What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-04-23 16:10:10 | Abusing MySQL LOCAL INFILE to read client files (lien direct) | Recently, I was playing the VolgaCTF 2018 CTF with my teammates from TheGoonies and we came across an interesting Web challenge that we didn't manage to solve during the competition. The following day, I read the write-up and learned a cool technique to attack the MySQL client directly via the LOAD DATA INFILE statement.The "Corp Monitoring" task consisted of a Corporate Monitoring API that would test the healthcheck of a given server by connecting and verifying if the FTP, Web and MySQL servers were up. The MySQL user for the connection was restricted and the healthcheck validation was based on a few queries including the "SHOW DATABASE" command.The key to solve the challenge was to identify the "Can Use LOAD DATA LOCAL" client capability and point the API to a Rogue MySQL server that would read arbitrary files from the client via LOAD DATA INFILE statements.After reading about the technique, I decided to check how several libraries, clients and Web Frameworks could be exploited. I also ended up writing a a Bettercap module to abuse this feature in combination with MITM attacks. Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". |
Hack Tool Vulnerability | ★★★★ | ||
| 2016-12-01 18:15:55 | LuaBot: Malware targeting cable modems (lien direct) | During mid-2015 I disclosed some vulnerabilities affecting multiple ARRIS cable modems. I wrote a blogpost about ARRIS' nested backdoor and detailed some of my cable modem research during the 2015 edition from NullByte Security Conference.CERT/CC released the Vulnerability Note VU#419568 and it got lots of media coverage. I did not provide any POC's during that time because I was pretty sure that those vulnerabilities were easily wormable... And guess what? Someone is actively exploiting those devices since May/2016.The malware targets Puma 5 (ARM/Big Endian) cable modems, including the ARRIS TG862 family. The infection happens in multiple stages and the dropper is very similar to many common worm that targets embedded devices from multiple architectures. The final stage is an ARMEB version from the LuaBot Malware.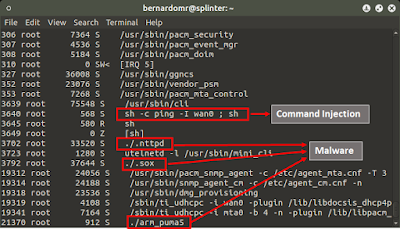 The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. |
Malware Tool Vulnerability | ★★★★ | ||
| 2016-03-15 19:09:18 | 0CTF 2016 Write Up: Monkey (Web 4) (lien direct) | The Chinese 0CTF took place on March 12-13 and it was yet another fun CTF. I played with my teammates from TheGoonies and we were ranked #48.I found the Web task "Monkey" particularly interesting: I solved it with the help from my friend @danilonc, but it took way longer than it should because of some **Spoiler Alert** DNS glitches. According to the scoreboard status, approximately 35 teams were able to solve it.Task: Monkey (Web - 4pts)What is Same Origin Policy?you can test this problem on your local machinehttp://202.120.7.200The running application receives a Proof-of-Work string and an arbitrary URL, instructing a "monkey" to browse the inputted URL for 2 minutes.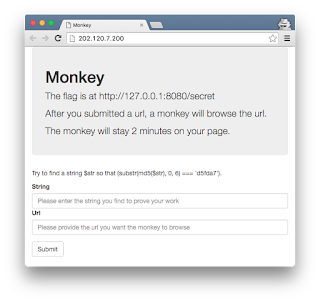 Proof-of-WorkSolving the proof-of-work is pretty straightforward. We had to generate random strings and compare the first 6 chars from its MD5 against the challenge. The POW challenge was more cpu-intensive than normal, so the traditional bash/python one-liner ctf scripts would require some performance improvements.@danilonc had written a quick hack using Go to bruteforce and solve POW from older CTF challs, so we just slightly modified it: Solving the Proof-of-Work: Proof-of-WorkSolving the proof-of-work is pretty straightforward. We had to generate random strings and compare the first 6 chars from its MD5 against the challenge. The POW challenge was more cpu-intensive than normal, so the traditional bash/python one-liner ctf scripts would require some performance improvements.@danilonc had written a quick hack using Go to bruteforce and solve POW from older CTF challs, so we just slightly modified it: Solving the Proof-of-Work: Same-Origin-Policy and CORSThe Same-Origin-Policy (SOP) deems pages having the same URI scheme, hostname and port as residing at the same-origin. If any of these three attributes varies, the resource is in a different origin. Hence, if provided resources come from the same hostname, scheme and port, they can interact without restriction.If you try to use an XMLHttpRequest to send a request to a different origin, you can't read the response. However, the request will still arrive at its destination. This policy prevents a malicious script on one page from obtaining access to sensitive data (both the header and the body) on another web page, on a different origin.For this particular CTF challenge, if the secret internal webpage had had an insecure CORS header like "Access-Control-Allow-Origin: *", we would be able to retrieve its data with no effort. This, of course, was not the case.Bypassing the Same-OriginThe flag was accessible on an internal webserver hosted at http://127.0.0.1:8080/secret. The first thing we did was hooking the monkey's browser using BeEF, so we could fingerprint his device, platform, plugins and components. Same-Origin-Policy and CORSThe Same-Origin-Policy (SOP) deems pages having the same URI scheme, hostname and port as residing at the same-origin. If any of these three attributes varies, the resource is in a different origin. Hence, if provided resources come from the same hostname, scheme and port, they can interact without restriction.If you try to use an XMLHttpRequest to send a request to a different origin, you can't read the response. However, the request will still arrive at its destination. This policy prevents a malicious script on one page from obtaining access to sensitive data (both the header and the body) on another web page, on a different origin.For this particular CTF challenge, if the secret internal webpage had had an insecure CORS header like "Access-Control-Allow-Origin: *", we would be able to retrieve its data with no effort. This, of course, was not the case.Bypassing the Same-OriginThe flag was accessible on an internal webserver hosted at http://127.0.0.1:8080/secret. The first thing we did was hooking the monkey's browser using BeEF, so we could fingerprint his device, platform, plugins and components. |
