What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2019-07-18 17:03:01 | Over 800,000 Systems Still Vulnerable to BlueKeep Attacks (lien direct) | Users and organizations continue to patch the Windows vulnerability tracked as BlueKeep and CVE-2019-0708, but over 800,000 systems are still exposed to attacks. | Vulnerability | Wannacry | ||
| 2019-05-15 06:06:05 | Microsoft Patches RDS Vulnerability Allowing WannaCry-Like Attacks (lien direct) | Microsoft's Patch Tuesday updates for May 2019 address nearly 80 vulnerabilities, including a zero-day and a flaw that can be exploited by malware to spread similar to the way the notorious WannaCry did back in 2017. | Malware Vulnerability | Wannacry | ||
| 2019-04-09 15:36:04 | Get Ready for the First Wave of AI Malware (lien direct) | While viruses and malware have stubbornly stayed as a top-10 “things I lose sleep over as a CISO,” the overall threat has been steadily declining for a decade. Unfortunately, WannaCry, NotPetya, and an entourage of related self-propagating ransomware abruptly propelled malware back up the list and highlighted the risks brought by modern inter-networked business systems and the explosive growth of unmanaged devices. | Ransomware Malware Threat | NotPetya Wannacry | ||
| 2018-08-06 11:29:05 | Flaw in Popular Framework Exposes ICS Devices to Attack (lien direct) |
Type:
Story
Image:
 Link:
Chip Giant TSMC Says WannaCry Ransomware Behind Production Halt
Chip Giant TSMC Says WannaCry Ransomware Behind Production Halt
Link:
Chip Giant TSMC Says WannaCry Ransomware Behind Production Halt
Chip Giant TSMC Says WannaCry Ransomware Behind Production Halt
|
Ransomware | Wannacry | ||
| 2018-08-06 11:08:00 | Chip Giant TSMC Says WannaCry Behind Production Halt (lien direct) |  Image Source: Taiwan Semiconductor Manufacturing Co., Ltd.
Image Source: Taiwan Semiconductor Manufacturing Co., Ltd.
|
Wannacry | |||
| 2018-05-11 17:41:04 | One Year After WannaCry Outbreak, EternalBlue Exploit Still a Threat (lien direct) | One year after the WannaCry ransomware outbreak, the NSA-linked exploit used for propagation is still threatening unpatched and unprotected systems, security researchers say. | Wannacry | |||
| 2018-05-03 16:36:04 | Commodity Ransomware Declines as Corporate Attacks Increase (lien direct) | 2017 was a landmark year for ransomware, with WannaCry and NotPetya grabbing headlines around the world. Ransomware attacks grew by more than 400% over the year, while the number unique families and variants increased by 62%. These statistics, however, disguise an apparent change in the ransomware industry following the summer of 2017. | NotPetya Wannacry | |||
| 2018-04-13 16:10:02 | Illumio, Qualys Partner on Vulnerability-based Micro-Segmentation (lien direct) | Vulnerability management has two major components: discovering vulnerabilities, and mitigating those vulnerabilities. The first component is pointless without the second component. So, for example, Equifax, WannaCry, NotPetya, and many other breaches -- if not most breaches -- are down to a failure to patch, which is really a failure in vulnerability management. | NotPetya Wannacry Equifax | |||
| 2018-03-27 17:04:04 | Statistics Say Don\'t Pay the Ransom; but Cleanup and Recovery Remains Costly (lien direct) | Businesses have lost faith in the ability of traditional anti-virus products to detect and prevent ransomware. Fifty-three percent of U.S companies infected by ransomware in 2017 blamed legacy AV for failing to detect the ransomware. Ninety six percent of those are now confident that they can prevent future attacks, and 68% say this is because they have replaced legacy AV with next-gen endpoint protection. Thes details come from a February 2018 survey undertaken by Vanson Bourne for SentinelOne, a next-gen provider, allowing SentinelOne to claim, "This distrust in legacy AV further confirms the required shift to next-gen endpoint protection in defending against today's most prominent information security threats." This is a fair statement, but care should be taken to not automatically confuse 'legacy AV' with all traditional suppliers -- many can also now be called next-gen providers with their own flavors of AI-assisted malware detection. SentinelOne's Global Ransomware Report 2018 (PDF) questioned 500 security and risk professionals (200 in the U.S., and 100 in each of France, Germany and the UK) employed in a range