The next layer in your defense should be a user that\'s properly educated using security awareness training to easily identify financial fraud and other phishing-based threats, stopping them before they do actual damage.
Blog post with links:https://blog.knowbe4.com/financial-fraud-phishing
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us Wednesday, June 7, @ 2:00 PM (ET), for a live demonstration of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
CyberheistNews Vol 13 #22 | May 31st, 2023
[Eye on Fraud] A Closer Look at the Massive 72% Spike in Financial Phishing Attacks
With attackers knowing financial fraud-based phishing attacks are best suited for the one industry where the money is, this massive spike in attacks should both surprise you and not surprise you at all.
When you want tires, where do you go? Right – to the tire store. Shoes? Yup – shoe store. The most money you can scam from a single attack? That\'s right – the financial services industry, at least according to cybersecurity vendor Armorblox\'s 2023 Email Security Threat Report.
According to the report, the financial services industry as a target has increased by 72% over 2022 and was the single largest target of financial fraud attacks, representing 49% of all such attacks. When breaking down the specific types of financial fraud, it doesn\'t get any better for the financial industry:
51% of invoice fraud attacks targeted the financial services industry
42% were payroll fraud attacks
63% were payment fraud
To make matters worse, nearly one-quarter (22%) of financial fraud attacks successfully bypassed native email security controls, according to Armorblox. That means one in five email-based attacks made it all the way to the Inbox.
The next layer in your defense should be a user that\'s properly educated using security awareness training to easily identify financial fraud and other phishing-based threats, stopping them before they do actual damage.
Blog post with links:https://blog.knowbe4.com/financial-fraud-phishing
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us Wednesday, June 7, @ 2:00 PM (ET), for a live demonstration of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
|
Ransomware Malware Hack Tool Threat Conference | Uber ChatGPT ChatGPT Guam | ★★ | |
| 2023-03-07 14:00:00 | CyberheistNews Vol 13 #10 [Eye Opener] BusinessWeek: The Satellite Hack Everyone Is Finally Talking About (lien direct) |
 CyberheistNews Vol 13 #10 | March 7th, 2023
[Eye Opener] BusinessWeek: The Satellite Hack Everyone Is Finally Talking About
This week, Bloomberg News pointed at a brand-new article at BusinessWeek, one of their media properties. This is an excellent article that exposes the vulnerabilities when communications systems are not secure by design. It is an excellent wake-up call for your C-level execs and powerful budget ammo.
They started out with: "As Putin began his invasion of Ukraine, a network used throughout Europe-and by the Ukrainian military-faced an unprecedented cyberattack that doubled as an industrywide wake-up call. What they refer to is the Viasat hack. The KnowBe4 blog initially reported on this hack on March 24, 2022 here: https://blog.knowbe4.com/wired-a-mysterious-satellite-hack-has-victims-far-beyond-ukraine and in our CyberheistNews May 17, 2022 here: https://blog.knowbe4.com/cyberheistnews-vol-12-20-heads-up-now-you-need-to-watch-out-for-spoofed-vanity-urls.
The article continues to describe how a large number of Viasat customers lost connectivity. Here is a quote: "Viasat staffers in the U.S., where the company is based, were caught by surprise, too. Across Europe and North Africa, tens of thousands of internet connections in at least 13 countries were going dead.
"Some of the biggest service disruptions affected providers Bigblu Broadband PLC in the U.K. and NordNet AB in France, as well as utility systems that monitor thousands of wind turbines in Germany. The most critical affected Ukraine: Several thousand satellite systems that President Volodymyr Zelenskiy's government depended on were all down, making it much tougher for the military and intelligence services to coordinate troop and drone movements in the hours after the invasion."
"Industry was caught flat-footed," says Gregory Falco, a space cybersecurity expert who has advised the U.S. government. "Ukrainians paid the price. The war is really just revealing the capabilities," says Erin Miller, who runs the Space Information Sharing and Analysis Center, a trade group that gathers data on orbital threats. Cyberattacks affecting the industry, she says, have become a daily occurrence. The Viasat hack was widely considered a harbinger of attacks to come."
For many end-users, the frustrating thing about the Viasat hack is that, unlike with a phishing attack, there was nothing they could have done to prevent it. But the Russians (this smells like GRU) would have to know a lot of detail about Viasat's systems to execute an attack like th
CyberheistNews Vol 13 #10 | March 7th, 2023
[Eye Opener] BusinessWeek: The Satellite Hack Everyone Is Finally Talking About
This week, Bloomberg News pointed at a brand-new article at BusinessWeek, one of their media properties. This is an excellent article that exposes the vulnerabilities when communications systems are not secure by design. It is an excellent wake-up call for your C-level execs and powerful budget ammo.
They started out with: "As Putin began his invasion of Ukraine, a network used throughout Europe-and by the Ukrainian military-faced an unprecedented cyberattack that doubled as an industrywide wake-up call. What they refer to is the Viasat hack. The KnowBe4 blog initially reported on this hack on March 24, 2022 here: https://blog.knowbe4.com/wired-a-mysterious-satellite-hack-has-victims-far-beyond-ukraine and in our CyberheistNews May 17, 2022 here: https://blog.knowbe4.com/cyberheistnews-vol-12-20-heads-up-now-you-need-to-watch-out-for-spoofed-vanity-urls.
