What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-07-28 15:52:00 | L'opération de N. Linée en Corée combine des leurres militaires américains, des sites de commerce électronique coréen N. Korea-linked operation combines US military lures, S. Korean e-commerce sites (lien direct) |
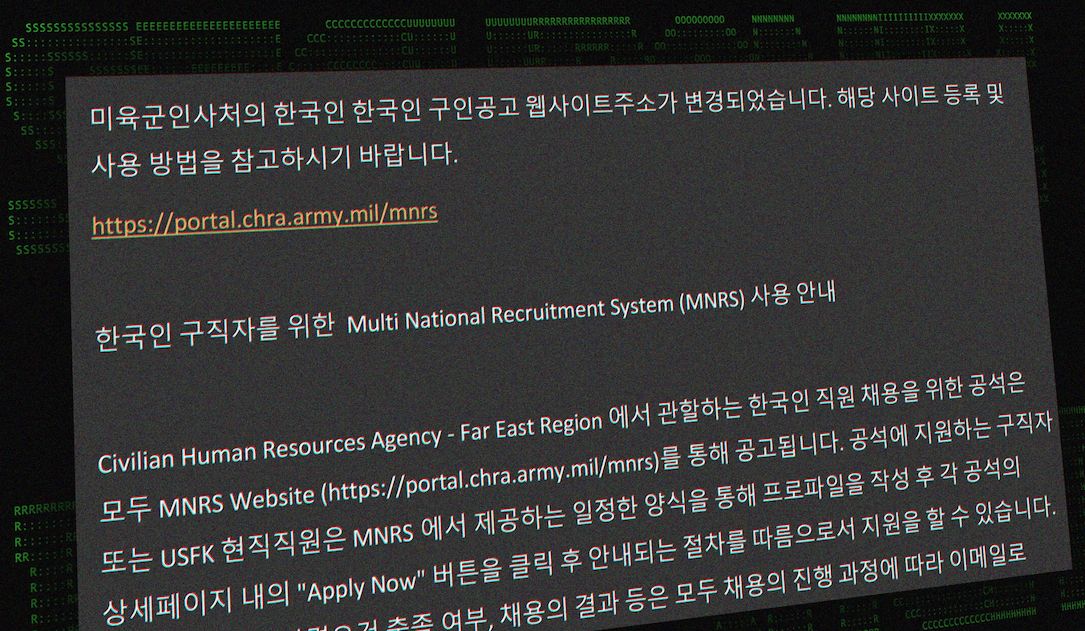 Les pirates auraient été connectés au gouvernement nord-coréen utilisent de faux documents de recrutement d'emploi militaire américain pour attirer les gens dans le téléchargement de logiciels malveillants organisés sur des sites de commerce électronique légitimes - mais compromis - coréens.Oleg Kolesnikov, vice-président de la recherche sur les menaces à Securonix, a déclaré à enregistrer les futures nouvelles que ce qui se démarque le plus dans la campagne est
Les pirates auraient été connectés au gouvernement nord-coréen utilisent de faux documents de recrutement d'emploi militaire américain pour attirer les gens dans le téléchargement de logiciels malveillants organisés sur des sites de commerce électronique légitimes - mais compromis - coréens.Oleg Kolesnikov, vice-président de la recherche sur les menaces à Securonix, a déclaré à enregistrer les futures nouvelles que ce qui se démarque le plus dans la campagne est
 Hackers allegedly connected to the North Korean government are using fake U.S. military job-recruitment documents to lure people into downloading malware staged on legitimate - but compromised - South Korean e-commerce sites. Oleg Kolesnikov, vice president of threat research at Securonix, told Recorded Future News that what stands out the most about the campaign is
Hackers allegedly connected to the North Korean government are using fake U.S. military job-recruitment documents to lure people into downloading malware staged on legitimate - but compromised - South Korean e-commerce sites. Oleg Kolesnikov, vice president of threat research at Securonix, told Recorded Future News that what stands out the most about the campaign is |
Malware Threat | ★★ | ||
| 2023-07-21 12:18:00 | Virustotal s'excuse pour une fuite accidentelle qui a exposé les données des clients VirusTotal apologizes for accidental leak that exposed customer data (lien direct) |
 Vendredi, la plate-forme de balayage de logiciels malveillants de Google a publié des excuses vendredi après que des centaines de personnes travaillant pour des agences de défense et de renseignement aient eu leurs noms et adresses e-mail accidentellement exposée par un employé.Dans un Déclaration publique , Virustotal a déclaré qu'il s'est excusé "pour toute préoccupation ou confusion"
Vendredi, la plate-forme de balayage de logiciels malveillants de Google a publié des excuses vendredi après que des centaines de personnes travaillant pour des agences de défense et de renseignement aient eu leurs noms et adresses e-mail accidentellement exposée par un employé.Dans un Déclaration publique , Virustotal a déclaré qu'il s'est excusé "pour toute préoccupation ou confusion"
 Google\'s malware scanning platform VirusTotal published an apology on Friday after hundreds of individuals working for defense and intelligence agencies globally had their names and email addresses accidentally exposed by an employee. In a public statement, VirusTotal said it apologized “for any concern or confusion” the exposure may have caused and said it took place
Google\'s malware scanning platform VirusTotal published an apology on Friday after hundreds of individuals working for defense and intelligence agencies globally had their names and email addresses accidentally exposed by an employee. In a public statement, VirusTotal said it apologized “for any concern or confusion” the exposure may have caused and said it took place |
Malware | ★★ | ||
| 2023-07-18 12:08:00 | Google expose les noms d'employés de l'intelligence et de la défense dans la fuite de Virustotal Google exposes intelligence and defense employee names in VirusTotal leak (lien direct) |
 Des centaines de personnes travaillant pour des agences de défense et de renseignement dans le monde ont eu leurs noms et adresses e-mail accidentellement exposées par un employé de la plate-forme de balayage de logiciels malveillants de Google Virustotal.Le service en ligne permet aux organisations télécharger des logiciels malveillants présumés à vérifier dans une gamme d'outils anti-virus.Virustotal partage ensuite ces fichiers avec la communauté de sécurité, créant
Des centaines de personnes travaillant pour des agences de défense et de renseignement dans le monde ont eu leurs noms et adresses e-mail accidentellement exposées par un employé de la plate-forme de balayage de logiciels malveillants de Google Virustotal.Le service en ligne permet aux organisations télécharger des logiciels malveillants présumés à vérifier dans une gamme d'outils anti-virus.Virustotal partage ensuite ces fichiers avec la communauté de sécurité, créant
 Hundreds of individuals working for defense and intelligence agencies globally have had their names and email addresses accidentally exposed by an employee at Google\'s malware scanning platform VirusTotal. The online service lets organizations upload suspected malware to be checked against a range of anti-virus tools. VirusTotal then shares these files with the security community, creating
Hundreds of individuals working for defense and intelligence agencies globally have had their names and email addresses accidentally exposed by an employee at Google\'s malware scanning platform VirusTotal. The online service lets organizations upload suspected malware to be checked against a range of anti-virus tools. VirusTotal then shares these files with the security community, creating |
Malware | ★★★★ | ||
| 2023-07-14 16:43:00 | Les pirates ciblent le gouvernement pakistanais, le fournisseur de banques et de télécommunications avec des logiciels malveillants de fabrication en Chine Hackers target Pakistani government, bank and telecom provider with China-made malware (lien direct) |
 Un groupe de pirates inconnu a compromis une application gouvernementale pakistanaise pour infecter les victimes du malware de ShadowPad lié à la Chine, ont révélé des chercheurs.La société de cybersécurité Trend Micro a identifié trois entités au Pakistan ciblées par Shadowpad l'année dernière: une agence gouvernementale anonyme, une banque d'État et un fournisseur de télécommunications.Les chercheurs pensent qu'il peut s'agir d'une attaque de la chaîne d'approvisionnement,
Un groupe de pirates inconnu a compromis une application gouvernementale pakistanaise pour infecter les victimes du malware de ShadowPad lié à la Chine, ont révélé des chercheurs.La société de cybersécurité Trend Micro a identifié trois entités au Pakistan ciblées par Shadowpad l'année dernière: une agence gouvernementale anonyme, une banque d'État et un fournisseur de télécommunications.Les chercheurs pensent qu'il peut s'agir d'une attaque de la chaîne d'approvisionnement,
 An unknown hacker group compromised a Pakistani government app to infect victims with the China-linked Shadowpad malware, researchers have found. Cybersecurity firm Trend Micro identified three entities in Pakistan targeted by Shadowpad last year: an unnamed government agency, a state bank and a telecommunications provider. The researchers believe it may have been a supply-chain attack,