Hack | ★★★★ | ||
| 2015-12-09 01:03:30 | Hack.lu 2015 CTF Write Up: Dr. Bob (Forensic 150) (lien direct) | Hack.lu 2015 CTF was organised by fluxfingers during October 20-22. It's one of the coolest CTFs around, the only drawback is that it runs during week days (hey guys patch this for the next years). My team TheGoonies ranked #59th, which is not bad considering we only played part-time.The task Dr. Bob was the one I found most interesting as it included disk forensics, memory forensics and basic crypto tasks.Task: Dr. Bob (Forensic 150)There are elections at the moment for the representative of the students and the winner will be announced tomorrow by the head of elections Dr. Bob. The local schoolyard gang is gambling on the winner and you could really use that extra cash. Luckily, you are able to hack into the mainframe of the school and get a copy of the virtual machine that is used by Dr. Bob to store the results. The desired information is in the file /home/bob/flag.txt, easy as that.Download: dr_bob_e22538fa166acecc68fa17ac148dcbe2.tar.gzThe file provided is a VirtualBox image in a saved state. According to the challenge instructions, we have to retrieve the flag from the user home folder. The VM starts on a login terminal of what seems to be a Linux distro.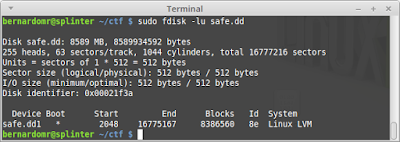 sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! |
Hack Tool | ★★★★ | ||
| 2015-11-20 00:02:04 | ARRIS Cable Modem has a Backdoor in the Backdoor (lien direct) | A couple of months ago, some friends invited me to give a talk at NullByte Security Conference. I started to study about some embedded device junk hacking hot topics and decided to talk about cable modem security. Braden Thomas keynoted at Infiltrate 2015 discussing about Practical Attacks on DOCSIS so, yeah, cable modem hacking is still mainstream.On November 21st I'll be at Salvador speaking on "Hacking cable modems: The Later Years". It's not a talk about theft of service and getting free Internet access. I'll focus on the security of the cable modems, the technology used to manage them, how the data is protected and how the ISPs upgrade the firmwares. Spoiler Alert: everything's really really bad.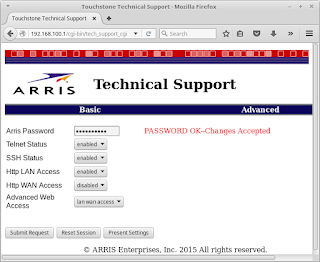 The default password for the SSH user 'root' is 'arris'. When you access the telnet session or authenticate over SSH, the system spawns the 'mini_cli' shell asking for the backdoor password. The default password for the SSH user 'root' is 'arris'. When you access the telnet session or authenticate over SSH, the system spawns the 'mini_cli' shell asking for the backdoor password. |
★★★★ | |||
| 2015-10-07 11:26:14 | Mac OS X 10.11 Partial Lock Screen Bypass (lien direct) | Lock screen bypasses are becoming mainstream. The most notable recent bypasses are the one from Ubuntu 14.04 (hold enter, lock screen crashes, computer unlocked) and the one from Android 5.x (input large strings in the password field, destabilize the lock screen, crash to the home screen).Many respected researcher had found and published something about this class of bugs and this blog is no different: this post describes a completely useless super serious vulnerability affecting Mac OS X 10.11 and earlier.Mac OS X 10.11 Partial Lock Screen BypassMac OS X 10.11 (and probably older versions) are vulnerable to a partial lock screen bypass. This is not a *complete* lock screen bypass as you won't be able to freely interact with the Desktop (as far as I know). Here are the steps to reproduce this bug:1 - Hit the Exposé Key (F3) 2 - Click on any window and keep holding it 2 - Click on any window and keep holding it 3 - Keep holding the left mouse button and lock the screen using Command + Option + Eject (hold all these keys together for some time) 3 - Keep holding the left mouse button and lock the screen using Command + Option + Eject (hold all these keys together for some time) That's it, now the lock screen has an "extra layer" with the miniaturised desktop windows. If you move the mouse cursor over the correct application position and hit the Space Key, a bigger window will be displayed. That's it, now the lock screen has an "extra layer" with the miniaturised desktop windows. If you move the mouse cursor over the correct application position and hit the Space Key, a bigger window will be displayed. You can watch Youtube videos and interact with media players (Quicktime, Spotify etc) using the media control keys. You can't interact directly with the app: if you left-click on the windows or hit Enter, the lock screen takes over that invisible layer.Proof-of-concept - Mac OS X 10.11:If Youtube is blocking the video in your country, watch it here:If you are a serious tech journalist reporting about this bug feature, don't forget to say that You can watch Youtube videos and interact with media players (Quicktime, Spotify etc) using the media control keys. You can't interact directly with the app: if you left-click on the windows or hit Enter, the lock screen takes over that invisible layer.Proof-of-concept - Mac OS X 10.11:If Youtube is blocking the video in your country, watch it here:If you are a serious tech journalist reporting about this bug feature, don't forget to say that |
★★★★ | |||
