What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-05-01 14:00:00 | Uncharmed: Untangling Iran\'s APT42 Operations (lien direct) | Written by: Ofir Rozmann, Asli Koksal, Adrian Hernandez, Sarah Bock, Jonathan Leathery
APT42, an Iranian state-sponsored cyber espionage actor, is using enhanced social engineering schemes to gain access to victim networks, including cloud environments. The actor is targeting Western and Middle Eastern NGOs, media organizations, academia, legal services and activists. Mandiant assesses APT42 operates on behalf of the Islamic Revolutionary Guard Corps Intelligence Organization (IRGC-IO). APT42 was observed posing as journalists and event organizers to build trust with their victims through ongoing correspondence, and to deliver invitations to conferences or legitimate documents. These social engineering schemes enabled APT42 to harvest credentials and use them to gain initial access to cloud environments. Subsequently, the threat actor covertly exfiltrated data of strategic interest to Iran, while relying on built-in features and open-source tools to avoid detection. In addition to cloud operations, we also outline recent malware-based APT42 operations using two custom backdoors: NICECURL and TAMECAT. These backdoors are delivered via spear phishing, providing the attackers with initial access that might be used as a command execution interface or as a jumping point to deploy additional malware. APT42 targeting and missions are consistent with its assessed affiliation with the IRGC-IO, which is a part of the Iranian intelligence apparatus that is responsible for monitoring and preventing foreign threats to the Islamic Republic and domestic unrest. APT42 activities overlap with the publicly reported actors CALANQUE (Google Threat Analysis Group), Charming Kitten (ClearSky and CERTFA), Mint Sandstorm/Phosphorus (Microsoft), TA453 (Proofpoint), Yellow Garuda (PwC), and ITG18 ( |
Malware Tool Threat Cloud | Yahoo APT 35 APT 42 | ★★ | |
| 2024-04-30 14:00:00 | Protection des ransomwares et stratégies de confinement: conseils pratiques pour le durcissement et la protection des infrastructures, des identités et des points de terminaison Ransomware Protection and Containment Strategies: Practical Guidance for Hardening and Protecting Infrastructure, Identities and Endpoints (lien direct) |
Written by: Matthew McWhirt, Omar ElAhdan, Glenn Staniforth, Brian Meyer
 Multi-faceted extortion via ransomware and/or data theft is a popular end goal for attackers, representing a global threat targeting organizations in all industries. The impact of a successful ransomware event can be material to an organization, including the loss of access to data, systems, and prolonged operational outages. The potential downtime, coupled with unforeseen expenses for restoration, recovery, and implementation of new security processes and controls can be overwhelming.Since the initial launch of our report in 2019, data theft and ransomware deployment tactics have continued to evolve and escalate. This evolution marks a shift from manual or script-based ransomware deployment to sophisticated, large-scale operations, including:
Weaponizing Trusted Service Infrastructure (TSI): Adversaries are increasingly abusing legitimate infrastructure and security tools (TSI) to rapidly propagate malware or ransomware across entire networks.
Targeting Virtualization Platforms: Attackers are actively focusing on the virtualization layer, aiming to mass-encrypt virtual machines (VMs) and other critical systems at scale.
Targeting Backup Data / Platforms: Threat actors are exploiting misconfigurations or security gaps in backup systems to either erase or corrupt data backups, severely hindering recovery efforts.
Based upon these newer techniques, it is critical that organizations identify the span of the attack surface, and align proper security controls and visibility that includes coverage for protecting:
Identities
Endpoints
Network Architectures
Remote Access Platforms
Trusted Service Infrastructure (TSI)
Cascading weaknesses across these layers create opportunities for attackers to breach an organization\'s perimeter, gain initial access, and maintain a persistent foothold within the compromised network.
In our updated report,
Multi-faceted extortion via ransomware and/or data theft is a popular end goal for attackers, representing a global threat targeting organizations in all industries. The impact of a successful ransomware event can be material to an organization, including the loss of access to data, systems, and prolonged operational outages. The potential downtime, coupled with unforeseen expenses for restoration, recovery, and implementation of new security processes and controls can be overwhelming.Since the initial launch of our report in 2019, data theft and ransomware deployment tactics have continued to evolve and escalate. This evolution marks a shift from manual or script-based ransomware deployment to sophisticated, large-scale operations, including:
Weaponizing Trusted Service Infrastructure (TSI): Adversaries are increasingly abusing legitimate infrastructure and security tools (TSI) to rapidly propagate malware or ransomware across entire networks.
Targeting Virtualization Platforms: Attackers are actively focusing on the virtualization layer, aiming to mass-encrypt virtual machines (VMs) and other critical systems at scale.
Targeting Backup Data / Platforms: Threat actors are exploiting misconfigurations or security gaps in backup systems to either erase or corrupt data backups, severely hindering recovery efforts.
Based upon these newer techniques, it is critical that organizations identify the span of the attack surface, and align proper security controls and visibility that includes coverage for protecting:
Identities
Endpoints
Network Architectures
Remote Access Platforms
Trusted Service Infrastructure (TSI)
Cascading weaknesses across these layers create opportunities for attackers to breach an organization\'s perimeter, gain initial access, and maintain a persistent foothold within the compromised network.
In our updated report, |
Ransomware Malware Tool Threat | ★★★ | ||
| 2024-04-29 14:00:00 | De l'assistant à l'analyste: la puissance de Gemini 1.5 Pro pour l'analyse des logiciels malveillants From Assistant to Analyst: The Power of Gemini 1.5 Pro for Malware Analysis (lien direct) |
Executive Summary A growing amount of malware has naturally increased workloads for defenders and particularly malware analysts, creating a need for improved automation and approaches to dealing with this classic threat. With the recent rise in generative AI tools, we decided to put our own Gemini 1.5 Pro to the test to see how it performed at analyzing malware. By providing code and using a simple prompt, we asked Gemini 1.5 Pro to determine if the file was malicious, and also to provide a list of activities and indicators of compromise. We did this for multiple malware files, testing with both decompiled and disassembled code, and Gemini 1.5 Pro was notably accurate each time, generating summary reports in human-readable language. Gemini 1.5 Pro was even able to make an accurate determination of code that - at the time - was receiving zero detections on VirusTotal. In our testing with other similar gen AI tools, we were required to divide the code into chunks, which led to vague and non-specific outcomes, and affected the overall analysis. Gemini 1.5 Pro, however, processed the entire code in a single pass, and often in about 30 to 40 seconds. Introduction The explosive growth of malware continues to challenge traditional, manual analysis methods, underscoring the urgent need for improved automation and innovative approaches. Generative AI models have become invaluable in some aspects of malware analysis, yet their effectiveness in handling large and complex malware samples has been limited. The introduction of Gemini 1.5 Pro, capable of processing up to 1 million tokens, marks a significant breakthrough. This advancement not only empowers AI to function as a powerful assistant in automating the malware analysis workflow but also significantly scales up the automation of code analysis. By substantially increasing the processing capacity, Gemini 1.5 Pro paves the way for a more adaptive and robust approach to cybersecurity, helping analysts manage the asymmetric volume of threats more effectively and efficiently. Traditional Techniques for Automated Malware Analysis The foundation of automated malware analysis is built on a combination of static and dynamic analysis techniques, both of which play crucial roles in dissecting and understanding malware behavior. Static analysis involves examining the malware without executing it, providing insights into its code structure and unobfuscated logic. Dynamic analysis, on the other hand, involves observing the execution of the malware in a controlled environment to monitor its behavior, regardless of obfuscation. Together, these techniques are leveraged to gain a comprehensive understanding of malware. Parallel to these techniques, AI and machine learning (ML) have increasingly been employed to classify and cluster malware based on behavioral patterns, signatures, and anomalies. These methodologies have ranged from supervised learning, where models are trained on labeled datasets, to unsupervised learning for clustering, which identifies patterns without predefined labels to group similar malware. | Malware Hack Tool Vulnerability Threat Studies Prediction Cloud Conference | Wannacry | ★★★ | |
| 2024-04-25 10:00:00 | Pole Voûte: cyber-menaces aux élections mondiales Poll Vaulting: Cyber Threats to Global Elections (lien direct) |
Written by: Kelli Vanderlee, Jamie Collier
Executive Summary The election cybersecurity landscape globally is characterized by a diversity of targets, tactics, and threats. Elections attract threat activity from a variety of threat actors including: state-sponsored actors, cyber criminals, hacktivists, insiders, and information operations as-a-service entities. Mandiant assesses with high confidence that state-sponsored actors pose the most serious cybersecurity risk to elections. Operations targeting election-related infrastructure can combine cyber intrusion activity, disruptive and destructive capabilities, and information operations, which include elements of public-facing advertisement and amplification of threat activity claims. Successful targeting does not automatically translate to high impact. Many threat actors have struggled to influence or achieve significant effects, despite their best efforts. When we look across the globe we find that the attack surface of an election involves a wide variety of entities beyond voting machines and voter registries. In fact, our observations of past cycles indicate that cyber operations target the major players involved in campaigning, political parties, news and social media more frequently than actual election infrastructure. Securing elections requires a comprehensive understanding of many types of threats and tactics, from distributed denial of service (DDoS) to data theft to deepfakes, that are likely to impact elections in 2024. It is vital to understand the variety of relevant threat vectors and how they relate, and to ensure mitigation strategies are in place to address the full scope of potential activity. Election organizations should consider steps to harden infrastructure against common attacks, and utilize account security tools such as Google\'s Advanced Protection Program to protect high-risk accounts. Introduction The 2024 global election cybersecurity landscape is characterized by a diversity of targets, tactics, and threats. An expansive ecosystem of systems, administrators, campaign infrastructure, and public communications venues must be secured against a diverse array of operators and methods. Any election cybersecurity strategy should begin with a survey of the threat landscape to build a more proactive and tailored security posture. The cybersecurity community must keep pace as more than two billion voters are expected to head to the polls in 2024. With elections in more than an estimated 50 countries, there is an opportunity to dynamically track how threats to democracy evolve. Understanding how threats are targeting one country will enable us to better anticipate and prepare for upcoming elections globally. At the same time, we must also appreciate the unique context of different countries. Election threats to South Africa, India, and the United States will inevitably differ in some regard. In either case, there is an opportunity for us to prepare with the advantage of intelligence. |
Ransomware Malware Hack Tool Vulnerability Threat Legislation Cloud Technical | APT 40 APT 29 APT 28 APT 43 APT 31 APT 42 | ★★★ | |
| 2024-04-23 12:00:00 | M-Trends 2024: Notre vue depuis les fronts M-Trends 2024: Our View from the Frontlines (lien direct) |
 Attackers are taking greater strides to evade detection. This is one of the running themes in our latest release: M-Trends 2024. This edition of our annual report continues our tradition of providing relevant attacker and defender metrics, and insights into the latest attacker tactics, techniques and procedures, along with guidance and best practices on how organizations and defenders should be responding to threats.
This year\'s M-Trends report covers Mandiant Consulting investigations of targeted attack activity conducted between January 1, 2023 and December 31, 2023. During that time, many of our observations demonstrate a more concerted effort by attackers to evade detection, and remain undetected on systems for longer periods of time:
Increased targeting of edge devices, and platforms that traditionally lack endpoint detection and response solutions.
A more than 50% growth in zero-day usage over the same reporting period in 2022, both by espionage groups as well as financially-motivated attackers.
More “living off the land,” or use of legitimate, pre-installed tools and software within an environment.
Despite the increased focus on evasion by attackers, we are pleased to report that defenders are generally continuing to improve at detecting threats. Dwell time represents the period an attacker is on a system from compromise to detection, and in 2023 the global median dwell time is now 10 days, down from 16 days in 2022. While various factors (such as ransomware) help drive down dwell time, it\'s still a big win for defenders. We can\'t let up, however. Mandiant red teams need only five to seven days on average to achieve their objectives, so organizations must remain vigilant. Other M-Trends 2024 metrics include:
54% of organizations first learned of a compromise from an external source (down from 63% in 2022), while 46% first identified evidence of a compromise internally.