of verticals and different company sizes. The result provides evidence that paying a ransom is not necessarily a solution to ransomware. Forty-five percent of U.S. companies infected with ransomware paid at least one ransom, but only 26% had their files unlocked. Furthermore, 73% of those firms that paid the ransom were targeted at least once again. Noticeably, while defending against ransomware is a security function, responding to it is a business function: 44% of companies that paid up did so without the involvement or sanction of the IT/security teams. The attackers appear to have concluded that U.S. firms are the more likely to pay a ransom, and more likely to pay a higher ransom. While the global average ransom is $49,060, the average paid by U.S. companies was $57,088. "If the cost of paying the ransomware is less than the lost productivity caused by downtime from the attack, they tend to pay," SentinelOne's director of product management, Migo Kedem, told SecurityWeek. "This is not good news, as it means the economics behind ransomware campaigns still make sense, so attacks will continue." This is in stark contrast to the UK, where the average payment is almost $20,000 lower at $38,500. It is tempting to wonder if this is because UK companies just don't pay ransoms. In 2016, 17% of infected UK firms paid up; now it is just 3%. This may reflect the slightly different approaches in law enforcement advice. While LEAs always say it is best not to pay, the UK's NCSC says flatly, 'do not pay', while the FBI admits that it is ultimately the decision of each company. Paying or not paying, is, however, only a small part of the cost equation; and the UK's Office for National Statistics (ONS) provides useful figures. According the SentinelOne, these figures show that in a 12-month period, the average cost of a ransomware infection to a UK business was £329,976 ($466,727). With 40% of businesses with more than 1000 employees being infected, and 2,625 such organizations in the UK, the total cost of ransomware to UK business in 12 months was £346.4 m | Guideline | Wannacry | ||
| 2018-03-26 13:19:01 | (Déjà vu) Energy Sector Most Impacted by ICS Flaws, Attacks: Study (lien direct) | The energy sector was targeted by cyberattacks more than any other industry, and many of the vulnerabilities disclosed last year impacted products used in this sector, according to a report published on Monday by Kaspersky Lab. The security firm has analyzed a total of 322 flaws disclosed in 2017 by ICS-CERT, vendors and its own researchers, including issues related to industrial control systems (ICS) and general-purpose software and protocols used by industrial organizations. Of the total number of security holes, 178 impact control systems used in the energy sector. Critical manufacturing organizations – this includes manufacturers of primary metals, machinery, electrical equipment, and transportation equipment – were affected by 164 of these vulnerabilities. Other industries hit by a significant number of vulnerabilities are water and wastewater (97), transportation (74), commercial facilities (65), and food and agriculture (61). Many of the vulnerabilities disclosed last year impacted SCADA or HMI components (88), industrial networking devices (66), PLCs (52), and engineering software (52). However, vulnerabilities in general purpose software and protocols have also had an impact on industrial organizations, including the WPA flaws known as KRACK and bugs affecting Intel technology. Learn More at SecurityWeek's ICS Cyber Security Conference As for the types of vulnerabilities, nearly a quarter are web-related and 21 percent are authentication issues. A majority of the flaws have been assigned severity ratings of medium or high, but 60 weaknesses are considered critical based on their CVSS score. Kaspersky pointed out that all vulnerabilities with a CVSS score of 10 are related to authentication and they are all easy to exploit remotely. Kaspersky said 265 of the vulnerabilities can be exploited remotely without authentication and without any special knowledge or skills. It also noted that exploits are publicly available for 17 of the security holes. The company has also shared data on malware infections and other security incidents. In the second half of 2017, Kaspersky security products installed on industrial automation systems detected nearly 18,000 malware variants from roughly 2,400 families. Malware attacks were blocked on almost 38 percent of ICS computers protected by the company, which was slightly less than in the second half of the previous year. Again, the energy sector was the most impacted. According to the security firm, roughly 40 percent of the devices housed by energy organizations were targeted. | Guideline | Wannacry | ★★★★★ | |