| 2015-09-21 20:34:10 | CSAW CTF 2015 Write Up: Weebdate (web500) (lien direct) | The anual CSAW CTF Qualification Round took place on September 18-20 and it was yet another really cool CTF. I played with my friends from TheGoonies and we ranked #128 overall (The Goonies 'R' Good Enough).Task - Weebdate (web500)Since the Ashley Madison hack, a lot of high profile socialites have scrambled to find the hottest new dating sites. Unfortunately for us, that means they're taking more safety measures and only using secure websites. We have some suspicions that Donald Trump is using a new dating site called "weebdate" and also selling cocaine to fund his presidential campaign. We need you to get both his password and his 2 factor TOTP key so we can break into his profile and investigate.Flag is md5($totpkey.$password)http://54.210.118.179/This is a basic Flask application running a dating site. The website has some features like most web applications we are used to: creating users, editing profiles, sending messages, searching users and exposing the whole customer data thourgh SQL Injection and LFI.SQLiThe CSP reporting URI was vulnerable to SQL injection. SQLmap had no problems finding and exploiting it.python sqlmap.py -u 'http://54.210.118.179:80/csp/view/1' --cookie='session=donaldtrump010_1442717300_f65cb746b519c2b49f8e938a896e08e96f5fc533' --dbms=mysql --batch  The 'weeb' database had three tables: messages, reports and users. The 'user' table had eight columns: user_id, user_name, user_password, user_ip, user_image, user_credits,user_register_time and user_profile. The 'weeb' database had three tables: messages, reports and users. The 'user' table had eight columns: user_id, user_name, user_password, user_ip, user_image, user_credits,user_register_time and user_profile. |
★★★★ | |||
| 2015-05-04 23:57:38 | Firmware Forensics: Diffs, Timelines, ELFs and Backdoors (lien direct) | This post covers some common techniques that I use to analyze and reverse firmware images. These techniques are particularly useful to dissect malicious firmwares, spot backdoors and detect unwanted modifications.Backdooring and re-flashing firmware images is becoming mainstream: malicious guys are infecting embedded devices and inserting trojans in order to achieve persistence. Recent articles covered the increasing number of trojanized android firmwares and routers that are being permanently modified.Attackers with a privileged network position may MITM your requests and forge fake updates containing malicious firmwares. Writing Evilgrade modules for this is really simple, as most vendors keep failing to deliver updates securely, right ASUS? Valid signature -> nvram_set("rsasign_check", "1")NoConName 2014 CTF Finals: VodkaI'll keep my tradition of writing posts based on CTF challenges because everybody upvotes CTF posts on reddit it's cool.The challenge "Vodka", from NoConName 2014 CTF Finals was created by @MarioVilas, who kindly provided the files here (thanks dude!).I did not participate on the CTF finals, but I found the challenge really interesting because there were many different ways to solve it, summarizing the actions needed to audit a compromised f Valid signature -> nvram_set("rsasign_check", "1")NoConName 2014 CTF Finals: VodkaI'll keep my tradition of writing posts based on CTF challenges because everybody upvotes CTF posts on reddit it's cool.The challenge "Vodka", from NoConName 2014 CTF Finals was created by @MarioVilas, who kindly provided the files here (thanks dude!).I did not participate on the CTF finals, but I found the challenge really interesting because there were many different ways to solve it, summarizing the actions needed to audit a compromised f |
Malware Hack Tool | ★★★★ | ||
| 2015-02-27 00:56:54 | Extracting RAW pictures from memory dumps (lien direct) | IntroductionEarlier today, while reading my Twitter timeline, I saw some Infosec folks discussing about scripts/tools to identify RAW pictures in memory dumps. I decided, then, to write this blog post and share a small hack that I use to visualize data (including memory dumps). Memory DumpsThe first thing you will want to do is to narrow the analysis to the process containing interesting images/pictures. I'm going to use three different memory dumps here:Remote Desktop Client - Windows 7 x64 (mstsc.exe)Let's use the Windows built-in RDP client to connect to an external server and dump the processmemory using procdump: Memory DumpsThe first thing you will want to do is to narrow the analysis to the process containing interesting images/pictures. I'm going to use three different memory dumps here:Remote Desktop Client - Windows 7 x64 (mstsc.exe)Let's use the Windows built-in RDP client to connect to an external server and dump the processmemory using procdump: |
Hack Tool | ★★★★ | ||
| 2014-12-04 20:47:07 | 9447 2014 CTF Write Up: coor coor (lien direct) | The Australian 9447 Security Society CTF took place on November 29-30 and it was yet another fun and really professionally organized CTF. I played with my friends from TheGoonies once again (The Goonies 'R' Good Enough, right?).I found the task "coor coor" particularly interesting: it was a good way to practice some concepts from the new book I recently bought: The Art of Memory Forensics (authored by @attrc and @gleeda).Task: coor coor (misc - 400)A 9447 CTF organizer is giving away flags to friends that he trusts. This memory dump was taken off a competitor's computer after a raid by the pwnpolice. Download provided: https://s3-us-west-2.amazonaws.com/elasticbeanstalk-us-west-2-467703568171/challenges/coorcoor.tar.bz2Let's start by identifying the Operating System profile:python vol.py -f challenge.vmem imageinfo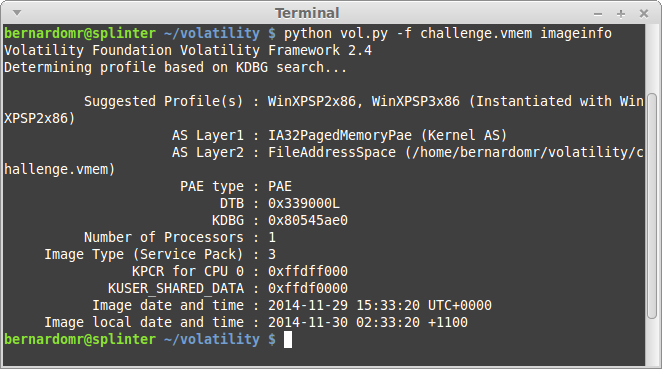 Let's take screenshot to see what the user was doing:python vol.py -f challenge.vmem screenshot -D screenshot/ Let's take screenshot to see what the user was doing:python vol.py -f challenge.vmem screenshot -D