Our engagements most frequently occurred at financial services organizations (17.3%), business and professional services (13.3%), high tech (12.4%), retail and hospitality (8.6%), healthcare (8.1%), and government (8.1%).
The most common initial infection vectors were exploits (38%), phishing (17%), prior compromise (15%), and stolen credentials (10%).
Additional topics covered in detail in M-Trends 2024 include Chinese espionage operations targeting the visibility gap, the evolution of phishing amid shifting security controls, the use of adversary-in-the-middle to overcome multi-factor authentication, cloud intrusion trends, an
Attackers are taking greater strides to evade detection. This is one of the running themes in our latest release: M-Trends 2024. This edition of our annual report continues our tradition of providing relevant attacker and defender metrics, and insights into the latest attacker tactics, techniques and procedures, along with guidance and best practices on how organizations and defenders should be responding to threats.
This year\'s M-Trends report covers Mandiant Consulting investigations of targeted attack activity conducted between January 1, 2023 and December 31, 2023. During that time, many of our observations demonstrate a more concerted effort by attackers to evade detection, and remain undetected on systems for longer periods of time:
Increased targeting of edge devices, and platforms that traditionally lack endpoint detection and response solutions.
A more than 50% growth in zero-day usage over the same reporting period in 2022, both by espionage groups as well as financially-motivated attackers.
More “living off the land,” or use of legitimate, pre-installed tools and software within an environment.
Despite the increased focus on evasion by attackers, we are pleased to report that defenders are generally continuing to improve at detecting threats. Dwell time represents the period an attacker is on a system from compromise to detection, and in 2023 the global median dwell time is now 10 days, down from 16 days in 2022. While various factors (such as ransomware) help drive down dwell time, it\'s still a big win for defenders. We can\'t let up, however. Mandiant red teams need only five to seven days on average to achieve their objectives, so organizations must remain vigilant. Other M-Trends 2024 metrics include:
54% of organizations first learned of a compromise from an external source (down from 63% in 2022), while 46% first identified evidence of a compromise internally.
Our engagements most frequently occurred at financial services organizations (17.3%), business and professional services (13.3%), high tech (12.4%), retail and hospitality (8.6%), healthcare (8.1%), and government (8.1%).
The most common initial infection vectors were exploits (38%), phishing (17%), prior compromise (15%), and stolen credentials (10%).
Additional topics covered in detail in M-Trends 2024 include Chinese espionage operations targeting the visibility gap, the evolution of phishing amid shifting security controls, the use of adversary-in-the-middle to overcome multi-factor authentication, cloud intrusion trends, an |
Tool Vulnerability Threat Medical Cloud | ★★★★ | ||
| 2024-04-22 14:00:00 | Niveaux FAKENET-NG: Présentation de la sortie interactive basée sur HTML FakeNet-NG Levels Up: Introducing Interactive HTML-Based Output (lien direct) |
Written by: Beleswar Prasad Padhi, Tina Johnson, Michael Bailey, Elliot Chernofsky, Blas Kojusner
FakeNet-NG is a dynamic network analysis tool that captures network requests and simulates network services to aid in malware research. The FLARE team is committed to maintaining and updating the tool to improve its capabilities and usability. FakeNet is compatible across platforms and extensively customizable; however, we recognized a need to present captured network data in a more intuitive and user-friendly way to help you quickly identify relevant Network-Based Indicators (NBIs). To address this challenge and further enhance the usability, we extended FakeNet-NG to generate HTML-based output that enables you to view, explore, and share captured network data. This feature was implemented by Beleswar Prasad Padhi as part of a Google Summer of Code (GSoC) project that the Mandiant FLARE team mentored in 2023. To learn more about the program and our open-source contributors, check out the introductory post. Interactive HTML-Based Output FakeNet-NG\'s new interactive output is backed by an HTML page coupled with inline CSS and Javascript. Figure 1 shows the new HTML-based output and Figure 2 shows FakeNet-NG\'s existing text-based output.  Figure 1: FakeNet-NG\'s new HTML-based output
Figure 1: FakeNet-NG\'s new HTML-based output
 Figure 2: FakeNet-NG\'s text-based output
FakeNet-NG generates each report using a
Figure 2: FakeNet-NG\'s text-based output
FakeNet-NG generates each report using a |
Malware Tool Cloud | ★★ | ||
| 2024-04-17 10:00:00 | Unearthing APT44: Russia\'s Notorious Cyber Sabotage Unit Sandworm (lien direct) | Written by: Gabby Roncone, Dan Black, John Wolfram, Tyler McLellan, Nick Simonian, Ryan Hall, Anton Prokopenkov, Luke Jenkins, Dan Perez, Lexie Aytes, Alden Wahlstrom
With Russia\'s full-scale invasion in its third year, Sandworm (aka FROZENBARENTS) remains a formidable threat to Ukraine. The group\'s operations in support of Moscow\'s war aims have proven tactically and operationally adaptable, and as of today, appear to be better integrated with the activities of Russia\'s conventional forces than in any other previous phase of the conflict. To date, no other Russian government-backed cyber group has played a more central role in shaping and supporting Russia\'s military campaign. Yet the threat posed by Sandworm is far from limited to Ukraine. Mandiant continues to see operations from the group that are global in scope in key political, military, and economic hotspots for Russia. Additionally, with a record number of people participating in national elections in 2024, Sandworm\'s history of attempting to interfere in democratic processes further elevates the severity of the threat the group may pose in the near-term. Given the active and diffuse nature of the threat posed by Sandworm globally, Mandiant has decided to graduate the group into a named Advanced Persistent Threat: APT44. As part of this process, we are releasing a report, “APT44: Unearthing Sandworm”, that provides additional insights into the group\'s new operations, retrospective insights, and context on how the group is adjusting to support Moscow\'s war aims. Key Findings Sponsored by Russian military intelligence, APT44 is a dynamic and operationally mature threat actor that is actively engaged in the full spectrum of espionage, attack, and influence operations. While most state-backed threat groups tend to specialize in a specific mission such as collecting intelligence, sabotaging networks, or conducting information operations, APT44 stands apart in how it has honed each of these capabilities and sought to integrate them into a unified playbook over time. Each of these respective components, and APT44\'s efforts to blend them for combined effect, are foundational to Russia\'s guiding “information confrontation” concept for cyber warfare.  Figure 1: APT44\'s spectrum of operations
APT44 has aggressively pursued a multi-
Figure 1: APT44\'s spectrum of operations
APT44 has aggressively pursued a multi- |
Malware Tool Threat Mobile Cloud | NotPetya | ★★ | |
| 2024-04-09 14:00:00 | Apache XML Security pour la bibliothèque C ++ permet la contrefaçon de demande côté serveur Apache XML Security for C++ Library Allows for Server-Side Request Forgery (lien direct) |
Written by: Jacob Thompson
The Apache XML Security for C++ library, code named xml-security-c, is part of the Apache Santuario project. The library implements the XML Digital Signature and the XML Signature specifications, making them available to C++ developers. By default, the library resolves references to external URIs passed in Extensible Markup Language (XML) signatures, allowing for server-side request forgery (SSRF). There is no way to disable this feature through configuration alone, and there is no patch available; the developer must either scan their codebase to find every usage of xml-security-c and override the URI resolver to avoid SSRF, or manually patch and recompile the library to remove the capability entirely. We recommend that C++ developers using XML audit their code bases for usage of this library and determine whether they have introduced a security vulnerability, and if so, modify their code to avoid SSRF. Background Server-side request forgery (SSRF) is a class of security vulnerability in which an untrusted party tricks a server into making an HTTP request by passing the server a malicious input. Although the attacker usually cannot view the response, requests to the loopback interface (127.0.0.1), RFC 1918 addresses (e.g., 10.0.0.0/8 or 192.168.0.0/16), or any other destination occur from the point of view of the server, allowing requests that would otherwise be restricted by firewall rules or that would be impossible to perform externally. Consider the obvious consequences if a server\'s uninterruptible power supply offers a web service bound to 127.0.0.1:8080 without authentication and that accepts a GET request http://127.0.0.1:8080/ups/changePowerState?state=off-and what happens if this service is reachable via server-side request forgery. The Extensible Markup Language (XML) is complex and contains many optional features that are not suitable or even useful in the common case of a server accepting untrusted XML documents on an external interface. Some allow cross-site request forgery just by initializing an XML parser in its default configuration and passing an untrusted document. For example, XML External Entities allow a document to define custom entity values (analogous to < meaning |
Vulnerability | ★★★ | ||
| 2024-04-04 14:00:00 | Cutting avant, partie 4: Ivanti Connect Secure VPN Post-Exploitation Mouvement latéral Études de cas Cutting Edge, Part 4: Ivanti Connect Secure VPN Post-Exploitation Lateral Movement Case Studies (lien direct) |
Written by: Matt Lin, Austin Larsen, John Wolfram, Ashley Pearson, Josh Murchie, Lukasz Lamparski, Joseph Pisano, Ryan Hall, Ron Craft, Shawn Chew, Billy Wong, Tyler McLellan
Since the initial disclosure of CVE-2023-46805 and CVE-2024-21887 on Jan. 10, 2024, Mandiant has conducted multiple incident response engagements across a range of industry verticals and geographic regions. Mandiant\'s previous blog post, Cutting Edge, Part 3: Investigating Ivanti Connect Secure VPN Exploitation and Persistence Attempts, details zero-day exploitation of CVE-2024-21893 and CVE-2024-21887 by a suspected China-nexus espionage actor that Mandiant tracks as UNC5325. This blog post, as well as our previous reports detailing Ivanti exploitation, help to underscore the different types of activity that Mandiant has observed on vulnerable Ivanti Connect Secure appliances that were unpatched or did not have the appropriate mitigation applied. Mandiant has observed different types of post-exploitation activity across our incident response engagements, including lateral movement supported by the deployment of open-source tooling and custom malware families. In addition, we\'ve seen these suspected China-nexus actors evolve their understanding of Ivanti Connect Secure by abusing appliance-specific functionality to achieve their objectives. As of April 3, 2024, a patch is readily available for every supported version of Ivanti Connect Secure affected by the vulnerabilities. We recommend that customers follow Ivanti\'s latest patching guidance and instructions to prevent further exploitation activity. In addition, Ivanti released a new enhanced external integrity checker tool (ICT) to detect potential attempts of malware persistence across factory resets and system upgrades and other tactics, techniques, and procedures (TTPs) observed in the wild. We also released a remediation and hardening guide |
Malware Tool Vulnerability Threat Studies Mobile Cloud | Guam | ★★★ | |
| 2024-03-28 13:00:00 | Seseeyouexec: Windows Session Rijacking via CCMEXEC SeeSeeYouExec: Windows Session Hijacking via CcmExec (lien direct) |
Written by: Andrew Oliveau
