What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-02-02 16:54:14 | Un autre hôpital de Chicago annonce de la cyberattaque Another Chicago hospital announces cyberattack (lien direct) |
 Pour la deuxième fois cette semaine, un hôpital de Chicago a annoncé une cyberattaque, avec des responsables disant que cela les a forcés à retirer tout le réseau de l'installation \\.L'hôpital de Lurie Children \\ est l'une des plus grandes organisations de soins de santé des enfants dans le Midwest, desservant 239 000 enfants chaque année.Jeudi soir, l'hôpital a publié un avis expliquant la source
Pour la deuxième fois cette semaine, un hôpital de Chicago a annoncé une cyberattaque, avec des responsables disant que cela les a forcés à retirer tout le réseau de l'installation \\.L'hôpital de Lurie Children \\ est l'une des plus grandes organisations de soins de santé des enfants dans le Midwest, desservant 239 000 enfants chaque année.Jeudi soir, l'hôpital a publié un avis expliquant la source
 For the second time this week, a Chicago hospital announced a cyberattack, with officials saying it forced them to take the facility\'s entire network offline. Lurie Children\'s Hospital is one of the biggest children\'s healthcare organizations in the Midwest, serving 239,000 children each year. On Thursday evening, the hospital published a notice explaining the source
For the second time this week, a Chicago hospital announced a cyberattack, with officials saying it forced them to take the facility\'s entire network offline. Lurie Children\'s Hospital is one of the biggest children\'s healthcare organizations in the Midwest, serving 239,000 children each year. On Thursday evening, the hospital published a notice explaining the source |
★★★ | |||
| 2024-02-01 22:25:43 | La FTC s'installe avec Blackbaud sur de mauvaises pratiques de données menant à un hack massif FTC settles with Blackbaud over poor data practices leading to massive hack (lien direct) |
 Blackbaud, une société de services de données et de logiciels, sera tenu de supprimer des données personnelles dont il n'a pas besoin dans le cadre d'un règlement de la Federal Trade Commission tenant la société responsable des pratiques de données qui ont permis à un pirate d'exfiltrer des informations sensibles appartenant à des millionsdes clients, a annoncé jeudi l'agence.La société basée à la Caroline du Sud \ \ \ est faible
Blackbaud, une société de services de données et de logiciels, sera tenu de supprimer des données personnelles dont il n'a pas besoin dans le cadre d'un règlement de la Federal Trade Commission tenant la société responsable des pratiques de données qui ont permis à un pirate d'exfiltrer des informations sensibles appartenant à des millionsdes clients, a annoncé jeudi l'agence.La société basée à la Caroline du Sud \ \ \ est faible
 Blackbaud, a data and software services company, will be required to delete personal data it doesn\'t need as part of a Federal Trade Commission settlement holding the company responsible for poor data practices which allowed a hacker to exfiltrate sensitive information belonging to millions of customers, the agency announced Thursday. The South Carolina-based company\'s weak
Blackbaud, a data and software services company, will be required to delete personal data it doesn\'t need as part of a Federal Trade Commission settlement holding the company responsible for poor data practices which allowed a hacker to exfiltrate sensitive information belonging to millions of customers, the agency announced Thursday. The South Carolina-based company\'s weak |
Hack | ★★★ | ||
| 2024-02-01 21:58:00 | L'acteur de l'État-nation a utilisé des références okta volées dans l'attaque de Thanksgiving, dit Cloudflare Nation-state actor used stolen Okta credentials in Thanksgiving attack, Cloudflare says (lien direct) |
 Senior executives at networking giant Cloudflare said a suspected nation-state attacker used credentials stolen from Okta to breach the company\'s systems in late November. In a blog post Thursday afternoon, Cloudflare CEO Matthew Prince and others said the company detected on Thanksgiving Day a threat actor on its self-hosted Atlassian server. “Our security team immediately
Senior executives at networking giant Cloudflare said a suspected nation-state attacker used credentials stolen from Okta to breach the company\'s systems in late November. In a blog post Thursday afternoon, Cloudflare CEO Matthew Prince and others said the company detected on Thanksgiving Day a threat actor on its self-hosted Atlassian server. “Our security team immediately
 Senior executives at networking giant Cloudflare said a suspected nation-state attacker used credentials stolen from Okta to breach the company\'s systems in late November. In a blog post Thursday afternoon, Cloudflare CEO Matthew Prince and others said the company detected on Thanksgiving Day a threat actor on its self-hosted Atlassian server. “Our security team immediately
Senior executives at networking giant Cloudflare said a suspected nation-state attacker used credentials stolen from Okta to breach the company\'s systems in late November. In a blog post Thursday afternoon, Cloudflare CEO Matthew Prince and others said the company detected on Thanksgiving Day a threat actor on its self-hosted Atlassian server. “Our security team immediately |
Threat | ★★★★ | ||
| 2024-02-01 20:05:04 | FritzFrog Botnet exploite le bug de log4shell maintenant, disent les experts FritzFrog botnet is exploiting Log4Shell bug now, experts say (lien direct) |
 Une variante d'un botnet de longue date abuse désormais de la vulnérabilité Log4Shell, mais va au-delà des applications orientées Internet et cible tous les hôtes dans un réseau interne d'une victime.Les chercheurs d'Akamai expliquent le changement dans le botnet Fritzfrog - qui existe depuis 2020 - dans un Rapport publié jeudi.Le botnet utilise généralement une force brute
Une variante d'un botnet de longue date abuse désormais de la vulnérabilité Log4Shell, mais va au-delà des applications orientées Internet et cible tous les hôtes dans un réseau interne d'une victime.Les chercheurs d'Akamai expliquent le changement dans le botnet Fritzfrog - qui existe depuis 2020 - dans un Rapport publié jeudi.Le botnet utilise généralement une force brute
 A variant of a long-running botnet is now abusing the Log4Shell vulnerability but is going beyond internet-facing applications and is targeting all hosts in a victim\'s internal network. Researchers at Akamai explain the shift in the FritzFrog botnet - which has existed since 2020 - in a report released Thursday. The botnet typically uses brute-force
A variant of a long-running botnet is now abusing the Log4Shell vulnerability but is going beyond internet-facing applications and is targeting all hosts in a victim\'s internal network. Researchers at Akamai explain the shift in the FritzFrog botnet - which has existed since 2020 - in a report released Thursday. The botnet typically uses brute-force |
Vulnerability | ★★ | ||
| 2024-02-01 18:29:26 | Les États-Unis annoncent une autre arrestation dans le cas de cybercriminalité BTC-E US announces another arrest in BTC-e cybercrime case (lien direct) |
 Un ressortissant biélorusse et chypriote serait lié au défunt échange de crypto-monnaie BTC-E est en garde à vue et fait face à des accusations liées au blanchiment d'argent, ont annoncé jeudi les procureurs fédéraux.Aliaksandr Klimenka, 42
Un ressortissant biélorusse et chypriote serait lié au défunt échange de crypto-monnaie BTC-E est en garde à vue et fait face à des accusations liées au blanchiment d'argent, ont annoncé jeudi les procureurs fédéraux.Aliaksandr Klimenka, 42
 A Belarusian and Cypriot national allegedly connected with the defunct cryptocurrency exchange BTC-e is in U.S. custody and faces charges related to money laundering, federal prosecutors said Thursday. Aliaksandr Klimenka, 42, is accused of helping to run BTC-e, which was “a significant cybercrime and online money laundering entity that allowed its users to trade in
A Belarusian and Cypriot national allegedly connected with the defunct cryptocurrency exchange BTC-e is in U.S. custody and faces charges related to money laundering, federal prosecutors said Thursday. Aliaksandr Klimenka, 42, is accused of helping to run BTC-e, which was “a significant cybercrime and online money laundering entity that allowed its users to trade in |
★★ | |||
| 2024-02-01 18:10:21 | Les lois sur la vie privée des États ont été paralysées par Big Tech, dit un nouveau rapport State privacy laws have been crippled by big tech, new report says (lien direct) |
 L'industrie technologique a façonné une série de lois sur la confidentialité faibles à l'échelle nationale, selon un nouveau rapport, la moitié des 14 États ayant adopté ces lois recevant des notes défaillantes et aucune ne recevant un «A» sur le tableau de bord du rapport \\.Le Electronic Privacy Information Center et le US PIRG Education Fund ont évalué les 14 factures à travers
L'industrie technologique a façonné une série de lois sur la confidentialité faibles à l'échelle nationale, selon un nouveau rapport, la moitié des 14 États ayant adopté ces lois recevant des notes défaillantes et aucune ne recevant un «A» sur le tableau de bord du rapport \\.Le Electronic Privacy Information Center et le US PIRG Education Fund ont évalué les 14 factures à travers
 The tech industry has shaped a series of weak privacy laws nationwide, according to a new report, with half of the 14 states to have passed such laws receiving failing grades and none receiving an “A” on the report\'s scorecard. The Electronic Privacy Information Center and U.S. PIRG Education Fund assessed the 14 bills across
The tech industry has shaped a series of weak privacy laws nationwide, according to a new report, with half of the 14 states to have passed such laws receiving failing grades and none receiving an “A” on the report\'s scorecard. The Electronic Privacy Information Center and U.S. PIRG Education Fund assessed the 14 bills across |
★★ | |||
| 2024-02-01 16:40:49 | Les espions russes se mite à l'identité des chercheurs occidentaux dans la campagne de piratage en cours Russian spies impersonating Western researchers in ongoing hacking campaign (lien direct) |
 Les pirates travaillant pour les services de renseignement de la Russie sont usurpés par les chercheurs et les universitaires dans une campagne en cours pour accéder à leurs collègues de messagerie, selon les messages et les fichiers vus par les futures nouvelles enregistrées et analysées indépendamment par deux sociétés de cybersécurité.Keir Giles, l'auteur britannique de « guerre de la Russie sur tout le monde » et un conseil consultant chez
