What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2025-02-05 14:00:00 | Mobile Indian Cyber Heist: FatBoyPanel And His Massive Data Breach (lien direct) | >Our zLabs research team has discovered a mobile malware campaign consisting of almost 900 malware samples primarily targeting users of Indian banks.
>Our zLabs research team has discovered a mobile malware campaign consisting of almost 900 malware samples primarily targeting users of Indian banks. |
Data Breach Malware Mobile | ★★★ | ||
| 2025-02-04 12:52:54 | Smiths Group Discloses Security Breach (lien direct) | Smiths Group, a multinational engineering business, has disclosed a data breach. The company, which is based in London but employees more than 15,000 people in over 50 countries, published a filing to the London Stock Exchange (LSE) on Tuesday saying that it is “currently managing a cyber security incident” involving “unauthorized access to the Company\'s [...]
Smiths Group, a multinational engineering business, has disclosed a data breach. The company, which is based in London but employees more than 15,000 people in over 50 countries, published a filing to the London Stock Exchange (LSE) on Tuesday saying that it is “currently managing a cyber security incident” involving “unauthorized access to the Company\'s [...] |
Data Breach | ★★★ | ||
| 2025-02-04 12:28:51 | Personal Information Compromised in GrubHub Data Breach (lien direct) | >Food delivery firm GrubHub has disclosed a data breach impacting the personal information of drivers and customers.
>Food delivery firm GrubHub has disclosed a data breach impacting the personal information of drivers and customers. |
Data Breach | ★★★ | ||
| 2025-02-04 04:24:46 | GrubHub data breach impacts customers, drivers, and merchants (lien direct) | Food delivery company GrubHub disclosed a data breach impacting the personal information of an undisclosed number of customers, merchants, and drivers after attackers breached its systems using a service provider account. [...]
Food delivery company GrubHub disclosed a data breach impacting the personal information of an undisclosed number of customers, merchants, and drivers after attackers breached its systems using a service provider account. [...] |
Data Breach | ★★★ | ||
| 2025-02-04 03:53:17 | What Is a Security Operations Center (SOC)? (lien direct) | Data breaches continue to cost organizations millions of dollars each year, with costs rising steadily. According to IBM\'s 2024 Cost of a Data Breach Report, the average cost of a data breach has surged to $4.88 million globally, reflecting the increasing complexity and sophistication of cyberattacks. In the United States, this figure is even higher, averaging $9.8 million per breach, and the healthcare industry remains a prime target, with an average breach cost of $10 million-the highest of any sector. What Drives These Staggering Costs? Several factors contribute to these sky-high figures...
Data breaches continue to cost organizations millions of dollars each year, with costs rising steadily. According to IBM\'s 2024 Cost of a Data Breach Report, the average cost of a data breach has surged to $4.88 million globally, reflecting the increasing complexity and sophistication of cyberattacks. In the United States, this figure is even higher, averaging $9.8 million per breach, and the healthcare industry remains a prime target, with an average breach cost of $10 million-the highest of any sector. What Drives These Staggering Costs? Several factors contribute to these sky-high figures... |
Data Breach Medical | ★★★ | ||
| 2025-02-03 18:38:35 | Mississippi electric utility warns 20,000 residents of data breach (lien direct) | The Yazoo Valley Electric Power Association initially warned customers in August of software problems. Last week, the utility disclosed that "unauthorized access" had led to a breach of sensitive customer information.
The Yazoo Valley Electric Power Association initially warned customers in August of software problems. Last week, the utility disclosed that "unauthorized access" had led to a breach of sensitive customer information. |
Data Breach | ★★ | ||
| 2025-02-03 15:24:46 | Japanese sportswear company Mizuno confirms data breach after 2024 ransomware claims (lien direct) | In a filing in the U.S., sports equipment manufacturer Mizuno says it discovered a data breach beginning in early November. The Japanese company did not specify how many customers were affected.
In a filing in the U.S., sports equipment manufacturer Mizuno says it discovered a data breach beginning in early November. The Japanese company did not specify how many customers were affected. |
Ransomware Data Breach | ★★★ | ||
| 2025-02-03 14:06:14 | 3rd February – Threat Intelligence Report (lien direct) | >For the latest discoveries in cyber research for the week of 3rd February, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Mizuno USA, giant sports equipment manufacturer, has confirmed a cyber-attack that resulted in the theft of personal information from its network between August and October 2024. The data breach included names, Social […]
>For the latest discoveries in cyber research for the week of 3rd February, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Mizuno USA, giant sports equipment manufacturer, has confirmed a cyber-attack that resulted in the theft of personal information from its network between August and October 2024. The data breach included names, Social […] |
Data Breach Threat | ★★ | ||
| 2025-02-03 11:10:48 | Insurance Company Globe Life Notifying 850,000 People of Data Breach (lien direct) | >Insurance firm Globe Life says a threat actor may have compromised the personal information of roughly 850,000 individuals.
>Insurance firm Globe Life says a threat actor may have compromised the personal information of roughly 850,000 individuals. |
Data Breach Threat | ★★★ | ||
| 2025-02-03 09:54:11 | (Déjà vu) 1 Million Impacted by Data Breach at Connecticut Healthcare Provider (lien direct) | >Community Health Center, Inc. says hackers stole the personal and health information of over one million individuals.
