What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2016-09-15 04:49:00 | The best messaging apps with end-to-end encryption (lien direct) | There is a growing consciousness about the desire to keep one's messages private. Some are concerned about hackers, or worry about the government spying on them, but most people just agree with the general principle that what you say in your chat conversations ought to stay between you and the people you chat with.It's not a pleasant idea to think that your messages could be archived for perpetuity on a large company's server or analyzed by some algorithm. The quest for privacy has birthed a whole generation of apps that promise to give you exactly that. Services like Telegram and Signal have turned the phrase “end-to-end encryption†into a popular discussion. We're here to help you figure out what this is all about and which apps to try.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-15 03:22:00 | Awareness training: How much is too much? (lien direct) | Security experts agree that humans are the weakest link in the security chain. Virtually all of them agree that security awareness training can strengthen many of those weaknesses.But how best to do that can generate some debate.Lysa Myers, a security researcher at ESET, summarized in a recent post what she said was a collective message from several presentations at the recent Black Hat conference: While it is possible to train employees to be "hyper-vigilant, it can create more problems than it solves.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-15 03:10:00 | 7 ways to avoid alert fatigue (lien direct) | So much noise Image by ThinkstockAs a company grows, more tools are required, and with more tools come more alerts and often a breakdown of processes and procedures to handle them. Soon enough, the alerts coming from each of your systems and tools sound like an obnoxiously loud cocktail party, everyone having different conversations about different things. As a result, Security and DevOps teams become so desensitized to these alerts that even when the system flags a truly anomalous activity, it may get ignored due to burnout.To read this article in full or to leave a comment, please click here Image by ThinkstockAs a company grows, more tools are required, and with more tools come more alerts and often a breakdown of processes and procedures to handle them. Soon enough, the alerts coming from each of your systems and tools sound like an obnoxiously loud cocktail party, everyone having different conversations about different things. As a result, Security and DevOps teams become so desensitized to these alerts that even when the system flags a truly anomalous activity, it may get ignored due to burnout.To read this article in full or to leave a comment, please click here |
||||
| 2016-09-14 23:47:00 | Gmail outage for business users lasted over 12 hours (lien direct) | Gmail service for users of the Google for Work cloud-based productivity suite was down for over 12 hours on Wednesday, apparently affecting users in a number of countries including the U.S.Google reported early Thursday that the problem was resolved for the vast majority of affected customers, and it would be working individually with the rest of them. It said it would provide a more detailed analysis of the incident to customers once its internal investigation is completed.The company first acknowledged the problem on its Apps Status Dashboard at 8:16 a.m. Pacific Time on Wednesday, stating that it is investigating reports of an issue with Gmail. “Based on reports, it affects only Google for Work Gmail users," Google said. Affected users were redirected to a page with 'Service not available, contact your administrator.'To read this article in full or to leave a comment, please click here | ||||
| 2016-09-14 12:50:00 | Government, carmakers more worried than ever about vehicle cyber attacks (lien direct) | Automakers and legislators appear to be coming together on the need for greater cybersecurity for vehicles that are increasingly connected to the internet and controlled by ever-more sophisticated computer systems and software.Volkswagen today announced it will form a cybersecurity company headed by Yuval Diskin, the former head of Israel's security agency. The company, CyMotive Technologies, will be 40% owned by the German automaker and the rest will be controlled by Diskin and two other former leaders in Israel's Shin Bet intelligence agency.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-14 10:06:00 | Banks find big innovation payoff in hackathons (lien direct) | Vishal Srivastava pulled an all-nighter coding one weekend building a mobile application that turned the onerous and sometimes awkward task of settling a restaurant bill into a game. An amusing twist on credit card roulette, the software includes monsters that eat their way around the screen before settling on the photo of the victim who must pay the tab.The app, Undutchly, won the $15,000 grand prize in a hackathon held last month at Plug and Play's Tech Center in Sunnyvale, Calif, hosted by U.S. Bank and MasterCard. The competition, which included 100 developers spread across 23 teams, is part of U.S. Bank's bid to uncover new software by tapping into Silicon Valley's programming talent. "We thought, let's engage the smart folks in Silicon Valley to build solutions using APIs," Doug Nielson, U.S. Bank's senior vice president for innovation research and development, tells CIO.com.