What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-08-02 08:00:14 | Manjusaka: A Chinese sibling of Sliver and Cobalt Strike (lien direct) |  By Asheer Malhotra and Vitor Ventura.Cisco Talos recently discovered a new attack framework called "Manjusaka" being used in the wild that has the potential to become prevalent across the threat landscape. This framework is advertised as an imitation of the Cobalt Strike framework.The implants for the new malware family are written in the Rust language for Windows and Linux.A fully functional version of the command and control (C2), written in GoLang with a User Interface in Simplified Chinese, is freely available and can generate new implants with custom configurations with ease, increasing the likelihood of wider adoption of this framework by malicious actors.We recently discovered a campaign in the wild using lure documents themed around COVID-19 and the Haixi Mongol and Tibetan Autonomous Prefecture, Qinghai Province. These maldocs ultimately led to the delivery of Cobalt Strike beacons on infected endpoints.We have observed the same threat actor using the Cobalt Strike beacon and implants from the Manjusaka framework.IntroductionCisco Talos has discovered a relatively new attack framework called "Manjusaka" (which can be translated to "cow flower" from the Simplified Chinese writing) by their authors, being used in the wild.As defenders, it is important to keep track of offensive frameworks such as Cobalt Strike and Sliver so that enterprises can effectively defend against attacks employing these tools. Although we haven't observed widespread usage of this framework in the wild, it has the potential to be adopted by threat actors all over the world. This disclosure from Talos intends to provide early notification of the usage of Manjusaka. We also detail the framework's capabilities and the campaign that led to the discovery of this attack framework in the wild.The research started with a malicious Microsoft Word document (maldoc) that contained a Cobalt Strike (CS) beacon. The lure on this document mentioned a COVID-19 outbreak in Golmud City, one of the largest cities in the Haixi Mongol and Tibetan Autonomous Prefecture, Qinghai Province. During the investigation, Cisco Talos found no direct link between the campaign and the framework developers, aside from the usage of the framework (which is freely available on GitHub). However, we could not find any data that could support victimology definition. This is justifiable considering there's a low number of victims, indicating the early stages of the campaign, further supported by the maldoc metadata that indicates it was created in the second half of June 2022.While investigating the maldoc infection chain, we found an implant used to instrument Manjusaka infections, contacting the same IP address as the CS beacon. This implant is written in the Rust programming language and we found samples for Windows and Linux operating systems. The Windows implant included test samples, which had non-internet-routable IP addresses as command and control (C2). Talos also discovered the Manjusaka C2 executable - a fully functional C2 ELF binary written in GoLang with a User Interface in Simplified Chinese - on GitHub. While analyzing the C2, we generated implants by specifying our configurations. The developer advertises it has an advers By Asheer Malhotra and Vitor Ventura.Cisco Talos recently discovered a new attack framework called "Manjusaka" being used in the wild that has the potential to become prevalent across the threat landscape. This framework is advertised as an imitation of the Cobalt Strike framework.The implants for the new malware family are written in the Rust language for Windows and Linux.A fully functional version of the command and control (C2), written in GoLang with a User Interface in Simplified Chinese, is freely available and can generate new implants with custom configurations with ease, increasing the likelihood of wider adoption of this framework by malicious actors.We recently discovered a campaign in the wild using lure documents themed around COVID-19 and the Haixi Mongol and Tibetan Autonomous Prefecture, Qinghai Province. These maldocs ultimately led to the delivery of Cobalt Strike beacons on infected endpoints.We have observed the same threat actor using the Cobalt Strike beacon and implants from the Manjusaka framework.IntroductionCisco Talos has discovered a relatively new attack framework called "Manjusaka" (which can be translated to "cow flower" from the Simplified Chinese writing) by their authors, being used in the wild.As defenders, it is important to keep track of offensive frameworks such as Cobalt Strike and Sliver so that enterprises can effectively defend against attacks employing these tools. Although we haven't observed widespread usage of this framework in the wild, it has the potential to be adopted by threat actors all over the world. This disclosure from Talos intends to provide early notification of the usage of Manjusaka. We also detail the framework's capabilities and the campaign that led to the discovery of this attack framework in the wild.The research started with a malicious Microsoft Word document (maldoc) that contained a Cobalt Strike (CS) beacon. The lure on this document mentioned a COVID-19 outbreak in Golmud City, one of the largest cities in the Haixi Mongol and Tibetan Autonomous Prefecture, Qinghai Province. During the investigation, Cisco Talos found no direct link between the campaign and the framework developers, aside from the usage of the