>Community Health Center, Inc. says hackers stole the personal and health information of over one million individuals. |
Data Breach Medical | ★★★ | ||
| 2025-01-31 21:53:14 | Community Health Center Data Breach Affects 1M Patients (lien direct) | The CHC remains operational, but a host of personal data is now in the hands of a "skilled cybercriminal," it said.
The CHC remains operational, but a host of personal data is now in the hands of a "skilled cybercriminal," it said. |
Data Breach | ★★ | ||
| 2025-01-31 14:59:40 | Insider Breach of the Month: A Departing Employee Takes a Trove of Data from a Large Law Firm (lien direct) | The Insider Breach of the Month blog series sheds light on the growing problem of email exfiltration of sensitive data to unauthorized accounts. It also examines how Proofpoint helps protect against these serious data loss events. Stories in this series have all been anonymized. Proofpoint regularly catches insider data loss events during our complimentary email data loss assessments. During these assessments, Proofpoint helps companies identify if their sensitive data is being exfiltrated to unauthorized email accounts, like personal freemail accounts, private domain email accounts or even a family member\'s email account. Today, we\'ll explore a major breach at a large law firm, which was caused by an employee who had accepted a role at another practice. The scenario In this case, the customer was a large law firm with locations in multiple countries. An employee accepted a new role at a competing firm and then proceeded to send multiple pages of attachments to their personal account. This exposed a massive amount of the law firm\'s sensitive data, putting it at risk for a data breach. The threat: How did the data loss happen? On the last day of their employment, the departing employee emailed the data to a personal email account. The chart below shows the anomalous activity in red. This reflects a typical pattern. When an employee leaves a company, there\'s often an increase in the volume and frequency of sensitive data being sent within a short span of time. Proofpoint Adaptive Email DLP chart that shows anomalous email pattern of the departing employee. The assessment: How Proofpoint identified this data loss We deployed Adaptive Email DLP to learn from and detect anomalies based on six months of historical email data. Adaptive Email DLP uses Proofpoint Nexus behavioral AI and the industry\'s broadest email data sets. This enables it to analyze working relationships to understand when sensitive data is being sent to unauthorized accounts rather than during regular business communication. By analyzing and learning normal email sending behaviors, trusted relationships and how users handle sensitive data, Adaptive Email DLP can detect when anomalous email behavior is occurring. During the assessment, Adaptive Email DLP identified unauthorized email accounts and anomalous activity related to the sensitive data that was sent to those accounts. Then, we met with the customer to review specific events where we detected sensitive data loss. As part of the review, we provided a list of all unauthorized accounts that were detected. We also provided all the emails that were sent to those accounts. Details about those emails included: Sender Recipient Subject Attachments Anonymized and redacted examples of the data that was exfiltrated. Prevention: What are the lessons learned? Here are some tips to stop your data from being sent to unauthorized accounts: Adopt a multilayered approach. Rules-based email data loss prevention (DLP) is critical in preventing sensitive data loss. However, it focuses on content and rules are based on known risks and specific RegEx patterns. An adaptive, behavioral approach is necessary to detect unknown risks that you can\'t define in a rule. Look for a tool that uses behavioral AI and machine learning. These technologies can analyze context and the relationships between a sender and a recipient, as well as other important details to detect whether data is being sent to an unauthorized account. Use in-the-moment warnings. With an adaptive approach, you can implement in-the-moment nudges that warn users when their behavior is risky. This helps them make informed decisions. Plus, it reinforces your security policies. And it prevents emails with sensitive data from leaving your organization. Proofpoint d | Data Breach Tool Threat | ★★ | ||
| 2025-01-31 10:24:38 | Globe Life data breach may impact an additional 850,000 clients (lien direct) | Insurance giant Globe Life finished the investigation into the data breach it suffered last June and says that the incident may have impacted an additional 850,000 customers. [...]
Insurance giant Globe Life finished the investigation into the data breach it suffered last June and says that the incident may have impacted an additional 850,000 customers. [...] |
Data Breach | ★★★ | ||
| 2025-01-31 10:12:06 | Mizuno USA says hackers stayed in its network for two months (lien direct) | Mizuno USA, a subsidiary of Mizuno Corporation, one of the world\'s largest sporting goods manufacturers, confirmed in data breach notification letters that unknown attackers stole files from its network between August and October 2024. [...]
Mizuno USA, a subsidiary of Mizuno Corporation, one of the world\'s largest sporting goods manufacturers, confirmed in data breach notification letters that unknown attackers stole files from its network between August and October 2024. [...] |
Data Breach | ★★ | ||
| 2025-01-31 09:53:02 | NorthBay Health Data Breach Impacts 569,000 Individuals (lien direct) | >NorthBay Health says hackers stole the personal information of 569,000 individuals in a 2024 ransomware attack.
>NorthBay Health says hackers stole the personal information of 569,000 individuals in a 2024 ransomware attack. |
Ransomware Data Breach | ★★ | ||
| 2025-01-31 08:18:29 | US healthcare provider data breach impacts 1 million patients (lien direct) | Community Health Center (CHC), a leading Connecticut healthcare provider, is notifying over 1 million patients that their personal and health information was stolen in an October breach. [...]
