What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-10-31 18:59:51 | Researcher Spotlight: How Azim Khodjibaev went from hunting real-world threats to threats on the dark web (lien direct) | Most of the time, Khodjibaev is combing through various dark web forums, ransomware group chats, Russian-speaking websites and other sources trying to learn of attackers' next moves. | Ransomware | |||
| 2022-10-25 08:00:00 | Quarterly Report: Incident Response Trends in Q3 2022 (lien direct) |  Ransomware and pre-ransomware engagements make up 40 percent of threats seen this quarterBy Caitlin Huey.For the first time since compiling these reports, Cisco Talos Incident Response saw an equal number of ransomware and pre-ransomware engagements, making up nearly 40 percent of threats this quarter. It can be difficult to determine what constitutes a pre-ransomware attack if ransomware never executes and encryption does not take place. However, Talos IR assesses that the combination of Cobalt Strike and credential-harvesting tools like Mimikatz, paired with enumeration and discovery techniques, indicates a high likelihood that ransomware is the final objective. Ransomware and pre-ransomware engagements make up 40 percent of threats seen this quarterBy Caitlin Huey.For the first time since compiling these reports, Cisco Talos Incident Response saw an equal number of ransomware and pre-ransomware engagements, making up nearly 40 percent of threats this quarter. It can be difficult to determine what constitutes a pre-ransomware attack if ransomware never executes and encryption does not take place. However, Talos IR assesses that the combination of Cobalt Strike and credential-harvesting tools like Mimikatz, paired with enumeration and discovery techniques, indicates a high likelihood that ransomware is the final objective..jpg) TargetingAttackers targeted the education sector the most of any vertical this quarter, closely followed by the financial services, government, and energy sectors, respectively. For the first time since Q4 2021, telecommunications was not the top-targeted vertical. While the reason for the education sector being more frequently targeted this quarter is unknown, this is a popular time TargetingAttackers targeted the education sector the most of any vertical this quarter, closely followed by the financial services, government, and energy sectors, respectively. For the first time since Q4 2021, telecommunications was not the top-targeted vertical. While the reason for the education sector being more frequently targeted this quarter is unknown, this is a popular time |
Threat Ransomware Guideline Tool Vulnerability | |||
| 2022-10-03 12:40:56 | Researcher Spotlight: Globetrotting with Yuri Kramarz (lien direct) | From the World Cup in Qatar to robotics manufacturing in east Asia, this incident responder combines experience from multiple arenas By Jon Munshaw. Yuri “Jerzy” Kramarz helped secure everything from the businesses supporting the upcoming World Cup in Qatar to the Black Hat security conference and critical national infrastructure. He's no stranger to cybersecurity on the big stage, but he still enjoys working with companies and organizations of all sizes in all parts of the world. “What really excites me is making companies more secure,” he said in a recent interview. “That comes down to a couple things, but it's really about putting a few solutions together at first and then hearing the customer's feedback and building from there.” Yuri is a senior incident response consultant with Cisco Talos Incident Response (CTIR) currently based in Qatar. He walks customers through various exercises, incident response plan creation, recovery in the event of a cyber attack and much more under the suite of offerings CTIR has. Since moving from the UK to Qatar, he is mainly focused on preparing various local entities in Qatar for the World Cup slated to begin in November. Qatar estimates more than 1.7 million people will visit the country for the international soccer tournament, averaging 500,000 per day at various stadiums and event venues. For reference, the World Bank estimates that 2.9 million people currently live in Qatar. This means the businesses and networks in the country will face more traffic than ever and will no doubt draw the attention of bad actors looking to make a statement or make money off ransomware attacks. “You have completely different angles in preparing different customers for defense during major global events depending on their role, technology and function,” Kramarz said. In every major event, there were different devices, systems and networks interconnected to provide visitors and fans with various hospitality facilities that could be targeted in a cyber attack. Any country participating in the event needs to make sure they understand the risks associated with it and consider various adversary activities that might play out to secure these facilities. Kramarz has worked in several different geographic areas in his roughly 12-year security career, including Asia, the Middle East, Europe and the U.S. He has experience leading red team engagements (simulating attacks against targets to find potential security weaknesses) in traditional IT and ICS/OT environments, vulnerability research and blue team defense. The incident response field has been the perfect place for him to put all these skills to use.  He joined Portcullis Securit He joined Portcullis Securit |
Ransomware Hack Guideline Vulnerability | |||
