One Article Review
| Source | |
|---|---|
| Identifiant | 352306 |
| Date de publication | 2017-04-03 18:09:04 (vue: 2017-04-03 18:09:04) |
| Titre | APT10 - Operation Cloud Hopper |
| Texte | Written by Adrian Nish and Tom RowlesBACKGROUNDFor many businesses the network now extends to suppliers who provide management of applications, cloud storage, helpdesk, and other functions. With the right integration and service levels Managed Service Providers (MSPs) can become a key enabler for businesses by allowing them to focus on their core mission while suppliers take care of background tasks. However, the network connectivity which exists between MSPs and their customers also provides a vector for attackers to jump through. Successful global MSPs are even more attractive as they become a hub from which an intruder may access multiple end-victim networks.Since late 2016 we have been investigating a campaign of intrusions against several major MSPs. These attacks can be attributed to the actor known as APT10 (a.k.a. CVNX, Stone Panda, MenuPass, and POTASSIUM). Their activity seems to have increased in mid-2016, and has focused on compromise of MSPs as a stepping stone into victim organisations.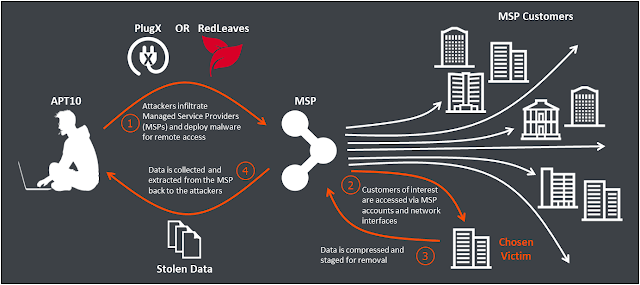 Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope |
| Envoyé | Oui |
| Condensat | 2014 2016 2016in about access across activity activity:1 actor actors actors2 address adrian against all allowing also altogether analysis applications apt apt10 architecture are area at:https://www attack attackers attacks attractive attributed awareness back backdoor background become been below between blog both business business; businesses but c&c c&cs campaign can cannot care chain chches chosen cloud common companies compromise compromised conclusionsmanaged connections connectivity continue core covered current custom customer customers customerswe cvnx cyber data defence depicts detect detection developed disclosed dll dns domain domains domainsvictimsthrough driving dropper dynamic easily either elsewhere enabler end engineering enterprise espionage even execute exists expanded exploiting extends featured figure finding findings fireeye first focus focused forced forces found from full fully functions further geo global going government graph group groups hard hardening has have helpdesk highly historic historically hold hopper hosting how however html htmloverviewthe hub identified impacted implants implying importantly impossible improved improvements incidents include including:1 increased increasing independent india infiltrated infiltration infrastructure integration intelligence interconnected intruder intrusions investigating investigation investigations iocs japan japanese joined joint jointly jump jumping key known large late latter learned legal lessons levels leveraging likely linkage linked linking links loading locations look lowest main major make makes malware;2 malware;the manage managed management many matters may menupass mid might mission mitigate monitoring months monthsinfrastructurethe more most msp msps much multiple needs network networks new newer newly nish nodes not nothing now number older one operation operations opportunity organisations other others overlap panda particularly payload payloads performed perimeter persistence perspective plugx point possible post potassium predominantly price privacy/insights/operation procurement provide providers provides public put pwc raise rdp reasonable recent recommendations red redleaves regular related release report report: https://www represents research response responsible right risk route routes rowlesbackgroundfor say sectors security see seems sensitive service services sets several shared should shown side siesta significant significantly simulated since single skill some split stages stepping stone storage strong subset success successful such suggest suppliers supply systems take targeted targeting tasks teaming techniques terms testers testing them themselves these thousands threat through timing tom tool tools two uk/issues/cyber use used various vector vectors versa vice victim victims view viewing visualised volumes vpn well where which whilst who would written |
| Tags | |
| Stories | APT 10 APT 1 |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.