One Article Review
| Source | |
|---|---|
| Identifiant | 742946 |
| Date de publication | 2018-07-12 19:54:20 (vue: 2018-07-13 02:02:15) |
| Titre | Your IoT security concerns are stupid |
| Texte | Lots of government people are focused on IoT security, such as this recent effort. They are usually wrong. It's a typical cybersecurity policy effort which knows the answer without paying attention to the question.Patching has little to do with IoT security. For one thing, consumers will not patch vulns, because unlike your phone/laptop computer which is all "in your face", IoT devices, once installed, are quickly forgotten. For another thing, the average lifespan of a device on your network is at least twice the duration of support from the vendor making patches available.Naive solutions to the manual patching problem, like forcing autoupdates from vendors, increase rather than decrease the danger. Manual patches that don't get applied cause a small, but manageable constant hacking problem. Automatic patching causes rarer, but more catastrophic events when hackers hack the vendor and push out a bad patch. People are afraid of Mirai, a comparatively minor event that led to a quick cleansing of vulnerable devices from the Internet. They should be more afraid of notPetya, the most catastrophic event yet on the Internet that was launched by subverting an automated patch of accounting software.Vulns aren't even the problem. Mirai didn't happen because of accidental bugs, but because of conscious design decisions. Security cameras have unique requirements of being exposed to the Internet and needing a remote factory reset, leading to the worm. While notPetya did exploit a Microsoft vuln, it's primary vector of spreading (after the subverted update) was via misconfigured Windows networking, not that vuln. In other words, while Mirai and notPetya are the most important events people cite supporting their vuln/patching policy, neither was really about vuln/patching.Such technical analysis of events like Mirai and notPetya are ignored. Policymakers are only cherrypicking the superficial conclusions supporting their goals. They assiduously ignore in-depth analysis of such things because it inevitably fails to support their positions, or directly contradicts them.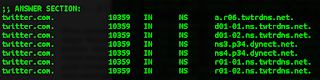 IoT security is going to be solved regardless of what government does. All this policy talk is premised on things being static unless government takes action. This is wrong. Government is still waffling on its response to Mirai, but the market quickly adapted. Those off-brand, poorly engineered security cameras you buy for $19 from Amazon.com shipped directly from Shenzen now look very different, having less Internet exposure, than the ones used in Mirai. Major Internet sites like Twitter now use multiple DNS providers so that a DDoS attack on one won't take down their services.In addition, technology is fundamentally changing. Mirai attacked IPv4 addresses outside the firewall. The 100-billion IoT devices going on the network in the next decade will not work this way, cannot work this way, because there are only 4-billion IPv4 addresses. Instead, they'll be behind NATs or accessed via IPv6, both of which prevent Mirai-style worms from functioning. Your fridge and toaster won't connect via your home WiFi anyway, but via a 5G chip unrelated to your home.Lastly, focusing on the ven IoT security is going to be solved regardless of what government does. All this policy talk is premised on things being static unless government takes action. This is wrong. Government is still waffling on its response to Mirai, but the market quickly adapted. Those off-brand, poorly engineered security cameras you buy for $19 from Amazon.com shipped directly from Shenzen now look very different, having less Internet exposure, than the ones used in Mirai. Major Internet sites like Twitter now use multiple DNS providers so that a DDoS attack on one won't take down their services.In addition, technology is fundamentally changing. Mirai attacked IPv4 addresses outside the firewall. The 100-billion IoT devices going on the network in the next decade will not work this way, cannot work this way, because there are only 4-billion IPv4 addresses. Instead, they'll be behind NATs or accessed via IPv6, both of which prevent Mirai-style worms from functioning. Your fridge and toaster won't connect via your home WiFi anyway, but via a 5G chip unrelated to your home.Lastly, focusing on the ven |
| Envoyé | Oui |
| Condensat | $19 the 100 about above accessed accidental accounting action adapt adapted add addition addresses afraid after all amazon analysis another answer anyway applied are aren assiduously attack attacked attention automated automatic autoupdates available average bad because behind being benefits best billion both brand bugs but buy cameras can cannot catastrophic cause causes changing cherrypicking chip chronic cite cleansing cliche com come comparatively computer concerns conclusions connect conscious consider constant consumers contradicts control costs cybersecurity danger ddos decade decisions decrease depth design device devices did didn different directly dns does don down duration effort engineered even event events exploit exposed exposure face factory failing fails firewall focused focusing forcing forgotten fridge from functioning fundamentally further future get goal goals going government hack hackers hacking happen has have having home how ideas ignore ignored important increase inevitably insecurities insignificant installed instead interesting interests internet iot ipv4 ipv6 issues its itself knows lastly launched leading least led less lifespan like little look lots major makers making manageable manual market microsegment microsoft minor mirai misconfigured more most multiple naive nats needing neither network networking networks new next not nothing notpetya now off once one ones only other out outside patch patches patching paying people phone/laptop policy policymakers political poorly positions premised prevent primary problem problems propose proposed providers push question quick quickly rarer rather really recent regardless remote requirements requiring reset response security services shenzen shipped should significant sites small software solutions solved something spreading static stupid style subverted subverting such superficial support supporting take takes talk technical technology than them they thing things those tired toaster today twice twitter typical unique unless unlike unrelated unsolved update use used users usually vector vendor vendors very vuln vuln/patching vulnerable vulns waffling way what when which wholly wifi will windows within without won words work worm worms wrong year yet your |
| Tags | Hack Patching Guideline |
| Stories | NotPetya |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.