One Article Review
| Source | |
|---|---|
| Identifiant | 365767 |
| Date de publication | 2017-05-17 03:33:55 (vue: 2017-05-17 03:33:55) |
| Titre | WanaCrypt0r Ransomworm |
| Texte | Written by Sergei Shevchenko and Adrian NishBACKGROUNDSince the release of the ETERNALBLUE exploit by 'The Shadow Brokers' last month security researchers have been watching for a mass attack on global networks. This came on Friday 12th May when it was bundled with ransomware called WanaCrypt0r and let loose. Initial reports of attacks were highlighted by Telefonica in Spain but the malware quickly spread to networks in the UK where the National Health Service (NHS) was impacted, followed by many other networks across the world.The infographic below illustrates the key components of the WanaCrypt0r ransomware. This is described in further detail in subsequent sections of this report along with initial clues on attribution.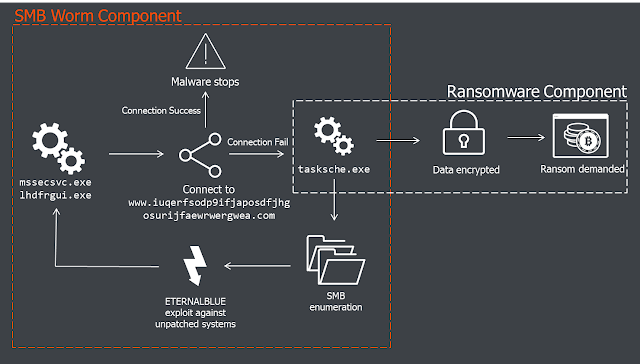 ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs |
| Envoyé | Oui |
| Condensat | $17361hence $24045115p7ummngoj1pmvkphijcrdfjnxj6lrln $2641012t9ydpgwuez9nymgw519p7aa8isjr6smw $68k $recycle &bcdedit &name &buf &name && multiplex && nt && recv && recv && send // if nt 0 internet // and nt break; // then quit the loop closesocket return 1; // return true * // finally backdoor 57u infect sleep // and doublepulsar is active return 1; // return true * *& do do send * hsocket = socket internetclosehandle name name = arg payload • add • b • block • c • c: • cg • consider • content • ensure • install • msg • n • negotiate • r • s • session • t • t1 • t2 • taskdl • taskse • temporary • this • tree • u &szurl *&target // doublepulsar installed 0 1 1024 103 16 4 445 78 82 88 = htons = inet >> 8 connect host is vulnerable to ms17 i // repeat up to 5 times int buf int size internet is backdoored is ok negotiate ok peeknamedpipe session then quit trans2 wait 3 sec | sig & 0xff0000 &szurl &target &wbadmin &wmic *it *name *name++ + /all /grant /im /quiet /set 0 circl: 0 == 5 & |
| Tags | Guideline Medical |
| Stories | Wannacry APT 38 |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.