Les pirates travaillant pour les services de renseignement de la Russie sont usurpés par les chercheurs et les universitaires dans une campagne en cours pour accéder à leurs collègues de messagerie, selon les messages et les fichiers vus par les futures nouvelles enregistrées et analysées indépendamment par deux sociétés de cybersécurité.Keir Giles, l'auteur britannique de « guerre de la Russie sur tout le monde » et un conseil consultant chez
 Hackers working for Russia\'s intelligence services are impersonating researchers and academics in an ongoing campaign to gain access to their colleagues\' email accounts, according to messages and files seen by Recorded Future News and independently analyzed by two cybersecurity companies. Keir Giles, the British author of “Russia\'s War on Everybody” and a consulting fellow at
Hackers working for Russia\'s intelligence services are impersonating researchers and academics in an ongoing campaign to gain access to their colleagues\' email accounts, according to messages and files seen by Recorded Future News and independently analyzed by two cybersecurity companies. Keir Giles, the British author of “Russia\'s War on Everybody” and a consulting fellow at |
★★★ | |||
| 2024-02-01 15:55:08 | Interpol arrête plus de 30 cybercriminels dans l'opération globale \\ 'Synergie \\' Interpol arrests more than 30 cybercriminals in global \\'Synergia\\' operation (lien direct) |
 Les forces de l'ordre internationales ont annoncé jeudi avoir détenu 31 cybercriminels présumés et identifié 1 300 serveurs malveillants qu'ils avaient utilisés pour effectuer des attaques de phishing et distribuer des logiciels malveillants.La soi-disant la synergie de l'opération d'Interpol, qui s'est déroulée de septembre à novembre 2023, «a été lancée en réponse à la croissance claire, à l'escalade et à la professionnalisation de la cybercriminalité transnationale et au besoin
Les forces de l'ordre internationales ont annoncé jeudi avoir détenu 31 cybercriminels présumés et identifié 1 300 serveurs malveillants qu'ils avaient utilisés pour effectuer des attaques de phishing et distribuer des logiciels malveillants.La soi-disant la synergie de l'opération d'Interpol, qui s'est déroulée de septembre à novembre 2023, «a été lancée en réponse à la croissance claire, à l'escalade et à la professionnalisation de la cybercriminalité transnationale et au besoin
 International law enforcement announced Thursday that they detained 31 suspected cybercriminals and identified 1,300 malicious servers that they used to carry out phishing attacks and distribute malware. Interpol\'s so-called Operation Synergia, which ran from September to November 2023, “was launched in response to the clear growth, escalation and professionalization of transnational cybercrime and the need
International law enforcement announced Thursday that they detained 31 suspected cybercriminals and identified 1,300 malicious servers that they used to carry out phishing attacks and distribute malware. Interpol\'s so-called Operation Synergia, which ran from September to November 2023, “was launched in response to the clear growth, escalation and professionalization of transnational cybercrime and the need |
Malware | ★★★ | ||
| 2024-02-01 15:55:03 | Toutes les agences civiles fédérales condamnées à déconnecter les produits Ivanti à risque d'ici vendredi All federal civilian agencies ordered to disconnect at-risk Ivanti products by Friday (lien direct) |
 Vendredi, toutes les agences civiles fédérales des États-Unis ont été condamnées à déconnecter les produits Secure et Policy Secure et Policy Secure après que d'autres vulnérabilités aient été trouvées dans les outils cette semaine.Dans un Directive mise à jour publiée mercredi, l'agence de sécurité de cybersécurité et d'infrastructure (CISA) a donné aux agences jusqu'à vendredi à minuit pour supprimer les outils
Vendredi, toutes les agences civiles fédérales des États-Unis ont été condamnées à déconnecter les produits Secure et Policy Secure et Policy Secure après que d'autres vulnérabilités aient été trouvées dans les outils cette semaine.Dans un Directive mise à jour publiée mercredi, l'agence de sécurité de cybersécurité et d'infrastructure (CISA) a donné aux agences jusqu'à vendredi à minuit pour supprimer les outils
 All federal civilian agencies in the U.S. have been ordered to disconnect Ivanti Connect Secure and Policy Secure products by Friday after more vulnerabilities were found in the tools this week. In an updated directive published on Wednesday, the Cybersecurity and Infrastructure Security Agency (CISA) gave agencies until Friday at midnight to remove the tools
All federal civilian agencies in the U.S. have been ordered to disconnect Ivanti Connect Secure and Policy Secure products by Friday after more vulnerabilities were found in the tools this week. In an updated directive published on Wednesday, the Cybersecurity and Infrastructure Security Agency (CISA) gave agencies until Friday at midnight to remove the tools |
Tool Vulnerability | ★★★ | ||
| 2024-02-01 15:21:36 | Les pirates liés à l'Inde ciblent le Pakistan avec des logiciels espions dans une nouvelle campagne India-linked hackers target Pakistan with spyware in new campaign (lien direct) |
 Les pirates suspects parrainés par l'État indien ont utilisé des escroqueries romantiques pour attirer les victimes du Pakistan pour installer des applications malveillantes, infectant leurs appareils par des logiciels malveillants d'espionnage, selon de nouvelles recherches.Le groupe, connu sous le nom de patchwork, a créé au moins 12 applications Android malveillantes, y compris MeetMe, le chat de Let \\, le chat rapide et le rafaqat, et les a distribués via Google Play et autres
Les pirates suspects parrainés par l'État indien ont utilisé des escroqueries romantiques pour attirer les victimes du Pakistan pour installer des applications malveillantes, infectant leurs appareils par des logiciels malveillants d'espionnage, selon de nouvelles recherches.Le groupe, connu sous le nom de patchwork, a créé au moins 12 applications Android malveillantes, y compris MeetMe, le chat de Let \\, le chat rapide et le rafaqat, et les a distribués via Google Play et autres
 Suspected Indian state-sponsored hackers have used romance scams to lure victims in Pakistan into installing malicious apps, infecting their devices with spying malware, according to new research. The group, known as Patchwork, created at least 12 malicious Android apps, including MeetMe, Let\'s Chat, Quick Chat, and Rafaqat, and distributed them through Google Play and other
Suspected Indian state-sponsored hackers have used romance scams to lure victims in Pakistan into installing malicious apps, infecting their devices with spying malware, according to new research. The group, known as Patchwork, created at least 12 malicious Android apps, including MeetMe, Let\'s Chat, Quick Chat, and Rafaqat, and distributed them through Google Play and other |
Malware Mobile | ★★★ | ||
| 2024-02-01 13:14:33 | Nouvelle enquête parlementaire pour examiner l'intégrité démocratique du Royaume-Uni avant les élections New parliamentary inquiry to examine UK\\'s democratic integrity ahead of election (lien direct) |
 Une enquête parlementaire examinera les travaux d'un groupe de travail du Conseil de sécurité nationale (NSC) qui vise à protéger l'intégrité démocratique du Royaume-Uni contre les ingérences étrangères.Dans une annonce jeudi intitulée «Deepfakes, désinformation, fraude et cyberattaques», le comité conjoint sur la stratégie de sécurité nationale (JCNSS) a déclaré qu'il soulèverait des questions sur
Une enquête parlementaire examinera les travaux d'un groupe de travail du Conseil de sécurité nationale (NSC) qui vise à protéger l'intégrité démocratique du Royaume-Uni contre les ingérences étrangères.Dans une annonce jeudi intitulée «Deepfakes, désinformation, fraude et cyberattaques», le comité conjoint sur la stratégie de sécurité nationale (JCNSS) a déclaré qu'il soulèverait des questions sur
 A parliamentary inquiry will scrutinize the work of a National Security Council (NSC) taskforce that aims to protect the democratic integrity of the United Kingdom from foreign interference. In an announcement on Thursday titled “deepfakes, misinformation, fraud and cyberattacks” the Joint Committee on the National Security Strategy (JCNSS) said it would be raising questions about
A parliamentary inquiry will scrutinize the work of a National Security Council (NSC) taskforce that aims to protect the democratic integrity of the United Kingdom from foreign interference. In an announcement on Thursday titled “deepfakes, misinformation, fraud and cyberattacks” the Joint Committee on the National Security Strategy (JCNSS) said it would be raising questions about |
★★★ | |||
| 2024-02-01 09:00:00 | Rapport: Civil Society in Jordan sous agression par les logiciels espions Pegasus de NSO \\ Report: Civil society in Jordan under assault by NSO\\'s Pegasus spyware (lien direct) |
 Une enquête basée sur des entretiens, des documents et une analyse médico-légale révèle de nouvelles preuves que les téléphones de trois douzaines de journalistes, défenseurs des droits de l'homme et avocats en Jordanie ont été infectés par des logiciels espions de Pegasus.Dans un rapport publié jeudi, accès maintenant , une organisation de défense des droits numériques, a uni ses forces avec le Citizen Lab , une organisation de surveillance de cybersécurité au
Une enquête basée sur des entretiens, des documents et une analyse médico-légale révèle de nouvelles preuves que les téléphones de trois douzaines de journalistes, défenseurs des droits de l'homme et avocats en Jordanie ont été infectés par des logiciels espions de Pegasus.Dans un rapport publié jeudi, accès maintenant , une organisation de défense des droits numériques, a uni ses forces avec le Citizen Lab , une organisation de surveillance de cybersécurité au
 An investigation based on interviews, documents and forensic analysis reveals new evidence that the phones of some three dozen journalists, human rights advocates and lawyers in Jordan were infected with Pegasus spyware. In a report released Thursday, Access Now, a digital rights organization, joined forces with the Citizen Lab, a cybersecurity watchdog organization at the
An investigation based on interviews, documents and forensic analysis reveals new evidence that the phones of some three dozen journalists, human rights advocates and lawyers in Jordan were infected with Pegasus spyware. In a report released Thursday, Access Now, a digital rights organization, joined forces with the Citizen Lab, a cybersecurity watchdog organization at the |
