What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-08-10 12:36:30 | DTX Europe 2023 (lien direct) | DTX rassemble des esprits créatifs, des experts techniques et les derniers outils nécessaires pour stimuler le changement et générer de la valeur dans les organisations d'aujourd'hui.«Votre maison de transformation numérique» couvrant le cloud, les réseaux et les infrastructures;données, analyses et IA;Génie logiciel et DevOps;et la cybersécurité, l'événement présente la technologie, les solutions et les stratégies essentielles pour faire avancer les projets numériques [& # 8230;]
DTX brings together creative minds, technical experts and the latest tools needed to drive change and generate value across today\'s organisations. “Your Home of Digital Transformation” Covering cloud, networks and infrastructure; data, analytics and AI; software engineering and DevOps; and cyber security, the event showcases the technology, solutions and strategies essential to advance digital projects […] |
Tool | ★★★ | ||
| 2023-08-10 12:01:36 | Rendre le chrome plus sécurisé en apportant une épingle clé sur Android Making Chrome more secure by bringing Key Pinning to Android (lien direct) |
Posted by David Adrian, Joe DeBlasio and Carlos Joan Rafael Ibarra Lopez, Chrome Security
Chrome 106 added support for enforcing key pins on Android by default, bringing Android to parity with Chrome on desktop platforms. But what is key pinning anyway?
One of the reasons Chrome implements key pinning is the “rule of two”. This rule is part of Chrome\'s holistic secure development process. It says that when you are writing code for Chrome, you can pick no more than two of: code written in an unsafe language, processing untrustworthy inputs, and running without a sandbox. This blog post explains how key pinning and the rule of two are related.
The Rule of Two
 Chrome is primarily written in the C and C++ languages, which are vulnerable to memory safety bugs. Mistakes with pointers in these languages can lead to memory being misinterpreted. Chrome invests in an ever-stronger multi-process architecture built on sandboxing and site isolation to help defend against memory safety problems. Android-specific features can be written in Java or Kotlin. These languages are memory-safe in the common case. Similarly, we\'re working on adding support to write Chrome code in Rust, which is also memory-safe.
Much of Chrome is sandboxed, but the sandbox still requires a core high-privilege “broker” process to coordinate communication and launch sandboxed processes. In Chrome, the broker is the browser process. The browser process is the source of truth that allows the rest of Chrome to be sandboxed and coordinates communication between the rest of the processes.
If an attacker is able to craft a malicious input to the browser process that exploits a bug and allows the attacker to achieve remote code execution (RCE) in the browser process, that would effectively give the attacker full control of the victim\'s Chrome browser and potentially the rest of the device. Conversely, if an attacker achieves RCE in a sandboxed process, such as a renderer, the attacker\'s capabilities are extremely limited. The attacker cannot reach outside of the sandbox unless they can additionally exploit the sandbox itself.
Without sandboxing, which limits the actions an attacker can take, and without memory safety, which removes the ability of a bug to disrupt the intended control flow of the program, the rule of two requires that the browser process does not handle untrustworthy inputs. The relative risks between sandboxed processes and the browser process are why the browser process is only allowed to parse trustworthy inputs and specific IPC messages.
Trustworthy inputs are defined extremely strictly: A “trustworthy source” means that Chrome can prove that the data comes from Google. Effectively, this means that in situations where the browser process needs access to data from e
Chrome is primarily written in the C and C++ languages, which are vulnerable to memory safety bugs. Mistakes with pointers in these languages can lead to memory being misinterpreted. Chrome invests in an ever-stronger multi-process architecture built on sandboxing and site isolation to help defend against memory safety problems. Android-specific features can be written in Java or Kotlin. These languages are memory-safe in the common case. Similarly, we\'re working on adding support to write Chrome code in Rust, which is also memory-safe.
Much of Chrome is sandboxed, but the sandbox still requires a core high-privilege “broker” process to coordinate communication and launch sandboxed processes. In Chrome, the broker is the browser process. The browser process is the source of truth that allows the rest of Chrome to be sandboxed and coordinates communication between the rest of the processes.
If an attacker is able to craft a malicious input to the browser process that exploits a bug and allows the attacker to achieve remote code execution (RCE) in the browser process, that would effectively give the attacker full control of the victim\'s Chrome browser and potentially the rest of the device. Conversely, if an attacker achieves RCE in a sandboxed process, such as a renderer, the attacker\'s capabilities are extremely limited. The attacker cannot reach outside of the sandbox unless they can additionally exploit the sandbox itself.