| 2022-09-07 11:00:19 | Multiple ransomware data leak sites experience DDoS attacks, facing intermittent outages and connectivity issues (lien direct) |  By Azim Khodjibaev, Colin Grady, Paul Eubanks.Since Aug. 20, 2022, Cisco Talos has been monitoring suspected distributed denial-of-service (DDoS) attacks resulting in intermittent downtime and outages affecting several ransomware-as-a-service (RaaS) data leak sites. While the source and origin of this activity remain unknown, this appears to be a concentrated effort against RaaS leak sites to disrupt their efforts to announce and post new victim information.Actors' responses have varied, with LockBit and ALPHV implementing new measures to counteract DDoS attacks against their sites while other groups like Quantum have simply resorted to redirecting web traffic elsewhere. LockBit also appears to have co-opted this technique by advertising that they are now adding DDoS as an extortion tactic in addition to encrypting and leaking data.RaaS leak sites experience intermittent outagesIn late August, Talos became aware of several prominent ransomware operations, such as ALPHV (also referred to as BlackCat) and LockBit, experiencing suspected DDoS attacks against their public data leak sites. These leak sites are typically hosted on Tor hidden services where, in a tactic known as double extortion, RaaS affiliates post victim information if the ransom demand is not met. On Aug. 26, we also observed at least seven more RaaS leak sites for LV, Hive, Everest, BianLian, Yanluowang, Snatch and Lorenz become inaccessible and go offline intermittently and/or experience slow traffic. Security researchers have also identified additional RaaS leak sites for Ragnar Locker and Vice Society which may have also been affected by this activity. However, we have only verified the Ragnar Locker claim at this time, as their leak site continues to experience outages. At the time of analysis, many of the aforementioned groups are still affected by connectivity issues and continue to face a variety of intermittent outages to their data leak sites, including frequent disconnects and unreachable hosts, suggesting that this is part of a sustained effort to thwart updates to those sites. On Aug. 20, a LockBit representative, "LockBitSupp", reported that nearly 1,000 servers were targeting the LockBit data leak sites, with nearly 400 requests per second. After reporting that their leak sites became unavailable due to a DDoS attack, LockBit provided screenshots alleging that the attack began as soon as they started to publish data to their leak site for Entrust, a digital security company LockBit targeted in July. By Azim Khodjibaev, Colin Grady, Paul Eubanks.Since Aug. 20, 2022, Cisco Talos has been monitoring suspected distributed denial-of-service (DDoS) attacks resulting in intermittent downtime and outages affecting several ransomware-as-a-service (RaaS) data leak sites. While the source and origin of this activity remain unknown, this appears to be a concentrated effort against RaaS leak sites to disrupt their efforts to announce and post new victim information.Actors' responses have varied, with LockBit and ALPHV implementing new measures to counteract DDoS attacks against their sites while other groups like Quantum have simply resorted to redirecting web traffic elsewhere. LockBit also appears to have co-opted this technique by advertising that they are now adding DDoS as an extortion tactic in addition to encrypting and leaking data.RaaS leak sites experience intermittent outagesIn late August, Talos became aware of several prominent ransomware operations, such as ALPHV (also referred to as BlackCat) and LockBit, experiencing suspected DDoS attacks against their public data leak sites. These leak sites are typically hosted on Tor hidden services where, in a tactic known as double extortion, RaaS affiliates post victim information if the ransom demand is not met. On Aug. 26, we also observed at least seven more RaaS leak sites for LV, Hive, Everest, BianLian, Yanluowang, Snatch and Lorenz become inaccessible and go offline intermittently and/or experience slow traffic. Security researchers have also identified additional RaaS leak sites for Ragnar Locker and Vice Society which may have also been affected by this activity. However, we have only verified the Ragnar Locker claim at this time, as their leak site continues to experience outages. At the time of analysis, many of the aforementioned groups are still affected by connectivity issues and continue to face a variety of intermittent outages to their data leak sites, including frequent disconnects and unreachable hosts, suggesting that this is part of a sustained effort to thwart updates to those sites. On Aug. 20, a LockBit representative, "LockBitSupp", reported that nearly 1,000 servers were targeting the LockBit data leak sites, with nearly 400 requests per second. After reporting that their leak sites became unavailable due to a DDoS attack, LockBit provided screenshots alleging that the attack began as soon as they started to publish data to their leak site for Entrust, a digital security company LockBit targeted in July. |
Ransomware | |||
| 2022-09-06 08:00:00 | Researcher Spotlight: How Asheer Malhotra looks for \'instant gratification\' in threat hunting (lien direct) | The India native has transitioned from a reverse-engineer hobbyist to a public speaker in just a few years By Jon Munshaw. Ninety percent of Asheer Malhotra's work will never see the light of day. But it's that 10 percent that keeps him motivated to keep looking for something new. The Talos Outreach researcher spends most of his days looking into potential new threats. Many times, that leads to dead ends of threats that have already been discovered and blocked or don't have any additional threads to pull on. But eventually, the “lightbulb goes off,” as he puts it, which indicates something is a new threat the wider public needs to know about. During his time at Talos, Malhotra has spent much of his time looking into cyber attacks and state-sponsored threat actors in Asia, like the Transparent Tribe group he's written about several times. “At some point, I say 'Hey, I don't think I've seen this before.' I start analyzing public disclosures, and slowly start gaining confidence and being able to craft a narrative around the motivations and tactics around a specific threat actor or malware campaign,” he said. In the case of Transparent Tribe, Malhotra's tracked their growth as a major player in the threat landscape in Asia, as they've added several remote access trojans to their arsenal, targeted high-profile government-adjacent entities in India and expanded their scope across the region. When he's not threat hunting, Malhotra also speaks to Cisco customers about the current state of cybersecurity in briefings and delivers presentations at conferences around the world (mainly virtually during the COVID-19 pandemic).  “I always try to find the latest and new stuff to talk about. … I've been honing my skills and trying to speak more confidently publicly, but the confidence is backed up with the right kind of knowledge and the threat intelligence, that's what helps me succeed,” he said. Malhotra is a native of India and spent most of his life there before coming to the U.S. for his master's degree at Mississippi State University. Mississippi was a far cry from everything else he had known up until that point, but he quickly adjusted. “That was the 'Deep South,'” he said. “So there was a culture shock, but the southern hospitality is such a real thing, and it felt very normal there.” Growing up, Malhotra always knew he wanted to work with computers, starting out as a teenager reverse-engineering exploits he'd see others talk about on the internet or just poking at smaller applications. His additional interest in politics and national security made it natural for him to combine the two and focus his research on state-sponsored actors. He enjoys continuing his research in the Indian subcontinent and sees many parallels between the state of security in India and the U.S. “Th “I always try to find the latest and new stuff to talk about. … I've been honing my skills and trying to speak more confidently publicly, but the confidence is backed up with the right kind of knowledge and the threat intelligence, that's what helps me succeed,” he said. Malhotra is a native of India and spent most of his life there before coming to the U.S. for his master's degree at Mississippi State University. Mississippi was a far cry from everything else he had known up until that point, but he quickly adjusted. “That was the 'Deep South,'” he said. “So there was a culture shock, but the southern hospitality is such a real thing, and it felt very normal there.” Growing up, Malhotra always knew he wanted to work with computers, starting out as a teenager reverse-engineering exploits he'd see others talk about on the internet or just poking at smaller applications. His additional interest in politics and national security made it natural for him to combine the two and focus his research on state-sponsored actors. He enjoys continuing his research in the Indian subcontinent and sees many parallels between the state of security in India and the U.S. “Th |
Threat Ransomware Malware Guideline | APT 36 | ||
| 2022-08-18 08:00:00 | Ukraine and the fragility of agriculture security (lien direct) |  By Joe Marshall.The war in Ukraine has had far-reaching global implications and one of the most immediate effects felt will be on the global supply chain for food. This war-induced fragility has exposed the weaknesses of how we feed ourselves globally. Ransomware cartels and other adversaries are well aware of this and are actively exploiting that fragility. For the past six years, Cisco Talos has been actively involved in assisting public and private institutions in Ukraine to defend themselves against state-sponsored actors. Our involvement stretches the gamut from commercial to critical infrastructure, to election security. Our presence has afforded us unique opportunities and observations about cybersecurity in a macro and micro way. Ukraine has been a frequent victim of state-sponsored cyber attacks aimed at critical infrastructures like power and transportation. Talos is proud to stand with our partners in Ukraine and help defend their critical networks and help users there maintain access to necessary services. Now that Russia has invaded Ukraine, those threats have escalated to kinetic attacks that are wreaking havoc on a critical element of our world: agriculture and our global food supply chain. Even worse is the implications this war will have for future cyber attacks, as fragility is considered a lucrative element in deciding victimology by threat actors like ransomware cartels. To truly grasp the implications of the war in Ukraine, we have to examine how vital Ukrainian agriculture feeds the world, the current state of affairs, and what this means for the global cybersecurity posture to protect agricultural assets. Where there is weakness, there is opportunityRansomware cartels and their affiliates are actively targeting the agricultural industry. Moreover, these actors have done their homework and are targeting agricultural companies during the two times of the year where they cannot suffer disruptions: planting and harvesting. Per the published FBI PIN Alert: “Cyber actors may perceive cooperatives as lucrative targets with a willingness to pay due to the time-sensitive role they play in agricultural production.” This is far from unusual for these adversaries - they are shrewd and calculating, and understand their victims' weaknesses and industries. H By Joe Marshall.The war in Ukraine has had far-reaching global implications and one of the most immediate effects felt will be on the global supply chain for food. This war-induced fragility has exposed the weaknesses of how we feed ourselves globally. Ransomware cartels and other adversaries are well aware of this and are actively exploiting that fragility. For the past six years, Cisco Talos has been actively involved