★★★ | |||
| 2024-01-31 22:20:10 | Deux nouveaux bogues Ivanti découverts comme CISA met en garde contre les pirates contournant les atténuations Two new Ivanti bugs discovered as CISA warns of hackers bypassing mitigations (lien direct) |
 La société informatique Ivanti a déclaré cette semaine qu'elle avait découvert deux nouvelles vulnérabilités affectant ses produits lors de l'enquête sur les bogues découverts plus tôt dans le mois.Les problèmes affectent la politique sécurisée d'Ivanti et Ivanti Connect Secure VPN qui sont largement utilisés à travers le gouvernement américain et d'autres industries.Les deux vulnérabilités - appelées CVE-2024-21888 et
La société informatique Ivanti a déclaré cette semaine qu'elle avait découvert deux nouvelles vulnérabilités affectant ses produits lors de l'enquête sur les bogues découverts plus tôt dans le mois.Les problèmes affectent la politique sécurisée d'Ivanti et Ivanti Connect Secure VPN qui sont largement utilisés à travers le gouvernement américain et d'autres industries.Les deux vulnérabilités - appelées CVE-2024-21888 et
 IT company Ivanti said this week that it discovered two new vulnerabilities affecting its products while investigating bugs discovered earlier in the month. The issues affect Ivanti\'s Policy Secure and Ivanti Connect Secure VPN products that are used widely across the U.S. government and other industries. The two vulnerabilities - referred to as CVE-2024-21888 and
IT company Ivanti said this week that it discovered two new vulnerabilities affecting its products while investigating bugs discovered earlier in the month. The issues affect Ivanti\'s Policy Secure and Ivanti Connect Secure VPN products that are used widely across the U.S. government and other industries. The two vulnerabilities - referred to as CVE-2024-21888 and |
Vulnerability | ★★ | ||
| 2024-01-31 20:48:29 | L'audience du comité judiciaire inculpé promeut les factures de sécurité en ligne des enfants, excore des PDG technologiques Charged Judiciary Committee hearing promotes child online safety bills, excoriates tech CEOs (lien direct) |
 Un groupe bipartite de sénateurs a attaqué sans relâche les PDG de cinq principales plateformes de médias sociaux mercredi lors d'une audience émotionnelle de près de quatre heures du comité judiciaire du Sénat a porté sur les plateformes \\ '' de ne pas arrêter l'exploitation sexuelle des enfants en ligne.Les projets de loi sur les comités judiciaires destinés à répondre aux prétendus dommages aux enfants par les plateformes de médias sociaux ont une écrasante majorité
Un groupe bipartite de sénateurs a attaqué sans relâche les PDG de cinq principales plateformes de médias sociaux mercredi lors d'une audience émotionnelle de près de quatre heures du comité judiciaire du Sénat a porté sur les plateformes \\ '' de ne pas arrêter l'exploitation sexuelle des enfants en ligne.Les projets de loi sur les comités judiciaires destinés à répondre aux prétendus dommages aux enfants par les plateformes de médias sociaux ont une écrasante majorité
 A bipartisan group of senators relentlessly attacked CEOs from five major social media platforms Wednesday during an emotional nearly four-hour Senate Judiciary Committee hearing focused on the platforms\' alleged failure to stop the sexual exploitation of children online. Judiciary Committee bills meant to address the purported harms to children by social media platforms have overwhelming
A bipartisan group of senators relentlessly attacked CEOs from five major social media platforms Wednesday during an emotional nearly four-hour Senate Judiciary Committee hearing focused on the platforms\' alleged failure to stop the sexual exploitation of children online. Judiciary Committee bills meant to address the purported harms to children by social media platforms have overwhelming |
★★ | |||
| 2024-01-31 19:25:01 | Les États-Unis confirment le retrait du botnet géré par la Chine ciblant les routeurs à domicile et au bureau US confirms takedown of China-run botnet targeting home and office routers (lien direct) |
 Le ministère américain de la Justice a confirmé mercredi qu'il avait perturbé un botnet géré par une opération de piratage du gouvernement chinois prolifique connu sous le nom de Volt Typhoon.Les nouvelles du démontage du botnet ont émergé mardi pour la première fois, lorsque Reuters a rapporté que le ministère de la Justice et le FBI ont obtenu l'autorisation légale d'un tribunal américain pour désactiver à distance les outils implantés
Le ministère américain de la Justice a confirmé mercredi qu'il avait perturbé un botnet géré par une opération de piratage du gouvernement chinois prolifique connu sous le nom de Volt Typhoon.Les nouvelles du démontage du botnet ont émergé mardi pour la première fois, lorsque Reuters a rapporté que le ministère de la Justice et le FBI ont obtenu l'autorisation légale d'un tribunal américain pour désactiver à distance les outils implantés
 The U.S. Justice Department confirmed on Wednesday that it disrupted a botnet run by a prolific Chinese government hacking operation known as Volt Typhoon. News of the botnet takedown first emerged on Tuesday, when Reuters reported that the Justice Department and FBI got legal authorization from a U.S. court to remotely disable the tools implanted
The U.S. Justice Department confirmed on Wednesday that it disrupted a botnet run by a prolific Chinese government hacking operation known as Volt Typhoon. News of the botnet takedown first emerged on Tuesday, when Reuters reported that the Justice Department and FBI got legal authorization from a U.S. court to remotely disable the tools implanted |
Tool | Guam | ★★★ | |
| 2024-01-31 17:17:14 | Les patrons du crime derrière le Myanmar Cyber \\ 'Fraud Dens \\' ont été remis au gouvernement chinois Crime bosses behind Myanmar cyber \\'fraud dens\\' handed over to Chinese government (lien direct) |
 Les autorités du Myanmar ont remis au gouvernement chinois 10 suspects accusés de participation à l'industrie de la cyber-fraude organisée, y compris les chefs de trois familles de crimes éminentes.Les arrestations interviennent après que le ministère de la Sécurité publique de la Chine a publié une liste recherchée en décembre pour les membres des« Syndicats de crime familial », qui ont des liens avec le Myanmar \\ 's
Les autorités du Myanmar ont remis au gouvernement chinois 10 suspects accusés de participation à l'industrie de la cyber-fraude organisée, y compris les chefs de trois familles de crimes éminentes.Les arrestations interviennent après que le ministère de la Sécurité publique de la Chine a publié une liste recherchée en décembre pour les membres des« Syndicats de crime familial », qui ont des liens avec le Myanmar \\ 's
 Myanmar authorities handed over to the Chinese government 10 suspects accused of involvement in the organized cyber fraud industry, including the heads of three prominent crime families. The arrests come after China\'s Ministry of Public Security released a wanted list in December for the members of the “family crime syndicates,” which have ties to Myanmar\'s
Myanmar authorities handed over to the Chinese government 10 suspects accused of involvement in the organized cyber fraud industry, including the heads of three prominent crime families. The arrests come after China\'s Ministry of Public Security released a wanted list in December for the members of the “family crime syndicates,” which have ties to Myanmar\'s |
★★ | |||
| 2024-01-31 15:11:37 | Nakasone: 2024 sera les élections les plus sécurisées \\ 'à ce jour \\' Nakasone: 2024 will be most secure election \\'to date\\' (lien direct) |
 Le directeur sortant de la plus grande agence de renseignement du pays et de la meilleure organisation de lutte contre la guerre numérique a prédit mardi que les élections américaines de 2024 seraient la plus sûre à ce jour de l'ingérence étrangère.«Oui, je crois que ce sera l'élection la plus sûre que nous ayons eu à ce jour», a retiré le cyber commandement américain et le général de l'armée en chef de la NSA, Paul Nakasone,
Le directeur sortant de la plus grande agence de renseignement du pays et de la meilleure organisation de lutte contre la guerre numérique a prédit mardi que les élections américaines de 2024 seraient la plus sûre à ce jour de l'ingérence étrangère.«Oui, je crois que ce sera l'élection la plus sûre que nous ayons eu à ce jour», a retiré le cyber commandement américain et le général de l'armée en chef de la NSA, Paul Nakasone,
 The outgoing director of the country\'s largest intelligence agency and top digital warfighting organization on Tuesday predicted that the 2024 U.S. election would be the safest yet from foreign interference. “Yes, I believe it will be the most secure election we\'ve had to date,” retiring U.S. Cyber Command and NSA chief Army Gen. Paul Nakasone
The outgoing director of the country\'s largest intelligence agency and top digital warfighting organization on Tuesday predicted that the 2024 U.S. election would be the safest yet from foreign interference. “Yes, I believe it will be the most secure election we\'ve had to date,” retiring U.S. Cyber Command and NSA chief Army Gen. Paul Nakasone |
★★★ | |||
| 2024-01-31 14:21:50 | Cyberattack de décembre sur l'hôpital communautaire de Chicago revendiqué par Lockbit Gang December cyberattack on Chicago community hospital claimed by LockBit gang (lien direct) |
 Une cyberattaque récemment annoncée dans un grand hôpital communautaire de Chicago a été revendiquée par le gang de ransomware de Lockbit.Saint Anthony Hospital on the City \'s West Side Lundi et a déclaré que l'attaque avait été découverte pour la première fois le 18 décembre. Mardi soir, le gang de ransomware de Lockbit a publié l'hôpital à
Une cyberattaque récemment annoncée dans un grand hôpital communautaire de Chicago a été revendiquée par le gang de ransomware de Lockbit.Saint Anthony Hospital on the City \'s West Side Lundi et a déclaré que l'attaque avait été découverte pour la première fois le 18 décembre. Mardi soir, le gang de ransomware de Lockbit a publié l'hôpital à
 A recently announced cyberattack on a large community hospital in Chicago was claimed by the LockBit ransomware gang. Saint Anthony Hospital on the city\'s west side acknowledged the incident in a statement on Monday and said the attack was first discovered on December 18. On Tuesday evening, the LockBit ransomware gang posted the hospital to
A recently announced cyberattack on a large community hospital in Chicago was claimed by the LockBit ransomware gang. Saint Anthony Hospital on the city\'s west side acknowledged the incident in a statement on Monday and said the attack was first discovered on December 18. On Tuesday evening, the LockBit ransomware gang posted the hospital to |