| 2018-03-23 19:45:03 | (Déjà vu) Ransomware Hits City of Atlanta (lien direct) | A ransomware attack -- possibly a variant of SamSam -- has affected some customer-facing applications and some internal services at the City of Atlanta. The FBI and incident response teams from Microsoft and Cisco are investigating. The city's police department, water services and airport are not affected. The attack was detected early on Thursday morning. By mid-day the city had posted an outage alert to Twitter. In a press conference held Thursday afternoon, mayor Keisha Bottoms announced that the breach had been ransomware. She gave no details of the ransomware demands, but noticeably declined to say whether the ransom would be payed or refused. Bottoms could not at this stage confirm whether personal details had also been stolen in the same breach, but suggested that customers and staff should monitor their credit accounts. Questions on the viability of data backups and the state of system patches were not clearly answered; but it was stressed that the city had adopted a 'cloud first' policy going forwards specifically to improve security and mitigate against future ransomware attacks. A city employee obtained and sent a screenshot of the ransom note to local radio station 11Alive. The screenshot shows a bitcoin demand for $6,800 per system, or $51,000 to unlock all systems. It is suggested that the ransom note is similar to ones used by the SamSam strain of ransomware. Steve Ragan subsequently tweeted, "1 local, 2 remote sources are telling me City of Atlanta was hit by SamSam. The wallet where the ransom is to be sent (if they pay) has collected $590,000 since Jan 27." SamSam ransomware infected two healthcare organizations earlier this year. SamSam is not normally introduced via a phishing attack, but rather following a pre-existing breach. This could explain the concern over data theft on top of the data encryption. It also raises the question over whether the initial breach was due to a security failure, an unpatched system, or via a third-party supplier. Ransomware is not a new threat, and there are mitigations -- but it continues to cause havoc. Official advice is, wherever at all possible, refuse to pay. The theory is if the attackers cease getting a return on their attacks, they will turn to something easier with a better ROI on their time. This approach simply isn't working. Sometimes payment can be avoided by recovering data from backups | NotPetya Wannacry | |||
| 2018-03-19 12:24:04 | Preventing Business Email Compromise Requires a Human Touch (lien direct) | Human-powered Intelligence Plays a Critical Role in Defending Against Socially Engineered Attacks The FBI's Internet Crime Complaint Center (IC3) declared Business Email Compromise (BEC) the “3.1 billion dollar scam” in 2016, an amount which then grew in the span of one year into a “5 billion dollar scam.” Trend Micro now projects those losses in excess of 9 billion dollars. It's an understatement to say BEC scams and the resulting damages are on the rise. But with cybersecurity spending across all sectors at an all-time high, how is such an unsophisticated threat still costing otherwise well-secured organizations billions of dollars? Unlike the numerous types of attacks that incorporate malware, most BEC scams rely solely on social engineering. In fact, its use of trickery, deception, and psychological manipulation rather than malware is largely why BEC continually inflicts such substantial damages. Since most network defense solutions are designed to detect emails containing malware and malicious links, BEC emails often land directly in users' inboxes. And when this happens, the fate of an attempted BEC scam is in the hands of its recipient. Indeed, BEC underscores why even the most technically sophisticated cyber defenses aren't always a match for low-tech threats. Combating BEC requires more than just advanced technologies and robust perimeter security-it requires humans to understand the threat. Here's why: Human-Powered