What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-11-08 03:00:00 | Top application security tools for 2019 (lien direct) | The 2018 Verizon Data Breach Investigations Report says most hacks still happen through breaches of web applications. For this reason, testing and securing applications has become a priority for many organizations. That job is made easier by a growing selection of application security tools. Below is a list of some of the best application security tools available, with descriptions of the situations where they can be most effective. | Data Breach | |||
| 2018-11-07 03:00:00 | Experience an RDP attack? It\'s your fault, not Microsoft\'s (lien direct) | I've seen blog posts and forum threads bad mouthing Microsoft and Remote Desktop Protocol (RDP). Usually it's in conjunction with someone complaining that a ransomware or cryptominer variant had successfully compromised their environment through RDP. The rants are often followed by calls for everyone to dump Microsoft Windows and how “Microsoft security sucks!”It's not only boring and pedantic. It's a case of blaming the wrong culprit. | ||||
| 2018-11-06 08:56:00 | Worst malware and threat actors of 2018 so far (lien direct) | What's the worst malware so far into 2018? The worst botnets and banking trojans, according to Webroot, were Emotet, Trickbot, and Zeus Panda. Crysis/Dharma, GandCrab, and SamSam were the worst among ransomware. The top three in cryptomining/cryptojacking were GhostMiner, Wanna Mine, and Coinhive.And included in the list of top 10 threat actors so far this year, we find Lazarus Group, Sofacy and MuddyWater coming in the top three spots, according to AlienVault. Lazarus Group took the top spot from Sofacy this year. The reported locations for the top 10 threat actors are North Korea, with two groups; Russia, with three groups; Iran, with two groups; China, with two groups; and India, with one. Microsoft Office was the most exploited application, but Adobe Flash, WebLogic, Microsoft Windows, Drupal and GPON routers were also listed in the top 10. | Malware Threat Medical | APT 38 | ||
| 2018-11-06 02:54:00 | The OPM hack explained: Bad security practices meet China\'s Captain America (lien direct) | In April of 2015, IT staffers within the United States Office of Personnel Management (OPM), the agency that manages the government's civilian workforce, discovered that some of its personnel files had been hacked. Among the sensitive data that was exfiltrated were millions of SF-86 forms, which contain extremely personal information gathered in background checks for people seeking government security clearances, along with records of millions of people's fingerprints. The OPM breach led to a Congressional investigation and the resignation of top OPM executives, and its full implications-for national security, and for the privacy of those whose records were stolen-are still not entirely clear. | Hack | |||
| 2018-11-05 12:59:00 | BrandPost: Up-Close Look at Threat Response in 2 Industries (lien direct) | A new global survey by Ponemon and ServiceNow of nearly 3,000 cybersecurity professionals reveals that more than half the companies have experienced a breach in the past year.In this session Bob Bragdon, Senior Vice President and Publisher of CSO, and Piero DePaoli, Sr. Director for Security and Risk, ServiceNow, explore how respondents in 2 specific industries – financial services and healthcare – are handling threats.The survey found that both sectors had similar responses regarding breaches: 45% of financial services companies have had one or more breach in the last 2 years, and 50% of healthcare organizations. But the survey also revealed that financial services organizations appear better at handling those breaches. Why is this the case? | Threat | |||
| 2018-11-05 08:42:00 | (Déjà vu) Republican Kemp accuses Georgia Democrats of hacking but provides no proof (lien direct) | Toss around accusations of a failed attempt to hack a state's voter registration system - without actually providing any proof - that's one way to really stir things up right before the midterm elections.That is what Brian Kemp, Georgia's current secretary of state - who is also the Republican candidate for governor - did on Sunday. With the midterm elections just a few days away, Kemp accused the Democratic Party of Georgia of hacking the state's voter registration system. Democrat Stacey Abrams, his opponent, called it “a reckless and unethical ploy” to mislead voters. | Hack Guideline | |||
| 2018-11-05 08:42:00 | (Déjà vu) Republican Kemp accused Georgia Democrats of hacking but provided no proof (lien direct) | Toss around accusations of a failed attempt to hack a state's voter registration system – without actually providing any proof, that's one way to really stir things up right before the midterm election.That is what Brian Kemp, Georgia's current secretary of state – who is also the Republican candidate for governor, did on Sunday. As you know, midterm elections are on Tuesday. So right before the election, Kemp accused the Democratic Party of Georgia of hacking. Democrat Stacey Abrams, his opponent, called it “a reckless and unethical ploy” to mislead voters. | Hack Guideline | |||
| 2018-11-04 09:19:00 | (Déjà vu) Meaner, more violent Stuxnet variant reportedly hits Iran (lien direct) | Stuxnet allegedly has a vicious little brother, or perhaps it is a malicious cousin; the complex malware was likened to being similar to Stuxnet but “more violent, more advanced and more sophisticated.”Iran, according to the Times of Israel, admitted that its “infrastructure and strategic networks” were hit by a meaner, leaner version of Stuxnet. A TV news report added that the Iranians are “not admitting, of course, how much damage has been caused.”The report came after Iranian Supreme Leader Ayatollah Ali Khamenei said Iran needed to step up efforts to fight enemy “infiltration.” Reuters also reported that Gholamreza Jalali, the head of Iran's civil defense agency, said, “Recently we discovered a new generation of Stuxnet which consisted of several parts ... and was trying to enter our systems.” Jalali didn't go into more detail. | Malware Guideline | |||
