What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-07-23 21:51:04 | Defending anti-netneutrality arguments (lien direct) | Last week, activists proclaimed a "NetNeutrality Day", trying to convince the FCC to regulate NetNeutrality. As a libertarian, I tweeted many reasons why NetNeutrality is stupid. NetNeutrality is exactly the sort of government regulation Libertarians hate most. Somebody tweeted the following challenge, which I thought I'd address here.@ErrataRob I'd like to see you defend your NN stance in this context.https://t.co/2yvwMLo1m1https://t.co/a7CYxd9vcW- Tanner Bennett (@NSExceptional) July 21, 2017The links point to two separate cases.the Comcast BitTorrent throttling casea lawsuit against Time Warning for poor serviceThe tone of the tweet suggests that my anti-NetNeutrality stance cannot be defended in light of these cases. But of course this is wrong. The short answers are:the Comcast BitTorrent throttling benefits customerspoor service has nothing to do with NetNeutralityThe long answers are below.The Comcast BitTorrent ThrottlingThe presumption is that any sort of packet-filtering is automatically evil, and against the customer's interests. That's not true.Take GoGoInflight's internet service for airplanes. They block access to video sites like NetFlix. That's because they often have as little as 1-mbps for the entire plane, which is enough to support many people checking email and browsing Facebook, but a single person trying to watch video will overload the internet connection for everyone. Therefore, their Internet service won't work unless they filter video sites.GoGoInflight breaks a lot of other NetNeutrality rules, such as providing free access to Amazon.com or promotion deals where users of a particular phone get free Internet access that everyone else pays for. And all this is allowed by FCC, allowing GoGoInflight to break NetNeutrality rules because it's clearly in the customer interest.Comcast's throttling of BitTorrent is likewise clearly in the customer interest. Until the FCC stopped them, BitTorrent users were allowed unlimited downloads. Afterwards, Comcast imposed a 300-gigabyte/month bandwidth cap.Internet access is a series of tradeoffs. BitTorrent causes congestion during prime time (6pm to 10pm). Comcast has to solve it somehow -- not solving it wasn't an option. Their options were:Charge all customers more, so that the 99% not using BitTorrent subsidizes the 1% who do.Impose a bandwidth cap, preventing heavy BitTorrent usage.Throttle BitTorrent packets during prime-time hours when the network is congested.Option 3 is clearly the best. BitTorrent downloads take hours, days, and sometimes weeks. BitTorrent users don't mind throttling during prime-time congested hours. That's preferable to the other option, bandwidth caps.I'm a BitTorrent user, and a heavy downloader (I scan the Internet on a regular basis from cloud machines, then download the results to home, which can often be 100-gigabytes in size for a single scan). I want prime-time BitTorrent throttling rather than bandwidth caps. The EFF/FCC's action that prevented BitTorrent throttling forced me to move to Comcast Business Class which doesn't have bandwidth caps, charging me $100 more a month. It's why I don't contribute the EFF -- if they had not agitated for this, taking such choices away from customers, I'd have $1200 more per year to donate to worthy causes.Ask any user of BitTorrent which they prefer: 30 | Guideline | |||
| 2017-06-05 16:15:45 | Some non-lessons from WannaCry (lien direct) | This piece by Bruce Schneier needs debunking. I thought I'd list the things wrong with it.The NSA 0day debateSchneier's description of the problem is deceptive:When the US government discovers a vulnerability in a piece of software, however, it decides between two competing equities. It can keep it secret and use it offensively, to gather foreign intelligence, help execute search warrants, or deliver malware. Or it can alert the software vendor and see that the vulnerability is patched, protecting the country -- and, for that matter, the world -- from similar attacks by foreign governments and cybercriminals. It's an either-or choice.The government doesn't "discover" vulnerabilities accidentally. Instead, when the NSA has a need for something specific, it acquires the 0day, either through internal research or (more often) buying from independent researchers.The value of something is what you are willing to pay for it. If the NSA comes across a vulnerability accidentally, then the value to them is nearly zero. Obviously such vulns should be disclosed and fixed. Conversely, if the NSA is willing to pay $1 million to acquire a specific vuln for imminent use against a target, the offensive value is much greater than the fix value.What Schneier is doing is deliberately confusing the two, combing the policy for accidentally found vulns with deliberately acquired vulns.The above paragraph should read instead:When the government discovers a vulnerability accidentally, it then decides to alert the software vendor to get it patched. When the government decides it needs as vuln for a specific offensive use, it acquires one that meets its needs, uses it, and keeps it secret. After spending so much money acquiring an offensive vuln, it would obviously be stupid to change this decision and not use it offensively.Hoarding vulnsSchneier also says the NSA is "hoarding" vulns. The word has a couple inaccurate connotations.One connotation is that the NSA is putting them on a heap inside a vault, not using them. The opposite is true: the NSA only acquires vulns it for which it has an active need. It uses pretty much all the vulns it acquires. That can be seen in the ShadowBroker dump, all the vulns listed are extremely useful to attackers, especially ETERNALBLUE. Efficiency is important to the NSA. Your efficiency is your basis for promotion. There are other people who make their careers finding waste in the NSA. If you are hoarding vulns and not using them, you'll quickly get ejected from the NSA.Another connotation is that the NSA is somehow keeping the vulns away from vendors. That's like saying I'm hoarding naked selfies of myself. Yes, technically I'm keeping them away from you, but it's not like they ever belong to you in the first place. The same is true the NSA. Had it never acquired the ETERNALBLUE 0day, it never would've been researched, never found.The VEPSchneier describes the "Vulnerability Equities Process" or "VEP", a process that is supposed to manage the vulnerabilities the government gets.There's no evidence the VEP process has ever been used, at least not with 0days acquired by the NSA. The VEP allows exceptions for important vulns, and all the NSA vulns are important, so all are excepted from the process. Since the NSA is in charge of the VEP, of course, this is at the sole discretion of the NSA. Thus, the entire point of the VEP process goes away.Moreover, it can't work in many cases. The vulns acquired by the NSA often come with clauses that mean they can't be shared.New classes of vulnsOne reason sellers forbid 0days from being shared is because they use new classes of vulnerabilities, such that sha | Guideline | Wannacry | ||
| 2017-06-03 11:12:04 | How to track that annoying pop-up (lien direct) | In a recent update to their Office suite on Windows, Microsoft made a mistake where every hour, for a fraction of a second, a black window pops up on the screen. This leads many to fear their system has been infected by a virus. I thought I'd document how to track this down.The short answer is to use Mark Russinovich's "sysinternals.com" tools. He's Windows internals guru at Microsoft and has been maintaining a suite of tools that are critical for Windows system maintenance and security. Copy all the tools from "https://live.sysinternals.com". Also, you can copy with Microsoft Windows Networking (SMB). Of these tools, what we want is something that looks at "processes". There are several tools that do this, but focus on processes that are currently running. What we want is something that monitors process creation.The tool for that is "sysmon.exe". It can monitor not only process creation, but a large number of other system events that a techy can use to see what the system has been doing, and if you are infected with a virus.Sysmon has a fairly complicated configuration file, and if you enabled everything, you'd soon be overwhelmed with events. @SwiftOnSecurity has published a configuration file they use in the real world in real environment that cuts down on the noise, and focuses on events that are really important. It enables monitoring of "process creation", but filters out know good processes that might fill up your logs. You grab the file here. Save it to the same directory to where you saved Sysmon:https://raw.githubusercontent.com/SwiftOnSecurity/sysmon-config/master/sysmonconfig-export.xmlOnce you've done it, run the following command to activate the Sysmon monitoring service using this configuration file by running the following command as Administrator. (Right click on the Command Prompt icon and select More/Run as Administrator).sysmon.exe -accepteula -i sysmonconfig-export.xml Of these tools, what we want is something that looks at "processes". There are several tools that do this, but focus on processes that are currently running. What we want is something that monitors process creation.The tool for that is "sysmon.exe". It can monitor not only process creation, but a large number of other system events that a techy can use to see what the system has been doing, and if you are infected with a virus.Sysmon has a fairly complicated configuration file, and if you enabled everything, you'd soon be overwhelmed with events. @SwiftOnSecurity has published a configuration file they use in the real world in real environment that cuts down on the noise, and focuses on events that are really important. It enables monitoring of "process creation", but filters out know good processes that might fill up your logs. You grab the file here. Save it to the same directory to where you saved Sysmon:https://raw.githubusercontent.com/SwiftOnSecurity/sysmon-config/master/sysmonconfig-export.xmlOnce you've done it, run the following command to activate the Sysmon monitoring service using this configuration file by running the following command as Administrator. (Right click on the Command Prompt icon and select More/Run as Administrator).sysmon.exe -accepteula -i sysmonconfig-export.xml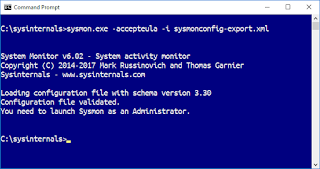 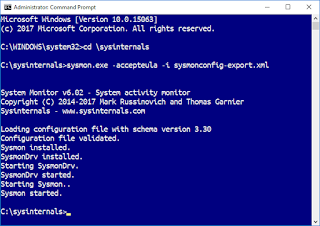 Now sit back and relax until that popup happens again. Right after it does, go into the "Event Viewer" application (click on Windows menu and type "Event Viewer", or run 'eventvwr.exe'. Now y Now sit back and relax until that popup happens again. Right after it does, go into the "Event Viewer" application (click on Windows menu and type "Event Viewer", or run 'eventvwr.exe'. Now y |