in assisting public and private institutions in Ukraine to defend themselves against state-sponsored actors. Our involvement stretches the gamut from commercial to critical infrastructure, to election security. Our presence has afforded us unique opportunities and observations about cybersecurity in a macro and micro way. Ukraine has been a frequent victim of state-sponsored cyber attacks aimed at critical infrastructures like power and transportation. Talos is proud to stand with our partners in Ukraine and help defend their critical networks and help users there maintain access to necessary services. Now that Russia has invaded Ukraine, those threats have escalated to kinetic attacks that are wreaking havoc on a critical element of our world: agriculture and our global food supply chain. Even worse is the implications this war will have for future cyber attacks, as fragility is considered a lucrative element in deciding victimology by threat actors like ransomware cartels. To truly grasp the implications of the war in Ukraine, we have to examine how vital Ukrainian agriculture feeds the world, the current state of affairs, and what this means for the global cybersecurity posture to protect agricultural assets. Where there is weakness, there is opportunityRansomware cartels and their affiliates are actively targeting the agricultural industry. Moreover, these actors have done their homework and are targeting agricultural companies during the two times of the year where they cannot suffer disruptions: planting and harvesting. Per the published FBI PIN Alert: “Cyber actors may perceive cooperatives as lucrative targets with a willingness to pay due to the time-sensitive role they play in agricultural production.” This is far from unusual for these adversaries - they are shrewd and calculating, and understand their victims' weaknesses and industries. H |
Threat Ransomware Guideline Cloud | NotPetya Uber APT 37 APT 32 APT 28 APT 10 APT 21 Guam | ||
| 2022-08-10 15:44:23 | Cisco Talos shares insights related to recent cyber attack on Cisco (lien direct) | Executive summaryOn May 24, 2022, Cisco became aware of a potential compromise. Since that point, Cisco Security Incident Response (CSIRT) and Cisco Talos have been working to remediate. During the investigation, it was determined that a Cisco employee's credentials were compromised after an attacker gained control of a personal Google account where credentials saved in the victim's browser were being synchronized. The attacker conducted a series of sophisticated voice phishing attacks under the guise of various trusted organizations attempting to convince the victim to accept multi-factor authentication (MFA) push notifications initiated by the attacker. The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user. CSIRT and Talos are responding to the event and we have not identified any evidence suggesting that the attacker gained access to critical internal systems, such as those related to product development, code signing, etc. After obtaining initial access, the threat actor conducted a variety of activities to maintain access, minimize forensic artifacts, and increase their level of access to systems within the environment. The threat actor was successfully removed from the environment and displayed persistence, repeatedly attempting to regain access in the weeks following the attack; however, these attempts were unsuccessful. We assess with moderate to high confidence that this attack was conducted by an adversary that has been previously identified as an initial access broker (IAB) with ties to the UNC2447 cybercrime gang, Lapsus$ threat actor group, and Yanluowang ransomware operators. For further information see the Cisco Response page here. Initial vectorInitial access to the Cisco VPN was achieved via the successful compromise of a Cisco employee's personal Google account. The user had enabled password syncing via Google Chrome and had stored their Cisco credentials in their browser, enabling that information to synchronize to their Google account. After obtaining the user's credentials, the attacker attempted to bypass multifactor authentication (MFA) using a variety of techniques, including voice phishing (aka "vishing") and MFA fatigue, the process of sending a high volume of push requests to the target's mobile device until the user accepts, either accidentally or simply to attempt to silence the repeated push notifications they are receiving. Vishing is an increasingly common social engineering technique whereby attackers try to trick employees into divulging sensitive information over the phone. In this instance, an employee reported that they received multiple calls over several days in which the callers – who spoke in English with various international accents and dialects – purported to be associated with support organizations trusted by the user. Once the attacker had obtained initial access, they enrolled a series of new devices for MFA and authenticated successfully to the Cisco VPN. The attacker then escalated to administrative privileges, allowing them to login to multiple systems, which alerted our Cisco Security Incident Response Team (CSIRT), who subsequently responded to the incident. The actor in question dropped a variety of tools, including remote access tools like LogMeIn and TeamViewer, offensive security tools such as Cobalt Strike, PowerSploit, Mimikatz, and Impacket, and added their own backdoor accounts and persistence mechanisms. | Threat Ransomware Malware Guideline | |||
