What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-11-03 04:15:21 | CVE-2023-36620 (lien direct) | Un problème a été découvert dans l'application de contrôle parental de Boomerang avant 13.83 pour Android.L'application manque l'attribut Android: allongBackup = "false" dans le manifeste.Cela permet à l'utilisateur de sauvegarder la mémoire interne de l'application sur un PC.Cela donne à l'utilisateur l'accès au jeton API qui est utilisé pour authentifier les demandes à l'API.
An issue was discovered in the Boomerang Parental Control application before 13.83 for Android. The app is missing the android:allowBackup="false" attribute in the manifest. This allows the user to backup the internal memory of the app to a PC. This gives the user access to the API token that is used to authenticate requests to the API. |
Mobile | |||
| 2023-11-02 23:02:15 | Google abandonne cette API qui ressemblait un peu à DRM pour les sites Web Google gives up on that API that looked more than a bit like DRM for websites (lien direct) |
Au lieu de cela, Chocolate Factory se concentre sur une attestation plus limitée pour Android WebViews Au milieu de l'inquiétude croissante de la communauté, Google dit qu'il ne développera plus de technologies controversées qui auraient lutté contre la fraude en ligne, mais les critiques ressemblaient davantage à DRMpour les sites Web… | Mobile | ★★★ | ||
| 2023-11-02 20:13:20 | Apple glisse de 2013 Skewer Android comme "un appareil de suivi massif" Apple slides from 2013 skewer Android as “a massive tracking device” (lien direct) |
Mais Apple voulait également savoir quels résultats les utilisateurs ont cliqué sur Google à partir d'iPhones.
But Apple also wanted to know what results users clicked on Google from iPhones. |
Mobile | ★★ | ||
| 2023-11-02 15:17:00 | Utilisateurs de WhatsApp de langue arabophone ciblés avec des logiciels espions Arabic-speaking WhatsApp users targeted with spyware (lien direct) |
 Les pirates inconnus ciblent les utilisateurs en Arabie saoudite, au Yémen et en Azerbaïdjan avec l'espionnage des logiciels malveillants distribués via des mods WhatsApp créés par l'utilisateur qui personnalisent ou ajoutent de nouvelles fonctionnalités au service.Dans la dernière campagne, les chercheurs de la société de cybersécurité Kaspersky ont découvert des mods WhatsApp auparavant inoffensifs qui avaient reçu un code malveillant conçu pour espionner sur Android
Les pirates inconnus ciblent les utilisateurs en Arabie saoudite, au Yémen et en Azerbaïdjan avec l'espionnage des logiciels malveillants distribués via des mods WhatsApp créés par l'utilisateur qui personnalisent ou ajoutent de nouvelles fonctionnalités au service.Dans la dernière campagne, les chercheurs de la société de cybersécurité Kaspersky ont découvert des mods WhatsApp auparavant inoffensifs qui avaient reçu un code malveillant conçu pour espionner sur Android
 Unknown hackers are targeting users in Saudi Arabia, Yemen and Azerbaijan with spying malware distributed through user-created WhatsApp mods that customize or add new features to the service. In the latest campaign, researchers at the cybersecurity firm Kaspersky discovered previously harmless WhatsApp mods that had been injected with malicious code designed to spy on Android
Unknown hackers are targeting users in Saudi Arabia, Yemen and Azerbaijan with spying malware distributed through user-created WhatsApp mods that customize or add new features to the service. In the latest campaign, researchers at the cybersecurity firm Kaspersky discovered previously harmless WhatsApp mods that had been injected with malicious code designed to spy on Android |
Malware Mobile | ★★★ | ||
| 2023-11-02 13:53:20 | AppDome s'associe à JetBrains TeamCity pour automatiser la livraison des applications mobiles sécurisées Appdome Partners with JetBrains TeamCity to Automate Delivery of Secure Mobile Apps (lien direct) |
AppDome s'associe à JetBrains TeamCity pour automatiser la livraison d'applications mobiles sécurisées
Le partenariat amène Android et IOS Cyber Defense Automation à l'intérieur du pipeline CI / CD de JetBrains TeamCity
-
nouvelles commerciales
Appdome Partners with JetBrains TeamCity to Automate Delivery of Secure Mobile Apps Partnership Brings Android and iOS Cyber Defense Automation Inside the JetBrains TeamCity CI/CD Pipeline - Business News |
Mobile | ★★ | ||
| 2023-11-02 13:00:00 | Collection d'adhésion de Lenovo \\'s Tab: une preuve de concept de vêtements pour prendre des comprimés à l'extérieur Lenovo\\'s Tab Wear Collection: A Clothing Proof-of-Concept for Taking Tablets Outdoors (lien direct) |
Lenovo s'est associé à des créateurs de mode pour faire des vêtements d'extérieur pour transporter et utiliser - ses tablettes Android à l'extérieur de la maison.
Lenovo teamed up with fashion designers to make outerwear for carrying-and using-its Android tablets outside the home. |
Mobile | ★★ | ||
| 2023-11-02 12:00:24 | Plus de moyens pour les utilisateurs d'identifier les applications testées sur la sécurité indépendante sur Google Play More ways for users to identify independently security tested apps on Google Play (lien direct) |
Posted by Nataliya Stanetsky, Android Security and Privacy Team
Keeping Google Play safe for users and developers remains a top priority for Google. As users increasingly prioritize their digital privacy and security, we continue to invest in our Data Safety section and transparency labeling efforts to help users make more informed choices about the apps they use.