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-14 10:04:00 | Tenable brings network visibility into Google Cloud Platform (lien direct) | Tenable Network Security has integrated Tenable SecurityCenter Continuous View with Google Cloud Platform, giving administrators better visibility into what is happening within their cloud infrastructure.Cloud-based infrastructure eases IT's administrative woes and lowers operating costs, but the benefits don't count for much if there is any doubt about the security of key applications running in the cloud. While system administrators can easily spin up new services and hosts, security teams don't always know what applications and services are running in their cloud and hybrid environments or understand the risks associated with each one.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-14 08:17:00 | (Déjà vu) IDG Contributor Network: How to deal with the new Privacy Shield agreement (lien direct) | Earlier this summer the European Commission and the US Department of Justice signed the much-anticipated EU-US Privacy Shield data pact agreement. As of Aug. 1, 2016, companies and other entities in the United States are able to register with the Commerce Department, self-certifying their compliance with the Privacy Shield's principles.Many companies are still deciding whether they will self-certify because they don't completely understand what the rollout will look like and the impact it will have on data transfer and storage.Kendall Burman, a cybersecurity and data privacy counsel at Mayer Brown, offered some advice on the data transfer and storage issues companies need to be prepared for, including and extending beyond Privacy Shield. Hopefully these insights will help you to determine what is the best course of action for your enterprise in light of this new agreement.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-14 06:32:00 | IDG Contributor Network: Rolling out the new Privacy Shield agreement (lien direct) | Earlier this summer the European Commission and the US Department of Justice signed the much-anticipated EU-US Privacy Shield data pact agreement. As of August 1, 2016, companies and other entities in the United States are able to register with the Commerce Department, self-certifying their compliance with the Privacy Shield's principles. Many companies are still deciding whether they will self-certify because they don't completely understand what the rollout will look like and the impact it will have on data transfer and storage.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-14 05:19:00 | Attackers Launch DDoS Attacks And the Kitchen Sink (lien direct) | First off, full disclosure, I work for Akamai as my day job. I don't want any illusion on the point as I discuss the latest State of the Internet report that I was fortunate enough to be a part of creating. That being said, it was an interesting quarter.Last quarter shed some light on some interesting developments with regards to Distributed Denial of Service (DDOS) as attackers tried their hand at various different approaches. We hear. time and again, about DDoSdistributed denial of service attacks and theis last most recent quarter gave rise to one of significant volume. This example was a rather significant attack that was a confirmed 363 Gbps of attack traffic against a media organization customer in Europe. Nothing to sneeze at to be certain. Is your organization in a position to sustain operations while weathering an attack of this magnitude?To read this article in full or to leave a comment, please click here | ||||
| 2016-09-14 04:39:00 | A single ransomware network has pulled in $121 million (lien direct) | A single ransomware author and distributor was able to collect $121 million in ransomware payments during the first half of this year, netting $94 million after expenses, according to a report released today."Ransomware has grown over the years, and in 2015 and 2016 we really saw a serious spike," said Vincent Weafer, vice president of Intel Security's McAfee Labs.Weafer estimated that total ransomware revenues could be in the hundreds of millions."And that's on the conservative side," he said.WHAT SHOULD YOU DO: How to respond to ransomware threats Total ransomware increased by 128 percent during the first half of 2016 compared to the same period last year. There were 1.3 million new ransomware samples recorded, the highest number since McAfee began tracking it.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-14 04:27:00 | NTP reflection attacks hit record high (lien direct) | Distributed denial of service attacks that take advantage of misconfigured NTP servers were up 276 percent last quarter compared to the same time last year, reaching a new record high, according to a new report.Part of the reason for the increase is economics, said report editor Martin McKeay, security advocate at Akamai Technologies.In an NTP reflection campaign, the attacker sends a short message to an NTP server, and the NTP server replies with a significantly longer message. But instead of going back to the attacker, the response is addressed to the victim of the attack.This allows the attacker to significantly magnify the amount of traffic hitting the victim all at once.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-14 02:58:00 | 9 biases killing your security program (lien direct) | I see what I want to see Image by ThinkstockWe're not always as rational in our decision-making as we'd like to think we are. This is often true in our daily decisions; from what you'd like to eat for lunch to the bigger decisions we make, such as what kind of car to buy to where we choose to live. These cognitive biases, or deviations from rational judgement, can affect every aspect of our decision-making. It'd be foolish to think such irrational thinking doesn't lead to a distorted view of cybersecurity risks, or inaccurate judgements in defending enterprise systems. Here's a (by no means all-inclusive) list of nine such cognitive biases that security professionals should especially remain aware.To read this article in full or to leave a comment, please click here Image by ThinkstockWe're not always as rational in our decision-making as we'd like to think we are. This is often true in our daily decisions; from what you'd like to eat for lunch to the bigger decisions we make, such as what kind of car to buy to where we choose to live. These cognitive biases, or deviations from rational judgement, can affect every aspect of our decision-making. It'd be foolish to think such irrational thinking doesn't lead to a distorted view of cybersecurity risks, or inaccurate judgements in defending enterprise systems. Here's a (by no means all-inclusive) list of nine such cognitive biases that security professionals should especially remain aware.To read this article in full or to leave a comment, please click here |