| 2018-11-04 09:19:00 | (Déjà vu) Meaner, more violent Stuxnet variant reportedly hit Iran (lien direct) | Stuxnet allegedly has a vicious little brother, or perhaps it is a malicious cousin; the complex malware was likened to being similar to Stuxnet but “more violent, more advanced and more sophisticated.” Iran, according to the Times of Israel, admitted that its “infrastructure and strategic networks” were hit by a meaner, leaner version of Stuxnet. A TV news report added that the Iranians are “not admitting, of course, how much damage has been caused.”The report came after Iranian Supreme Leader Ayatollah Ali Khamenei said Iran needed to step up efforts to fight enemy “infiltration.” Reuters also reported that Gholamreza Jalali, the head of Iran's civil defense agency, said, “Recently we discovered a new generation of Stuxnet which consisted of several parts ... and was trying to enter our systems.” Jalali didn't go into more detail. | Malware Guideline | |||
| 2018-10-31 14:54:00 | BrandPost: The Patching Paradox (lien direct) | A new global survey by Ponemon and ServiceNow of nearly 3,000 cybersecurity professionals reveals that more than half the companies have experienced a breach in the past year.In this session Bob Bragdon, Senior Vice President and Publisher of CSO, and Cliff Huntington, head of global sales for governance, risk, and compliance at ServiceNow, explore how high-performing security teams prevent breaches and what other teams can do to emulate their success.One particular area deserves a close look: unpatched enterprise software. The survey revealed that a majority of cyber-attack victims say their breaches could have been prevented by installing patches – and the survey also found that organizations can reduce their breach risk by 20% by scanning. | Patching | |||
| 2018-10-30 03:00:00 | Biggest data breach penalties for 2018 (lien direct) | Uber: $148 million Image by Getty/UberIn 2016 ride-hailing app Uber had 600,000 driver and 57 million user accounts were breached. Instead of reporting the incident the company paid the perpetrator $100,000 to keep the hack under wraps. Those actions, however, cost the company dearly. The company was fined $148 million -- the biggest data-breach payout in history – for violation of state data breach notification laws. Image by Getty/UberIn 2016 ride-hailing app Uber had 600,000 driver and 57 million user accounts were breached. Instead of reporting the incident the company paid the perpetrator $100,000 to keep the hack under wraps. Those actions, however, cost the company dearly. The company was fined $148 million -- the biggest data-breach payout in history – for violation of state data breach notification laws. |
Data Breach Hack | Uber | ||
| 2018-10-29 08:50:00 | Flaws in brain stimulation tech could let hackers erase or hold memories for ransom (lien direct) | Oh goody! Erasing memories or rewriting them and then implanting false ones are not just the stuff of sci-fi or horror flicks, as a new report warns that hackers will be able to attack the memories of people with implanted brain stimulation devices.New research by Kaspersky Lab and the University of Oxford Functional Neurosurgery Group identified vulnerabilities currently in implanted devices used for deep brain stimulation. The devices, known as neurostimulators or implantable pulse generators, send electrical impulses to parts of the brain; they can be used to treat disorders such as Parkinson's disease, Obsessive–Compulsive Disorder, major depression and essential tremor. | ||||
| 2018-10-29 03:00:00 | Why the best antivirus software isn\'t enough (and why you still need it) (lien direct) | Traditional signature-based antivirus is notoriously bad at stopping newer threats such as zero-day exploits and ransomware, but it still has a place in the enterprise, experts say, as part of a multi-layer endpoint security protection strategy. The best antivirus products act as the first layer of defense, stopping the vast majority of malware attacks and leaving the broader endpoint protection software with a smaller workload to deal with. | Malware | |||
| 2018-10-23 09:00:00 | Burned malware returns, says Cylance report: Is Hacking Team responsible? (lien direct) | Burning malware is like Hercules fighting the nine-headed Hydra. For every head he cuts off, two more grow back in its place. That's the lesson from a new report by Cylance today, and one both enterprise network defenders-and the public at large-should pay attention to.[ Keep up with 8 hot cyber security trends (and 4 going cold). Give your career a boost with top security certifications: Who they're for, what they cost, and which you need. | Sign up for CSO newsletters. ] Cyber mercenaries sell malware to oppressive regimes in the Middle East, which then use that malware to attack their own citizens, research from the Citizen Lab suggested earlier this year. The current regimes in Turkey and Egypt compel local ISPs to run Canadian-made Sandvine/Procera deep packet inspection middleboxes that inject the malware into unencrypted HTTP downloads of popular software like Avast, VLC Player and WinRAR. Large numbers of users in Egypt, Turkey and Syria (near the border with Turkey) are affected. | Malware | |||
| 2018-10-23 07:42:00 | (Déjà vu) High-tech thieves used a relay attack to steal a Tesla Model S (lien direct) | Tesla owners, if you haven't enabled the PIN to Drive security feature to safeguard your very expensive ride, then hopefully watching the security footage of thieves quickly stealing a Tesla Model S will serve to make it a priority.Antony Kennedy, the owner of the Model S, caught surveillance footage of his fine ride being heisted. One of the crooks appears to use a tablet to capture the signal from the key fob located in the Essex, England, house. The second thief with a mobile phone in hand waits next to the car door. The relay attack took under 50 seconds until they had successfully tricked the car into responding as if the owner was standing there with the key fob. | Tesla | |||