Over the last several years, the security community has witnessed an uptick in System Center Configuration Manager (SCCM)-related attacks. From extracting network access account (NAA) credentials to deploying malicious applications to targeted devices, SCCM attacks have aided in accomplishing complex objectives and evading existing detections. Mandiant\'s Red Team has utilized SCCM technology to perform novel attacks against mature clients where conventional methodology was not possible. One such SCCM attack is introduced in this blog post. There was a time when red teamers with elevated privileges on a Windows system could effortlessly inject shellcode into an unsuspecting user\'s processes. This allowed red teamers to carry out post-exploitation activities within that new process, such as keylogging or accessing LDAP as the affected user. However, as endpoint detection and response (EDR) systems have improved, remote process injection has turned into a risky operation, pushing red teamers to seek alternative methods to hijack a user\'s session. Enter CcmExec, a service native to SCCM Windows clients that has an interesting design that is useful for red teamers. In this blog post, we delve into how the CcmExec service can be utilized for session hijacking and introduce CcmPwn, a tool designed to facilitate this technique. Finally, we will discuss detection strategies for security teams. AppDomainManager Injection Before diving into CcmExec, it is important to understand the intricacies of AppDomainManager injection, a loader hijacking technique used by attackers to execute arbitrary code within a .NET application. In essence, the .NET framework provides a way to manage application domains, which are isolated environments where .NET applications can run code. The AppDomainManager class is a key part of this infrastructure, responsible for creating and managing these application domains. However, if an attacker were to override the AppDomainManager class constructor, they could force the hosting application to run attacker-defined behavior when creating an application domain. The most common method to perform AppDomainManager injection is through a .config file. This approach involves modifying the application\'s configuration file to specify a custom dynamic-link library file (DLL) and AppDomainManager to be executed by the .NET application. Here\'s how it\'s done: Create a custom AppDomainManager: Develop a class that derives from AppDomainManager and includes malicious code. Compile this class into a DLL. Create a configuration file: Modify or create the application\'s |
Tool | ★★ | ||
| 2024-03-28 11:00:00 | La vie après la mort?Les campagnes de l'IO liées à un homme d'affaires russe notoire Prigozhin persiste après sa chute politique et sa mort Life After Death? IO Campaigns Linked to Notorious Russian Businessman Prigozhin Persist After His Political Downfall and Death (lien direct) |
Written by: Alden Wahlstrom, David Mainor, Daniel Kapellmann Zafra
In June 2023, Russian businessman Yevgeniy Prigozhin and his private military company (PMC) “Wagner” carried out an armed mutiny within Russia. The events triggered the meteoric political downfall of Prigozhin, raising questions about the future of his various enterprises that were only underscored when he died two months later under suspicious circumstances. Up to that point, Prigozhin and his enterprises worked to advance the Kremlin\'s interests as the manifestation of the thinnest veil of plausible deniability for state-guided actions on multiple continents. Such enterprises included the Wagner PMC; overt influence infrastructure, like his media company Patriot Group that housed his media companies, including the “RIA FAN” Federal News Agency; covert influence infrastructures; and an array of businesses aimed at generating personal wealth and the resourcing necessary to fund his various ventures. Mandiant has for years tracked and reported on covert information operations (IO) threat activity linked to Prigozhin. His involvement in IO was first widely established in the West as part of the public exposure of Russian-backed interference in the 2016 U.S. presidential election-this included activity conducted by Russia\'s Internet Research Agency (IRA), which the U.S. Government publicly named Prigozhin as its financier. Subsequently, Prigozhin was publicly connected to a web of IO activity targeting the U.S., EU, Ukraine, Russian domestic audiences, countries across Africa, and further afield. Such activity has worked not only to advance Russian interests on matters of strategic importance, but also has attempted to exploit existing divisions in societies targeting various subgroups across their population. Throughout 2023, Mandiant has observed shifts in the activity from multiple IO campaigns linked to Prigozhin, including continued indicators that components of these campaigns have remained viable since his death. This blog post examines a sample of Prigozhin-linked IO campaigns to better understand their outcomes thus far and provide an overview of what can be expected from these activity sets in the future. This is relevant not only because some of the infrastructure of these campaigns remains viable despite Prigozhin\'s undoing, but also because we advance into a year in which Ukraine continues to dominate Russia\'s strategic priorities and there are multiple global elections that Russia may seek to influence. Mandiant and Google\'s Threat Analysis Group (TAG) work together in support of our respective missions at Google. TAG has likewise been tracking coordinated influence operations linked to Prigozhin and the Internet Research Agency (IRA) for years; and in 2023, Google took over 400 enforcement actions to disrupt IO campaigns linked to the IRA, details of which are reported in the quarterly TAG Bulletin. TAG has not observed significant activity from the IRA or other Prigozhin-linked entities specifically on Google platforms since Prigozhin\'s death, |
Threat Studies Legislation Prediction | ★★★ | ||
| 2024-03-26 22:00:00 | Tendances les jours zéro exploités dans le monde en 2023 Trends on Zero-Days Exploited In-the-Wild in 2023 (lien direct) |
Written by: Maddie Stone, Jared Semrau, James Sadowski
Combined data from Google\'s Threat Analysis Group (TAG) and Mandiant shows 97 zero-day vulnerabilities were exploited in 2023; a big increase over the 62 zero-day vulnerabilities identified in 2022, but still less than 2021\'s peak of 106 zero-days. This finding comes from the first-ever joint zero-day report by TAG and Mandiant. The report highlights 2023 zero-day trends, with focus on two main categories of vulnerabilities. The first is end user platforms and products such as mobile devices, operating systems, browsers, and other applications. The second is enterprise-focused technologies such as security software and appliances. Key zero-day findings from the report include: Vendors\' security investments are working, making certain attacks harder. Attacks increasingly target third-party components, affecting multiple products. Enterprise targeting is rising, with more focus on security software and appliances. Commercial surveillance vendors lead browser and mobile device exploits. People\'s Republic of China (PRC) remains the top state-backed exploiter of zero-days. Financially-motivated attacks proportionally decreased. Threat actors are increasingly leveraging zero-days, often for the purposes of evasion and persistence, and we don\'t expect this activity to decrease anytime soon. Progress is being made on all fronts, but zero-day vulnerabilities remain a major threat. A Look Back - 2023 Zero-Day Activity at a Glance Barracuda ESG: CVE-2023-2868 Barracuda disclosed in May 2023 that a zero-day vulnerability (CVE-2023-2868) in their Email Security Gateway (ESG) had been actively exploited since as early as October 2022. Mandiant investigated and determined that UNC4841, a suspected Chinese cyber espionage actor, was conducting attacks across multiple regions and sectors as part of an espionage campaign in support of the PRC. Mandiant released a blog post with findings from the initial investigation, a follow-up post with more details as the investigation continued |
Vulnerability Threat Mobile Cloud Technical | ★★ | ||
| 2024-03-22 11:00:00 | APT29 utilise Wineloader pour cibler les partis politiques allemands APT29 Uses WINELOADER to Target German Political Parties (lien direct) |
Résumé exécutif fin février, l'APT29 a utilisé une nouvelle variante de porte dérobée suivie publiquement comme wineloader pour cibler les fêtes politiques allemandes avecun leurre sur le thème de la CDU. & nbsp; & nbsp; C'est la première fois que nous voyons ce cluster APT29 cible des partis politiques, indiquant une zone émergente émergenteFocus opérationnel au-delà du ciblage typique des missions diplomatiques. basée sur la responsabilité du SVR \\ de collecter l'intelligence politique et cette cluster APT29 \\ 'sModèles de ciblage historiques, nous jugeons cette activité pour présenter une large menace pour les partis politiques européens et autres occidentaux de tous les politiques
Executive SummaryIn late February, APT29 used a new backdoor variant publicly tracked as WINELOADER to target German political parties with a CDU-themed lure. This is the first time we have seen this APT29 cluster target political parties, indicating a possible area of emerging operational focus beyond the typical targeting of diplomatic missions.Based on the SVR\'s responsibility to collect political intelligence and this APT29 cluster\'s historical targeting patterns, we judge this activity to present a broad threat to European and other Western political parties from across the political |
Threat | APT 29 | ★★ | |
| 2024-03-22 00:00:00 | APT29 Uses WINELOADER to Target German Political Parties (lien direct) | Written by: Luke Jenkins, Dan Black
Executive Summary In late February, APT29 used a new backdoor variant publicly tracked as WINELOADER to target German political parties with a CDU-themed lure. This is the first time we have seen this APT29 cluster target political parties, indicating a possible area of emerging operational focus beyond the typical targeting of diplomatic missions. Based on the SVR\'s responsibility to collect political intelligence and this APT29 cluster\'s historical targeting patterns, we judge this activity to present a broad threat to European and other Western political parties from across the political spectrum. Please see the Technical Annex for technical details and MITRE ATT&CK techniques, (T1543.003, T1012, T1082, T1134, T1057, T1007, T1027, T1070.004, T1055.003 and T1083) Threat Detail In late February 2024, Mandiant identified APT29 - a Russian Federation backed threat group linked by multiple governments to Russia\'s Foreign Intelligence Service (SVR) - conducting a phishing campaign targeting German political parties. Consistent with APT29 operations extending back to 2021, this operation leveraged APT29\'s mainstay first-stage payload ROOTSAW (aka EnvyScout) to deliver a new backdoor variant publicly tracked as WINELOADER. Notably, this activity represents a departure from this APT29 initial access cluster\'s typical remit of targeting governments, foreign embassies, and other diplomatic missions, and is the first time Mandiant has seen an operational interest in political parties from this APT29 subcluster. Additionally, while APT29 has previously used lure documents bearing the logo of German government organizations, this is the first instance where we have seen the group use German-language lure content - a possible artifact of the targeting differences (i.e. domestic vs. foreign) between the two operations. Phishing emails were sent to victims purporting to be an invite to a dinner reception on 01 March bearing a logo from the Christian Democratic Union (CDU), a major political party in Germany (see Figure 1). The German-language lure document contains a phishing link directing victims to a malicious ZIP file containing a ROOTSAW dropper hosted on an actor-controlled compromised website “https://waterforvoiceless[.]org/invite.php”. ROOTSAW delivered a second-stage CDU-themed lure document and a next stage WINELOADER payload retrieved from “waterforvoiceless[.]org/util.php”. WINELOADER was first observed in operational use in late January 2024 in an operation targeting likely diplomatic entities in Czechia, Germany, India, Italy, Latvia, and Peru. The backdoor contains several features and functions that overlap with several known APT29 malware families including BURNTBATTER, MUSKYBEAT and BEATDROP, indicating they are likely created by a common developer (see Technical Annex for additional details). |
Malware Threat Cloud Technical | APT 29 | ★★★ | |
| 2024-03-21 09:00:00 | Rendre l'accès - Les courtiers d'accès initiaux exploitent F5 Big-IP (CVE-2023-46747) et ScreenConnect Bringing Access Back - Initial Access Brokers Exploit F5 BIG-IP (CVE-2023-46747) and ScreenConnect (lien direct) |
Au cours d'une enquête d'intrusion fin octobre 2023, Mandiant a observé une nouvelle exploitation n-day de & nbsp; CVE-2023-46747 Interface utilisateur de gestion du trafic Big-IP F5.De plus, en février 2024, nous avons observé l'exploitation de ConnectWise Screenconnect CVE-2024-1709 par le même acteur.Ce mélange d'outillage personnalisé et du cadre SuperShell exploité dans ces incidents est évalué avec une confiance modérée pour être unique pour une menace de la République de Chine (PRC), unc5174. Mandiant évalue UNC5174 (censé utiliser le personnage "Uteus") est un ancien membre de la Chine