Ransomware | ★★ | ||
| 2024-01-31 13:30:18 | Le domaine Internet de haut niveau russe souffre d'une panne massive Russian top-level internet domain suffers massive outage (lien direct) |
 Les citoyens russes ne pouvaient pas accéder à la majorité des sites Web du domaine du pays \\..La panne était
Les citoyens russes ne pouvaient pas accéder à la majorité des sites Web du domaine du pays \\..La panne était
 Russian citizens couldn\'t access the majority of websites on the country\'s .ru domain for several hours on Tuesday, including the Yandex search engine, the VKontakte social media platform, the major state-owned bank Sberbank and news outlets. The outage was reportedly caused by a technical problem with the .ru domain\'s global Domain Name System Security Extensions,
Russian citizens couldn\'t access the majority of websites on the country\'s .ru domain for several hours on Tuesday, including the Yandex search engine, the VKontakte social media platform, the major state-owned bank Sberbank and news outlets. The outage was reportedly caused by a technical problem with the .ru domain\'s global Domain Name System Security Extensions, |
Technical | ★★ | ||
| 2024-01-30 21:31:33 | Le sénateur propose une nouvelle disposition de chiffrement dans le projet de loi contre l'exploitation des enfants en ligne Senator proposes new encryption provision in bill against online child exploitation (lien direct) |
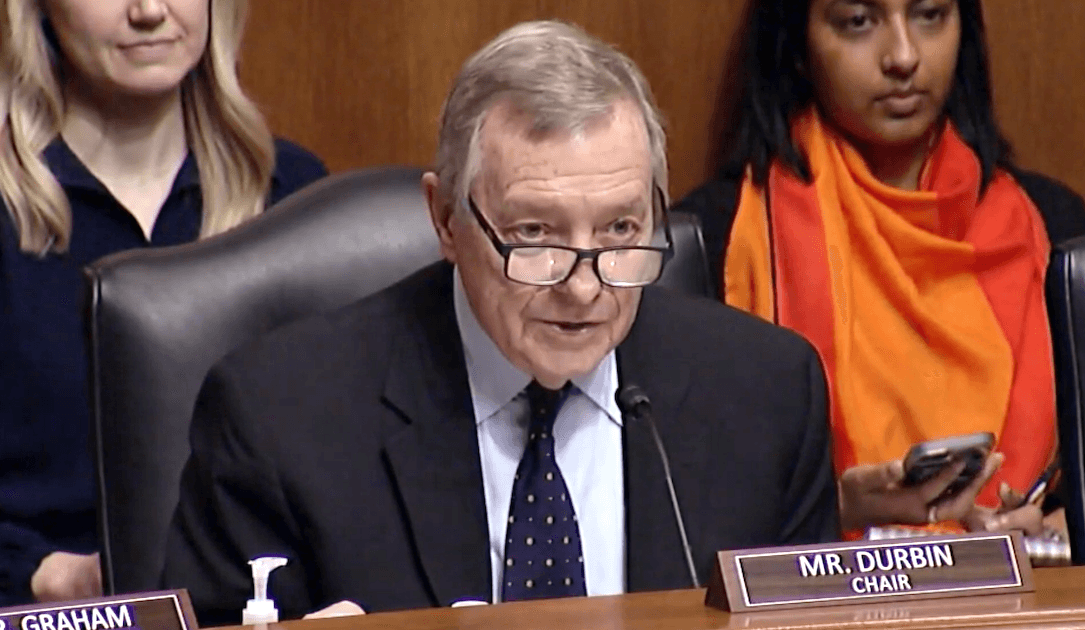 Le sénateur Dick Durbin a fait circuler une version mise à jour de la législation conçue pour réprimer les documents d'exploitation des enfants en ligne, avec de nouveaux libellés qui feraient moins pour éroder les protections juridiques pour les communications cryptées, selon les défenseurs de la vie privée.Le nouveau projet du projet de loi, comme le montre les nouvelles réduites, vient du comité judiciaire du Sénat
Le sénateur Dick Durbin a fait circuler une version mise à jour de la législation conçue pour réprimer les documents d'exploitation des enfants en ligne, avec de nouveaux libellés qui feraient moins pour éroder les protections juridiques pour les communications cryptées, selon les défenseurs de la vie privée.Le nouveau projet du projet de loi, comme le montre les nouvelles réduites, vient du comité judiciaire du Sénat
 Sen. Dick Durbin has been circulating an updated version of legislation designed to crack down on child exploitation materials online, with new wording that would do less to erode legal protections for encrypted communications, privacy advocates say. The new draft of the bill, as seen by Recorded Future News, comes as the Senate Judiciary Committee
Sen. Dick Durbin has been circulating an updated version of legislation designed to crack down on child exploitation materials online, with new wording that would do less to erode legal protections for encrypted communications, privacy advocates say. The new draft of the bill, as seen by Recorded Future News, comes as the Senate Judiciary Committee |
Legislation | ★★ | ||
| 2024-01-30 20:44:47 | Le plus grand comté de Georgia \\ confirme la cyberattaque provoquant des problèmes généralisés Georgia\\'s largest county confirms cyberattack causing widespread issues (lien direct) |
 Le comté le plus peuplé de Géorgie est confronté à une panne informatique causée par une cyberattaque découverte au cours du week-end.Le président du conseil des commissaires du comté de Fulton, Robb Pitts, a tenu un Conférence de presse Lundi, expliquant que l'attaque a affecté les systèmes téléphoniques du bureau du comté et en ligneTransactions, y compris celles impliquant des armes à feu et des licences de mariage."Pendant le weekend,
Le comté le plus peuplé de Géorgie est confronté à une panne informatique causée par une cyberattaque découverte au cours du week-end.Le président du conseil des commissaires du comté de Fulton, Robb Pitts, a tenu un Conférence de presse Lundi, expliquant que l'attaque a affecté les systèmes téléphoniques du bureau du comté et en ligneTransactions, y compris celles impliquant des armes à feu et des licences de mariage."Pendant le weekend,
 The most populous county in Georgia is dealing with an IT outage caused by a cyberattack discovered over the weekend. Fulton County Board of Commissioners Chairman Robb Pitts held a press conference Monday explaining that the attack affected county office phone systems and online transactions, including those involving firearm and marriage licenses. “Over the weekend,
The most populous county in Georgia is dealing with an IT outage caused by a cyberattack discovered over the weekend. Fulton County Board of Commissioners Chairman Robb Pitts held a press conference Monday explaining that the attack affected county office phone systems and online transactions, including those involving firearm and marriage licenses. “Over the weekend, |
★★ | |||
| 2024-01-30 19:04:46 | La police brésilienne procède à des arrestations dans un cas de logiciels malveillants de Grandoreiro Banking Brazilian police make arrests in Grandoreiro banking malware case (lien direct) |
 La police brésilienne a déclaré avoir interrompu l'exploitation d'un groupe criminel responsable d'un programme de fraude bancaire soupçonné de voler ses victimes de & Euro; 3,6 millions (3,9 millions de dollars) depuis 2019.Grandoreiro pour cibler les victimes au Brésil, au Mexique et en Espagne, Selon les chercheurs à la société Slovaquie ESET, qui a aidé Brésilien
La police brésilienne a déclaré avoir interrompu l'exploitation d'un groupe criminel responsable d'un programme de fraude bancaire soupçonné de voler ses victimes de & Euro; 3,6 millions (3,9 millions de dollars) depuis 2019.Grandoreiro pour cibler les victimes au Brésil, au Mexique et en Espagne, Selon les chercheurs à la société Slovaquie ESET, qui a aidé Brésilien
 Brazilian police said they disrupted the operation of a criminal group responsible for a banking fraud scheme suspected of robbing its victims of €3.6 million ($3.9 million) since 2019. The criminals used banking malware called Grandoreiro to target victims in Brazil, Mexico and Spain, according to researchers at the Slovakia-based company ESET, who helped Brazilian
Brazilian police said they disrupted the operation of a criminal group responsible for a banking fraud scheme suspected of robbing its victims of €3.6 million ($3.9 million) since 2019. The criminals used banking malware called Grandoreiro to target victims in Brazil, Mexico and Spain, according to researchers at the Slovakia-based company ESET, who helped Brazilian |
Malware | ★★ | ||
| 2024-01-30 18:26:36 | Le cyber-travail présumé de l'Etat islamique invite les sanctions américaines sur deux ressortissants égyptiens Alleged ISIS cyber work prompts US sanctions on two Egyptian nationals (lien direct) |
 Le Département du Trésor américain a sanctionné deux ressortissants égyptiens pour leur travail qui aurait formé des membres de l'Etat islamique en cybersécurité et facilitant les efforts de financement à l'étranger pour le groupe.Mardi, Le département a dit mu \\ 'min al-mawji Mahmud Salim et sa partenaire Sarah Jamal MuhammadAl-Sayyid est derrière Electronic Horizons Foundation (EHF) - une plate-forme qui, selon les États-Unis, est
Le Département du Trésor américain a sanctionné deux ressortissants égyptiens pour leur travail qui aurait formé des membres de l'Etat islamique en cybersécurité et facilitant les efforts de financement à l'étranger pour le groupe.Mardi, Le département a dit mu \\ 'min al-mawji Mahmud Salim et sa partenaire Sarah Jamal MuhammadAl-Sayyid est derrière Electronic Horizons Foundation (EHF) - une plate-forme qui, selon les États-Unis, est
 The U.S. Treasury Department sanctioned two Egyptian nationals for their work allegedly training members of ISIS on cybersecurity and facilitating overseas funding efforts for the group. On Tuesday, the department said Mu\'min Al-Mawji Mahmud Salim and his partner Sarah Jamal Muhammad Al-Sayyid are behind Electronic Horizons Foundation (EHF) - a platform the U.S. believes is
The U.S. Treasury Department sanctioned two Egyptian nationals for their work allegedly training members of ISIS on cybersecurity and facilitating overseas funding efforts for the group. On Tuesday, the department said Mu\'min Al-Mawji Mahmud Salim and his partner Sarah Jamal Muhammad Al-Sayyid are behind Electronic Horizons Foundation (EHF) - a platform the U.S. believes is |
★★★ | |||
| 2024-01-30 17:39:33 | Schneider Electric confirme l'attaque des ransomwares contre la division de la durabilité Schneider Electric confirms ransomware attack on sustainability division (lien direct) |
 La multinationale française Schneider Electric a déclaré que sa division commerciale de durabilité avait souffert d'une attaque de ransomware au début du mois.La société a confirmé l'incident dans un communiqué cette semaine que l'attaque a affecté son produit de conseil en ressources - un outil de visualisation des données pour les informations sur la durabilité - ainsi que d'autres «systèmes spécifiques à la division».Schneider Electric a dit qu'ils
La multinationale française Schneider Electric a déclaré que sa division commerciale de durabilité avait souffert d'une attaque de ransomware au début du mois.La société a confirmé l'incident dans un communiqué cette semaine que l'attaque a affecté son produit de conseil en ressources - un outil de visualisation des données pour les informations sur la durabilité - ainsi que d'autres «systèmes spécifiques à la division».Schneider Electric a dit qu'ils
 French multinational Schneider Electric said its Sustainability Business division suffered from a ransomware attack earlier this month. The company confirmed the incident in a statement this week that the attack affected its Resource Advisory product - a data visualization tool for sustainability information - as well as other “division specific systems.” Schneider Electric said they
French multinational Schneider Electric said its Sustainability Business division suffered from a ransomware attack earlier this month. The company confirmed the incident in a statement this week that the attack affected its Resource Advisory product - a data visualization tool for sustainability information - as well as other “division specific systems.” Schneider Electric said they |
Ransomware Tool | ★★ | ||
| 2024-01-30 17:29:55 | Les fédéraux disent que les efforts anti-robocals semblent travailler contre des sources étrangères Feds say anti-robocall efforts appear to be working against foreign sources (lien direct) |
