One Article Review
| Source | |
|---|---|
| Identifiant | 8300164 |
| Date de publication | 2014-12-04 20:47:07 (vue: 2023-01-11 16:56:00) |
| Titre | 9447 2014 CTF Write Up: coor coor |
| Texte | The Australian 9447 Security Society CTF took place on November 29-30 and it was yet another fun and really professionally organized CTF. I played with my friends from TheGoonies once again (The Goonies 'R' Good Enough, right?).I found the task "coor coor" particularly interesting: it was a good way to practice some concepts from the new book I recently bought: The Art of Memory Forensics (authored by @attrc and @gleeda).Task: coor coor (misc - 400)A 9447 CTF organizer is giving away flags to friends that he trusts. This memory dump was taken off a competitor's computer after a raid by the pwnpolice. Download provided: https://s3-us-west-2.amazonaws.com/elasticbeanstalk-us-west-2-467703568171/challenges/coorcoor.tar.bz2Let's start by identifying the Operating System profile:python vol.py -f challenge.vmem imageinfo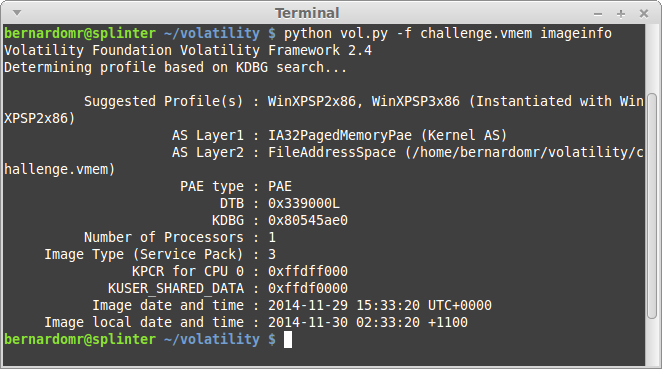 Let's take screenshot to see what the user was doing:python vol.py -f challenge.vmem screenshot -D screenshot/ Let's take screenshot to see what the user was doing:python vol.py -f challenge.vmem screenshot -D screenshot/ The user was running something inside VirtualBox, let's keep digging:python vol.py -f challenge.vmem psxview The user was running something inside VirtualBox, let's keep digging:python vol.py -f challenge.vmem psxview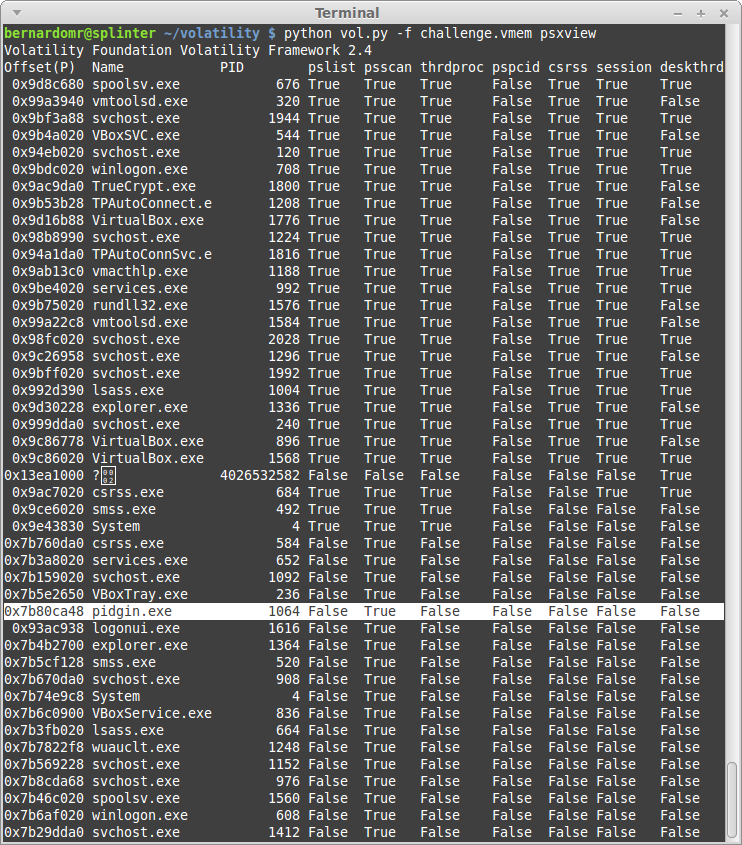 python vol.py -f challenge.vmem filescan | grep -e "\.tc\|TrueCrypt" python vol.py -f challenge.vmem filescan | grep -e "\.tc\|TrueCrypt"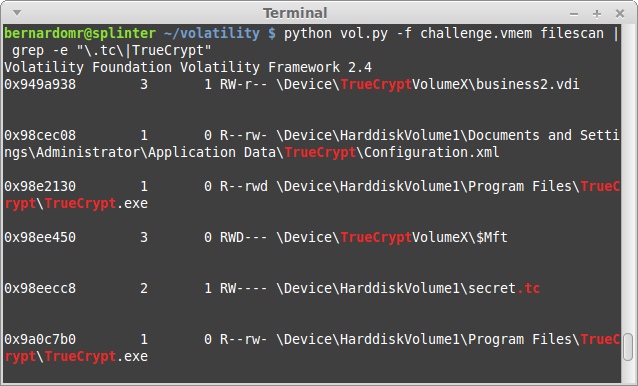 The user was basically running a VirtualBox machine (business2.vdi) from an Encrypted TrueCrypt container (secret.tc). That's why we used psxview to list the system processes before. Note that the lower offsets are used by the Host and the higher ones (after 0x7b760da0) are used by the guest OS. So what was he doing?python vol.py -f challenge.vmem connscan The user was basically running a VirtualBox machine (business2.vdi) from an Encrypted TrueCrypt container (secret.tc). That's why we used psxview to list the system processes before. Note that the lower offsets are used by the Host and the higher ones (after 0x7b760da0) are used by the guest OS. So what was he doing?python vol.py -f challenge.vmem connscan |