| 2018-10-23 07:42:00 | (Déjà vu) Surveillance video shows high-tech thieves using relay attack to steal Tesla Model S (lien direct) | Tesla owners, if you haven't enabled the “PIN to Drive” security feature to safeguard your very expensive ride, then hopefully watching the security footage of thieves quickly stealing a Tesla Model S will serve to make it a priority.Antony Kennedy, the owner of the Model S, caught surveillance footage of his fine ride being heisted. One of the crooks appears to use a tablet to capture the signal from the key fob located in the Essex, England, house. The second thief with a mobile phone in hand waits next to the car door. The relay attack took under 50 seconds until they had successfully tricked the car into responding as if the owner was standing there with the key fob. | Tesla | |||
| 2018-10-22 14:04:00 | BrandPost: The Answer to Cyber Threats: People or Technology? (lien direct) | A new global survey by Ponemon and ServiceNow of nearly 3,000 cybersecurity professionals reveals that more than half the companies have experienced a breach in the past year. Compounding this issue: the volume of cyberattacks continue to increase, and the industry is facing a shortage of qualified security pros.But experts agree that hiring more people isn't necessarily the answer to solving this cyber threat puzzle. In this session Bob Bragdon, Senior Vice President and Publisher of CSO, and Myke Lyons, Security Transformational Leader at ServiceNow, explore the answers. | Threat Guideline | |||
| 2018-10-22 14:00:00 | BrandPost: Know the Facts – Today\'s Cyberthreat Landscape (lien direct) | The facts are undeniable: A new global survey by Ponemon and ServiceNow of nearly 3,000 cybersecurity professionals reveals that more than half the companies have experienced a breach in the past year.In this session Bob Bragdon, Senior Vice President and Publisher of CSO, and Janene Casella, Director of Product Marketing for Security and Risk, ServiceNow, explore the Ponemon survey findings.Casella offers a sobering take on the 48% stat. “As our IT environments continue to expand, we're more and more vulnerable to attacks -- and we know that cybercrime is very profitable, whether that's selling personal information or ransomware, which was huge last year,” she says. “The other thing is that cybercrime is becoming more and more expensive for those who get breached. The average cost of data breach is reaching about $3 million US.” | Data Breach | |||
| 2018-10-22 03:06:00 | 3 top multi-cloud security challenges, and how to build a strategy (lien direct) | A data breach or intruder alert will send security teams into high gear as they scramble to stem the damage and determine the cause. | Data Breach | |||
| 2018-10-21 09:40:00 | Another government system breached; 75,000 people affected (lien direct) | On Friday, the Centers for Medicare & Medicaid Service admitted to a breach in which attackers made off with the sensitive and personal information of 75,000 people. The “anomalous activity” was detected on October 13; the breach in Federally Facilitated Exchanges that agents and brokers use to help people signup for healthcare plans was declared on October 16. What exact sensitive and private info the hackers made off with was not explained, although people hand over a great deal of both types of information when signing up for healthcare. | ||||
| 2018-10-19 11:22:00 | (Déjà vu) Trend Micro shines a light on its new cybersecurity solutions (lien direct) | Last week, Trend Micro came to Boston for its annual Trend Insights industry analyst event. The company provided an overview of its business, products, and strategy. Here are a few of my take-aways: Trend Micro is prepared for the next chapter in endpoint security. To maintain its market leadership, Trend Micro is rolling out Apex One, its newest endpoint security product. Apex One provides more prevention/detection capabilities while consolidating all endpoint security functions onto a single agent. Trend Micro has also decided to swim against the industry tide by including EDR as part of its core commercial endpoint security product (note: EDR requires a licensing change), thus all customers who upgrade will get Trend Micro EDR, alleviating the need to shop elsewhere. Apex One will be an easy decision for existing Trend Micro customers and may be an attractive alternative for CISOs looking for an endpoint security solution will all the bells and whistles. Trend Micro product strategy: Better together. Trend Micro talks about connected threat defense, which brings together several its individual endpoint, network, and cloud products together as an integrated cybersecurity technology architecture. Good timing, as ESG research indicates that 62% of organizations would be willing to buy a majority of their cybersecurity products from a single enterprise-class vendor. For example, TippingPoint IDS/IPS is tightly integrated with Deep Discovery, Trend Micro's malware detection sandbox, while Deep Security, Trend Micro's cloud workload security offering, integrates with both of these products. As part of its business strategy, Trend Micro is working with customers to replace discrete point tools with Trend Micro products and reap integration benefits such as improved threat prevention/detection while streamlining security operations. Moving toward managed services. While Trend Micro engineered its EDR offering for ease of use, it recognizes that many organizations don't have the resources or skills to deploy, learn, or operate detection/response tools on their own. To work with these customers, Trend Micro is rolling out a managed detection and response service (MDR) as a complement to its products. Furthermore, Trend Micro is spinning out a new company called Cysiv, which offers several other advanced managed security services. With these moves, Trend Micro is demonstrating that it wants to play a direct role in the growing market for security services – rather than an indirect role as an arms dealer alone. All in on cloud security. Trend Micro jumped on the server virtualization and cloud computing bandwagons early by forming tight partnerships with