An unknown hacker group compromised a Pakistani government app to infect victims with the China-linked Shadowpad malware, researchers have found. Cybersecurity firm Trend Micro identified three entities in Pakistan targeted by Shadowpad last year: an unnamed government agency, a state bank and a telecommunications provider. The researchers believe it may have been a supply-chain attack, |
Malware Prediction | ★★★ | ||
| 2023-07-06 17:42:00 | Des pirates basés en Iran ciblant les experts en sécurité nucléaire via Mac, Windows Malware Iran-based hackers targeting nuclear security experts through Mac, Windows malware (lien direct) |
 Les pirates soutenant le gouvernement de l'Iran ciblent des experts des affaires du Moyen-Orient et de la sécurité nucléaire dans une nouvelle campagne qui, selon les chercheurs, impliquait des logiciels malveillants pour les produits Apple et Microsoft.Les experts en cybersécurité de Proofpoint ont attribué la campagne à un groupe qu'ils appellent TA453 mais est également connu sous le nom de Charming Kitten, Mint Sandstorm ou APT42,
Les pirates soutenant le gouvernement de l'Iran ciblent des experts des affaires du Moyen-Orient et de la sécurité nucléaire dans une nouvelle campagne qui, selon les chercheurs, impliquait des logiciels malveillants pour les produits Apple et Microsoft.Les experts en cybersécurité de Proofpoint ont attribué la campagne à un groupe qu'ils appellent TA453 mais est également connu sous le nom de Charming Kitten, Mint Sandstorm ou APT42,
 Hackers supporting the government of Iran are targeting experts in Middle Eastern affairs and nuclear security in a new campaign that researchers said involved malware for both Apple and Microsoft products. Cybersecurity experts from Proofpoint attributed the campaign to a group they call TA453 but also is known as Charming Kitten, Mint Sandstorm or APT42,
Hackers supporting the government of Iran are targeting experts in Middle Eastern affairs and nuclear security in a new campaign that researchers said involved malware for both Apple and Microsoft products. Cybersecurity experts from Proofpoint attributed the campaign to a group they call TA453 but also is known as Charming Kitten, Mint Sandstorm or APT42, |
Malware | APT 35 APT 42 | ★★★ | |
| 2023-07-06 17:29:00 | Les cyber-agences avertissent les nouvelles variantes de logiciels malveillants TrueBot qui nous ciblent et les entreprises canadiennes Cyber agencies warn of new TrueBot malware variants targeting US and Canadian firms (lien direct) |
 Les agences de cybersécurité aux États-Unis et au Canada ont averti jeudi que les acteurs de la menace utilisent de nouvelles variantes de logiciels malveillants TrueBot pour voler des données aux victimes.Dans un Advisory co-écrit par l'Agence américaine de sécurité de la cybersécurité et de l'infrastructure (CISA), le FBI, le centre de partage et d'analyse multi-états (MS-ISAC) et le Centre canadien de cybersécurité (CCCS), le
Les agences de cybersécurité aux États-Unis et au Canada ont averti jeudi que les acteurs de la menace utilisent de nouvelles variantes de logiciels malveillants TrueBot pour voler des données aux victimes.Dans un Advisory co-écrit par l'Agence américaine de sécurité de la cybersécurité et de l'infrastructure (CISA), le FBI, le centre de partage et d'analyse multi-états (MS-ISAC) et le Centre canadien de cybersécurité (CCCS), le
 Cybersecurity agencies in the U.S. and Canada warned Thursday that threat actors are using new TrueBot malware variants to steal data from victims. In an advisory co-written by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the FBI, the Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Canadian Centre for Cyber Security (CCCS), the
Cybersecurity agencies in the U.S. and Canada warned Thursday that threat actors are using new TrueBot malware variants to steal data from victims. In an advisory co-written by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the FBI, the Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Canadian Centre for Cyber Security (CCCS), the |
Malware Threat | ★★ | ||
| 2023-06-23 14:35:00 | Des pirates chinois soutenus par l'État ont accidentellement infecté un hôpital européen avec des logiciels malveillants Chinese state-backed hackers accidentally infected a European hospital with malware (lien direct) |
 Un incident de cybersécurité dans un hôpital européen met en évidence la propagation incontrôlée des logiciels malveillants par des pirates liés à l'armée chinoise, ont révélé des chercheurs.Des experts de la société de cybersécurité Check Point ont répondu à un incident plus tôt cette année impliquant un hôpital qui a été affecté par inadvertance par une infection par malware d'auto-propagation introduite au réseau de l'établissement de soins de santé.
Un incident de cybersécurité dans un hôpital européen met en évidence la propagation incontrôlée des logiciels malveillants par des pirates liés à l'armée chinoise, ont révélé des chercheurs.Des experts de la société de cybersécurité Check Point ont répondu à un incident plus tôt cette année impliquant un hôpital qui a été affecté par inadvertance par une infection par malware d'auto-propagation introduite au réseau de l'établissement de soins de santé.
 A cybersecurity incident at a European hospital highlights the uncontrolled spread of malware by hackers connected to the Chinese military, researchers have found. Experts from the cybersecurity company Check Point responded to an incident earlier this year involving a hospital that was inadvertently affected by a self-propagating malware infection introduced to the healthcare institution\'s network.
A cybersecurity incident at a European hospital highlights the uncontrolled spread of malware by hackers connected to the Chinese military, researchers have found. Experts from the cybersecurity company Check Point responded to an incident earlier this year involving a hospital that was inadvertently affected by a self-propagating malware infection introduced to the healthcare institution\'s network. |
Malware | ★★★ | ||
| 2023-06-22 17:24:00 | La NSA met en garde contre \\ 'False Sense of Security \\' contre Blacklotus Malware NSA warns of \\'false sense of security\\' against BlackLotus malware (lien direct) |
 L'Agence de sécurité nationale a déclaré jeudi que les organisations devraient réfléchir à deux fois pour savoir s'ils étaient protégés contre le malware «Bootkit» BlackLotus que les experts en cybersécurité ont mis en garde en mars.BlackLotus est conçu pour esquiver UEFI Secure Boot, qui regarde des logiciels malveillants en tant que machine Microsoft Windows démarre le firmware qui contrôle les fonctions matérielles de base.
L'Agence de sécurité nationale a déclaré jeudi que les organisations devraient réfléchir à deux fois pour savoir s'ils étaient protégés contre le malware «Bootkit» BlackLotus que les experts en cybersécurité ont mis en garde en mars.BlackLotus est conçu pour esquiver UEFI Secure Boot, qui regarde des logiciels malveillants en tant que machine Microsoft Windows démarre le firmware qui contrôle les fonctions matérielles de base.
 The National Security Agency said Thursday that organizations should think twice about whether they\'re protected against the BlackLotus “bootkit” malware that cybersecurity experts first warned about in March. BlackLotus is designed to dodge UEFI Secure Boot, which watches for malicious software as a Microsoft Windows machine starts up the firmware that controls basic hardware functions.