framework (which is freely available on GitHub). However, we could not find any data that could support victimology definition. This is justifiable considering there's a low number of victims, indicating the early stages of the campaign, further supported by the maldoc metadata that indicates it was created in the second half of June 2022.While investigating the maldoc infection chain, we found an implant used to instrument Manjusaka infections, contacting the same IP address as the CS beacon. This implant is written in the Rust programming language and we found samples for Windows and Linux operating systems. The Windows implant included test samples, which had non-internet-routable IP addresses as command and control (C2). Talos also discovered the Manjusaka C2 executable - a fully functional C2 ELF binary written in GoLang with a User Interface in Simplified Chinese - on GitHub. While analyzing the C2, we generated implants by specifying our configurations. The developer advertises it has an advers |
Malware Threat Guideline | APT 19 | ||
| 2022-08-01 12:18:19 | Vulnerability Spotlight: How misusing properly serialized data opened TCL LinkHub Mesh Wi-Fi system to 17 vulnerabilities (lien direct) |  By Carl Hurd. The TCL LinkHub Mesh Wi-Fi system is a multi-device Wi-Fi system that allows users to expand access to their network over a large physical area. What makes the LInkHub system unique is the lack of a network interface to manage the devices individually or in the mesh. Instead, a phone application is the only method to interact with these devices. This is noteworthy because, in theory, it significantly reduces the common attack surface on most small office/home office (SOHO) routers, as it moves the entire HTTP/S code base from the product. This means, in theory, fewer issues with integration or hacked-together scripts to trigger various functions within the device. One of the issues with this approach though is that its functionality still needs to reside somewhere for the user to manage the device. By Carl Hurd. The TCL LinkHub Mesh Wi-Fi system is a multi-device Wi-Fi system that allows users to expand access to their network over a large physical area. What makes the LInkHub system unique is the lack of a network interface to manage the devices individually or in the mesh. Instead, a phone application is the only method to interact with these devices. This is noteworthy because, in theory, it significantly reduces the common attack surface on most small office/home office (SOHO) routers, as it moves the entire HTTP/S code base from the product. This means, in theory, fewer issues with integration or hacked-together scripts to trigger various functions within the device. One of the issues with this approach though is that its functionality still needs to reside somewhere for the user to manage the device. |
Vulnerability | |||
| 2022-08-01 08:00:00 | Researcher Spotlight: You should have been listening to Lurene Grenier years ago (lien direct) | The exploit researcher recently rejoined Talos after starting her career with the company's predecessor By Jonathan Munshaw. Lurene Grenier says state-sponsored threat actors keep her up at night, even after years of studying and following them. She's spent her security career warning people why this was going to be a problem. Today if someone is compromised by a well-funded, state-sponsored actor, she is concerned but doesn't necessarily feel sorry. After all, she's been warning the security community about this for years. “You think about the phrase 'fool me once, shame on you...' Five years ago if we had this discussion and you were hit with an attack, you'd think 'shame on China,'” she said. “Today, if we have that discussion about why you were hit, it's shame on us.” Grenier has spent her career looking at state-sponsored actor trends and writing detection content to block those actors. She was one of the first of the smaller research staff at the Sourcefire Vulnerability Research Team, which eventually merged with a few other teams to form Talos. Matt Watchinski, who is now the vice president of Talos, initially hired Grenier as a vulnerability exploit researcher, doing the job of what more than a dozen people do today for Talos. Grenier looked at vulnerability details for regular patch cycles like Microsoft Patch Tuesday and write her own exploit code for the vulnerabilities, which eventually fed into detection content that would block attackers' attempts to target these issues in the wild. She grew with VRT, eventually overseeing the Analyst Team, which today is the main producer of detection content for Cisco Secure products and Snort. She eventually took a few other paths on her security journey outside of Cisco and Talos, but recently rejoined Talos as a special advisor to Watchinski, studying state-sponsored actors and major attacker trends using Talos' data and telemetry. “My main directive is to come up with plans for this mountain of data that we have,” Grenier said. “I look at the data that we do have and see what outcomes for customers we can achieve with it. Can we create something like a semi-autonomous mediation plan when there is a breach? Can we track actors in a more granular manner so we can match them with what we've seen in the past?” Even during her time away from Talos, Grenier never lost connection, speaking at two Talos Threat Research Summits that were a part of Cisco Live. In 2018, she even gave a presentation on how organizations were not taking threats from state-sponsored actors seriously enough and warned about the theft of