Community Health Center (CHC), a leading Connecticut healthcare provider, is notifying over 1 million patients that their personal and health information was stolen in an October breach. [...] |
Data Breach Medical | ★★ | ||
| 2025-01-30 11:32:13 | This month in security with Tony Anscombe – January 2025 edition (lien direct) | DeepSeek\'s bursting onto the AI scene, apparent shifts in US cybersecurity policies, and a massive student data breach all signal another eventful year in cybersecurity and data privacy
DeepSeek\'s bursting onto the AI scene, apparent shifts in US cybersecurity policies, and a massive student data breach all signal another eventful year in cybersecurity and data privacy |
Data Breach | ★ | ||
| 2025-01-30 11:20:00 | 152,000 Impacted by Data Breach at Berman & Rabin (lien direct) | Law firm Berman & Rabin says 152,000 people are impacted by a data breach resulting from a July 2024 ransomware attack.
Law firm Berman & Rabin says 152,000 people are impacted by a data breach resulting from a July 2024 ransomware attack. |
Ransomware Data Breach | ★★ | ||
| 2025-01-29 10:38:59 | Australia\\'s Health Sector Receives $6.4 Million Cybersecurity Boost with New Threat Information-Sharing Network (lien direct) | > The Australian Government has awarded a $6.4 million grant to CI-ISAC Australia, enabling the establishment of a new Health Cyber Sharing Network (HCSN). This initiative is designed to facilitate the rapid exchange of critical cyber threat information within Australia\'s healthcare industry, which has become a target for cyberattacks.
The recent surge in cyberattacks on Australian healthcare organizations, including hospitals and health insurance providers, has highlighted the pressing need for enhanced cybersecurity measures. In response, the Australian Government has made healthcare the priority sector for its formal funding efforts.
This grant is part of a broader strategy to address the vulnerabilities in the nation\'s health sector and ensure it is better equipped to handle the cyber threats faced by the industry.
A Growing Threat: The Cost of Cybersecurity Breaches
The healthcare industry globally has been facing increasing cybersecurity challenges, and Australia is no exception. According to reports from 2023, the global healthcare sector continues to experience the most expensive data breaches across industries for the 13th consecutive year. The average cost of a healthcare data breach was a staggering AUD$10.93 million, nearly double that of the financial industry, which recorded an average cost of $5.9 million.
Australia\'s health sector, which encompasses a diverse range of organizations, from public and private hospitals to medical clinics and insurance providers, is increasingly vulnerable to cyber threats. This sector includes approximately 750 government hospitals, 650 private hospitals, and over 6,500 general practitioner clinics, along with numerous third-party suppliers and vendors.
The creation of the HCSN aims to address these risks by providing a secure, collaborative platform for information sharing. The network will enable health sector organizations to work together more effectively, breaking down silos and improving the speed and quality of cybersecurity threat information exchange.
The Role of CI-ISAC and the Health Cyber-Sharing Network
CI-ISAC Australia, the recipient of the $6.4 million Australian Government grant, will spearhead the creation and management of the Health Cyber Sharing Network. The HCSN will focus on fostering collaboration between Australian healthcare organizations, ensuring they can share relevant
The Australian Government has awarded a $6.4 million grant to CI-ISAC Australia, enabling the establishment of a new Health Cyber Sharing Network (HCSN). This initiative is designed to facilitate the rapid exchange of critical cyber threat information within Australia\'s healthcare industry, which has become a target for cyberattacks.
The recent surge in cyberattacks on Australian healthcare organizations, including hospitals and health insurance providers, has highlighted the pressing need for enhanced cybersecurity measures. In response, the Australian Government has made healthcare the priority sector for its formal funding efforts.
This grant is part of a broader strategy to address the vulnerabilities in the nation\'s health sector and ensure it is better equipped to handle the cyber threats faced by the industry.
A Growing Threat: The Cost of Cybersecurity Breaches
The healthcare industry globally has been facing increasing cybersecurity challenges, and Australia is no exception. According to reports from 2023, the global healthcare sector continues to experience the most expensive data breaches across industries for the 13th consecutive year. The average cost of a healthcare data breach was a staggering AUD$10.93 million, nearly double that of the financial industry, which recorded an average cost of $5.9 million.
Australia\'s health sector, which encompasses a diverse range of organizations, from public and private hospitals to medical clinics and insurance providers, is increasingly vulnerable to cyber threats. This sector includes approximately 750 government hospitals, 650 private hospitals, and over 6,500 general practitioner clinics, along with numerous third-party suppliers and vendors.
The creation of the HCSN aims to address these risks by providing a secure, collaborative platform for information sharing. The network will enable health sector organizations to work together more effectively, breaking down silos and improving the speed and quality of cybersecurity threat information exchange.
The Role of CI-ISAC and the Health Cyber-Sharing Network
CI-ISAC Australia, the recipient of the $6.4 million Australian Government grant, will spearhead the creation and management of the Health Cyber Sharing Network. The HCSN will focus on fostering collaboration between Australian healthcare organizations, ensuring they can share relevant |
Data Breach Vulnerability Threat Medical Cloud | ★★★ | ||
| 2025-01-29 00:59:10 | MGM agrees to pay $45 million to victims of 2019 data breach and 2023 ransomware attack (lien direct) | MGM Resorts International agreed to pay $45 million to settle multiple class action lawsuits related to a data breach in 2019 and a ransomware attack the company experienced in 2023.