During the course of an intrusion investigation in late October 2023, Mandiant observed novel N-day exploitation of CVE-2023-46747 affecting F5 BIG-IP Traffic Management User Interface. Additionally, in February 2024, we observed exploitation of Connectwise ScreenConnect CVE-2024-1709 by the same actor. This mix of custom tooling and the SUPERSHELL framework leveraged in these incidents is assessed with moderate confidence to be unique to a People\'s Republic of China (PRC) threat actor, UNC5174.Mandiant assesses UNC5174 (believed to use the persona "Uteus") is a former member of Chinese |
Threat | ★★ | ||
| 2024-03-21 00:00:00 | Bringing Access Back - Initial Access Brokers Exploit F5 BIG-IP (CVE-2023-46747) and ScreenConnect (lien direct) | Written by: Michael Raggi, Adam Aprahamian, Dan Kelly, Mathew Potaczek, Marcin Siedlarz, Austin Larsen
During the course of an intrusion investigation in late October 2023, Mandiant observed novel N-day exploitation of CVE-2023-46747 affecting F5 BIG-IP Traffic Management User Interface. Additionally, in February 2024, we observed exploitation of Connectwise ScreenConnect CVE-2024-1709 by the same actor. This mix of custom tooling and the SUPERSHELL framework leveraged in these incidents is assessed with moderate confidence to be unique to a People\'s Republic of China (PRC) threat actor, UNC5174. Mandiant assesses UNC5174 (believed to use the persona "Uteus") is a former member of Chinese hacktivist collectives that has since shown indications of acting as a contractor for China\'s Ministry of State Security (MSS) focused on executing access operations. UNC5174 has been observed attempting to sell access to U.S. defense contractor appliances, UK government entities, and institutions in Asia in late 2023 following CVE-2023-46747 exploitation. In February 2024, UNC5174 was observed exploiting ConnectWise ScreenConnect vulnerability (CVE-2024-1709) to compromise hundreds of institutions primarily in the U.S. and Canada. Targeting and Timeline UNC5174 has been linked to widespread aggressive targeting and intrusions of Southeast Asian and U.S. research and education institutions, Hong Kong businesses, charities and non-governmental organizations (NGOs), and U.S. and UK government organizations during October and November 2023, as well as in February 2024. The actor appears primarily focused on executing access operations. Mandiant observed UNC5174 exploiting various vulnerabilities during this time. ConnectWise ScreenConnect Vulnerability CVE-2024-1709 F5 BIG-IP Configuration Utility Authentication Bypass Vulnerability CVE-2023-46747 Atlassian Confluence CVE-2023-22518 Linux Kernel Exploit CVE-2022-0185 Zyxel Firewall OS Command Injection Vulnerability CVE-2022-30525 Investigations revealed several instances of UNC5174 infrastructure, exposing the attackers\' bash command history. This history detailed artifacts of extensive reconnaissance, web application fuzzing, and aggressive scanning for vulnerabilities on internet-facing systems belonging to prominent universities in the U.S., Oceania, and Hong Kong regions. Additionally, key strategic targets like think tanks in the U.S. and Taiwan were identified; however, Mandiant does not have significant evidence to determine successful exploitation of these targets.  Figure 1: UNC5174 global targeting map
Initial Disclosure of CVE-2023-46747
On Oct. 25, 2023, Praetorian published an advisory and proof-of-concept (PoC) for a zero-day (0-day) vulnerabil
Figure 1: UNC5174 global targeting map
Initial Disclosure of CVE-2023-46747
On Oct. 25, 2023, Praetorian published an advisory and proof-of-concept (PoC) for a zero-day (0-day) vulnerabil |
Malware Tool Vulnerability Threat Cloud | ★★★ | ||
| 2024-03-06 17:30:00 | Placer dans Dalvik: un aperçu des fichiers dex Delving into Dalvik: A Look Into DEX Files (lien direct) |
Lors de l'analyse d'un échantillon de Troie bancaire ciblant les smartphones Android, Mandiant a identifié l'utilisation répétée d'un mécanisme d'obscurcation de chaîne tout au long du code d'application.Pour analyser et comprendre pleinement la fonctionnalité de l'application \\, une possibilité est de décoder manuellement les chaînes dans chaque méthode obscurcie rencontrée, qui peut être un processus long et répétitif. & Nbsp; Une autre possibilité consiste à utiliser des outils payants tels que & nbsp; jeb décompulier qui permettent une identification et un correctif rapides du code dans les applications Android, mais nous avons constaté que la possibilité de faire de même avec la statique gratuite
During the analysis of a banking trojan sample targeting Android smartphones, Mandiant identified the repeated use of a string obfuscation mechanism throughout the application code. To fully analyze and understand the application\'s functionality, one possibility is to manually decode the strings in each obfuscated method encountered, which can be a time-consuming and repetitive process. Another possibility is to use paid tools such as JEB decompiler that allow quick identification and patching of code in Android applications, but we found that the ability to do the same with free static |
Tool Patching Mobile | ★★ | ||
| 2024-02-28 00:00:00 | Quand les chats volent: l'acteur de menace iranienne présumée UNC1549 cible les secteurs de l'aérospatiale et de la défense israéliens et du Moyen-Orient When Cats Fly: Suspected Iranian Threat Actor UNC1549 Targets Israeli and Middle East Aerospace and Defense Sectors (lien direct) |
Aujourd'hui, Mandiant publie un article de blog sur & nbsp; Activité d'espionnage Iran-Nexus présumée ciblant les industries aérospatiales, de l'aviation et de la défense au Moyen-Orient Des pays, dont Israël et les Émirats arabes unis (EAU) et potentiellement la Turquie, l'Inde et l'Albanie. & nbsp; mandiant attribue cette activité avec une confiance modéréeà l'acteur iranien UNC1549 , qui chevauche & nbsp; tortue -Un acteur de menace qui a été publiquement & nbsp; lié à & nbsp; Le Corps de la Garde révolutionnaire islamique de l'Iran \\ (IRGC) .Tortoirhesell a déjà tenté de compromettre les chaînes d'approvisionnement en ciblant les entrepreneurs de défense et il
Today Mandiant is releasing a blog post about suspected Iran-nexus espionage activity targeting the aerospace, aviation and defense industries in Middle East countries, including Israel and the United Arab Emirates (UAE) and potentially Turkey, India, and Albania. Mandiant attributes this activity with moderate confidence to the Iranian actor UNC1549, which overlaps with Tortoiseshell-a threat actor that has been publicly linked to Iran\'s Islamic Revolutionary Guard Corps (IRGC). Tortoiseshell has previously attempted to compromise supply chains by targeting defense contractors and IT |
Threat | ★★★ | ||
| 2024-02-27 21:30:00 | Cutting avant, partie 3: Enquête sur Ivanti Connect Secure Secure VPN Exploitation et Tentatives de persistance Cutting Edge, Part 3: Investigating Ivanti Connect Secure VPN Exploitation and Persistence Attempts (lien direct) |
Les enquêtes de mandiant et ivanti \\ sur les larges et nbsp; Ivanti Exploitation zéro-jour se sont poursuivis à travers une variété de verticales de l'industrie, y compris le secteur de la base industrielle de la défense américaine.Après la publication initiale du 10 janvier 2024, Mandiant a observé des tentatives de masse pour exploiter ces vulnérabilités par un petit nombre d'acteurs de la menace de Chine-Nexus, et le développement d'un byligation d'exploitation de ciblage & nbsp; CVE-2024-21893 utilisé par & nbsp; unc5325 , que nous avons introduit dans notre & nbsp; " Cutting Edge, partie 2 "Blog Article . & nbsp; notamment, Mandiant a identifié unc5325 en utilisant une combinaison de vie-the-land (LOTL)
Mandiant and Ivanti\'s investigations into widespread Ivanti zero-day exploitation have continued across a variety of industry verticals, including the U.S. defense industrial base sector. Following the initial publication on Jan. 10, 2024, Mandiant observed mass attempts to exploit these vulnerabilities by a small number of China-nexus threat actors, and development of a mitigation bypass exploit targeting CVE-2024-21893 used by UNC5325, which we introduced in our "Cutting Edge, Part 2" blog post. Notably, Mandiant has identified UNC5325 using a combination of living-off-the-land (LotL) |
Vulnerability Threat Industrial | ★★ | ||
| 2024-02-24 00:30:00 | Guide de correction et de durcissement pour ConnectWise Screenconnect Vulnérabilités (CVE-2024-1708 et CVE-2024-1709) Remediation and Hardening Guide for ConnectWise ScreenConnect Vulnerabilities (CVE-2024-1708 and CVE-2024-1709) (lien direct) |
Le 19 février 2024, ConnectWise a annoncé deux vulnérabilités pour leur produit ScreenConnect affectant (sur site) 23.9.7 et plus tôt: CVE-2024-1708 & # 8211;Vulnérabilité de contournement de l'authentification (10.0) CVE-2024-1709 & # 8211;Vulnérabilité de traversée de chemin (8.4) Ces vulnérabilités permettent à un acteur non authentifié de contourner l'authentification et d'accès à des environnements screenconnets qui peuvent êtreDerrière un pare-feu d'entreprise. & nbsp; connectWise a publié un & nbsp; version usée du produit Screenconnect (23.9.8+) qui atténue les vulnérabilités.ConnectWise a supprimé les restrictions de licence, donc Screenconnect aux consommateurs qui
On Feb. 19, 2024, ConnectWise announced two vulnerabilities for their ScreenConnect product affecting (on-premises) versions 23.9.7 and earlier:CVE-2024-1708 – Authentication Bypass Vulnerability (10.0)CVE-2024-1709 – Path Traversal Vulnerability (8.4)These vulnerabilities allow an unauthenticated actor to bypass authentication, and access ScreenConnect environments that may be behind a corporate firewall. ConnectWise released an updated version of the ScreenConnect product (23.9.8+) that mitigates the vulnerabilities. ConnectWise has removed license restrictions so ScreenConnect consumers who |
Vulnerability | ★★★ | ||
| 2024-02-21 00:00:00 | Dévoiler l'évaluation de l'échéance du programme d'intelligence de cyber-menace de Maniant Unveiling Mandiant\\'s Cyber Threat Intelligence Program Maturity Assessment (lien direct) |
Dans le cadre de l'engagement continu de Google Cloud \\ à améliorer l'état global de cybersécurité pour la société, Mandiant publie aujourd'hui publiquement un Discovery des capacités d'intelligence basées sur les web (ICD) pour aider les organisations commerciales et gouvernementales à évaluerLa maturité de leur programme d'intelligence cyber-menace (CTI).La CIM est conçue pour fournir aux praticiens de la cybersécurité et aux dirigeants du renseignement des menaces une estimation de la façon dont le programme CTI \\ de l'organisation crée un impact organisationnel positif et réduit le risque pour l'entreprise.La CIM joue un critique
As part of Google Cloud\'s continuing commitment to improving the overall state of cybersecurity for society, today Mandiant is publicly releasing a web-based Intelligence Capability Discovery (ICD) to help commercial and governmental organizations evaluate the maturity of their cyber threat intelligence (CTI) program. The ICD is designed to provide cyber security practitioners and threat intelligence leaders with an estimate of how effectively and efficiently the organization\'s CTI program is creating a positive organizational impact and reducing risk for the business. The ICD plays a critical |
Threat Cloud Commercial | ★★★ | ||
| 2024-02-14 18:15:00 | Riding Dragons: Capa harcèles Ghidra Riding Dragons: capa Harnesses Ghidra (lien direct) |
capa est l'équipe Flare \\ 's ouverteoutil source qui détecte les capacités dans les fichiers exécutables. ghidra est un cadre d'ingénierie de logiciel open source créé et entretenu par leDirection de la recherche de l'Agence de sécurité nationale.Avec le version de capa v7 , nous avons intégré CAPAavec Ghidra, apportant directement les capacités de détection de Capa \\ à l'interface utilisateur de Ghidra \\.Avec cette intégration, nous espérons avoir un impact positif sur les workflows de la grande base d'utilisateurs de Ghidra \\ en aidant les utilisateurs de Ghidra à identifier rapidement le code qui suggère un comportement intéressant.Nous sommes ravis de partager ce travail avec le
capa is the FLARE team\'s open source tool that detects capabilities in executable files. Ghidra is an open source software reverse engineering framework created and maintained by the National Security Agency Research Directorate. With the release of capa v7, we have integrated capa with Ghidra, bringing capa\'s detection capabilities directly to Ghidra\'s user interface. With this integration, we hope to positively impact the workflows of Ghidra\'s large user base by helping Ghidra users quickly identify code that suggests an interesting behavior. We are excited to share this work with the |
Tool | ★★ | ||