intellectual property. Some of the same techniques and actors she warned about in that talk resurfaced earlier this year in a warning from federal agencies in the U.S. and the U.K., stating that Chinese state-sponsored actors were stealing important IP and creating fraudulent “tech transfer” agreements. While Grenier still tracks these same actors daily, she views their activity as more of an inevitability that's going to produce the worst-case scenario rather than anything that can be avoided at this point. “It's like earthquakes or famine, it's really just horrible,” she said. At this point, Grenier is focusing her work on how to make attacks as costly as possible for the adversary, rather than trying to avoid them altogether. If her research can help even slow down an actor for a bit or cost them more resources when they go to attack again, that's a small victory to build off. “People have to see the cost of these breaches,” she said. “And they're not going to see the inflection point for a while now, but it will eventually become very obvious.” Although she spent several years away from Talos, coming back to the organization (a few hundred mor | Vulnerability Threat Guideline | |||
| 2022-07-27 12:22:17 | Vulnerability Spotlight: How a code re-use issue led to vulnerabilities across multiple products (lien direct) |  By Francesco Benvenuto. Recently, I was performing some research on a wireless router and noticed the following piece of code: By Francesco Benvenuto. Recently, I was performing some research on a wireless router and noticed the following piece of code: |
Vulnerability Guideline Medical | APT 38 APT 19 | ||
| 2022-07-27 08:00:00 | What Talos Incident Response learned from a recent Qakbot attack hijacking old email threads (lien direct) |  By Nate Pors and Terryn Valikodath. Executive summary In a recent malspam campaign delivering the Qakbot banking trojan, Cisco Talos Incident Response (CTIR) observed the adversary using aggregated, old email threads from multiple organizations that we assess were likely harvested during the 2021 ProxyLogon-related compromises targeting vulnerable Microsoft Exchange servers. This campaign relies on external thread hijacking, whereby the adversary is likely using a bulk aggregation of multiple organizations' harvested emails to launch focused phishing campaigns against previously uncompromised organizations. This differs from the more common approach to thread hijacking, in which attackers use a single compromised organization's emails to deliver their threat. This many-to-one approach is unique from what we have generally observed in the past and is likely an indirect effect of the widespread compromises and exfiltration of large volumes of email from 2020 and 2021. Understanding the difference between external and single-victim thread hijacking is essential for detecting these threats. Below, we have several tips for defenders on how to identify key indicators of this activity. External thread hijacking Cisco Talos has observed threat actors using external thread hijacking, a method by which attackers weaponize emails previously harvested from other organizations. This differs from the more common approach to thread hijacking, in which adversaries compromise the victim organization's Exchange server to obtain email threads that are then weaponized. We recently observed this in June 2022 as part of a broader campaign that delivered the Qakbot banking trojan. In this threat activity, the attackers used old emails harvested months to years ago during the 2021 ProxyLogon campaign, tracked as CVE-2021-26855, targeting vulnerable Exchange servers. External thread hijacking is not dependent on the threat actor gaining initial access to the victim environment. This is notable from a digital forensics and incident response (DFIR) perspective because the target organization only saw inbound phishing emails with its own legitimate emails as the source material, with multiple external organizations represented in the email threads. Our assessment of the adversary's use of emails obtained from the ProxyLogon compromises is based on a number of observations, including the timing of the emails and research into publicly acknowledged ProxyLogon compromises. The attackers selectively used these emails to target senders or recipients from the target organization. In the external thread hijacking attack observed by CTIR, the adversary likely took the following steps: The attacker took control of multiple third-party organizations' Exchange servers or individual inboxes and exported emails for later use. The adversary selected the emails relevant to the target organization By Nate Pors and Terryn Valikodath. Executive summary In a recent malspam campaign delivering the Qakbot banking trojan, Cisco Talos Incident Response (CTIR) observed the adversary using aggregated, old email threads from multiple organizations that we assess were likely harvested during the 2021 ProxyLogon-related compromises targeting vulnerable Microsoft Exchange servers. This campaign relies on external thread hijacking, whereby the adversary is likely using a bulk aggregation of multiple organizations' harvested emails to launch focused phishing campaigns against previously uncompromised organizations. This differs from the more common approach to thread hijacking, in which attackers use a single compromised organization's emails to deliver their threat. This many-to-one approach is unique from what we have generally observed in the past and is likely an indirect effect of the widespread compromises