One Article Review
| Source | |
|---|---|
| Identifiant | 647877 |
| Date de publication | 2018-05-14 09:05:47 (vue: 2018-05-14 15:11:18) |
| Titre | Some notes on eFail |
| Texte | I've been busy trying to replicate the "eFail" PGP/SMIME bug. I thought I'd write up some notes.PGP and S/MIME encrypt emails, so that eavesdroppers can't read them. The bugs potentially allow eavesdroppers to take the encrypted emails they've captured and resend them to you, reformatted in a way that allows them to decrypt the messages.Disable remote/external content in emailThe most important defense is to disable "external" or "remote" content from being automatically loaded. This is when HTML-formatted emails attempt to load images from remote websites. This happens legitimately when they want to display images, but not fill up the email with them. But most of the time this is illegitimate, they hide images on the webpage in order to track you with unique IDs and cookies. For example, this is the code at the end of an email from politician Bernie Sanders to his supporters. Notice the long random number assigned to track me, and the width/height of this image is set to one pixel, so you don't even see it: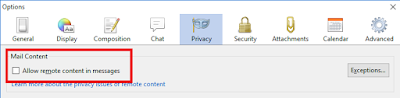 The problem is that as you read email messages, you often get frustrated by the fact the error messages and missing content, so you keep adding exceptions: The problem is that as you read email messages, you often get frustrated by the fact the error messages and missing content, so you keep adding exceptions: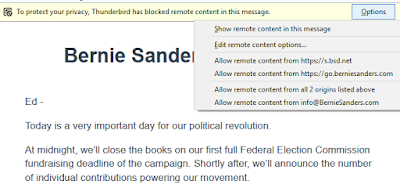 The correct defense against this eFail bug is to make sure such remote content is disabled and that you have no exceptions, or at least, no HTTP exceptions. HTTPS exceptions (those using SSL) are okay as long as they aren't to a website the attacker controls. Unencrypted exceptions, though, the hacker can eavesdrop on, so it doesn't matter if they control the website the requests go to. If the attacker can eavesdrop on your emails, they can probably eavesdrop on your HTTP sessions as well.Some have recommended disabling PGP and S/MIME completely. That's probably overkill. As long as the attacker can use the "remote content" in emails, you are fine. Likewise, some have recommend disabling HTML completely. That's not even an option in any email client I've used -- you can disable sending HTML emails, but not receiving them. It's sufficient to just disable grabbing remote content, not the rest of HTML email rendering.I couldn't replicate the direct exfiltrationThere rare two related bugs. One allows direct exfiltration, which appends the decrypted PGP email onto the end of an IMG tag (like The correct defense against this eFail bug is to make sure such remote content is disabled and that you have no exceptions, or at least, no HTTP exceptions. HTTPS exceptions (those using SSL) are okay as long as they aren't to a website the attacker controls. Unencrypted exceptions, though, the hacker can eavesdrop on, so it doesn't matter if they control the website the requests go to. If the attacker can eavesdrop on your emails, they can probably eavesdrop on your HTTP sessions as well.Some have recommended disabling PGP and S/MIME completely. That's probably overkill. As long as the attacker can use the "remote content" in emails, you are fine. Likewise, some have recommend disabling HTML completely. That's not even an option in any email client I've used -- you can disable sending HTML emails, but not receiving them. It's sufficient to just disable grabbing remote content, not the rest of HTML email rendering.I couldn't replicate the direct exfiltrationThere rare two related bugs. One allows direct exfiltration, which appends the decrypted PGP email onto the end of an IMG tag (like |
| Envoyé | Oui |
| Condensat | above accidentally according adding adds after against all allow allowing allows already any appended appends are aren around assigned attacker attackers attempt automatically been being bernie between bit blog bug bugs busy but can captured case cases causing chunk client clients code com com/ completely consisting content contents control controls cookies correct could couldn decrypt decrypted default defense detect direct disable disabled disabling display doesn don each easily eavesdrop eavesdroppers eavesdropping efail email emails emailthe enabled encrypt encrypted end ending enignmail entire error even example exceptions exceptions:the exfiltration exfiltrationthere exploit extension external external/remote fact far fill fine first following formatted from front frustrated generate get getting going grab grabbing guard hacker hackers happen happens has hast have hide his html http https huge ids ignored illegitimate image images img important indeed instead isn it:such just keep latest least legitimately like like:that likewise lines load loaded long looks make matter may message messages missing most multipart multipart/mixed multiple next not notes notice number often okay one only onto option order overkill own part parts pastes pernicious pgp pgp/smime pixel place point politician potentially previous privacy probably problem puts quotes random rare read received receiving recommend recommended reformatted related remote remote/external rendering replicate reproducible request requests resend rest robertgraham s/mime safe sanders section see seems sending sent server sessions set settings should some ssl standard starting starts stuff such sufficient summaryit supporters sure tag tags take terminate tests that them then they this:i this:the those though thought thunderbird thunderbird:the time together track trackers tracking trick trying two unencrypted unique url use used using version violation want way webpage website websites weird well what when which who why width/height will without work works write you your |
| Tags | |
| Stories | |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.