 Le gouvernement américain a déclaré mardi que les «fournisseurs de passerelles» de télécommunications semblent faire un meilleur travail en bloquant les robocalles internationaux axés sur l'escroquerie d'atteindre les Américains.La Federal Communications Commission (FCC) a déclaré que ses efforts avec la Federal Trade Commission (FTC) «réduitApparemment le trafic de robocall illégal sur plusieurs réseaux. »Les deux agences ont contacté l'année dernière à sept
Le gouvernement américain a déclaré mardi que les «fournisseurs de passerelles» de télécommunications semblent faire un meilleur travail en bloquant les robocalles internationaux axés sur l'escroquerie d'atteindre les Américains.La Federal Communications Commission (FCC) a déclaré que ses efforts avec la Federal Trade Commission (FTC) «réduitApparemment le trafic de robocall illégal sur plusieurs réseaux. »Les deux agences ont contacté l'année dernière à sept
 The U.S. government said on Tuesday that telecom “gateway providers” appear to be doing a better job blocking scam-oriented international robocalls from reaching Americans. The Federal Communications Commission (FCC) said its efforts with the Federal Trade Commission (FTC) “reduced apparently illegal robocall traffic across multiple networks.” The two agencies reached out last year to seven
The U.S. government said on Tuesday that telecom “gateway providers” appear to be doing a better job blocking scam-oriented international robocalls from reaching Americans. The Federal Communications Commission (FCC) said its efforts with the Federal Trade Commission (FTC) “reduced apparently illegal robocall traffic across multiple networks.” The two agencies reached out last year to seven |
★★ | |||
| 2024-01-30 15:16:17 | La Russie de 72 ans a condamné à 5 ans de prison pour des publications anti-guerre sur les réseaux sociaux 72-year-old Russian woman sentenced to 5 years in prison for anti-war posts on social media (lien direct) |
 Une femme russe de 72 ans a été condamnée à 5,5 ans de prison pour avoir partagé des messages anti-guerre sur la plate-forme de médias sociaux Vkontakte dans le dernier exemple de la répression du Kremlin contre les citoyens critiquant le gouvernement en ligne.Evgeniya Mayboroda, résidente de la région de Rossia \\ s Rostov, était a été reconnu coupable de répandre les appels à des activités extrémistes et de présumés «militaires»Fakes motivés par
Une femme russe de 72 ans a été condamnée à 5,5 ans de prison pour avoir partagé des messages anti-guerre sur la plate-forme de médias sociaux Vkontakte dans le dernier exemple de la répression du Kremlin contre les citoyens critiquant le gouvernement en ligne.Evgeniya Mayboroda, résidente de la région de Rossia \\ s Rostov, était a été reconnu coupable de répandre les appels à des activités extrémistes et de présumés «militaires»Fakes motivés par
 A 72-year-old Russian woman received a 5.5-year prison sentence for sharing anti-war messages on social media platform VKontakte in the latest example of the Kremlin\'s crackdown on citizens criticizing the government online. Evgeniya Mayboroda, a resident of Russia\'s Rostov region, was found guilty of spreading calls for extremist activity and alleged “military” fakes motivated by
A 72-year-old Russian woman received a 5.5-year prison sentence for sharing anti-war messages on social media platform VKontakte in the latest example of the Kremlin\'s crackdown on citizens criticizing the government online. Evgeniya Mayboroda, a resident of Russia\'s Rostov region, was found guilty of spreading calls for extremist activity and alleged “military” fakes motivated by |
Legislation | ★★ | ||
| 2024-01-30 14:45:43 | Dans la législation sur la protection de la vie privée de l'État, le lobby technologique voit un seul champ de bataille In patchwork of state privacy legislation, tech lobby sees a single battlefield (lien direct) |
 Le gouverneur du New Jersey \\ a signé une loi durable sur les données de la vie privée plus tôt ce mois-ci, faisant de l'État l'un des huit à l'échelle nationale pour adopter une législation complète de la vie privée au cours de la dernière année.Il n'était pas facile de s'y rendre, dit le législateur qui était le moteur du projet de loi.Le sénateur de l'État Raj Mukherji a déclaré que l'effort de l'industrie technologique contre le
Le gouverneur du New Jersey \\ a signé une loi durable sur les données de la vie privée plus tôt ce mois-ci, faisant de l'État l'un des huit à l'échelle nationale pour adopter une législation complète de la vie privée au cours de la dernière année.Il n'était pas facile de s'y rendre, dit le législateur qui était le moteur du projet de loi.Le sénateur de l'État Raj Mukherji a déclaré que l'effort de l'industrie technologique contre le
 New Jersey\'s governor signed a hard-fought data privacy law earlier this month, making the state one of eight nationwide to enact comprehensive privacy legislation in the past year. Getting there wasn\'t easy, though, says the legislator who was the driving force behind the bill. State Sen. Raj Mukherji says the technology industry\'s effort against the
New Jersey\'s governor signed a hard-fought data privacy law earlier this month, making the state one of eight nationwide to enact comprehensive privacy legislation in the past year. Getting there wasn\'t easy, though, says the legislator who was the driving force behind the bill. State Sen. Raj Mukherji says the technology industry\'s effort against the |
Legislation | ★★ | ||
| 2024-01-29 20:13:34 | L'Europe sanctionne l'agence de censure Internet russe et son chef Europe sanctions Russian internet censorship agency and its leader (lien direct) |
 Le Conseil européen a imposé des sanctions à une agence russe responsable de la censure sur Internet dans le pays.Le conseil a déclaré dans une déclaration lundi que l'organisation para-gouvernementale russe appelé leLigue Internet sûre «aide le gouvernement russe à faire respecter les pratiques de censure», tandis que sa présidente, Ekaterina Mizulina, «est responsable des abus graves et systématiques
Le Conseil européen a imposé des sanctions à une agence russe responsable de la censure sur Internet dans le pays.Le conseil a déclaré dans une déclaration lundi que l'organisation para-gouvernementale russe appelé leLigue Internet sûre «aide le gouvernement russe à faire respecter les pratiques de censure», tandis que sa présidente, Ekaterina Mizulina, «est responsable des abus graves et systématiques
 The European Council has imposed sanctions on a Russian agency responsible for internet censorship in the country. The council said in a statement on Monday that the Russian para-governmental organization called the Safe Internet League “aids the Russian government in enforcing censorship practices,” while its chairwoman, Ekaterina Mizulina, “is responsible for serious and systematic abuses
The European Council has imposed sanctions on a Russian agency responsible for internet censorship in the country. The council said in a statement on Monday that the Russian para-governmental organization called the Safe Internet League “aids the Russian government in enforcing censorship practices,” while its chairwoman, Ekaterina Mizulina, “is responsible for serious and systematic abuses |
★★★ | |||
| 2024-01-29 18:16:10 | L'intelligence iranienne a utilisé le trafiquant de Narco pour recruter Hells Angel pour l'assassinat prévu Iranian intelligence used narco trafficker to recruit Hells Angel for planned assassination (lien direct) |
 Un prétendu trafiquant de drogue iranien avec des liens avec les services de renseignement de Téhéran a été inculpé aux États-Unis d'avoir recruté un membre des Hells Angels dans un complot visant à assassiner un transfuge iranien qui avait déjà fui vers le Maryland.Un l'acte d'accusation du grand jury contre Naji Sharifi Zindashti, 49
Un prétendu trafiquant de drogue iranien avec des liens avec les services de renseignement de Téhéran a été inculpé aux États-Unis d'avoir recruté un membre des Hells Angels dans un complot visant à assassiner un transfuge iranien qui avait déjà fui vers le Maryland.Un l'acte d'accusation du grand jury contre Naji Sharifi Zindashti, 49
 An alleged Iranian drug trafficker with ties to Tehran\'s intelligence services has been charged in the United States with recruiting a member of the Hells Angels in a plot to murder an Iranian defector who had previously fled to Maryland. A Grand Jury Indictment against Naji Sharifi Zindashti, 49, was unsealed on Monday, at the
An alleged Iranian drug trafficker with ties to Tehran\'s intelligence services has been charged in the United States with recruiting a member of the Hells Angels in a plot to murder an Iranian defector who had previously fled to Maryland. A Grand Jury Indictment against Naji Sharifi Zindashti, 49, was unsealed on Monday, at the |
★★★★ | |||
| 2024-01-29 17:55:19 | L'agence de prisonniers de guerre de l'Ukraine \\ a été frappée par Cyberattack Ukraine\\'s prisoners of war agency hit by cyberattack (lien direct) |
 L'agence d'État ukrainienne supervisant le traitement des prisonniers de guerre a déclaré Attaque du déni de service (DDOS) au cours du week-end.Le siège de coordination du pays pour le traitement des prisonniers de guerre travaille avec des familles de militaires qui ont été capturés ou
L'agence d'État ukrainienne supervisant le traitement des prisonniers de guerre a déclaré Attaque du déni de service (DDOS) au cours du week-end.Le siège de coordination du pays pour le traitement des prisonniers de guerre travaille avec des familles de militaires qui ont été capturés ou
 The Ukrainian state agency overseeing the treatment of prisoners of war said on Monday that it had restored access to its website after being hit by a distributed denial-of-service (DDoS) attack over the weekend. The country\'s Coordination Headquarters for the Treatment of Prisoners of War works with families of military personnel who were captured or
The Ukrainian state agency overseeing the treatment of prisoners of war said on Monday that it had restored access to its website after being hit by a distributed denial-of-service (DDoS) attack over the weekend. The country\'s Coordination Headquarters for the Treatment of Prisoners of War works with families of military personnel who were captured or |
★★★ | |||
| 2024-01-29 13:12:01 | Les législateurs britanniques remettent en question la légalité de la technologie de reconnaissance faciale en direct British lawmakers question legality of live facial recognition technology (lien direct) |
 Les membres de la Chambre des Lords ont écrit au secrétaire à l'Intérieur du Royaume-Uni avertissant que l'utilisation de la technologie de reconnaissance faciale en direct par la police n'a pas de base juridique, et appelant à la législation sur la question à voter par le Parlement.Logiciel de reconnaissance faciale en direct (LFR), qui fonctionne en comparant les images faciales de