The National Security Agency said Thursday that organizations should think twice about whether they\'re protected against the BlackLotus “bootkit” malware that cybersecurity experts first warned about in March. BlackLotus is designed to dodge UEFI Secure Boot, which watches for malicious software as a Microsoft Windows machine starts up the firmware that controls basic hardware functions. |
Malware | ★★ | ||
| 2023-06-21 21:19:00 | Apple aborde deux jours zéro exploités dans l'opération Campagne de logiciels spy Apple addresses two zero-days exploited in Operation Triangulation spyware campaign (lien direct) |
 Apple a publié patchs pour deux jours zéro exploités dans une campagne spyware que le gouvernement russe a blâmé aux États-Unis. Les États-Unis.La campagne, surnommée Opération Triangulation, a été publiée par la société de cybersécurité basée à Moscou Kaspersky à début juin après que les logiciels malveillants ont été détectés suriPhones au sein de son réseau, ainsi que mercredi à nouvelle recherche
Apple a publié patchs pour deux jours zéro exploités dans une campagne spyware que le gouvernement russe a blâmé aux États-Unis. Les États-Unis.La campagne, surnommée Opération Triangulation, a été publiée par la société de cybersécurité basée à Moscou Kaspersky à début juin après que les logiciels malveillants ont été détectés suriPhones au sein de son réseau, ainsi que mercredi à nouvelle recherche
 Apple has released patches for two zero-days exploited in a spyware campaign that the Russian government has blamed on the U.S. The campaign, dubbed Operation Triangulation, was publicized by the Moscow-based cybersecurity company Kaspersky in early June after the malware was detected on iPhones within its network, as well as on Wednesday in new research
Apple has released patches for two zero-days exploited in a spyware campaign that the Russian government has blamed on the U.S. The campaign, dubbed Operation Triangulation, was publicized by the Moscow-based cybersecurity company Kaspersky in early June after the malware was detected on iPhones within its network, as well as on Wednesday in new research |
Malware | ★★ | ||
| 2023-06-14 17:25:00 | Les pirates créent de faux profils GitHub pour livrer des logiciels malveillants via des référentiels Hackers create fake GitHub profiles to deliver malware through repositories (lien direct) |
 Les pirates ont lancé une campagne élaborée mais probablement infructueuse pour tromper les professionnels de la cybersécurité sur la plate-forme d'hébergement de code Github et les inciter à télécharger des logiciels malveillants, selon la recherche publiée mercredi.Le groupe a créé de faux profils de vrais chercheurs en sécurité pour promouvoir les référentiels de code qui semblent abriter des exploits pour les populations populairesdes produits comme Chrome, Exchange et Discord.
Les pirates ont lancé une campagne élaborée mais probablement infructueuse pour tromper les professionnels de la cybersécurité sur la plate-forme d'hébergement de code Github et les inciter à télécharger des logiciels malveillants, selon la recherche publiée mercredi.Le groupe a créé de faux profils de vrais chercheurs en sécurité pour promouvoir les référentiels de code qui semblent abriter des exploits pour les populations populairesdes produits comme Chrome, Exchange et Discord.
 Hackers launched an elaborate but likely unsuccessful campaign to deceive cybersecurity professionals on the code-hosting platform GitHub and trick them into downloading malware, according to research published on Wednesday. The group created fake profiles of real security researchers to promote code repositories that appear to house exploits for popular products like Chrome, Exchange, and Discord.
Hackers launched an elaborate but likely unsuccessful campaign to deceive cybersecurity professionals on the code-hosting platform GitHub and trick them into downloading malware, according to research published on Wednesday. The group created fake profiles of real security researchers to promote code repositories that appear to house exploits for popular products like Chrome, Exchange, and Discord. |
Malware | ★★★ | ||
| 2023-06-12 20:02:00 | Gozi Malware Hacker condamné à trois ans de prison américaine Gozi malware hacker sentenced to three years in US prison (lien direct) |
 Un pirate roumain qui dirigeait l'infrastructure derrière plusieurs souches de logiciels malveillants a été condamné lundi à trois ans de prison fédérale américaine.Les procureurs ont déclaré que Mihai Ionut Paunescu, 39 ans, avait aidé à gérer le service «Hosting» Powerhost [.] RO, ce qui a aidé les cybercriminels à distribuer le virus Gozi, le Trojan Zeus, le Trojan Spyeye et le malice de malice noircener.Les cybercriminels ont utilisé le malware
Un pirate roumain qui dirigeait l'infrastructure derrière plusieurs souches de logiciels malveillants a été condamné lundi à trois ans de prison fédérale américaine.Les procureurs ont déclaré que Mihai Ionut Paunescu, 39 ans, avait aidé à gérer le service «Hosting» Powerhost [.] RO, ce qui a aidé les cybercriminels à distribuer le virus Gozi, le Trojan Zeus, le Trojan Spyeye et le malice de malice noircener.Les cybercriminels ont utilisé le malware
 A Romanian hacker who ran the infrastructure behind several malware strains was sentenced to three years in U.S. federal prison on Monday. Prosecutors said 39-year-old Mihai Ionut Paunescu helped run “bulletproof hosting” service PowerHost[.]ro, which helped cybercriminals distribute the Gozi Virus, the Zeus Trojan, the SpyEye Trojan, and the BlackEnergy malware. Cybercriminals used the malware
A Romanian hacker who ran the infrastructure behind several malware strains was sentenced to three years in U.S. federal prison on Monday. Prosecutors said 39-year-old Mihai Ionut Paunescu helped run “bulletproof hosting” service PowerHost[.]ro, which helped cybercriminals distribute the Gozi Virus, the Zeus Trojan, the SpyEye Trojan, and the BlackEnergy malware. Cybercriminals used the malware |
Malware | ★★ | ||
| 2023-06-06 21:05:00 | New \\'PowerDrop\\' malware targeting US aerospace industry (lien direct) |
 Un nouveau script PowerShell malveillant vise l'industrie aérospatiale des États-Unis, ont révélé des chercheurs.Le malware, surnommé PowerDrop, a été trouvé implanté sur le réseau d'un entrepreneur de défense sans nom en mai par Adlumin menace Research .Le malware est utilisé comme un cheval de Troie à distance pour exécuter des commandes sur les réseaux de victime après avoir accédé à
Un nouveau script PowerShell malveillant vise l'industrie aérospatiale des États-Unis, ont révélé des chercheurs.Le malware, surnommé PowerDrop, a été trouvé implanté sur le réseau d'un entrepreneur de défense sans nom en mai par Adlumin menace Research .Le malware est utilisé comme un cheval de Troie à distance pour exécuter des commandes sur les réseaux de victime après avoir accédé à
 A new malicious PowerShell script is targeting the United States aerospace industry, researchers have found. The malware, dubbed PowerDrop, was found implanted on the network of an unnamed defense contractor in May by Adlumin Threat Research. The malware is used as a remote access trojan to run commands on victim networks after getting access to
A new malicious PowerShell script is targeting the United States aerospace industry, researchers have found. The malware, dubbed PowerDrop, was found implanted on the network of an unnamed defense contractor in May by Adlumin Threat Research. The malware is used as a remote access trojan to run commands on victim networks after getting access to |
Malware Threat | ★★ | ||
| 2023-06-01 16:18:00 | La Russie nous accuse de pirater des milliers d'appareils Apple à espionner les diplomates Russia accuses US of hacking thousands of Apple devices to spy on diplomats (lien direct) |
 Le Federal Security Service (FSB) de la Russie accuse le renseignement américain de pirater des «milliers de téléphones de pomme» pour espionner les diplomates russes.Selon FSB \\ 's Déclaration Publié jeudi, jeudi, jeudiLes États-Unis ont utilisé des logiciels malveillants précédemment inconnus pour cibler les appareils iOS.La société russe de cybersécurité Kaspersky a également publié un rapport jeudi sur les logiciels malveillants iOS d'une source inconnue.Porte-parole
Le Federal Security Service (FSB) de la Russie accuse le renseignement américain de pirater des «milliers de téléphones de pomme» pour espionner les diplomates russes.Selon FSB \\ 's Déclaration Publié jeudi, jeudi, jeudiLes États-Unis ont utilisé des logiciels malveillants précédemment inconnus pour cibler les appareils iOS.La société russe de cybersécurité Kaspersky a également publié un rapport jeudi sur les logiciels malveillants iOS d'une source inconnue.Porte-parole
 Russia\'s Federal Security Service (FSB) is accusing U.S. intelligence of hacking “thousands of Apple phones” to spy on Russian diplomats. According to FSB\'s statement published on Thursday, the U.S. used previously unknown malware to target iOS devices. Russian cybersecurity company Kaspersky also issued a report Thursday on iOS malware from an unknown source. A spokeswoman