| 2024-02-13 20:15:00 | Les informations d'identification volées vous font vous demander qui a vraiment accès Stolen Credentials Make You Question Who Really Has Access (lien direct) |
Vos mots de passe flottent-ils sur le Web sombre?Comment sauriez-vous s'ils l'étaient?Il est plus important que jamais d'être proactif pour protéger les données de votre organisation.L'une des meilleures façons d'y parvenir est de surveiller les fuites d'identification. Une fuite d'identification se produit lorsque des informations sensibles, telles que les noms d'utilisateur, les mots de passe et l'APIKeys, est exposé au public.Cela peut se produire de plusieurs manières, y compris les violations de données, les attaques de phishing, les voleurs d'identification et l'ingénierie sociale.Une fois les informations d'identification divulguées, ils peuvent être utilisés par les attaquants pour obtenir un accès non autorisé à votre organisation \'s
Are your passwords floating around on the dark web? How would you know if they were? It\'s more important than ever to be proactive in protecting your organization\'s data. One of the best ways to do this is to monitor for credential leaks.A credential leak occurs when sensitive information, such as usernames, passwords, and API keys, is exposed to the public. This can happen in any number of ways, including data breaches, phishing attacks, credential stealers, and social engineering. Once credentials are leaked, they can be used by attackers to gain unauthorized access to your organization\'s |
★★★ | |||
| 2024-02-01 16:45:00 | CAPA dynamique: exploration du comportement d'exécution exécutable avec le sandbox Cape Dynamic capa: Exploring Executable Run-Time Behavior with the CAPE Sandbox (lien direct) |
Nous sommes ravis d'annoncer que CAPA V7.0 identifie désormais les capacités du programme à partir de rapports d'analyse dynamique générés via le cape sandbox .Cette expansion de CAPA \'s Approche d'analyse statique originale permet aux analystes de mieux les échantillons emballés et obscurcis et résument les capacités (malware) dans les traces d'API de bac à sable.Le plus récent binaires de libération de capa et code source sont disponibles dans notre githubPage. Cette fonction a été implémentée par Yacine Elhamer ( @yelhamer ) dans le cadre d'un Projet Google Summer of Code (GSOC) que l'équipe Mandiant Flare a encadré en 2023. Pour en savoir plus sur le programme et
We are excited to announce that capa v7.0 now identifies program capabilities from dynamic analysis reports generated via the CAPE sandbox. This expansion of capa\'s original static analysis approach allows analysts to better triage packed and obfuscated samples, and summarizes (malware) capabilities in sandbox API traces. The newest capa release binaries and source code are available at our GitHub page.This feature was implemented by Yacine Elhamer (@yelhamer) as part of a Google Summer of Code (GSoC) project that the Mandiant FLARE team mentored in 2023. To learn more about the program and |
★★ | |||
| 2024-01-31 16:30:00 | Cutting Edge, partie 2: Enquêter Ivanti Connect Secure VPN Exploitation Zero-Day Cutting Edge, Part 2: Investigating Ivanti Connect Secure VPN Zero-Day Exploitation (lien direct) |
Le 12 janvier 2024, Mandiant a publié un Article de blog Détaillant deux vulnérabilités à haut impact, CVE-2023-46805 et CVE-2024-21887 , affectant Ivanti Connect Secure VPN (CS, anciennement Secure Secure) et Ivanti Secure (Ps) Appareils.Le 31 janvier 2024, Ivanti divulgué Deux vulnérabilités supplémentaires ayant un impact sur les dispositifs CS et PS, CVE-2024-21888 et CVE-2024-21893. Les vulnérabilités permettent à un acteur de menace non authentifié d'exécuter des commandes arbitraires sur l'appareil avec des privilèges élevés.Comme indiqué précédemment, Mandiant a identifié l'exploitation zéro jour de ces vulnérabilités
On Jan. 12, 2024, Mandiant published a blog post detailing two high-impact zero-day vulnerabilities, CVE-2023-46805 and CVE-2024-21887, affecting Ivanti Connect Secure VPN (CS, formerly Pulse Secure) and Ivanti Policy Secure (PS) appliances. On Jan. 31, 2024, Ivanti disclosed two additional vulnerabilities impacting CS and PS devices, CVE-2024-21888 and CVE-2024-21893.The vulnerabilities allow for an unauthenticated threat actor to execute arbitrary commands on the appliance with elevated privileges. As previously reported, Mandiant has identified zero-day exploitation of these vulnerabilities |
Vulnerability Threat | ★★ | ||
| 2024-01-30 20:30:00 | Évolution de UNC4990: Découvrir les profondeurs cachées de USB MALWARE \\ Evolution of UNC4990: Uncovering USB Malware\\'s Hidden Depths (lien direct) |
Défense gérée mandiante Suivi unc4990 , un acteur qui utilise fortement les périphériques USB pour l'infection initiale.UNC4990 cible principalement les utilisateurs basés en Italie et est probablement motivé par un gain financier.Nos recherches montrent que cette campagne est en cours depuis au moins 2020. malgré son apparition sur la tactique séculaire de l'armement USBDrives, UNC4990 continue d'évoluer leurs outils, tactiques et procédures (TTPS).L'acteur est passé de l'utilisation de fichiers texte codés apparemment bénins à l'hébergement de charges utiles sur des sites Web populaires tels que Ars Technica, Github, Gitlab et Vimeo. Les services légitimes abusés par
Mandiant Managed Defense has been tracking UNC4990, an actor who heavily uses USB devices for initial infection. UNC4990 primarily targets users based in Italy and is likely motivated by financial gain. Our research shows this campaign has been ongoing since at least 2020.Despite relying on the age-old tactic of weaponizing USB drives, UNC4990 continues to evolve their tools, tactics and procedures (TTPs). The actor has moved from using seemingly benign encoded text files to hosting payloads on popular websites such as Ars Technica, GitHub, GitLab, and Vimeo.The legitimate services abused by |
Malware Tool Cloud | ★★★★ | ||
| 2024-01-19 17:30:00 | Le groupe d'espionnage chinois UNC3886 a trouvé l'exploitation du CVE-2023-34048 depuis la fin 2021 Chinese Espionage Group UNC3886 Found Exploiting CVE-2023-34048 Since Late 2021 (lien direct) |
Bien que signalé et corrigé publiquement en octobre 2023, la sécurité des produits Mandiant et VMware a trouvé unc3886 , un groupe d'espionnage China-Nexus très avancé, a exploité CVE-2023-34048 jusqu'à la fin 2021. Ces résultats proviennent de la recherche continue de Maniant \\ de Les nouveaux chemins d'attaque utilisés par unc3886 , qui se concentre historiquement sur les technologies qui ne sont pas en mesure de les déployer par EDR.UNC3886 a une expérience en utilisant des vulnérabilités zéro-jours pour terminer leur mission sans être détectée, et ce dernier exemple démontre en outre leurs capacités. Lorsque vous couvrez
While publicly reported and patched in October 2023, Mandiant and VMware Product Security have found UNC3886, a highly advanced China-nexus espionage group, has been exploiting CVE-2023-34048 as far back as late 2021.These findings stem from Mandiant\'s continued research of the novel attack paths used by UNC3886, which historically focuses on technologies that are unable to have EDR deployed to them. UNC3886 has a track record of utilizing zero-day vulnerabilities to complete their mission without being detected, and this latest example further demonstrates their capabilities. When covering |
Vulnerability Threat | ★★★★ | ||
| 2024-01-11 02:00:00 | Cutting avant: cibles présumées APT Ivanti Connect Secure VPN dans une nouvelle exploitation zéro-jour Cutting Edge: Suspected APT Targets Ivanti Connect Secure VPN in New Zero-Day Exploitation (lien direct) |
Remarque: Il s'agit d'une campagne de développement sous analyse active de Mandiant et Ivanti.Nous continuerons à ajouter plus d'indicateurs, de détections et d'informations à ce billet de blog au besoin. le 10 janvier 2024, ivanti divulgué Deux vulnérabilités, CVE-2023-46805 et CVE-2024-21887 , impactant Ivanti Connect Secure VPN (" CS ", anciennement Secure Secure) et Ivanti Secure (" PS") appareils électroménagers.Une exploitation réussie pourrait entraîner un contournement d'authentification et une injection de commandement, entraînant un autre compromis en aval d'un réseau de victimes.Mandiant a identifié l'exploitation zéro-jour de ces vulnérabilités
Note: This is a developing campaign under active analysis by Mandiant and Ivanti. We will continue to add more indicators, detections, and information to this blog post as needed.On January 10, 2024, Ivanti disclosed two vulnerabilities, CVE-2023-46805 and CVE-2024-21887, impacting Ivanti Connect Secure VPN (“CS”, formerly Pulse Secure) and Ivanti Policy Secure (“PS”) appliances. Successful exploitation could result in authentication bypass and command injection, leading to further downstream compromise of a victim network. Mandiant has identified zero-day exploitation of these vulnerabilities |
Vulnerability Threat | ★★★ | ||
| 2024-01-10 22:00:00 | Des centaines de milliers de dollars d'actifs de crypto-monnaie Solana volés lors de récentes campagnes de draineur Clinksink Hundreds of Thousands of Dollars Worth of Solana Cryptocurrency Assets Stolen in Recent CLINKSINK Drainer Campaigns (lien direct) |
Le 3 janvier 2024, le compte de médias sociaux de Mandiant \\ a été repris et utilisé par la suite pour distribuer des liens vers une page de phishing de drainage de crypto-monnaie.En travaillant avec X, nous avons pu reprendre le contrôle du compte et, sur la base de notre enquête sur les jours suivants, nous n'avons trouvé aucune preuve d'activité malveillante ou de compromis de, tous les systèmes de cloud mandiant ou Google qui ont conduit au compromis de cettecompte.Le billet de blog suivant fournit un aperçu supplémentaire de Draineur Levé dans cette campagne, que nous avons surnommé Clinksink. De nombreux acteurs ont mené des campagnes depuis
On January 3, 2024, Mandiant\'s X social media account was taken over and subsequently used to distribute links to a cryptocurrency drainer phishing page. Working with X, we were able to regain control of the account and, based on our investigation over the following days, we found no evidence of malicious activity on, or compromise of, any Mandiant or Google Cloud systems that led to the compromise of this account. The following blog post provides additional insight into the drainer leveraged in this campaign, which we have dubbed CLINKSINK.Numerous actors have conducted campaigns since |
Cloud | ★★★ | ||
| 2023-12-14 21:00:00 | Le cyber-instantané du défenseur du défenseur, le numéro 5 - Insiders, applications et risque atténuant The Defender\\'s Advantage Cyber Snapshot, Issue 5 - Insiders, Applications, and Mitigating Risk (lien direct) |
Le rapport de cyber-instantan avant le défenseur \\ fournit un aperçu des sujets de cyber-défense d'une importance croissante en fonction des observations de première ligne mandiantes et des expériences du monde réel. La cinquième édition couvre un large éventail de sujets, y compris l'idéologie et le paysage des menaces d'initiés, des étapes critiques pour aider à atténuer votre cyber-risque, la croissance de la croissance deCiblage de l'industrie maritime, sécurisation de la cyber-défenses de votre application, et l'importance de la chasse aux menaces dirigée par le renseignement. Téléchargez l'avantage complet du Defender \\ du défenseur complet, le numéro 5 du rapport Pour en savoir plusÀ propos de ces cinq sujets chauds: compresseur
The Defender\'s Advantage Cyber Snapshot report provides insights into cyber defense topics of growing importance based on Mandiant frontline observations and real-world experiences. The fifth edition covers a wide range of topics, including the ideology and landscape of insider threats, critical steps to help mitigate your cyber risk, the growth of maritime industry targeting, securing your application\'s cyber defenses, and the importance of intelligence-led threat hunting.Download the full Defender\'s Advantage Cyber Snapshot, Issue 5 report to learn more about these five hot topics: Understan |
Threat | ★★ | ||
| 2023-12-14 17:00:00 | Ouvrir une boîte de publicités Whoop: détecter et perturber une campagne de malvertisation distribuant des déambulations Opening a Can of Whoop Ads: Detecting and Disrupting a Malvertising Campaign Distributing Backdoors (lien direct) |
Plus tôt cette année, l'équipe de chasse des menaces de défense gérée de Mandiant \\ a identifié une campagne de publicité malveillante («malvertisante») UNC2975 faisant la promotion de sites Web malveillants sur le thème des fonds non réclamés.Cette campagne remonte au moins le 19 juin 2023, et a abusé du trafic de moteurs de recherche et des publicités malveillantes à effet de levier pour affecter plusieurs organisations, ce qui a entraîné la livraison des délais de Danabot et Darkgate. La défense gérée a travaillé avec des pratiques avancées et avec l'équipe anti-Malvertising Google pour supprimer les publicités malveillantes de l'écosystème d'annonces, puis