MGM Resorts International agreed to pay $45 million to settle multiple class action lawsuits related to a data breach in 2019 and a ransomware attack the company experienced in 2023. |
Ransomware Data Breach | ★★★ | ||
| 2025-01-28 12:45:00 | Mega Data Breaches Push US Victim Count to 1.7 Billion (lien direct) | The number of data breach victims increased 312% annually to exceed 1.7 billion in 2024, according to the ITRC 2024 Annual Data Breach Report
The number of data breach victims increased 312% annually to exceed 1.7 billion in 2024, according to the ITRC 2024 Annual Data Breach Report |
Data Breach | ★★ | ||
| 2025-01-28 10:43:31 | PowerSchool starts notifying victims of massive data breach (lien direct) | Education software giant PowerSchool has started notifying individuals in the U.S. and Canada whose personal data was exposed in a late December 2024 cyberattack. [...]
Education software giant PowerSchool has started notifying individuals in the U.S. and Canada whose personal data was exposed in a late December 2024 cyberattack. [...] |
Data Breach | ★★ | ||
| 2025-01-27 16:50:26 | TalkTalk Confirms Data Breach, Downplays Impact (lien direct) | >UK telecoms firm TalkTalk has confirmed falling victim to a data breach after a threat actor boasted about hacking it.
>UK telecoms firm TalkTalk has confirmed falling victim to a data breach after a threat actor boasted about hacking it. |
Data Breach Threat | ★★★ | ||
| 2025-01-27 11:26:55 | Change Healthcare Data Breach Impact Grows to 190 Million Individuals (lien direct) | >The impact of the Change Healthcare ransomware-caused data breach has increased from 100 million to 190 million individuals.
>The impact of the Change Healthcare ransomware-caused data breach has increased from 100 million to 190 million individuals. |
Data Breach Medical | ★★ | ||
| 2025-01-27 01:19:44 | Cybersecurity Stop of the Month: E-Signature Phishing Nearly Sparks Disaster for an Electric Company (lien direct) | The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today\'s cybercriminals and how Proofpoint helps organizations better fortify their email defenses to protect people against today\'s emerging threats. Phishing remains the No. 1 tactic that cybercriminals use to target your people and steal valuable data and funds. According to Verizon, phishing is the top method that attackers use to gain unauthorized access, and it continues to evolve in both frequency and sophistication. This trend is not just alarming-it\'s costly. IBM estimates the average data breach that originates with phishing causes a staggering $4.88 million in damages. In this post, we\'ll analyze a new and complex e-signature phishing threat. In it, attackers combine several novel tactics to get around native Microsoft email security. Background In an e-signature phishing attack, bad actors will spoof a trusted brand and send malicious content through legitimate digital channels. Often, they use advanced methods like adversary-in-the-middle (AitM) to bypass multifactor authentication (MFA) in an effort to further extend their access. And when bad actors use combined tactics, such as Adversary-in-the-Middle plus geofencing, they can be extremely successful in evading detection. Let\'s look at e-signature phishing attacks in more depth: Impersonating trusted brands Threat actors leverage brands and services of trusted electronic signature services, such as DocuSign or Adobe Sign. They use them to trick recipients into directly downloading malicious documents or visiting fake websites where they enter their login credentials. Of the billions of phishing emails that Proofpoint sees each year, our 2024 State of the Phish report shows that 3.5M malicious messages abused DocuSign branding. Bypassing MFA Attackers that use e-signature phishing lures frequently seek more than just credentials. They also aim to intercept MFA codes or steal session cookies. Adversary-in-the-middle (AitM) tactics use proxy sites to capture login details and MFA codes in real-time. This grants attackers access to the victim\'s account and any active session cookies which can, in turn, unlock other websites. Steps in the adversary-in-the-middle threat technique. Geofencing access Threat actors use geofencing techniques to limit from where their targets can access their phishing sites or malicious content. By restricting access to specific geographic locations, such as the target\'s region or country, they reduce the likelihood of detection by IT teams and automated security scanning tools based in other regions. Deploying just one of these tactics can be enough to convince your people to take action. But what happens when a savvy scammer uses all three? The scenario Our recent example shows how combining the methods above enabled a threat actor to successfully target a global electric company. The threat actor\'s intended victim supplies power to one of the world\'s largest cities and employs more than 15K people. In this attack, the offending message was delivered to the mailbox of a C-suite executive. It bypassed Microsoft security tools as well as additional detection meant to stop such multi-stage campaigns. Thankfully, Proofpoint caught this threat and helped secure the company from a possible cyberattack or data breach. The named threat actor launching this threat was first observed by Proofpoint in 2021. They are known for using delivery mechanisms like multistep redirection chains, advanced filtering and highly customized lures. Frequent targets include the manufacturing, technology and energy industries. While they often spoof brands like Microsoft OneDrive and LinkedIn, in this e-signature-based phishing attack they chose popular digital transaction management platform, DocuSign. The threat: How did the attack happen? Here\'s how the attack unfolded: 1. Setting a lure. The attack started with an email that spoofed DocuSign\'s brand to appear as a legitimate follow up notice. It offered the recipient | Data Breach Malware Tool Threat Prediction Medical Cloud | ★★★★ | ||
| 2025-01-26 11:29:17 | UnitedHealth now says 190 million impacted by 2024 data breach (lien direct) | UnitedHealth has revealed that 190 million Americans had their personal and healthcare data stolen in the Change Healthcare ransomware attack, nearly doubling the previously disclosed figure. [...]