Guideline | |||
| 2016-09-13 14:27:00 | Russian spies blamed for WADA hack, leaked documents confirm drug exemptions (lien direct) | On Tuesday, a group calling itself Fancy Bear, and claiming association with Anonymous, said they've hacked the World Anti-Doping Agency, and offered drug screening results as proof. Only, the leaked documents don't contain incriminating facts. If anything, they show athletes following the rules as expected.The thing about Anonymous is that anyone can claim to be associated with the brand. These days, Anonymous is nothing like it was during its prime (e.g. 2008-2012), but that doesn't stop people from resonating with their ideals and launching operations associated with the Anonymous name and symbolism.On Tuesday, during the announcement of OpOlympics, a group claiming association with Anonymous and calling themselves Fancy Bears' international hack team, claimed credit for hacking World Anti-Doping Agency (WADA).To read this article in full or to leave a comment, please click here | APT 28 | |||
| 2016-09-13 08:21:00 | IDG Contributor Network: Cyberwar is here! Offense, defense and \'special teams\' (lien direct) | If anyone is asleep at the switch and thinks cyber is just a fad or trend, then consider this: Ginni Rometty, chairman, president and CEO of IBM, recently said, “We believe that data is the phenomenon of our time. It is the world's new natural resource. It is the new basis of competitive advantage, and it is transforming every profession and industry. If all of this is true – even inevitable – then cybercrime, by definition, is the greatest threat to every profession, every industry, every company in the world.†Do I have your attention now?Analogies to NFL teams (offense, defense and special teams) as well as military special forces can be applied to organizing elite talent around a specific objective to the corporate cyber challenge each company faces.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-13 05:49:00 | ​The rise of the successful corporate psychopath (lien direct) | Businesses should undertake psychological screening to help identify 'successful psychopaths' as higher level of psychopathic traits exist among people found in the upper echelons of the corporate sector.Forensic psychologist, Nathan Brooks – who is speaking about the emergence of non-criminal psychopathy at the APS Congress in Melbourne this week – says many businesses have their recruitment screening back to front.“Too often companies look at skills first and then secondly, consider personality features,†said Brooks. “Really it needs to be firstly about the candidate's character and then, if they pass the character test, consider whether they have the right skills,†he said.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-13 05:45:00 | Empower your employees by embracing shadow IT (lien direct) | Shadow IT is often viewed as something that opens up businesses to data and security threats, leaving IT without control over business apps and services. But that attitude is changing as more businesses adopt a friendly attitude towards unconventional IT practices."Some CIOs certainly see 'shadow' IT as a negative, hence the less flattering terms 'feral' or 'rogue' IT, but more progressive CIOs know that, given today's technology and the increasing savvy of the business, it's in their best interest to embrace shadow IT," says Tracy Cashman, senior vice president and partner of WinterWyman Executive Search.Cashman says it's time for IT to embrace the fact that they can't control everything and instead, help drive innovation around IT practices so that they align with the modern reality of technology. It's about empowering users because otherwise, they'll go around IT and download the software they want to use anyway.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-13 04:00:00 | Is your security awareness training program working? (lien direct) | Employees at Axe Investment, the fictional firm of biollionaire Bobby Axelrod in Showtimes new series, Billions, were downright angry when they learned that surprise SEC raid was only a test. Axelrod, though, found the mock raid fruitful as it revealed the internal weak links of his organization. These are metrics that enterprises should be using to evaluate the success of their security awareness programs. In order for awareness training to work, it has to keep everyone in the enterprise, well, aware. A recent Wombat report revealed that in addition to the ever growing problem of phishing, employees across industries struggle with oversharing on social media, unsafe use of WiFi, and company confidential data exposure. Those ubiquitous posts pose serious risks.