Without sandboxing, which limits the actions an attacker can take, and without memory safety, which removes the ability of a bug to disrupt the intended control flow of the program, the rule of two requires that the browser process does not handle untrustworthy inputs. The relative risks between sandboxed processes and the browser process are why the browser process is only allowed to parse trustworthy inputs and specific IPC messages.
Trustworthy inputs are defined extremely strictly: A “trustworthy source” means that Chrome can prove that the data comes from Google. Effectively, this means that in situations where the browser process needs access to data from e |
Tool | ★★ | ||
| 2023-08-09 21:39:00 | DARPA lance un concours de deux ans pour construire des outils d'IA pour réparer les vulnérabilités DARPA Launches Two-Year Contest to Build AI Tools to Fix Vulnerabilities (lien direct) |
Un défi sera offert aux équipes pour créer des outils à l'aide de l'IA afin de résoudre les défis de vulnérabilité de l'Open Source.
A challenge will be offered to teams to build tools using AI in order to solve open source\'s vulnerability challenges. |
Tool Vulnerability | ★★ | ||
| 2023-08-09 20:38:00 | Un nouvel outil LLM cherche et corrige les vulnérabilités New LLM Tool Seeks and Remediates Vulnerabilities (lien direct) |
Vicarius a lancé vuln_gpt, qui, selon lui, générera et exécutera des scripts pour améliorer les défauts tels que la porte arrière Tetra.
Vicarius launched vuln_GPT, which it says will generate and execute scripts to ameliorate flaws such as the TETRA backdoor. |
Tool Vulnerability | ★★ | ||
| 2023-08-09 18:15:10 | CVE-2022-48580 (lien direct) | Une vulnérabilité d'injection de commande existe dans la fonction d'outil de périphérique Ping ARP de ScienceLogic SL1 qui prend une entrée contrôlée par l'utilisateur non animé et la transmet directement à une commande shell.Cela permet & acirc; & nbsp; l'injection de commandes arbitraires au système d'exploitation sous-jacent.
A command injection vulnerability exists in the ARP ping device tool feature of the ScienceLogic SL1 that takes unsanitized user controlled input and passes it directly to a shell command. This allows for the injection of arbitrary commands to the underlying operating system. |
Tool Vulnerability | |||
| 2023-08-09 17:06:00 | Validation de sécurité continue avec les tests de pénétration en tant que service (PTAAS) Continuous Security Validation with Penetration Testing as a Service (PTaaS) (lien direct) |
Validez la sécurité en continu à travers votre pile complète avec test de stylo en tant que service.
Dans le centre d'opérations de sécurité moderne d'aujourd'hui (SOC), c'est une bataille entre les défenseurs et les cybercriminels.Les deux utilisent des outils et de l'expertise & # 8211;Cependant, les cybercriminels ont l'élément de surprise de leur côté et une multitude de tactiques, de techniques et de procédures (TTP) qui ont évolué.Ces externes
Validate security continuously across your full stack with Pen Testing as a Service. In today\'s modern security operations center (SOC), it\'s a battle between the defenders and the cybercriminals. Both are using tools and expertise – however, the cybercriminals have the element of surprise on their side, and a host of tactics, techniques, and procedures (TTPs) that have evolved. These external |
Tool | ★★★★ | ||
| 2023-08-09 16:26:00 | Sweet Security débute la gestion de l'exécution pour le cloud Sweet Security Debuts Runtime Management for Cloud (lien direct) |
Les outils de détection existants fournissent des fonctionnalités limitées ou sont optimisées pour le cloud, affirme les startups israéliennes.
Existing detection tools either provide limited functionality or aren\'t optimized for the cloud, Israeli startup claims. |
Tool Cloud | ★★ | ||
| 2023-08-09 14:35:00 | La base de données sur les risques d'IA aborde les risques de la chaîne d'approvisionnement de l'IA AI Risk Database Tackles AI Supply Chain Risks (lien direct) |
L'outil open source - une collaboration entre Robust Intelligence, Mitre et Indiana University - évalue les modèles d'apprentissage automatique fortement partagé pour le risque.