VMware, Amazon, and Microsoft. Now that every other established vendor and VC-backed startup is all in on the cloud, Trend Micro is moving beyond basic cloud security support. For example, Trend Micro cloud security products are tightly-coupled with its connected threat defense for prevention/detection. From a cloud perspective, Trend Micro has gotten very familiar with application developers and DevOps to make sure that Trend Micro cloud security products fit seamlessly into a CI/CD pipeline. Trend Micro has also expanded its purview to cover containers micro-services, and even cloud-based application security. In this way, Trend Micro is aligning with cloud innovation and culture – not just hawking security products. More business investment. Over the past five years, Trend Micro business has gone through some significant shifts. For example, a larger percentage of the company's revenue comes from commercial sales rather than consumer sales, while Trend Micro has seen rapid market growth in North America. Trend Micro will hire engineers, expand sales staff, and service channel partners to keep this momentum going. | Malware Threat Guideline | |||
| 2018-10-19 11:22:00 | (Déjà vu) Cybersecurity Trends – With Trend Micro (lien direct) | Last week, Trend Micro came to Boston for its annual Trend Insights industry analyst event. The company provided an overview of its business, products, and strategy. Here are a few of my take-aways: Trend is prepared for the next chapter in endpoint security. To maintain its market leadership, Trend Micro is rolling out ApexOne, its newest endpoint security product. ApexOne provides more prevention/detection capabilities while consolidating all endpoint security functions onto a single agent. Trend has also decided to swim against the industry tide by including EDR as part of its core commercial endpoint security product, thus all customers who upgrade will get Trend EDR, alleviating the need to shop elsewhere. ApexOne will be an easy decision for existing Trend Micro customers and may be an attractive alternative for CISOs looking for an endpoint security solution will all the bells and whistles. Trend product strategy: Better together. Trend talks about connected threat defense which brings together several its individual endpoint, network, and cloud products together as an integrated cybersecurity technology architecture. Good timing as ESG research indicates that 62% of organizations would be willing to buy a majority of their cybersecurity products from a single enterprise-class vendor. For example, TippingPoint IDS/IPS is tightly integrated with Deep Discovery, Trend's malware detection sandbox while Deep Security, Trend's cloud workload security offering integrates with both of these products. As part of its business strategy, Trend is working with customers to replace discrete point tools with Trend products and reap integration benefits like improved threat prevention/detection while streamlining security operations. Moving toward managed services. While Trend engineered its EDR offering for ease-of-use, it recognizes that many organizations don't have the resources or skills to deploy, learn, or operate detection/response tools on their own. To work with these customers, Trend Micro is rolling out a managed detection and response service (MDR) as a complement to its products. Furthermore, Trend is spinning out a new company called Cysiv which offers several other advanced managed security services. With these moves, Trend is demonstrating that it wants to play a direct role in the growing market for security services – rather than an indirect role as an arms dealer alone. All in on cloud security. Trend Micro jumped on the server virtualization and cloud computing bandwagons early by forming tight partnerships with VMware, Amazon, and Microsoft. Now that every other established vendor and VC-backed startup are all-in on the cloud, Trend is moving beyond basic cloud security support. For example, Trend cloud security products are tightly-coupled with its connected threat defense for prevention/detection. From a cloud perspective, Trend has gotten very familiar with application developers and DevOps to make sure that Trend cloud security products fit seamlessly into a CI/CD pipeline. Trend has also expanded its purview to cover containers micro-services, and even cloud-based application security. In this way, Trend Micro is aligning with cloud innovation and culture – not just hawking security products. More business investment. Over the past 5 years, Trend Micro business has gone through some significant shifts. For example, a larger percentage of the company's revenue comes from commercial sales rather than consumer sales, while Trend has seen rapid market growth in North America. Trend Micro will hire engineers, expand sales staff, and service channel partners to keep this momentum going. In my humble opinion, Trend Micro remains a bit of a diamond in the rough – its security expertise and advanced techno | Malware Threat Guideline | |||
| 2018-10-18 03:00:00 | 7 best practices for negotiating ransomware payments (lien direct) | Whether through ransomware, data theft, a distributed denial of service attack (DDoS) attack or General Data Protection Regulation (GDPR)-based extortion, criminals demanding money from organizations in exchange for the return of data or to continue business operations continues to be a common occurrence. The best advice, of course, is not to pay, but as a last resort some organizations might feel the need to negotiate with cybercriminals during a cyberattack. | Ransomware | |||
| 2018-10-17 08:22:00 | (Déjà vu) Ransomware attack hits North Carolina water utility following hurricane (lien direct) | Bad timing, bad luck or heartless baddies - maybe all three came into play when a critical water utility in North Carolina, which was still recovering from Hurricane Florence, was brought to its knees by a ransomware attack.Despite still dealing with the aftermath of Hurricane Florence, which ripped through the state in September, Onslow Water and Sewer Authority (ONWASA) said it has no intention of paying the ransom demanded. In the Jacksonville, North Carolina, utility's words, it “will not negotiate with criminals nor bow to their demands.” | Ransomware | |||