screenshot/ The user was running something inside VirtualBox, let's keep digging:python vol.py -f challenge.vmem psxview The user was running something inside VirtualBox, let's keep digging:python vol.py -f challenge.vmem psxview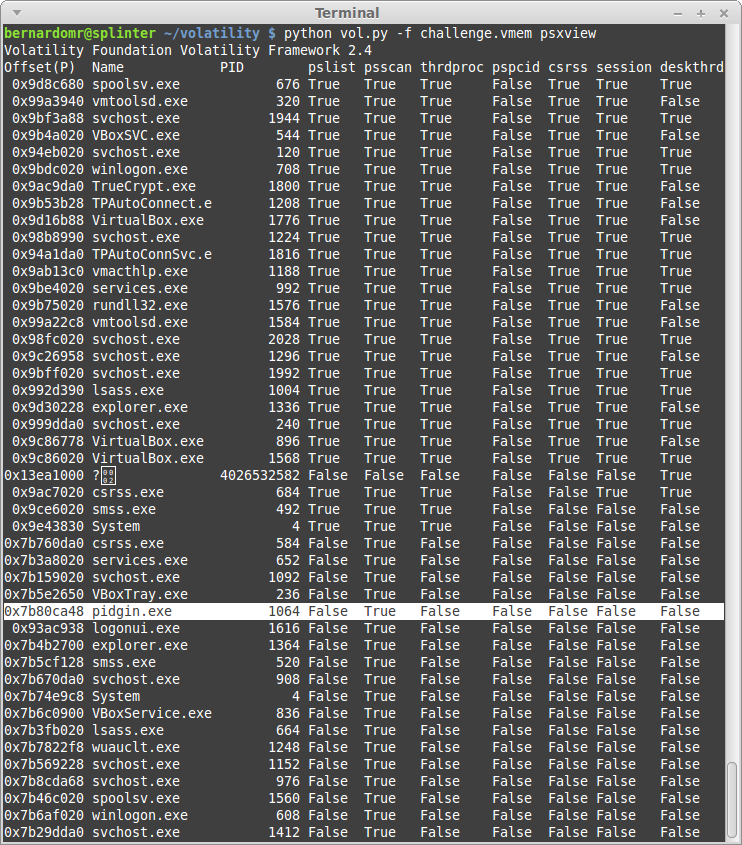 python vol.py -f challenge.vmem filescan | grep -e "\.tc\|TrueCrypt" python vol.py -f challenge.vmem filescan | grep -e "\.tc\|TrueCrypt"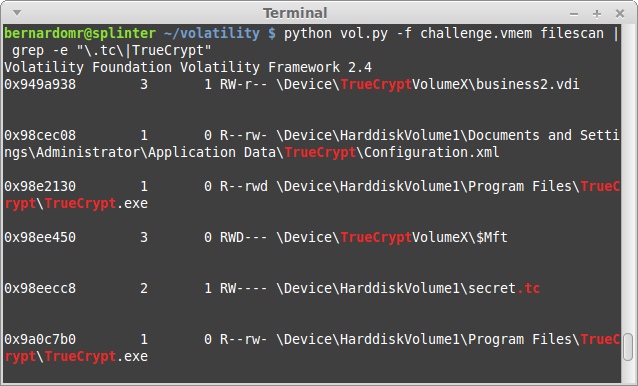 The user was basically running a VirtualBox machine (business2.vdi) from an Encrypted TrueCrypt container (secret.tc). That's why we used psxview to list the system processes before. Note that the lower offsets are used by the Host and the higher ones (after 0x7b760da0) are used by the guest OS. So what was he doing?python vol.py -f challenge.vmem connscan The user was basically running a VirtualBox machine (business2.vdi) from an Encrypted TrueCrypt container (secret.tc). That's why we used psxview to list the system processes before. Note that the lower offsets are used by the Host and the higher ones (after 0x7b760da0) are used by the guest OS. So what was he doing?python vol.py -f challenge.vmem connscan |
★★★★ | |||
| 2014-10-24 03:50:16 | Hack.lu 2014 CTF Write Up: At Gunpoint (lien direct) | Hack.lu's 2014 CTF took place on October 21-23. The event was organized by fluxfingers, and this year's challenges were really enjoyable, huge props to them. I played with my friends from TheGoonies - after winning the Brazilian CTF Pwn2Win we are now getting better organized to become more competitive. There are quite a few write ups around and I decided to post about a few tasks which we had a different solution from other teams.Task: At Gunpoint (Reversing - 200)You're the sheriff of a small town, investigating news about a gangster squad passing by. Rumor has it they're easy to outsmart, so you have just followed one to their encampment by the river. You know you can easily take them out one by one, if you would just know their secret handshake. Download provided: gunpoint_2daf5fe3fb236b398ff9e5705a058a7f.datFile utility showed us that it was a GameBoy ROM. Having former Console Hackers on the team came handy during this challenge as we already knew in advance which tools to use and what to look for. We used TLayer TileMolester from the legendary SnowBro to gather information about the graphics and the font data. Firstly, we switched the Codec to 1bpp and found the font used by the game. We used TLayer TileMolester from the legendary SnowBro to gather information about the graphics and the font data. Firstly, we switched the Codec to 1bpp and found the font used by the game. We were about to create a character table when, after switching the Codec to 2bpp planar (GameBoy's native Codec), we found something interesting: We were about to create a character table when, after switching the Codec to 2bpp planar (GameBoy's native Codec), we found something interesting: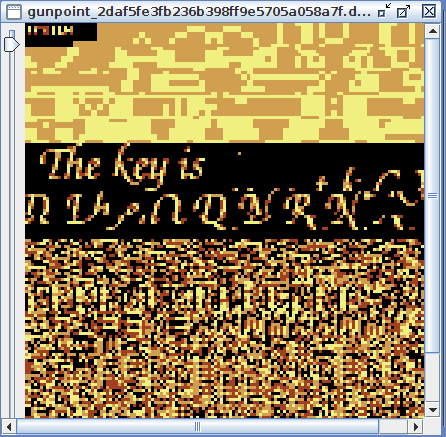 After some offset adjustment (using +, -, Shift + left and Shift + right) we got this image: After some offset adjustment (using +, -, Shift + left and Shift + right) we got this image: We submitted the key "tkCXDtheQDNRN", but it wasn't accepted. I wanted to confirm that those tiles were disposed in a linear way, so I kept analyzing the ROM.The GameBoy's screen has a resolution of 20x18 tiles. In order to check if the order of the tiles (and the flag) was correct, I performed a relative search using Darkl0rd's Monkey-Moore: We submitted the key "tkCXDtheQDNRN", but it wasn't accepted. I wanted to confirm that those tiles were disposed in a linear way, so I kept analyzing the ROM.The GameBoy's screen has a resolution of 20x18 tiles. In order to check if the order of the tiles (and the flag) was correct, I performed a relative search using Darkl0rd's Monkey-Moore: |
★★★★ | |||
| 2014-08-22 01:56:46 | Scan the Internet & Screenshot All the Things (lien direct) | During Defcon 22, @ErrataRob, @paulm and @Viss (mass)scanned the Internet and presented some Tips, Tricks and Results. Lots of people confronted @Viss after he posted some VNC screenshots on his Twitter timeline. He posted a follow-up article on his blog and Kashmir Hill, from Forbes, wrote an article about the exposed VNC services.Internet scanning isn't new anymore and people are still surprised with these results. For this post, I'll share some techniques I commonly use to map and screenshot several Internet services during pentest engagements. All this could easily be adapted for other protocols and services, so let's start to Screenshot All the Things. VNCThe easiest way to snapshot these services is to use preexisting tools and script/mod them according to your needs. In order to take screenshots from VNC, I generally use noVNC (an HTML5 VNC client) and a command line utility to capture the WebKit's rendering of a web page.The process is pretty straightforward:1 - Clone the noVNC project from github:git clone git://github.com/kanaka/noVNC2 - Start the mini-webserver and specify the location of the VNC server you want to screenshot:./noVNC/utils/launch.sh --vnc 192.168.1.142:5900 VNCThe easiest way to snapshot these services is to use preexisting tools and script/mod them according to your needs. In order to take screenshots from VNC, I generally use noVNC (an HTML5 VNC client) and a command line utility to capture the WebKit's rendering of a web page.The process is pretty straightforward:1 - Clone the noVNC project from github:git clone git://github.com/kanaka/noVNC2 - Start the mini-webserver and specify the location of the VNC server you want to screenshot:./noVNC/utils/launch.sh --vnc 192.168.1.142:5900 3 - Take a webpage screenshot from command line using CutyCapt, for example:cutycapt --url="http://127.0.0.1:6080/vnc_auto.html" --javascript=on --out=vnc.png --delay=3000 3 - Take a webpage screenshot from command line using CutyCapt, for example:cutycapt --url="http://127.0.0.1:6080/vnc_auto.html" --javascript=on --out=vnc.png --delay=3000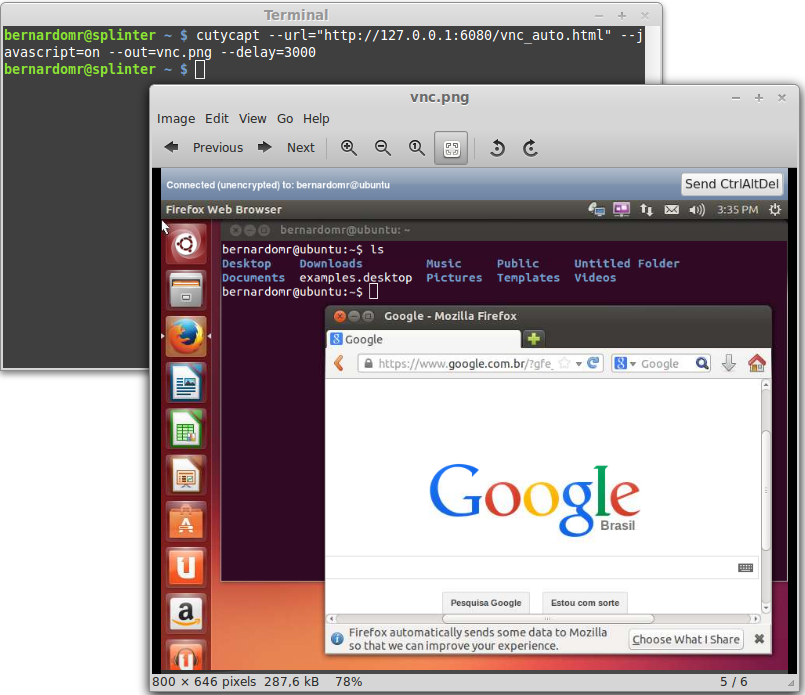 4 - Profit!!!Now all you have to do is masscan the target for ports 5900-5910 (used by VNC), save the results on a text file and create a simple script to take the screenshots. You can also try vncsnapshot, used by @paulm during his Toorcon 2013 talk.RDPMy tool of choice for taking snapshots of RDP ser 4 - Profit!!!Now all you have to do is masscan the target for ports 5900-5910 (used by VNC), save the results on a text file and create a simple script to take the screenshots. You can also try vncsnapshot, used by @paulm during his Toorcon 2013 talk.RDPMy tool of choice for taking snapshots of RDP ser |
