One Article Review
| Source | |
|---|---|
| Identifiant | 8300156 |
| Date de publication | 2016-12-01 18:15:55 (vue: 2023-01-11 16:56:00) |
| Titre | LuaBot: Malware targeting cable modems |
| Texte | During mid-2015 I disclosed some vulnerabilities affecting multiple ARRIS cable modems. I wrote a blogpost about ARRIS' nested backdoor and detailed some of my cable modem research during the 2015 edition from NullByte Security Conference.CERT/CC released the Vulnerability Note VU#419568 and it got lots of media coverage. I did not provide any POC's during that time because I was pretty sure that those vulnerabilities were easily wormable... And guess what? Someone is actively exploiting those devices since May/2016.The malware targets Puma 5 (ARM/Big Endian) cable modems, including the ARRIS TG862 family. The infection happens in multiple stages and the dropper is very similar to many common worm that targets embedded devices from multiple architectures. The final stage is an ARMEB version from the LuaBot Malware.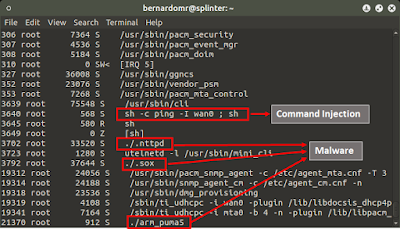 The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. |
| Envoyé | Oui |
| Condensat | #86:i 80 also they which *all* /dev/urandom /gdbserver /mw/dropconnect /strace /var/tmp 0/0 0/24 0/24185 0/24217 0/2485 0/2495 000 000:i 00879 061b03f8911c41ad18f417223840bce0 0x000c3000 0x000df000 0x8274: 0xa40b8 100 1058 114 11833 122 12280 135 143 148 168 17:35:34:another 182 192 1:12345lastly 2000 20100224dropper 2015 2016 202613 205 213 22:these 433 4446 490 4b8c0ec8b36c6bf679b3afcc6f54442a 4gcc: 5 5deb17c660de9d449675ab32048756ed 600 610cker 716kb 8080 889100a188a42369fd93e7010f7c654b 92ip 9999 :luabot :the about access accessible actively actually additional addr addr=inet administrative affecting after again against:after all almost also alt+f7 always analise analyse analysed analysis and and blocking any approach approaches approximately architecture architectures are arm arm/big armeb armel armset around arris aspects attach attacker attacker:46 attacks attempt: attempts attempts:cmd=cd attention author auxiliary available backdoor backdoors backdoorsbefore based bbot because becoming been being below best better big bigger bigset binaries binaries are binaries:drop binariesthe binary bitcoin blob block blogpost bot both botnet botnets bots browse bruteforce bruteforcing building buildroot builtin bulletins contributed but bypass bytecode c867d00e4ed65a4ae91ee65ee00271c7 cable cached calls can capabilities cat catchy cert/cc certificates checking checks childgef choose cli click cloners close cnc code com/bmaia/slides/raw/master/nullbyte command commands common compiled composed compromise compromised conclusionthe conference configuration connect connection contact contain contains contribute control controlled copy corresponding course coverage covers craft create created creates creation creators criminals cross crypgtographers current custom daemonize data database databases day ddos deal debug debugger debugging delete deleted denial described detailed detect detection device devices devices/firmwares diaphora diaphora:we did didn die diff different diffing disclosed display dissected dns dnscrypt dnsparser documented doesn domain don done download downloaded downloading dropper dummy dump during dynamic ease easier easily easy echo echoing ecosystems ed25519 edition effort elf embedded enabled:if endian engine enodev enterprises entire environment environments escape event everything evserver evsocket evsocketlib evtimer example exec executes exploit exploiting exploits export exposed external facing fact families family family=af favorite few file file/script final find finishes firmware firmwares first flooding/ddos follow following for fork forks from from nothink from nullbyte full function functionalities functions further g9ff11e0 gateway:all gcc gdbserver gef gef/gdb generated get git gnu google got grab greetings guess gzip hacking had happen happens hardcoded:the has have head header heap heap:vmmapdump help isps here high his hit home honeypots hours how https://github ida import included includes including indicates indicators inet infect infected infection infectionluabot information initial initially injection injections installed instead instructions integrates interesting interfaces internal internet internet and interoperability interpreter interview into iocs iot ips ips:46 iptables ipv6 isps issues its javascript job keep key:meterpreter know known lack language large last later learn legible let lfs:the lib libev functionalities library libuclibc like line linked linksys linux list listening load loaded localhost:12345 location log logging lots low lpeg lua luabot luabot: luabot:the luabotthe made make making malicious malware manage manual manually manufacturers many mark masscan matches may/2016 md5 mechanism media mem memory messages mid mix mode modem modems modems: modified modify modular modules modules:the monitor more most much multi multiarch multiple must mutex my cross named named checkanus native need nested net network networks never new not note note vu#419568 noticed now nowadays nttpd nu |
| Tags | Malware Tool Vulnerability |
| Stories | |
| Notes | ★★★★ |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.