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-13 03:47:00 | 6 questions CISOs need to ask about containers (lien direct) | Shoring up containers Image by ThinkstockContainer technology promises greater agility and efficiency when it comes to building and deploying applications, a critical ability in this age of zero tolerance for downtime and great expectations for capabilities on demand. But with any new technology comes new risk, and security professionals must be able to accurately determine the risk-reward balance of containers for their organizations. Lars Herrmann, general manager, Integrated Solutions Business Unit at Red Hat, poses six questions CISOs must ask when evaluating container platforms.To read this article in full or to leave a comment, please click here Image by ThinkstockContainer technology promises greater agility and efficiency when it comes to building and deploying applications, a critical ability in this age of zero tolerance for downtime and great expectations for capabilities on demand. But with any new technology comes new risk, and security professionals must be able to accurately determine the risk-reward balance of containers for their organizations. Lars Herrmann, general manager, Integrated Solutions Business Unit at Red Hat, poses six questions CISOs must ask when evaluating container platforms.To read this article in full or to leave a comment, please click here |
||||
| 2016-09-13 01:20:00 | Montreal cops hunting data thieves (lien direct) | When I was a kid growing up I was always enamored with the old cops and robbers movies. I was always amazed a the criminals terrible OPSEC even at a young age. I could never fathom how they didn't get pinched with that striped shirt, mask and bag with the dollar sign on the side. Seemed like the obvious candidate back then.Times have changed. Thieves don't stand out as they could literally be anyone these days. Your personal information even has a monetary value in the darker parts of the Internet. Usually we find attackers attempting to steal information from financial institutions or even from healthcare facilities. Wherever they can get the information they need to steal as much money as they can get their hands on.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-13 00:00:00 | BrandPost: Fight Against Ransomware Takes to the Cloud (lien direct) | “How many visitors do you expect to access the No More Ransom Portal?â€This was the simple question asked prior to this law enforcement (Europol's European Cybercrime Centre, Dutch Police) and private industry (Kaspersky Lab, Intel Security) portal going live, which I didn't have a clue how to answer. What do YOU think? How many people do you expect to access a website dedicated to fighting ransomware? If you said 2.6 million visitors in the first 24 hours, then please let me know six numbers you expect to come up in the lottery this weekend (I will spend time until the numbers are drawn to select the interior of my new super yacht). I have been a long-time advocate of public cloud technology, and its benefit of rapid scalability came to the rescue when our visitor numbers blew expected numbers out of the water. To be honest, if we had attempted to host this site internally, my capacity estimates would have resulted in the portal crashing within the first hour of operation. That would have been embarrassing and entirely my fault.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-12 13:45:00 | Recent MySQL vulnerability a lesson in privilege assignments (lien direct) | A recently disclosed flaw in MySQL seems to be more about permissions than remote code execution (RCE). While the flaw is a bit over-hyped, the underlying problems are legit concerns for organizations that just slap a web server together and toss it into production.In 2003, a vulnerability in MySQL was disclosed, which if exploited, allows an attacker to create world-writable files and elevate the mysql user to root via SELECT * INFO OUTFILE operator to overwrite the my.cnf file.Now, thirteen years later, a disclosure from legalhackers.com reports a similar issue, where an attacker can chain several configuration problems together in order to inject custom settings into a my.cnf file.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-12 11:05:00 | If an Infosec policy falls in the forest (lien direct) | When you are building an Information Security practice you need a solid governance structure in place. For those of you who might not be familiar we can look at it a more accessible way. If you are building a house you need a solid foundation otherwise the thing will collapse.Much in the same vein, if you do not have a solid set of policies, you are destined to fail. All is not lost as there are all sorts of resources that are available to help you online. The key point to remember is that with anything you find should never be used verbatim. If you cut and paste a policy you find online and swap the letterhead you should just hang up your tin star now. Do not pass go. Do not collect $200.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-12 09:52:00 | CISO Desk Reference Guide (lien direct) | Are you an aspiring, recently hired or promoted CISO looking for the definitive how-to guide for your position? Look no no further. An experienced CISO along with two security subject matter experts have authored a comprehensive modern day text -- 'CISO Desk Reference Guide: A practical guide for CISOs' -- which covers risk management, compliance, audit, IT security disciplines, cybersecurity extending to IoT (internet of things) devices, cyber insurance, staffing, board concerns, and everything in between.The three authors -- Bill Bonney, Gary Hayslip, and Matt Stamper -- state their decision to write the book came from the shared realization that the dramatic escalation in cyber threats was not going to peak any time soon. A recent report from Cybersecurity Ventures aligns with their thinking -- and predicts cybercrime damages will cost the world $6 trillion annually by 2021, up from $3 trillion last year.