What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-05-22 14:00:00 | Extinction de l'IOC?Les acteurs de cyber-espionnage de Chine-Nexus utilisent des réseaux orbes pour augmenter les coûts des défenseurs IOC Extinction? China-Nexus Cyber Espionage Actors Use ORB Networks to Raise Cost on Defenders (lien direct) |
Written by: Michael Raggi
Mandiant Intelligence is tracking a growing trend among China-nexus cyber espionage operations where advanced persistent threat (APT) actors utilize proxy networks known as “ORB networks” (operational relay box networks) to gain an advantage when conducting espionage operations. ORB networks are akin to botnets and are made up of virtual private servers (VPS), as well as compromised Internet of Things (IoT) devices, smart devices, and routers that are often end of life or unsupported by their manufacturers. Building networks of compromised devices allows ORB network administrators to easily grow the size of their ORB network with little effort and create a constantly evolving mesh network that can be used to conceal espionage operations. By using these mesh networks to conduct espionage operations, actors can disguise external traffic between command and control (C2) infrastructure and victim environments including vulnerable edge devices that are being exploited via zero-day vulnerabilities. These networks often use both rented VPS nodes in combination with malware designed to target routers so they can grow the number of devices capable of relaying traffic within compromised networks. Mandiant assesses with moderate confidence that this is an effort to raise the cost of defending an enterprise\'s network and shift the advantage toward espionage operators by evading detection and complicating attribution. Mandiant believes that if network defenders can shift the current enterprise defense paradigm away from treating adversary infrastructure like indicators of compromise (IOCs) and instead toward tracking ORB networks like evolving entities akin to APT groups, enterprises can contend with the rising challenge of ORB networks in the threat landscape. IOC Extinction and the Rise of ORB Networks The cybersecurity industry has reported on the APT practice of ORB network usage in the past as well as on the functional implementation of these networks. Less discussed are the implications of broad ORB network usage by a multitude of China-nexus espionage actors, which has become more common over recent years. The following are three key points and paradigm shifting implications about ORB networks that require enterprise network defenders to adapt the way they think about China-nexus espionage actors: ORB networks undermine the idea of “Actor-Controlled Infrastructure”: ORB networks are infrastructure networks administered by independent entities, contractors, or administrators within the People\'s Republic of China (PRC). They are not controlled by a single APT actor. ORB networks create a network interface, administer a network of compromised nodes, and contract access to those networks to multiple APT actors that will use the ORB networks to carry out their own distinct espionage and reconnaissance. These networks are not controlled by APT actors using them, but rather are temporarily used by these APT actors often to deploy custom tooling more conventionally attributable to known China-nexus adversaries. ORB network infrastructure has a short lifesp |
Malware Tool Vulnerability Threat Prediction Cloud Commercial | APT 15 APT 5 APT 31 | ★★★ | |
| 2024-04-29 14:00:00 | De l'assistant à l'analyste: la puissance de Gemini 1.5 Pro pour l'analyse des logiciels malveillants From Assistant to Analyst: The Power of Gemini 1.5 Pro for Malware Analysis (lien direct) |
Executive Summary A growing amount of malware has naturally increased workloads for defenders and particularly malware analysts, creating a need for improved automation and approaches to dealing with this classic threat. With the recent rise in generative AI tools, we decided to put our own Gemini 1.5 Pro to the test to see how it performed at analyzing malware. By providing code and using a simple prompt, we asked Gemini 1.5 Pro to determine if the file was malicious, and also to provide a list of activities and indicators of compromise. We did this for multiple malware files, testing with both decompiled and disassembled code, and Gemini 1.5 Pro was notably accurate each time, generating summary reports in human-readable language. Gemini 1.5 Pro was even able to make an accurate determination of code that - at the time - was receiving zero detections on VirusTotal. In our testing with other similar gen AI tools, we were required to divide the code into chunks, which led to vague and non-specific outcomes, and affected the overall analysis. Gemini 1.5 Pro, however, processed the entire code in a single pass, and often in about 30 to 40 seconds. Introduction The explosive growth of malware continues to challenge traditional, manual analysis methods, underscoring the urgent need for improved automation and innovative approaches. Generative AI models have become invaluable in some aspects of malware analysis, yet their effectiveness in handling large and complex malware samples has been limited. The introduction of Gemini 1.5 Pro, capable of processing up to 1 million tokens, marks a significant breakthrough. This advancement not only empowers AI to function as a powerful assistant in automating the malware