Earlier this year, Mandiant\'s Managed Defense threat hunting team identified an UNC2975 malicious advertising (“malvertising”) campaign promoting malicious websites themed around unclaimed funds. This campaign dates back to at least June 19, 2023, and has abused search engine traffic and leveraged malicious advertisements to affect multiple organizations, which resulted in the delivery of the DANABOT and DARKGATE backdoors.Managed Defense worked with Advanced Practices and with the Google Anti-Malvertising team to remove the malicious advertisements from the ads ecosystem, and subsequently |
Threat | ★★ | ||
| 2023-12-13 17:00:00 | Floss pour gophers et crabes: extraire les chaînes de go et les exécutables de rouille FLOSS for Gophers and Crabs: Extracting Strings from Go and Rust Executables (lien direct) |
|
Tool Technical | ★★★★ | ||
| 2023-11-30 17:00:00 | Amélioration des outils d'analyse des logiciels malveillants de Flare \\ à Google Summer of Code 2023 Improving FLARE\\'s Malware Analysis Tools at Google Summer of Code 2023 (lien direct) |
Cet été a marqué la première année de la première année de l'équipe Flare \\ à googleÉté du code (GSOC) .GSOC est un programme mondial de mentorat en ligne axé sur l'introduction de nouveaux contributeurs au développement de logiciels open source.Les contributeurs du GSOC travaillent avec des mentors pour réaliser des projets de plus de 12 semaines qui soutiennent les organisations open source.En 2023, Flare a été acceptée en GSOC et a eu le privilège de travailler avec quatre contributeurs. Flare est une équipe d'ingénieurs et de chercheurs insensés qui se spécialisent dans l'analyse des logiciels malveillants, Exploiter Analyse et formation de logiciels malveillants.Flare développe, maintient et publie divers ouverts
This summer marked the FLARE team\'s first year participating in Google Summer of Code (GSoC). GSoC is a global online mentoring program focused on introducing new contributors to open source software development. GSoC contributors work with mentors to complete 12+ week projects that support open source organizations. During 2023 FLARE was accepted into GSoC and had the privilege of working with four contributors.FLARE is a team of reverse engineers and researchers who specialize in malware analysis, exploit analysis, and malware training. FLARE develops, maintains, and publishes various open |
Malware Tool Threat | ★★★ | ||
| 2023-11-16 18:00:00 | Menace d'initié: chasse et détection Insider Threat: Hunting and Detecting (lien direct) |
La menace d'initié est un défi à multiples facettes qui représente aujourd'hui un risque de cybersécurité significatif pour les organisations.Certains sont des initiés malveillants tels que les employés qui cherchent à voler des données ou à saboter l'organisation.Certains sont des initiés involontaires tels que des employés qui commettent des erreurs imprudents ou sont victimes de phisses. Si vous avez besoin d'un rafraîchissement sur les menaces d'initiés ou leur impact, veuillez vous référer à nos articles de blog précédents: menace d'initié: les dangers à l'intérieur menace d'initié: Études d'impact L'identification des menaces d'initié devient de plus en plus importante.Les initiés malveillants transportent souvent
The insider threat is a multifaceted challenge that represents a significant cybersecurity risk to organizations today. Some are malicious insiders such as employees looking to steal data or sabotage the organization. Some are unintentional insiders such as employees who make careless mistakes or fall victim to phishing attacks. If you need a refresher on what insider threats are or their impact, please refer to our previous blog posts:Insider Threat: The Dangers WithinInsider Threat: Impact StudiesIdentifying insider threats is becoming increasingly important. Malicious insiders often carry |
Threat | ★★★★ | ||
| 2023-11-14 17:00:00 | Le processus CTI Hyperloop: une mise en œuvre pratique du cycle de vie du processus CTI The CTI Process Hyperloop: A Practical Implementation of the CTI Process Lifecycle (lien direct) |
Implémentation du cycle de vie du processus CTI en tant que Hyperloop Le cycle Hyperloop de renseignement est un modèle de mise en œuvre du cyber-menace Intelligence (CTI).Le cycle de vie est un processus bien établi décrivant la façon dont les produits d'intelligence sont motivés par la planification et la direction initialement, suivis des phases de collecte, de traitement, d'analyse, de production et de diffusion.La nature cyclique décrit comment les produits diffusés éclairent ensuite une nouvelle étape de planification et de direction d'un nouveau cycle. | Threat | ★★★★ | ||
| 2023-11-11 03:00:00 | Flare-on 10 Challenge Solutions (lien direct) |  Notre objectif cette année était de relever le défi le plus difficile de l'évolution que nous ayons jamais produit pour célébrer une décennie complète de concours.Au moment de la rédaction de cet article, 219 finisseurs évolués sur 4 767 utilisateurs enregistrés, ce qui en fait le taux de finition le plus bas que nous ayons jamais eu.Vraiment, seule l'élite de l'élite peut prétendre être un finisseur Flare-on 10.Ces quelques chanceux recevront ce fanion (conception et non finale). Nous tenons à remercier les auteurs de défi individuellement pour leurs grands puzzles et solutions. x -Nick Harbor (@nickharbour) itsonfire - Raymond Leong mypassion -Moritz Raabe (@m_r Notre objectif cette année était de relever le défi le plus difficile de l'évolution que nous ayons jamais produit pour célébrer une décennie complète de concours.Au moment de la rédaction de cet article, 219 finisseurs évolués sur 4 767 utilisateurs enregistrés, ce qui en fait le taux de finition le plus bas que nous ayons jamais eu.Vraiment, seule l'élite de l'élite peut prétendre être un finisseur Flare-on 10.Ces quelques chanceux recevront ce fanion (conception et non finale). Nous tenons à remercier les auteurs de défi individuellement pour leurs grands puzzles et solutions. x -Nick Harbor (@nickharbour) itsonfire - Raymond Leong mypassion -Moritz Raabe (@m_r
 Our goal this year was to make the most difficult Flare-On challenge we\'ve ever produced to celebrate a full decade of contests. At the time of this writing, there were 219 Flare-On finishers out of 4,767 registered users, which makes it the lowest finishing rate we\'ve ever had. Truly, only the elite of the elite can claim to be a Flare-On 10 finisher. These lucky few will receive this pennant (design not final).We would like to thank the challenge authors individually for their great puzzles and solutions.X - Nick Harbour (@nickharbour)ItsOnFire - Raymond LeongMypassion - Moritz Raabe (@m_r Our goal this year was to make the most difficult Flare-On challenge we\'ve ever produced to celebrate a full decade of contests. At the time of this writing, there were 219 Flare-On finishers out of 4,767 registered users, which makes it the lowest finishing rate we\'ve ever had. Truly, only the elite of the elite can claim to be a Flare-On 10 finisher. These lucky few will receive this pennant (design not final).We would like to thank the challenge authors individually for their great puzzles and solutions.X - Nick Harbour (@nickharbour)ItsOnFire - Raymond LeongMypassion - Moritz Raabe (@m_r |
★★★ | |||
| 2023-11-09 15:00:00 | Le ver de sable perturbe le pouvoir en Ukraine en utilisant une nouvelle attaque contre la technologie opérationnelle Sandworm Disrupts Power in Ukraine Using a Novel Attack Against Operational Technology (lien direct) |
fin 2022, Mandiant a répondu à un incident de cyber-physique perturbateur dans lequel l'acteur de menace lié à la Russie a ciblé une organisation d'infrastructure critique ukrainienne.Cet incident était une cyberattaque multi-événements qui a exploité une nouvelle technique pour avoir un impact sur les systèmes de contrôle industriel (CI) / technologie opérationnelle (OT).L'acteur a d'abord utilisé le niveau OT vivant des techniques terrestres (LOTL) pour déclencher probablement les disjoncteurs de sous-station de la victime, provoquant une panne de courant imprévue qui coïncidait avec les frappes de missiles de masse sur les infrastructures critiques à travers l'Ukraine.Sandworm plus tard
In late 2022, Mandiant responded to a disruptive cyber physical incident in which the Russia-linked threat actor Sandworm targeted a Ukrainian critical infrastructure organization. This incident was a multi-event cyber attack that leveraged a novel technique for impacting industrial control systems (ICS) / operational technology (OT). The actor first used OT-level living off the land (LotL) techniques to likely trip the victim\'s substation circuit breakers, causing an unplanned power outage that coincided with mass missile strikes on critical infrastructure across Ukraine. Sandworm later |
Threat Industrial | APT 28 | ★★ | |
| 2023-10-31 14:00:00 | Enquête sur le détournement de session via Citrix Netcaler ADC et la vulnérabilité de la passerelle (CVE-2023-4966) Investigation of Session Hijacking via Citrix NetScaler ADC and Gateway Vulnerability (CVE-2023-4966) (lien direct) |
Remarque: Il s'agit d'une campagne en développement sous analyse active.Nous continuerons d'ajouter plus d'indicateurs, de conseils de chasse et d'informations à cet article de blog au besoin.
Le 10 octobre 2023, Citrix a publié un bulletin de sécurité pour un divulgation d'informations sensibles (CVE-2023-4966) Impactant NetScaler ADC et NetScaler Gateway Appliances .
mandiant a identifié l'exploitation zéro-jour de cette vulnérabilité dans la nature commençant fin août 2023 égalementcomme exploitation des jours après la publication de Citrix \\.Mandiant étudie plusieurs instances d'exploitation réussie de CVE-2023
Note: This is a developing campaign under active analysis. We will continue to add more indicators, hunting tips, and information to this blog post as needed. On Oct. 10, 2023, Citrix released a security bulletin for a sensitive information disclosure vulnerability (CVE-2023-4966) impacting NetScaler ADC and NetScaler Gateway appliances. Mandiant has identified zero-day exploitation of this vulnerability in the wild beginning in late August 2023 as well as n-day exploitation after Citrix\'s publication. Mandiant is investigating multiple instances of successful exploitation of CVE-2023 |
Vulnerability | ★★★ | ||
| 2023-10-17 17:30:00 | Correction des régimes pour Citrix NetScaler ADC et Vulnérabilité Gateway (CVE-2023-4966) Remediations for Citrix NetScaler ADC and Gateway Vulnerability (CVE-2023-4966) (lien direct) |
Le 10 octobre 2023, Citrix a publié un | Vulnerability | ★★ | ||
| 2023-10-13 11:15:00 | Mises à jour des produits de renseignement Mandiant Threat pour octobre 2023 Mandiant Threat Intelligence Product Updates for October 2023 (lien direct) |
mandiantIntelligence de menace a ajouté un certain nombre de fonctionnalités et capacités nouvelles et mises à jour, qui sont désormais disponibles dans l'aperçu public ou la disponibilité générale.Ces nouvelles capacités vous aident à gagner du temps et à mieux comprendre les menaces vous ciblant.
Aperçu public
Surveillance des informations d'identification compromises: Surveillez vos informations d'identification compromises qui peuvent avoir fui sur la toile profonde et sombre.Les capacités de surveillance des informations d'identification compromises dans Surveillance des menaces numériques peut vous alerter automatiquement si des comptes liés à votre organisation - les deux employés interneset les clients - ont
Mandiant Threat Intelligence has added a number of new and updated features and capabilities, which are now available in public preview or general availability. These new capabilities help you save time and gain more insight into the threats targeting you. Public Preview Compromised credentials monitoring: Monitor your compromised credentials that may have leaked on the deep and dark web. The compromised credentials monitoring capabilities in Digital Threat Monitoring can automatically alert you if any accounts linked to your organization - both internal employees and customers - have |
Threat | ★★★ | ||
| 2023-10-10 07:00:00 | Évalué la cyber-structure et les alignements de la Corée du Nord en 2023 Assessed Cyber Structure and Alignments of North Korea in 2023 (lien direct) |
résumé exécutif
Le programme offensif de DPRK \\ continue d'évoluer, montrant que le régime est déterminé à continuer à utiliser des cyber-intrusions pour mener les deuxEspionage et crime financier pour projeter le pouvoir et financer à la fois leurs capacités cyber et cinétiques.
Les dernières opérations de Nexus DPRK font allusion à une augmentation de l'adaptabilité et de la complexité, y compris une attaque de chaîne d'approvisionnement en cascade vue pour la première fois, et ciblant régulièrementBlockchain et fintech verticals.