The open source tool - a collaboration between Robust Intelligence, MITRE, and Indiana University - assesses heavily shared, public machine learning models for risk. |
Tool | ★★★ | ||
| 2023-08-09 13:00:00 | Découvrir les vulnérabilités de sécurité cachées avec un sast plus profond Uncovering hidden security vulnerabilities with deeper SAST (lien direct) |
Découvrir les vulnérabilités de sécurité est particulièrement difficile car ces problèmes peuvent être complexes et profondément cachés lorsque votre code utilise et interagit avec le code de dépendance tiers.Nous sommes ravis de partager davantage sur une percée majeure dans notre détection de vulnérabilités de sécurité profondément cachées que les outils traditionnels ne peuvent pas détecter.
Uncovering security vulnerabilities is particularly challenging because these issues can be complex and deeply hidden when your code uses and interacts with third-party dependency code. We are excited to share more about a major breakthrough in our detection of deeply hidden security vulnerabilities that traditional tools cannot detect. |
Tool Vulnerability | ★★ | ||
| 2023-08-09 10:00:00 | Attention à l'écart (d'interprétation): une autre raison pour laquelle la modélisation des menaces est importante Mind the (Interpretation) gap: Another reason why threat modeling is important (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Where do vulnerabilities fit with respect to security standards and guidelines? Was it a coverage issue or an interpretation and implementation issue? Where does a product, environment, organization, or business vertical fail the most in terms of standards requirements? These questions are usually left unanswered because of the gap between standards or regulations on the one hand, and requirements interpretation and implementation, on the other. Certified products and environments often suffer from security issues that were supposed to be covered by the requirements of the standard. In [1], for instance, the authors give examples of vulnerable products that were IEC 62443 certified. In [2], SANS discusses the case of PCI-certified companies and why they are still being breached. This “interpretation gap,” whether it manifests in the implementation of requirements or in the assessment process, hinders security and leads to the fact that being compliant is not necessarily the same as being secure. Admittedly, the interpretation of guidelines and requirements in standards, which have a descriptive approach in general, is not an easy task. Requirements can be rather generic and wide open to interpretation depending on the context, resources, the current threat landscape, the underlying technologies, etc. Specific requirements might also lead to conflicting interpretations depending on the type of stakeholder, which will inevitably affect the implementation side. Threat modeling is one way to avoid shortcomings (or even possible shortcuts) in the implementation of standards, and the organization\'s own security policies. Think of threat modeling as an enforcement mechanism for the proper implementation of requirements. The reason this is the case is simple; threat modeling thinks of the requirements in terms of relevant threats to the system, and determines mitigations to reduce or completely avoid the associated risks. Consequently, each requirement is mapped to a set of threats and mitigations that covers relevant use cases under specific conditions or context, e.g., what are the trust boundaries, protocols and technologies under use or consideration, third-party interactions, dataflows, data storage, etc. This is becoming a must-have nowadays since, when it comes to technical requirements, the concern about their interpretation still persists even when companies have been audited against them. In the following, the presented data analysis makes the link between disclosed vulnerabilities in Industrial Control Systems (ICS) and the technical requirements reported in the ‘gold standard’ of standards in this area, namely the IEC 62443. It shows the difficulty of satisfying the requirements in broad terms and the need for more specific context and processes. CISA ICS advisories’ mapping The analysis of CISA ICS advisories data, representing close to 2,5K advisories released between 2010 and mid-2023 [3], reveals the extent of the challenge an implementer or an assessor is faced with. Table 1 presents the top weaknesses and the associated count of advisories as well as IEC 62443 requirements’ mapping. Affected sectors, the CVSS severity distribution, and top weaknesses per sector are also reported; in Figures 1 and 2, and Table 2. Table 1. Top weaknesses in CISA’s ICS advisories and their IEC 62443 mapping. Weakness Name | Tool Vulnerability Threat Industrial Prediction | ★★ | ||
| 2023-08-08 18:15:16 | CVE-2023-36903 (lien direct) | Élévation de l'outil d'évaluation du système Windows Élévation de la vulnérabilité des privilèges
Windows System Assessment Tool Elevation of Privilege Vulnerability |
Tool Vulnerability | |||
| 2023-08-08 18:15:15 | CVE-2023-36897 (lien direct) | Outils Visual Studio pour la vulnérabilité de l'usurpation de l'Office Runtime
Visual Studio Tools for Office Runtime Spoofing Vulnerability |
Tool Vulnerability | |||
| 2023-08-08 11:59:13 | Android 14 présente les fonctionnalités de sécurité de la connectivité cellulaire en son genre Android 14 introduces first-of-its-kind cellular connectivity security features (lien direct) |
Posted by Roger Piqueras Jover, Yomna Nasser, and Sudhi Herle
Android is the first mobile operating system to introduce advanced cellular security mitigations for both consumers and enterprises. Android 14 introduces support for IT administrators to disable 2G support in their managed device fleet. Android 14 also introduces a feature that disables support for null-ciphered cellular connectivity.