| 2018-10-17 08:22:00 | (Déjà vu) Ransomware attack hit North Carolina water utility in aftermath of hurricane (lien direct) | Bad timing, bad luck or heartless baddies, maybe all three came into play when a critical water utility in North Carolina, which was still recovering from the effects of a hurricane disaster, was brought to its knees by a ransomware attack.Despite still dealing with the aftermath of Hurricane Florence, which ripped through in September, Onslow Water and Sewer Authority (ONWASA) said it has no intention of paying the ransom demanded. In the Jacksonville, North Carolina, utility's words, it “will not negotiate with criminals nor bow to their demands.” | Ransomware | |||
| 2018-10-16 11:47:00 | Best new Windows 10 security features: More patching, updating flexibility (lien direct) | With the new era of Windows as a service, Microsoft is rolling out changes to the operating system twice a year. Many of those changes will allow you to improve your security posture and offer more security choices. You no longer have to wait for a new operating system to deploy new security features. [ Learn how to identify, block and remove malware from Windows PCs. | Get the latest from CSO by signing up for our newsletters. ] Below is a summary of all the new security features and options in Windows 10 version 1809, which features Windows Defender Advanced Threat Protection (ATP) enhancements, more options for enterprises to update and patch Windows, and other security improvements. Bookmark this article, because we will be adding new security features as Microsoft releases future Windows updates. | Malware Threat | |||
| 2018-10-16 06:18:00 | BrandPost: Addressing the Modern Threat Landscape with Threat Intelligence Services (lien direct) | For your customers, identifying and quickly securing against modern cyberthreats is paramount-especially as they adopt digital transformation strategies to better meet the needs of their consumers. Unfortunately, cybercriminals are also moving at an increasingly rapid pace by continually innovating and evolving to exploit new attack vectors.However, given the current cybersecurity skills shortage impacting businesses across industries, the need for rapid threat identification and security implementation is often tempered by human-caused security errors and misconfigurations. In order to maintain an effective security posture that can adapt and respond to the evolving threat landscape at pace-without hindering digital transformation efforts-network professionals need faster and more accurate threat intelligence gathering. With this in mind, Fortinet's threat intelligence services provides your customers with the type of information and analysis they need to secure their digital businesses against modern cyberthreats and facilitate success. | Threat | |||
| 2018-10-15 08:43:00 | Zeek: A free, powerful way to monitor networks, detect threats (lien direct) | It's common in many organizations for network and security operations to exist in silos. This may have been OK a couple of decades ago when threats only came in through a single point and applications were vertically integrated. Today, however, the environment is completely different, as the cloud, mobility, Internet of Things (IoT), and other trends have fundamentally changed the security landscape. Consequently, finding the source of a breach has never been more difficult.Security professionals need network data Today's CISOs and security architects need to think differently and turn to the network for a source of information. The world has become network-centric, and the network holds a wealth of valuable information that's relevant to security. The problem is legacy network monitoring tools are designed for network teams, which prevents security professionals from being able to tap into that network information and extract the information they need. | ||||
| 2018-10-10 09:52:00 | Top cybersecurity facts, figures and statistics for 2018 (lien direct) | Looking for hard numbers to back up your sense of what's happening in the cybersecurity world? We dug into studies and surveys of the industry's landscape to get a sense of the lay of the land-both in terms of what's happening and how your fellow IT pros are reacting to it.Ransomware is down, cryptomining is up With last year's outbreak of NotPetya, ransomware-malicious programs that encrypt your files and demand a ransom payment in bitcoin to restore them-became one of the most talked about forms of malware of 2017. Yet at the same time, the actual rates of malware infection began to plummet around the middle of the year, until by December 2017 it represented only about 10 percent of infections. | Malware Studies | NotPetya | ||
| 2018-10-08 08:49:00 | Facebook wants you to put a Portal camera and microphone in your home (lien direct) | Just say no when it comes to Facebook's Portal video chat device. This is the same company which has consistently taken steps that are bad for privacy – working from a mindset of it is better to ask for forgiveness than for permission – and now it wants you to put its camera and microphone-enabled device in your home? Oh, hell no!Facebook's Portal tablets come in two flavors, the $199 10-inch 720p Portal and the $349 15-inch 1080p Portal+. The company claimed it started working on a “privacy-first plan” for Portal two years ago. The devices were supposed to launch in May, but Facebook had decided by March to delay the launch as it was embroiled in the Cambridge Analytica data scandal. Not even two weeks ago, Facebook admitted to a breach that affected 50 million people. The timing of the launch is curious as now doesn't seem the best time to be asking people to rely on Facebook to protect their privacy and security, although it is just in time for the devices to start shipping in November before the holidays. | ||||