Alors que différents groupes de menaces partagent des outils et du code, l'activité de menace nord-coréenne continue de s'adapter et de changer
Executive Summary The DPRK\'s offensive program continues to evolve, showing that the regime is determined to continue using cyber intrusions to conduct both espionage and financial crime to project power and to finance both their cyber and kinetic capabilities. Latest DPRK nexus operations hint at an increase in adaptability and complexity, including a cascading software supply chain attack seen for the first time, and consistently targeting blockchain and fintech verticals. While different threat groups share tooling and code, North Korean threat activity continues to adapt and change |
Threat | ★★★ | ||
| 2023-09-28 12:00:00 | Analyse des tendances du temps à exploiter: 2021-2022 Analysis of Time-to-Exploit Trends: 2021-2022 (lien direct) |
résumé exécutif
Mandiant Intelligence a analysé 246 vulnérabilités qui ont été exploitées entre 2021 et 2022.
soixante-deux pour cent (153) des vulnérabilités ont d'abord été exploitées sous forme de vulnérabilités de jour zéro.
Le nombre de vulnérabilités exploitées chaque année continue d'augmenter, tandis que les temps à exploiter (TTES) globaux que nous voyons diminuent.
L'exploitation d'une vulnérabilité est le plus susceptible de se produire avant la fin du premier mois suivant la sortie d'un correctif.
Microsoft, Google et Apple continuent d'être les fournisseurs les plus exploités d'une année à l'autre, mais les deux dernières années
Executive Summary Mandiant Intelligence analyzed 246 vulnerabilities that were exploited between 2021 and 2022. Sixty-two percent (153) of the vulnerabilities were first exploited as zero-day vulnerabilities. The number of exploited vulnerabilities each year continues to increase, while the overall times-to-exploit (TTEs) we are seeing are decreasing. Exploitation of a vulnerability is most likely to occur before the end of the first month following the release of a patch. Microsoft, Google, and Apple continue to be the most exploited vendors year-over-year, but the last two years |
Vulnerability Studies | ★★★★ | ||
| 2023-09-21 12:15:00 | Consulter les infrastructures gouvernementales avec un financement de subventions de cybersécurité national et local Shore Up Government Infrastructure With State and Local Cybersecurity Grant Funding (lien direct) |
Les tensions géopolitiques ont augmenté de manière significative au cours des dernières années.En fait, de toutes les intrusions couvertes dans m-tendances 2023 , les efforts de réponse pour les entités du secteur public capturées 25% de toutes les enquêtes, contre 9% en 2021. Les gouvernements des États et locaux ont la possibilité de profiter des ressources fédérales début octobre pour aider à contrecarrer ces attaques.
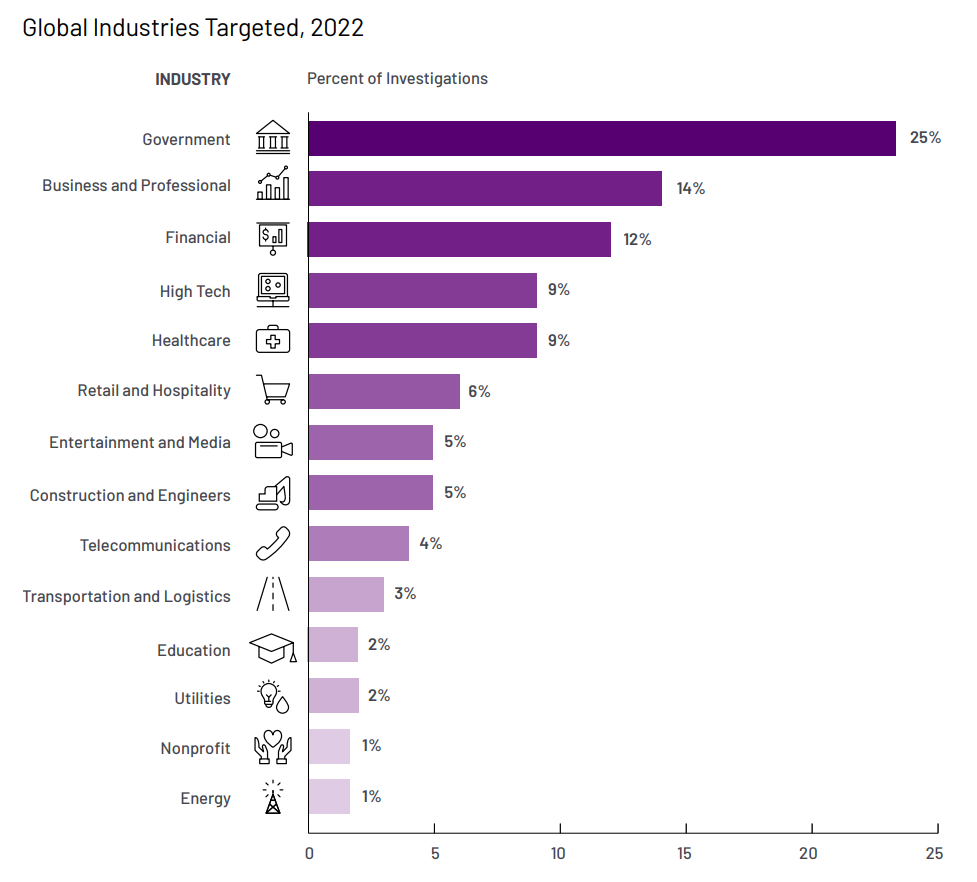 financement du mandat: slcgp
Dans le cadre de sa réponse, le gouvernement fédéral a établi le programme de subventions de cybersécurité de l'État et local (SLCGP) en vertu du 2021 Investissement d'infrastructure Act .Les récompenses SLCGP
financement du mandat: slcgp
Dans le cadre de sa réponse, le gouvernement fédéral a établi le programme de subventions de cybersécurité de l'État et local (SLCGP) en vertu du 2021 Investissement d'infrastructure Act .Les récompenses SLCGP
Geopolitical tensions have increased significantly over the past few years. In fact, of all the intrusions covered in M-Trends 2023, response efforts for public sector entities captured 25% of all investigations, compared to 9% in 2021. State and local governments have the opportunity to take advantage of federal resources in early October to help thwart these attacks. 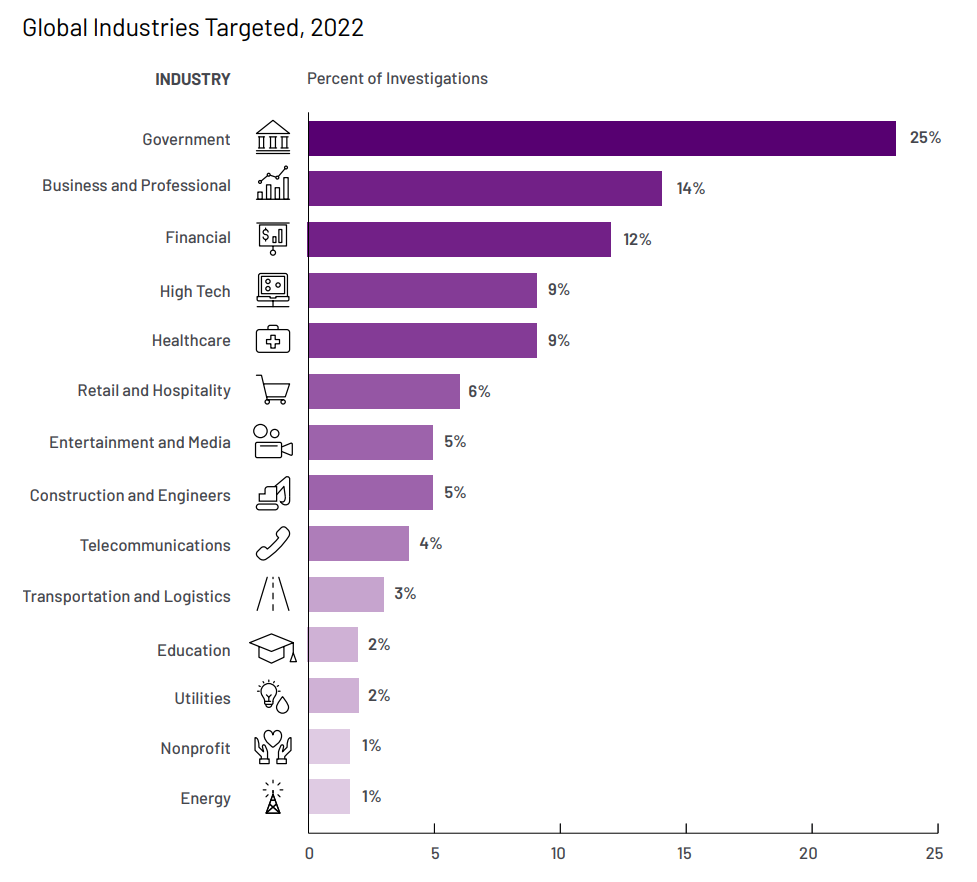 Funding the Mandate: SLCGP
As part of its response, the federal government established the State and Local Cybersecurity Grant Program (SLCGP) under the 2021 Infrastructure Investment and Jobs Act. The SLCGP awards
Funding the Mandate: SLCGP
As part of its response, the federal government established the State and Local Cybersecurity Grant Program (SLCGP) under the 2021 Infrastructure Investment and Jobs Act. The SLCGP awards |
★★ | |||
| 2023-09-21 09:00:00 | Diplomatie de backchannel: les opérations de phishing diplomatique en évolution rapide de l'APT29 Backchannel Diplomacy: APT29\\'s Rapidly Evolving Diplomatic Phishing Operations (lien direct) |
Insights de clé
Le rythme d'opérations d'APT29 \\ et l'accent mis sur l'Ukraine a augmenté au cours de la première moitié de 2023 alors que Kyiv a lancé sa contre-offensive, pointantau rôle central du SVR \\ dans la collecte d'intelligence concernant la phase pivot actuelle de la guerre.
Pendant cette période, Mandiant a suivi des changements substantiels dans l'outillage et le métier d'Apt29 \\, probablement conçus pour soutenir la fréquence et la portée accrues deopérations et entraver l'analyse médico-légale.
apt29 a utilisé diverses chaînes d'infection simultanément sur différentes opérations, indiquant que les opérateurs d'accès initiaux distincts ou
Key Insights APT29\'s pace of operations and emphasis on Ukraine increased in the first half of 2023 as Kyiv launched its counteroffensive, pointing to the SVR\'s central role in collecting intelligence concerning the current pivotal phase of the war. During this period, Mandiant has tracked substantial changes in APT29\'s tooling and tradecraft, likely designed to support the increased frequency and scope of operations and hinder forensic analysis. APT29 has used various infection chains simultaneously across different operations, indicating that distinct initial access operators or |
APT 29 | ★★★ | ||
| 2023-09-18 07:00:00 | Concentrez-vous sur les résultats: attaquez la réduction de la surface à grande échelle Focus on Outcomes: Attack Surface Reduction at Scale (lien direct) |
La surface d'attaque d'une organisation \\ est toujours en pleine expansion, ce qui en fait une cible privilégiée pour les acteurs malveillants d'exploiter les vulnérabilités inconnues dans les systèmes et les réseaux.Mais, il génère également une grande quantité de données de sécurité des sites Web et applications accessibles au public aux serveurs et bases de données internes.Analyse à travers ces données pour identifier, hiérarchiser et corriger les vulnérabilités - avant que les attaquants puissent agir sur eux - peut être une tâche intimidante, même pour les équipes de sécurité les plus expérimentées.