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-12 04:33:00 | Trouble spotted on the network (lien direct) | We had a scare the other day with a critical cross-site scripting (XSS) attack that seemed to be entirely contained - source and destination - on our own network. Tracking it down and resolving the issue were fairly routine procedures, but it's worth noting how it's possible to spot potential security problems when you don't have a world-class security operations center (SOC) that's staffed with skilled analysts and stuffed with large-screen monitors and all the bells and whistles. Trouble Ticket At issue: A cross-site scripting attack seems to be targeting the source code repository.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-12 03:32:00 | Emerging technologies are poking holes in security (lien direct) | Accelerated change challenges change management, security DevOps and emerging technologies that enable business innovation and opportunities demand fast, frequent change from the enterprise. The speed and regularity as well as the kinds of change challenge change management and ultimately security. To secure the enterprise in environments of unwieldy change, the business needs to know how each new technology affects change management and the organization's security defenses. Organizations can then begin to evolve change management and security to close those gaps and avoid impacts on security. Emerging technologies such as DevOps, IoT, automation/intelligent software, information technology service partnering, cloud computing and BYOD all straighten out the curves in the race to make changes that propel the enterprise forward.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-09 14:47:00 | IDG Contributor Network: 9/11: My story (lien direct) | On Sept. 11, 2001, at 6:45 am, AA flight #1017 lifted off LaGuardia runway #4 on its way to Minneapolis. As it made a lazy right turn over Manhattan and past the twin towers, I remarked to myself how crystal clear the sky was. Having lived in NYC for 25 years, I remembered many peaceful fall mornings like that. Our flight was completely uneventful until we reached MSP airport where chaos was in the air and on the monitors. People were hoping that a small plane had hit the North Tower, but I knew it was a terrorist attack. On such a clear day I knew that no pilot could make that mistake. I didn't know it would take me a week to get back home.It feels like a lifetime has passed since 9/11, although it has been only 15 years. We lost friends and neighbors. A pall hung over the city for months and I was hesitant to revisit the place where I had worked as an information security consultant and trainer only a few years earlier. Recently, visiting the new Freedom Tower gave me hope and thanks in our ability to bring out the good in people.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-09 10:16:00 | Memories of 9/11: More than lost buildings (lien direct) | Like many, my memories of 9/11 are personal and still vivid. At the time, I was Chief of the Technology Crime Unit of the Nassau County District Attorney's Office, the county immediately to the east of New York City. I always listened to local news or talk radio in my office, and on that morning I heard the announcement of a plane striking the World Trade Center.As most people, I interpreted it to be a stray two-passenger plane that bounced off one of the Towers. Still, I was curious enough to walk downstairs and enter the deputy chief investigator's office to watch his TV.Put four or five prosecutors and investigators in a room watching events like this unfold in real time, and the inevitable analysis of what we observed immediately began. The massive hole in the side of North Tower belied any possibility of this being a small plane. Moreover, the size and position of the impact point led us all to begin wondering if this was an intentional act.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-09 08:43:00 | Why you need tiered security training for IT staff (lien direct) | In an earlier post discussing security awareness training, I discussed the failings of general security awareness training for end users at companies. When it comes to training the IT staff about security, there are also some gaps. A lot of effort goes into certification and advanced training for specified security team members, but that leaves out a lot of other IT staff members (the help desk, for example), often the front-line team when it comes to dealing with cyber-attacks on end users. In this episode of Security Sessions, I spoke once again with Bill Rosenthal, CEO of Logical Operations, about the difference in training methods for IT staff members and IT security team, as well as the need for multi-vendor certification training. Among the highlights of the video are the following sections: 0:43 The distinction between security awareness training and security training 2:00 How IT staff security training differs from general employee awareness training. 03:08 Why do most companies feel that cyber-security training is a specialized function? 4:11 Certifications: Why most training is limited to one piece of software or hardware, and not multi-vendor. 5:43 The need for going beyond theoretical security training. 7:19 Why there needs to be more active threat analysis training at companies. 8:19 Advice for CSOs on how to reduce costs for security training.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-09 01:00:00 | White House picks a CISO and, spoiler alert, I didn\'t get the job (lien direct) | There simply isn't an emoji to capture my emotion at a moment like this. I didn't even get a rejection letter. The White House first announced that they were seeking a candidate in February 2016. Yesterday, The White House selected their first CISO candidate yesterday and it wasn't me. Of course, I'm being facetious. The small entanglement of being a Canadian may have been a limiting factor in my candidacy that never was.This position was created as an output from the Cybersecurity National Action Plan (CNAP). But, it should be noted that this is a CISO position that comes with funding. The Information Technology Modernization Fund (ITMF) was created to provide $3.1 billion to drag US government IT kicking and screaming into the future. I know, I had to pause after I read that there is funding the first time too.