One Article Review
| Source | |
|---|---|
| Identifiant | 8300168 |
| Date de publication | 2014-07-16 23:41:20 (vue: 2023-01-11 16:56:00) |
| Titre | Foxit PDF Reader Stored XSS |
| Texte | A friend of mine was performing an external pentest recently and he started to complain that his traditional Java exploits were not being effective. He was able to map a few applications and defenses in place protecting the client's network but he still needed an initial access to start pivoting.Basic protections like AV, application white-listing as well as more advanced ones like EMET are used to make the life of criminals (and pentesters) harder, but they're often bypassed. While discussing alternatives with my friend, he told me that the company replaced Adobe Reader after seeing lots of Security Advisories for the product. And what was the replacement? Foxit Reader: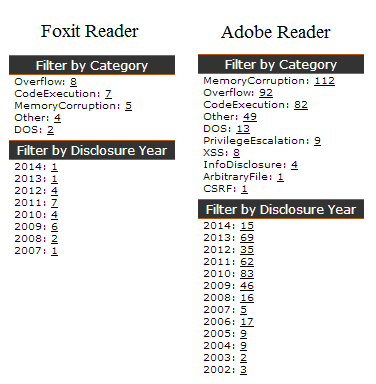 Advisories for Adobe Reader and Foxit Reader listed on OSVDB (May/2014)Less advisories means that the product is more secure, right? Marc Ruef's talk about VDB management summarizes this point: Advisories for Adobe Reader and Foxit Reader listed on OSVDB (May/2014)Less advisories means that the product is more secure, right? Marc Ruef's talk about VDB management summarizes this point: |
| Envoyé | Oui |
| Condensat | = marc ones 01: 03: 0429 1/foxit 11: 2014 21fixed 24: :affected able about accepts access activex admin adobe advanced advisories advisory advisoryhttp://www after ago all also alternative alternatives analyze and another answered any application applications approaches are ask asking assigned attachment attachments attack attackers attempt av/whitelisting backdoor basic basically because beef behavior being bernardo better big block blocked blog booted brazilian browser or browser pdf bug bulletins but bypass bypassed called can cansecwest case cause caused certainly chars chong clearly click clicking client com/support/security comic company comparison complain complete completed compressed compromise compromised confirmed contact cool core could couple cpl craft create created creates criminals critical current cve david days default defenses described describing desktop>reg desktop>type detect detection different dilbert disclose disclosed discovery:exploit discussing displaying displays distribute dna document documents” does doesn double drag drops during earlierfoxit earliersolutionupgrade edit editor effective embed emet encodings engagement enjoyed enterprise entry entry:c: everybody example executable exploit exploitation exploits external fall favorite featuring few file file1 filenames filenamethat files files/documents filex finish first firstly fit fixed flag flagged flaw folder for found foxit foxitsoftware framework friend from getting gmail gmail:3 good hacking had haifei harder have head hearing here him his hkey hook hope how idea ideal import initial installation:1 instruct interesting internal into ioc issue issue;2014 it: itmost itthere java knew know leading least less let life like likes linux list listed listing load localhost long lots mail mails: make makes malicious malware management many map matter may may/2014 means mechanism microsoft mine modify moment more most much need needed network noisy not notified now object offensive often old one open opened opening operation origin osvdb other outlook outlook:registry pac page panel part patch patching path: paths payload pdf pentest pentesters people performing persistence phantompdf phishing phishingi php#frd pivoting place players please point:the policy post posture powershell problems process2014 product products project prompted properly protecting protections providers proxy publicly pwn pwned rare reader reader:advisories reading recent recently reg registry regthe regwindows released releasing reliable remembered replaced replacement respond restrictions right rodrigues ross made rtf ruef run same scenario scenarios scripts section secure security seeing seem send sending services sets should showing simple situation software solution solutions some soon sophisticated special start started still stored subject successfully summarizes summaryfoxit system systems tab talk tamper targeted technique techniques technologies temp test that the their them them:registry there these they think this threats three time to load told traditional tried twice two unable unusual use used user users using vdb vectors vendor version versionsfoxit victim video vulnerabilities vulnerability w00t wait waited want warning:conclusionyou was wasn ways well were what when whenever where while white why window windows winrar with won word wordpad would write writing xss yet you your youtube zip “recent |
| Tags | Malware Vulnerability Patching Guideline |
| Stories | |
| Notes | ★★★★ |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.