Tool | ★★★★ | ||
| 2014-07-21 11:49:10 | Hacking Asus RT-AC66U and Preparing for SOHOpelesslyBroken CTF (lien direct) | So it's finally July, time to pack for DEFCON, follow @defconparties on Twitter and decide which villages to visit and which talks to attend.There's a new hacking competition this year called SOHOpelesslyBroken, presented by ISE and EFF. The objective on Track 0 is to demonstrate previously unidentified vulnerabilities in off-the-shelf consumer wireless routers. Track 1 will hold a live CTF for the duration of DEFCON. CTFs are always fun and this contest involves hacking real embedded devices, what makes it even more fun. Yes, that's my workstation =PI'm particularly interested on the EFF Open Wireless Router, but they didn't disclose details about the device yet. According to the event rules, the ASUS RT-AC66U (HW Ver. A2) [Version 3.0.0.4.266] is one of the possible targets. As I had a spare RT-AC66U at home, I decided to write a quick guide for everyone interested in participating in this competition CTF.reconThe first thing to do is to find the firmware and its source code. Hopefully, Asus RT-AC66U is GPL'ed and we can easily find its source online. The version used for the contest is an old one, from 2012. In order to perform a better analysis, we are going to grab the sources and the firmware from v3.0.0.4.266 and v3.0.0.4.376.1123 (the most recent one as of this writing).Asus RT-AC66u v3.0.0.4.266 - FirmwareAsus RT-AC66u v3.0.0.4.266 - Source CodeAsus RT-AC66u v3.0.0.4.376.1123 - FirmwareAsus RT-AC66u v3.0.0.4.376.1123 - Source CodeMany firmware versions were published between these two releases, we can review the changelogs to find security issues:http://www.asus.com/Networking/RTAC66U/HelpDesk_Download Yes, that's my workstation =PI'm particularly interested on the EFF Open Wireless Router, but they didn't disclose details about the device yet. According to the event rules, the ASUS RT-AC66U (HW Ver. A2) [Version 3.0.0.4.266] is one of the possible targets. As I had a spare RT-AC66U at home, I decided to write a quick guide for everyone interested in participating in this competition CTF.reconThe first thing to do is to find the firmware and its source code. Hopefully, Asus RT-AC66U is GPL'ed and we can easily find its source online. The version used for the contest is an old one, from 2012. In order to perform a better analysis, we are going to grab the sources and the firmware from v3.0.0.4.266 and v3.0.0.4.376.1123 (the most recent one as of this writing).Asus RT-AC66u v3.0.0.4.266 - FirmwareAsus RT-AC66u v3.0.0.4.266 - Source CodeAsus RT-AC66u v3.0.0.4.376.1123 - FirmwareAsus RT-AC66u v3.0.0.4.376.1123 - Source CodeMany firmware versions were published between these two releases, we can review the changelogs to find security issues:http://www.asus.com/Networking/RTAC66U/HelpDesk_Download According to the rules, we have to identify and exploit a 0-day vulnerability. We can combine different flaws with known issues in order to score points. If the vendor had silently patched an issue and you create an exploit for it, that should be scored as a valid 0-day (I'm not going to start discussing terminologies here).Now that we have the source code, it's time to extract and audi According to the rules, we have to identify and exploit a 0-day vulnerability. We can combine different flaws with known issues in order to score points. If the vendor had silently patched an issue and you create an exploit for it, that should be scored as a valid 0-day (I'm not going to start discussing terminologies here).Now that we have the source code, it's time to extract and audi |
Tool | ★★★★ | ||
| 2014-07-16 23:41:20 | Foxit PDF Reader Stored XSS (lien direct) | A friend of mine was performing an external pentest recently and he started to complain that his traditional Java exploits were not being effective. He was able to map a few applications and defenses in place protecting the client's network but he still needed an initial access to start pivoting.Basic protections like AV, application white-listing as well as more advanced ones like EMET are used to make the life of criminals (and pentesters) harder, but they're often bypassed. While discussing alternatives with my friend, he told me that the company replaced Adobe Reader after seeing lots of Security Advisories for the product. And what was the replacement? Foxit Reader: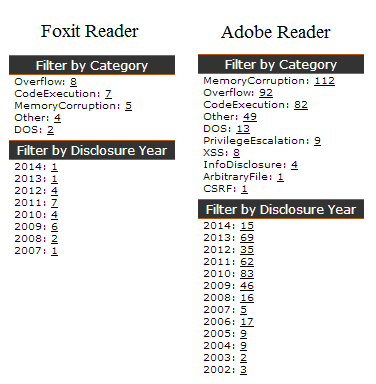 Advisories for Adobe Reader and Foxit Reader listed on OSVDB (May/2014)Less advisories means that the product is more secure, right? Marc Ruef's talk about VDB management summarizes this point: Advisories for Adobe Reader and Foxit Reader listed on OSVDB (May/2014)Less advisories means that the product is more secure, right? Marc Ruef's talk about VDB management summarizes this point: |
Malware Vulnerability Patching Guideline | ★★★★ | ||