| 2022-08-08 08:42:23 | Small-time cybercrime is about to explode - We aren\'t ready (lien direct) |  By Nick Biasini.The cybersecurity industry tends to focus on extremely large-scale or sophisticated, state-sponsored attacks. Rightfully so, as it can be the most interesting, technically speaking. When most people think of cybercrime they think of large-scale breaches because that's what dominates the headlines. However, the problem is much bigger. In 2021, the Internet Crime Complaint Center (IC3) received a staggering 847,376 complaints, with each victim losing a little more than $8,000 on average. Once you account for the high-value breaches, the true impact is even lower. The average person is far more likely to have their identity stolen or fall victim to some other sort of scam than be directly affected by a large-scale breach - and business is booming.A deeper look at the data from IC3 shows that the amount of complaints and revenue being generated from cybercrime continues to rise. Interestingly there is a huge jump in cybercrime during the pandemic with a staggering increase of more than 60% in complaints between 2019 and 2020, with it increasing further in 2021. It's clear that cybercrime is on the rise, but what's driving it? By Nick Biasini.The cybersecurity industry tends to focus on extremely large-scale or sophisticated, state-sponsored attacks. Rightfully so, as it can be the most interesting, technically speaking. When most people think of cybercrime they think of large-scale breaches because that's what dominates the headlines. However, the problem is much bigger. In 2021, the Internet Crime Complaint Center (IC3) received a staggering 847,376 complaints, with each victim losing a little more than $8,000 on average. Once you account for the high-value breaches, the true impact is even lower. The average person is far more likely to have their identity stolen or fall victim to some other sort of scam than be directly affected by a large-scale breach - and business is booming.A deeper look at the data from IC3 shows that the amount of complaints and revenue being generated from cybercrime continues to rise. Interestingly there is a huge jump in cybercrime during the pandemic with a staggering increase of more than 60% in complaints between 2019 and 2020, with it increasing further in 2021. It's clear that cybercrime is on the rise, but what's driving it? There have been a variety of reports that criminals are turning increasingly to cybercrime instead of traditional drug crimes, with which they were commonly associated in the past. This is both a blessing and a curse - it removes a lot of violence and crime from the streets but is adding a significant amount of pressure on local law enforcement. This is an international problem. Several recent reports highlight that this is also an issue in Italy and Spain.There are cybercriminals everywhere and the U.S. is no exception. What's changed is who is involved. Historically, cybercrime was considered white-collar criminal behavior perpetrated by those that were knowledgeable and turned bad. Now, technology has become such an integral part of our lives that anyone with a smartphone and desire can get started in cybercrime. The growth of cryptocurrencies and associated anonymity, whether legitimate or not, has garnered the attention of criminals that formerly operated in traditional criminal enterprises and have now shifted to cybercrime and identity theft.Cybercrime is a local law enforcement problemFor cybercrime to get the attention of national law enforcement, There have been a variety of reports that criminals are turning increasingly to cybercrime instead of traditional drug crimes, with which they were commonly associated in the past. This is both a blessing and a curse - it removes a lot of violence and crime from the streets but is adding a significant amount of pressure on local law enforcement. This is an international problem. Several recent reports highlight that this is also an issue in Italy and Spain.There are cybercriminals everywhere and the U.S. is no exception. What's changed is who is involved. Historically, cybercrime was considered white-collar criminal behavior perpetrated by those that were knowledgeable and turned bad. Now, technology has become such an integral part of our lives that anyone with a smartphone and desire can get started in cybercrime. The growth of cryptocurrencies and associated anonymity, whether legitimate or not, has garnered the attention of criminals that formerly operated in traditional criminal enterprises and have now shifted to cybercrime and identity theft.Cybercrime is a local law enforcement problemFor cybercrime to get the attention of national law enforcement, |
Ransomware Malware Guideline | |||
| 2022-07-26 10:11:15 | Quarterly Report: Incident Response Trends in Q2 2022 (lien direct) | Commodity malware usage surpasses ransomware by narrow margin  By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. 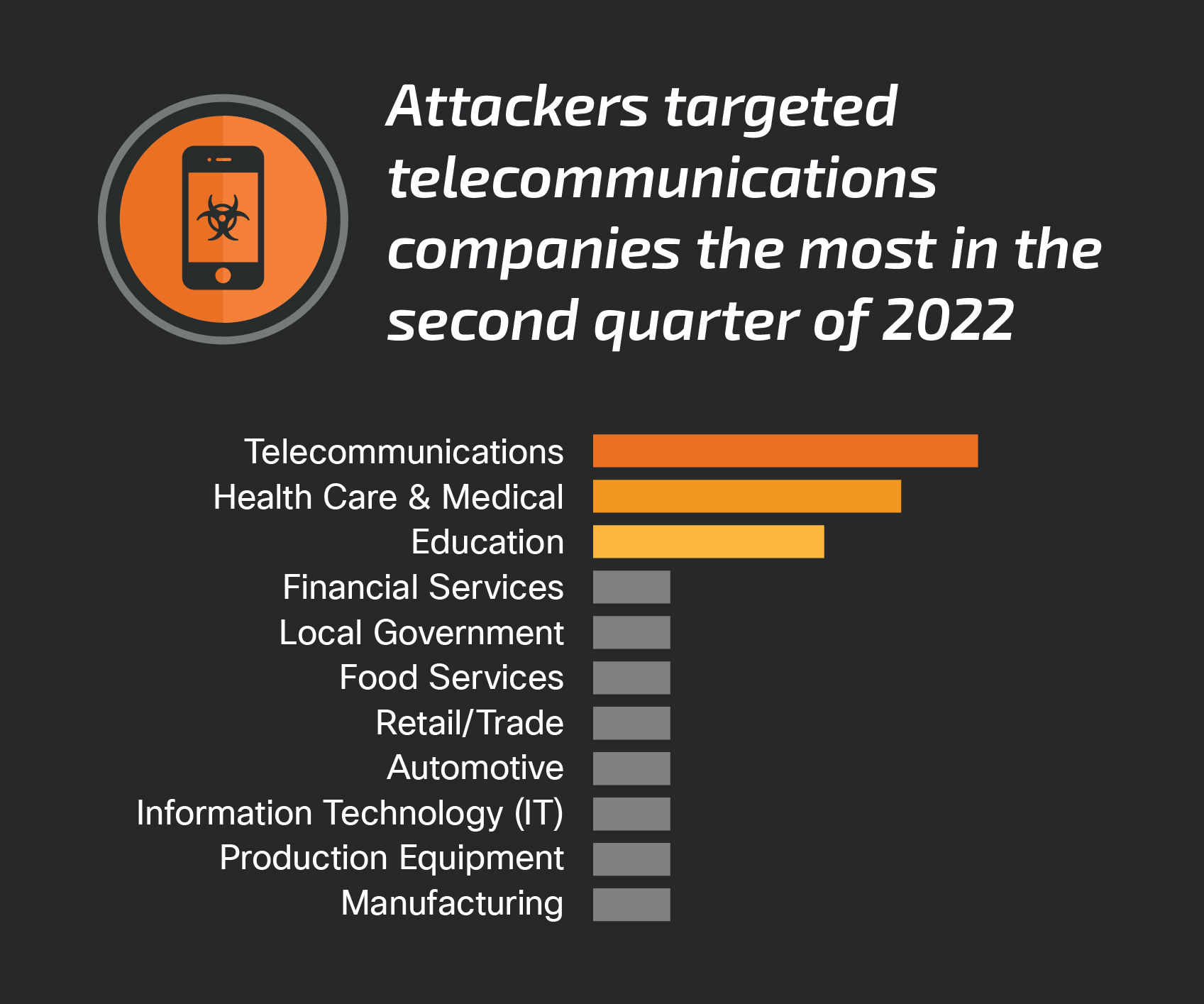 Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity |
Threat Ransomware Spam Malware | |||
| 2022-06-28 04:00:00 | De-anonymizing ransomware domains on the dark web (lien direct) | By Paul Eubanks. We have developed three techniques to identify ransomware operators' dark websites hosted on public IP addresses, allowing us to uncover previously unknown infrastructure for the DarkAngels, Snatch, Quantum and Nokoyawa ransomware groups.The methods we used to identify the public... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2022-06-21 03:59:59 | Avos ransomware group expands with new attack arsenal (lien direct) | By Flavio Costa, Chris Neal and Guilherme Venere. In a recent customer engagement, we observed a month-long AvosLocker campaign. The attackers utilized several different tools, including Cobalt Strike, Sliver and multiple commercial network scanners. The initial ingress point in this incident was... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2022-05-18 04:04:21 | The BlackByte ransomware group is striking users all over the globe (lien direct) | News summary Cisco Talos has been monitoring the BlackByte Ransomware Group for several months, infecting victims all over the world, from North America to Colombia, Netherlands, China, Mexico and Vietnam.The FBI released a joint cybersecurity advisory in February 2022 warning about... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2022-05-03 05:00:00 | Conti and Hive ransomware operations: What we learned from these groups\' victim chats (lien direct) | As part of Cisco Talos' continuous efforts to learn more about the current ransomware landscape, we recently examined a trove of chat logs between the Conti and Hive ransomware gangs and their victims. Ransomware-as-a-service groups have exploded in popularity over the past few years, with... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2022-04-26 06:19:27 | Quarterly Report: Incident Response trends in Q1 2022 (lien direct) | Ransomware continues as the top threat, while a novel increase in APT activity emerges By Caitlin Huey. Ransomware was still the top threat Cisco Talos Incident Response (CTIR) saw in active engagements this quarter, continuing a trend that started in 2020. As mentioned in the 2021... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Threat Ransomware | |||
| 2022-03-17 05:33:47 | From BlackMatter to BlackCat: Analyzing two attacks from one affiliate (lien direct) | By Tiago Pereira with contributions from Caitlin Huey. BlackCat is a recent and growing ransomware-as-a-service (RaaS) group that targeted several organizations worldwide over the past few months.There are rumors of a relationship between BlackCat and the BlackMatter/DarkSide ransomware groups,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2022-01-22 05:45:18 | Talos Incident Response year-in-review for 2021 (lien direct) | By David Liebenberg. Cisco Talos Incident Response (CTIR), as with everyone else in the cybersecurity world, dealt with a bevy of threats last year, as responders dealt with an expanding set of ransomware adversaries and several major cybersecurity incidents affecting organizations worldwide,... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Ransomware | |||
| 2021-11-03 05:00:10 | Microsoft Exchange vulnerabilities exploited once again for ransomware, this time with Babuk (lien direct) | By Chetan Raghuprasad and Vanja Svajcer, with contributions from Caitlin Huey.
Cisco Talos recently discovered a malicious campaign deploying variants of the Babuk ransomware predominantly affecting users in the U.S. with smaller number of infections in U.K., Germany, Ukraine, Finland, Brazil,...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2021-10-28 05:00:00 | Quarterly Report: Incident Response trends from Q3 2021 (lien direct) | Ransomware again dominated the threat landscape, while BEC grew
By David Liebenberg and Caitlin Huey.
Once again, ransomware was the most dominant threat observed in Cisco Talos Incident Response (CTIR) engagements this quarter.
CTIR helped resolve several significant...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware | |||
| 2021-10-08 05:45:58 | Talos Takes Ep. #71 (NCSAM edition): Reflecting on ransomware in 2021 (lien direct) | By Jon Munshaw.
The latest episode of Talos Takes is available now. Download this episode and subscribe to Talos Takes using the buttons below, or visit the Talos Takes page.
We are from the first (or last) people to say this, but 2021 is the year of ransomware. It's by far the biggest story...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2021-09-10 07:20:00 | Talos Takes Ep. #67: What a leaked playbook tells us about the Conti ransomware group (lien direct) | By Jon Munshaw.
The latest episode of Talos Takes is available now. Download this episode and subscribe to Talos Takes using the buttons below, or visit the Talos Takes page.
There's a lot to take apart in the recently leaked Conti ransomware playbook. After a disgruntled member of the...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2021-09-02 05:02:00 | Translated: Talos\' insights from the recently leaked Conti ransomware playbook (lien direct) | By Caitlin Huey, David Liebenberg, Azim Khodjibaev, and Dmytro Korzhevin.
Executive summary
Cisco Talos recently became aware of a leaked playbook that has been attributed to the ransomware-as-a-service (RaaS) group Conti. Talos has a team of dedicated, native-level speakers that translated these...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2021-08-12 15:35:12 | Vice Society Leverages PrintNightmare In Ransomware Attacks (lien direct) | By Edmund Brumaghin, Joe Marshall, and Arnaud Zobec.
Executive Summary
Another threat actor is actively exploiting the so-called PrintNightmare vulnerability (CVE-2021-1675 / CVE-2021-34527) in Windows' print spooler service to spread laterally across a victim's network as part of a recent...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware Vulnerability | |||
| 2021-08-11 05:00:00 | Talos Incident Response quarterly threat report - The top malware families and TTPs used in Q2 2021 (lien direct) | By David Liebenberg and Caitlin Huey.
Last quarter, ransomware was not the most dominant threat for the first time since we began compiling these reports. We theorized that this was due to a huge uptick in Microsoft Exchange exploitation, which temporarily became a primary focus for Cisco...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware Malware | |||
| 2021-07-02 19:11:10 | REvil ransomware actors attack Kaseya in supply chain attack (lien direct) | Attackers are actively exploiting the Kaseya VSA endpoint monitoring software to conduct a widespread supply chain attack targeting a number of Managed Service Providers (MSPs), according to multiple reports. Organizations usually use Kaseya VSA to perform centralized orchestration of systems in...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2021-06-07 05:02:43 | Intelligence-driven disruption of ransomware campaigns (lien direct) | By Neil Jenkins and Matthew Olney.