Russia\'s Federal Security Service (FSB) is accusing U.S. intelligence of hacking “thousands of Apple phones” to spy on Russian diplomats. According to FSB\'s statement published on Thursday, the U.S. used previously unknown malware to target iOS devices. Russian cybersecurity company Kaspersky also issued a report Thursday on iOS malware from an unknown source. A spokeswoman |
Malware | ★★★ | ||
| 2023-05-29 17:40:00 | NOUVEAU \\ 'BANDIT SPEEUR \\' Malware Siphons Données des navigateurs, portefeuilles cryptographiques New \\'Bandit Stealer\\' malware siphons data from browsers, crypto wallets (lien direct) |
 Les chercheurs en cybersécurité ont identifié un nouveau malware de vol d'information qui cible les navigateurs et les portefeuilles de crypto-monnaie.Bien que le malware, appelé Bandit Stealer, ait seulement ciblé les systèmes Windows jusqu'à présent, il a le potentiel de s'étendre à d'autres plates-formes telles que Linux.Ce qui rend Bandit Stealer particulièrement dangereux, c'est qu'il est difficile pour les victimes de détecter, les chercheurs à la mode
Les chercheurs en cybersécurité ont identifié un nouveau malware de vol d'information qui cible les navigateurs et les portefeuilles de crypto-monnaie.Bien que le malware, appelé Bandit Stealer, ait seulement ciblé les systèmes Windows jusqu'à présent, il a le potentiel de s'étendre à d'autres plates-formes telles que Linux.Ce qui rend Bandit Stealer particulièrement dangereux, c'est qu'il est difficile pour les victimes de détecter, les chercheurs à la mode
 Cybersecurity researchers identified a new information-stealing malware that targets browsers and cryptocurrency wallets. Although the malware, called Bandit Stealer, has only targeted Windows systems so far, it has the potential to expand to other platforms such as Linux. What makes Bandit Stealer particularly dangerous is that it\'s difficult for victims to detect, researchers at Trend
Cybersecurity researchers identified a new information-stealing malware that targets browsers and cryptocurrency wallets. Although the malware, called Bandit Stealer, has only targeted Windows systems so far, it has the potential to expand to other platforms such as Linux. What makes Bandit Stealer particularly dangerous is that it\'s difficult for victims to detect, researchers at Trend |
Malware Prediction | ★★ | ||
| 2023-05-25 17:59:00 | Les logiciels malveillants liés à la nouvelle Russie peuvent nuire physiquement à des réseaux électriques, rapporte mandiant New Russia-linked malware can physically harm power grids, Mandiant reports (lien direct) |
 En décembre 2021, un utilisateur avec une adresse IP russe téléchargée de logiciels malveillants mystérieux sur le service de numérisation du virus de Google \\.Selon un Analyse Publié jeudi par des chercheurs de sécurité mandiant, ce logiciel malveillant est conçuPour perturber et endommager les systèmes d'infrastructures critiques, y compris les réseaux électriques.Le malware, étiqueté Cosmicenergy par Mandiant, est similaire à Industryer , utilisé
En décembre 2021, un utilisateur avec une adresse IP russe téléchargée de logiciels malveillants mystérieux sur le service de numérisation du virus de Google \\.Selon un Analyse Publié jeudi par des chercheurs de sécurité mandiant, ce logiciel malveillant est conçuPour perturber et endommager les systèmes d'infrastructures critiques, y compris les réseaux électriques.Le malware, étiqueté Cosmicenergy par Mandiant, est similaire à Industryer , utilisé
 In December 2021, a user with a Russian IP address uploaded mysterious malware to Google\'s virus scanning service VirusTotal. According to an analysis published Thursday by Mandiant security researchers, this malicious software is designed to disrupt and damage critical infrastructure systems, including power grids. The malware, labeled CosmicEnergy by Mandiant, is similar to Industroyer, used
In December 2021, a user with a Russian IP address uploaded mysterious malware to Google\'s virus scanning service VirusTotal. According to an analysis published Thursday by Mandiant security researchers, this malicious software is designed to disrupt and damage critical infrastructure systems, including power grids. The malware, labeled CosmicEnergy by Mandiant, is similar to Industroyer, used |
Malware | CosmicEnergy | ★★ | |
| 2023-05-16 18:19:00 | \\ 'lancefly \\' groupe d'espionnage des organisations ciblant les organisations en Asie avec des logiciels malveillants personnalisés \\'Lancefly\\' espionage group targeting organizations across Asia with custom malware (lien direct) |
 Un groupe de piratage soutenu par le gouvernement connu sous le nom de «Lancefly» a été vu en utilisant des logiciels malveillants sur mesure pour attaquer les gouvernements, les télécommunications et d'autres organisations à travers l'Asie.Des chercheurs de Symantec ont déclaré que Lancefly, étiquetée comme une menace persistante avancée (APT), était auparavant impliquée dans plusieurs attaques de 2020 qui ont utilisé des leurres de phishing basés sur le 37e asean Summit.La dernière campagne -
Un groupe de piratage soutenu par le gouvernement connu sous le nom de «Lancefly» a été vu en utilisant des logiciels malveillants sur mesure pour attaquer les gouvernements, les télécommunications et d'autres organisations à travers l'Asie.Des chercheurs de Symantec ont déclaré que Lancefly, étiquetée comme une menace persistante avancée (APT), était auparavant impliquée dans plusieurs attaques de 2020 qui ont utilisé des leurres de phishing basés sur le 37e asean Summit.La dernière campagne -
 A government-backed hacking group known as “Lancefly” has been seen using custom-made malware to attack governments, telecoms and other organizations across Asia. Researchers from Symantec said Lancefly, labeled as an advanced persistent threat (APT), was previously implicated in several 2020 attacks that used phishing lures based on the 37th ASEAN Summit. The latest campaign -
A government-backed hacking group known as “Lancefly” has been seen using custom-made malware to attack governments, telecoms and other organizations across Asia. Researchers from Symantec said Lancefly, labeled as an advanced persistent threat (APT), was previously implicated in several 2020 attacks that used phishing lures based on the 37th ASEAN Summit. The latest campaign - |
Malware Threat | ★★ | ||
| 2023-05-09 15:01:00 | Kremlin Linked \\ 'Snake \\' Espionage malware éliminé, dit le ministère de la Justice Kremlin-linked \\'Snake\\' espionage malware eliminated, Justice Department says (lien direct) |
 Les États-Unis et les organismes internationaux d'application de la loi ont annoncé mardi qu'ils avaient réussi à démonter un implant de logiciels malveillants utilisé par un groupe de piratage notoire soutenu par le Kremlin.Le ministère de la Justice a déclaré qu'il avait obtenu l'autorisation du tribunal lundi qui a permis aux forces de l'ordre américaines d'effacer le code malveillant, surnommé «Snake», utilisé par [Turla] (http://therecord.media/tag/turla), qui a longtemps étéaffilié à
Les États-Unis et les organismes internationaux d'application de la loi ont annoncé mardi qu'ils avaient réussi à démonter un implant de logiciels malveillants utilisé par un groupe de piratage notoire soutenu par le Kremlin.Le ministère de la Justice a déclaré qu'il avait obtenu l'autorisation du tribunal lundi qui a permis aux forces de l'ordre américaines d'effacer le code malveillant, surnommé «Snake», utilisé par [Turla] (http://therecord.media/tag/turla), qui a longtemps étéaffilié à
 The U.S. and international law enforcement agencies announced Tuesday they had successfully dismantled a malware implant utilized by a notorious Kremlin-backed hacking group. The Justice Department said it obtained court authorization on Monday that allowed U.S. law enforcement to wipe out the malicious code, dubbed “Snake,” used by [Turla](http://therecord.media/tag/turla), which has long been affiliated with
The U.S. and international law enforcement agencies announced Tuesday they had successfully dismantled a malware implant utilized by a notorious Kremlin-backed hacking group. The Justice Department said it obtained court authorization on Monday that allowed U.S. law enforcement to wipe out the malicious code, dubbed “Snake,” used by [Turla](http://therecord.media/tag/turla), which has long been affiliated with |
Malware | ★★ | ||
| 2023-05-03 19:32:00 | Les utilisateurs de MacBook se méfient: les logiciels malveillants du voleur atomique obtiennent de nouvelles capacités MacBook users beware: Atomic Stealer malware gets new capabilities (lien direct) |
 Les cybercriminels déploient de plus en plus les logiciels malveillants de voleur d'informations pour cibler les ordinateurs Apple, selon des chercheurs en cybersécurité.L'un de ces infostelleurs macos, atomic Stealer, a attiré l'attention de la société de cybersécurité Sentinelone, qui a rapporté mercredi qu'il [repérait une nouvelle version] (https://www.sentinelone.com/blog/atomic-telleer-thereat-actor-Spawns-Second-Variant-of-Macos-Malware-Sold-on-Telegram /) du malware.La dernière version, qui n'a pas été décrite auparavant, est plus ciblée dans les données qu'elle