| 2014-07-16 23:40:46 | Wildcard DNS, Content Poisoning, XSS and Certificate Pinning (lien direct) | Hi everyone, this time I'm going o talk about an interesting vulnerability that I reported to Google and Facebook a couple of months ago. I had some spare time last October and I started testing for vulnerabilities on a few companies with established bug bounty programs. Google awarded me with $5000,00 and Facebook payed me $500,00 for reporting the bugs.I know you may be more interested on highly sophisticated exploits that allow arbitrary file upload to the Internet, with custom payloads that may lead to unexpected behavior like closing Security Lists. Hopefully this class of bugs is already patched by Fyodor and Attrition is offering an efficient exploit mitigation technique.The title may be a little confusing, but I'm going to show that it's possible to combine all these techniques to exploit vulnerable systems.Content Poisoning and Wildcard DNSHost header poisoning occurs when the application doesn't validate full URL's generated from the HTTP Host header, including the domain name. Recently, the Django Framework fixed a few vulnerabilities related to that and James Kettle made an interesting post discussing lots of attack scenarios using host header attacks.While testing this issue, I found a different kind of Host header attack that abuses the possibility to browse wildcard domains. Let's have a quick look at the Wikipedia entry on Hostnames:"The Internet standards (Request for Comments) for protocols mandate that component hostname labels may contain only the ASCII letters 'a' through 'z' (in a case-insensitive manner), the digits '0' through '9', and the hyphen ('-'). The original specification of hostnames in RFC 952, mandated that labels could not start with a digit or with a hyphen, and must not end with a hyphen. However, a subsequent specification (RFC 1123) permitted hostname labels to start with digits. No other symbols, punctuation characters, or white space are permitted."The fun part here is that the network stack from Windows, Linux and Mac OS X consider domains like -www.plus.google.com, www-.plus.google.com and www.-.plus.google.com valid. It's interesting to note that Android won't resolve these domains for some reason. | Vulnerability Guideline | ★★★★ | ||
| 2014-02-18 09:43:31 | Analyzing Malware for Embedded Devices: TheMoon Worm (lien direct) | All the media outlets are reporting that Embedded Malware is becoming mainstream. This is something totally new and we never heard of this before, right? The high number of Linux SOHO routers with Internet-facing administrative interfaces, the lack of firmware updates and the ease to craft exploits make them a perfect target for online criminals. The Internet of Threats is wildly insecure, but definitely not unpatchable.To all infosec people out there, it's important to understand these threats and report it properly to the media. Some top-notch researchers recently uncovered "Massive Botnets" infecting refrigerators, microwaves, gaming consoles, soda machines and tamagotchis. The problem is that they never provided any sort of evidence, no malware samples, no IOC's and did not write a Hakin9 article describing it. Refrigerator Botnet? Revd. Pastor Laphroaig says Show the PoC || GTFOThe aim for this post is to provide more information to identify/execute embedded binaries, describing how to set your own virtual lab. In case you missed it, head to the first post from the "Analyzing and Running binaries from Firmware Images" series.TheMoon WormJohannes from SANS provided me a sample from "TheMoon" malware and posted some interesting information on their handler's diary. Their honeypots captured the scanning activity and linked the exploit to a vulnerable CGI script running on specific firmwares from the following Linksys routers: E4200, E3200, E3000, E2500, E2100L, E2000, E1550, E1500, E1200, E1000,E900.SANS handlers classified TheMoon as a Worm because of the self-replicating nature of the malware. The worm searches for a "HNAP1" URL to fingerprint and identify potentially vulnerable routers. If you check your FW and Server logs you may find lot's of different IP's probing this URL.The worm was named like this because it contains images from the movie "The Moon". It's possible to carve a few PNG's inside the ELF binary: Refrigerator Botnet? Revd. Pastor Laphroaig says Show the PoC || GTFOThe aim for this post is to provide more information to identify/execute embedded binaries, describing how to set your own virtual lab. In case you missed it, head to the first post from the "Analyzing and Running binaries from Firmware Images" series.TheMoon WormJohannes from SANS provided me a sample from "TheMoon" malware and posted some interesting information on their handler's diary. Their honeypots captured the scanning activity and linked the exploit to a vulnerable CGI script running on specific firmwares from the following Linksys routers: E4200, E3200, E3000, E2500, E2100L, E2000, E1550, E1500, E1200, E1000,E900.SANS handlers classified TheMoon as a Worm because of the self-replicating nature of the malware. The worm searches for a "HNAP1" URL to fingerprint and identify potentially vulnerable routers. If you check your FW and Server logs you may find lot's of different IP's probing this URL.The worm was named like this because it contains images from the movie "The Moon". It's possible to carve a few PNG's inside the ELF binary: |
Malware Vulnerability Patching | ★★★★ | ||