Research shows that transparent security labeling plays a crucial role in consumer risk perception, building trust, and influencing product purchasing decisions. We believe the same principles apply for labeling and badging in the Google Play store. The transparency of an app\'s data security and privacy play a key role in a user\'s decision to download, trust, and use an app.
Highlighting Independently Security Tested VPN Apps
Last year, App Defense Alliance (ADA) introduced MASA (Mobile App Security Assessment), which allows developers to have their apps independently validated against a global security standard. This signals to users that an independent third-party has validated that the developers designed their apps to meet these industry mobile security and privacy minimum best practices and the developers are going the extra mile to identify and mitigate vulnerabilities. This, in turn, makes it harder for attackers to reach users\' devices and improves app quality across the ecosystem. Upon completion of the successful validation, Google Play gives developers the option to declare an “Independent security review” badge in its Data Safety section, as shown in the image below. While certification to baseline security standards does not imply that a product is free of vulnerabilities, the badge associated with these validated apps helps users see at-a-glance that a developer has prioritized security and privacy practices and committed to user safety.
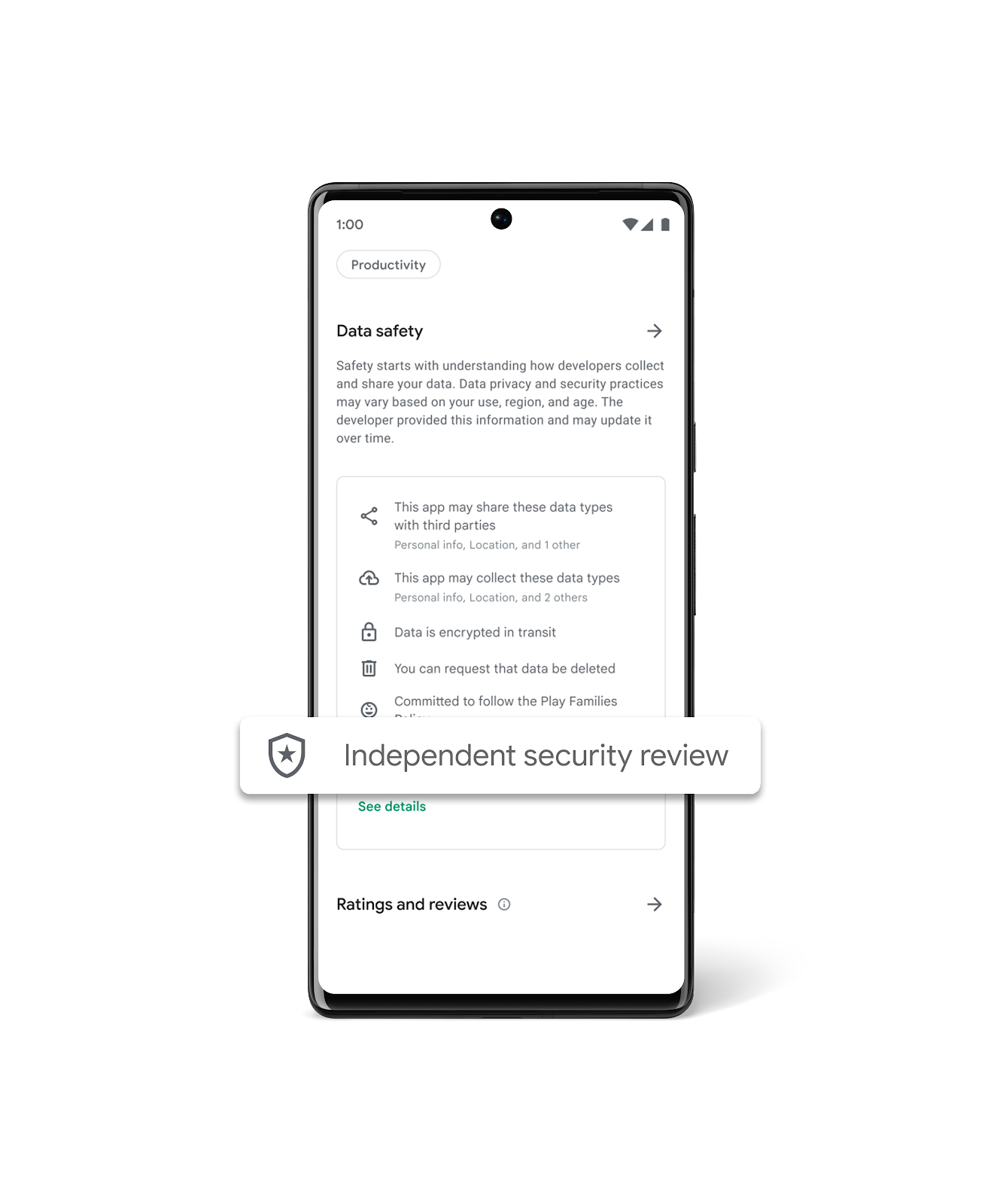 To help give users a simplified view of which apps have undergone an independent security validation, we\'re introducing a new Google Play store banner for specific app types, starting with VPN apps. We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle. When a user searches for VPN apps, they will now see a banner at the top of Google Play that educates them about the “Independent security review” badge in the Data Safety Section. Users also have the ability to “Learn More”, which redirects them to the App Validation Directory, a centralized place to view all VPN apps that have been independently security reviewed. Users can also discover additional technical assessment details in the App Validation Directory, helping them to make more informed decisions about what VPN apps to download, use, and trust with their data.