Les cybercriminels déploient de plus en plus les logiciels malveillants de voleur d'informations pour cibler les ordinateurs Apple, selon des chercheurs en cybersécurité.L'un de ces infostelleurs macos, atomic Stealer, a attiré l'attention de la société de cybersécurité Sentinelone, qui a rapporté mercredi qu'il [repérait une nouvelle version] (https://www.sentinelone.com/blog/atomic-telleer-thereat-actor-Spawns-Second-Variant-of-Macos-Malware-Sold-on-Telegram /) du malware.La dernière version, qui n'a pas été décrite auparavant, est plus ciblée dans les données qu'elle
 Cybercriminals are increasingly deploying information-stealing malware to target Apple computers, cybersecurity researchers say. One of these macOS infostealers, Atomic Stealer, has caught the attention of cybersecurity company SentinelOne, which reported Wednesday that it [spotted a new version](https://www.sentinelone.com/blog/atomic-stealer-threat-actor-spawns-second-variant-of-macos-malware-sold-on-telegram/) of the malware. The latest version, which hasn\'t been described before, is more targeted in the data it
Cybercriminals are increasingly deploying information-stealing malware to target Apple computers, cybersecurity researchers say. One of these macOS infostealers, Atomic Stealer, has caught the attention of cybersecurity company SentinelOne, which reported Wednesday that it [spotted a new version](https://www.sentinelone.com/blog/atomic-stealer-threat-actor-spawns-second-variant-of-macos-malware-sold-on-telegram/) of the malware. The latest version, which hasn\'t been described before, is more targeted in the data it |
Malware | ★★★ | ||
| 2023-04-30 16:51:00 | Iran apt utilisant \\ 'Bellaciao \\' malware contre les cibles aux États-Unis, en Europe et en Asie Iran APT using \\'BellaCiao\\' malware against targets in US, Europe and Asia (lien direct) |
 Un groupe de piratage parrainé par l'État iranien a été accusé d'avoir déployé une nouvelle souche de logiciels malveillants nommé Bellaciao contre plusieurs victimes aux États-Unis, en Europe, en Inde, en Turquie et dans d'autres pays.Des chercheurs de la société de cybersécurité Bitdefender [attribuée] (https://www.bitdefender.com/blog/businessinsights/unpacking-bellaciaooo-a-closer-look-at-irans-latest-malware/) le maline à APT35 / APT42 & #8211;également connu sous le nom de Mint Sandstorm ou Charming Kitten & # 8211;un groupe de menaces persistantes avancé qui
Un groupe de piratage parrainé par l'État iranien a été accusé d'avoir déployé une nouvelle souche de logiciels malveillants nommé Bellaciao contre plusieurs victimes aux États-Unis, en Europe, en Inde, en Turquie et dans d'autres pays.Des chercheurs de la société de cybersécurité Bitdefender [attribuée] (https://www.bitdefender.com/blog/businessinsights/unpacking-bellaciaooo-a-closer-look-at-irans-latest-malware/) le maline à APT35 / APT42 & #8211;également connu sous le nom de Mint Sandstorm ou Charming Kitten & # 8211;un groupe de menaces persistantes avancé qui
 An Iranian state-sponsored hacking group has been accused of deploying a new strain of malware named BellaCiao against several victims in the U.S., Europe, India, Turkey and other countries. Researchers from cybersecurity firm Bitdefender [attributed](https://www.bitdefender.com/blog/businessinsights/unpacking-bellaciao-a-closer-look-at-irans-latest-malware/) the malware to APT35/APT42 – also known as Mint Sandstorm or Charming Kitten – an advanced persistent threat group that
An Iranian state-sponsored hacking group has been accused of deploying a new strain of malware named BellaCiao against several victims in the U.S., Europe, India, Turkey and other countries. Researchers from cybersecurity firm Bitdefender [attributed](https://www.bitdefender.com/blog/businessinsights/unpacking-bellaciao-a-closer-look-at-irans-latest-malware/) the malware to APT35/APT42 – also known as Mint Sandstorm or Charming Kitten – an advanced persistent threat group that |
Malware Threat | APT 35 APT 42 | ★★★ | |
| 2023-04-26 19:51:00 | Les pirates de langue chinois ont compromis l'application Tencent pour espionner l'organisme à but non lucratif, dit le rapport Chinese-speaking hackers compromised Tencent app to spy on nonprofit, report says (lien direct) |
 Un groupe de piratage soutenu par le gouvernement chinois présumé a ciblé une organisation à but non lucratif en Chine avec des logiciels malveillants personnalisés conçus pour espionner ses victimes et collecter des données auprès de leurs appareils, selon New Cybersecurity Research.Dans son [rapport] (https://www.welivesecurity.com/2023/04/26/evasive-panda-apt-group-malware-updates-popular-chinese-software/), la société de cybersécurité eset n'a pas révélé le nomde l'organisation.Le chercheur qui a enquêté sur l'incident, Facundo Mu & Ntilde; Oz, a déclaré
Un groupe de piratage soutenu par le gouvernement chinois présumé a ciblé une organisation à but non lucratif en Chine avec des logiciels malveillants personnalisés conçus pour espionner ses victimes et collecter des données auprès de leurs appareils, selon New Cybersecurity Research.Dans son [rapport] (https://www.welivesecurity.com/2023/04/26/evasive-panda-apt-group-malware-updates-popular-chinese-software/), la société de cybersécurité eset n'a pas révélé le nomde l'organisation.Le chercheur qui a enquêté sur l'incident, Facundo Mu & Ntilde; Oz, a déclaré
 An alleged Chinese government-backed hacking group targeted a nonprofit organization in China with custom malware designed to spy on its victims and collect data from their devices, according to new cybersecurity research. In its [report](https://www.welivesecurity.com/2023/04/26/evasive-panda-apt-group-malware-updates-popular-chinese-software/), cybersecurity company ESET did not reveal the name of the organization. The researcher who investigated the incident, Facundo Muñoz, told
An alleged Chinese government-backed hacking group targeted a nonprofit organization in China with custom malware designed to spy on its victims and collect data from their devices, according to new cybersecurity research. In its [report](https://www.welivesecurity.com/2023/04/26/evasive-panda-apt-group-malware-updates-popular-chinese-software/), cybersecurity company ESET did not reveal the name of the organization. The researcher who investigated the incident, Facundo Muñoz, told |
Malware | ★★★ | ||
| 2023-04-24 19:40:00 | Le bureau du shérif du comté de San Bernardino \\ a du mal à se remettre de l'incident \\ 'malware \\' San Bernardino County sheriff\\'s office struggling to recover from \\'malware\\' incident (lien direct) |
 Le département du shérif du comté de San Bernardino est en train de se remettre d'une cyberattaque impliquant des logiciels malveillants des semaines après son début.Le responsable de l'information du département, Mara Rodriguez, a déclaré à Future News que le département du sud de la Californie avait identifié pour la première fois une perturbation du réseau le 7 avril et a confirmé plus tard qu'elle impliquait des logiciels malveillants.Rodriguez ne dirait pas
Le département du shérif du comté de San Bernardino est en train de se remettre d'une cyberattaque impliquant des logiciels malveillants des semaines après son début.Le responsable de l'information du département, Mara Rodriguez, a déclaré à Future News que le département du sud de la Californie avait identifié pour la première fois une perturbation du réseau le 7 avril et a confirmé plus tard qu'elle impliquait des logiciels malveillants.Rodriguez ne dirait pas
 The San Bernardino County Sheriff\'s Department is in the process of recovering from a cyberattack involving malware weeks after it began. Department public information officer Mara Rodriguez told Recorded Future News that the Southern California department first identified a network disruption on April 7 and later confirmed that it involved malware. Rodriguez would not say
The San Bernardino County Sheriff\'s Department is in the process of recovering from a cyberattack involving malware weeks after it began. Department public information officer Mara Rodriguez told Recorded Future News that the Southern California department first identified a network disruption on April 7 and later confirmed that it involved malware. Rodriguez would not say |
Malware | ★★ | ||
| 2023-04-13 18:16:00 | Crafty PDF Link fait partie d'une autre campagne de logiciels malveillants de saison fiscale Crafty PDF link is part of another tax-season malware campaign (lien direct) |
 Les cabinets comptables semblent être la principale cible d'une campagne de logiciels malveillants qui mélange des mouvements familiers avec un exploit moins commun impliquant un raccourci de fichiers manipulé, ont déclaré jeudi des chercheurs en cybersécurité.Au moins deux clients de la société de cybersécurité Sophos [ont rapporté les attaques] (https://news.sophos.com/en-us/2023/04/13/tax-firts-targeted-by-precision-malware-attacks/) plus tôtCette année alors que l'industrie de la comptabilité américaine s'accélère pour la taxe