Intelligence Trumps Automation Since socially engineered attacks such as BEC are designed to exploit human instincts and emotions, human-powered intelligence naturally plays a critical role in defending against these attacks. I've written previously about the limitations of so-called automated intelligence and why human expertise and analysis are irreplaceable. BEC epitomizes this notion. After all, intelligence offerings that rely solely on automation tend to comprise little more than technical indicators of compromise (IoCs). BEC campaigns can have IoCs-but they tend to be less technical and more nuanced, often pertaining to an attacker's syntax, dialect, or other behavioral characteristics. While an IoC for a phishing campaign, for example, might be an email address, an IoC for a BEC campaign could be the phrase an attacker uses to open or sign off the email. Automated intelligence offerings and traditional network security solutions are generally not desig | Guideline | Wannacry | ||
| 2018-03-15 13:03:01 | (Déjà vu) Microsoft Publishes Bi-annual Security Intelligence Report (SIR) (lien direct) | !function(){if("undefined"==typeof powerbiresize){powerbiresize=1;var e=function(){for(var e=document.querySelectorAll("[pbi-resize=powerbi]"),i=0;i | NotPetya Wannacry | |||
| 2017-12-22 13:55:39 | Industry Reactions to U.S. Blaming North Korea for WannaCry (lien direct) | The United States, Canada, Japan, Australia and New Zealand have all officially accused North Korea this week of being behind the WannaCry campaign. They join the United Kingdom, which blamed Pyongyang for the attack back in October. | Wannacry | |||
| 2017-12-21 13:20:46 | North Korea Denies Role in WannaCry Ransomware Attack (lien direct) | North Korea on Thursday denied US accusations it was behind the WannaCry global ransomware cyberattack, saying Washington was demonising it. | Wannacry | |||
| 2017-12-20 06:35:10 | Australia, Canada, Others Blame North Korea for WannaCry Attack (lien direct) | The United States is not the only country to officially accuse North Korea this week of being behind the WannaCry ransomware campaign. Canada, Japan, Australia and New Zealand have also blamed Pyongyang for the attack. | Wannacry | |||
| 2017-12-19 13:05:49 | U.S. Declares North Korea Led Huge WannaCry Cyberattack (lien direct) | The United States officially accused North Korea late Monday of carrying out the massive WannaCry attack that infected some 300,000 computers in 150 countries earlier this year. | Wannacry | |||
| 2017-10-31 11:32:00 | North Korea Denies Involvement in WannaCry Cyberattack (lien direct) | North Korea has slammed Britain for accusing it of being behind a global ransomware attack that hit the National Health Service, calling the allegation a "wicked attempt" to further tighten international sanctions against Pyongyang. | Wannacry | |||
| 2017-08-21 12:51:46 | Code Linked to MalwareTech and Kronos Published in 2009 (lien direct) | A piece of code linked to both the British researcher Marcus Hutchins, known online as MalwareTech, and the banking Trojan named Kronos was first published in 2009. Hutchins became famous and was named a “hero†after he helped stop the WannaCry ransomware attack by registering a domain that acted as a kill switch for the malware. | Wannacry | |||
| 2017-08-18 16:43:40 | Patching Against the Next WannaCry Vulnerability (CVE-2017-8620) (lien direct) | This month's Microsoft patch updates include one particular vulnerability that is raising concerns: CVE-2017-8620, which affects all versions of Windows from 7 onwards. Microsoft explained, "in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer." | Wannacry | |||
| 2017-08-04 16:30:16 | Arrest Shines Light on Shadowy Community of Good, Bad Hackers (lien direct) | Two months ago, Marcus Hutchins was an "accidental hero," a young computer whiz living with his parents in Britain who found the "kill switch" to the devastating WannaCry ransomware. | Wannacry | |||
| 2017-08-03 20:21:45 | UK Security Researcher \'Hero\' Accused of Creating Bank Malware (lien direct) | A British computer security researcher hailed as a hero for thwarting the "WannaCry" ransomware onslaught was in US custody on Thursday after being indicted on charges of creating malware to attack banks. | Wannacry | ★★★★ | ||