and exfiltration of large volumes of email from 2020 and 2021. Understanding the difference between external and single-victim thread hijacking is essential for detecting these threats. Below, we have several tips for defenders on how to identify key indicators of this activity. External thread hijacking Cisco Talos has observed threat actors using external thread hijacking, a method by which attackers weaponize emails previously harvested from other organizations. This differs from the more common approach to thread hijacking, in which adversaries compromise the victim organization's Exchange server to obtain email threads that are then weaponized. We recently observed this in June 2022 as part of a broader campaign that delivered the Qakbot banking trojan. In this threat activity, the attackers used old emails harvested months to years ago during the 2021 ProxyLogon campaign, tracked as CVE-2021-26855, targeting vulnerable Exchange servers. External thread hijacking is not dependent on the threat actor gaining initial access to the victim environment. This is notable from a digital forensics and incident response (DFIR) perspective because the target organization only saw inbound phishing emails with its own legitimate emails as the source material, with multiple external organizations represented in the email threads. Our assessment of the adversary's use of emails obtained from the ProxyLogon compromises is based on a number of observations, including the timing of the emails and research into publicly acknowledged ProxyLogon compromises. The attackers selectively used these emails to target senders or recipients from the target organization. In the external thread hijacking attack observed by CTIR, the adversary likely took the following steps: The attacker took control of multiple third-party organizations' Exchange servers or individual inboxes and exported emails for later use. The adversary selected the emails relevant to the target organization |
Malware Threat | |||
| 2022-07-26 10:11:15 | Quarterly Report: Incident Response Trends in Q2 2022 (lien direct) | Commodity malware usage surpasses ransomware by narrow margin  By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. 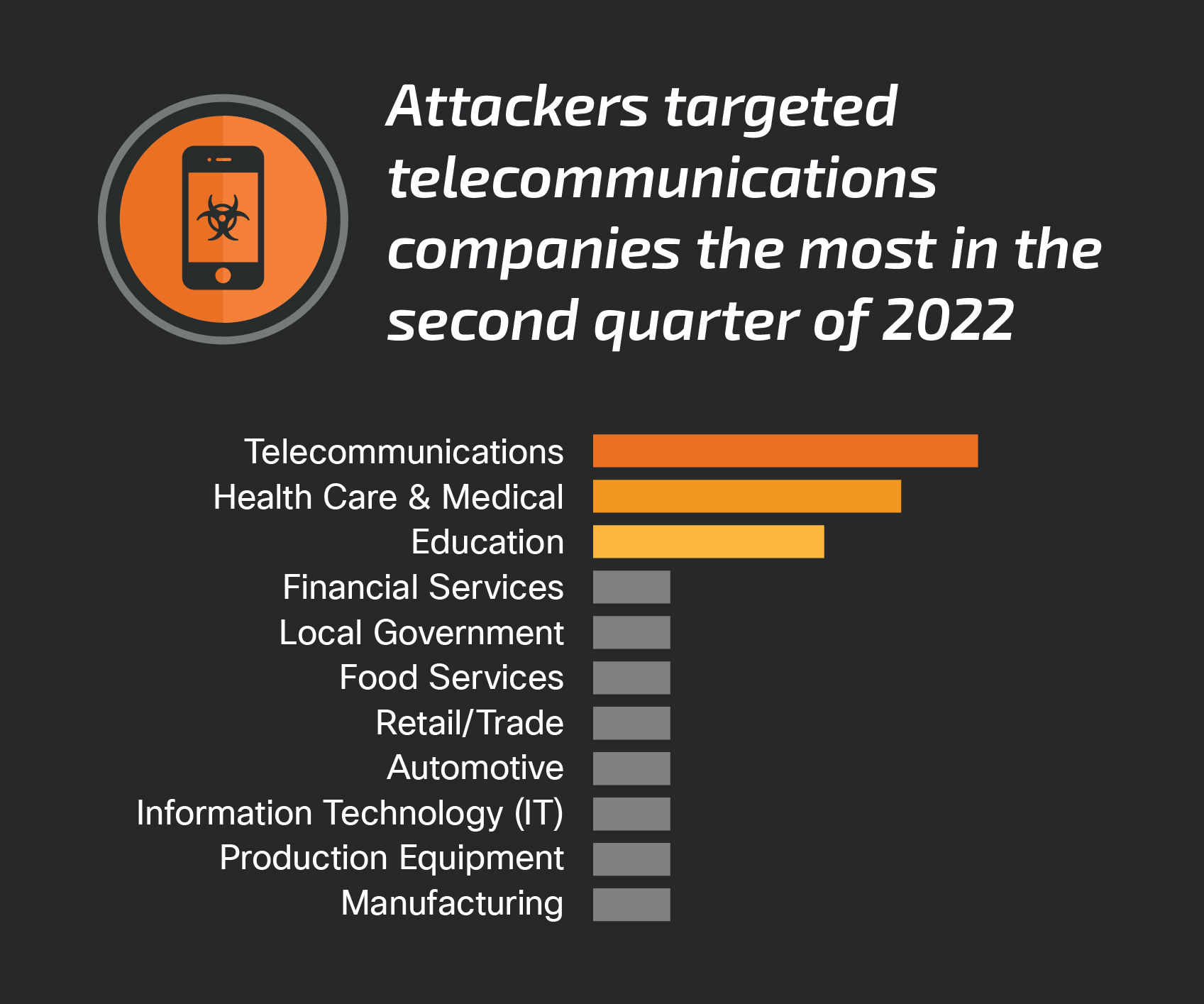 Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity |
Ransomware Spam Malware Threat | |||
| 2022-07-21 08:00:05 | Attackers target Ukraine using GoMet backdoor (lien direct) |  Executive summarySince the Russian invasion of Ukraine began, Ukrainians have been under a nearly constant barrage of cyber attacks. Working jointly with Ukrainian organizations, Cisco Talos has discovered a fairly uncommon piece of malware targeting Ukraine - this time aimed at a large software development company whose software is used in various state organizations within Ukraine. We believe that this campaign is likely sourced by Russian state-sponsored actors or those acting in their interests. As this firm is involved in software development, we cannot ignore the possibility that the perpetrating threat actor's intent was to gain access to source a supply chain-style attack, though at this time we do not have any evidence that they were successful. Cisco Talos confirmed that the malware is a slightly modified version of the open-source backdoor named "GoMet." The malware was first observed on March 28, 2022. GoMet backdoorThe story of this backdoor is rather curious - there are two documented cases of its usage by sophisticated threat actors. First, in 2020, attackers were deploying this malware after the successful exploitation of CVE-2020-5902, a vulnerability in F5 BIG-IP so severe that USCYBERCOM posted a tweet urging all users to patch the application. The second is more recent and involved the successful exploitation of CVE-2022-1040, a remote code execution vulnerability in Sophos Firewall. Both cases are very similar. They both start with the exploitation of a public vulnerability on appliances where the malicious actors then dropped GoMet as a backdoor. As of publishing time, Cisco Talos has no reason to believe these cases are related to the usage of this backdoor in Ukraine. The original GoMet author posted the code on GitHub on March 31, 2019 and had commits until April 2, 2019. The commits didn't add any features but did fix some code convention aesthetics. The backdoor itself is a rather simple piece of software written in the Go programming language. It contains nearly all the usual functions an attacker might want in a remotely controlled agent. Agents can be deployed on a variety of operating systems (OS) or architectures (amd64, arm, etc.). GoMet supports job scheduling (via Cron or task scheduler depending on the OS), single command execution, file download, file upload or opening a shell. An additional notable feature of GoMet lies in its ability to daisy chain - whereby the attackers gain access to a network or machine and then use that same information to gain access to multiple networks and computers - connections from one implanted host to another. Such a feature could allow for communication out to the internet from otherwise completely "isolated" hosts.This version was changed by malicious actors, in the original code, the cronjob is configured to be executed once every hour on the hour. In our samples, the cronjob is configured to run every two seconds. This change makes the sample slightly more noisy since it executes every two seconds, but also prevents an hour-long sleep if the connection fails which would Executive summarySince the Russian invasion of Ukraine began, Ukrainians