To help give users a simplified view of which apps have undergone an independent security validation, we\'re introducing a new Google Play store banner for specific app types, starting with VPN apps. We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle. When a user searches for VPN apps, they will now see a banner at the top of Google Play that educates them about the “Independent security review” badge in the Data Safety Section. Users also have the ability to “Learn More”, which redirects them to the App Validation Directory, a centralized place to view all VPN apps that have been independently security reviewed. Users can also discover additional technical assessment details in the App Validation Directory, helping them to make more informed decisions about what VPN apps to download, use, and trust with their data.
|
Tool Vulnerability Mobile Technical | ★★ | ||
| 2023-11-02 11:30:00 | Bugy octets # 216 & # 8211;Injections SQL, Android XSS et rédaction de rapports de qualité Bug Bytes #216 – SQL injections, Android XSS and Writing Quality Reports (lien direct) |
> Bug Bytes est une newsletter hebdomadaire organisée par les membres de la communauté Bug Bounty.La deuxième série est organisée par InsiderPhd.Chaque semaine, elle nous tient à jour avec une liste complète des articles, des outils, des tutoriels et des ressources.Ce numéro couvre la semaine du 23 octobre au 29 octobre Intigriti News de mon cahier
>Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by InsiderPhD. Every week, she keeps us up to date with a comprehensive list of write-ups, tools, tutorials and resources. This issue covers the week from October 23rd to October 29th Intigriti News From my notebook |
Tool Mobile Technical | ★★★ | ||
| 2023-11-01 13:00:00 | Tirer parti des normes NIST pour rationaliser votre stratégie de sécurité sur mobile axée sur le mobile Leveraging NIST Standards to Streamline Your Mobile-First Security Strategy (lien direct) |
> Ce webinaire enseigne comment les professionnels de la cybersécurité s'appuient sur des ressources, telles que les normes NIST, pour développer leur approche de sécurité des appareils mobiles.
>This webinar teaches how cybersecurity professionals rely on resources, such as NIST standards, to develop their mobile device security approach. |
Mobile | ★★★ | ||
| 2023-10-25 15:00:00 | Gardez les résidents \\ 'les appareils mobiles en sécurité avec Secure Boston Keep Residents\\' Mobile Devices Safe with Secure Boston (lien direct) |
Secure Boston garde les appareils mobiles de Boston en sécurité avec les alertes du réseau Wi-Fi, la sécurité des applications Android, la falsification du système & # 038;détection de phishing, et plus.
Secure Boston keeps Boston residents\' mobile devices safe with Wi-Fi network alerts, Android app safety, system tampering & phishing detection, and more. |
Mobile | ★★★ | ||
| 2023-10-16 17:41:00 | Spynote: Méfiez-vous de ce cheval de Troie Android qui enregistre les appels audio et téléphoniques SpyNote: Beware of This Android Trojan that Records Audio and Phone Calls (lien direct) |
Le cheval de Troie bancaire Android connu sous le nom de Spynote a été disséqué pour révéler ses diverses fonctionnalités de collecte d'informations.
Selon F-Secure, les campagnes de phishing SMS impliquant les victimes potentielles de l'astuce spyware pour installer l'application en cliquant sur le lien intégré, selon F-Secure.
En plus de demander des autorisations invasives pour accéder aux journaux d'appels, à la caméra, aux messages SMS et
The Android banking trojan known as SpyNote has been dissected to reveal its diverse information-gathering features. Typically spread via SMS phishing campaigns, attack chains involving the spyware trick potential victims into installing the app by clicking on the embedded link, according to F-Secure. Besides requesting invasive permissions to access call logs, camera, SMS messages, and external |
Mobile | ★★★ | ||
| 2023-10-16 11:18:28 | Fake \\ 'RedAlert \\' Rocket Alert App for Israel installe Android Spyware Fake \\'RedAlert\\' rocket alert app for Israel installs Android spyware (lien direct) |
Les utilisateurs d'Android israéliens sont ciblés par une version malveillante de l'application \\ 'redalert - Rocket Alertes \' qui, bien qu'elle offre la fonctionnalité promise, agit comme un logiciel espion en arrière-plan.[...]
Israeli Android users are targeted by a malicious version of the \'RedAlert - Rocket Alerts\' app that, while it offers the promised functionality, acts as spyware in the background. [...] |
Mobile | ★★ | ||
| 2023-10-04 20:34:30 | Transformer la sécurité basée sur l'identité avec la défense des menaces mobiles de Zimperium et la plate-forme de protection des menaces d'identité OKTA Transforming Identity-Based Security with Zimperium Mobile Threat Defense and Okta Identity Threat Protection Platform (lien direct) |
> Zimperium est ravi d'annoncer qu'il s'agit d'un partenaire d'intégration fondateur de la protection des menaces d'identité d'Okta \\ avec Okta AI, offrant une protection contre les menaces d'identité en temps réel et améliorant la sécurité des clients conjoints.
