One Article Review
| Source | |
|---|---|
| Identifiant | 2713131 |
| Date de publication | 2021-04-29 04:15:50 (vue: 2021-04-29 09:05:33) |
| Titre | Anatomy of how you get pwned |
| Texte | Today, somebody had a problem: they kept seeing a popup on their screen, and obvious scam trying to sell them McAfee anti-virus. Where was this coming from?In this blogpost, I follow this rabbit hole on down. It starts with "search engine optimization" links and leads to an entire industry of tricks, scams, exploiting popups, trying to infect your machine with viruses, and stealing emails or credit card numbers.Evidence of the attack first appeared with occasional popups like the following. The popup isn't part of any webpage.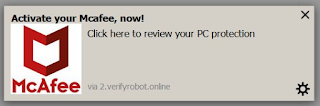 This is obviously a trick. But from where? How did it "get on the machine"?There's lots of possible answers. But the most obvious answer (to most people), that your machine is infected with a virus, is likely wrong. Viruses are generally silent, doing evil things in the background. When you see something like this, you aren't infected ... yet.Instead, things popping with warnings is almost entirely due to evil websites. But that's confusing, since this popup doesn't appear within a web page. It's off to one side of the screen, nowhere near the web browser.Moreover, we spent some time diagnosing this. We restarted the webbrowser in "troubleshooting mode" with all extensions disabled and went to a clean website like Twitter. The popup still kept happening.As it turns out, he had another windows with Firefox running under a different profile. So while he cleaned out everything in this one profile, he wasn't aware the other one was still runningThis happens a lot in investigations. We first rule out the obvious things, and then struggle to find the less obvious explanation -- when it was the obvious thing all along.In this case, the reason the popup wasn't attached to a browser window is because it's a new type of popup notification that's suppose to act more like an app and less like a web page. It has a hidden web page underneath called a "service worker", so the popups keep happening when you think the webpage is closed.Once we figured the mistake of the other Firefox profile, we quickly tracked this down and saw that indeed, it was in the Notification list with Permissions set to Allow. Simply changing this solved the problem. This is obviously a trick. But from where? How did it "get on the machine"?There's lots of possible answers. But the most obvious answer (to most people), that your machine is infected with a virus, is likely wrong. Viruses are generally silent, doing evil things in the background. When you see something like this, you aren't infected ... yet.Instead, things popping with warnings is almost entirely due to evil websites. But that's confusing, since this popup doesn't appear within a web page. It's off to one side of the screen, nowhere near the web browser.Moreover, we spent some time diagnosing this. We restarted the webbrowser in "troubleshooting mode" with all extensions disabled and went to a clean website like Twitter. The popup still kept happening.As it turns out, he had another windows with Firefox running under a different profile. So while he cleaned out everything in this one profile, he wasn't aware the other one was still runningThis happens a lot in investigations. We first rule out the obvious things, and then struggle to find the less obvious explanation -- when it was the obvious thing all along.In this case, the reason the popup wasn't attached to a browser window is because it's a new type of popup notification that's suppose to act more like an app and less like a web page. It has a hidden web page underneath called a "service worker", so the popups keep happening when you think the webpage is closed.Once we figured the mistake of the other Firefox profile, we quickly tracked this down and saw that indeed, it was in the Notification list with Permissions set to Allow. Simply changing this solved the problem.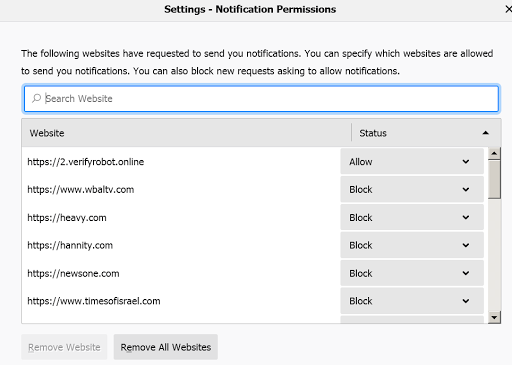 Note that the above picture of the popup has a little wheel in the lower right. We are taught not to click on dangerous thing, so the user in this case was avoiding it. However, had the user clicked on it, it wouldn't led him straight here to the solution. Though, I can't recommend you click on such a thing and trust it, because that means in the future, malicious tricks will contain such safe looking icons that aren't so safe.Anyway, the next question is: which website did this come from?The answer is Google.In the news today was the story of the Michigan guys who tried to kidnap the governor. The user googled "attempted kidnap sentencing guidelines". This search produced a pa Note that the above picture of the popup has a little wheel in the lower right. We are taught not to click on dangerous thing, so the user in this case was avoiding it. However, had the user clicked on it, it wouldn't led him straight here to the solution. Though, I can't recommend you click on such a thing and trust it, because that means in the future, malicious tricks will contain such safe looking icons that aren't so safe.Anyway, the next question is: which website did this come from?The answer is Google.In the news today was the story of the Michigan guys who tried to kidnap the governor. The user googled "attempted kidnap sentencing guidelines". This search produced a pa |