Guideline | |||
| 2017-05-12 02:51:43 | Some notes on Trump\'s cybersecurity Executive Order (lien direct) | President Trump has finally signed an executive order on "cybersecurity". The first draft during his first weeks in power were hilariously ignorant. The current draft, though, is pretty reasonable as such things go. I'm just reading the plain language of the draft as a cybersecurity expert, picking out the bits that interest me. In reality, there's probably all sorts of politics in the background that I'm missing, so I may be wildly off-base.Holding managers accountableThis is a great idea in theory. But government heads are rarely accountable for anything, so it's hard to see if they'll have the nerve to implement this in practice. When the next breech happens, we'll see if anybody gets fired."antiquated and difficult to defend Information Technology"The government uses laughably old computers sometimes. Forces in government wants to upgrade them. This won't work. Instead of replacing old computers, the budget will simply be used to add new computers. The old computers will still stick around."Legacy" is a problem that money can't solve. Programmers know how to build small things, but not big things. Everything starts out small, then becomes big gradually over time through constant small additions. What you have now is big legacy systems. Attempts to replace a big system with a built-from-scratch big system will fail, because engineers don't know how to build big systems. This will suck down any amount of budget you have with failed multi-million dollar projects.It's not the antiquated systems that are usually the problem, but more modern systems. Antiquated systems can usually be protected by simply sticking a firewall or proxy in front of them."address immediate unmet budgetary needs necessary to manage risk"Nobody cares about cybersecurity. Instead, it's a thing people exploit in order to increase their budget. Instead of doing the best security with the budget they have, they insist they can't secure the network without more money.An alternate way to address gaps in cybersecurity is instead to do less. Reduce exposure to the web, provide fewer services, reduce functionality of desktop computers, and so on. Insisting that more money is the only way to address unmet needs is the strategy of the incompetent.Use the NIST frameworkProbably the biggest thing in the EO is that it forces everyone to use the NIST cybersecurity framework.The NIST Framework simply documents all the things that organizations commonly do to secure themselves, such run intrusion-detection systems or impose rules for good passwords.There are two problems with the NIST Framework. The first is that no organization does all the things listed. The second is that many organizations don't do the things well.Password rules are a good example. Organizations typically had bad rules, such as frequent changes and complexity standards. So the NIST Framework documented them. But cybersecurity experts have long opposed those complex rules, so have been fighting NIST on them.Another good example is intrusion-detection. These days, I scan the entire Internet, setting off everyone's intrusion-detection systems. I can see first hand that they are doing intrusion-detection wrong. But the NIST Framework recommends they do it, because many organizations do it, but the NIST Framework doesn't demand they do it well.When this EO forces everyone to follow the NIST Framework, then, it's likely just going to i | Guideline | Yahoo Tesla | ||
| 2017-03-15 13:39:32 | Assert() in the hands of bad coders (lien direct) | Using assert() creates better code, as programmers double-check assumptions. But only if used correctly. Unfortunately, bad programmers tend to use them badly, making code worse than if no asserts were used at all. They are a nuanced concept that most programmers don't really understand.We saw this recently with the crash of "Bitcoin Unlimited", a version of Bitcoin that allows more transactions. They used an assert() to check the validity of input, and when they received bad input, most of the nodes in the network crashed.The Bitcoin code is full of bad uses of assert. The following examples are all from the file main.cpp.Example #1: this line of code: if (nPos >= coins->vout.size() || coins->vout[nPos].IsNull()) assert(false); This use of assert is silly. The code should look like this: assert | Guideline | |||
| 2017-03-07 22:53:37 | Only lobbyist and politicians matter, not techies (lien direct) | The NSA/CIA will only buy an 0day if they can use it. They can't use it if they disclose the bug.I point this out, yet again, because of this WaPo article [*] built on the premise that the NSA/CIA spend millions of dollars on 0day they don't use, while unilaterally disarming tiself. Since that premise is false, the entire article is false. It's the sort of article you get when all you interview are Washington D.C. lobbyists and Washington D.C. politicians -- and no outside experts.It quotes former cyberczar (under Obama) Michael Daniel explaining that the "default assumption" is to disclose 0days that the NSA/CIA get. This is a Sean Spicer style lie. He's paid to say this, but it's not true. The NSA/CIA only buy 0day if they can use it. They won't buy 0day if the default assumption is that they will disclose it. QED: the default assumption of such 0day is they won't disclose them.The story quotes Ben Wizner of the ACLU saying that we should patch 0days instead of using them. Patching isn't an option. If we aren't using them, then we aren't buying them, and hence, there are no 0days to patch. The two options are to not buy 0days at all (and not patch) or buy to use them (and not patch). Either way, patching doesn't happen.Wizner didn't actually say "use them". He said "stockpiling" them, a word that means "hold in reserve for use in the future". That's not what the NSA/CIA does. They buy 0days to use, now. They've got budgets and efficiency ratings. They don't buy 0days which they can't use in the near future. In other words, Wizner paints the choice between an 0day that has no particular value to the government, and one would have value being patched.The opposite picture is true. Almost all the 0days possessed by the NSA/CIA have value, being actively used against our adversaries right now. Conversely, patching an 0day provides little value for defense. Nobody else knew about the 0day anyway (that's what 0day means), so nobody was in danger, so nobody was made safer by patching it.Wizner and Snowden are quoted in the article that somehow the NSA/CIA is "maintaining vulnerabilities" and "keeping the holes open". This phrasing is deliberately misleading. The NSA/CIA didn't create the holes. They aren't working to keep them open. If somebody else finds the same 0day hole and tells the vendor (like Apple), then the NSA/CIA will do nothing to stop them. They just won't work to close the holes.Activists like Wizner and Snowden deliberate mislead on the issue because they can't possibly win a rational debate. The government is not going to continue to spend millions of dollars on buying 0days just to close them, because everyone agrees the value proposition is crap, that the value of fixing yet another iPhone hole is not worth the $1 million it'll cost, and do little to stop Russians from finding an unrelated hole. Likewise, while the peacenicks (rightfully, in many respects) hate the militarization of cyberspace, they aren't going to win the argument that the NSA/CIA should unilaterally disarm themselves. So instead they've tried to morph the debate into some crazy argument that makes no sense.This is the problem with Washington D.C. journalism. It presumes the only people who matter are those in Washington, either the lobbyists of one position, or government defenders of another position. At no point did they go out and talk to technical experts, such as somebody who has discovered, weaponized, used an 0day exploit. So they write articles premised on the fact that the NSA/CIA, out of their offensive weapons budget, will continue to buy 0days that are immediately patched and fixed without ever being useful. | Guideline | ★★ | ||