Hardening network security on Android
The Android Security Model assumes that all networks are hostile to keep users safe from network packet injection, tampering, or eavesdropping on user traffic. Android does not rely on link-layer encryption to address this threat model. Instead, Android establishes that all network traffic should be end-to-end encrypted (E2EE).
When a user connects to cellular networks for their communications (data, voice, or SMS), due to the distinctive nature of cellular telephony, the link layer presents unique security and privacy challenges. False Base Stations (FBS) and Stingrays exploit weaknesses in cellular telephony standards to cause harm to users. Additionally, a smartphone cannot reliably know the legitimacy of the cellular base station before attempting to connect to it. Attackers exploit this in a number of ways, ranging from traffic interception and malware sideloading, to sophisticated dragnet surveillance.
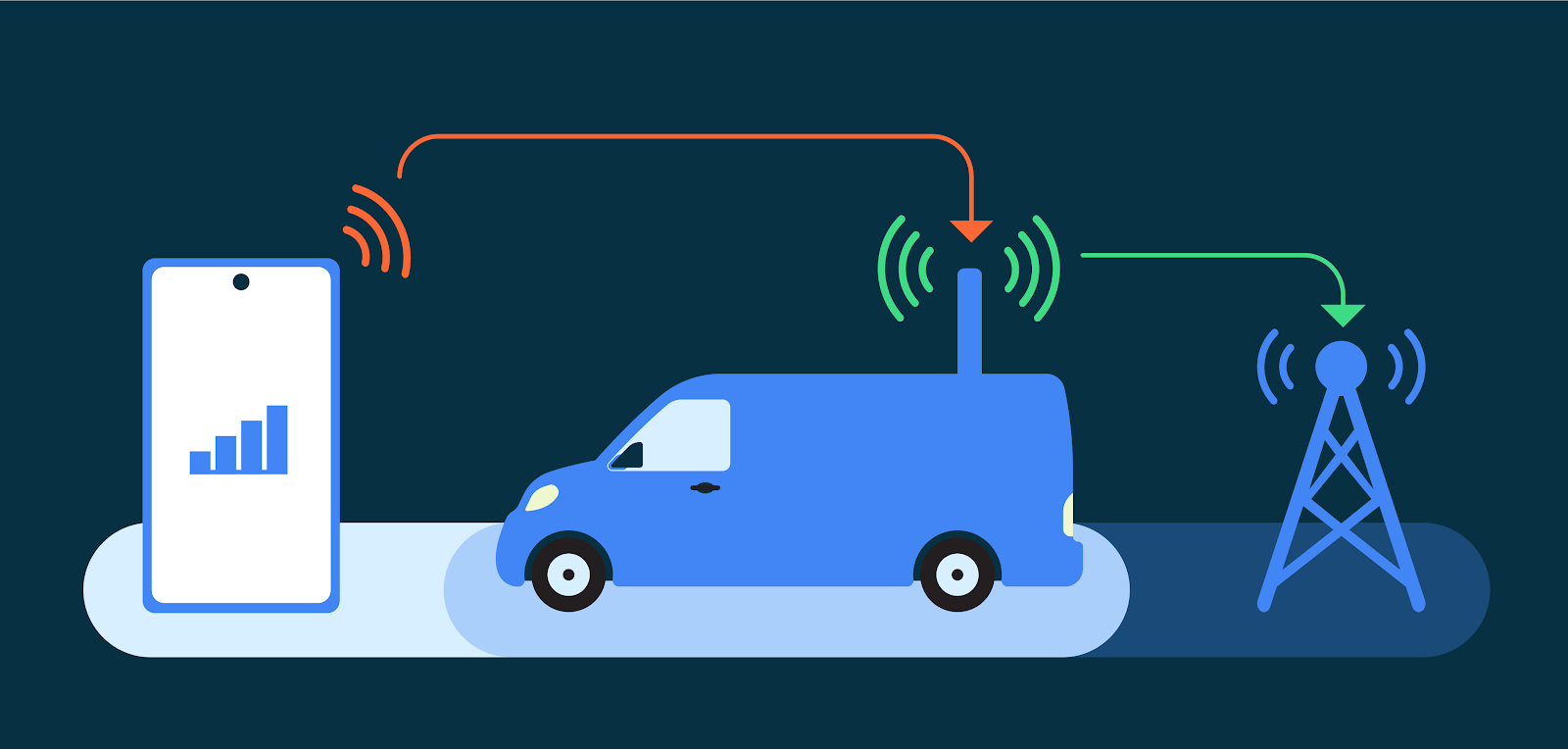 Recognizing the far reaching implications of these attack vectors, especially for at-risk users, Android has prioritized hardening cellular telephony. We are tackling well-known insecurities such as the risk presented by 2G networks, the risk presented by null ciphers, other false base station (FBS) threats, and baseband hardening with our ecosystem partners.