analysis workflow but also significantly scales up the automation of code analysis. By substantially increasing the processing capacity, Gemini 1.5 Pro paves the way for a more adaptive and robust approach to cybersecurity, helping analysts manage the asymmetric volume of threats more effectively and efficiently. Traditional Techniques for Automated Malware Analysis The foundation of automated malware analysis is built on a combination of static and dynamic analysis techniques, both of which play crucial roles in dissecting and understanding malware behavior. Static analysis involves examining the malware without executing it, providing insights into its code structure and unobfuscated logic. Dynamic analysis, on the other hand, involves observing the execution of the malware in a controlled environment to monitor its behavior, regardless of obfuscation. Together, these techniques are leveraged to gain a comprehensive understanding of malware. Parallel to these techniques, AI and machine learning (ML) have increasingly been employed to classify and cluster malware based on behavioral patterns, signatures, and anomalies. These methodologies have ranged from supervised learning, where models are trained on labeled datasets, to unsupervised learning for clustering, which identifies patterns without predefined labels to group similar malware. | Malware Hack Tool Vulnerability Threat Studies Prediction Cloud Conference | Wannacry | ★★★ | |
| 2024-03-28 11:00:00 | La vie après la mort?Les campagnes de l'IO liées à un homme d'affaires russe notoire Prigozhin persiste après sa chute politique et sa mort Life After Death? IO Campaigns Linked to Notorious Russian Businessman Prigozhin Persist After His Political Downfall and Death (lien direct) |
Written by: Alden Wahlstrom, David Mainor, Daniel Kapellmann Zafra
In June 2023, Russian businessman Yevgeniy Prigozhin and his private military company (PMC) “Wagner” carried out an armed mutiny within Russia. The events triggered the meteoric political downfall of Prigozhin, raising questions about the future of his various enterprises that were only underscored when he died two months later under suspicious circumstances. Up to that point, Prigozhin and his enterprises worked to advance the Kremlin\'s interests as the manifestation of the thinnest veil of plausible deniability for state-guided actions on multiple continents. Such enterprises included the Wagner PMC; overt influence infrastructure, like his media company Patriot Group that housed his media companies, including the “RIA FAN” Federal News Agency; covert influence infrastructures; and an array of businesses aimed at generating personal wealth and the resourcing necessary to fund his various ventures. Mandiant has for years tracked and reported on covert information operations (IO) threat activity linked to Prigozhin. His involvement in IO was first widely established in the West as part of the public exposure of Russian-backed interference in the 2016 U.S. presidential election-this included activity conducted by Russia\'s Internet Research Agency (IRA), which the U.S. Government publicly named Prigozhin as its financier. Subsequently, Prigozhin was publicly connected to a web of IO activity targeting the U.S., EU, Ukraine, Russian domestic audiences, countries across Africa, and further afield. Such activity has worked not only to advance Russian interests on matters of strategic importance, but also has attempted to exploit existing divisions in societies targeting various subgroups across their population. Throughout 2023, Mandiant has observed shifts in the activity from multiple IO campaigns linked to Prigozhin, including continued indicators that components of these campaigns have remained viable since his death. This blog post examines a sample of Prigozhin-linked IO campaigns to better understand their outcomes thus far and provide an overview of what can be expected from these activity sets in the future. This is relevant not only because some of the infrastructure of these campaigns remains viable despite Prigozhin\'s undoing, but also because we advance into a year in which Ukraine continues to dominate Russia\'s strategic priorities and there are multiple global elections that Russia may seek to influence. Mandiant and Google\'s Threat Analysis Group (TAG) work together in support of our respective missions at Google. TAG has likewise been tracking coordinated influence operations linked to Prigozhin and the Internet Research Agency (IRA) for years; and in 2023, Google took over 400 enforcement actions to disrupt IO campaigns linked to the IRA, details of which are reported in the quarterly TAG Bulletin. TAG has not observed significant activity from the IRA or other Prigozhin-linked entities specifically on Google platforms since Prigozhin\'s death, |
Threat Studies Legislation Prediction | ★★★ | ||
| 2022-11-02 08:00:00 | Prévisions de cybersécurité mandiante 2023 Mandiant Cyber Security Forecast 2023 (lien direct) |
 Defenders must always be ready for the unexpected-everything from chasing down an alert to containing a compromise. In the cyber security realm, it\'s impossible to predict what we will experience day after day. However, that doesn\'t mean we cannot be ready for the threats that matter most. Organizations can always improve their preparedness and readiness, and part of that involves exploring the trends we are starting to see now so we are ready for them in the year ahead.