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-08 13:05:00 | Clinton email highlights frustrating reality of bypassed IT policies (lien direct) | An email recently released by House Democrats isn't just a political response to Hillary Clinton's usage of personal technology while Secretary of State.The email between Clinton and General Colin Powell is a perfect example of what some call Shadow IT, and a common problem IT teams face daily with executives and senior officials.In January of 2009, Secretary Clinton emailed General Colin Powell, one of her predecessors, with a question. What were the restrictions placed on him with regard to his usage of a BlackBerry? Did he use one in his personal office?To read this article in full or to leave a comment, please click here | ||||
| 2016-09-08 12:24:00 | Brazzers gets the shaft in data breach (lien direct) | Years ago, I remember a time when water was free. You would just drink it from the tap and you had to pay for your 'dirty magazines'. Times have changed to say the least. I was in the market the other day and they were selling a bottled water that was advertised as being a good source of “oxygenâ€. I didn't have the heart to counter and argue about the possible dangers of dihydrogen monoxide poisoning. But, I digress. Nowadays you can get your porn fix for free online. Well, there can be a cost. This week porn site aficionados who frequent the adult site, Brazzers, found their personal bits swinging in the breeze after a data breach came to light. Almost 800,000 user accounts were compromised in a data breach that apparently took place in 2012.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-08 11:00:00 | Security Recruiter Directory (lien direct) | Looking for a qualified candidate or new job? CSO's security recruiter directory is your one-stop shop. The recruiters listed below can help you find your next Chief Security Officer (CSO), Chief Information Security Officer (CISO), or VP of Security and fill hard-to-hire positions in risk management, security operations, security engineering, compliance, application security, penetration testers, and computer forensics, among many others. If you're a security recruiting firm, we want your information! Our goal is to provide the most complete recruiter resource available, but to do that we need your assistance. Please send the name, contact info and a few sentences about your company and its specialties to Amy Bennett (abennett@cxo.com).To read this article in full or to leave a comment, please click here | ||||
| 2016-09-08 10:27:00 | IDG Contributor Network: Woe is IT, the pain of risk management (lien direct) | As I've spoken with leaders in the security industry over the course of developing this blog, I've learned a lot about the modern CISO. More often, enterprises are looking to hire leaders who not only have a background in IT but also have the required business acumen to understand risk.Risk assessment and risk management are key elements in a successful security strategy because the threat landscape continues to expand with the explosion of IoT. Devices are everywhere, and everyone is connecting to the network causing headaches for security management professionals.LogMeIn recently polled 500 IT professionals on the array of challenges ongoing in their security threat landscape. Not surprisingly, cloud security, devices, and user behavior are some of the most often reported pain points for IT professionals.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-08 06:00:00 | Ransomware prevalent in cloud-based malware (lien direct) | Cloud-based filesharing, collaboration and social networking applications are common vectors for malware infections, a large portion of of which are ransomware delivery vehicles, according to a report released today.Javascript exploits and droppers, Microsoft Office macros, and PDF exploits make up 43.7 percent of the total detected cloud malware, said Jamie Barnett, CMO at Netskope, the company that released the report."These are typical ransomware delivery vehicles," she said.Cloud-based applications such as Dropbox can be used to spread malware in a couple of different ways. Attackers can upload the infected files to the cloud service, then share them with victims. Since there are many legitimate users of these services, they are not typically blocked by enterprises.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-08 05:06:00 | How it works: Iris scanning improves smartphone security (lien direct) | You hold your smartphone in front of your face, the angle and distance guided by on-screen feedback. It flashes near-infrared (NIR) light into your eyes -- a brief dull-red glow. Your smartphone recognizes one or both of your irises, and unlocks itself.At least, that's the new smartphone login scenario. Previously seen mostly in military devices and fixed installations, iris scanning is joining other biometric authentication methods (such as fingerprint scanning, facial recognition and voice recognition) intended to move mobile devices beyond the limitations of password-based security.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-08 05:04:00 | Microsoft\'s tin ear for privacy (lien direct) | Microsoft keeps making news of the privacy front, and not in a good way.Much has been made of the way Cortana in Windows 10 may invade your privacy by collecting data such as the words you speak and the keys you strike. Though that is disturbing to many people, Microsoft has responded by noting that Cortana needs to know that information in order to fulfill users' requests. That's true, but beside the point. The real issue, as my fellow columnist Steven J. Vaughan-Nichols points out, is that it's extremely difficult, if not impossible, to completely turn off Cortana.