| 2017-03-07 20:40:20 | Some comments on the Wikileaks CIA/#vault7 leak (lien direct) | I thought I'd write up some notes about the Wikileaks CIA "#vault7" leak. This post will be updated frequently over the next 24 hours.The CIA didn't remotely hack a TV. The docs are clear that they can update the software running on the TV using a USB drive. There's no evidence of them doing so remotely over the Internet. If you aren't afraid of the CIA breaking in an installing a listening device, then you should't be afraid of the CIA installing listening software.The CIA didn't defeat Signal/WhattsApp encryption. The CIA has some exploits for Android/iPhone. If they can get on your phone, then of course they can record audio and screenshots. Technically, this bypasses/defeats encryption -- but such phrases used by Wikileaks arehighly misleading, since nothing related to Signal/WhatsApp is happening. What's happening is the CIA is bypassing/defeating the phone. Sometimes. If they've got an exploit for it, or can trick you into installing their software.There's no overlap or turf war with the NSA. The NSA does "signals intelligence", so they hack radios and remotely across the Internet. The CIA does "humans intelligence", so they hack locally, with a human. The sort of thing they do is bribe, blackmail, or bedazzle some human "asset" (like a technician in a nuclear plant) to stick a USB drive into a slot. All the various military, law enforcement, and intelligence agencies have hacking groups to help them do their own missions.The CIA isn't more advanced than the NSA. Most of this dump is child's play, simply malware/trojans cobbled together from bits found on the Internet. Sometimes they buy more advanced stuff from contractors, or get stuff shared from the NSA. Technologically, they are far behind the NSA in sophistication and technical expertise.The CIA isn't hoarding 0days. For one thing, few 0days were mentioned at all. The CIA's techniques rely upon straightforward hacking, not super secret 0day hacking Second of all, they aren't keeping 0days back in a vault somewhere -- if they have 0days, they are using them.The VEP process is nonsense. Activists keep mentioning the "vulnerability equities process", in which all those interested in 0days within the government has a say in what happens to them, with the eventual goal that they be disclosed to vendors. The VEP is nonsense. The activist argument is nonsense. As far as I can tell, the VEP is designed as busy work to keep people away from those who really use 0days, such as the NSA and the CIA. If they spend millions of dollars buying 0days because it has that value in intelligence operations, they aren't going to destroy that value by disclosing to a vendor. If VEP forces disclosure, disclosure still won't happen, the NSA will simply stop buying vulns.There's no false flags. In several places, the CIA talks about making sure that what they do isn't so unique, so it can't be attributed to them. However, Wikileaks's press release hints that the "UMBRAGE" program is deliberately stealing techniques from Russia to use as a false-flag operation. This is nonsense. For example, the DNC hack attribution was live command-and-control servers simultaneously used against different Russian targets -- not a few snippets of code.This hurts the CIA a lot. Already, one AV researcher has told me that a virus they once suspected came from the Russians or Chinese can now be attributed to the CIA, as it matches the description perfectly to something in the leak. We can develop anti-virus and intrusion-detection signatures based on this information that will defeat much of what we read in these documents. This would put a multi-year delay in the CIA's development efforts. Plus, it'll now go on a witch-hunt looking for the leaker, which will erode morale. Update: Three extremely smart and knowledgeable people who I respect disagree, claiming | Guideline | |||
| 2017-01-27 00:40:02 | Is \'aqenbpuu\' a bad password? (lien direct) | Press secretary Sean Spicer has twice tweeted a random string, leading people to suspect he's accidentally tweeted his Twitter password. One of these was 'aqenbpuu', which some have described as a "shitty password". Is is actually bad?No. It's adequate. Not the best, perhaps, but not "shitty".It depends upon your threat model. The common threats are password reuse and phishing, where the strength doesn't matter. When the strength does matter is when Twitter gets hacked and the password hashes stolen.Twitter uses the bcrypt password hashing technique, which is designed to be slow. A typical desktop with a GPU can only crack bcrypt passwords at a rate of around 321 hashes-per-second. Doing the math (26 to the power of 8, divided by 321, divided by one day) it will take 20 years for this desktop to crack the password.That's not a good password. A botnet with thousands of desktops, or a somebody willing to invest thousands of dollars on a supercomputer or cluster like Amazon's, can crack that password in a few days.But, it's not a bad password, either. A hack of a Twitter account like this would be a minor event. It's not worth somebody spending that much resources hacking. Security is a tradeoff -- you protect a ton of gold with Ft. Knox like protections, but you wouldn't invest the same amount protecting a ton of wood. The same is true with passwords -- as long as you don't reuse your passwords, or fall victim to phishing, eight lower case characters is adequate.This is especially true if using two-factor authentication, in which case, such a password is more than adequate.I point this out because the Trump administration is bad, and Sean Spicer is a liar. Our criticism needs to be limited to things we can support, such as the DC metro ridership numbers (which Spicer has still not corrected). Every time we weakly criticize the administration on things we cannot support, like "shitty passwords", we lessen our credibility. We look more like people who will hate the administration no matter what they do, rather than people who are standing up for principles like "honesty". The numbers above aren't approximations. I actually generated a bcrypt hash and attempted to crack it in order to benchmark how long this would take. I'll describe the process here.First of all, I installed the "PHP command-line". While older versions of PHP used MD5 for hashing, the newer versions use Bcrypt.# apt-get install php5-cliI then created a PHP program that will hash the password: 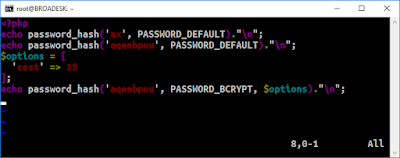 I actually use it three ways. The first way is to hash a small password "ax", one short enough that the password cracker will actually succeed in hashing. The second is to hash the password with PHP defaults, which is what I assume Twitter is using. The third is to increase the difficulty level, in case Twitter has increased the default difficulty level at all in order to protect weak passwords.I then ran the PHP script, producing these hashes:$ php spicer.php$2y$10$1BfTonhKWDN23cGWKpX3YuBSj5Us3eeLzeUsfylemU0PK4JFr4moa I actually use it three ways. The first way is to hash a small password "ax", one short enough that the password cracker will actually succeed in hashing. The second is to hash the password with PHP defaults, which is what I assume Twitter is using. The third is to increase the difficulty level, in case Twitter has increased the default difficulty level at all in order to protect weak passwords.I then ran the PHP script, producing these hashes:$ php spicer.php$2y$10$1BfTonhKWDN23cGWKpX3YuBSj5Us3eeLzeUsfylemU0PK4JFr4moa |
Guideline | |||
| 2017-01-21 18:12:43 | The command-line, for cybersec (lien direct) | On Twitter I made the mistake of asking people about command-line basics for cybersec professionals. A got a lot of useful responses, which I summarize in this long (5k words) post. It's mostly driven by the tools I use, with a bit of input from the tweets I got in response to my query.bashBy command-line this document really means bash.There are many types of command-line shells. Windows has two, 'cmd.exe' and 'PowerShell'. Unix started with the Bourne shell 'sh', and there have been many variations of this over the years, 'csh', 'ksh', 'zsh', 'tcsh', etc. When GNU rewrote Unix user-mode software independently, they called their shell “Bourne Again Shell†or “bash†(queue "JSON Bourne" shell jokes here).Bash is the default shell for Linux and macOS. It's also available on Windows, as part of their special “Windows Subsystem for Linuxâ€. The windows version of 'bash' has become my most used shell.For Linux IoT devices, BusyBox is the most popular shell. It's easy to clear, as it includes feature-reduced versions of popular commands.man'Man' is the command you should not run if you want help for a command.Man pages are designed to drive away newbies. They are only useful if you already mostly an expert with the command you desire help on. Man pages list all possible features of a program, but do not highlight examples of the most common features, or the most common way to use the commands.Take 'sed' as an example. It's used most commonly to do a search-and-replace in files, like so:$ sed 's/rob/dave/' foo.txtThis usage is so common that many non-geeks know of it. Yet, if you type 'man sed' to figure out how to do a search and replace, you'll get nearly incomprehensible gibberish, and no example of this most common usage.I point this out because most guides on using the shell recommend 'man' pages to get help. This is wrong, it'll just endlessly frustrate you. Instead, google the commands you need help on, or better yet, search StackExchange for answers.You might try asking questions, like on Twitter or forum sites, but this requires a strategy. If you ask a basic question, self-important dickholes will respond by telling you to “rtfm†or “read the fucking manualâ€. A better strategy is to exploit their dickhole nature, such as saying “too bad command xxx cannot do yyyâ€. Helpful people will gladly explain why you are wrong, carefully explaining how xxx does yyy.If you must use 'man', use the 'apropos' command to find the right man page. Sometimes multiple things in the system have the same or similar names, leading you to the wrong page.apt-get install yumUsing the command-line means accessing that huge open-source ecosystem. Most of the things in this guide do no already exist on the system. You have to either compile them from source, or install via a package-manager. Linux distros ship with a small footprint, but have a massive database of precompiled software “packages†in the cloud somewhere. Use the "package manager" to install the software from the cloud.On Debian-derived systems (like Ubuntu, Kali, Raspbian), type “apt-get install masscan†to install “masscan†(as an example). Use “apt-cache search scan†to find a bunch of scanners you might want to install.On RedHat systems, use “yum†instead. On BSD, use the “ports†system, which you can also get working for macOS.If no pre-compiled package exists for a program, then you'll have to download the source code and compile it. There's about an 80% chance this will work easy, following the instructions. There is a 20% | Guideline | |||