>Zimperium is excited to announce it is a founding integration partner of Okta\'s Identity Threat Protection with Okta AI, delivering real-time identity threat protection and enhancing the security of joint customers. |
Threat Mobile | ★★★ | ||
| 2023-10-03 14:12:57 | La mise à jour de la sécurité Android Octobre corrige les jours zéro exploités dans les attaques Android October security update fixes zero-days exploited in attacks (lien direct) |
Google a publié les mises à jour de sécurité d'octobre 2023 pour Android, abordant 54 vulnérabilités uniques, dont deux connues pour être activement exploitées.[...]
Google has released the October 2023 security updates for Android, addressing 54 unique vulnerabilities, including two known to be actively exploited. [...] |
Vulnerability Mobile | ★★★ | ||
| 2023-09-29 18:43:00 | Le fournisseur de logiciels espions cible les organisations égyptiennes avec une chaîne d'exploitation iOS rare Spyware Vendor Targets Egyptian Orgs With Rare iOS Exploit Chain (lien direct) |
La société israélienne a développé des logiciels malveillants mobiles très ciblés qui rendraient tout jaloux.
The Israeli company developed highly-targeted, mobile malware that would make any APT jealous. |
Malware Mobile | ★★★ | ||
| 2023-09-28 11:25:36 | La société d'acquisition russe zéro-jour offre 20 millions de dollars pour Android, iOS exploits Russian Zero-Day Acquisition Firm Offers $20 Million for Android, iOS Exploits (lien direct) |
La société d'acquisition russe zéro-jour Operation Zero propose désormais 20 millions de dollars pour les chaînes d'exploitation Android complètes et iOS.
Russian zero-day acquisition firm Operation Zero is now offering $20 million for full Android and iOS exploit chains. |
Threat Mobile | ★★★★ | ||
| 2023-09-08 08:30:00 | Apple Patches deux jours zéro exploités dans les attaques de pégase Apple Patches Two Zero-Days Exploited in Pegasus Attacks (lien direct) |
Les utilisateurs d'appareils iOS ont demandé à activer le mode de verrouillage
Users of iOS devices urged to enable lockdown mode |
Patching Mobile | ★★ | ||
| 2023-09-06 19:32:00 | Alerte zéro-jour: la dernière mise à jour du patch Android comprend une correction pour une faille nouvellement activement exploitée Zero-Day Alert: Latest Android Patch Update Includes Fix for Newly Actively Exploited Flaw (lien direct) |
Google a déployé des correctifs de sécurité mensuels pour Android afin de traiter un certain nombre de défauts, y compris un bug zéro-jour qui, selon lui, pourrait avoir été exploité dans la nature.
Suivi en CVE-2023-35674, la vulnérabilité de haute sévérité est décrite comme un cas d'escalade de privilèges impactant le cadre Android.
«Il y a des indications que le CVE-2023-35674 peut être sous une exploitation limitée et ciblée», le
Google has rolled out monthly security patches for Android to address a number of flaws, including a zero-day bug that it said may have been exploited in the wild. Tracked as CVE-2023-35674, the high-severity vulnerability is described as a case of privilege escalation impacting the Android Framework. “There are indications that CVE-2023-35674 may be under limited, targeted exploitation,” the |
Vulnerability Mobile | ★★ | ||
| 2023-08-29 11:00:00 | Dévoiler les tactiques de la lapsus $: une revue des vecteurs d'attaques internes, de l'exploitation des appareils mobiles et des techniques d'ingénierie sociale Unveiling the Tactics of Lapsus$: A Review of Internal Attacks Vectors, Mobile Device Exploitation, and Social Engineering Techniques (lien direct) |
> Le 10 août 2023, le rapport du Département américain de la sécurité intérieure (DHS) a publié le rapport du Cyber Safety Review Board (CSRB) résumant les conclusions de son examen dans les activités du groupe d'acteur de menace Lapsus $, qui, à la fin de 2021 et à continuerà la fin de 2022, a tenté d'extorquer des dizaines de mondiaux bien connus [& # 8230;]
>On August 10, 2023, the U.S. Department of Homeland Security (DHS) released the Cyber Safety Review Board (CSRB) report summarizing the findings of its review into the activities of threat actor group Lapsus$, who, beginning in late 2021 and continuing into late 2022, attempted to extort dozens of well-known global […] |
Threat Mobile | ★★★ | ||
| 2023-08-09 12:19:00 | Nouvelle fonctionnalité de sécurité Android 14: les administrateurs informatiques peuvent désormais désactiver les réseaux 2G New Android 14 Security Feature: IT Admins Can Now Disable 2G Networks (lien direct) |
Google a introduit une nouvelle fonctionnalité de sécurité dans Android 14 qui permet aux administrateurs informatiques de désactiver la prise en charge des réseaux cellulaires 2G dans leur flotte de périphériques gérés.
Le géant de la recherche a déclaré qu'il introduisait un deuxième paramètre utilisateur pour désactiver la prise en charge, au niveau du modèle, pour les connexions cellulaires à nuls nuls.