| 2017-07-24 17:21:39 | One in Ten U.S. Organizations Hit by WannaCry: Study (lien direct) | A recent survey discovered that the vast majority of organizations in the United States weren't prepared for the WannaCry ransomware attack, but just one in ten ended up being infected by the malware. | Wannacry | |||
| 2017-07-06 11:28:03 | Android Ransomware Mimics WannaCry (lien direct) | Android file-encrypting ransomware SLocker was recently observed using an interface similar to that of the WannaCry malware that hit Windows systems worldwide last month, TrendMicro security researchers reveal. | Wannacry | |||
| 2017-07-05 16:41:06 | Fake WannaCry Ransomware Uses NotPetya\'s Distribution System (lien direct) | The NotPetya wiper wasn't the only piece of malware distributed last week using the compromised M.E.Doc update mechanism: a fake WannaCry ransomware variant was delivered using the same channel, Kaspersky Lab reports. | NotPetya Wannacry | |||
| 2017-06-30 19:43:37 | Microsoft Tackles Ransomware with Controlled Folder Access (lien direct) | In the wake of global malicious attacks such as WannaCry and NotPetya, Microsoft this week announced a new feature meant to keep users' data safe from ransomware and other type of malware. | NotPetya Wannacry | |||
| 2017-06-28 14:56:16 | UK\'s Metropolitan Police Still Using 10,000 Windows XP Computers (lien direct) | Legacy Windows XP systems used by public authorities in the UK remains a concern. The WannaCry outbreak last month followed by the current 'NotPetya' outbreak -- both using a vulnerability patched in newer versions of Windows, but initially unpatched in XP -- highlights the problem. | NotPetya Wannacry | |||
| 2017-06-20 15:28:47 | Why WannaCry Was a Wake Up Call for Critical Infrastructure Security (lien direct) | Many OT Networks are Susceptible to Threats Like WannaCry | Wannacry | |||
| 2017-06-15 16:54:22 | U.K. Center of Security Excellence Hit by Ransomware (lien direct) | One of the world's top ten universities, awarded the status of "centre of excellence in cyber-security research" by the UK's GCHQ, has been hit by a so-far unrecognized strain of ransomware. This comes just one month after many UK health trusts were struck by the global WannaCry ransomware. | Wannacry | |||
| 2017-06-15 13:11:22 | Why WannaCry Really Makes Me Want to Cry (lien direct) | Recently, the WannaCry ransomware worm was big news. For security professionals working inside organizations with unpatched systems vulnerable to infection, it was a particularly busy period. Plenty has been written about the malware itself, how it spread, the need to patch, and many other technical topics around the recent outbreak. Much great analysis has been done, and I certainly don't need to rehash that here. I'd like to focus on a different angle ent | Wannacry | |||
| 2017-06-07 14:20:19 | Protecting Against Malware Requires a DevOps Mindset (lien direct) | Imagine a world where cyber-criminals include kill switches in all their malware that's as simple to activate as registering a domain name. | Wannacry | |||
| 2017-06-04 20:28:08 | Jaff Ransomware Operation Tied to Cybercrime Store (lien direct) | Jaff, a ransomware family that emerged on May 12, the same day WannaCry did, appears connected to wider operations, as a recent sample was found to share server space with a refined cybercrime marketplace, Heimdal Security warns. | Wannacry | |||
| 2017-06-03 12:36:04 | \'Tallinn Manual 2.0\' - the Rulebook for Cyberwar (lien direct) | Tallinn - With ransomware like "WannaCry" sowing chaos worldwide and global powers accusing rivals of using cyberattacks to interfere in domestic politics, the latest edition of the world's only book laying down the law in cyberspace could not be more timely. | Wannacry | |||
| 2017-05-30 16:10:22 | China, U.S. Most Affected by WannaCry Ransomware (lien direct) | New data released by security company Kryptos Logic reveals that China and the United States were affected the most by the WannaCry outbreak over the past weeks. | Wannacry | ★★★★★ | ||
| 2017-05-30 15:55:19 | Latest WannaCry Theory: Currency Manipulation (lien direct) | The recent WannaCry outbreak is still a mystery. We know what (ransomware), and how (a Windows vulnerability on unsupported or unpatched systems); but we don't know who or why. We're not short of theories: Lazarus, North Korea, some other nation-state actor, Chinese or Russian actors -- but none of these has gained general acceptance. | Wannacry APT 38 | |||