2G and a history of inherent security risk
The mobile ecosystem is rapidly adopting 5G, the latest wireless standard for mobile, and many carriers have started to turn down 2G service. In the United States, for example, most major carriers have shut down 2G networks. However, all existing mobile devices still have support for 2G. As a result, when available, any mobile device will connect to a 2G network. This occurs automatically when 2G is the only network available, but this can also be remotely triggered in a malicious attack, silently inducing devices to downgrade to 2G-only connectivity and thus, ignoring any non-2G network. This behavior happens regardless of whether local operators have already sunset their 2G infrastructure.
2G networks, first implemented in 1991, do not provide the same level of security as subsequent mobile generat
Recognizing the far reaching implications of these attack vectors, especially for at-risk users, Android has prioritized hardening cellular telephony. We are tackling well-known insecurities such as the risk presented by 2G networks, the risk presented by null ciphers, other false base station (FBS) threats, and baseband hardening with our ecosystem partners.
2G and a history of inherent security risk
The mobile ecosystem is rapidly adopting 5G, the latest wireless standard for mobile, and many carriers have started to turn down 2G service. In the United States, for example, most major carriers have shut down 2G networks. However, all existing mobile devices still have support for 2G. As a result, when available, any mobile device will connect to a 2G network. This occurs automatically when 2G is the only network available, but this can also be remotely triggered in a malicious attack, silently inducing devices to downgrade to 2G-only connectivity and thus, ignoring any non-2G network. This behavior happens regardless of whether local operators have already sunset their 2G infrastructure.
2G networks, first implemented in 1991, do not provide the same level of security as subsequent mobile generat |
Malware Tool Threat Conference | ★★★ | ||
| 2023-08-08 11:15:12 | CVE-2023-4203 (lien direct) | Les appareils EKI-1524, EKI-1522, EKI-1521 EKI-1522, EKI-1521 via 1,21 sont affectés par une vulnérabilité de script de site transversale stockée, qui peut être déclenchée par des utilisateurs authentifiés dans l'outil Ping de l'interface Web.
Advantech EKI-1524, EKI-1522, EKI-1521 devices through 1.21 are affected by a Stored Cross-Site Scripting vulnerability, which can be triggered by authenticated users in the ping tool of the web-interface. |
Tool | |||
| 2023-08-04 21:15:00 | Le procès accuse l'hôpital de partager les données de santé des patients avec Facebook Lawsuit accuses hospital of sharing patient health data with Facebook (lien direct) |
 Un procès en recours collectif déposé jeudi allègue qu'un hôpital de la région de Seattle a autorisé les outils de suivi en ligne de Facebook \\ pour s'intégrer à son site Web, conduisant à des données de santé personnelles appartenant à des centaines de milliers de personnes à partager avec Meta et d'autres tiers.Le demandeur, Jacq Nienaber, allègue que Meta Pixel ainsi que le
Un procès en recours collectif déposé jeudi allègue qu'un hôpital de la région de Seattle a autorisé les outils de suivi en ligne de Facebook \\ pour s'intégrer à son site Web, conduisant à des données de santé personnelles appartenant à des centaines de milliers de personnes à partager avec Meta et d'autres tiers.Le demandeur, Jacq Nienaber, allègue que Meta Pixel ainsi que le
 A proposed class action lawsuit filed Thursday alleges that a Seattle-area hospital allowed Facebook\'s online tracking tools to integrate with its website, leading to personal health data belonging to hundreds of thousands of people to be shared with Meta and other third parties. The plaintiff, Jacq Nienaber, alleges that Meta Pixel as well as the
A proposed class action lawsuit filed Thursday alleges that a Seattle-area hospital allowed Facebook\'s online tracking tools to integrate with its website, leading to personal health data belonging to hundreds of thousands of people to be shared with Meta and other third parties. The plaintiff, Jacq Nienaber, alleges that Meta Pixel as well as the |
Tool | ★★ | ||
| 2023-08-04 13:20:47 | Les acteurs de la menace abusent du tunnel Cloudflare pour un accès persistant, vol de données Threat Actors Abuse Cloudflare Tunnel for Persistent Access, Data Theft (lien direct) |
> Les acteurs de menace ont été observés abusant de l'outil de tunnel de nuage de nuage open source.