"Le modèle de sécurité Android suppose que tous les réseaux sont hostiles pour protéger les utilisateurs
Google has introduced a new security feature in Android 14 that allows IT administrators to disable support for 2G cellular networks in their managed device fleet. The search giant said it\'s introducing a second user setting to turn off support, at the model level, for null-ciphered cellular connections. "The Android Security Model assumes that all networks are hostile to keep users safe from |
Mobile | ★★★ | ||
| 2023-08-04 13:36:07 | Adware invisible: dévoilement de la fraude publicitaire ciblant les utilisateurs d'Android Invisible Adware: Unveiling Ad Fraud Targeting Android Users (lien direct) |
>  Rendu par Sangryol Ryu, chercheur à menace McAfee, nous vivons dans un monde où les publicités sont partout, et ce n'est pas une surprise ...
Rendu par Sangryol Ryu, chercheur à menace McAfee, nous vivons dans un monde où les publicités sont partout, et ce n'est pas une surprise ...
>  Authored by SangRyol Ryu, McAfee Threat Researcher We live in a world where advertisements are everywhere, and it’s no surprise...
Authored by SangRyol Ryu, McAfee Threat Researcher We live in a world where advertisements are everywhere, and it’s no surprise...
|
Threat Mobile | ★★ | ||
| 2023-07-28 00:00:00 | Cherryblos connexes et logiciels malveillants Android associés impliqués dans des campagnes d'escroquerie Related CherryBlos and FakeTrade Android Malware Involved in Scam Campaigns (lien direct) |
L'équipe du Service de réputation d'application mobile de Trend Micro \'s Mobile a découvert deux nouvelles familles de logiciels malveillants Android impliqués dans des crypto-monnaies et des campagnes d'escroquerie motivées financièrement ciblant les utilisateurs d'Android.
Trend Micro\'s Mobile Application Reputation Service (MARS) team discovered two new related Android malware families involved in cryptocurrency-mining and financially-motivated scam campaigns targeting Android users. |
Malware Mobile Prediction | ★★ | ||
| 2023-07-20 09:34:15 | Lookout découvre un logiciel de surveillance Android avancée lié à l'APT41 de la Chine Lookout Uncovers Advanced Android Surveillanceware Linked To China\\'s APT41 (lien direct) |
Hier, Lookout, Inc., a annoncé la découverte de logiciels de surveillance Android sophistiqués connus sous le nom de Wyrmspy et Dragonegg, qui a été lié au groupe d'espionnage chinois Apt41 (aka Double Dragon, Barium et Winnti).Bien qu'il ait été inculpé de plusieurs accusations du gouvernement américain pour ses attaques contre plus de 100 entreprises privées et publiques aux États-Unis [& # 8230;]
Yesterday, Lookout, Inc., announced the discovery of sophisticated Android surveillanceware known as WyrmSpy and DragonEgg, which has been linked to the Chinese espionage group APT41 (AKA Double Dragon, BARIUM and Winnti). Despite being indicted on multiple charges by the U.S. government for its attacks on more than 100 private and public enterprises in the U.S. […] |
Mobile | APT 41 APT 41 | ★★★ | |
| 2023-07-13 08:27:12 | Vigilance.fr - IBM QRadar SIEM : obtention d\'information via Delegated Admin Tenant User, analysé le 28/06/2023 (lien direct) | Un attaquant peut contourner les restrictions d'accès aux données de IBM QRadar SIEM, via Delegated Admin Tenant User, afin d'obtenir des informations sensibles. - Vulnérabilités | Vulnerability Mobile | ★★★ | ||
| 2023-07-10 07:50:05 | Android dans Windows : les dernières avancées chez Microsoft (lien direct) | Coup d'œil sur quelques-uns des derniers ajouts dans le sous-système Windows pour Android, ainsi que sur la roadmap. | Mobile | ★★ | ||
| 2023-03-23 17:25:00 | Nexus: un nouveau cheval de Troie bancaire androïde croissant ciblant 450 applications financières [Nexus: A New Rising Android Banking Trojan Targeting 450 Financial Apps] (lien direct) | Un troyen bancaire Android émergent surnommé Nexus a déjà été adopté par plusieurs acteurs de menace pour cibler 450 demandes financières et procéder à une fraude.
"Nexus semble être à ses débuts de développement", a déclaré Cleafy, la société italienne de cybersécurité, dans un rapport publié cette semaine.
"Nexus fournit toutes les principales fonctionnalités pour effectuer des attaques ATO (rachat de compte) contre les portails bancaires et
An emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450 financial applications and conduct fraud. "Nexus appears to be in its early stages of development," Italian cybersecurity firm Cleafy said in a report published this week. "Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and |
Threat Mobile | ★★★ | ||
| 2023-03-23 12:02:12 | \\ 'Nexus \\' Android Trojan cible 450 applications financières [\\'Nexus\\' Android Trojan Targets 450 Financial Applications] (lien direct) | Promu comme un maas, le Trojan Android Nexus cible 450 applications financières pour la prise de contrôle du compte.
Promoted as a MaaS, the Nexus Android trojan targets 450 financial applications for account takeover. |
Mobile | ★★ | ||
| 2023-03-15 14:17:16 | Russia Calling? Scammers Target High-level Western Officials (lien direct) | Promu comme un maas, le Trojan Android Nexus cible 450 applications financières pour la prise de contrôle du compte.