| 2018-10-08 03:00:00 | Why I don\'t believe Bloomberg\'s Chinese spy chip report (lien direct) | I'm very dubious of the recent Bloomberg report stating that several American companies were compromised by spy chips inserted secretly by the Chinese on U.S.-used computer motherboards. The Bloomberg article should be used as a starting point for a very real, serious, and long overdue discussion of supply chain risks, but I'd rather start with the facts supported by evidence instead of anonymous claims that have been unsupported for over three decades. | ||||
| 2018-10-03 08:49:00 | (Déjà vu) Recipe Unlimited denies ransomware attack, despite alleged ransom note (lien direct) | Recipe Unlimited, which operates 19 franchise restaurant brands, must think that claiming to be a victim of a “malware outbreak” sounds better than saying it was a victim of a ransomware attack. Nevertheless, nine of its restaurant brands were impacted by the attack, and some have even closed as the bitcoin ransom demand total grows higher each day.Corporate said that after the attack (“malware outbreak”), which happened on Friday, Sept. 28, it tried to stop the spread of the ransomware by taking several of its systems offline and suspending internet access to affected locations. | Ransomware | |||
| 2018-10-03 08:49:00 | (Déjà vu) Recipe Unlimited denies ransomware attack, despite alleged ransom note demanding bitcoin (lien direct) | Recipe Unlimited, which operates 19 franchise restaurant brands, must think that claiming to be a victim of a “malware outbreak” sounds better than saying it was a victim of a ransomware attack; nevertheless, nine of its restaurant brands were impacted by the attack and some have even closed down shop as the bitcoin ransom demand total grows higher each day.Corporate said that after the attack (“malware outbreak”), which happened on Friday, Sept. 28, it tried to stop the spread of the ransomware by taking “a number of our systems offline and suspended internet access to affected locations as a precaution.” | Ransomware | |||
| 2018-10-02 14:18:00 | Gwinnett Medical Center investigating possible data breach (lien direct) | After being contacted by Salted Hash about a possible data breach, Gwinnett Medical Center(GMC), a not-for-profit network of healthcare providers in Gwinnett County, Georgia, has confirmed they're investigating what they're calling an IT incident.Salted Hash first became aware of a possible data breach at GMC late last week, but the exact details surrounding the incident were not immediately available.What we learned was that on Saturday (Sept. 29), IT staff at GMC Lawrenceville became aware of an incident involving several hundred patient records at the least. Immediately following the discovery, the alleged attackers sent threats.Sometime later, an agent from the local FBI field office arrived and offered to assist, but it isn't clear if the FBI knew something was wrong, or if the law enforcement agency was called in after the threats were made. | Data Breach | |||
| 2018-10-02 08:47:00 | SQL injection explained: How these attacks work and how to prevent them (lien direct) | SQL injection definition Structured Query Language (SQL) injection is a type of attack that can give an adversary complete control over your web application database by inserting arbitrary SQL into a database query.Immortalized by "Little Bobby Drop Tables" in XKCD 327, SQL injection (SQLi) was first discovered in 1998, yet continues to plague web applications across the internet. Even the OWASP Top Tenlists injection as the number one threat to web application security. [ Learn why you need an API security program, not a piecemeal approach. | Get the latest from CSO by signing up for our newsletters. ] The good news? SQL injection is the lowest of the low-hanging fruit for both attackers and defenders. SQLi isn't some cutting edge NSA Shadow Brokers kit, it's so simple a three-year old can do it. This is script kiddie stuff-and fixing your web application to mitigate the risk of SQLi is so easy that failure to do so looks more and more like gross negligence. | Threat | |||
| 2018-10-01 08:14:00 | New vicious Torii IoT botnet discovered (lien direct) | Torii – you might not have heard the name yet, but this new botnet has advanced techniques and persistence and is a threat to nearly every type of computer. Researchers from Avast warned about Torii, which is certainly no spinoff of Mirai. Torii, they said, is an “example of the evolution of IoT malware” and “its sophistication is a level above anything we have seen before.”For starters, Torii can run on almost every modern computer, smartphone, and tablet. Target architectures include x86_64, x86, ARM, MIPS, Motorola 68k, SuperH, PPC and others. Avast security researcher Martin Hron told The Parallax that one server had over 100 versions of malware payloads and supported 15 to 20 architectures. This suggests a “team effort,” as what Torii can do “would be hard for any on person to accomplish.” | Malware Threat | ★★ | ||
| 2018-09-28 07:00:00 | BrandPost: Securing the Multi-Cloud: 3 Steps for Maintaining Control and Visibility (lien direct) | A hybrid, multi-cloud environment offers the advantages of high resiliency combined with the agility to adapt quickly to changing digital business requirements. In one recent analysis, 86% of surveyed organizations stated that they had already adopted a multi-cloud strategy. Tempering the advantages of such a strategy, however, are a number of related security concerns. For example, if migrating to one cloud environment expands the attack surface, multiple clouds magnify it even further. Organizations need to consider how to scale protection to accommodate issues like growth, as well as how to consistently track and secure workloads that span multiple cloud environments. | ||||
| 2018-09-27 08:40:00 | Hey Facebook: Quit discouraging people from using 2FA (lien direct) | Facebook should not be monetizing users' two-factor authentication (2FA) phone numbers. The practice will discourage some users from enabling 2FA, a net loss for security that makes it easier for criminals and spies to breach user accounts.The gargantuan Facebook monster is determined to gobble up every little bit of data about you, including what phone number you register for 2FA - then using that phone number to manipulate you with targeted advertising, according to reporting by Kashmir Hill yesterday at Gizmodo. | ||||