| 2014-01-08 23:57:00 | Unpacking Firmware Images from Cable Modems (lien direct) | Hacking Cable modems used to be very popular during the early 2000's. People like DerEngel and Isabella from TCNiSO carried lots of research on the topic and talks from bitemytaco (R.I.P) and BlakeSelf during DEFCON 16 and DEFCON 18 covered lots of information on the subject.Securing cable modems is more difficult than other embedded devices because, on most cases, you can't choose your own device/firmware and software updates are almost entirely controlled by your ISP. Most cable modems offer a limited administrative interface and management commands are sent using SNMP.Cable Modem FirmwareThere are basically three types of firmware images for cable modems:- Signed and compresed (PKCS#7 & binary)- Compressed binary images- RAM dump images (uncompressed & raw)You can dump your own firmware image using JTAG or sniffing the connection during upgrades, for example. I'm a big fan of binwalk and I always wondered why it doesn't unpack firmwares from popular Broadcom based cable modems so I decided to research on this.Unpacking the FirmwareFor this analysis I'll use Cisco DPC3925, which is a very common DOCSIS 3.0 modem here in Brazil. Cisco DPC3925 has a BCM3380 chipset, 16MB Flash x 64MB DRAM memory configuration.  The compressed firmware image has around 4MB. Using strings against the file didn't help much and binwalk v1.2.1 (without any additional parameters) did not recognize it. The compressed firmware image has around 4MB. Using strings against the file didn't help much and binwalk v1.2.1 (without any additional parameters) did not recognize it. We can gather lots of useful information from the vendor's page: user guides, datasheets, licensing information and open source disclaimer for the product. There are no sources available on Cisco's home, but the Copyright Notices section states that the product uses LZMA SDK 4.21. We can gather lots of useful information from the vendor's page: user guides, datasheets, licensing information and open source disclaimer for the product. There are no sources available on Cisco's home, but the Copyright Notices section states that the product uses LZMA SDK 4.21.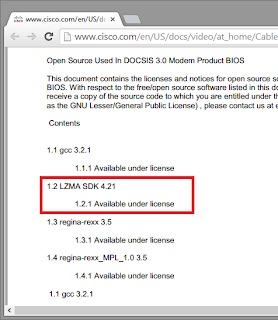 So we know that the firmware is probably packed using LZMA but we still need to figure out how to unpack it. Binwalk - So we know that the firmware is probably packed using LZMA but we still need to figure out how to unpack it. Binwalk - |
Tool | ★★★★ | ||
| 2013-12-10 17:36:29 | Binwally: Directory tree diff tool using Fuzzy Hashing (lien direct) | For this post, I'll discuss about the concept of directory tree and binary diffing and how it could be used to find potential vulnerabilities and security issues that were (silently) patched on firmware images.Silent patching is a big deal as we don't have many security researchers like Spender around. This is a common practice among companies that create software and firmwares for embedded devices. Changelogs from new firmwares often contains few information about security issues, outlining the changes as "bugfixes" or "enhancements": we get no CVE's and we don't know how critical the flaws are.In addition to that, you may occasionally find some reference for the string 'Ac1db1tch3z' on your code (which means that you got a free vulnerability assessment) or your employee Joel might forget to remove a backdoor from the firmware. Diffing the content from previous firmwares may be useful to find out when these backdoors were first installed, modified and/or removed.I introduce you to Binwally: a simple script to perform directory tree diffing using the concept of Fuzzy Hashing (ssdeep) to define a matching score between binaries. Binwally says "no" to Silent PatchingFuzzy HashingFuzzy Hashing, also know as context triggered piecewise hashes (CTPH), can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The concept was introduced by Andrew Tridgell and the most well-known tool is ssdeep, created by Jesse Kornblum.The usage example outlined on ssdeep's homepage summarizes it well:$ ls -l foo.txt-rw-r--r-- 1 jessekor jessekor 240 Oct 25 08:01 foo.txt$ cp foo.txt bar.txt$ echo 1 >> bar.txtA cryptographic hashing algorithm like MD5 can't be used to match these files; they have wildly different hashes.$ md5deep foo.txt bar.txt7b3e9e08ecc391f2da684dd784c5af7c /Users/jessekornblum/foo.txt32436c952f0f4c53bea1dc955a081de4 /Users/jessekornblum/bar.txtBut fuzzy hashing can! We compute the fuzzy hash of one file and use the matching mode to match the other one.$ ssdeep -b foo.txt > hashes.txt$ ssdeep -bm hashes.txt bar.txtbar.txt matches foo.txt (64)The number at the end of the line is a match score, or a weighted measure of how similar these files are. The higher the number, the more similar the files.BinwallyBinwally is a simple Python script that uses this concept to diff directory trees in order to find different, unique and matching files, displaying an overall score of the results. It was based on diffall.py from the book Programming Python (4th Ed Binwally says "no" to Silent PatchingFuzzy HashingFuzzy Hashing, also know as context triggered piecewise hashes (CTPH), can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The concept was introduced by Andrew Tridgell and the most well-known tool is ssdeep, created by Jesse Kornblum.The usage example outlined on ssdeep's homepage summarizes it well:$ ls -l foo.txt-rw-r--r-- 1 jessekor jessekor 240 Oct 25 08:01 foo.txt$ cp foo.txt bar.txt$ echo 1 >> bar.txtA cryptographic hashing algorithm like MD5 can't be used to match these files; they have wildly different hashes.$ md5deep foo.txt bar.txt7b3e9e08ecc391f2da684dd784c5af7c /Users/jessekornblum/foo.txt32436c952f0f4c53bea1dc955a081de4 /Users/jessekornblum/bar.txtBut fuzzy hashing can! We compute the fuzzy hash of one file and use the matching mode to match the other one.$ ssdeep -b foo.txt > hashes.txt$ ssdeep -bm hashes.txt bar.txtbar.txt matches foo.txt (64)The number at the end of the line is a match score, or a weighted measure of how similar these files are. The higher the number, the more similar the files.BinwallyBinwally is a simple Python script that uses this concept to diff directory trees in order to find different, unique and matching files, displaying an overall score of the results. It was based on diffall.py from the book Programming Python (4th Ed |