Promoted as a MaaS, the Nexus Android trojan targets 450 financial applications for account takeover. |
Mobile | ★★★ | ||
| 2022-12-13 06:13:36 | Cette application d\'espionnage siphonne les données de milliers de smartphones (lien direct) |  Des dizaines de milliers d'utilisateurs d'iPhone et de smartphones Android ont peut-être vu leurs données personnelles volées sans même le savoir. En cause, une application d'espionnage compromise par des failles de sécurité. Des dizaines de milliers d'utilisateurs d'iPhone et de smartphones Android ont peut-être vu leurs données personnelles volées sans même le savoir. En cause, une application d'espionnage compromise par des failles de sécurité. |
Mobile | ★★ | ||
| 2022-12-07 09:30:23 | Over 75 Vulnerabilities Patched in Android With December 2022 Security Updates (lien direct) | Google this week announced the December 2022 Android updates with patches for over 75 vulnerabilities, including multiple critical remote code execution (RCE) flaws. The most severe of the RCE bugs is CVE-2022-20411, an issue in Android's System component that could be exploited over Bluetooth. | Mobile | ★★★★ | ||
| 2022-12-05 14:04:27 | Nouvelle vulnérabilité sur Android Venafi pointe l\'absence de contrôles de sécurité appropriés sur les certificats de signature de code (lien direct) | Les équipes Venafi se sont intéressées à une importante fuite de sécurité qui a mené à la création d'applications malveillantes " de confiance " pouvant accéder à l'ensemble du système d'exploitation Android sur les appareils de Samsung, LG, et d'autres. Plusieurs OEM Android ont eu leurs clés de signature de plate-forme fuité en dehors de leurs entreprises respectives. Cette clé est utilisée pour s'assurer que la version d'Android qui s'exécute sur un appareil est légitime et créée par le fabricant. Cette même clé peut également être utilisée pour signer des applications individuelles. - Vulnérabilités | Mobile | ★★★ | ||
| 2022-12-04 10:11:22 | Android malware apps with 2 million installs spotted on Google Play (lien direct) | A new set of Android malware, phishing, and adware apps have infiltrated the Google Play store, tricking over two million people into installing them. [...] | Malware Mobile | ★★★ | ||
| 2022-11-25 11:15:09 | Google lance l\'alerte : des millions de smartphones Android exposés à des failles de sécurité (lien direct) |  L'équipe d'experts en sécurité informatique de Google, connue sous le nom " Project Zero ", a publié un billet de blog alertant sur la vulnérabilité des GPU Mali que l'on retrouve dans des millions de smartphones Android. L'équipe d'experts en sécurité informatique de Google, connue sous le nom " Project Zero ", a publié un billet de blog alertant sur la vulnérabilité des GPU Mali que l'on retrouve dans des millions de smartphones Android. |
Mobile | ★★★ | ||
| 2022-11-24 16:00:00 | Bahamut Spyware Group Compromises Android Devices Via Fake VPN Apps (lien direct) | The app used as part of the campaign was a trojanized version of SoftVPN or OpenVPN | Mobile | Bahamut Bahamut | ★★ | |
| 2021-01-19 07:04:55 | Researchers Discover Raindrop - 4th Malware Linked to the SolarWinds Attack (lien direct) | Cybersecurity researchers have unearthed a fourth new malware strain-designed to spread the malware onto other computers in victims' networks-which was deployed as part of the SolarWinds supply chain attack disclosed late last year.
Dubbed "Raindrop" by Broadcom-owned Symantec, the malware joins the likes of other malicious implants such as Sunspot, Sunburst (or Solorigate), and Teardrop that |
Malware Mobile | Solardwinds Solardwinds | ||
| 2021-01-12 12:32:07 | Potential Link between SolarWinds and Turla APT (lien direct) | Researchers at Kaspersky have recently discovered considerable similarities between the Sunburst and Kazuar backdoors. The similarities potentially link the Sunburst backdoors, used in the SolarWinds supply-chain attack, to a previously known Turla weapon. Kazuar, a malware written using the .NET framework, was first reported in 2017. These have been used in unison throughout various breaches […] | Malware Mobile | Solardwinds Solardwinds | ||
| 2021-01-12 11:25:00 | Third Malware Strain Discovered as Part of SolarWinds Attack (lien direct) | Sunspot used to inject Sunburst into Orion platform, says CrowdStrike | Malware Mobile | Solardwinds Solardwinds | ||
| 2021-01-11 22:29:57 | Unveiled: SUNSPOT Malware Was Used to Inject SolarWinds Backdoor (lien direct) | As the investigation into the SolarWinds supply-chain attack continues, cybersecurity researchers have disclosed a third malware strain that was deployed into the build environment to inject the backdoor into the company's Orion network monitoring platform.
Called "Sunspot," the malignant tool adds to a growing list of previously disclosed malicious software such as Sunburst and Teardrop.