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-08 03:34:00 | Hack the vote: Experts say the risk is real (lien direct) | You should be worried about the November election. Not so much that the candidates you support won't win, but about the risk that the “winners†may not really be the winners, due to hackers tampering with the results.Or, that even if the winners really are the winners, there will be enough doubt about it to create political chaos.This is not tinfoil-hat conspiracy theory. The warnings are coming from some of the most credible security experts in the industry.Richard Clarke, former senior cybersecurity policy adviser to presidents Bill Clinton and George W. Bush, wrote recently in a post for ABC News that not only are US election systems vulnerable to hacking, but that it would not be difficult to do so.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-08 03:22:00 | How identity management helps protect what ails patients (lien direct) | Empowering the patient Image by ThinkstockThere is serious personal risk associated with a healthcare data breach, especially with multiple connected devices and health record systems generating and storing a patient's sensitive health data. Every person interacting with an online system needs a digital identity, and it should be authenticated in real time, so that unusual behavior can be detected at any time, whether at login or midway through a session.To read this article in full or to leave a comment, please click here Image by ThinkstockThere is serious personal risk associated with a healthcare data breach, especially with multiple connected devices and health record systems generating and storing a patient's sensitive health data. Every person interacting with an online system needs a digital identity, and it should be authenticated in real time, so that unusual behavior can be detected at any time, whether at login or midway through a session.To read this article in full or to leave a comment, please click here |
||||
| 2016-09-08 03:00:00 | Build security into software development (lien direct) | Devops is transforming how developers and operations teams work together to deliver better software faster. At its core, devops is about automation. When several tasks in development, testing, and deployment are automated, developers can make changes to code and deploy to production frequently. Amazon, a leading devops proponent, at one point claimed to have more than 1,000 deployments a day.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-07 20:38:00 | Humpday data breach report (lien direct) | It has been a helluva week to say the least. But, before I get to the cavalcade of compromised companies let's roll back the clock to July 2012. Back that summer I was simply gobsmacked by the number of breaches that were cropping up in the news. It was somewhat daunting at the time. Just the sheer volume of records that were leaked was troubling.I was wondering when the bleeding would stop. I thought I was being witty when I dubbed the breaches the “Summer of Breachâ€. Only, it didn't stop there. Here we are 4 years later and I'm having some flashbacks regarding at least a couple of the reported breaches. Now, I've decided to start tracking breaches with Wednesday reporting hence, humpday.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-07 11:12:00 | BrandPost: Private Cloud Security (lien direct) |
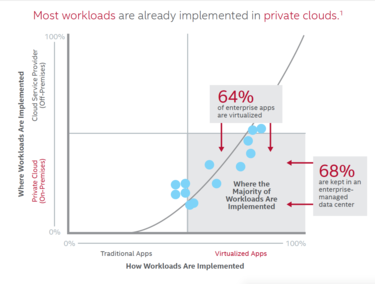 If you are like most organizations, the majority of your apps have been virtualized but are still running in your own data center[1]. IT has been busy renovating the data center to take advantage of the increased agility and reduced operating costs of a private cloud. You may have virtualized data-center network and storage as well, adding automation and orchestration, resulting in a software-defined data center (SDDC) that can reduce costs up to 75% and decrease deployment times from weeks to minutes.[2]To read this article in full or to leave a comment, please click here
If you are like most organizations, the majority of your apps have been virtualized but are still running in your own data center[1]. IT has been busy renovating the data center to take advantage of the increased agility and reduced operating costs of a private cloud. You may have virtualized data-center network and storage as well, adding automation and orchestration, resulting in a software-defined data center (SDDC) that can reduce costs up to 75% and decrease deployment times from weeks to minutes.[2]To read this article in full or to leave a comment, please click here |
||||
| 2016-09-07 09:01:00 | Half of network management systems vulnerable to injection attacks (lien direct) | Cross-site scripting and SQL injection attacks are well-known threats for public-facing Web applications, but internal systems can be attacked as well. For example, about half of network management systems studied had these vulnerabilities, according to a report released today.It all comes down to input validation, or lack of it, said Deral Heiland, research lead at Boston-based Rapid7, Inc. and one of the authors of the report.Network management systems are in regular communication with the devices on a company's network. But, because the communications are machine-to-machine people sometimes forget that the inputs still need to be checked to make sure there's nothing weird or malicious in there.