Les membres de la Chambre des Lords ont écrit au secrétaire à l'Intérieur du Royaume-Uni avertissant que l'utilisation de la technologie de reconnaissance faciale en direct par la police n'a pas de base juridique, et appelant à la législation sur la question à voter par le Parlement.Logiciel de reconnaissance faciale en direct (LFR), qui fonctionne en comparant les images faciales de
 Members of the House of Lords have written to the United Kingdom\'s home secretary warning that the use of live facial recognition technology by police lacks a legal basis, and calling for legislation on the matter to be voted on by Parliament. Live facial recognition (LFR) software, which works by comparing the facial images of
Members of the House of Lords have written to the United Kingdom\'s home secretary warning that the use of live facial recognition technology by police lacks a legal basis, and calling for legislation on the matter to be voted on by Parliament. Live facial recognition (LFR) software, which works by comparing the facial images of |
Legislation | ★★★ | ||
| 2024-01-26 22:11:10 | Populaire Washington, DC Latino Theatre à nouveau à nouveau après le piratage de comptes vidés Popular Washington, DC Latino theater whole again after hack emptied accounts (lien direct) |
 Un théâtre populaire de Washington, D.C.Le Gala Hispanic Theatre - un centre national pour les arts du spectacle latino - a été piraté le 11 janvier et tout son compte bancaire a été vidé en un éclair.Exécutif
Un théâtre populaire de Washington, D.C.Le Gala Hispanic Theatre - un centre national pour les arts du spectacle latino - a été piraté le 11 janvier et tout son compte bancaire a été vidé en un éclair.Exécutif
 A popular theater in Washington, D.C. had more than $250,000 in stolen funds returned after hackers managed to siphon the money out of their bank account. The GALA Hispanic Theatre - a national center for Latino performing arts - was hacked on January 11 and its entire bank account was emptied in a flash. Executive
A popular theater in Washington, D.C. had more than $250,000 in stolen funds returned after hackers managed to siphon the money out of their bank account. The GALA Hispanic Theatre - a national center for Latino performing arts - was hacked on January 11 and its entire bank account was emptied in a flash. Executive |
Hack | ★★ | ||
| 2024-01-26 19:49:23 | Vol de données affligeant les écoles K-12 après les attaques de la saison des fêtes Data theft plaguing K-12 schools after holiday season attacks (lien direct) |
 Les écoles des États-Unis restent des objectifs fertiles pour les pirates, avec une liste d'entités K-12 en lutte contre les cyberattaques et les vols de données après la saison des fêtes.Depuis le début de l'année, une poignée d'écoles ont signalé des violations de données, notamment Butte School District au Montana, Edmonds School District à Washington, [Fullerton Joint Union High School
Les écoles des États-Unis restent des objectifs fertiles pour les pirates, avec une liste d'entités K-12 en lutte contre les cyberattaques et les vols de données après la saison des fêtes.Depuis le début de l'année, une poignée d'écoles ont signalé des violations de données, notamment Butte School District au Montana, Edmonds School District à Washington, [Fullerton Joint Union High School
 Schools across the U.S. remain fertile targets for hackers, with a slate of K-12 entities contending with cyberattacks and data thefts following the holiday season. Since the start of the year, a handful of schools have reported data breaches including Butte School District in Montana, Edmonds School District in Washington, [Fullerton Joint Union High School
Schools across the U.S. remain fertile targets for hackers, with a slate of K-12 entities contending with cyberattacks and data thefts following the holiday season. Since the start of the year, a handful of schools have reported data breaches including Butte School District in Montana, Edmonds School District in Washington, [Fullerton Joint Union High School |
★★ | |||
| 2024-01-26 19:45:15 | Ukraine \\'s Security Service détient le membre du Russe \\ 'Cyber Army \\' Ukraine\\'s security service detains member of Russian \\'Cyber Army\\' (lien direct) |
 Le service de sécurité de l'Ukraine \\, le SBU, a déclaré Cyber Armée de Russie.Le suspect, un spécialiste de la technologie de la ville ukrainienne du nord-est de Kharkiv, a été recruté par le renseignement russe via une chaîne de pirate sur le Telegram de l'application de messagerie, a déclaré le SBU.La loi de l'Ukraine \\
Le service de sécurité de l'Ukraine \\, le SBU, a déclaré Cyber Armée de Russie.Le suspect, un spécialiste de la technologie de la ville ukrainienne du nord-est de Kharkiv, a été recruté par le renseignement russe via une chaîne de pirate sur le Telegram de l'application de messagerie, a déclaré le SBU.La loi de l'Ukraine \\
 Ukraine\'s security service, the SBU, said it had detained a suspected member of the pro-Kremlin hacker group known as the Cyber Army of Russia. The suspect, a tech specialist from the northeastern Ukrainian city of Kharkiv, was recruited by Russian intelligence through a hacker channel on the messaging app Telegram, the SBU said. Ukraine\'s law
Ukraine\'s security service, the SBU, said it had detained a suspected member of the pro-Kremlin hacker group known as the Cyber Army of Russia. The suspect, a tech specialist from the northeastern Ukrainian city of Kharkiv, was recruited by Russian intelligence through a hacker channel on the messaging app Telegram, the SBU said. Ukraine\'s law |
★★★ | |||
| 2024-01-26 19:35:38 | Meta ajoute de nouvelles protections de l'enfant avant le témoignage du Congrès de Zuckerberg \\ Meta adds new child protections ahead of Zuckerberg\\'s congressional testimony (lien direct) |
 Days avant le méta-PDG de Meta, Mark Zuckerberg \\, avant le Congrès, la société a annoncé de nouvelles fonctionnalités conçues pour mieux protéger les enfants en utilisant ses plateformes Instagram et Facebook en recevant des avancées sexuelles indésirables et en rencontrant un contenu inapproprié.Zuckerberg, ainsi que les PDG de X (anciennement connu sous le nom de Twitter), Tiktok, Snap et Discord, ont été assignés
Days avant le méta-PDG de Meta, Mark Zuckerberg \\, avant le Congrès, la société a annoncé de nouvelles fonctionnalités conçues pour mieux protéger les enfants en utilisant ses plateformes Instagram et Facebook en recevant des avancées sexuelles indésirables et en rencontrant un contenu inapproprié.Zuckerberg, ainsi que les PDG de X (anciennement connu sous le nom de Twitter), Tiktok, Snap et Discord, ont été assignés
 Days ahead of Meta CEO Mark Zuckerberg\'s appearance before Congress, the company has announced new features designed to better protect children using its Instagram and Facebook platforms from receiving unwanted sexual advances and encountering inappropriate content. Zuckerberg, along with the CEOs of X (formerly known as Twitter), TikTok, Snap and Discord, have been subpoenaed to
Days ahead of Meta CEO Mark Zuckerberg\'s appearance before Congress, the company has announced new features designed to better protect children using its Instagram and Facebook platforms from receiving unwanted sexual advances and encountering inappropriate content. Zuckerberg, along with the CEOs of X (formerly known as Twitter), TikTok, Snap and Discord, have been subpoenaed to |
★★ | |||
| 2024-01-26 18:03:00 | L'avocat est condamné à 10 ans pour le blanchiment de l'escroquerie Onecoin Proceds Lawyer gets 10-year sentence for laundering OneCoin scam proceeds (lien direct) |
 Un avocat reconnu coupable d'avoir blanchi plus de 400 millions de dollars de produit de l'arnaque frauduleux de la crypto-monnaie Onecoin a été condamné jeudi à 10 ans de prison fédérale américaine.Mark Scott a été condamné en 2019 pour avoir participé à «l'un des plus grands régimes de fraude jamais perpétrés», a déclaré le ministère de la Justice - une con qui a trompé
Un avocat reconnu coupable d'avoir blanchi plus de 400 millions de dollars de produit de l'arnaque frauduleux de la crypto-monnaie Onecoin a été condamné jeudi à 10 ans de prison fédérale américaine.Mark Scott a été condamné en 2019 pour avoir participé à «l'un des plus grands régimes de fraude jamais perpétrés», a déclaré le ministère de la Justice - une con qui a trompé
 A lawyer convicted of laundering more than $400 million of proceeds from the fraudulent OneCoin cryptocurrency scam was sentenced to 10 years in U.S. federal prison on Thursday. Mark Scott was convicted in 2019 of participating in “one of the largest fraud schemes ever perpetrated,” the Department of Justice said - a con that tricked
A lawyer convicted of laundering more than $400 million of proceeds from the fraudulent OneCoin cryptocurrency scam was sentenced to 10 years in U.S. federal prison on Thursday. Mark Scott was convicted in 2019 of participating in “one of the largest fraud schemes ever perpetrated,” the Department of Justice said - a con that tricked |
Legislation | ★★ | ||
| 2024-01-26 17:02:23 | Microsoft dit que les pirates russes ont utilisé une tactique précédemment identifiée pour infraction Microsoft says Russian hackers used previously-identified tactic to breach senior exec emails (lien direct) |
 Les pirates russes ont abusé d'un outil d'authentification populaire pour accéder aux comptes de messagerie des cadres supérieurs de Microsoft, selon une nouvelle déclaration du géant de la technologie.Microsoft a été serré à propos d'un incident - annoncé vendredi après-midi La semaine dernière - la semaine dernière - la semaine dernière -Le fait qu'ils aient dit impliquant le compromis de plusieurs mois des comptes de messagerie d'entreprise.
Les pirates russes ont abusé d'un outil d'authentification populaire pour accéder aux comptes de messagerie des cadres supérieurs de Microsoft, selon une nouvelle déclaration du géant de la technologie.Microsoft a été serré à propos d'un incident - annoncé vendredi après-midi La semaine dernière - la semaine dernière - la semaine dernière -Le fait qu'ils aient dit impliquant le compromis de plusieurs mois des comptes de messagerie d'entreprise.
 Russian hackers abused a popular authentication tool to gain access to the email accounts of senior executives at Microsoft, according to a new statement from the tech giant. Microsoft has been tightlipped about an incident - announced late on Friday afternoon last week - that they said involved the months-long compromise of corporate email accounts.