"This |
Malware Tool Mobile | Solardwinds Solardwinds | ||
| 2021-01-11 21:37:06 | Connecting the dots between SolarWinds and Russia-linked Turla APT (lien direct) | Experts have found some similarities between the Sunburst backdoor used in the SolarWinds supply chain attack and Turla’s backdoor Kazuar. Security experts from Kaspersky have identified multiple similarities between the Sunburst malware used in the SolarWinds supply chain attack and the Kazuar backdoor that has been employed in cyber espionage campaigns conducted by Russia-linked APT group Turla. The discovery […] | Malware Mobile | Solardwinds Solardwinds | ||
| 2021-01-11 17:53:21 | SolarWinds Hack Potentially Linked to Turla APT (lien direct) | Researchers have spotted notable code overlap between the Sunburst backdoor and a known Turla weapon. | Hack Mobile | Solardwinds Solardwinds | ||
| 2021-01-11 13:47:16 | Malware Used in SolarWinds Attack Linked to Backdoor Attributed to Turla Cyberspies (lien direct) | Researchers have identified some similarities between the Sunburst malware used in the SolarWinds supply chain attack and Kazuar, a backdoor that appears to have been used by the Russia-linked cyber-espionage group known as Turla. | Malware Mobile | Solardwinds Solardwinds | ||
| 2021-01-11 12:19:03 | Sunburst – Les experts ont trouvé des liens entre l\'attaque de SolarWinds et le backdoor Kazuar (lien direct) | Le 13 décembre dernier, FireEye, Microsoft et SolarWinds découvraient dans leurs réseaux informatiques une attaque sophistiquée ciblant leur chaîne logistique. Cette attaque déployait alors un nouveau malware, jusqu'ici inconnu, " Sunburst ", utilisé contre les clients informatiques d'Orion de SolarWinds. The post Sunburst – Les experts ont trouvé des liens entre l'attaque de SolarWinds et le backdoor Kazuar first appeared on UnderNews. | Mobile | Solardwinds Solardwinds | ||
| 2021-01-11 10:00:00 | Sunburst backdoor – code overlaps with Kazuar (lien direct) | While looking at the Sunburst backdoor, we discovered several features that overlap with a previously identified backdoor known as Kazuar. Our observations shows that Kazuar was used together with Turla tools during multiple breaches in past years. | Mobile | Solardwinds Solardwinds | ||
| 2021-01-11 09:07:54 | Sunburst backdoor shares features with Russian APT malware (lien direct) | Kaspersky researchers found that the Sunburst backdoor, the malware deployed during the SolarWinds supply-chain attack, shows feature overlaps with Kazuar, a .NET backdoor tentatively linked to the Russian Turla hacking group. [...] | Malware Mobile | Solardwinds Solardwinds | ||
| 2021-01-04 11:00:50 | Our New Year\'s Resolution for You: Protect Your IoT Networks and Devices! (lien direct) | By, Mitch Muro, Product Marketing Manager Can 2020 just be over yet?! I mean, come on. Not only have we been struck with one of the most sophisticated and severe attacks seen to date (which of course is the Generation V SolarWinds Sunburst Attack), but cyber criminals are even taking advantage of the increase in… | Mobile | Solardwinds Solardwinds | ||
| 2020-12-29 21:55:38 | SolarWinds hackers aimed at access to victims\' cloud assets (lien direct) | Microsoft says that SolarWinds hackers aimed at compromising the victims’ cloud infrastructure after deploying the Solorigate backdoor (aka Sunburst). The Microsoft 365 Defender Team revealed that the goal of the threat actors behind the SolarWinds supply chain attack was to move to the victims’ cloud infrastructure once infected their network with the Sunburst/Solorigate backdoor. “With […] | Threat Mobile | Solardwinds | ||
| 2020-12-29 21:22:00 | Actionable Threat Intelligence Available for Sunburst Cyber Attacks on SolarWinds (lien direct) | On Dec. 13, FireEye published a detailed analysis about the attack carried out against SolarWinds, which appears to have compromised its Orion IT monitoring and management platform to spread the Sunburst Backdoor malware. As part of the attack, which started in March, the Orion platform started sending out the digitally-signed trojanized malware via regular updates. According to SolarWinds, the compromised update may have been installed by fewer than 18,000 of its customers, including many U.S. federal agencies and Fortune 500 firms that use Orion to monitor the health of their IT networks. In a related blog post, FireEye also announced that a highly sophisticated state-sponsored adversary penetrated its network and stole FireEye Red Team tools used to test customers’ security. In response to the attacks, Anomali has collected, curated, and distributed clear and concise open-source intelligence (OSINT) to help organizations determine if they have been impacted. Two key resources released include a SolarWinds Breach Threat Bulletin and a FireEye Red Team Tools Breach Threat Bulletin. These continually updated resources, for use inside Anomali ThreatStream, include threat analysis, signature threat models, and over 2,000 operationalized indicators of compromise (IOCs) for automated distribution to security controls. Both are available now to Anomali’s 1,500 customers. What Can I Do with This Threat Intelligence?...and How to Do It Our intent in aggregating and curating this threat intelligence is to provide organizations with high-fidelity IOCs that can immediately be pushed into their security stacks for rapid, proactive blocking and alerting. Security products that can take advantage of this actionable threat intelligence include security information and event management (SIEM), endpoint detection and response platforms, firewalls, domain name system (DNS) servers, security orchestration, automation, and response (SOAR) platforms, and other operational security products. These Anomali threat bulletins are designed to be used in conjunction with Anomali