Note: Our guest co-author, Neil Jenkins, is the Chief Analytic Officer at the Cyber Threat Alliance. He leads the CTA's analytic efforts, focusing on the development of threat profiles, adversary playbooks and other analysis using the threat intelligence in the...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware Guideline | |||
| 2021-05-13 11:00:00 | Threat Source Newsletter (May 13, 2021) (lien direct) | Newsletter compiled by Jon Munshaw.
Good afternoon, Talos readers.
In case you missed the Friday news drop last week, we have an update on the Lemon Duck cryptocurrency miner. It's not as eye-catching as the ransomware attacks that make the news, but Lemon Duck's...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2021-04-29 11:00:00 | Threat Source Newsletter (April 29, 2021) (lien direct) | Newsletter compiled by Jon Munshaw.
Good afternoon, Talos readers.
Ransomware is not just financial extortion. It is crime that transcends business, academic and geographic boundaries. Talos was proud to assist with a newly released report from the international Ransomware Task...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2021-04-12 06:32:04 | Recording: Analyzing Android Malware - From triage to reverse-engineering (lien direct) | It's easy to get wrapped up worry about large-scale ransomware attacks on the threat landscape. These are the types of attacks that make headlines and strike fear into the hearts of CISOs everywhere. But if you want to defend the truly prolific and widespread threats that target some of the devices...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware Malware | |||
| 2021-02-05 08:34:18 | Talos Takes Ep. #40: Takeaways from interviewing a ransomware operator (lien direct) | The latest episode of Talos Takes is available now. Download this episode and subscribe to Talos Takes using the buttons below, or visit the Talos Takes page.
This week, we have two guests on (a Talos Takes first!) to discuss our recent research paper on the LockBit ransomware. Two of the authors, who spoke to the actor directly, join the show to talk about their major takeaways. They talk about how the operator chooses their targets and what defenders should take away from the paper.Apple...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2021-02-05 08:27:34 | A ransomware primer (lien direct) | Ransomware defenseCyber security is continually a relevant topic for Cisco customers and other stakeholders. Ransomware is quickly becoming one of the hottest topics in the technology space as these malware families target high-leverage companies and organizations. We at Cisco are often contacted for guidance and recommendations for ways organizations can prepare for, detect and prevent ransomware attacks. Some of Cisco's vendors have also been affected by ransomware and have looked to Cisco...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware Malware | |||
| 2021-02-04 11:00:06 | Threat Source newsletter (Feb. 4, 2021) (lien direct) | Newsletter compiled by Jon Munshaw.
Good afternoon, Talos readers.
We are excited to finally share this LockBit research paper with you all after months of work. Some of our researchers spoke to a ransomware operator, which provided us insight into a threat actor's day-to-day goals and tactics.
The paper includes information on how the attacker chooses its targets and why it's easier for the attacker to operate in some countries than others.
Upcoming public engagements...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware | |||
| 2021-02-02 07:08:45 | Interview with a LockBit ransomware operator (lien direct) | By Azim Khodjibaev, Dymtro Korzhevin and Kendall McKay.
Ransomware is still highly prevalent in our current threat landscape - it's one of the top threats Cisco Talos Incident Response responds to. One such ransomware family we encounter is called LockBit, a ransomware-as-a-service (RaaS) platform that's known for its automation and the speed at which it attacks its victims.
At Cisco Talos, we strive to understand the malware utilized in ransomware, the infrastructure leveraged...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware Malware | |||
| 2021-01-07 10:52:13 | Threat Source newsletter (Jan. 7, 2021) (lien direct) | Newsletter compiled by Jon Munshaw.
Good afternoon, Talos readers and welcome to the first Threat Source newsletter of 2021.
We hit the ground running already this year with a new Beers with Talos episode. It was recorded back in 2020, but the lessons regarding ransomware attacks and how actors choose their targets are still very much relevant.
On the written word front, we have a full, technical breakdown of a recent Lokibot strain we've seen in the wild. Check...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware | |||
| 2021-01-04 10:14:40 | Beers with Talos Ep. #98: Why ransomware actors are (and aren\'t) targeting health care (lien direct) | Beers with Talos (BWT) Podcast episode No. 97 is now available. Download this episode and subscribe to Beers with Talos:Apple Podcasts Google PodcastsSpotify StitcherIf iTunes and Google Play aren't your thing, click here.
By Mitch Neff.
Recorded early November 2020.
This is an episode we recorded in early November but got pushed back in the end of year shuffle to make production schedules work. We're happy to put this one out now with somewhat belated takes on...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2020-12-09 06:32:50 | Quarterly Report: Incident Response trends from Fall 2020 (lien direct) | By David Liebenberg and Caitlin Huey.
For the sixth quarter in a row, Cisco Talos Incident Response (CTIR) observed ransomware dominating the threat landscape. However, for the first quarter since we began compiling these reports, no engagements that were closed out involved the ransomware Ryuk (though there were engagements that were kicked off this quarter involving Ryuk, but have yet to close). The top ransomware families observed were Maze and Sodinokibi, though barely more than any...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware | |||
| 2020-12-03 11:00:03 | Threat Source newsletter (Dec. 3, 2020) (lien direct) | Newsletter compiled by Jon Munshaw.
Good afternoon, Talos readers.