Russian hackers abused a popular authentication tool to gain access to the email accounts of senior executives at Microsoft, according to a new statement from the tech giant. Microsoft has been tightlipped about an incident - announced late on Friday afternoon last week - that they said involved the months-long compromise of corporate email accounts. |
Tool | ★★ | ||
| 2024-01-26 00:58:13 | Achats de la NSA d'Américains \\ 'Les données personnelles des courtiers sont illégales, dit le sénateur NSA purchases of Americans\\' personal data from brokers is illegal, senator says (lien direct) |
 Le sénateur Ron Wyden (D-Ore.) A affirmait jeudi que l'achat de l'agence de sécurité nationale \\ (NSA) des Américains \\ 'Internet Records de Data Brokers est illégal sur la base d'une récente décision de la Federal Trade Commission, Wyden a publié des documents montrantDes hauts responsables de la défense reconnaissant qu'ils achètent des données commerciales, y compris les métadonnées Internet et les informations associées aux téléphones situés aux États-Unis
Le sénateur Ron Wyden (D-Ore.) A affirmait jeudi que l'achat de l'agence de sécurité nationale \\ (NSA) des Américains \\ 'Internet Records de Data Brokers est illégal sur la base d'une récente décision de la Federal Trade Commission, Wyden a publié des documents montrantDes hauts responsables de la défense reconnaissant qu'ils achètent des données commerciales, y compris les métadonnées Internet et les informations associées aux téléphones situés aux États-Unis
 Sen. Ron Wyden (D-Ore.) on Thursday asserted that National Security Agency\'s (NSA) purchase of Americans\' internet records from data brokers is illegal based on a recent Federal Trade Commission ruling, Wyden released documents showing senior defense officials acknowledging they buy commercial data, including internet metadata and information associated with phones located inside the U.S. The
Sen. Ron Wyden (D-Ore.) on Thursday asserted that National Security Agency\'s (NSA) purchase of Americans\' internet records from data brokers is illegal based on a recent Federal Trade Commission ruling, Wyden released documents showing senior defense officials acknowledging they buy commercial data, including internet metadata and information associated with phones located inside the U.S. The |
Commercial | ★★★ | ||
| 2024-01-25 21:39:20 | Kansas State, Clackamas Community College répond aux cyberattaques Kansas State, Clackamas Community College respond to cyberattacks (lien direct) |
 La Kansas State University et un collège communautaire populaire de l'Oregon sont en train de se remettre de cyberattaques qui ont éliminé les systèmes du campus pendant des jours après le retour des étudiants de Noël.Kansas State University - desservant près de 20 000 étudiants de son siège social à Manhattan, Kansas - a initialement annoncé une perturbation du réseau le 16 janvier
La Kansas State University et un collège communautaire populaire de l'Oregon sont en train de se remettre de cyberattaques qui ont éliminé les systèmes du campus pendant des jours après le retour des étudiants de Noël.Kansas State University - desservant près de 20 000 étudiants de son siège social à Manhattan, Kansas - a initialement annoncé une perturbation du réseau le 16 janvier
 Kansas State University and a popular community college in Oregon are in the process of recovering from cyberattacks that knocked out campus systems for days after students returned from the Christmas holiday break. Kansas State University - serving nearly 20,000 students from its headquarters in Manhattan, Kansas - initially announced a network disruption January 16
Kansas State University and a popular community college in Oregon are in the process of recovering from cyberattacks that knocked out campus systems for days after students returned from the Christmas holiday break. Kansas State University - serving nearly 20,000 students from its headquarters in Manhattan, Kansas - initially announced a network disruption January 16 |
★★ | |||
| 2024-01-25 20:49:47 | Le développeur russe de Trickbot Malware condamné à cinq ans de prison Russian developer of Trickbot malware sentenced to five years in prison (lien direct) |
 Un développeur russe de Trickbot Malware a été condamné à cinq ans et quatre mois de prison, le département américain de la Justice a déclaré jeudi.Selon des documents judiciaires, Vladimir Dunaev, 40 ans, a été impliqué dans le développement et le déploiement du logiciel malveillant pour lancer des cyberattaques contre les hôpitaux, les écoles et les entreprises américains.Dunaev a été extradé du sud
Un développeur russe de Trickbot Malware a été condamné à cinq ans et quatre mois de prison, le département américain de la Justice a déclaré jeudi.Selon des documents judiciaires, Vladimir Dunaev, 40 ans, a été impliqué dans le développement et le déploiement du logiciel malveillant pour lancer des cyberattaques contre les hôpitaux, les écoles et les entreprises américains.Dunaev a été extradé du sud
 A Russian developer of Trickbot malware has been sentenced to five years and four months in prison, the U.S. Department of Justice said on Thursday. According to court documents, 40-year-old Vladimir Dunaev was involved in developing and deploying the malicious software to launch cyberattacks against American hospitals, schools and businesses. Dunaev was extradited from South
A Russian developer of Trickbot malware has been sentenced to five years and four months in prison, the U.S. Department of Justice said on Thursday. According to court documents, 40-year-old Vladimir Dunaev was involved in developing and deploying the malicious software to launch cyberattacks against American hospitals, schools and businesses. Dunaev was extradited from South |
Malware Legislation | ★★★ | ||
| 2024-01-25 18:20:28 | Russie Social Media Putage Probablement causée par le régulateur d'État sur Internet Russia social media outage likely caused by state internet regulator (lien direct) |
 La Russie a connu une autre grande panne de médias sociaux cette semaine, avec des applications de messagerie comme Telegram, WhatsApp et Viber qui baissent pour des milliers de citoyens.Selon un site Web de surveillance Internet , les applications de messagerie étaient pour la plupart indisponibles mardi dans la ville sibérienne de Novosibirsk et l'extrême-orientalRégions de Khabarovsk Krai et Sakha.Résidents
La Russie a connu une autre grande panne de médias sociaux cette semaine, avec des applications de messagerie comme Telegram, WhatsApp et Viber qui baissent pour des milliers de citoyens.Selon un site Web de surveillance Internet , les applications de messagerie étaient pour la plupart indisponibles mardi dans la ville sibérienne de Novosibirsk et l'extrême-orientalRégions de Khabarovsk Krai et Sakha.Résidents
 Russia experienced another major social media outage this week, with messaging apps like Telegram, WhatsApp and Viber going down for thousands of citizens. According to a Russian internet monitoring website, messaging apps were mostly unavailable on Tuesday in the Siberian city of Novosibirsk and the far eastern regions of Khabarovsk Krai and Sakha. Residents of
Russia experienced another major social media outage this week, with messaging apps like Telegram, WhatsApp and Viber going down for thousands of citizens. According to a Russian internet monitoring website, messaging apps were mostly unavailable on Tuesday in the Siberian city of Novosibirsk and the far eastern regions of Khabarovsk Krai and Sakha. Residents of |
★★★ | |||
| 2024-01-25 18:19:47 | Un nouveau projet de loi cherche à consolider la nourriture américaine, les secteurs de l'agriculture New bill looks to shore up US food, agriculture sectors (lien direct) |
 Un duo bipartite des sénateurs américains a présenté jeudi une législation pour stimuler les défenses numériques protégeant les secteurs de l'agriculture et des infrastructures critiques. The Farm and Food Cybersecurity Act De Sens. Kirsten Gillibrand (D-ny) et Tom et Tom et TomLe coton (R-AR) obligerait le secrétaire à l'Agriculture à mener une étude tous les deux ans sur les cyber-menaces
Un duo bipartite des sénateurs américains a présenté jeudi une législation pour stimuler les défenses numériques protégeant les secteurs de l'agriculture et des infrastructures critiques. The Farm and Food Cybersecurity Act De Sens. Kirsten Gillibrand (D-ny) et Tom et Tom et TomLe coton (R-AR) obligerait le secrétaire à l'Agriculture à mener une étude tous les deux ans sur les cyber-menaces
 A bipartisan duo of U.S. senators on Thursday introduced legislation to boost the digital defenses protecting the agriculture and food critical infrastructure sectors. The Farm and Food Cybersecurity Act from Sens. Kirsten Gillibrand (D-NY) and Tom Cotton (R-AR) would require the Secretary of Agriculture to conduct a study every two years on the cyber threats
A bipartisan duo of U.S. senators on Thursday introduced legislation to boost the digital defenses protecting the agriculture and food critical infrastructure sectors. The Farm and Food Cybersecurity Act from Sens. Kirsten Gillibrand (D-NY) and Tom Cotton (R-AR) would require the Secretary of Agriculture to conduct a study every two years on the cyber threats |
Studies Legislation | ★★★ | ||
| 2024-01-25 17:28:00 | Les gouvernements locaux du Colorado, de la Pennsylvanie et du Missouri traitant des ransomwares Local governments in Colorado, Pennsylvania and Missouri dealing with ransomware (lien direct) |
 Plusieurs gouvernements locaux traitent des cyberattaques, notamment des incidents de ransomwares, cette semaine, provoquant des pannes et des problèmes pour les hôpitaux du comté, les bibliothèques et autres services locaux.Bucks County, Pennsylvanie - abritant près de 650 000 personnes - a déclaré mercredi qu'il était toujours aux prises avec un incident de cybersécurité qui avait éliminé les communications d'urgence \\ 'du département \\.
Plusieurs gouvernements locaux traitent des cyberattaques, notamment des incidents de ransomwares, cette semaine, provoquant des pannes et des problèmes pour les hôpitaux du comté, les bibliothèques et autres services locaux.Bucks County, Pennsylvanie - abritant près de 650 000 personnes - a déclaré mercredi qu'il était toujours aux prises avec un incident de cybersécurité qui avait éliminé les communications d'urgence \\ 'du département \\.