ThreatStream, a threat intelligence platform that allows organizations to aggregate, curate, analyze, and distribute multiple sources of threat intelligence to their operational security systems. Inside of the SolarWinds Breach Threat Bulletin, all of these IOCs have been tagged with “solarwinds”, “sunburst backdoor”, “unc2452”, or “avsvmcloud.com.” This enables ThreatStream users to create a simple rule to automatically push IOCs to their security systems, enabling real-time defense against both attacks. For example, if a compromised server inside the organization attempts to connect to a command and control (C2) server outside of the organization, Anomali customers that have activated this research will automatically block the C2 URL, avoiding risk of further compromise and data exfiltration. How Can I Get This Intelligence? The Anomali SolarWinds and FireEye Threat Bulletins are automatically available to Anomali’s ThreatStream customers, and all organizations participating in Anomali-powered threat intelligence sharing communities (ISACs). Anomali Threat Research also created a | Malware Threat Mobile | Solardwinds Solardwinds | ||
| 2020-12-29 20:12:00 | Anomali ThreatStream Sunburst Backdoor Custom Dashboard Provides Machine Readable IOCs Related To SolarWinds Supply Chain Attack (lien direct) | SolarWinds, a provider of IT management and monitoring software deployed by thousands of global customers, was breached between March and June of 2020 by an Advanced Persistent Threat (APT) that cybersecurity company FireEye is tracking as UNC2452. As part of the supply chain attack, the APT compromised the company’s Orion business software with trojanized malware known as Sunburst, which opens a backdoor into the networks of customers who executed Orion updates.
Immediately following news of the attack, Anomali Threat Research launched a custom threat intelligence dashboard called Sunburst Backdoor. Now available to Anomali ThreatStream customers, the dashboard is accessible via the user console. It is preconfigured to provide immediate access and visibility into all known Sunburst Backdoor indicators of compromise (IOCs) that are made available through commercial and open-source threat feeds that users manage on ThreatStream.
Customers using ThreatStream, Anomali Match, and Anomali Lens can immediately detect any IOCs present in their environments, quickly consume threat bulletins containing machine readable IOCs to operationalize threat intelligence across their security infrastructures, and communicate to all stakeholders how they have been impacted.
As part of ongoing product enhancements that further automate and speed essential tasks performed by threat intelligence and security operations analysts, Anomali recently added thematic dashboards that respond to significant global events. In addition to Sunburst Backdoor, ThreatStream customers currently have access to additional dashboards announced as part of our December quarterly product release.
Customers can integrate Sunburst Backdoor and other dashboards via the “+ Add Dashboard” tab in the ThreatStream console:
 After integration, users will have immediate access to the Sunburst Backdoor dashboard, which continually updates IOCs as they become available:
After integration, users will have immediate access to the Sunburst Backdoor dashboard, which continually updates IOCs as they become available:
 Organizations interested in learning more about Anomali ThreatStream and our custom dashboard capabilities can request a demo here.
For organizations interested in gaining wider visibility and detection capabilities for the Sunburst cyberattack, Anomali Threat Research has compiled and curated an initial threat bulletin and downloadable set of OSINT IOCs available here.
Organizations interested in learning more about Anomali ThreatStream and our custom dashboard capabilities can request a demo here.
For organizations interested in gaining wider visibility and detection capabilities for the Sunburst cyberattack, Anomali Threat Research has compiled and curated an initial threat bulletin and downloadable set of OSINT IOCs available here. |
Malware Threat Mobile | Solardwinds Solardwinds | ||
| 2020-12-22 21:52:57 | Researchers shared the lists of victims of SolarWinds hack (lien direct) | Security experts shared lists of organizations that were infected with the SolarWinds Sunburst backdoor after decoding the DGA mechanism. Security experts started analyzing the DGA mechanism used by threat actors behind the SolarWinds hack to control the Sunburst/Solarigate backdoor and published the list of targeted organizations. Researchers from multiple cybersecurity firms published a list that […] | Hack Threat Mobile | Solardwinds Solardwinds | ||
| 2020-12-21 21:32:24 | (Déjà vu) How A Device to Cloud Architecture Defends Against the SolarWinds Supply Chain Compromise (lien direct) |  In a blog post released 13 Dec 2020, FireEye disclosed that threat actors compromised SolarWinds's Orion IT monitoring and management software with a trojanized version of SoalrWinds.Orion.Core.BusinessLayer.dll delivered as part of a digitally-signed Windows Installer Patch. The trojanized file delivers a backdoor, dubbed SUNBURST by FireEye (and Solorigate by Microsoft), that communicates to third-party servers for […]
In a blog post released 13 Dec 2020, FireEye disclosed that threat actors compromised SolarWinds's Orion IT monitoring and management software with a trojanized version of SoalrWinds.Orion.Core.BusinessLayer.dll delivered as part of a digitally-signed Windows Installer Patch. The trojanized file delivers a backdoor, dubbed SUNBURST by FireEye (and Solorigate by Microsoft), that communicates to third-party servers for […]
|
Threat Mobile | Solardwinds Solardwinds |
To see everything:
Our RSS (filtrered)