| 2016-12-21 18:44:41 | "From Putin with Love" - a novel by the New York Times (lien direct) | In recent weeks, the New York Times has written many stories on Russia's hacking of the Trump election. This front page piece [*] alone takes up 9,000 words. Combined, the NYTimes coverage on this topic exceeds the length of a novel. Yet, for all this text, the number of verifiable facts also equals that of a novel, namely zero. There's no evidence this was anything other than an undirected, Anonymous-style op based on a phishing campaign.The question that drives usIt's not that Russia isn't involved, it's that the exact nature of their involvement is complicated. Just because the hackers live in Russia doesn't automatically mean their attacks are directed by the government.It's like the recent Islamic terrorist attacks in Europe and America. Despite ISIS claiming credit, and the perpetrators crediting ISIS, we are loathe to actually blame the attacks directly on ISIS. Overwhelmingly, it's individuals who finance and plan their attacks, with no ISIS organizational involvement other than inspiration.The same goes for Russian hacks. The Russian hacker community is complicated. There are lots of actors with various affiliations with the government. They are almost always nationalistic, almost always pro-Putin. There are many individuals and groups who act to the benefit of Putin/Russia with no direct affiliation with the government. Others do have ties with the government, but these are often informal relationships, sustained by patronage and corruption.Evidence tying Russian attacks to the Russian government is thus the most important question of all -- and it's one that the New York Times is failing to answer. The fewer facts they have, the more they fill the void with vast amounts of verbiage.Sustaining the narrativeHere's a trick when reading New York Times articles: when they switch to passive voice, they are covering up a lie. An example is this paragraph from the above story [*]:The Russians were also quicker to turn their attacks to political purposes. A 2007 cyberattack on Estonia, a former Soviet republic that had joined NATO, sent a message that Russia could paralyze the country without invading it. The next year cyberattacks were used during Russia's war with Georgia.Normally, editors would switch this to the active voice, or:The next year, Russia used cyberattacks in their war against Georgia.But that would be factually wrong. Yes, cyberattacks happened during the conflicts with Estonia and Georgia, but the evidence in both cases points to targets and tools going viral on social media and web forums. It was the people who conducted the attacks, not the government. Whether it was the government who encouraged the people is the big question -- to which we have no answer. Since the NYTimes has no evidence pointing to the Russian government, they switch to the passive voice, hoping you'll assume they meant the government was to blame.It's a clear demonstration that the NYTimes is pushing a narrative, rather than reporting just the facts allowing you to decide for yourself.Tropes and clichesThe NYTimes story is dominated by cliches or "tropes".One such trope is how hackers are always "sophisticated", which leads to the conclusion they must be state-sponsored, not simple like the Anonymous collective. Amusingly, the New York Times tries to give two conflicting "sophisticated" narratives at once. Their article [*] has a section titled "Honing Stealthy Tactics", which ends with describing the attacks as "brazen" | Guideline | |||
| 2016-12-20 23:08:58 | No, that House Judiciary committee did not reject backdoors (lien direct) | A House of Representatives committee has produced a report on "encryption". It's tilted in our favor, the "strong crypto" side of the debate, but not enough for us to embrace it. It stops short of explicitly condemning crypto-backdoors, but also supports "compelled disclosure" and "government hacking". It tries to thread the needle, claiming both "security interests" and "individual privacy" can be accommodated. They can't be.I point this out because on many issues, our side has compromised, only to have that used against us. Those like the EFF compromised on the USA FREEDOM act, supporting it at the beginning as a way to reform NSA metadata surveillance, only to have the end product increase such surveillance. Yes, the EFF then retracted their support, but by then, the damage had been done.Our side came up with the euphemism "strong crypto" to position our opposition to "backdoors", that any attempt to backdoor crypto inevitably "weakens" it. This is going to bite us in the end when lawmakers decide to compromise on "strong backdoors".While this committee report explicitly says "Congress should not weaken this vital technology because doing so works against the national interest", and suggests other approaches to gather evidence, nowhere does it explicitly reject "backdoors". The idea of "strong backdoors" is consistent with the report.I'm not saying the report actually supports "strong backdoors". It does a good job arguing our side, such as how there's no way to mandate backdoors in foreign crypto software we might install on our phones. While it doesn't explicitly mention "backdoors", it does so many times euphemistically, driving home the (correct) point that strong encryption is critically important to our economy and modern society.Thus, the removal of the word "backdoor" is obviously an attempt to make the document more palatable to the other side, the law enforcement side. It explicitly avoids taking a "binary" position.The paper then suggests two other controversial policies: compelled disclosure and hacking."Compelled disclosure" is where law enforcement compels somebody to either reveal their password, or decrypt something. This is problematic for a number of reasons. One is the Fifth Amendment provisions against self incrimination. The other is the practical fact that the suspect may not be able to, either because they've forgotten the password to an old backup drive, or because the phone they are being forced to decrypt isn't actually theirs. Most of us oppose "compelled disclosure", though not as strongly as "backdoors". That's mostly because any abuse would immediately be visible, whereas backdoors can be exploited in secret."Hacking" is where the government breaks into your computer. "End-to-end" crypto doesn't protect you when the NSA has hacked one "end", such as by breaking into your phone. Many in the community oppose this, because it can be abused in secret with no public accountability. Recent "Rule 41" changes have been especially contentious. The recent "Playpen" case is also controversial, especially the way the FBI keeps its exploit secret. On the other hand, many vigorous opponents of backdoors are also vigorous supporters of government hacking, wanting neither artificial abilities for, or artificial limitations against, law enforcement [this includes me].In conclusion, the above paper stresses that there is no "binary" debate between pro-encryption and law enforcement. This is wrong. The debate over "backdoors" is indeed binary: law enforcement won't accept any solution without them, and freedom activists will accept no solution with them. Compelled decryption may also be such a sticky, uncompromisable debate. Only "government hac | Guideline | |||
| 2016-12-13 00:50:13 | That anti-Trump Recode article is terrible (lien direct) | Trump's a dangerous populist. However, the left-wing media's anti-Trump fetishism is doing nothing to stop Trump. It's no better than "fake news" -- it gets passed around a lot on social-media, but is intellectually bankrupt, unlikely to change anybody's mind. A good example is this op-ed on Re/Code [*] about Silicon Valley leaders visiting Trump.The most important feature of that Re/code article is that it contains no criticism of Trump other than the fact that he's a Republican. Half the country voted for Trump. Half the country voted Republican. It's not just Trump that this piece imagines as being unreasonable, but half the country. It's a fashionable bigotry among some of Silicon Valley's leftist elite.But CEOs live in a world where half their customers are Republican, where half their share holders are Republican. They cannot lightly take political positions that differ from their investors/customers. The Re/code piece claims CEOs said "we are duty-bound as American citizens to attend". No, what they said was "we are duty-bound as officers of our corporations to attend".The word "officer", as in "Chief Operating Officer", isn't an arbitrary title like "Senior Software Engineer" that has no real meaning. Instead, "officer" means "bound by duty". It includes a lot of legal duties, for which they can go to jail if they don't follow. It includes additional duties to shareholders, for which the board can fire them if they don't follow.Normal employees can have Twitter disclaimers saying "these are my personal opinions only, not that of my employer". Officers of corporations cannot. They are the employer. They cannot champion political causes of their own that would impact their stock price. Sure, they can do minor things, like vote, or contribute quietly to campaigns, as long as they aren't too public. They can also do political things that enhances stock price, such