One Article Review
| Source | |
|---|---|
| Identifiant | 1100750 |
| Date de publication | 2019-05-09 10:30:01 (vue: 2019-05-09 17:01:04) |
| Titre | Dissecting Weird Packets |
| Texte | I was investigating traffic in my home lab yesterday, and noticed that about 1% of the traffic was weird. Before I describe the weird, let me show you a normal frame for comparison's sake.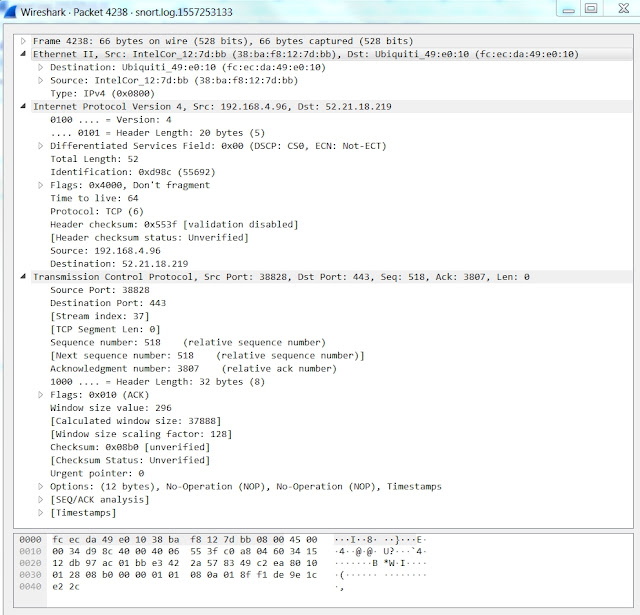 This is a normal frame with Ethernet II encapsulation. It begins with 6 bytes of the destination MAC address, 6 bytes of the source MAC address, and 2 bytes of an Ethertype, which in this case is 0x0800, indicating an IP packet follows the Ethernet header. There is no TCP payload as this is an ACK segment.You can also see this in Tshark.$ tshark -Vx -r frame4238.pcapFrame 1: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) Encapsulation type: Ethernet (1) Arrival Time: May 7, 2019 18:19:10.071831000 UTC [Time shift for this packet: 0.000000000 seconds] Epoch Time: 1557253150.071831000 seconds [Time delta from previous captured frame: 0.000000000 seconds] [Time delta from previous displayed frame: 0.000000000 seconds] [Time since reference or first frame: 0.000000000 seconds] Frame Number: 1 Frame Length: 66 bytes (528 bits) Capture Length: 66 bytes (528 bits) [Frame is marked: False] [Frame is ignored: False] [Protocols in frame: eth:ethertype:ip:tcp]Ethernet II, Src: IntelCor_12:7d:bb (38:ba:f8:12:7d:bb), Dst: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) Destination: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) Address: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) This is a normal frame with Ethernet II encapsulation. It begins with 6 bytes of the destination MAC address, 6 bytes of the source MAC address, and 2 bytes of an Ethertype, which in this case is 0x0800, indicating an IP packet follows the Ethernet header. There is no TCP payload as this is an ACK segment.You can also see this in Tshark.$ tshark -Vx -r frame4238.pcapFrame 1: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) Encapsulation type: Ethernet (1) Arrival Time: May 7, 2019 18:19:10.071831000 UTC [Time shift for this packet: 0.000000000 seconds] Epoch Time: 1557253150.071831000 seconds [Time delta from previous captured frame: 0.000000000 seconds] [Time delta from previous displayed frame: 0.000000000 seconds] [Time since reference or first frame: 0.000000000 seconds] Frame Number: 1 Frame Length: 66 bytes (528 bits) Capture Length: 66 bytes (528 bits) [Frame is marked: False] [Frame is ignored: False] [Protocols in frame: eth:ethertype:ip:tcp]Ethernet II, Src: IntelCor_12:7d:bb (38:ba:f8:12:7d:bb), Dst: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) Destination: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) Address: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) |
| Envoyé | Oui |
| Condensat | 0000 0010 0020 0030 0040 02 0x0038 0x0800 0x45 0xd98c 0xd98d 147 15 2003 2018 3339 38828 4238 4241 443 4a 664 7f 802 :this about acknowledgement activity address addresses again along also analysis anything appeared:you appears appendix approach are ask assistance assumption attempts b*w ballpark basically because before beginning begins being bejtlich believe below:dlt better blogspot blok bold bolded book bottom bridged broke but byte bytes can capture captured capturing case caused certain change clicking clue com comment comparative comparison complicated: control copyright corresponds corrupted could created data decides decimal decode defaults destination did different direction:$ display dissecting dlt doesn don dsap dst each earlier ec editcap either enough entry environment especially ethernet ethertype even exactly excerpt expect fact fairly far field filter first fit fix folks followed follows format found fpr frame frames get had handle happening has have header headers helpful helpfully here high his host how however hypothesize identical ieee incremented indicate instead interpret ipv4 ipx jwhat know lab layer len>y length let like line link linux listed llc mac making manual may meaning meant more much netsniff next nibbles nic not note notice novell now number=x numbers odd one open opened operating options org other out overall packet packets page parts payload pcap pcapnext per perfectly places ports preferences preferences:next presented presumed problem prompted protocol ps: purposes rather raw really recognized refer researching resembling results retransmission returned richard right running sake same saw see seeing seem seen segment selecting sense sequence share shown shown:after shows similar size sniffing softare software some sort source src ssap suggested sure system take taosecurity tcp tell telling than thank them then these think though timestamp too total trace traffic treat tried turns twitter two type understand unusual used user user0 value values version very virtualbox wanted way weird went what when where which wire wireshark words worried would www yellow |
| Tags | |
| Stories | |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.