| Envoyé | Oui |
| Condensat | for this 257048169 a/b able above accidentally act actually address address:i addresses advertisement advertising advertisingsteal after agent ago air algorithms all allow almost along also always anatomy another answer answers anti any anyway anywhere app apparently appcine appear appeared appearing are aren ask asked asking assume at&t attached attack attempt attempted avoiding aware away back background bad bank banks banksignups based because been behavior behaviors behind bill billing block blogpost both bother box brave broker brokera browser browseractual browsers browsers: bunch but call called came campaign can cancel canceled canceling captcha card cards cardthere careful case cat catch caused changing charge chargebacks charges check chrome clean cleaned click clicked clicking closed come comes coming companies company complained computer confused confusing constant contain containing content continue conversion converts could credit cybersecurity dangerous dark day days debit deliver described designed desired despite detect detection diagnosing did didn different direct disabled disconnected distributes documents does doesn doing don donation donations down download downloading downloads due each earn easiest easy effort either election else email emails emulated emulation encrypted end endless engine enter enters entire entirely environment error evade even eventually everyone everything evidence evil exactly examine example existing expert experts explanation exploit exploiting extensions extracted fake fast featured figured file files find fine firefox first focus follow following following:here forwards found fraud free from full future game generally get getting give giving gmail goal goes going google googled governor guidelines guys hack hacker hackers hacking hacks had happen happened happening happens happily hard harmless has have haven helping here hidden hides highest him hit hits hole hoping hostile hours how however humans icons identified identifies illegitimate image images important impossible incoming indeed index indexing industry infect infected install instead investigate investigations is: isn itself job keep kept kidnap knowledgeable known knows labels last layer layers leads least led legallyeven legitimate less lesson like likely link links list little log long longer looking lot lots lower macbook machine machines macos make makes making malicious manager may maybe mcafee means message michigan microsoft middleman middlemenmiddlemen might misclick misclicked misclicks mistake mixture mode money month more moreover most mostly mouse movie movies much names:with near nearly need net network new news next not note notification now nowhere number numbers obliged obvious obviously occasional off okay once one ones only open opened optimization order original other others out outright outside page part pass password passwords pattern pattern: pay pdf pdfs people percentage permissions phone picture pictures placing play point popping pops popup popups possible posted pretending probably problem problem: produced products profile profit program programs promised promises promoted purposes put pwned quasi question quickly rabbit random rather raw read real realize reason recommend regular repeated replicate requires rest restarted result result:google results reuse reused reverse rewards right robot rule run running runningthis runs safe safely safer same sample saw say saying scam scams screen screenshots script search second see seeing seem sell selling sells sends sent sentencing seo separate series service set show side sign signs signup silent simply since sit site site:it sites sitting skilled slimy slow slower small smartest snippet solution solved some somebody somehow something sometime sometimes sort specialists specializes spent spiders standard started starts steal stealing stop story straight streaming string struggle submission succeed succeeded such summaryso suppose suspicious takes taught tells terms tern testing text text:if than that them themselves then t |
| Tags | Guideline |
| Stories | |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.