UnitedHealth has revealed that 190 million Americans had their personal and healthcare data stolen in the Change Healthcare ransomware attack, nearly doubling the previously disclosed figure. [...] |
Ransomware Data Breach Medical | ★★★ | ||
| 2025-01-25 17:05:12 | UnitedHealth Group\\'s Massive Data Breach Impacts 190 Million Americans (lien direct) | UnitedHealth Group has confirmed that a ransomware attack targeted its subsidiary, Change Healthcare, in February 2024, impacting 190…
UnitedHealth Group has confirmed that a ransomware attack targeted its subsidiary, Change Healthcare, in February 2024, impacting 190… |
Ransomware Data Breach Medical | ★★ | ||
| 2025-01-25 16:23:24 | TalkTalk investigates breach after data for sale on hacking forum (lien direct) | UK telecommunications company TalkTalk is investigating a third-party supplier data breach after a threat actor began selling alleged customer data on a hacking forum. [...]
UK telecommunications company TalkTalk is investigating a third-party supplier data breach after a threat actor began selling alleged customer data on a hacking forum. [...] |
Data Breach Threat | ★★ | ||
| 2025-01-25 12:52:12 | UnitedHealth updates number of data breach victims to 190 million (lien direct) | The 2024 ransomware attack on Change Healthcare exposed the data of about 190 million people, according to an update from parent company UnitedHealth Group.
The 2024 ransomware attack on Change Healthcare exposed the data of about 190 million people, according to an update from parent company UnitedHealth Group. |
Ransomware Data Breach Medical | ★★ | ||
| 2025-01-25 10:15:25 | PayPal to pay $2 million settlement over 2022 data breach (lien direct) | New York State has announced a $2,000,000 settlement with PayPal over charges it failed to comply with the state\'s cybersecurity regulations, leading to a 2022 data breach. [...]
New York State has announced a $2,000,000 settlement with PayPal over charges it failed to comply with the state\'s cybersecurity regulations, leading to a 2022 data breach. [...] |
Data Breach | ★★★ | ||
| 2025-01-24 16:52:21 | PayPal penalized $2 million over data breach involving 35K Social Security numbers (lien direct) | The fine will settle violations of New York\'s financial cybersecurity regulation requiring companies like PayPal to have an adequate cyber posture.
The fine will settle violations of New York\'s financial cybersecurity regulation requiring companies like PayPal to have an adequate cyber posture. |
Data Breach | ★★ | ||
| 2025-01-24 12:00:00 | Millions Impacted by PowerSchool Data Breach (lien direct) | >Four decades of student and educator information was stolen from PowerSchool – tens of millions are potentially affected.
>Four decades of student and educator information was stolen from PowerSchool – tens of millions are potentially affected. |
Data Breach | ★★ | ||
| 2025-01-24 02:58:23 | New Law Could Mean Prison for Reporting Data Leaks (lien direct) | The Turkish government is proposing a controversial new cybersecurity law that could make it a criminal act to report on data breaches. The new legislation proposes penalties for various cybersecurity-related offences. But they key one which has people concerned is this: "Those who carry out activities aimed at targeting institutions or individuals by creating the perception that there has been a data breach in cyberspace, even though there has been no data breach, shall be sentenced to imprisonment for a term of two to five years." The problem is, of course, that such a law may discourage the...
The Turkish government is proposing a controversial new cybersecurity law that could make it a criminal act to report on data breaches. The new legislation proposes penalties for various cybersecurity-related offences. But they key one which has people concerned is this: "Those who carry out activities aimed at targeting institutions or individuals by creating the perception that there has been a data breach in cyberspace, even though there has been no data breach, shall be sentenced to imprisonment for a term of two to five years." The problem is, of course, that such a law may discourage the... |
Data Breach Legislation | ★★★ | ||
| 2025-01-23 12:30:57 | Data breach hitting PowerSchool looks very, very bad (lien direct) | Schools are now notifying families their data has been stolen.