| Envoyé | Oui |
| Condensat | #9447ctf messages otr 0x7b760da0 114 149 2014 400 467703568171/challenges/coorcoor 9447 9447ctfforemost @gleeda a metasploit acidburn88 active actually admin after again amazonaws and and otr another appdata are aren art asking australian 9447 authored away basically because before book bought: the business2 by @attrc and bz2let can carve challenge champ channel: com/elasticbeanstalk communication: otr competitor compromised computer concepts connect connscanthe container control conversation conversations coor could couple creates ctf ctf took day decided default description did digging:python doing doing:python download dump dump:because during easily encrypt encrypted encryption enough extension extracted figure figured files filescan fingerprint using fingerprints first flag:9447 flags following for foremost:python forensics forensics forge forward found friends frind from from thegoonies once fun get giving good goonies got grep guest hacked had happened higher his host how identifying imageinfolet impersonate inside installation instance interesting: irc just keep key keys let list live logged logs long lose lower machine managed memory message mftparser misc module to needed new next night not note november off offsets one ones only operating organized organizer otr out: own particularly perfect phase pidgin place played plumbing plumbing:6667 post practice previous private processes professionally profile:python provided: https://s3 prpl psxview psxviewpython purple pwnpolice python quickly raid read really recently replaced retrieve right running screenshot screenshot/the searched secrecy secret security see server session short sign signature sleep society some something spent start still stolen stuck system tags take taken tar task task: term testicool69 that the there these thing this those three time truecrypt trusted trusts trying up: used user using vdi virtualbox vmem vmemprivate vol was way west what whole why with works write yet yodawg you your |truecrypt |
| Tags | |
| Stories | |
| Notes | ★★★★ |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.