| 2018-09-25 13:42:00 | BrandPost: Malicious Tactics Have Evolved: Your DNS Needs to, Too (lien direct) | Unfortunately, as cyberthreats have evolved, over 86% of companies that leave DNS unmonitored have not modernized their DNS to help thwart malware before malicious adversaries exploit the glaring hole on the network. This blog looks at the ways threats have evolved to take advantage of legacy DNS, and what organizations should do now to increase their defenses and reduce their attack surface.Remember when cyberattacks were delivered via faxes from Nigerian princes? Although the objective – separating a business from its money – hasn't changed much, the methodologies certainly have. In the 80s and 90s, when enterprise networks were beginning to connect to the internet, DNS was simply the phone book that translated domain name to IP address. Soon enough, bad actors evolved from phreaking to phishing, dropping telephone scams in favor of the rapidly spreading internet, bombarding users with seemingly innocuous emails whose goal was to harvest network account and password information to gain inside access to applications, data, and ultimately money. | Malware | |||
| 2018-09-25 10:40:00 | IDG Contributor Network: The potential costs of cybercrime that can\'t be calculated (lien direct) | Analysis of the cost of cyberattacks often comes with a price tag attached. We regularly read reports highlighting the average and cumulative costs of data breaches, and those figures can be staggering, such as in a Juniper Research report that asserts the global cost of breaches could exceed $2 trillion by next year. While such whopping estimates rightfully garner attention, often overlooked is an even deeper and more jarring consideration - the relationship between information and cyber security and our physical security. Cybersecurity risk often is treated as a nebulous, abstract concept. Except for those working on the front lines as a security practitioner, it is easy to make a distinction between our digital and our physical environments - our homes, our offices, the park where we take our children and grandchildren. We read about cyberattacks in the headlines, but it probably does not rate as visceral of a reaction as when we read about a physical assault or a bank robbery, where the imagery that springs to mind is more harrowing and personal. Yet, as the volume of cyberattacks continues to rise and the attack methods of cybercriminals becomes more wide-ranging and less predictable– and more potent - the barrier between our digital and physical worlds is becoming thinner and more fragile. Increasingly, the possibility of kinetic attacks - those that can start as cyber incidents but turn out to be a precursor or conduit to physical attacks - are commanding more and more of our attention and vigilance. | ||||
| 2018-09-25 08:20:00 | (Déjà vu) First known malicious cryptomining campaign targeting Kodi discovered (lien direct) | Is your Kodi secretly mining Monero? Yes, sadly some cyber thugs have weaponized the media streaming app by hiding malware in Kodi add-ons. Researchers discovered the first known malicious cryptomining campaign to be launched via the Kodi platform. There are still about 5,000 victims unknowingly mining Monero via their Kodi for the cyber thugs.Ah, man, say it ain't so.Despite Kodi malware scare stories, there's been only one known time that malware was distributed via a Kodi add-on. But that hasn't stopped some anti-piracy groups from claiming Kodi was being used to distribute malware. [ Get inside the mind of a hacker, learn their motives and their malware. | Sign up for CSO newsletters. ] | Malware | |||
| 2018-09-25 08:20:00 | (Déjà vu) First known malicious cryptomining campaign targeting Kodi (lien direct) | Is your Kodi secretly mining Monero? Yes, sadly some cyberthugs have weaponized Kodi by hiding malware in Kodi add-ons. Researchers discovered the first known malicious cryptomining campaign to be launched via the Kodi platform. There are still about 5,000 victims unknowingly mining Monero via their Kodi for the cyberthugs.Ah man, say it ain't so. Despite Kodi malware scare stories, there's been only one known time that malware was distributed via a Kodi add-on. That hasn't stopped some anti-piracy groups from claiming Kodi was being used to distribute malware.For example, after a watching a video interview filmed at RSA about “how malware is growing on the Kodi/XMBC platform,” Torrent Freak scoffed. The group the interviewee worked with had been putting out Kodi-related malware scare stories to promote anti-piracy. Despite the alarming claims made which were short on actual facts, as far as Torrent Freak knew, only one Kodi addon had ever been used for DDoS purposes and that was back in 2017. The XBMC Foundation president had not heard of malware in a video stream and a threat analyst at BitDefender had not seen any malware in a video stream in the wild since in 2005. | Malware Threat | |||
| 2018-09-25 03:00:00 | The Sony hacker indictment: 5 lessons for IT security (lien direct) | In August 2018, the US Department of Justice (DoJ) unsealed the indictment of a North Korean spy, Park Jin Hyok, whom they claim was behind the hack against Sony and the creation and distribution of the WannaCry ransomware. The 170-plus-page document was written by Nathan Shields of the FBI's LA office and shows the careful sequence of forensic analysis they used to figure out how various attacks were conducted. | Hack | Wannacry | ||
| 2018-09-23 08:33:00 | Brewery became victim of targeted ransomware attack via job vacancy ad (lien direct) | You may not need a cautionary tale about opening email attachments, but this story is a reminder that you don't have to be the biggest and most well-known company to become the victim of a targeted ransomware attack; just look what happened to a small Scottish brewery.Arran Brewery in Scotland advertised job vacancies on its site; yet after the company filled the most current vacancy for a credit control and finance assistant, resumes from around the world started pouring in.The brewery's managing director Gerald Michaluk told the BBC, “Out of the blue we started getting applicants for the post from all over the country and the world. I assumed one of my colleagues had advertised the post. However, this was not the case.” | Ransomware | |||
