One Article Review
| Source | |
|---|---|
| Identifiant | 8300159 |
| Date de publication | 2015-12-09 01:03:30 (vue: 2023-01-11 16:56:00) |
| Titre | Hack.lu 2015 CTF Write Up: Dr. Bob (Forensic 150) |
| Texte | Hack.lu 2015 CTF was organised by fluxfingers during October 20-22. It's one of the coolest CTFs around, the only drawback is that it runs during week days (hey guys patch this for the next years). My team TheGoonies ranked #59th, which is not bad considering we only played part-time.The task Dr. Bob was the one I found most interesting as it included disk forensics, memory forensics and basic crypto tasks.Task: Dr. Bob (Forensic 150)There are elections at the moment for the representative of the students and the winner will be announced tomorrow by the head of elections Dr. Bob. The local schoolyard gang is gambling on the winner and you could really use that extra cash. Luckily, you are able to hack into the mainframe of the school and get a copy of the virtual machine that is used by Dr. Bob to store the results. The desired information is in the file /home/bob/flag.txt, easy as that.Download: dr_bob_e22538fa166acecc68fa17ac148dcbe2.tar.gzThe file provided is a VirtualBox image in a saved state. According to the challenge instructions, we have to retrieve the flag from the user home folder. The VM starts on a login terminal of what seems to be a Linux distro.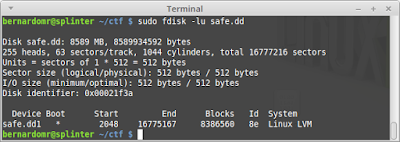 sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! |
| Envoyé | Oui |
| Condensat | #59th cryptsetup flag: flag i the virtualbox /bin/cat /dev/loop0 /dev/loop1 /dev/lvm /dev/sda5after /dev/vg/home /dev/vg/homethe /dev/vg/root /etc/shadow /findaes /home/bob/flag 0x0d 0x1ecc0701ei 1024 1048576 128 150 1: @rbaranyi 1fab015c1e3df9eac8728f65d3d16646 2015 2048 2: david 486 512 able according add administrative aes aes256 after all also analysis and announced any anything approach are arguments around as:c: assigning attempting bad base basic behavior berard berard pointed bin bincryptsetup bits bob bob brings bs=1024 build building built builtin bulk but bytes can carriage carve carving cash challenge char cipher=aes clean clgt cluster com/bmaia/rekall combination command command: considering contains conv=notrunc convert converttoraw coolest copy corresponding corrupt could couldn count=1hexdump crack create crypto cryptsetup cryptsetup:cryptsetup csi ctf ctf was ctfs data david days ddcryptsetup ddlet ddsudo debian debugging debugvm decided decrypt decrypting desired device devices: didn different disk disks displaying distro dmsetup does download: downloaded drawback dump dumped dumps dumpvmcore dumpyou during dwarf e22538fa166acecc68fa17ac148dcbe2 easier easiest easy ecb elections eliminating enabled encrypted encryption ept everything exe extended externally:sudo extra extract extracted extracting extractor f0r far fdisk file file= file=key filename=getthekey files final find findaes first flag fluxfingers during folder follow for forensic forensics forensics: format found framework from full gambling gang generate get gives good grab group guest guide guys gzthe hack hackish had has hash=sha1 hashes have head header headers here here:https://github hexdump hey hide home host hypervisors i386 i686 identifies identify if=/dev/vg/home if=/dev/zero image image= imagecopy images img imgdd imgecho imghexdump imgthey inception inceptionnow inceptionrekall included independent information installation installed instructions interesting internalcommands into introspection invoke involve iso it: kernel key key key: keynow keys keys:bulk kind know known lab layer let like line linux live liverekal local logically login logs/history losetup luckily luks luksaddkey luksdump luksformat lvmdiskscanthere machine machines mainframe make map mapper master matches math memdump memory mirrored module moment most mount mounted necessary need needed new newer next noes none normally not now october of=test offer offers offset one only operating option oracle organised original out output p3dr0 page parameter parse part pass passphrase passphrase:dd password patch payload perform physical played plugin plugin: plugins pluma pmem pointed possible pretty problems proceed profile profilelinux profiles profilesmemory profit program programs proper provided ram ranked raw rawthe really recreate rekal rekall rekallunlike remount replacing repository representative requires results retrieve return reveal revealed root route run running runs safe safeclone saved scans schedule school schoolyard search secrets seems set shows sign simple size size: size=128 skills software some standard start starts state step store straightforward strings students sudo support supports sure symbols system tables tailoured take tar target task task: tasks team teams terminal test that the thegoonies them then there these this time together tomorrow tool tools transparent tried true two txt unencrypted unleash up: update use used useful user using v0t3 valid value vboxmanage vdi verify virtual virtualbox virtualization vms vmscan vmware volatility volume was week well were what which will winner with work would wouldn write writeup xxd years you zip |
| Tags | Hack Tool |
| Stories | |
| Notes | ★★★★ |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.