Schools are now notifying families their data has been stolen. |
Data Breach | ★★★ | ||
| 2025-01-23 03:14:52 | You Can\\'t Trust Hackers, and Other Data Breach Verification Tales (lien direct) | It's hard to find a good criminal these days. I mean a really trustworthy one you can be confident won't lead you up the garden path with false promises of data breaches. Like this guy yesterday: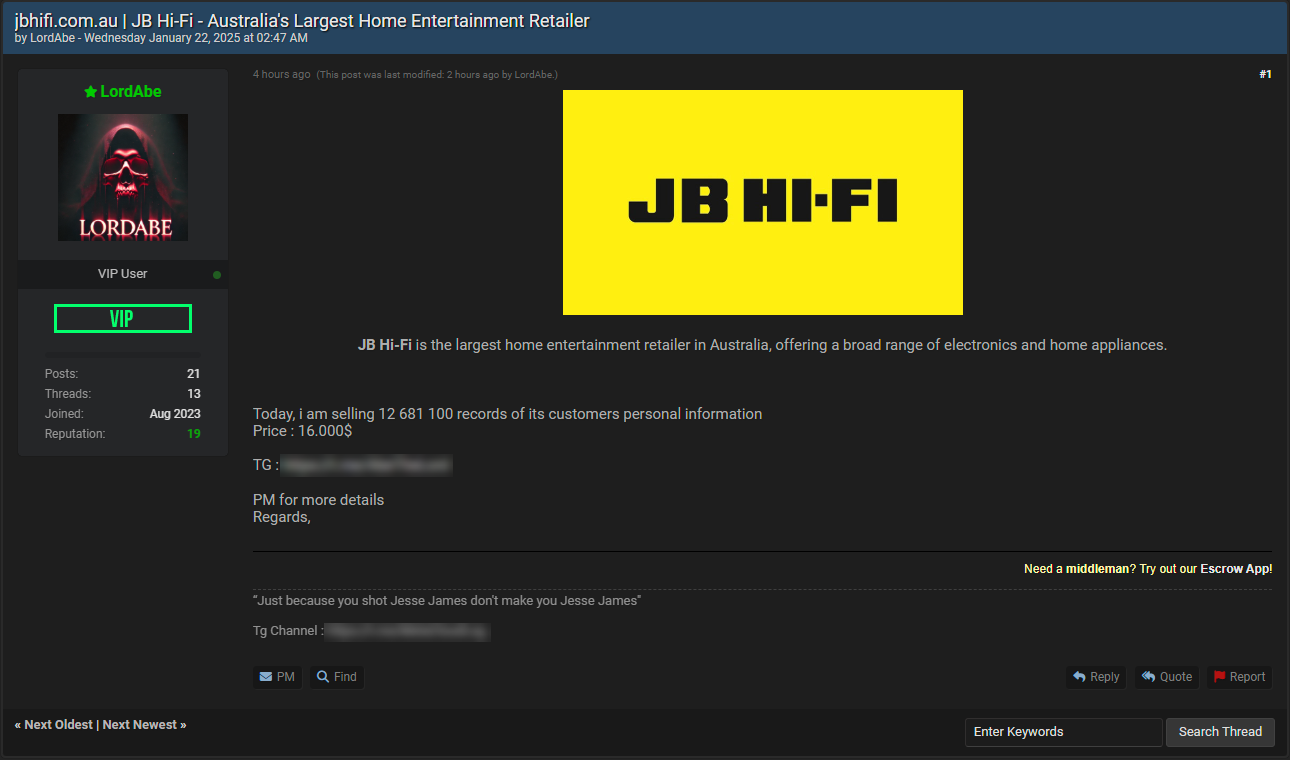 For my international friends, JB Hi-Fi is a massive electronics For my international friends, JB Hi-Fi is a massive electronics
It's hard to find a good criminal these days. I mean a really trustworthy one you can be confident won't lead you up the garden path with false promises of data breaches. Like this guy yesterday:  For my international friends, JB Hi-Fi is a massive electronics For my international friends, JB Hi-Fi is a massive electronics |
Data Breach | ★★★ | ||
| 2025-01-22 13:10:18 | Cyber Security Tips for Educators and Parents (lien direct) | >The numbers are staggering: the average number of weekly cyber attacks per organization rose to 1,673 in 2024, a 44% increase compared to the previous year, according to Check Point\'s The State of Cyber Security 2025 report. Among all sectors, education has been hit hardest, enduring a 75% year-over-year increase to a shocking 3,574 weekly attacks. Educational institutions have become prime targets for cyber criminals due to the wealth of personal information they manage. Most attacks originate from email (68%), with web-delivered attacks accounting for 32%, often involving malicious frameworks like FakeUpdates. The recent PowerSchool data breach illustrates the severe […]
>The numbers are staggering: the average number of weekly cyber attacks per organization rose to 1,673 in 2024, a 44% increase compared to the previous year, according to Check Point\'s The State of Cyber Security 2025 report. Among all sectors, education has been hit hardest, enduring a 75% year-over-year increase to a shocking 3,574 weekly attacks. Educational institutions have become prime targets for cyber criminals due to the wealth of personal information they manage. Most attacks originate from email (68%), with web-delivered attacks accounting for 32%, often involving malicious frameworks like FakeUpdates. The recent PowerSchool data breach illustrates the severe […] |
Data Breach | ★★★ | ||
| 2025-01-21 20:30:38 | HPE Investigates After Alleged Data Breach (lien direct) | The company reports that it is not experiencing any operational issues within its business, so far.
The company reports that it is not experiencing any operational issues within its business, so far. |
Data Breach | ★★★ | ||
| 2025-01-21 19:40:15 | Disciplinary and special ed records of Toronto students may have leaked in PowerSchool breach (lien direct) | The data breach at the educational software company may affect millions of students at Toronto public schools - one of thousands of districts using PowerSchool tools.
The data breach at the educational software company may affect millions of students at Toronto public schools - one of thousands of districts using PowerSchool tools. |
Data Breach Tool | ★★★ | ||
| 2025-01-21 15:36:23 | HPE Investigates Hacker’s Claim Of Selling Stolen Source Code (lien direct) | Hewlett Packard Enterprise (HPE) has launched an investigation into a new data breach after a threat actor claimed to have stolen sensitive information from the tech giant\'s systems.
The investigation follows an announcement by the prominent and notorious threat actor “IntelBroker,” who took to BreachForums on January 16th to announce that they are selling files reportedly obtained from HPE’s networks.