have been under a nearly constant barrage of cyber attacks. Working jointly with Ukrainian organizations, Cisco Talos has discovered a fairly uncommon piece of malware targeting Ukraine - this time aimed at a large software development company whose software is used in various state organizations within Ukraine. We believe that this campaign is likely sourced by Russian state-sponsored actors or those acting in their interests. As this firm is involved in software development, we cannot ignore the possibility that the perpetrating threat actor's intent was to gain access to source a supply chain-style attack, though at this time we do not have any evidence that they were successful. Cisco Talos confirmed that the malware is a slightly modified version of the open-source backdoor named "GoMet." The malware was first observed on March 28, 2022. GoMet backdoorThe story of this backdoor is rather curious - there are two documented cases of its usage by sophisticated threat actors. First, in 2020, attackers were deploying this malware after the successful exploitation of CVE-2020-5902, a vulnerability in F5 BIG-IP so severe that USCYBERCOM posted a tweet urging all users to patch the application. The second is more recent and involved the successful exploitation of CVE-2022-1040, a remote code execution vulnerability in Sophos Firewall. Both cases are very similar. They both start with the exploitation of a public vulnerability on appliances where the malicious actors then dropped GoMet as a backdoor. As of publishing time, Cisco Talos has no reason to believe these cases are related to the usage of this backdoor in Ukraine. The original GoMet author posted the code on GitHub on March 31, 2019 and had commits until April 2, 2019. The commits didn't add any features but did fix some code convention aesthetics. The backdoor itself is a rather simple piece of software written in the Go programming language. It contains nearly all the usual functions an attacker might want in a remotely controlled agent. Agents can be deployed on a variety of operating systems (OS) or architectures (amd64, arm, etc.). GoMet supports job scheduling (via Cron or task scheduler depending on the OS), single command execution, file download, file upload or opening a shell. An additional notable feature of GoMet lies in its ability to daisy chain - whereby the attackers gain access to a network or machine and then use that same information to gain access to multiple networks and computers - connections from one implanted host to another. Such a feature could allow for communication out to the internet from otherwise completely "isolated" hosts.This version was changed by malicious actors, in the original code, the cronjob is configured to be executed once every hour on the hour. In our samples, the cronjob is configured to run every two seconds. This change makes the sample slightly more noisy since it executes every two seconds, but also prevents an hour-long sleep if the connection fails which would |
Malware Vulnerability Threat | |||
| 2022-07-19 08:45:52 | (Déjà vu) Vulnerability Spotlight: Issue in Accusoft ImageGear could lead to memory corruption, code execution (lien direct) |  Emmanuel Tacheau of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered a use-after-free vulnerability in Accusoft ImageGear's PSD header processing function. The ImageGear library is a document-imaging developer toolkit that allows users to create, edit, annotate and convert various images. It supports more than 100 file formats such as DICOM, PDF and Microsoft Office. This vulnerability, TALOS-2022-1526 (CVE-2022-29465) could allow an attacker to cause a use-after-free condition by tricking the targeted user into opening a malformed .psd file in the application. The vulnerability leads to out-of-bounds heap writes, which causes memory corruption and, possibly, code execution. In adherence to Cisco's vulnerability disclosure policy, Accusoft patched this issue and released an update for ImageGear.Talos tested and confirmed Accusoft ImageGear, version 19.10, is affected by this vulnerability. Emmanuel Tacheau of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered a use-after-free vulnerability in Accusoft ImageGear's PSD header processing function. The ImageGear library is a document-imaging developer toolkit that allows users to create, edit, annotate and convert various images. It supports more than 100 file formats such as DICOM, PDF and Microsoft Office. This vulnerability, TALOS-2022-1526 (CVE-2022-29465) could allow an attacker to cause a use-after-free condition by tricking the targeted user into opening a malformed .psd file in the application. The vulnerability leads to out-of-bounds heap writes, which causes memory corruption and, possibly, code execution. In adherence to Cisco's vulnerability disclosure policy, Accusoft patched this issue and released an update for ImageGear.Talos tested and confirmed Accusoft ImageGear, version 19.10, is affected by this vulnerability. |
Vulnerability Guideline | |||
| 2022-07-15 06:37:07 | EMEAR Monthly Talos Update: Training the next generation of cybersecurity researchers (lien direct) | Cisco Talos and Cisco Secure have the latest edition of the Talos EMEAR Threat Update series out now, which you can watch above or over at this link, where Martin Lee and Hazel Burton talk about the cybersecurity skills gap that currently exists and how we can better train the next generation... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-07-14 06:24:52 | Vulnerability Spotlight: Use-after-free condition in Google Chrome WebGPU (lien direct) | Piotr Bania of Cisco Talos discovered this vulnerability. Blog by Jon Munshaw. Cisco Talos recently discovered an exploitable use-after-free vulnerability in Google Chrome's WebGPU standard. Google Chrome is a cross-platform web browser - and Chromium is the open-source version of... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Vulnerability | |||