as opposing encryption backdoors. Tim Cook can announce he's gay, because that enhances the brand image among Apple's key demographic of millennials. It's not something he could do if he were the CEO of John Deere Tractors.Among the things the CEO's cannot do is take a stance against Donald Trump. The Boeing thing is a good example. The Boeing's CEO criticized Trump's stance on free trade, and 30 minutes later Trump tweeted criticisms of a $4 billion contract with Boeing, causing an immediate billion drop in Boeing's stock price.This incident shows why the rest of us need to appose Trump. Such vindictive politics is how democracies have failed. We cannot allow this to happen here. But the hands of CEOs are tied -- they are duty bound to avoid such hits to their stock price.On the flip, this is one of the few chances CEOs will be able to lobby Trump. If Trump has proven anything, it's that he has no real positions on things. This would be a great time to change his mind on "encryption backdoors", for example.Trump is a dangerous populist who sews distrust in the institutions that give us a stable, prosperous country. Any institution, from the press, to the military, to the intelligence services, to the election system, is attacked, brought into disrepute, even if it supports him. Trump has a dubious relationship with the truth, such as his repeated insistence he won a landslide rather than by a slim margin. He has deep character flaws, such as his vindictive attacks against those who oppose him (Boeing is just one of many examples). Hamilton electors cite deep, patriotic principles for changing their votes, such as Trump's foreign influences and demagoguery.What I'm demonstrating here is that thinking persons have good reasons to oppose Trump that can be articulated without mentioning political issues that divide Democrats and Republicans. That the Re/code a | Guideline | |||
| 2016-12-11 02:46:15 | Some notes on a Hamilton election (lien direct) | At least one elector for Trump has promised to switch his vote, becoming a "Hamilton Elector". Assuming 36 more electors (about 10% of Trump's total) do likewise, and Trump fails to get the 270 absolute majority, then what happens? Since all of the constitutional law scholars I follow haven't taken a stab at this, I thought I would write up some notes.Foreign powers and populistsIn Federalist #68, Alexander Hamilton laid out the reasons why electors should switch their vote. The founders feared bad candidates unduly influenced by foreign powers, and demagogues. Trump is unabashedly both. He criticizes our own CIA claiming what every American knows, that Russia interfered in our election. Trump is the worst sort of populist demagogue, offering no solution to problems other than he'll be a strong leader.Therefore, electors have good reasons to change their votes. I'm not suggesting they should, only that doing so is consistent with our Constitutional principles and history.So if 10% of Trump's electors defect, how would this actually work?Failure to get 270 vote absolute majority (math)Well, to start with, let's count up the number of electors. Each state gets one elector for every House Representative and each Senator. Since there are 435 members of the House and 100 members of the Senate, that comes out to 535. However, the 23rd Amendment adds three more electors for Washington D.C. (so they can vote in the Presidential election but not Congress). So that means the there are 538 total electors.According to the Constitution, the winner must get an absolute majority, meaning over 50% of the electoral votes cast. Half of 538 is 269, plus one to get more than half to get majority, equals 270. Thus, Trump must get at least 270 electoral votes. If he gets only 269, the election fails.Trump won 306 electors in the election. To get below 270, then 37 electors must switch their votes, which is a little over 10%.Electors are free to change their votesConstitutionally, the electors are free to change their votes. However, for most, it would destroy their political careers. Most are state party people who have spent years building up power and reputation in their respective states. Violating their word would destroy all that -- nobody would trust them again. They would certainly never be chosen as an elector again, of course.Many states have laws against electors changing their votes. It is widely accepted that these laws are unconstitutional and would be struck down the courts, but in the meanwhile, some vote flippers would have to spend considerable time and money defending themselves from the legal punishment.Electors vote December 19We've only got until December 19th [*] for electors to change their minds. That's the date they vote. The votes are collected in their various states, then sent to Washington.Electoral votes counted January 6Ballots are theoretically sealed until January 6, when the votes are unsealed and counted in front of Congress.A 26 state majority of House delegationsIf the elector college fails to get an absolute majority of 270 votes, then the election is thrown into the House of Representatives. But it's not a straight up vote among all 435 members of the House. Instead, there are 50 votes -- one for each state delegation. Again, the winner must get an absolute majority to win, meaning 26 votes.This will be the newly elected House of Representatives, which will have been sworn in on January 3, three days earlier. They are instructed to immediately vote, right after the count | Guideline | |||
| 2016-12-05 23:41:40 | That "Commission on Enhancing Cybersecurity" is absurd (lien direct) | An Obama commission has publish a report on how to "Enhance Cybersecurity". It's promoted as having been written by neutral, bipartisan, technical experts. Instead, it's almost entirely dominated by special interests and the Democrat politics of the outgoing administration.In this post, I'm going through a random list of some of the 53 "action items" proposed by the documents. I show how they are policy issues, not technical issues. Indeed, much of the time the technical details are warped to conform to special interests.IoT passwordsThe recommendations include such things as Action Item 2.1.4:Initial best practices should include requirements to mandate that IoT devices be rendered unusable until users first change default usernames and passwords. This recommendation for changing default passwords is repeated many times. It comes from the way the Mirai worm exploits devices by using hardcoded/default passwords.But this is a misunderstanding of how these devices work. Take, for example, the infamous Xiongmai camera. It has user accounts on the web server to control the camera. If the user forgets the password, the camera can be reset to factory defaults by pressing a button on the outside of the camera.But here's the deal with security cameras. They are placed at remote sites miles away, up on the second story where people can't mess with them. In order to reset them, you need to put a ladder in your truck and drive 30 minutes out to the site, then climb the ladder (an inherently dangerous activity). Therefore, Xiongmai provides a RESET.EXE utility for remotely resetting them. That utility happens to connect via Telnet using a hardcoded password.The above report misunderstands what's going on here. It sees Telnet and a hardcoded password, and makes assumptions. Some people assume that this is the normal user account -- it's not, it's unrelated to the user accounts on the web server portion of the device. Requiring the user to change the password on the web service would have no effect on the Telnet service. Other people assume the Telnet service is accidental, that good security hygiene would remove it. Instead, it's an intended feature of the product, to remotely reset the device. Fixing the "password" issue as described in the above recommendations would simply mean the manufacturer would create a different, custom backdoor that hackers would eventually reverse engineer, creating MiraiV2 botnet. Instead of security guides banning backdoors, they need to come up with standard for remote reset.That characterization of Mirai as an IoT botnet is wrong. Mirai is a botnet of security cameras. Security cameras are fundamentally different from IoT devices like toasters and fridges because they are often exposed to the public Internet. To stream video on your phone from your security camera, you need a port open on the Internet. Non-camera IoT devices, however, are overwhelmingly protected by a firewall, with no exposure to the public Internet. While you can create a botnet of Internet cameras, you cannot create a botnet of Internet toasters.The point I'm trying to demonstrate here is that the above report was written by policy folks with little grasp of the technical details of what's going on. They use Mirai to justify several of their "Action Items", none of which actually apply to the technical details of Mirai. It has little to do with IoT, passwords, or hygiene.Public-private partnershipsAction Item 1.2.1: The President should create, through executive order, the National Cybersecurity Private–Public Program (NCP 3 ) as a forum for addressing cybersecurity issues through a high-level, joint public–private collaboration.We've had public-private partnerships to secure cyberspace for over 20 years, such as the FBI InfraGuard partner | Guideline | |||