To help us clear up some of the fog surrounding 2023, we turned to Mandiant leaders and experts. We already heard from Defenders must always be ready for the unexpected-everything from chasing down an alert to containing a compromise. In the cyber security realm, it\'s impossible to predict what we will experience day after day. However, that doesn\'t mean we cannot be ready for the threats that matter most. Organizations can always improve their preparedness and readiness, and part of that involves exploring the trends we are starting to see now so we are ready for them in the year ahead.
To help us clear up some of the fog surrounding 2023, we turned to Mandiant leaders and experts. We already heard from |
Prediction | ★★★ | ||
| 2022-01-13 11:00:00 | Le parcours du cyber-risque, première partie: où allons-nous d'ici? The Cyber Risk Journey, Part One: Where Do We Go From Here? (lien direct) |
Le cyber-risque peut être un gros point d'arrêt pour les organisations.Heureusement, les conseils d'administration et les hauts dirigeants sont plus engagés que jamais et travaillent à développer une meilleure compréhension de la gestion des cyber-risques au sein de leurs organisations.Plus de dialogue avec la gestion des cadres concernant le cyber-risque et les impacts que les mesures proactives et réactives ont sur un profil de risque d'organisation est une excellente tendance à voir.
Les équipes de cybersécurité-Office en arrière-plan sur les tâches écrasantes de soutenir les opérations quotidiennes tout en étant constamment préparées pour les attaquants dans leur environnement.Équilibrage
Cyber risk can be a big blindspot for organizations. Fortunately, Boards and senior leaders are more engaged than ever before and working to develop a better understanding of how cyber risk is being managed within their organizations. More dialogue with executive management around cyber risk and the impacts proactive and reactive measures have on an organization\'s risk profile is a great trend to see. Cyber security teams-often in the background-take on the overwhelming tasks of supporting day-to-day operations while constantly being prepared for attackers in their environment. Balancing |
Prediction | ★★★ | ||
| 2020-03-23 07:00:00 | Surveillance des outils de cyber-opération ICS et des modules d'exploitation de logiciels pour anticiper les menaces futures Monitoring ICS Cyber Operation Tools and Software Exploit Modules To Anticipate Future Threats (lien direct) |
Il n'y a eu qu'un petit nombre de cyberattaques largement documentées ciblant les technologies opérationnelles (OT) / systèmes de contrôle industriel (ICS) au cours de la dernière décennie.Bien que moins d'attaques soit clairement une bonne chose, l'absence d'une taille d'échantillon adéquate pour déterminer les seuils de risque peut rendre difficile pour les défenseurs de comprendre l'environnement de menace, de hiérarchiser les efforts de sécurité et de justifier l'allocation des ressources.
Pour résoudre ce problème, Fireeye Mandiant Threat Intelligence produit une gamme de rapports pour abonnement Les clients qui se concentrent sur différents indicateurs pour prédire les menaces futures
There has only been a small number of broadly documented cyber attacks targeting operational technologies (OT) / industrial control systems (ICS) over the last decade. While fewer attacks is clearly a good thing, the lack of an adequate sample size to determine risk thresholds can make it difficult for defenders to understand the threat environment, prioritize security efforts, and justify resource allocation. To address this problem, FireEye Mandiant Threat Intelligence produces a range of reports for subscription customers that focus on different indicators to predict future threats |
Tool Threat Industrial Prediction | ★★★★ | ||
| 2017-10-19 09:00:00 | Magnber Ransomware veut infecter uniquement les bonnes personnes Magniber Ransomware Wants to Infect Only the Right People (lien direct) |
L'utilisation du kit d'exploitation (EK) est en baisse depuis la fin de 2016;Cependant, une certaine activité reste cohérente.Le kit d'exploitation de magnitude est un tel exemple qui continue d'affecter les utilisateurs, en particulier dans la région de l'APAC.
Dans la figure 1, qui est basée sur les données recueillies en mars 2017, nous pouvons voir les régions affectées par l'activité EK de magnitude au cours des trois derniers mois de 2016 et les trois premiers mois de 2017.