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-07 04:21:00 | IDG Contributor Network: How to get a more cost-effective cyber insurance policy (lien direct) | A security practitioner who isn't worried about a breach is a rare find in the industry. Even if you are taking all the right steps to protect your assets, there is still a pretty good chance that your network will be compromised.For those who are new to security, you might be asking, "What are the right steps?" Jason McMahan, director of technology at Concept Technology, offered tips on how to to help mitigate the risk of an attack and obtain a more cost-effective insurance policy.McMahan said, "Cyber-security protection and liability insurance have a symbiotic relationship. By showing underwriters that strides are being made to reduce cyber-liability and keep data safe and easily recoverable, businesses may be able to secure lower premiums for their insurance."To read this article in full or to leave a comment, please click here | ||||
| 2016-09-07 04:00:00 | Security Solved: Company says their tech renders servers hack proof (lien direct) | Salted Hash has obtained an interesting press release from a security vendor that's running a contest.A company calling itself HackProof Systems Inc. has launched a contest that will pay $5,000 to first person who can crack a server protected by their technology. The company makes no mention of any rules of engagement, nor do they detail what the technology does exactly.From today until midnight on September 30, first person who is able to compromise the server located at 96.92.82.82 and discovers the "Golden Token" will be rewarded with $5,000 USD. The token has instructions, which must be followed exactly in order for the prize to be claimed.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-06 13:23:00 | BrandPost: Are fingerprint IDs really secure? (lien direct) | It's been nearly three years since Apple introduced its iPhone 5S in September 2013 and, with it, the phone's integral Touch ID fingerprint sensor. Fingerprint scanning as a method of user authentication existed well before the iPhone 5S, but the popular device brought this biometric security technology from the cybersecurity fringes into the mainstream. Today, the use of fingerprint scanners has become commonplace across the consumer-device landscape, joining more sophisticated systems deployed to secure corporate systems and facilities. On balance, the proliferation of these scanners has been a positive addition to the arsenal of cybersecurity tools, but they are by no means a “magic bullet†solution for authenticating users and granting them access to sensitive systems and data.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-06 13:08:00 | BrandPost: Why cyberpreparedness lags. 3 security experts weigh in (lien direct) | The barrage of recent headlines about cybersecurity breaches at prominent companies and government institutions should have at least one silver lining: It will prompt organizations to finally get their security act together. Or so you would think, but new research indicates that the opposite may be true. NTT Com Security's 2016 Global Threat Intelligence Report found that 77% of organizations say they don't have a formal security incident response plan in place, a number that is actually up slightly from last year. Most fail to implement basic security measures like patching and updating software. More than 12% of vulnerabilities that NTT log analysis discovered were more than five years old.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-06 10:04:00 | Can cybersecurity save the November elections? (lien direct) | The Federal Bureau of Investigation's disclosure earlier this month that foreign hackers had infiltrated voter registration systems in Illinois and Arizona came as no surprise to some cybersecurity experts.“Given where cybercrime has gone, it's not too surprising to think about how information risks might manifest themselves during the election season to cause some level of either potential disruption, change in voting, or even just political fodder to add the hype cycle,†says Malcolm Harkins, global chief information security officer at network security firm Cylance.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-06 07:32:00 | What is phishing success? (lien direct) | In putting together awareness programs for dozens of clients, the potential to integrate phishing simulations always comes up. For the most part, it seems like a staple of awareness programs. But when the concept of phishing is raised, I always ask, “Why?â€Yes, the question potentially costs me money. Also while most people perceive the phishing simulations as a direct way to decrease phishing susceptibility, the decrease might not be relevant or significant. So when I looked at a recent CSO article that asked security experts what they thought “success†meant when it came to phishing simulations, I was a frustrated.To read this article in full or to leave a comment, please click here | ||||
| 2016-09-06 05:12:00 | How blockchain will disrupt your business (lien direct) | Like mobile and cloud, blockchain - first implemented in the original source code of bitcoin in 2009 - stands poised to profoundly disrupt business. If it lives up to its promise, it won't just be financial institutions that are disrupted."If you can transfer money or something of value through the internet just like another form of data, what else can you do with it? It provides a way to establish trust in the digital world," says Angus Champion de Crespigny, Financial Services Blockchain and Distributed Infrastructure Strategy Leader, Ernst & Young. "How do you ensure something is the original copy of something on the internet? Prior to blockchain technology, you couldn't."To read this article in full or to leave a comment, please click here | Guideline |
To see everything:
Our RSS (filtrered)