While ransomware has made all the headlines this year, that doesn't mean cryptocurrency miners are going anywhere. We recently discovered a new actor we're calling “Xanthe” that's mining Monero on targets' machines. The main payload, in this case, is a variant of the XMRig Monero-mining program that is protected with a shared object developed to hide the presence of the miner's process from various tools for process...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware | |||
| 2020-11-17 10:56:55 | Nibiru ransomware variant decryptor (lien direct) | Nikhil Hegde developed this tool.
Weak encryption
The Nibiru ransomware is a .NET-based malware family. It traverses directories in the local disks, encrypts files with Rijndael-256 and gives them a .Nibiru extension. Rijndael-256 is a secure encryption algorithm. However, Nibiru uses a hard-coded string "Nibiru" to compute the 32-byte key and 16-byte IV values. The decryptor program leverages this weakness to decrypt files encrypted by this variant.
Ransomware
Nibiru ransomware is a poorly...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware Malware | |||
| 2020-11-12 11:39:02 | Threat Source newsletter (Nov. 12, 2020) (lien direct) | Newsletter compiled by Jon Munshaw.
Good afternoon, Talos readers.
We're back after a few-week hiatus! And to celebrate, we just dropped some new research on the CRAT trojan that's bringing some ransomware friends along with it. This blog post has all the details of this threat along with what you can do to stay protected.
We also had Microsoft Patch Tuesday this week. The company disclosed about 120 vulnerabilities this month that all users should patch now. Our blog post has a...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware | |||
| 2020-11-12 05:52:48 | CRAT wants to plunder your endpoints (lien direct) | By Asheer Malhotra.
Cisco Talos has observed a new version of a remote access trojan (RAT) family known as CRAT.Apart from the prebuilt RAT capabilities, the malware can download and deploy additional malicious plugins on the infected endpoint.One of the plugins is a ransomware known as "Hansom."CRAT has been attributed to the Lazarus APT Group in the past.The RAT consists of multiple obfuscation techniques to hide strings, API names, command and control (C2) URLs and instrumental functions,...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware Malware | APT 38 | ||
| 2020-10-30 14:51:47 | Cisco Talos Advisory on Adversaries Targeting the Healthcare and Public Health Sector (lien direct) | BackgroundCisco Talos has become aware that an adversary is leveraging Trickbot banking trojan and Ryuk ransomware to target U.S. hospitals and healthcare providers at an increasing rate. Security journalists reported on October 28, 2020 that the adversary was preparing to encrypt systems at “potentially hundreds” of medical centers and hospitals, based on a tip from a researcher who had been monitoring communications for the threat actor. On October 28 and 29, these claims were supported by...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware | |||
| 2020-10-13 07:59:21 | (Déjà vu) Lemon Duck brings cryptocurrency miners back into the spotlight (lien direct) | By Vanja Svajcer, with contributions from Caitlin Huey.
We are used to ransomware attacks and big-game hunting making headlines, but there are still methods adversaries use to monetize their efforts in less intrusive ways.Cisco Talos recently recorded increased activity of the Lemon Duck cryptocurrency-mining botnet using several techniques likely to be spotted by defenders, but are not immediately obvious to end-users.These threats demonstrate several techniques of the MITRE ATT&CK...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2020-09-01 08:00:07 | Quarterly Report: Incident Response trends in Summer 2020 (lien direct) | By David Liebenberg and Caitlin Huey.
For the fifth quarter in a row, Cisco Talos Incident Response (CTIR) observed ransomware dominating the threat landscape. Infections involved a wide variety of malware families including Ryuk, Maze, LockBit, and Netwalker, among others. In a continuation of trends observed in last quarter's report, these ransomware attacks have relied much less on commodity trojans such as Emotet and Trickbot. Interestingly, 66 percent of all ransomware attacks this...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware Malware | |||
| 2020-07-23 11:00:04 | Threat Source newsletter for July 23, 2020 (lien direct) | Newsletter compiled by Jon Munshaw.
Good afternoon, Talos readers.
While ransomware attacks continue to hog all the headlines, cryptocurrency miners are still running the background, sapping computing power from unsuspecting victims. We have what we believe is the first documentation of a new botnet we're calling "Prometei" that mines for Monero. Here's why you need to be on the lookout for this botnet and why it could be a sign of worse things to come if you're infected.
If you didn't get...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Threat Ransomware | |||
| 2020-07-22 08:38:21 | Prometei botnet and its quest for Monero (lien direct) | By Vanja Svajcer
NEWS SUMMARYWe are used to ransomware attacks and big-game hunting making the headlines, but there are still methods adversaries use to monetize their efforts in less intrusive ways.Cisco Talos recently discovered a cryptocurrency-mining botnet attack we're calling "Prometei" using several techniques that defenders are likely to spot, but are not immediately obvious to end-users.These threats demonstrate several techniques of the MITRE ATT&CK framework, most notably...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware | |||
| 2020-07-08 07:12:56 | WastedLocker Goes "Big-Game Hunting" in 2020 (lien direct) | By Ben Baker, Edmund Brumaghin, JJ Cummings and Arnaud Zobec.
Threat summary
After initially compromising corporate networks, the attacker behind WastedLocker performs privilege escalation and lateral movement prior to activating ransomware and demanding ransom payment.The use of "dual-use" tools and "LoLBins" enables adversaries to evade detection and stay under the radar as they further operate towards their objectives in corporate environments.WastedLocker is one of the latest examples of...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware |
1
We have: 45 articles.
We have: 45 articles.
To see everything:
Our RSS (filtrered)