Pour aider les défenseurs d'aujourd'hui à combattre la fatigue qui vient de la pataugeoire à travers une mer de données, nous dévoilons Nouveau
An organization\'s attack surface is always expanding, making it a prime target for malicious actors to exploit unknown vulnerabilities in systems and networks. But, it also generates a large amount of security data from public-facing websites and applications to internal servers and databases. Parsing through this data to identify, prioritize, and remediate vulnerabilities-before attackers can act on them-can be a daunting task, even for the most experienced security teams. To help today\'s defenders combat the fatigue that comes from wading through a sea of data, we\'re unveiling new |
Vulnerability | ★★★ | ||
| 2023-09-14 17:00:00 | Pourquoi tu m'envoyez un texto?UNC3944 tire parti des campagnes de phishing SMS pour l'échange de SIM, les ransomwares, l'extorsion et la notoriété Why Are You Texting Me? UNC3944 Leverages SMS Phishing Campaigns for SIM Swapping, Ransomware, Extortion, and Notoriety (lien direct) |
unc3944 est un cluster de menace motivé financièrement qui a utilisé de manière persistante Génie social basé sur téléphone et les campagnes de phishing SMS (SMSHing) pour obtenir des informations d'identification pour gagner et augmenter l'accès aux organisations victimes.Au moins, certains acteurs de la menace UNC3944 semblent opérer dans des communautés souterraines, telles que Telegram et Forums Underground, qu'ils peuvent exploiter pour acquérir des outils, des services et / ou d'autres soutiens pour augmenter leurs opérations.Cette activité chevauche une activité qui a été rapportée dans des sources ouvertes comme " 0ktapus , "" disperser les porcs , "et" Araignée dispersée . "Depuis 2022 et via
UNC3944 is a financially motivated threat cluster that has persistently used phone-based social engineering and SMS phishing campaigns (smshing) to obtain credentials to gain and escalate access to victim organizations. At least some UNC3944 threat actors appear to operate in underground communities, such as Telegram and underground forums, which they may leverage to acquire tools, services, and/or other support to augment their operations. This activity overlaps with activity that has been reported in open sources as "0ktapus," "Scatter Swine," and "Scattered Spider." Since 2022 and through |
Threat | ★★ | ||
| 2023-09-11 09:00:00 | Supprimer votre chemin dans le système: pourquoi les vulnérabilités de suppression de fichiers arbitraires sont importantes Deleting Your Way Into SYSTEM: Why Arbitrary File Deletion Vulnerabilities Matter (lien direct) |
Les vulnérabilités de suppression de fichiers arbitraires de Windows ne doivent plus être considérées comme de simples gênes ou outils pour les attaques de déni de service (DOS).Au cours des deux dernières années, ces vulnérabilités se sont maturées à de puissantes menaces capables de dénicher un portail à un compromis complet du système.Cette transformation est illustrée dans CVE-2023-27470 (une vulnérabilité de suppression de fichiers arbitraires dans l'agent de contrôle de Nable \\ avec un score de base CVSS de 8,8) démontrant que ce qui pourrait sembler inoffensif peut, en fait, exposer des faiblesses inattenduesdans votre système.
comme suivi de la Escalating
Windows arbitrary file deletion vulnerabilities should no longer be considered mere annoyances or tools for Denial-of-Service (DoS) attacks. Over the past couple of years, these vulnerabilities have matured into potent threats capable of unearthing a portal to full system compromise. This transformation is exemplified in CVE-2023-27470 (an arbitrary file deletion vulnerability in N-Able\'s Take Control Agent with a CVSS Base Score of 8.8) demonstrating that what might initially seem innocuous can, in fact, expose unexpected weaknesses within your system. As a follow up to the Escalating |
Tool Vulnerability | ★★★ | ||
| 2023-09-08 13:30:00 | Célébrer une décennie de plaisir en ingénierie inverse - annonçant le 10e défi de l'échelle annuelle Celebrating a Decade of Reverse Engineering Fun - Announcing the 10th Annual Flare-On Challenge (lien direct) |
 nous ne pouvons pas croire qu'aujourd'hui nous annonçons officiellement le 10e défi de l'échelle annuelle!Le défi a parcouru un long chemin depuis le début.Dans le tout premier défi Flare-on, 7 140 personnes ont participé et 226 personnes l'ont terminée.Notre premier prix pour ceux qui ont relevé les sept défis ont été cette pièce très cool, et depuis lors, nous avons donné boucles de ceinture, médailles etune clé squelette.
Notre dernier dixième défi annuel évasé commencera à 20h00 HE le 29 septembre 2023. Le défi Flare-On attireraDes milliers de joueurs chaque année, et est le défi de style CTF pour nous ne pouvons pas croire qu'aujourd'hui nous annonçons officiellement le 10e défi de l'échelle annuelle!Le défi a parcouru un long chemin depuis le début.Dans le tout premier défi Flare-on, 7 140 personnes ont participé et 226 personnes l'ont terminée.Notre premier prix pour ceux qui ont relevé les sept défis ont été cette pièce très cool, et depuis lors, nous avons donné boucles de ceinture, médailles etune clé squelette.
Notre dernier dixième défi annuel évasé commencera à 20h00 HE le 29 septembre 2023. Le défi Flare-On attireraDes milliers de joueurs chaque année, et est le défi de style CTF pour
 We can\'t believe that today we\'re officially announcing the 10th annual Flare-On Challenge! The challenge has come a long way since it began. In the very first Flare-On challenge, 7,140 people participated and 226 people completed it. Our first prize for those who completed all seven challenges was this very cool coin, and since then we\'ve given out belt buckles, medals, and a skeleton key.
Our latest tenth annual Flare-On Challenge will begin at 8:00pm ET on Sept. 29th, 2023. The Flare-On challenge draws in thousands of players every year, and is the single-player CTF-style challenge for We can\'t believe that today we\'re officially announcing the 10th annual Flare-On Challenge! The challenge has come a long way since it began. In the very first Flare-On challenge, 7,140 people participated and 226 people completed it. Our first prize for those who completed all seven challenges was this very cool coin, and since then we\'ve given out belt buckles, medals, and a skeleton key.
Our latest tenth annual Flare-On Challenge will begin at 8:00pm ET on Sept. 29th, 2023. The Flare-On challenge draws in thousands of players every year, and is the single-player CTF-style challenge for |
★★★ | |||
| 2023-09-01 10:37:53 | M-Trans 2023: Perceptions de la ligne de rupture de sécurité M-Trends 2023: Percepções da linha de frente da segurança cibernética (lien direct) |
 Nous sommes heureux d'annoncer aujourd'hui les M-Trends 2023, les rapports complets que nous préparons à partir des lignes de première ligne de réponse aux incidents qui offre les types d'attaques observés, eux des secteurs plus ciblés et comment les défenseurs réagissent.Il apporte également des perçus perçus sur les envahisseurs les plus récents, et les conseils et les recommandés recommandés pour tous les nouveaux envahisseurs (TTP). Les gens des organisations organisationnelles - déres de professionnels - à ces menaces.
Le rapport M-Trends de cette année couvre les enquêtes qui
Nous sommes heureux d'annoncer aujourd'hui les M-Trends 2023, les rapports complets que nous préparons à partir des lignes de première ligne de réponse aux incidents qui offre les types d'attaques observés, eux des secteurs plus ciblés et comment les défenseurs réagissent.Il apporte également des perçus perçus sur les envahisseurs les plus récents, et les conseils et les recommandés recommandés pour tous les nouveaux envahisseurs (TTP). Les gens des organisations organisationnelles - déres de professionnels - à ces menaces.
Le rapport M-Trends de cette année couvre les enquêtes qui
 Temos o prazer de anunciar hoje o lançamento do M-Trends 2023, o relatório abrangente que preparamos a partir das linhas de frente de resposta a incidentes e que oferece métricas sobre os tipos de ataques observados, os setores mais visados e como os defensores estão reagindo. Ele também traz percepções sobre as táticas, técnicas e procedimentos (TTPs) mais recentes dos invasores, e orientações e práticas recomendadas sobre a reação de todas as pessoas da organização - de líderes seniores a profissionais - a essas ameaças.
O relatório M-Trends deste ano abrange as investigações que
Temos o prazer de anunciar hoje o lançamento do M-Trends 2023, o relatório abrangente que preparamos a partir das linhas de frente de resposta a incidentes e que oferece métricas sobre os tipos de ataques observados, os setores mais visados e como os defensores estão reagindo. Ele também traz percepções sobre as táticas, técnicas e procedimentos (TTPs) mais recentes dos invasores, e orientações e práticas recomendadas sobre a reação de todas as pessoas da organização - de líderes seniores a profissionais - a essas ameaças.
O relatório M-Trends deste ano abrange as investigações que |
★ | |||
| 2023-08-31 09:00:00 | Meilleures pratiques de protection des données Data Protection Best Practices (lien direct) |
Le vol de données d'entreprise est en augmentation alors que les attaquants cherchent à monétiser l'accès via l'extorsion et d'autres moyens.En 2022, 40% des intrusions experts Mandiant ont entraîné une perte de données, un bond de 11% par rapport à l'année précédente.Cette année, une vulnérabilité majeure dans un logiciel de transfert de fichiers a entraîné une perte de données à grande échelle pour les organisations du monde> Vulnérabilité zéro-jour ) .
 Référence: mandiant M-Trends 2023 pour protéger efficacement les données d'entreprise sensibles, les organisations doivent établir des programmes de protection des données qui consistent en un financement dédié, des outils de sécurité et des équipes définies Référence: mandiant M-Trends 2023 pour protéger efficacement les données d'entreprise sensibles, les organisations doivent établir des programmes de protection des données qui consistent en un financement dédié, des outils de sécurité et des équipes définies
Corporate data theft is on the rise as attackers look to monetize access through extortion and other means. In 2022, 40% of the intrusions Mandiant experts worked on resulted in data loss, an 11% jump from the previous year. Just this year, a major vulnerability in a file transfer software has resulted in large-scale data loss for organizations across the globe (read our research on the MOVEit zero-day vulnerability). 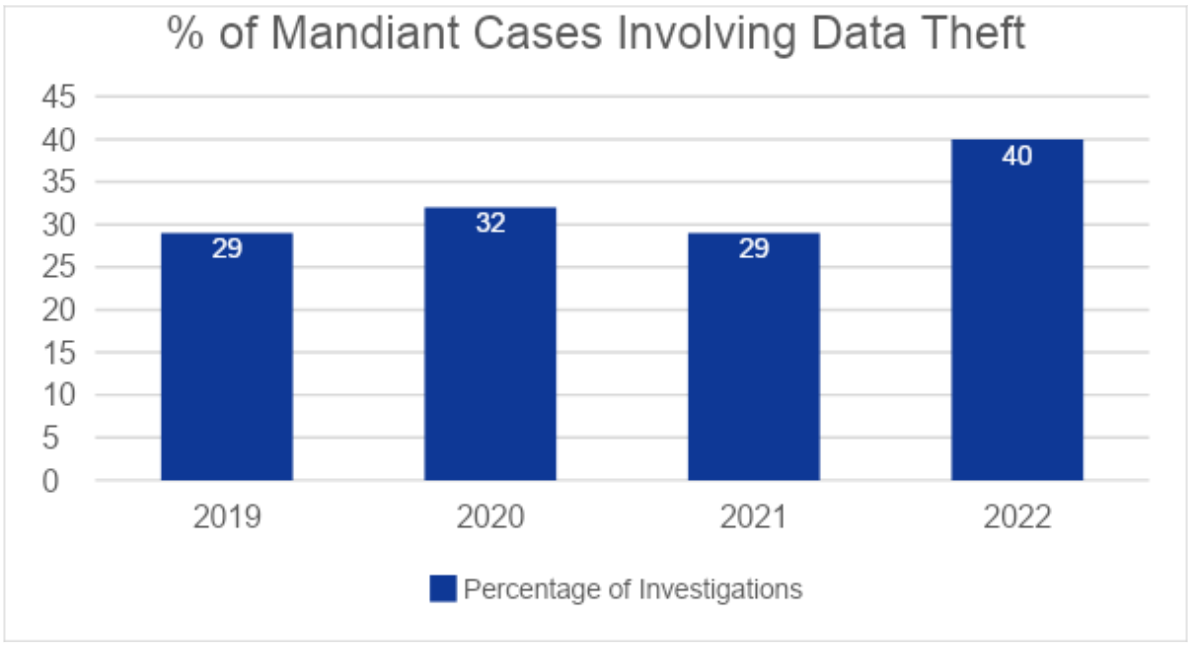 Reference: Mandiant M-Trends 2023To effectively protect sensitive corporate data, organizations should establish data protection programs that consist of dedicated funding, security tooling, and defined teams Reference: Mandiant M-Trends 2023To effectively protect sensitive corporate data, organizations should establish data protection programs that consist of dedicated funding, security tooling, and defined teams |
Vulnerability | ★★★ |

