One Article Review
| Source | |
|---|---|
| Identifiant | 8300158 |
| Date de publication | 2015-11-20 00:02:04 (vue: 2023-01-11 16:56:00) |
| Titre | ARRIS Cable Modem has a Backdoor in the Backdoor |
| Texte | A couple of months ago, some friends invited me to give a talk at NullByte Security Conference. I started to study about some embedded device junk hacking hot topics and decided to talk about cable modem security. Braden Thomas keynoted at Infiltrate 2015 discussing about Practical Attacks on DOCSIS so, yeah, cable modem hacking is still mainstream.On November 21st I'll be at Salvador speaking on "Hacking cable modems: The Later Years". It's not a talk about theft of service and getting free Internet access. I'll focus on the security of the cable modems, the technology used to manage them, how the data is protected and how the ISPs upgrade the firmwares. Spoiler Alert: everything's really really bad.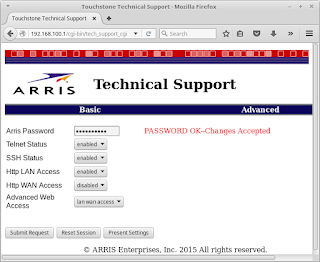 The default password for the SSH user 'root' is 'arris'. When you access the telnet session or authenticate over SSH, the system spawns the 'mini_cli' shell asking for the backdoor password. The default password for the SSH user 'root' is 'arris'. When you access the telnet session or authenticate over SSH, the system spawns the 'mini_cli' shell asking for the backdoor password. |
| Envoyé | Oui |
| Condensat | cert/cc was https://github /usr/sbin/cli 000 031115 1/cgi 10/10 100 168 2009 2015 21st 600 862 :/usr/sbin/arris :conclusioni ;restrictedin @daveitel: able about access accessible account across acts administrative advised affecting affects afl performed again agent agent/usr/sbin/snmp ago alert: algorithm all allowing almost analysis analyzing and api/usr/sbin/mini are armeb arris arriscmdoc30accessclientseed art artist ascii asked asking attacks authenticate authentication awful backdoor backdoors backdoorsarris bad based because been beneficial best bin/adv bin/tech blackhat blog bother braden broader built busybox but bypassing cable can cases cert/cc cgi cgi/usr/www/cgi cgiarris changing check check:yes chiptune choose chosen cli cli/usr/sbin/pacm cm/usr/www/cgi code com/bmaia/cross committee compiled conference consolecowboys contain controlled cool correlating could couple course cross custom customized daily data day day is days decided default describing detailed details device device/firmware devices dg860a did didn different difficult digits disclose disclosure discover discussing distribute dlink dns docsis so dumb embedded enable encoded end entirely envy eulas everything example exploiting externally families fancy feedback files find finish firmware firmwares five fix flaws focus following font for found free friends from full fuzzers gdbserver generate generated generation get getting ghidorah ghost github give going grade graphs guess guys hacking had has have haven heard helpful here here: hidden hired his hosted hosts hot how http http://192 immediately include including indicate infiltrate init/usr/sbin/dimclient/usr/sbin/docsis interesting interface internet invited isp isps issue joel junk just key keygen knowing known last later lcamtuf leet legendary libarris library like load log logins logo long lose mac mainstream make manage manager/usr/sbin/ggncs/usr/sbin/gw manner many marketing marketingof media members metasploit mib mibs mini model modem modems modems: months more most mpsjkmdhai much multiple necessary need needs new not note november now nullbyte number numberafter only order other out over own password passwords people plant poc points policy post practical pretty previously privileged products protected puma5 put pwd qualys quoting really reappear receive redirected release released relieved remote remotely remove report reported researching responsible responsive restricted reverse reversing rfc right root roy/sac and royafnt1 salvador search searches securing security seed serial service session set shall shell shells shits shodan showing since snmp software soho some someone sound spawns speaking specialists spoiler ssh started state still story strace study subject support sure system talk tcpdump tdf technical technician technology telnet telnet/ssh tg862a tg862g than that the the pocs theft their them there these they third this thomas keynoted those thoughtful time timely toilet too toolchain tools topics ts0705125d turn twitter understand undisclosed undocumented update updates upgrade used useful user uses using utils/tree/master/armebwhile vendor vendors very via view visionary vulnerabilities vulnerability w00tsec wait waited was way well were what when whenever whether while with won works would write writing wrote yeah years yet you your |
| Tags | |
| Stories | |
| Notes | ★★★★ |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.