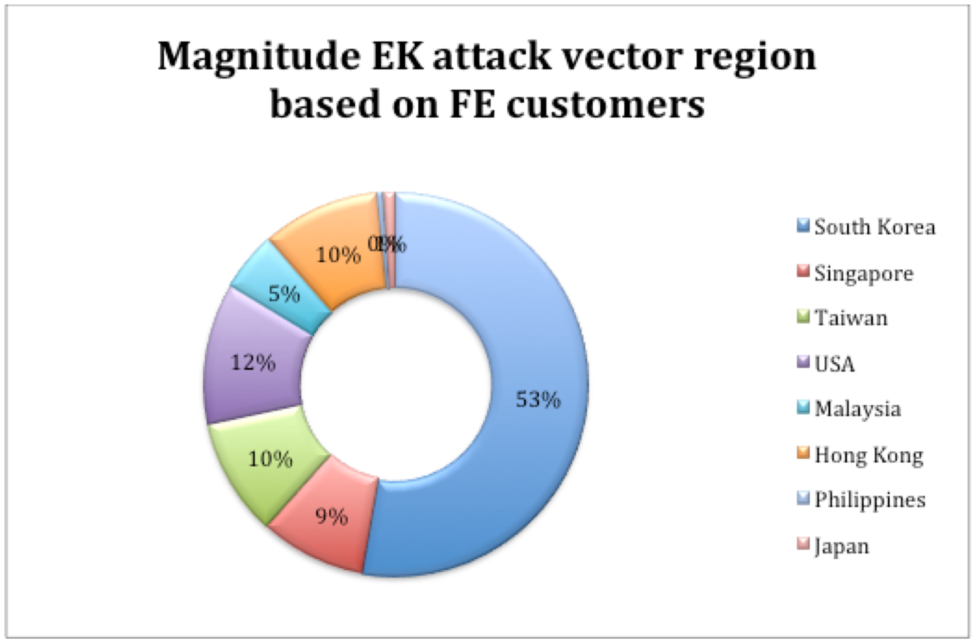 Figure 1: Distribution de l'amplitude EK comme le montre en mars 2017 Cette tendance s'est poursuivie jusqu'à la fin de septembre 2017, lorsque nous avons vu la magnitude EK se concentrer principalement sur la région de l'APAC, avec une grande partie ciblant la Corée du Sud.Activité EK de l'amplitude est ensuite tombée Figure 1: Distribution de l'amplitude EK comme le montre en mars 2017 Cette tendance s'est poursuivie jusqu'à la fin de septembre 2017, lorsque nous avons vu la magnitude EK se concentrer principalement sur la région de l'APAC, avec une grande partie ciblant la Corée du Sud.Activité EK de l'amplitude est ensuite tombée
Exploit kit (EK) use has been on the decline since late 2016; however, certain activity remains consistent. The Magnitude Exploit Kit is one such example that continues to affect users, particularly in the APAC region. In Figure 1, which is based on data gathered in March 2017, we can see the regions affected by Magnitude EK activity during the last three months of 2016 and the first three months of 2017.  Figure 1: Magnitude EK distribution as seen in March 2017This trend continued until late September 2017, when we saw Magnitude EK focus primarily on the APAC region, with a large chunk targeting South Korea. Magnitude EK activity then fell off Figure 1: Magnitude EK distribution as seen in March 2017This trend continued until late September 2017, when we saw Magnitude EK focus primarily on the APAC region, with a large chunk targeting South Korea. Magnitude EK activity then fell off |
Ransomware Prediction | ★★★ | ||
| 2016-08-22 07:00:00 | Piratage matériel intégré 101 & # 8211;Le lien Belkin Wemo Embedded Hardware Hacking 101 – The Belkin WeMo Link (lien direct) |
Pourquoi le piratage intégré?
Les appareils connectés à Internet ou exécutent un système d'exploitation complet deviennent de plus en plus répandus dans la société d'aujourd'hui.Des appareils pour les locomotives aux commutateurs d'éclairage sans fil, la tendance de l'Internet des objets (IoT) est en augmentation et ici pour rester.Cela a le potentiel de nous faciliter la vie;Cependant, la sensibilité croissante des appareils analogiques une fois permet également aux adversaires de les cibler et de les utiliser potentiellement.
Avec l'omniprésence de ces appareils connectés à Internet, il y a un excédent de «choses» à exploiter.L'intention principale de cet article de blog est
Why Embedded Hacking? Devices that are connected to the Internet or run a full operating system are becoming more and more prevalent in today\'s society. From devices for locomotives to wireless light switches, the Internet of Things (IoT) trend is on the rise and here to stay. This has the potential to make our lives much easier; however, the increasing sentience of once analog devices also enables adversaries to target them and potentially misuse them. With the ubiquity of these Internet-connected devices, there is a surplus of “Things” to exploit. The main intent of this blog post is |
Prediction Technical | ★★★★ |
1
We have: 8 articles.
We have: 8 articles.
To see everything:
Our RSS (filtrered)