| 2022-07-13 16:08:15 | Transparent Tribe begins targeting education sector in latest campaign (lien direct) | Cisco Talos has been tracking a new malicious campaign operated by the Transparent Tribe APT group.This campaign involves the targeting of educational institutions and students in the Indian subcontinent, a deviation from the adversary's typical focus on government entities.The attacks result in... [[ This is only the beginning! Please visit the blog for the complete entry ]] | APT 36 | |||
| 2022-07-13 07:49:24 | Vulnerability Spotlight: Adobe Acrobat DC use-after-free issue could lead to arbitrary code execution (lien direct) | Aleksandar Nikolic of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered two use-after-free vulnerabilities in Adobe Acrobat Reader DC that could allow an attacker to eventually gain the ability to execute arbitrary code. Acrobat is... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-07-12 09:33:37 | Microsoft Patch Tuesday for July 2022 - Snort rules and prominent vulnerabilities (lien direct) | By Jon Munshaw and Tiago Pereira. Microsoft released its monthly security update Tuesday, disclosing more than 80 vulnerabilities in the company's various software, hardware and firmware offerings, including one that's actively being exploited in the wild. July's security update... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-07-08 11:27:26 | (Déjà vu) Threat Roundup for July 1 to July 8 (lien direct) | Today, Talos is publishing a glimpse into the most prevalent threats we've observed between July 1 and July 8. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-07-07 10:00:00 | Threat Source newsletter (July 7, 2022) - Teamwork makes the dream work (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. I've been thinking a lot recently about the pros and cons of the way we publicize our threat research. I had a few conversations at Cisco Live with people - who are more generally IT-focused than... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-07-05 04:00:00 | Researcher Spotlight: Around the security world and back again with Nick Biasini (lien direct) | By Jon Munshaw. Nick Biasini's seen it all. Going on a nearly 20-year security career, he's been a part of some of Cisco Talos' largest undertakings in the company's history. From an attack on the global Olympic Games, to a wireless router malware that affected hundreds of... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | |||
| 2022-06-30 10:00:00 | Threat Source newsletter (June 30, 2022) - AI voice cloning is somehow more scary than deepfake videos (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. We took a week off for summer vacation but are back in the thick of security things now. My first exposure to deepfake videos was when Jordan Peele worked with BuzzFeed News to produce this video of... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-06-30 09:41:18 | Vulnerability Spotlight: Command injection vulnerabilities in Robustel cellular router (lien direct) | Lilith >_> of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered four vulnerabilities in the Robustel R1510 industrial cellular router. The R1510 is a portable router that shares 2G, 3G and 4G wireless internet access. It comes with... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-06-28 04:00:00 | De-anonymizing ransomware domains on the dark web (lien direct) | By Paul Eubanks. We have developed three techniques to identify ransomware operators' dark websites hosted on public IP addresses, allowing us to uncover previously unknown infrastructure for the DarkAngels, Snatch, Quantum and Nokoyawa ransomware groups.The methods we used to identify the public... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2022-06-24 13:59:06 | (Déjà vu) Threat Roundup for June 17 to June 24 (lien direct) | Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 17 and June 24. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-06-21 03:59:59 | Avos ransomware group expands with new attack arsenal (lien direct) | By Flavio Costa, Chris Neal and Guilherme Venere. In a recent customer engagement, we observed a month-long AvosLocker campaign. The attackers utilized several different tools, including Cobalt Strike, Sliver and multiple commercial network scanners. The initial ingress point in this incident was... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2022-06-17 13:57:36 | (Déjà vu) Threat Roundup for June 10 to June 17 (lien direct) | Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 10 and June 17. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-06-16 10:00:00 | Threat Source newsletter (June 16, 2022) - Three top takeaways from Cisco Live (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. I'm still decompressing from Cisco Live and the most human interaction I've had in a year and a half. But after spending a few days on the show floor and interacting with everyone, there are a... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-06-15 11:14:49 | Vulnerability Spotlight: Vulnerabilities in Anker Eufy Homebase could lead to code execution, authentication bypass (lien direct) | Lilith >_> of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered three vulnerabilities in the Anker Eufy Homebase 2. The Eufy Homebase 2 is the video storage and networking gateway that works with Anker's Eufy Smarthome ecosystem.... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-06-14 10:47:50 | Microsoft Patch Tuesday for June 2022 - Snort rules and prominent vulnerabilities (lien direct) | By Chetan Raghuprasad. Microsoft released its monthly security update Tuesday, disclosing 55 vulnerabilities in the company's firmware and software. One of these vulnerabilities is considered critical, 40 are listed as high severity, and the remainder is considered "moderate." The most... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-06-09 10:06:57 | Threat Source newsletter (June 9, 2022) - Get ready for Cisco Live (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. Another week, another conference. We're heading a few miles southeast from San Francisco to Las Vegas for Cisco Live. I hope everyone had a safe, healthy and enjoyable RSA, but the fun isn't over just... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-06-09 04:16:12 | Talos EMEA monthly update: Business email compromise (lien direct) | The latest edition of the Talos EMEA Monthly Update is available now on Cisco.com and Cisco's YouTube page. You can also view the episode in its entirety above. For June, Hazel and Martin got together to discuss business email compromise. BEC has quickly become the most lucrative attack vector for... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-06-03 16:08:10 | Threat Advisory: Atlassian Confluence zero-day vulnerability under active exploitation (lien direct) | Cisco Talos is monitoring reports of an actively exploited zero-day vulnerability in Confluence Data Center and Server. Confluence is a Java-based corporate Wiki employed by numerous enterprises. At this time, it is confirmed that all supported versions of Confluence are affected by this... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Vulnerability | |||
| 2022-06-03 11:07:29 | (Déjà vu) Threat Roundup for May 27 to June 3 (lien direct) | Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 27 and June 3. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-06-02 10:00:00 | Threat Source newsletter (June 2, 2022) - An RSA Conference primer (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. Many of you readers may be gearing up for a West Coast swing over the next few weeks through San Francisco and Las Vegas for RSA and Cisco Live, respectively. And we're right behind you! Talos... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-06-01 06:40:40 | Threat Advisory: Zero-day vulnerability in Microsoft diagnostic tool MSDT could lead to code execution (lien direct) | A recently discovered zero-day vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT) made headlines over the past few days. CVE-2022-30190, also known under the name "Follina," exists when MSDT is called using the URL protocol from an application, such as Microsoft Office, Microsoft... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Tool Vulnerability | |||
| 2022-05-31 05:00:00 | Researcher Spotlight: Martin Lee, EMEAR lead, Talos Strategic Communications (lien direct) | Who knew you could connect Moses to threat intelligence? By Jon Munshaw. When the security community usually thinks about the origins of cybersecurity and threat intelligence, the conversation may quickly center around the codebreakers in World War II or the Creeper software developed... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-05-27 12:38:24 | (Déjà vu) Threat Roundup for May 20 to May 27 (lien direct) | Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 20 and May 27. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-05-26 10:00:00 | Threat Source newsletter (May 26, 2022) - BlackByte adds itself to the grocery list of big game hunters (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. Given the recent tragedies in the U.S., I don't feel it's appropriate to open by being nostalgic or trying to be witty - let's just stick to some security news this week. The one big... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-05-25 07:18:30 | Vulnerability Spotlight: Vulnerabilities in Open Automation Software Platform could lead to information disclosure, denial of service (lien direct) | Jared Rittle of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered eight vulnerabilities in the Open Automation Software Platform that could allow an adversary to carry out a variety of malicious actions, including improperly authenticating into... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-05-20 10:26:05 | (Déjà vu) Threat Roundup for May 13 to May 20 (lien direct) | Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 13 and May 20. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-05-19 10:00:00 | Threat Source newsletter (May 19, 2022) - Why I\'m missing the days of iPods and LimeWire (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. I will openly admit that I still own a “classic” iPod - the giant brick that weighed down my skinny jeans in high school and did nothing except play music. There are dozens of hours of music on there that I... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-05-18 04:04:21 | The BlackByte ransomware group is striking users all over the globe (lien direct) | News summary Cisco Talos has been monitoring the BlackByte Ransomware Group for several months, infecting victims all over the world, from North America to Colombia, Netherlands, China, Mexico and Vietnam.The FBI released a joint cybersecurity advisory in February 2022 warning about... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2022-05-17 06:55:04 | Vulnerability Spotlight: Multiple memory corruption vulnerabilities in NVIDIA GPU driver (lien direct) | Piotr Bania of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered four vulnerabilities in the NVIDIA D3D10 driver for graphics cards that could allow an attacker to corrupt memory and write arbitrary memory on the card. NVIDIA graphics... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-05-13 12:04:28 | (Déjà vu) Threat Roundup for May 6 to May 13 (lien direct) | Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 6 and May 13. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-05-13 05:00:00 | EMEAR Monthly Talos Update: Wiper malware (lien direct) | Cisco Talos and Cisco Secure are launching a new video series to fill you in on the latest cybersecurity trends. We're thrilled to launch our first video in the new Talos Threat Update series, which you can watch above or over at this link, where Martin Lee and Hazel Burton talk about wiper... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware Threat | |||
| 2022-05-12 11:00:00 | (Déjà vu) Threat Source newsletter (May 12, 2022) - Mandatory MFA adoption is great, but is it too late? (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. Mandatory multi-factor authentication is all the rage nowadays. GitHub just announced that all contributors would have to enroll in MFA by 2023 to log into their accounts. And Google announced as part of... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | ★★★ | ||
| 2022-05-12 10:00:00 | Threat Source newsletter (May 12, 2022) - Mandatory MFA adoption is great, but is it too late? (lien direct) | By Jon Munshaw. Welcome to this week's edition of the Threat Source newsletter. Mandatory multi-factor authentication is all the rage nowadays. GitHub just announced that all contributors would have to enroll in MFA by 2023 to log into their accounts. And Google announced as part of... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | |||
| 2022-05-12 05:00:00 | (Déjà vu) Vulnerability Spotlight: How an attacker could chain several vulnerabilities in an industrial wireless router to gain root access (lien direct) | Francesco Benvenuto of Cisco Talos discovered these vulnerabilities. Blog by Francesco Benvenuto and Jon Munshaw. Cisco Talos recently discovered several vulnerabilities in InHand Networks' InRouter302 that could allow an attacker to escalate their privileges on the targeted device from a... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ★★★ | |||
| 2022-05-12 04:00:00 | Vulnerability Spotlight: How an attacker could chain several vulnerabilities in an industrial wireless router to gain root access (lien direct) | Francesco Benvenuto of Cisco Talos discovered these vulnerabilities. Blog by Francesco Benvenuto and Jon Munshaw. Cisco Talos recently discovered several vulnerabilities in InHand Networks' InRouter302 that could allow an attacker to escalate their privileges on the targeted device from a... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-05-11 05:00:11 | Bitter APT adds Bangladesh to their targets (lien direct) | Cisco Talos has observed an ongoing malicious campaign since August 2021 from the Bitter APT group that appears to target users in Bangladesh, a change from the attackers' usual victims.As part of this, there's a new trojan based on Apost Talos is calling "ZxxZ," that, among other... [[ This is only the beginning! Please visit the blog for the complete entry ]] | ||||
| 2022-05-10 12:31:53 | Microsoft Patch Tuesday for May 2022 - Snort rules and prominent vulnerabilities (lien direct) | By Jon Munshaw, with contributions from Jaeson Schultz. Microsoft returned to its normal monthly patching volume in May, disclosing and fixing 74 vulnerabilities as part of the company's latest security update. This month's Patch Tuesday includes seven critical vulnerabilities after Microsoft... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Patching | ★★★★ | ||
| 2022-05-10 12:07:30 | Talos Incident Response added to German BSI Advanced Persistent Threat response list (lien direct) | Cisco Talos Incident Response is now listed as an approved vendor on the Bundesamt für Sicherheit in der Informationstechnik (BSI) Advanced Persistent Threat (APT) response service providers list. Talos Incident Response successfully demonstrated to the BSI, through a review of our processes and a... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat | ★★★ | ||
| 2022-05-10 09:24:11 | Threat Advisory: Critical F5 BIG-IP Vulnerability (lien direct) | Summary A recently disclosed vulnerability in F5 Networks' BIG-IP could allow an unauthenticated attacker to access the BIG-IP system to execute arbitrary system commands, create and delete files, disable services and could lead to additional malicious activity. This vulnerability, tracked as... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Vulnerability Guideline | ★★★★ | ||
| 2022-05-10 07:20:09 | Vulnerability Spotlight: Vulnerability in Alyac antivirus program could stop virus scanning, cause denial of service (lien direct) | Jaewon Min of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered an out-of-bounds read vulnerability in the ESTsecurity Corp.'s Alyac antivirus software that could cause a denial-of-service condition. If successful, an attacker could... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Vulnerability | ★★★★ |
To see everything:
Our RSS (filtrered)