Les cabinets comptables semblent être la principale cible d'une campagne de logiciels malveillants qui mélange des mouvements familiers avec un exploit moins commun impliquant un raccourci de fichiers manipulé, ont déclaré jeudi des chercheurs en cybersécurité.Au moins deux clients de la société de cybersécurité Sophos [ont rapporté les attaques] (https://news.sophos.com/en-us/2023/04/13/tax-firts-targeted-by-precision-malware-attacks/) plus tôtCette année alors que l'industrie de la comptabilité américaine s'accélère pour la taxe
 Accounting firms appear to be the prime target of a malware campaign that mixes some familiar moves with a less common exploit involving a manipulated file shortcut, cybersecurity researchers said Thursday. At least two customers of cybersecurity company Sophos [reported the attacks](https://news.sophos.com/en-us/2023/04/13/tax-firms-targeted-by-precision-malware-attacks/) earlier this year as the U.S. accounting industry was ramping up for tax
Accounting firms appear to be the prime target of a malware campaign that mixes some familiar moves with a less common exploit involving a manipulated file shortcut, cybersecurity researchers said Thursday. At least two customers of cybersecurity company Sophos [reported the attacks](https://news.sophos.com/en-us/2023/04/13/tax-firms-targeted-by-precision-malware-attacks/) earlier this year as the U.S. accounting industry was ramping up for tax |
Malware | ★★ | ||
| 2023-04-11 17:28:00 | Des pirates nord-coréens liés à une attaque de chaîne d'approvisionnement 3CX, recherche d'enquête North Korean hackers linked to 3CX supply-chain attack, investigation finds (lien direct) |
 La société de téléphone d'entreprise 3CX a déclaré mardi qu'une récente attaque de chaîne d'approvisionnement contre son réseau - qui était utilisée par des pirates pour tenter d'installer des logiciels malveillants sur les clients \\ '- a été très probablement mené par un groupe connecté à la Corée du Nord.Le directeur de la Société de la sécurité de l'information de la société, Pierre Jourdan, a partagé [l'évaluation intérimaire] (https://www.3cx.com/blog/news/mandiant-initial-results/) de la
La société de téléphone d'entreprise 3CX a déclaré mardi qu'une récente attaque de chaîne d'approvisionnement contre son réseau - qui était utilisée par des pirates pour tenter d'installer des logiciels malveillants sur les clients \\ '- a été très probablement mené par un groupe connecté à la Corée du Nord.Le directeur de la Société de la sécurité de l'information de la société, Pierre Jourdan, a partagé [l'évaluation intérimaire] (https://www.3cx.com/blog/news/mandiant-initial-results/) de la
 Enterprise phone company 3CX said on Tuesday that a recent supply-chain attack on its network - which was used by hackers to attempt to install malware on clients\' desktops - was very likely conducted by a group connected to North Korea. The company\'s chief information security officer, Pierre Jourdan, shared the [interim assessment](https://www.3cx.com/blog/news/mandiant-initial-results/) of the
Enterprise phone company 3CX said on Tuesday that a recent supply-chain attack on its network - which was used by hackers to attempt to install malware on clients\' desktops - was very likely conducted by a group connected to North Korea. The company\'s chief information security officer, Pierre Jourdan, shared the [interim assessment](https://www.3cx.com/blog/news/mandiant-initial-results/) of the |
Malware | ★★ | ||
| 2023-04-02 17:37:00 | \\ 'Octopus tactique \\' Hackers Utilisation d'escroqueries de phishing liées à l'impôt pour répandre les logiciels malveillants \\'Tactical Octopus\\' hackers using tax-related phishing scams to spread malware (lien direct) |
 Les chercheurs mettent en garde contre un groupe de pirates qui utilisent des leurres d'e-mail liés à l'impôt pour diffuser des logiciels malveillants dangereux.Les experts en cybersécurité de Securonix ont déclaré qu'ils suivaient le groupe connu sous le nom de Tactical # Octopus depuis des mois avant la date limite fiscale du 18 avril, constatant qu'ils utilisent des documents fiscaux W-2 pour les employés apparemment valides, I-9
Les chercheurs mettent en garde contre un groupe de pirates qui utilisent des leurres d'e-mail liés à l'impôt pour diffuser des logiciels malveillants dangereux.Les experts en cybersécurité de Securonix ont déclaré qu'ils suivaient le groupe connu sous le nom de Tactical # Octopus depuis des mois avant la date limite fiscale du 18 avril, constatant qu'ils utilisent des documents fiscaux W-2 pour les employés apparemment valides, I-9
 Researchers are warning about a group of hackers that are using tax-related email lures to spread dangerous malware. Cybersecurity experts at Securonix said they have been tracking the group known as TACTICAL#OCTOPUS for months in advance of the April 18 U.S. tax deadline, finding that they are using seemingly valid employee W-2 tax documents, I-9
Researchers are warning about a group of hackers that are using tax-related email lures to spread dangerous malware. Cybersecurity experts at Securonix said they have been tracking the group known as TACTICAL#OCTOPUS for months in advance of the April 18 U.S. tax deadline, finding that they are using seemingly valid employee W-2 tax documents, I-9 |
Malware | ★★ | ||
| 2023-03-31 12:16:00 | Plus de preuves relie l'attaque de la chaîne d'approvisionnement 3CX au groupe de piratage nord-coréen [More evidence links 3CX supply-chain attack to North Korean hacking group] (lien direct) |
 L'attaque de la chaîne d'approvisionnement contre la société de téléphone d'entreprise 3CX a utilisé le code de piratage qui «correspond exactement» au malware maltraité précédemment dans les attaques par un groupe nord-coréen notoire, selon une nouvelle analyse.L'établissement de l'étendue des dommages causés par le pirat
L'attaque de la chaîne d'approvisionnement contre la société de téléphone d'entreprise 3CX a utilisé le code de piratage qui «correspond exactement» au malware maltraité précédemment dans les attaques par un groupe nord-coréen notoire, selon une nouvelle analyse.L'établissement de l'étendue des dommages causés par le pirat
 The supply-chain attack on the enterprise phone company 3CX used hacking code that “exactly matches” malware previously seen in attacks by a notorious North Korean group, according to new analysis. Establishing the extent of the damage caused by the hack has been a priority for researchers after a number of cybersecurity businesses went public with
The supply-chain attack on the enterprise phone company 3CX used hacking code that “exactly matches” malware previously seen in attacks by a notorious North Korean group, according to new analysis. Establishing the extent of the damage caused by the hack has been a priority for researchers after a number of cybersecurity businesses went public with |
Malware Hack | APT 38 | ★★ | |
| 2023-03-16 20:56:00 | Kaspersky releases decryptor for ransomware based on Conti source code (lien direct) |
 Cybersecurity firm Kaspersky on Thursday released a decryptor that could help victims who had their data locked down by a version of the Conti ransomware. Kaspersky said the tool can be used on a malware strain that infected dozens of “companies and state institutions” throughout December 2022. Kaspersky did not name the strain, but experts
Cybersecurity firm Kaspersky on Thursday released a decryptor that could help victims who had their data locked down by a version of the Conti ransomware. Kaspersky said the tool can be used on a malware strain that infected dozens of “companies and state institutions” throughout December 2022. Kaspersky did not name the strain, but experts |
Ransomware Malware Tool | ★★ | ||
| 2023-03-14 14:11:00 | Hackers target South Asian government entities with KamiKakaBot malware (lien direct) |
 Suspected government-backed hackers are attacking military and government organizations in South Asia with malware called KamiKakaBot that is designed to steal sensitive information. Researchers from Amsterdam-based cybersecurity firm EclecticIQ [attributed](https://blog.eclecticiq.com/dark-pink-apt-group-strikes-government-entities-in-south-asian-countries#A1) the attacks to the advanced persistent threat (APT) group Dark Pink. The group's previous victims include military, government, religious and non-profit organizations in Cambodia, Indonesia,
Suspected government-backed hackers are attacking military and government organizations in South Asia with malware called KamiKakaBot that is designed to steal sensitive information. Researchers from Amsterdam-based cybersecurity firm EclecticIQ [attributed](https://blog.eclecticiq.com/dark-pink-apt-group-strikes-government-entities-in-south-asian-countries#A1) the attacks to the advanced persistent threat (APT) group Dark Pink. The group's previous victims include military, government, religious and non-profit organizations in Cambodia, Indonesia, |
Malware Threat | ★★ | ||
| 2023-03-06 14:01:00 | Ransomware gang posts breast cancer patients\' clinical photographs (lien direct) |
 The ALPHV ransomware group, also known as BlackCat, is attempting to extort a healthcare network in Pennsylvania by publishing photographs of breast cancer patients.