| 2017-05-25 19:41:00 | Can We Ever be Prepared for the Next WannaCry? (lien direct) | The recent WannaCry ransomware outbreak is yet another wake-up call. Humans alone can no longer be expected to manually respond to brazen, fast-spreading cyber-attacks that strike without warning and routinely bypass porous network borders. | Wannacry | |||
| 2017-05-25 17:05:22 | Linguistic Analysis Suggests WannaCry Authors Speak Chinese (lien direct) | 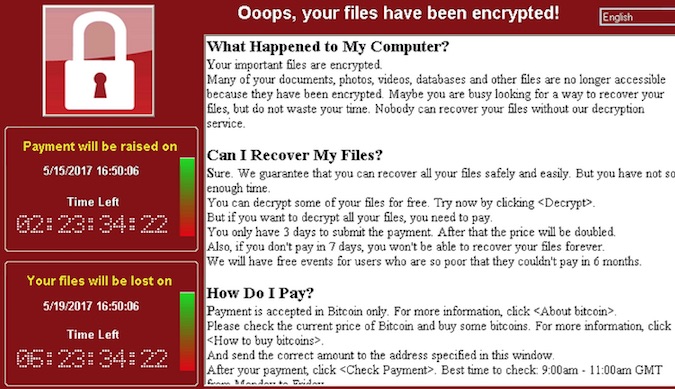
|
Wannacry | |||
| 2017-05-25 12:06:16 | The Impact of WannaCry on the Ransomware Conversation (lien direct) | By this point, we've all heard about the major ransomware attack that impacted an estimated 200,000 computers across 150 countries earlier this month. A malware variant dubbed WannaCry made its way into network infrastructure globally, encrypting data and demanding a ransom of $300 USD per infected computer. | Wannacry | |||
| 2017-05-24 20:33:45 | New Jaff Ransomware Variant Emerges (lien direct) | Although it dominated headlines over the past couple of weeks, WannaCry wasn't the only ransomware family running rampant. Another active threat was Jaff, a ransomware family that emerged just days before the WannaCry outbreak. | Wannacry | |||
| 2017-05-23 11:11:31 | WannaCry \'Highly Likely\' Work of North Korean-linked Hackers, Symantec Says (lien direct) | North Korea-linked Lazarus Hacking Group is "Highly Likely" to be Responsible for the Global "WannaCry" Ransomware Attack, Symantec Says | Wannacry APT 38 | |||
| 2017-05-22 13:01:34 | Windows 7 Most Hit by WannaCry Ransomware (lien direct) | Most of the computers affected by the WannaCry ransomware outbreak were running Windows 7, security researchers have revealed. | Wannacry | |||
| 2017-05-19 19:25:27 | North Korea Denies Role in Global Cyberattack (lien direct) | North Korea on Friday angrily dismissed reports linking its isolated regime to the global cyberattack that held thousands of computers to virtual ransom. Up to 300,000 computers in 150 countries were hit by the WannaCry worm, which seizes systems and demands payment in Bitcoin to return control to users. | Wannacry | |||
| 2017-05-19 19:17:05 | Stealth Backdoor Abused NSA Exploit Before WannaCrypt (lien direct) | In the aftermath the WannaCry ransomware outbreak, security researchers discovered numerous attacks that have been abusing the same EternalBlue exploit for malware delivery over the past several weeks. | Wannacry | |||
| 2017-05-19 17:17:21 | WannaCry Does Not Fit North Korea\'s Style, Interests: Experts (lien direct) | Some experts believe that, despite malware code similarities, the WannaCry ransomware is unlikely to be the work of North Korea, as the attack does not fit the country's style and interests. | Wannacry | |||
| 2017-05-19 09:29:56 | Medical Devices Infected With WannaCry Ransomware (lien direct) | 
|
Wannacry | |||
| 2017-05-19 00:12:17 | Microsoft Withheld Update That Could Have Slowed WannaCry: Report (lien direct) | American software giant Microsoft held back from distributing a free security update that could have protected computers from the WannaCry global cyber attack, the Financial Times reported Thursday. | Wannacry | |||
| 2017-05-18 14:06:04 | PATCH Act: A New Bill Designed to Prevent Occurrences Like WannaCrypt (lien direct) | Following the worldwide WannaCrypt ransomware attack that leveraged the EternalBlue exploit developed by and stolen from the NSA, Microsoft's chief legal officer called for governments to stop stockpiling 0-day exploits. His arguments are morally appealing but politically difficult. | Wannacry | |||
| 2017-05-17 17:06:55 | WannaCry Ransomware Creators Make Rookie Mistake (lien direct) | WannaCry Ransomware Didn't Utilize Trackable Bitcoin Wallets | Wannacry | |||
| 2017-05-16 17:05:04 | NSA\'s EternalBlue Exploit Fully Ported to Metasploit (lien direct) | The National Security Agency (NSA)-linked EternalBlue exploit that became well known after being used in a recent global ransomware campaign has been ported to the popular Metasploit penetration testing Framework. | Wannacry | |||
| 2017-05-16 14:06:11 | Industry Reactions to WannaCry Ransomware Attacks (lien direct) | The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, has infected more than 200,000 devices worldwide. The attacks affected banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants. | Wannacry |
To see everything:
Our RSS (filtrered)