For those unaware, IntelBroker is infamous for breaching major organizations like Cisco, Nokia, Europol, and AMD, often stealing and selling sensitive data on cybercrime forums.
Regarding HPE, the compromised data allegedly includes source code for products like Zerto and iLO, private Github repositories, Docker builds, SAP Hybris, Certificates (private and public keys), and even some old user personal identifiable information (PII) used for deliveries.
IntelBroker is also offering selling access to some HPE services, including APIs, WePay, GitHub, GitLab and more.
“Today, I am selling the HPE data breach,” IntelBroker wrote in a BreachForums post. “We have been connecting to some of their services for about 2 days now.”
HPE said it is investigating the breach claims but has found no evidence of a security breach.
It added that there is no operational impact on the company and no evidence that customer information was involved in the cyber incident.
“HPE became aware on January 16 of claims being made by a group called IntelBroker that it was in possession of information belonging to HPE. HPE immediately activated our cyber response protocols, disabled related credentials, and launched an investigation to evaluate the validity of the claims,” an HPE spokesperson said in a statement.
This is not the first time IntelBroker has made such breach claims against HPE. In February 2024, the threat actor claimed to have breached HPE and offered the company\'s stolen data for sale, which reportedly included Continuous Integration/Continuous Deployment (CI/CD) access, system logs, configuration files, access tokens, HPE StoreOnce files (such as serial numbers and warranty information), and access passwords, including email services.
Hewlett Packard Enterprise (HPE) has launched an investigation into a new data breach after a threat actor claimed to have stolen sensitive information from the tech giant\'s systems. The investigation follows an announcement by the prominent and notorious threat actor “IntelBroker,” who took to BreachForums on January 16th to announce that they are selling files reportedly obtained from HPE’s networks. For those unaware, IntelBroker is infamous for breaching major organizations like Cisco, Nokia, Europol, and AMD, often stealing and selling sensitive data on cybercrime forums. Regarding HPE, the compromised data allegedly includes source code for products like Zerto and iLO, private Github repositories, Docker builds, SAP Hybris, Certificates (private and public keys), and even some old user personal identifiable information (PII) used for deliveries. IntelBroker is also offering selling access to some HPE services, including APIs, WePay, GitHub, GitLab and more. “Today, I am selling the HPE data breach,” IntelBroker wrote in a BreachForums post. “We have been connecting to some of their services for about 2 days now.” HPE said it is investigating the breach claims but has found no evidence of a security breach. It added that there is no operational impact on the company and no evidence that customer information was involved in the cyber incident. “HPE became aware on January 16 of claims being made by a group called IntelBroker t |
Data Breach Threat | ★★★ | ||
| 2025-01-20 16:40:00 | HPE Launches Investigation After Hacker Claims Data Breach (lien direct) | HPE is investigating claims of data breach by hacker IntelBroker, who offered stolen files for sale
HPE is investigating claims of data breach by hacker IntelBroker, who offered stolen files for sale |
Data Breach | ★★★ | ||
| 2025-01-20 16:40:00 | Product Walkthrough: How Satori Secures Sensitive Data From Production to AI (lien direct) | Every week seems to bring news of another data breach, and it\'s no surprise why: securing sensitive data has become harder than ever. And it\'s not just because companies are dealing with orders of magnitude more data. Data flows and user roles are constantly shifting, and data is stored across multiple technologies and cloud environments. Not to mention, compliance requirements are only getting
Every week seems to bring news of another data breach, and it\'s no surprise why: securing sensitive data has become harder than ever. And it\'s not just because companies are dealing with orders of magnitude more data. Data flows and user roles are constantly shifting, and data is stored across multiple technologies and cloud environments. Not to mention, compliance requirements are only getting |
Data Breach Cloud | Satori | ★★★ | |
| 2025-01-20 15:44:27 | Alleged data breach at North Pole Company Canada: 500,000 users could be affected (lien direct) | […] | Data Breach | ★★★ | ||
| 2025-01-20 15:03:57 | 20th January– Threat Intelligence Report (lien direct) | >For the latest discoveries in cyber research for the week of 20th January, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Hotel management platform Otelier has suffered a data breach that resulted in extraction of almost eight terabytes of data. The threat actors compromised company\'s Amazon S3 cloud storage, stealing guests’ personal information […]
>For the latest discoveries in cyber research for the week of 20th January, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Hotel management platform Otelier has suffered a data breach that resulted in extraction of almost eight terabytes of data. The threat actors compromised company\'s Amazon S3 cloud storage, stealing guests’ personal information […] |
Data Breach Threat Cloud | ★★★ | ||
| 2025-01-17 15:17:22 | Otelier data breach exposes info, hotel reservations of millions (lien direct) | Hotel management platform Otelier suffered a data breach after threat actors breached its Amazon S3 cloud storage to steal millions of guests\' personal information and reservations for well-known hotel brands like Marriott, Hilton, and Hyatt. [...]
Hotel management platform Otelier suffered a data breach after threat actors breached its Amazon S3 cloud storage to steal millions of guests\' personal information and reservations for well-known hotel brands like Marriott, Hilton, and Hyatt. [...] |
Data Breach Threat Cloud | ★★★ | ||
| 2025-01-16 11:26:41 | Wolf Haldenstein law firm says 3.5 million impacted by data breach (lien direct) | Wolf Haldenstein Adler Freeman & Herz LLP ("Wolf Haldenstein") reports it has suffered a data breach that exposed the personal information of nearly 3.5 million individuals to hackers. [...]