| 2016-11-21 21:55:31 | The false-false-balance problem (lien direct) | Until recently, journalism in America prided itself on objectivity -- to report the truth, without taking sides. That's because big debates are always complexed and nuanced, and that both sides are equally reasonable. Therefore, when writing an article, reporters attempt to achieve balance by quoting people/experts/proponents on both sides of an issue.But what about those times when one side is clearly unreasonable? You'd never try to achieve balance by citing those who believe in aliens and big-foot, for example.Thus, journalists have come up with the theory of false-balance to justify being partisan and one-sided on certain issues.Typical examples where journalists cite false-balance is reporting on anti-vaxxers, climate-change denialists, and Creationists. More recently, false-balance has become an issue in the 2016 Trump election.But this concept of false-balance is wrong. It's not that anti-vaxxers, denialists, Creationists, and white supremacists are reasonable. Instead, the issue is that the left-wing has reframed the debate. They've simplified it into something black-and-white, removing nuance, in a way that shows their opponents as being unreasonable. The media then adopts the reframed debate.Let's talk anti-vaxxers. One of the policy debates is whether the government has the power to force vaccinations on people (or on people's children). Reasonable people say the government doesn't have this power. Many (if not most) people hold this opinion while agreeing that vaccines are both safe and effective (that they don't cause autism).Consider this February 2015 interview with Chris Christy. He's one of the few politicians who have taken the position that government can override personal choice, such as in the case of an outbreak. Yet, when he said "parents need to have some measure of choice in things as well, so that's the balance that the government has to decide", he was broadly reviled as an anti-vaxxer throughout the media. The press reviled other Republican candidates the same way, even while ignoring almost identical statements made at the same time by the Obama administration. They also ignored clearly anti-vax comments from both Hillary and Obama during the 2008 election.Yes, we can all agree that anti-vaxxers are a bunch of crazy nutjobs. In calling for objectivity, we aren't saying that you should take them seriously. Instead, we are pointing out the obvious bias in the way the media attacked Republican candidates as being anti-vaxxers, and then hiding behind "false-balance".Now let's talk evolution. The issue is this: Darwinism has been set up as some sort of competing religion against belief in God(s). High-schools teach children to believe in Darwinism, but not to understand Darwinism. Few kids graduate understanding Darwinism, which is why it's invariably misrepresented in mass-media (X-Men, Planet of the Apes, Waterworld, Godzilla, Jurassic Park, etc.). The only movie I can recall getting evolution correct is Idiocracy.Also, evolution has holes in it. This isn't a bad thing in science, every scientific theory has holes. Science isn't a religion. We don't care about the holes. That some things remain unexplained by a theory doesn't bother us. Science has no problem with gaps in knowledge, where we admit "I don't know". It's religion that has "God of the gaps", where ignorance isn't tolerated, and everything unexplained is explained by a deity.The hole in evolution is how the cell evolved. The fossil record teaches us a lot about multi-cellular organisms over the last 400-million years, but not much about how the cell evolved in th | Guideline | |||
| 2016-11-14 22:29:16 | How to teach endian (lien direct) | On /r/programming is this post about byte-order/endianness. It gives the same information as most documents on the topic. It is wrong. It's been wrong for over 30 years. Here's how it should be taught.One of the major disciplines in computer science is parsing/formatting. This is the process of converting the external format of data (file formats, network protocols, hardware registers) into the internal format (the data structures that software operates on).It should be a formal computer-science discipline, because it's actually a lot more difficult than you'd expect. That's because the majority of vulnerabilities in software that hackers exploit are due to parsing bugs. Since programmers don't learn about parsing formally, they figure it out for themselves, creating ad hoc solutions that are prone to bugs. For example, programmers assume external buffers cannot be larger than internal ones, leading to buffer overflows.An external format must be well-defined. What the first byte means must be written down somewhere, then what the second byte means, and so on. For Internet protocols, these formats are written in RFCs, such as RFC 791 for the "Internet Protocol". For file formats, these are written in documents, such as those describing GIF files, JPEG files, MPEG files, and so forth.Among the issues is how integers should be represented. The definition must include the size, whether signed/unsigned, what the bits means (almost always 2s-compliment), and the byte-order. Integers that have values above 255 must be represented with more than one byte. Whether those bytes go left-to-right or right-to-left is known as byte-order.We also called this endianness, where one form is big-endian and the other form is little-endian. This is a joke, referring back to Jonathan Swift's tale Gulliver's Travels, where two nations were at war arguing whether an egg should be cracked on the big end or the little end. The joke refers to the Holy Wars in computing where two sides argued strongly for one byte-order or the other. The commentary using the term "endianess" is that neither format matters.However, big-endian is how humans naturally process numbers. If we have the hex value 0x2211, then we expect that representing this number in a file/protocol will consist of one byte with the value 0x22 followed by another byte with the value 0x11. In a little-endian format specification, however, the order of bytes will be reversed, with a value of 0x2211 represented with 0x11 followed by 0x22.This is further confused by the fact that the nibbles in the byte will still be written in conventional, big-endian order. In other words, the big-endian format for the number 0x1234 is 0x12 0x34. however, the little-endian format is 0x34 0x12 -- not 0x43 0x21 as you might naively expect trying to swap everything around in your mind.If little-endian is so confusing to the human mind, why would anybody ever use it? The answer is that it can be more efficient for logic circuits. Or at least, back in the 1970s, when CPUs had only a few thousand logic gates, it could be more efficient. Therefore, a lot of internal processing was little-endian, and this bled over into external formats as well.On the other hand, most network protocols and file formats remain big-endian. Format specifications are written for humans to understand, and big-endian is easier for us humans.So once you understand the byte-order issue in external formats, the next problem is figuring out how to parse it, to convert it into an internal data structure. Well, we first have to understand how to parse things in general.There are two ways of parsing thing: buffered or streaming. In the buffered model, you read in the entire input f | Guideline | |||
| 2016-10-18 20:19:56 | Trump on cybersecurity: vacuous and populist (lien direct) | Trump has published his policy on cybersecurity. It demonstrates that he and his people do not understand the first thing about cybersecurity.Specifically, he wants “the best defense technologies†and “cyber awareness training for all government employeesâ€. These are well known bad policies in the cybersecurity industry. They are the sort of thing the intern with a degree from Trump University would come up with.Awareness training is the knee-jerk response to any problem. Employees already spend a lot of their time doing mandatory training for everything from environmental friendly behavior, to sexual harassment, to Sarbannes-Oxley financial compliance, to cyber-security. None of it has proven effective, but organizations continue to force it, either because they are required to, or they are covering their asses. No amount of training employees to not click on email attachments helps. Instead, the network must be secure enough that reckless clicking on attachments pose no danger.Belief in a technological Magic Pill that will stop hackers is common among those who know nothing about cybersecurity. Such pills don't exist. The least secure networks already have “the best defense technologiesâ€. Things like anti-virus, firewalls, and intrusion prevention systems do not stop hackers by themselves – but area instead tools that knowledgeable teams use in order to make their jobs easier. It's like how a chisel doesn't make a sculpture by itself, but is instead just a tool used by the artist. The government already has all the technology it needs. It's problems instead derive from the fact that they try to solve their problems the way Trump does – by assigning the task to some Trump University intern.Lastly, Trump suggests that on the offensive side, we need to improve our offensive abilities, in order to create a cyber deterrence. We already do that. The United States is by far the #1 nation in offensive capabilities. In 2015, Obama forced China to the table, to sign an agreement promising they'd stop hacking us. Since then, China has kept the agreement, and has dropped out of the news as being the source of cyber attacks. Privately, many people in government tell me its because we did some major cyber attack in China that successfully deterred them.[if gte mso 9]> [if gte mso 9]> Normal 0 false false false EN-US JA X-NONE | Guideline | |||