These clinical images, used by Lehigh Valley Health Network as part of radiotherapy to tackle malignant cells, were described as “nude photos” on the criminals' site.
Lehigh Valley Health Network disclosed on February 20 that it had been attacked by the BlackCat gang, which it described as linked to Russia, and stated that it would not pay a ransom.
“Based on our initial analysis, the attack was on the network supporting one physician practice located in Lackawanna County. We take this very seriously and protecting the data security and privacy of our patients, physicians and staff is critical,” said the network's president and chief executive, Brian Nester.
Nester added that the incident involved “a computer system used for clinically appropriate patient images for radiation oncology treatment and other sensitive information.”
At the time of the original statement, Nester said Lehigh Valley Health Network's services - including a cancer institute and a children's hospital - were not affected.
However the network's website is currently inaccessible. The Record was unable to contact the network for further comment following its listing on the ALPHV [.onion](https://en.wikipedia.org/wiki/Tor_(network)) website.
Onlookers have been revolted by the attempt to leverage the sensitivities around cancer treatment and intimate images to extort the organization.
Max Smeets, an academic at ETH Zurich - a public research university - and the director of the European Cyber Conflict Research Initiative, [wrote](https://twitter.com/Maxwsmeets/status/1632654116320075776): “This makes me so angry. I hope these barbarians will be held accountable for their heinous actions.”
"A new low. This is sickening," [wrote](https://twitter.com/rj_chap/status/1632465294580133888) malware analyst Ryan Chapman, while Nicholas Carroll, a cybersecurity professional, [said](https://twitter.com/sloppy_bear/status/1632468646873165824) the gang was “trying to set new standards in despicable.”
ALPHV itself celebrated the attack and the attention it brought.
“Our blog is followed by a lot of world media, the case will be widely publicized and will cause significant damage to your business. Your time is running out. We are ready to unleash our full power on you!”
Numerous healthcare organizations have been attacked by ransomware gangs in recent months. The criminal industry persists because of victims who pay, sometimes because their businesses face an existential threat, and sometimes to avoid the negative publicity.
Medibank, one of Australia's largest health insurance providers, stated last November that it would not be making a [ransom payment](https://therecord.media/medibank-says-it-will-not-pay-ransom-in-hack-that-impacted-9-7-million-customers/) after hackers gained access to the data of 9.7 million current and former customers, including 1.8 million international customers living abroad.
The information included sensitive healthcare claims data for around 480,000 individuals, including information about drug addiction treatments and abortions. Outrage at the attack prompted the government to [consider banning](https://therecord.media/australia-to-consider-banning-ransomware-payments/) ransomware payments in a bid to undermine the industry.
Back in January, the hospital technology giant [NextGen Healthcare](https://therecord.media/electronic-health-record-giant-nextgen-dealing-with-cyberattack/) said it was responding to a cyberattack after ALPHV added the company to its list of victims.
The ALPHV ransomware group, also known as BlackCat, is attempting to extort a healthcare network in Pennsylvania by publishing photographs of breast cancer patients.
These clinical images, used by Lehigh Valley Health Network as part of radiotherapy to tackle malignant cells, were described as “nude photos” on the criminals' site.
Lehigh Valley Health Network disclosed on February 20 that it had been attacked by the BlackCat gang, which it described as linked to Russia, and stated that it would not pay a ransom.
“Based on our initial analysis, the attack was on the network supporting one physician practice located in Lackawanna County. We take this very seriously and protecting the data security and privacy of our patients, physicians and staff is critical,” said the network's president and chief executive, Brian Nester.
Nester added that the incident involved “a computer system used for clinically appropriate patient images for radiation oncology treatment and other sensitive information.”
At the time of the original statement, Nester said Lehigh Valley Health Network's services - including a cancer institute and a children's hospital - were not affected.
However the network's website is currently inaccessible. The Record was unable to contact the network for further comment following its listing on the ALPHV [.onion](https://en.wikipedia.org/wiki/Tor_(network)) website.
Onlookers have been revolted by the attempt to leverage the sensitivities around cancer treatment and intimate images to extort the organization.
Max Smeets, an academic at ETH Zurich - a public research university - and the director of the European Cyber Conflict Research Initiative, [wrote](https://twitter.com/Maxwsmeets/status/1632654116320075776): “This makes me so angry. I hope these barbarians will be held accountable for their heinous actions.”
"A new low. This is sickening," [wrote](https://twitter.com/rj_chap/status/1632465294580133888) malware analyst Ryan Chapman, while Nicholas Carroll, a cybersecurity professional, [said](https://twitter.com/sloppy_bear/status/1632468646873165824) the gang was “trying to set new standards in despicable.”
ALPHV itself celebrated the attack and the attention it brought.
“Our blog is followed by a lot of world media, the case will be widely publicized and will cause significant damage to your business. Your time is running out. We are ready to unleash our full power on you!”
Numerous healthcare organizations have been attacked by ransomware gangs in recent months. The criminal industry persists because of victims who pay, sometimes because their businesses face an existential threat, and sometimes to avoid the negative publicity.
Medibank, one of Australia's largest health insurance providers, stated last November that it would not be making a [ransom payment](https://therecord.media/medibank-says-it-will-not-pay-ransom-in-hack-that-impacted-9-7-million-customers/) after hackers gained access to the data of 9.7 million current and former customers, including 1.8 million international customers living abroad.
The information included sensitive healthcare claims data for around 480,000 individuals, including information about drug addiction treatments and abortions. Outrage at the attack prompted the government to [consider banning](https://therecord.media/australia-to-consider-banning-ransomware-payments/) ransomware payments in a bid to undermine the industry.