| 2018-09-21 08:10:00 | Apple\'s dropping Back To My Mac Remote Access. Here\'s an Alternative, Currently Discounted. (lien direct) | Apple is dropping the Back To My Mac remote access feature, and in a recent support document they urge you to be prepared by looking for alternatives.RemotePC by iDrive is a full-featured remote access solution that lets you connect to your work or office computer securely from anywhere, and from any iOS or Android device. Right now, their 50 computer package is 90% off or just $6.95 for your 1st year. So if you need an alternative to Back To My Mac, or have been thinking about remote access, now is a good time to consider RemotePC. Learn more about it here. | ||||
| 2018-09-19 07:00:00 | BrandPost: Cybercriminals Shift Tactics to Keep a Low Profile (lien direct) | Over the past several years, cyberattacks have become more targeted and sophisticated. Cybercriminals have begun to augment their attacks with advanced technologies, such as machine learning and automation, to increase the speed and efficiency of attacks, as well as to expand the number of potential victims by being able to identify and target multiple vulnerabilities. They have also expanded pay-as-you-go “as a service” attack models to make it easier to proliferate attacks. Cybercriminals have also demonstrated their increased prowess at highly-disruptive public attacks, taking large numbers of organizations, and even segments of the Internet, offline on a regular basis. However, while tactics such as DDoS and ransomware can have a major impact on a network, their disruptive nature typically leads to fairly quick remediation efforts. | Ransomware Guideline | |||
| 2018-09-19 06:14:00 | (Déjà vu) State Department confirms breach of unclassified email system (lien direct) | The U.S. State Department confirmed it suffered a data breach that exposed employee data; the breach affected the State Department's unclassified email system.It's not like the agency suddenly decided to tell the public about the breach, though. The incident came to light only after Politico got hold of a Sept. 7, 2018, “Sensitive but Unclassified” notice about the breach.After a State Department spokesperson confirmed the compromise of its email system, Politico was told, “This is an ongoing investigation, and we are working with partner agencies, as well as the private sector service provider, to conduct a full assessment.” | Data Breach | |||
| 2018-09-19 06:14:00 | (Déjà vu) State Department confirms breach of unclassified email system, employee data exposed (lien direct) | The U.S. State Department confirmed it suffered a data breach that exposed employee data; the breach affected the State Department's unclassified email system.It's not like the agency suddenly decided to tell the public about the breach; the incident only came to light after Politico got hold of a Sept. 7 “Sensitive but Unclassified” notice about the breach.After a State Department spokesperson confirmed the compromise of its email system, Politico was told, “This is an ongoing investigation and we are working with partner agencies, as well as the private sector service provider, to conduct a full assessment.” | Data Breach | |||
| 2018-09-18 07:44:00 | (Déjà vu) Sophisticated mobile spyware Pegasus found in the US and 44 other countries (lien direct) |
In a new report, Citizen Lab researchers warned that sophisticated mobile spyware, dubbed Pegasus - made and sold by the Israeli company NSO Group - has been found not only on Androids and iPhones in countries with questionable human rights protections, but also in the U.S. The researchers believe this cross-border surveillance likely breaks the law in the U.S. and other countries.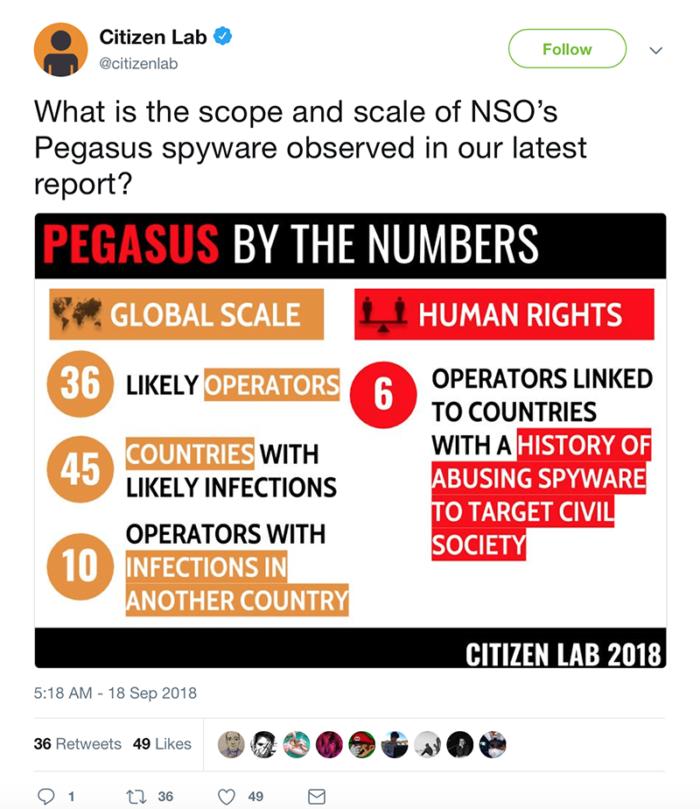 Citizen Lab via Twitter
To become an NSO Pegasus infection victim, the operator has to trick a person into clicking a link that then delivers a chain of zero-day exploits and secretly installs Pegasus on the phone. After the malware installs on the target's iPhone or Android phone without the user's knowledge, it is then capable of spying via the phone's camera and microphone. It can also steal text messages, passwords, photos, contact list, calendar events, and much more. Citizen Lab via Twitter
To become an NSO Pegasus infection victim, the operator has to trick a person into clicking a link that then delivers a chain of zero-day exploits and secretly installs Pegasus on the phone. After the malware installs on the target's iPhone or Android phone without the user's knowledge, it is then capable of spying via the phone's camera and microphone. It can also steal text messages, passwords, photos, contact list, calendar events, and much more. |
Malware | |||
| 2018-09-18 07:44:00 | (Déjà vu) Sophisticated mobile spyware Pegasus found in US and 44 other countries (lien direct) | In a new report, Citizen Lab researchers warned that sophisticated mobile spyware, dubbed Pegasus – made and sold by the Israeli company NSO Group – has been found not only on Androids and iPhones in countries with questionable human rights protections, but also in the US. The researchers believe this cross-border surveillance likely breaks the law in the US and other countries.To become an NSO Pegasus infection victim, the operator has to trick a person into clicking a link which then delivers a chain of zero-day exploits and secretly installs Pegasus on the phone. After the malware installs on the target's iPhone or Android phone without the user's knowledge, it is then capable of spying via the phone's camera and microphone; it can also steal text messages, passwords, photos, contact list, calendar events and much more. | Malware | ★★★★★ |
To see everything:
Our RSS (filtrered)