| 2016-09-28 19:01:08 | Some technical notes on the PlayPen case (lien direct) | In March of 2015, the FBI took control of a Tor onion childporn website ("PlayPen"), then used an 0day exploit to upload malware to visitors's computers, to identify them. There is some controversy over the warrant they used, and government mass hacking in general. However, much of the discussion misses some technical details, which I thought I'd discuss here.IP addressIn a post on the case, Orin Kerr claims:retrieving IP addresses is clearly a searchHe is wrong. Uploading malware to gather other things (hostname, username, MAC address) is clearly a search. But discovering the IP address is a different thing.Today's homes contain many devices behind a single router. The home has only one public IP address, that of the router. All the other devices have local IP addresses. The router then does network address translation (NAT) in order to convert outgoing traffic to all use the public IP address.The FBI sought the public IP address of the NAT/router, not the local IP address of the perp's computer. The malware ("NIT") didn't search the computer for the IP address. Instead the NIT generated network traffic, destined to the FBI's computers. The FBI discovered the suspect's public IP address by looking at their own computers.Historically, there have been similar ways of getting this IP address (from a Tor hidden user) without "hacking". In the past, Tor used to leak DNS lookups, which would often lead to the user's ISP, or to the user's IP address itself. Another technique would be to provide rich content files (like PDF) or video files that the user would have to be downloaded to view, and which then would contact the Internet (contacting the FBI's computers) themselves bypassing Tor.Since the Fourth Amendment is about where the search happens, and not what is discovered, it's not a search to find the IP address in packets arriving at FBI servers. How the FBI discovered the IP address may be a search (running malware on the suspect's computer), but the public IP address itself doesn't necessarily mean a search happened.In any event, if not for the IP address, then PlayPen searches still happened for the hostname, username, and MAC address. Imagine the FBI gets a search warrant, shows up at the suspect's house, and finds no child porn. They then look at the WiFi router, and find that suspected MAC address is indeed connected. They then use other tools to find that the device with that MAC address is located in the neighbor's house -- who has been piggybacking off the WiFi.It's a pre-crime warrant (#MinorityReport)The warrant allows the exploit/malware/search to be used whenever somebody logs in with a username and password.The key thing here is that the warrant includes people who have not yet created an account on the server at the time the warrant is written. They will connect, create an account, log in, then start accessing the site.In other words, the warrant includes people who have never committed a crime when the warrant was issued, but who first commit the crime after the warrant. It's a pre-crime warrant. Sure, it's possible in any warrant to catch pre-crime. For example, a warrant for a drug dealer may also catch a teenager making their first purchase of drugs. But this seems quantitatively different. It's not targeting the known/suspected criminal -- it's targeting future criminals.This could ea | Guideline | ★★★★★ | ||
| 2016-09-28 09:25:13 | Beware: Attribution & Politics (lien direct) | tl;dr - Digital location data can be inherently wrong and it can be spoofed. Blindly assuming that it is accurate can make an ass out of you on twitter and when regulating drones. Guest contributor and friend of Errata Security Elizabeth Wharton is an attorney and host of the technology-focused weekly radio show "Buzz Off with Lawyer Liz" on America's Web Radio. This post is merely her musings and not legal advice.Filtering through various campaign and debate analysis on social media, a tweet caught my eye. The message itself was not the concern and the underlying image has since been determined to be fake. Rather, I was stopped by the140 character tweet's absolute certainty that internet user location data is infallible. The author presented a data map as proof without question, caveat, or other investigation. Boom, mic drop - attribution!According to the tweeting pundit, "Russian trollbots" are behind the #TrumpWon hashtag trending on Twitter.  The proof? The twitter post claims that the Trendsmap showed the initial hashtag tweets as originating from accounts located in Russia. Within the first hour the tweet and accompanying map graphic was "liked" 1,400 times and retweeted 1,495 times. A gotcha moment because a pew-pew map showed that the #TrumpWon hashtag originated from Twitter accounts located in Russia. Boom, mic drop - attribution!Except, not so fast. First, Trendsmap has since clarified that the map and data in the tweet above are not theirs (the Washington Post details the faked data/map ). Moreover, location data is tricky. According to the Trendsmap FAQ page they use the location provided in a user's profile and GeoIP provided by Google. Google's GeoIP is crafted using a proprietary system and other databases such as MaxMind. IP mapping is not an exact art. Kashmir Hill, editor of Fusion's Real Future, and David Maynor, delved into the issues and inaccuracies of IP mapping earlier this year. Kashmir wrote extensively on their findings and how phantom IP addresses and MaxMind's use of randomly selected default locations created digital hells for individuals all over the country - Internet Mapping Glitch Turned Random Farm into Digital Hell.Reliance on such mapping and location information as an absolute has tripped up law enforcement and is poised to trip up the drone industry. Certain lawmakers like to point to geofencing and other location applications as security and safety cure-all solutions. Sen. Schumer (D-N.Y.) previously included geofencing as a key element of his 2015 drone safety bill. Geofencing as a safety measure was mentioned during Tuesday's U.S. House Small Business Committee hearing on Commercial Drone Operations. With geofencing, the drone is programmed to prohibit operations above a certain height or to keep out of certain locations. Attempt to fly in a prohibited area and the aircraft will automatically shut down. Geofencing relies on location data, including geospatial data collected from a variety of sources. As seen with GeoIP, data can be wrong. Additionally, the data must be interpreted and analyzed by the aircraft's software systems. Aircraft systems are not bui The proof? The twitter post claims that the Trendsmap showed the initial hashtag tweets as originating from accounts located in Russia. Within the first hour the tweet and accompanying map graphic was "liked" 1,400 times and retweeted 1,495 times. A gotcha moment because a pew-pew map showed that the #TrumpWon hashtag originated from Twitter accounts located in Russia. Boom, mic drop - attribution!Except, not so fast. First, Trendsmap has since clarified that the map and data in the tweet above are not theirs (the Washington Post details the faked data/map ). Moreover, location data is tricky. According to the Trendsmap FAQ page they use the location provided in a user's profile and GeoIP provided by Google. Google's GeoIP is crafted using a proprietary system and other databases such as MaxMind. IP mapping is not an exact art. Kashmir Hill, editor of Fusion's Real Future, and David Maynor, delved into the issues and inaccuracies of IP mapping earlier this year. Kashmir wrote extensively on their findings and how phantom IP addresses and MaxMind's use of randomly selected default locations created digital hells for individuals all over the country - Internet Mapping Glitch Turned Random Farm into Digital Hell.Reliance on such mapping and location information as an absolute has tripped up law enforcement and is poised to trip up the drone industry. Certain lawmakers like to point to geofencing and other location applications as security and safety cure-all solutions. Sen. Schumer (D-N.Y.) previously included geofencing as a key element of his 2015 drone safety bill. Geofencing as a safety measure was mentioned during Tuesday's U.S. House Small Business Committee hearing on Commercial Drone Operations. With geofencing, the drone is programmed to prohibit operations above a certain height or to keep out of certain locations. Attempt to fly in a prohibited area and the aircraft will automatically shut down. Geofencing relies on location data, including geospatial data collected from a variety of sources. As seen with GeoIP, data can be wrong. Additionally, the data must be interpreted and analyzed by the aircraft's software systems. Aircraft systems are not bui |
Guideline | ★★ | ||
| 2016-08-26 23:01:43 | Notes on that StJude/MuddyWatters/MedSec thing (lien direct) | I thought I'd write up some notes on the StJude/MedSec/MuddyWaters affair. Some references: [1] [2] [3] [4].The story so fartl;dr: hackers drop 0day on medical device company hoping to profit by shorting their stockSt Jude Medical (STJ) is one of the largest providers of pacemakers (aka. cardiac devices) in the country, around ~$2.5 billion in revenue, which accounts for about half their business. They provide "smart" pacemakers with an on-board computer that talks via radio-waves to a nearby monitor that records the functioning of the device (and health data). That monitor, "Merlin@Home", then talks back up to St Jude (via phone lines, 3G cell phone, or wifi). Pretty much all pacemakers work that way (my father's does, although his is from a different vendor).MedSec is a bunch of cybersecurity researchers (white-hat hackers) who have been investigating medical devices. In theory, their primary business is to sell their services to medical device companies, to help companies secure their devices. Their CEO is Justine Bone, a long-time white-hat hacker.Muddy Waters is an investment company known for investigating companies, finding problems like accounting fraud, and profiting by shorting the stock of misbehaving companies.Apparently, MedSec did a survey of many pacemaker manufacturers, chose the one with the most cybersecurity problems, and went to Muddy Waters with their findings, asking for a share of the profits Muddy Waters got from shorting the stock.Muddy Waters published their findings in [1] above. St Jude published their response in [2] above. They are both highly dishonest. I point that out because people want to discuss the ethics of using 0day to short stock when we should talk about the ethics of lying."Why you should sell the stock" [finance issues]In this section, I try to briefly summarize Muddy Water's argument why St Jude's stock will drop. I'm not an expert in this area (though I do a bunch of investment), but they do seem flimsy to me.Muddy Water's argument is that these pacemakers are half of St Jude's business, and that fixing them will first require recalling them all, then take another 2 year to fix, during which time they can't be selling pacemakers. Much of the Muddy Waters paper is taken up explaining this, citing similar medical cases, and so on.If at all true, and if the cybersecurity claims hold up, then yes, this would be good reason to short the stock. However, I suspect they aren't true -- and they are simply trying to scare people about long-term consequences allowing Muddy Waters to profit in the short term.@selenakyle on Twitter suggests this interest document [4] about market-solutions to vuln-disclosure, if you are interested in this angle of things.The 0day being droppedWell, they didn't actually drop 0day as such, just claims that 0day exists -- that it's been "demonstrated". Reading through their document a few times, I've created a list of the 0day they found, to the granularity that | Guideline | Deloitte | ||