Back in January, the hospital technology giant [NextGen Healthcare](https://therecord.media/electronic-health-record-giant-nextgen-dealing-with-cyberattack/) said it was responding to a cyberattack after ALPHV added the company to its list of victims. |
Ransomware Malware | ★★★ | ||
| 2023-03-01 00:34:26 | Victims of MortalKombat ransomware can now decrypt their locked files for free (lien direct) |  Cybersecurity firm Bitdefender released a universal decryptor for the MortalKombat ransomware – a strain first observed by threat researchers in January 2023. The malware has been used on dozens of victims across the U.S., United Kingdom, Turkey and the Philippines, according to a recent report from Cisco. Bogdan Botezatu, director of threat research and reporting [… Cybersecurity firm Bitdefender released a universal decryptor for the MortalKombat ransomware – a strain first observed by threat researchers in January 2023. The malware has been used on dozens of victims across the U.S., United Kingdom, Turkey and the Philippines, according to a recent report from Cisco. Bogdan Botezatu, director of threat research and reporting [… |
Ransomware Malware Threat | ★★ | ||
| 2023-02-23 21:57:12 | Russian accused of developing password-cracking tool extradited to US (lien direct) |  A 28-year-old Russian malware developer was extradited to the U.S. where he could face up to 47 years in federal prison for allegedly creating and selling a malicious password-cracking tool. Dariy Pankov, also known as “dpxaker,” developed what the Department of Justice called “powerful” password-cracking program that he marketed and sold to other cybercriminals for a [… A 28-year-old Russian malware developer was extradited to the U.S. where he could face up to 47 years in federal prison for allegedly creating and selling a malicious password-cracking tool. Dariy Pankov, also known as “dpxaker,” developed what the Department of Justice called “powerful” password-cracking program that he marketed and sold to other cybercriminals for a [… |
Malware Tool | ★★ | ||
| 2023-02-23 19:02:13 | Hackers use ChatGPT phishing websites to infect users with malware (lien direct) |  Cyble says cybercriminals are setting up phishing websites that mimic the branding of ChatGPT, an AI tool that has exploded in popularity Cyble says cybercriminals are setting up phishing websites that mimic the branding of ChatGPT, an AI tool that has exploded in popularity |
Malware Tool | ChatGPT | ★★★ | |
| 2023-02-22 21:25:30 | House Democrats want briefing on domestic terrorism at energy facilities, including malware (lien direct) |  Democrats in the House asked CISA and DHS for a briefing about domestic terrorists, including cyberattacks against energy infrastructure Democrats in the House asked CISA and DHS for a briefing about domestic terrorists, including cyberattacks against energy infrastructure |
Malware | ★★ | ||
| 2023-02-16 21:54:11 | Hackers target Chinese language speakers with FatalRAT malware (lien direct) |  Chinese-speaking users are being targeted with FatalRAT malware, spread via fake websites of popular apps, new research has found. First discovered in August 2021, FatalRat malware can capture keystrokes, change a victim's screen resolution, download and execute files, and steal or delete data stored in browsers. So far, the researchers from cybersecurity company ESET have [… Chinese-speaking users are being targeted with FatalRAT malware, spread via fake websites of popular apps, new research has found. First discovered in August 2021, FatalRat malware can capture keystrokes, change a victim's screen resolution, download and execute files, and steal or delete data stored in browsers. So far, the researchers from cybersecurity company ESET have [… |
Malware | ★★★ | ||
| 2023-02-16 20:35:07 | Espionage malware targeted telecoms in Middle East using Microsoft, Google, Dropbox tools (lien direct) |  An espionage campaign targeting telecommunications providers across the Middle East hid its activities through a range of popular tools from Microsoft, Google and Dropbox, according to a report released Thursday. Researchers at cybersecurity company SentinelOne named the campaign “WIP26” - work in progress - because they were unable to attribute it to any actor or [… An espionage campaign targeting telecommunications providers across the Middle East hid its activities through a range of popular tools from Microsoft, Google and Dropbox, according to a report released Thursday. Researchers at cybersecurity company SentinelOne named the campaign “WIP26” - work in progress - because they were unable to attribute it to any actor or [… |
Malware | ★★★★ | ||
| 2023-02-16 17:57:40 | New Mirai botnet variant has been very busy, researchers say (lien direct) |  Researchers have discovered a new variant of the infamous Mirai malware that compromises smart devices and adds them to a botnet. Called V3G4, the variant exploits 13 known vulnerabilities, according to research by Palo Alto Networks' Unit 42. Mirai typically allows for full control of devices, adding them to its network of remotely controlled bots [… Researchers have discovered a new variant of the infamous Mirai malware that compromises smart devices and adds them to a botnet. Called V3G4, the variant exploits 13 known vulnerabilities, according to research by Palo Alto Networks' Unit 42. Mirai typically allows for full control of devices, adding them to its network of remotely controlled bots [… |
Malware | ★★ | ||
| 2023-02-08 21:17:09 | New info-stealing malware used against Ukraine organizations (lien direct) |  A new information-stealing malware named Graphiron is being used against a wide range of targets in Ukraine, according to new research. Researchers from Symantec declined to say which sorts of organizations are being targeted but confirmed that the attacks are being launched by an espionage group named Nodaria. They added that there is “limited evidence” [… A new information-stealing malware named Graphiron is being used against a wide range of targets in Ukraine, according to new research. Researchers from Symantec declined to say which sorts of organizations are being targeted but confirmed that the attacks are being launched by an espionage group named Nodaria. They added that there is “limited evidence” [… |
Malware | ★★★ | ||
| 2023-02-08 20:42:52 | Hackers used fake websites to target state agencies in Ukraine and Poland (lien direct) |  Hackers attempted last week to infect Ukrainian government computer systems with malware hosted on fake websites impersonating legitimate state services. Ukraine's computer emergency response team, CERT-UA, attributed the attack to a group called WinterVivern. The group has been active since at least June and includes Russian-speaking members. In addition to its Ukrainian targets, it has [… Hackers attempted last week to infect Ukrainian government computer systems with malware hosted on fake websites impersonating legitimate state services. Ukraine's computer emergency response team, CERT-UA, attributed the attack to a group called WinterVivern. The group has been active since at least June and includes Russian-speaking members. In addition to its Ukrainian targets, it has [… |
Malware | ★★★ | ||
| 2023-02-01 20:59:46 | Russia-backed hacker group Gamaredon attacking Ukraine with info-stealing malware (lien direct) |  The Russian-sponsored hacker group known as Gamaredon continues to attack Ukrainian organizations and remains one of the “key cyber threats” for Ukraine's cyberspace, according to a report the Ukrainian government published Wednesday. Ukraine claims that Gamaredon operates from the city of Sevastopol in Russia-occupied Crimea, but acts on orders from the FSB Center for Information [… The Russian-sponsored hacker group known as Gamaredon continues to attack Ukrainian organizations and remains one of the “key cyber threats” for Ukraine's cyberspace, according to a report the Ukrainian government published Wednesday. Ukraine claims that Gamaredon operates from the city of Sevastopol in Russia-occupied Crimea, but acts on orders from the FSB Center for Information [… |
Malware | ★★★ | ||
| 2023-01-27 19:40:02 | ESET: Sandworm could be behind new file-deleting malware targeting Ukraine (lien direct) |  The notorious state-backed Russian hacking group known as Sandworm may be behind new malware targeting Ukraine, according to research published Friday by cybersecurity company ESET. Malware called SwiftSlicer hit one organization in Ukraine before it was discovered by the Slovakia-based firm this week. The researchers cannot disclose the name of the affected organization and don’t [… The notorious state-backed Russian hacking group known as Sandworm may be behind new malware targeting Ukraine, according to research published Friday by cybersecurity company ESET. Malware called SwiftSlicer hit one organization in Ukraine before it was discovered by the Slovakia-based firm this week. The researchers cannot disclose the name of the affected organization and don’t [… |
Malware | ★★★ | ||
| 2023-01-25 17:12:26 | North Korean hackers use fake job offers, salary bumps as lure for crypto theft (lien direct) |  Hackers connected to the North Korean military used a variety of new phishing methods in 2022 to steal cryptocurrency, according to a new report from Proofpoint. The hackers bombarded people with emails about fake job opportunities at prestigious firms or fictitious salary increases as a way to get people to open emails carrying malware that [… Hackers connected to the North Korean military used a variety of new phishing methods in 2022 to steal cryptocurrency, according to a new report from Proofpoint. The hackers bombarded people with emails about fake job opportunities at prestigious firms or fictitious salary increases as a way to get people to open emails carrying malware that [… |
Malware | ★★ | ||
| 2023-01-19 19:17:18 | Canada\'s largest alcohol retailer infected with card skimming malware twice since December (lien direct) |  On January 12, Canadian alcohol retail giant LCBO announced that an “unauthorized party embedded malicious code” onto its website in order to steal information from customers in the process of checking out. Over five days in January, they wrote, customers “may have had their information compromised.” In fact, the infection was one of several to […] On January 12, Canadian alcohol retail giant LCBO announced that an “unauthorized party embedded malicious code” onto its website in order to steal information from customers in the process of checking out. Over five days in January, they wrote, customers “may have had their information compromised.” In fact, the infection was one of several to […] |
Malware | ★★★ | ||
| 2023-01-16 05:00:03 | Ransomware Diaries: Undercover with the Leader of Lockbit (lien direct) |  An unusual announcement appeared in Russian Dark Web forums in June of 2020. Amid the hundreds of ads offering stolen credit card numbers and batches of personally identifiable information there was a Call for Papers. “We're kicking off the summer PAPER CONTEST,” it read. “Accepted article topics include any methods for popuring shells, malware and [… An unusual announcement appeared in Russian Dark Web forums in June of 2020. Amid the hundreds of ads offering stolen credit card numbers and batches of personally identifiable information there was a Call for Papers. “We're kicking off the summer PAPER CONTEST,” it read. “Accepted article topics include any methods for popuring shells, malware and [… |
Ransomware Malware Guideline | ★★★ |
To see everything:
Our RSS (filtrered)