 Multiple local governments are dealing with cyberattacks, including ransomware incidents, this week, causing outages and problems for county hospitals, libraries and other local services. Bucks County, Pennsylvania - home to nearly 650,000 people - said on Wednesday that it is still grappling with a cybersecurity incident that has knocked out the Emergency Communications\' Department\'s computer-aided
Multiple local governments are dealing with cyberattacks, including ransomware incidents, this week, causing outages and problems for county hospitals, libraries and other local services. Bucks County, Pennsylvania - home to nearly 650,000 people - said on Wednesday that it is still grappling with a cybersecurity incident that has knocked out the Emergency Communications\' Department\'s computer-aided |
Ransomware | ★★★ | ||
| 2024-01-25 16:32:42 | Outil Amazon à Sunset qui permettait aux forces de la loi d'obtenir des images à partir de sonnettes d'anneau Amazon to sunset tool that let law enforcement obtain footage from Ring doorbells (lien direct) |
 Amazon a annoncé mercredi qu'ils rendront plus difficile pour les services de police de demander des images générées par des sonnettes vidéo et des caméras de surveillance des clients.La pratique était depuis longtemps sous le feu des groupes de libertés civiles et Certains politiciens .Eric Kuhn, qui dirige la plate-forme de voisins de la société, a déclaré la fonction de «demande d'assistance» controversée de Ring \\
Amazon a annoncé mercredi qu'ils rendront plus difficile pour les services de police de demander des images générées par des sonnettes vidéo et des caméras de surveillance des clients.La pratique était depuis longtemps sous le feu des groupes de libertés civiles et Certains politiciens .Eric Kuhn, qui dirige la plate-forme de voisins de la société, a déclaré la fonction de «demande d'assistance» controversée de Ring \\
 Amazon announced Wednesday that they will make it harder for police departments to ask for footage generated from customers\' Ring video doorbells and surveillance cameras. The practice had long been under fire from civil liberties groups and some politicians. Eric Kuhn, who helms the company\'s Neighbors Platform, said Ring\'s controversial “Request for Assistance” (RFA) function
Amazon announced Wednesday that they will make it harder for police departments to ask for footage generated from customers\' Ring video doorbells and surveillance cameras. The practice had long been under fire from civil liberties groups and some politicians. Eric Kuhn, who helms the company\'s Neighbors Platform, said Ring\'s controversial “Request for Assistance” (RFA) function |
Tool | ★★★ | ||
| 2024-01-25 13:40:00 | Géant de l'énergie ukrainien, service postal, agences de transport frappées par des cyberattaques Ukrainian energy giant, postal service, transportation agencies hit by cyberattacks (lien direct) |
 KYIV - Plusieurs sociétés d'infrastructures critiques ukrainiennes appartenant à l'État ont signalé jeudi les cyberattaques sur leurs systèmes.Parmi les victimes, il y a la plus grande entreprise de pétrole et de gaz appartenant à l'État d'Ukraine, naftogaz .Selon sa déclaration, les pirates ont attaqué un centre de données.Au moment de la rédaction du temps de rédaction, le site Web et les centres d'appels de Naftogaz ne sont pas opérationnels.L'agence de cybersécurité de l'Ukraine \\ a raconté
KYIV - Plusieurs sociétés d'infrastructures critiques ukrainiennes appartenant à l'État ont signalé jeudi les cyberattaques sur leurs systèmes.Parmi les victimes, il y a la plus grande entreprise de pétrole et de gaz appartenant à l'État d'Ukraine, naftogaz .Selon sa déclaration, les pirates ont attaqué un centre de données.Au moment de la rédaction du temps de rédaction, le site Web et les centres d'appels de Naftogaz ne sont pas opérationnels.L'agence de cybersécurité de l'Ukraine \\ a raconté
 KYIV - Several state-owned Ukrainian critical infrastructure companies reported cyberattacks on their systems on Thursday. Among the victims is Ukraine\'s largest state-owned oil and gas company, Naftogaz. According to its statement, hackers attacked a data center. As of the time of writing, the Naftogaz website and call centers are not operational. Ukraine\'s cybersecurity agency told
KYIV - Several state-owned Ukrainian critical infrastructure companies reported cyberattacks on their systems on Thursday. Among the victims is Ukraine\'s largest state-owned oil and gas company, Naftogaz. According to its statement, hackers attacked a data center. As of the time of writing, the Naftogaz website and call centers are not operational. Ukraine\'s cybersecurity agency told |
★★★ | |||
| 2024-01-24 22:15:00 | Hewlett Packard Enterprise dit à SEC qu'elle a été violée par la Russie \\ 'S \\' Cozy Bear \\ 'Hackers Hewlett Packard Enterprise tells SEC it was breached by Russia\\'s \\'Cozy Bear\\' hackers (lien direct) |
 Des pirates avec des liens présumés avec le gouvernement russe ont eu accès au fabricant de technologies Hewlett Packard Enterprise Co. \'S (HPE) Environnement de messagerie basé sur le cloud, a annoncé mercredi la société.Dans un Déposant avec des régulateurs SEC le mercredi après-midi, HPE a déclaré qu'il avait été informé le 12 décembre que des pirates se connectaient à confort
Des pirates avec des liens présumés avec le gouvernement russe ont eu accès au fabricant de technologies Hewlett Packard Enterprise Co. \'S (HPE) Environnement de messagerie basé sur le cloud, a annoncé mercredi la société.Dans un Déposant avec des régulateurs SEC le mercredi après-midi, HPE a déclaré qu'il avait été informé le 12 décembre que des pirates se connectaient à confort
 Hackers with suspected ties to the Russian government gained access to the technology manufacturer Hewlett Packard Enterprise Co.\'s (HPE) cloud-based email environment, the company said Wednesday. In a filing with SEC regulators on Wednesday afternoon, HPE said it was notified on December 12 that hackers connected to Cozy Bear, also known as Midnight Blizzard, had
Hackers with suspected ties to the Russian government gained access to the technology manufacturer Hewlett Packard Enterprise Co.\'s (HPE) cloud-based email environment, the company said Wednesday. In a filing with SEC regulators on Wednesday afternoon, HPE said it was notified on December 12 that hackers connected to Cozy Bear, also known as Midnight Blizzard, had |
APT 29 | ★★★ | ||
| 2024-01-24 21:45:00 | La société de technologie financière équilibre dit que la reprise après la cyberattaque \\ 'peut prendre plusieurs jours \\' Financial tech firm EquiLend says recovery after cyberattack \\'may take several days\\' (lien direct) |
 La société de technologie financière Equlend a été frappée par une cyberattaque cette semaine qui a forcé plusieurs de ses systèmes hors ligne et peut nécessiter plusieurs jours pour se remettre.La société, fondée en 2000 par plusieurs des plus grandes sociétés financières du monde \\, a réalisé des nouvelles futures vers une déclaration disant qu'elle a identifié un problème technique sur
La société de technologie financière Equlend a été frappée par une cyberattaque cette semaine qui a forcé plusieurs de ses systèmes hors ligne et peut nécessiter plusieurs jours pour se remettre.La société, fondée en 2000 par plusieurs des plus grandes sociétés financières du monde \\, a réalisé des nouvelles futures vers une déclaration disant qu'elle a identifié un problème technique sur
 Financial technology firm EquiLend was hit with a cyberattack this week which forced several of its systems offline and may require several days to recover from. The company, which was founded in 2000 by several of the world\'s largest financial firms, directed Recorded Future News to a statement saying it identified a technical issue on
Financial technology firm EquiLend was hit with a cyberattack this week which forced several of its systems offline and may require several days to recover from. The company, which was founded in 2000 by several of the world\'s largest financial firms, directed Recorded Future News to a statement saying it identified a technical issue on |
Technical | ★★★ | ||
| 2024-01-24 21:15:00 | Les cybercriminels ont volé 1,7 milliard de dollars aux fonds cryptographiques en 2023 alors que les attaques prolifèrent Cybercriminals stole $1.7 billion from crypto funds in 2023 as attacks proliferated (lien direct) |
 Les pirates ont siphoné 1,7 milliard de dollars de plates-formes de crypto-monnaie en 2023 - en baisse d'environ 2 milliards de dollars sur un ensemble record de l'année précédente, selon les données recueillies par la société de recherche blockchain Chainalysis.Malgré la baisse de l'argent total perdu, le nombre d'incidents individuels ciblant ces plates-formes est passée de 219 en 2022 à 231
Les pirates ont siphoné 1,7 milliard de dollars de plates-formes de crypto-monnaie en 2023 - en baisse d'environ 2 milliards de dollars sur un ensemble record de l'année précédente, selon les données recueillies par la société de recherche blockchain Chainalysis.Malgré la baisse de l'argent total perdu, le nombre d'incidents individuels ciblant ces plates-formes est passée de 219 en 2022 à 231
 Hackers siphoned $1.7 billion from cryptocurrency platforms in 2023 - down by about $2 billion from a record high set the previous year, according to data collected by blockchain research firm Chainalysis. Despite the drop in total money lost, the number of individual incidents targeting these platforms grew from 219 in 2022 to 231 in
Hackers siphoned $1.7 billion from cryptocurrency platforms in 2023 - down by about $2 billion from a record high set the previous year, according to data collected by blockchain research firm Chainalysis. Despite the drop in total money lost, the number of individual incidents targeting these platforms grew from 219 in 2022 to 231 in |
★★★ | |||
| 2024-01-24 19:38:00 | Qui paie et pourquoi: un chercheur examine l'état d'esprit de la victime de la victime de ransomware Who pays, and why: A researcher examines the ransomware victim\\'s mindset (lien direct) |
 Qu'est-ce qui rend une victime de ransomware plus susceptible de payer qu'une autre?C'est ce qu'un chercheur néerlandais a entrepris de trouver, analysant les données de la police nationale et de l'incident sur des centaines de cas au cours des quatre dernières années.Les entreprises qui travaillent avec une société de réponse aux incidents tierces sont les plus disposées à payer leurs extorqueurs, il
Qu'est-ce qui rend une victime de ransomware plus susceptible de payer qu'une autre?C'est ce qu'un chercheur néerlandais a entrepris de trouver, analysant les données de la police nationale et de l'incident sur des centaines de cas au cours des quatre dernières années.Les entreprises qui travaillent avec une société de réponse aux incidents tierces sont les plus disposées à payer leurs extorqueurs, il
 What makes one ransomware victim more likely to pay up than another? That\'s what one Dutch researcher set out to find, analyzing national police and incident response data on hundreds of cases over the last four years. Companies that work with a third-party incident response firm are the most willing to pay their extortionists, he
What makes one ransomware victim more likely to pay up than another? That\'s what one Dutch researcher set out to find, analyzing national police and incident response data on hundreds of cases over the last four years. Companies that work with a third-party incident response firm are the most willing to pay their extortionists, he |
Ransomware | ★★★ | ||
| 2024-01-24 17:15:00 | \\ 'Facture de sécurité significative \\' Trouvé dans Google Software Container System \\'Significant security loophole\\' found in Google software container system (lien direct) |
 Google a fixé une échappatoire affectant un service cloud important après que les chercheurs ont découvert de nombreuses organisations - y compris une entreprise cotée en bourse - avaient des systèmes vulnérables aux infractions à la sécurité à l'échelle du système à la suite du problème.Le problème a affecté Google Kubernetes Engine (GKE), un système utilisé pour déployer, mettre à l'échelle et gérer la façon dont les applications sont «conteneurisées».Grenier
Google a fixé une échappatoire affectant un service cloud important après que les chercheurs ont découvert de nombreuses organisations - y compris une entreprise cotée en bourse - avaient des systèmes vulnérables aux infractions à la sécurité à l'échelle du système à la suite du problème.Le problème a affecté Google Kubernetes Engine (GKE), un système utilisé pour déployer, mettre à l'échelle et gérer la façon dont les applications sont «conteneurisées».Grenier
 Google has fixed a loophole affecting an important cloud service after researchers discovered numerous organizations - including a publicly traded company - had systems vulnerable to systemwide security breaches as a result of the issue. The issue affected Google Kubernetes Engine (GKE), a system used to deploy, scale and manage how applications are “containerized.” GKE
Google has fixed a loophole affecting an important cloud service after researchers discovered numerous organizations - including a publicly traded company - had systems vulnerable to systemwide security breaches as a result of the issue. The issue affected Google Kubernetes Engine (GKE), a system used to deploy, scale and manage how applications are “containerized.” GKE |
Cloud | ★★★ |
To see everything:
Our RSS (filtrered)