Tool Vulnerability Patching | ★★★★ | ||
| 2013-09-01 10:52:31 | Analyzing and Running binaries from Firmware Images - Part 1 (lien direct) | During the first part of SIMET Box Firmware analysis, we downloaded the firmware Image, extracted its contents, compared/analyzed its base and found a couple of interesting files (SSH keys, binary files, init scripts, firewall rules and so on).For this part we'll focus on identifying binaries, comparing and executing them to find interesting data. Whenever you're analyzing binaries from different architectures, there are a couple of nice tools that aid debugging, reversing and emulating their behavior, like objdump, readelf and QEMU.Embedded Debian Project provides pre-built binary toolchains for mips, mipsel, arm, armel, powerpc, and a couple of other architectures. In order to download and install it on Debian based Linux distros, you have to apt-get its archive signing key:sudo apt-get install emdebian-archive-keyringNow you you need to include their repository on your /etc/apt/sources.list: deb http://www.emdebian.org/debian/ squeeze mainAfter the apt-get update you can install binutils for you target archs:sudo apt-get install binutils-mips-linux-gnu binutils-mipsel-linux-gnu binutils-arm-linux-gnueabiFor this little exercise I'll analyze three busybox binaries, from three different firmwares: busybox-simet (from SIMET Box), busybox-asuswrt (from AsusWRT-Merlin firmware) and busybox-sb6120 (from Motorolla's SB6120 Surfboard Cable Modem).Architecture, Big-Endian or Little Endian?When analyzing SIMET Box we already knew that the device was based on ar71xx platform, which is MIPS based and big endian as stated on OpenWRT's official page. If you want to find it by your own you can use the file utility: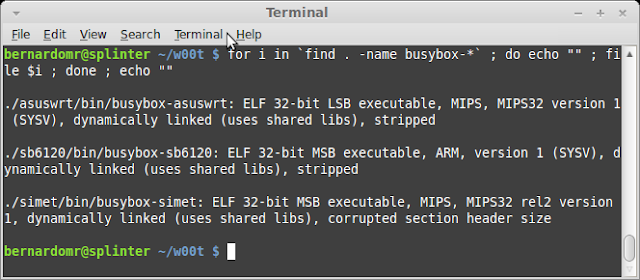 Emdebian binutils also provide useful tools to identify further info from unknown binaries. A nice hack that I commonly use is to display information from object files using different toolchains in order to find out which one understands the file structure properly. For example, objdump -f displays contents of the overall file header.SIMET Box tl-wr740n-v4 (architecture: mips:isa32r2, file format elf32-tradbigmips) Emdebian binutils also provide useful tools to identify further info from unknown binaries. A nice hack that I commonly use is to display information from object files using different toolchains in order to find out which one understands the file structure properly. For example, objdump -f displays contents of the overall file header.SIMET Box tl-wr740n-v4 (architecture: mips:isa32r2, file format elf32-tradbigmips)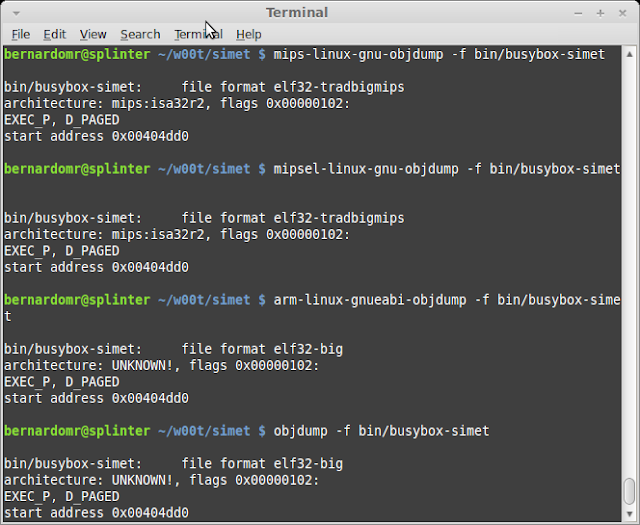 AsusWRT-Merlin v3.0.0.4.374.32 (architecture: mips:isa32 file format elf32-tradlittlemips) AsusWRT-Merlin v3.0.0.4.374.32 (architecture: mips:isa32 file format elf32-tradlittlemips) SB6120 v1.0.2.4-SCM01 (architecture: arm, file format elf32-bigarm) SB6120 v1.0.2.4-SCM01 (architecture: arm, file format elf32-bigarm) |
Malware Hack | ★★★★ | ||
| 2013-08-25 11:13:09 | SIMET Box Firmware Analysis: Embedded Device Hacking & Forensics (lien direct) | For my first blog post I decided to have a quick look on the firmware from SIMET Box. SIMET is organized by the Brazilian NIC.br in order to test and monitor the Internet speed across the country. For more info (in portuguese) visit their site here. All the data collected is available to the community on reports and heat maps like this.The organization is now handing out free Wi-Fi routers to Brazilians in order to measure the Internet quality on different regions. The SIMET Box equipment is a custom TL-WR740N pre-installed with OpenWRT. You can also download and install the standalone firmware on other TPLink's SOHO routers. The project is quite interesting but in times of PRISM and NSA I don't like the idea of using a "black box" at home, so I decided to check its design.FirmwareAs I don't have the actual box, I'll analyze SIMET Box's firmware image. The firmware can be downloaded from http://simet.nic.br/firmware. For this initial analysis I'll be using simetbox-tl-wr740n-v4.bin (MD5 d08798093e1591bece897671e96b5983).Let's start by using Craig Heffner's binwalk and firmware-mod-kit to unsquash the filesystem:binwalk -Me simetbox-tl-wr740n-v4.bin The project is quite interesting but in times of PRISM and NSA I don't like the idea of using a "black box" at home, so I decided to check its design.FirmwareAs I don't have the actual box, I'll analyze SIMET Box's firmware image. The firmware can be downloaded from http://simet.nic.br/firmware. For this initial analysis I'll be using simetbox-tl-wr740n-v4.bin (MD5 d08798093e1591bece897671e96b5983).Let's start by using Craig Heffner's binwalk and firmware-mod-kit to unsquash the filesystem:binwalk -Me simetbox-tl-wr740n-v4.bin After extracting the files we can browse through the squashfs-root dir and grep files to identify OpenWrt's version base: After extracting the files we can browse through the squashfs-root dir and grep files to identify OpenWrt's version base: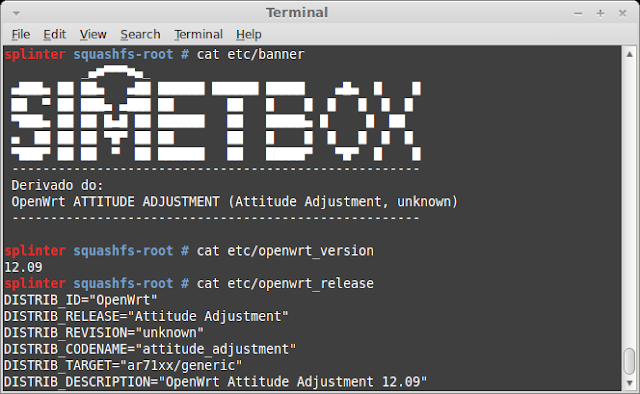 We now know that SIMET Box is based on Attitude Adjustment branch (v12.09) for Atheros AR71xx, downloadable on OpenWRT's official site: We now know that SIMET Box is based on Attitude Adjustment branch (v12.09) for Atheros AR71xx, downloadable on OpenWRT's official site: |
★★★★ | |||
| 2013-08-25 02:38:30 | Hello world (lien direct) | I just started this new Blog to talk about some personal projects, exploits and hacking in general. I'm a Brazilian Infosec guy interested on embedded device hacking (modems, routers etc), webapp security, console hacking and forensics. My twitter handle is @bernardomr, feel free to ping me. |
★ |
1
We have: 21 articles.
We have: 21 articles.
To see everything:
Our RSS (filtrered)
