One Article Review
| Source | |
|---|---|
| Identifiant | 916533 |
| Date de publication | 2018-11-24 15:23:09 (vue: 2018-11-24 22:02:56) |
| Titre | Even More on Threat Hunting |
| Texte |  In response to my post More on Threat Hunting, Rob Lee asked:[D]o you consider detection through ID'ing/“matching” TTPs not hunting?To answer this question, we must begin by clarifying "TTPs." Most readers know TTPs to mean tactics, techniques and procedures, defined by David Bianco in his Pyramid of Pain post as:How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between.In case you've forgotten David's pyramid, it looks like this. In response to my post More on Threat Hunting, Rob Lee asked:[D]o you consider detection through ID'ing/“matching” TTPs not hunting?To answer this question, we must begin by clarifying "TTPs." Most readers know TTPs to mean tactics, techniques and procedures, defined by David Bianco in his Pyramid of Pain post as:How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between.In case you've forgotten David's pyramid, it looks like this.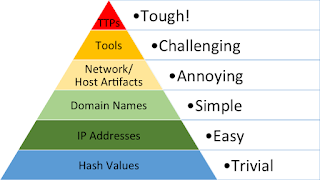 It's important to recognize that the pyramid consists of indicators of compromise (IOCs). David uses the term "indicator" in his original post, but his follow-up post from his time at Sqrrl makes this clear:There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Sqrrl Security Architect, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. At this point it should be clear that I consider TTPs to be one form of IOC.In The Practice of Network Security Monitoring, I included the following workflow: It's important to recognize that the pyramid consists of indicators of compromise (IOCs). David uses the term "indicator" in his original post, but his follow-up post from his time at Sqrrl makes this clear:There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Sqrrl Security Architect, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. At this point it should be clear that I consider TTPs to be one form of IOC.In The Practice of Network Security Monitoring, I included the following workflow: |
| Envoyé | Oui |
| Condensat | at he i milieu nevertheless today upon *this 193 2000s 2003 2013 2018 20this aaron about accomplishing actions activity added advanced adversary advice agent agent* agents agents aggregation ago air all already also alternative analysis analyst analysts analyzed answer answered any anything appealing architect are as:how asc ask asked: assumption assumptions attacker attackers automated baggage basic beating because begin bejtlich between bianco big blog blogspot blue book both build but called can case categorize centric chest chris cirt clarifying clear clear:there codify column com communicate communication community compared compromise concept consider consists copyright count counts course created critical data david defender defenders define defined definition detect detection did didn digital discernible discovered diverges does doing done during emotional emphasis enemy entries environment even every evidence examining example excerpts excited exfiltration expedite experts explore facilitate fact field file finally find findings follow following force forget forgotten form formally forms found free frequent frequently friendly from future goes group groups guides hacking had hashes have her here:select his how however http httpproxy human hunt hunter hunters hunting hypotheses hypothesis hypothesis: identify identifying important included incorporate indicator indicators informally ing/“matching” inputs insert instead interpret intruders invented investigate investigator ioc iocs italics its junior killer know language least lee let like likely limit list look looking looks love machine machines make makes malicious malware manifestations manual market match matching may mazilla/4 mean method methodologies methods mid might mindset mission modern monitoring more most must network networks new normal not nothing novel nsm observable occupying occurrences offered offers once one only operations order original over own packaged page pain part: people performed point popularized post post:assumption: practice prevention procedures process produced products professionals profile projection promote provide purposes pursue pyramid queries query question question: questions ranging reader readers recognize reconnaissance refer referred relying remember require responding response results results: richard rob rule sad said sanders say search second security see seems sees selects senior set should signs simple snort sometimes sorted source sqrrl step string strings success suggestive suricata suspicious system systems tactics taosecurity team technical technique techniques term thankful themselves then thinks threat threats through time titled tl;dr top traffic trips true ttps unique unknown unusual upon use useful user users uses using validate validating variety various vendors very victim wade way ways what where wherein whether which why wide wider will womp work workflow:you works world wrong wrote wrote:analysis www xxxx years you “did “hunting ”method: |
| Tags | Malware Threat |
| Stories | |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.