Wolf Haldenstein Adler Freeman & Herz LLP ("Wolf Haldenstein") reports it has suffered a data breach that exposed the personal information of nearly 3.5 million individuals to hackers. [...] |
Data Breach | ★★ | ||
| 2025-01-15 21:44:31 | OneBlood reports data breach to state regulators after ransomware attack (lien direct) | The blood donation organization notified regulators that sensitive data was stolen, nearly five months after a ransomware attack hampered its operations.
The blood donation organization notified regulators that sensitive data was stolen, nearly five months after a ransomware attack hampered its operations. |
Ransomware Data Breach | ★★★ | ||
| 2025-01-15 14:44:28 | Label giant Avery says website hacked to steal credit cards (lien direct) | Avery Products Corporation is warning it suffered a data breach after its website was hacked to steal customers\' credit cards and personal information. [...]
Avery Products Corporation is warning it suffered a data breach after its website was hacked to steal customers\' credit cards and personal information. [...] |
Data Breach | ★★★ | ||
| 2025-01-13 16:25:00 | How Hackers Steal Your Password (lien direct) | Password Crackers – How Hackers Get Passwords In today’s digital business environment, passwords are often the keys to your organization’s most sensitive assets—from financial records and customer accounts to intellectual property. Unfortunately, hackers are constantly developing methods to steal these passwords and gain unauthorized access. Understanding the techniques they use and how employees can protect themselves is crucial for maintaining digital security. This article explores how hackers crack passwords, the tools and techniques they employ, and the strategies your organization can adopt to safeguard online accounts. Password Hacker Dangers Password hacking, also known as password cracking, refers to the process of uncovering or bypassing passwords to gain unauthorized access to systems, accounts, or data. It stands as one of the most serious cyberthreats today, with hackers using both high-tech tools, such as advanced algorithms and automated software, and low-tech methods, like social engineering or physical observation. These attacks have led to devastating breaches, including the 2016 Democratic Party data leak, underscoring the critical importance of strong password security. Organizations and individuals must remain vigilant against this persistent threat to protect sensitive information. What Motivates Password Crackers Password cracking involves uncovering passwords from stored data or data transfers using specialized software and techniques. Hackers are often financially motivated, seeking to monetize stolen credentials by leaking sensitive information, committing fraud, or selling access to compromised accounts. Additionally, some hackers pursue data theft to disrupt organizations or exploit their intellectual property. By understanding these motivations, organizations can better appreciate the importance of robust password security measures to protect their assets and reputation. Types of Password Cracking To understand the threat, let’s explore the common ways hackers steal passwords: Phishing: Fake websites or deceptive emails trick users into entering their credentials, which hackers then capture for unauthorized access. Social Engineering: Hackers manipulate individuals into revealing passwords by exploiting trust, fear, or curiosity, often posing as IT support or sending urgent alerts. Keylogging: Malware-based keyloggers record every keystroke, including passwords. Brute Force Attacks: Password-cracking tools attempt every possible character combination until the correct password is found. This is particularly effective against weak passwords. Dictionary Attacks: A subset of brute force attacks, these use precompiled lists of common passwords and words to guess credentials. Credential Stuffing: Hackers exploit reused username-password combinations from previous breaches to access multiple accounts. Man-in-the-Middle (MitM) Attacks: Hackers intercept data during transmission, capturing passwords entered during login. Data Breaches: Cyberattacks on companies can expose millions of passwords, which are often sold or published on the dark web. Common Password Cracking Methods Hackers also use advanced techniques, such as: Rainbow Tables: Precomputed information on digital signatures that speed up the decryption of hashed passwords Password Spraying: Testing common passwords across many accounts to avoid detection Offline Cracking: Decrypting encrypted password files without interacting directly with users Shoulder Surfing: Physically observing someone typing their password Malware: Extracting stored pas | Data Breach Tool Vulnerability Threat Cloud | ★★★ | ||
| 2025-01-13 11:22:47 | Hackers Breach Telefonica Network, Leak 2.3 GB of Data Online (lien direct) | Telefónica faces a data breach impacting its internal systems, linked to hackers using compromised credentials. Learn more about this alarming cyber threat.
Telefónica faces a data breach impacting its internal systems, linked to hackers using compromised credentials. Learn more about this alarming cyber threat. |
Data Breach Threat | ★★★ | ||
| 2025-01-13 05:15:16 | Medusind Data Breach Exposes Over 360,000 Individuals\\' Healthcare Info (lien direct) | Medusind, a healthcare revenue cycle management provider, has disclosed a data breach that compromised the personal and health information of 360,934 people. The breach, which happened over a year ago, affirms the ongoing cybersecurity challenges in the healthcare sector. The company, which operates 12 locations across the US and India and supports more than 6,000 [...]
Medusind, a healthcare revenue cycle management provider, has disclosed a data breach that compromised the personal and health information of 360,934 people. The breach, which happened over a year ago, affirms the ongoing cybersecurity challenges in the healthcare sector. The company, which operates 12 locations across the US and India and supports more than 6,000 [...] |
Data Breach Medical | ★★★ |
To see everything:
Our RSS (filtrered)