| 2016-08-25 00:08:49 | Another lesson in confirmation bias (lien direct) | The biggest problem with hacker attribution is the confirmation bias problem. Once you develop a theory, your mind shifts to distorting evidence trying to prove the theory. After a while, only your theory seems possible as one that can fit all your carefully selected evidence.You can watch this happen in two recent blogposts [1] [2] by Krypt3ia attributing bitcoin payments to the Shadow Broker hackers as coming from the government (FBI, NSA, TAO). These posts are absolutely wrong. Nonetheless, the press has picked up on the story and run with it [*]. [Note: click on the pictures in this post to blow them up so you can see them better].The Shadow Brokers published their bitcoin address (19BY2XCgbDe6WtTVbTyzM9eR3LYr6VitWK) asking for donations to release the rest of their tools. They've received 66 transactions so far, totally 1.78 bitcoin, or roughly $1000 at today's exchange rate.Bitcoin is not anonymous by pseudonymous. Bitcoin is a public ledger with all transaction visible by everyone. Sometimes we can't tie addresses back to people, but sometimes we can. There are a lot of researchers who spent a lot of time on "taint anlysis" trying to track down the real identity of evildoers. Thus, it seems plausible that we might be able to discover the identities of those people making contributions to Shadow Brokers.The first of Krypt3ia's errant blogposts tries to use the Bitcoin taint analysis plugin within Maltego in order to do some analysis on the Shadow Broker address. What he found was links to the Silk Road address -- the address controlled by the FBI since they took down that darknet marketplace several years ago. Therefore, he created the theory that the government (FBI? NSA? TAO?) was up to some evil tricks, such as trying to fill the account with money so that they could then track where the money went in the public blockchain.But he misinterpreted the links. (He was wrong.) There were no payments from the Silk Road accounts to the Shadow Broker account. Instead, there were people making payments to both accounts. As a prank.To demonstrate how this prank wors, I made my own transaction, where I pay money to the Shadow Brokers (19BY2...), to Silk Road (1F1A...), and to a few other well-known accounts controlled by the government. The point here is that anybody can do these shenanigans. That government controlled addresses are involved means nothing. They are public, and anybody can send coin to them.That blogpost points to yet more shenanigans, such as somebody "rick rolling", to confirm that TAO hackers were involved. What you see in the picture below is a series of transactions using bitcoin addresses containing the phrase "never gonna give you up", the title of Rich Astley's song (I underlined the words in red). The point here is that anybody can do these shenanigans. That government controlled addresses are involved means nothing. They are public, and anybody can send coin to them.That blogpost points to yet more shenanigans, such as somebody "rick rolling", to confirm that TAO hackers were involved. What you see in the picture below is a series of transactions using bitcoin addresses containing the phrase "never gonna give you up", the title of Rich Astley's song (I underlined the words in red). |
Guideline | |||
| 2016-07-22 22:24:07 | My Raspeberry Pi cluster (lien direct) | So I accidentally ordered too many Raspberry Pi's. Therefore, I built a small cluster out of them. I thought I'd write up a parts list for others wanting to build a cluster.To start with is some pics of the cluster What you see is a stack of 7 RPis. At the bottom of the stack is a USB multiport charger and also an Ethernet hub. You see USB cables coming out of the charger to power the RPis, and out the other side you see Ethernet cables connecting the RPis to a network. I've including the mouse and keyboard in the picture to give you a sense of perspective. Here is the same stack turn around, seeing it from the other side. Out the bottom left you see three external cables, one Ethernet to my main network and power cables for the USB charger and Ethernet hub. You can see that the USB hub is nicely tied down to the frame, but that the Ethernet hub is just sort jammed in there somehow. Here is the same stack turn around, seeing it from the other side. Out the bottom left you see three external cables, one Ethernet to my main network and power cables for the USB charger and Ethernet hub. You can see that the USB hub is nicely tied down to the frame, but that the Ethernet hub is just sort jammed in there somehow. |
Guideline | ★★ | ||
| 2016-06-02 20:32:52 | My fellow Republicans: don\'t support Trump (lien direct) | Scott Adams, the creator of the Dilbert comic strip, has a post claiming a Trump presidency wouldn't be as bad as people fear. It's a good post. But it's wrong.Trump is certainly not as bad as his haters claim. Trump not only disables the critical-thinking ability of his supporters, but also of his enemies. In most conversations, I end up defending Trump -- not because I support him as a candidate, but because I support critical-thinking. He's only racist sometimes, most of the time I love his political incorrectness.But with all that said, he would indeed be a horrible president. As a long-term Republican, I'd prefer a Hillary Clinton presidency, and I hate Hillary to the depths of my soul. She's corrupt, and worst of all, she's a leftist.But there's a thing worse than being a leftist (or right-winger) and that's being a "populist demagogue". Populist demagogues tell you that all your problems are caused by them (you know, those people), and present unrealistic solutions to problems. They appeal to base emotion and ignorance.When nations fail because of politics, it's almost always due to populist demagogues. Virtually all dictators are a "man of the people", protecting the people's interests against the powerful (somehow, the dictators themselves are never part of the "powerful", since by definition, they are "of the people"). We see that in Venezuela right now, whose economy has crashed with oil prices (50% of their GDP was oil exports). The leader is making everything worse by running the playbook of bad populist policies. For example he's printing money, which first year economics textbooks tell you causes inflation, then blaming the resulting inflation on the United States and the CIA manipulating prices. That's the essence of populism: they pursue horrible policies, but blame the consequences on them.In a Trump presidency, bad results that educated people know is caused by the government policy will instead be blamed on Mexico, China, and so on. The worst things get, the more crowd will cheer on Trump's and congress's bad policies, the more they punish Mexico and China, and the more they make bad policies worse.Consider the $15 minimum wage promoted by Bernie Sanders, a hateful populist demagogue who is, if anything, worse than Trump. Hillary wanted $12.Why not $18? Why not $25? Why not $100/hour minimum wage? Presumably, there are some negative thingies that happen the more you hike minimum wage. Presumably, there are some educated people out there who have studied this problem and can measure these things. And there are. An example is this non-partisan, Congressional Office of Management and Budget (OMB) analysis of raising minimum wage to $10.10. It describes numerous positive and negative effects, none of which fits in a demagogic sound bite.Raising the minimum wage has broad popular support, even among Republicans, because few are educated enough to appreciate the downsides. But yet, it doesn't get raised. The only explanation by populists like Bernie, or Trump, is that there must be some conspiracy (such as by Wall Street billionaires) that prevents the minimum wage from being raised. The truth is that our political leaders are basing their decision on things like the OMB report. They are basing their votes on an educated analysis of the policy, not on corruption and bribes from Wall Street. Note that there is no right or wrong answer to raising the minimum wage. There are reasonable people on both sides. It's just that this true debate based on education is far different than the public debate, which is based on emotion and ignorance.Trade, which both Bernie and Trump oppose, is the same way. Educated people are fo | Guideline |
To see everything:
Our RSS (filtrered)