The article continues to describe how a large number of Viasat customers lost connectivity. Here is a quote: "Viasat staffers in the U.S., where the company is based, were caught by surprise, too. Across Europe and North Africa, tens of thousands of internet connections in at least 13 countries were going dead.
"Some of the biggest service disruptions affected providers Bigblu Broadband PLC in the U.K. and NordNet AB in France, as well as utility systems that monitor thousands of wind turbines in Germany. The most critical affected Ukraine: Several thousand satellite systems that President Volodymyr Zelenskiy's government depended on were all down, making it much tougher for the military and intelligence services to coordinate troop and drone movements in the hours after the invasion."
"Industry was caught flat-footed," says Gregory Falco, a space cybersecurity expert who has advised the U.S. government. "Ukrainians paid the price. The war is really just revealing the capabilities," says Erin Miller, who runs the Space Information Sharing and Analysis Center, a trade group that gathers data on orbital threats. Cyberattacks affecting the industry, she says, have become a daily occurrence. The Viasat hack was widely considered a harbinger of attacks to come."
For many end-users, the frustrating thing about the Viasat hack is that, unlike with a phishing attack, there was nothing they could have done to prevent it. But the Russians (this smells like GRU) would have to know a lot of detail about Viasat's systems to execute an attack like th |
Guideline | Uber | ★★ | |
| 2022-09-20 13:30:00 | (Déjà vu) CyberheistNews Vol 12 #38 [HEADS UP] New Uber Security Breach \'Looks Bad\', Caused by Social Engineering (lien direct) |

|
Uber Uber | |||
| 2022-09-16 12:36:02 | Uber security breach \'looks bad\', caused by social engineering (lien direct) |
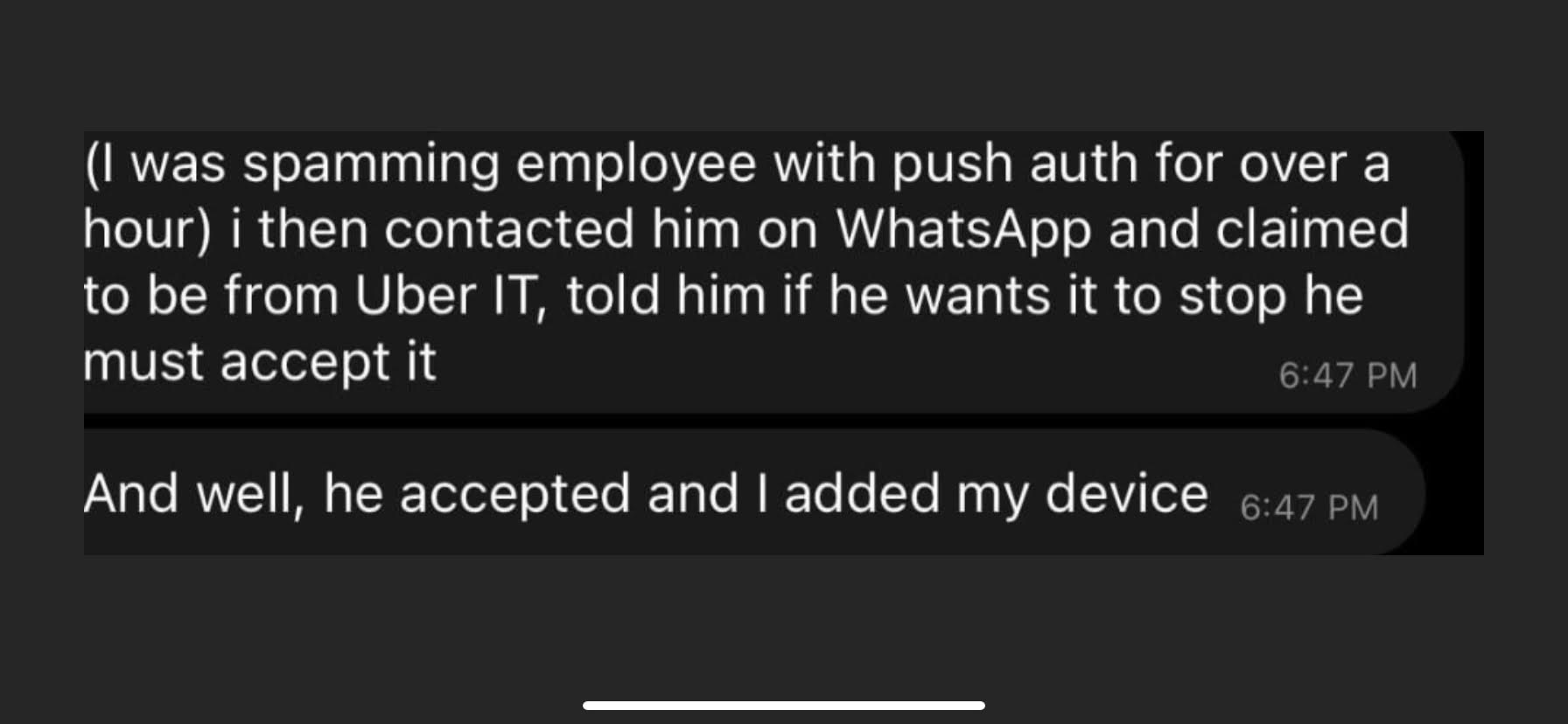
|
Uber |
1
We have: 5 articles.
We have: 5 articles.
To see everything:
Our RSS (filtrered)