>Threat actors have been observed abusing the open source Cloudflare Tunnel tool Cloudflared to maintain stealthy, persistent access to compromised systems. |
Tool Threat | ★★ | ||
| 2023-08-03 19:13:38 | Pathlock reconnu comme un leader dans deux rapports de l'industrie Kuppingercole mettant en évidence le leadership dans les solutions de contrôle d'accès pour les applications commerciales Pathlock Recognized as a Leader in Two KuppingerCole Industry Reports Highlighting Leadership in Access Control Solutions for Business Applications (lien direct) |
Pathlock reconnu comme un leader dans deux rapports de l'industrie de Kuppingercole mettant en évidence le leadership dans les solutions de contrôle d'accès pour les applications commerciales
Pathlock a nommé un leader global des outils de contrôle d'accès pour les environnements LOB multi-vendeurs
-
magic quadrant
Pathlock Recognized as a Leader in Two KuppingerCole Industry Reports Highlighting Leadership in Access Control Solutions for Business Applications Pathlock Named an Overall Leader in Access Control Tools for Multi-Vendor LoB Environments - MAGIC QUADRANT |
Tool | ★ | ||
| 2023-08-03 15:15:30 | CVE-2023-3348 (lien direct) | L'outil de ligne de commande Wrangler ( | Tool Vulnerability | |||
| 2023-08-02 17:20:00 | Les chercheurs découvrent l'agent AWS SSM abusant comme un accès à distance secrète Researchers Uncover AWS SSM Agent Misuse as a Covert Remote Access Trojan (lien direct) |
Les chercheurs en cybersécurité ont découvert une nouvelle technique post-exploitation dans Amazon Web Services (AWS) qui permet à l'agent AWS Systems Manager (Agent SSM) d'être exécuté en tant que Troie à distance sur Windows et Linux
"L'agent SSM, un outil légitime utilisé par les administrateurs pour gérer leurs instances, peut être réutilisé par un attaquant qui a obtenu un accès élevé sur un point final avec un point final avec
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services (AWS) that allows the AWS Systems Manager Agent (SSM Agent) to be run as a remote access trojan on Windows and Linux environments "The SSM agent, a legitimate tool used by admins to manage their instances, can be re-purposed by an attacker who has achieved high privilege access on an endpoint with |
Tool | ★★★ | ||
| 2023-08-02 10:00:00 | Code Mirage: Comment les cybercriminels exploitent le code halluciné AI pour les machinations malveillantes Code Mirage: How cyber criminals harness AI-hallucinated code for malicious machinations (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article.
Introduction:
The landscape of cybercrime continues to evolve, and cybercriminals are constantly seeking new methods to compromise software projects and systems. In a disconcerting development, cybercriminals are now capitalizing on AI-generated unpublished package names also known as “AI-Hallucinated packages” to publish malicious packages under commonly hallucinated package names. It should be noted that artificial hallucination is not a new phenomenon as discussed in [3]. This article sheds light on this emerging threat, wherein unsuspecting developers inadvertently introduce malicious packages into their projects through the code generated by AI.
 AI-hallucinations:
AI-hallucinations:
 Artificial intelligence (AI) hallucinations, as described [2], refer to confident responses generated by AI systems that lack justification based on their training data. Similar to human psychological hallucinations, AI hallucinations involve the AI system providing information or responses that are not supported by the available data. However, in the context of AI, hallucinations are associated with unjustified responses or beliefs rather than false percepts. This phenomenon gained attention around 2022 with the introduction of large language models like ChatGPT, where users observed instances of seemingly random but plausible-sounding falsehoods being generated. By 2023, it was acknowledged that frequent hallucinations in AI systems posed a significant challenge for the field of language models.
The exploitative process:
Cybercriminals begin by deliberately publishing malicious packages under commonly hallucinated names produced by large language machines (LLMs) such as ChatGPT within trusted repositories. These package names closely resemble legitimate and widely used libraries or utilities, such as the legitimate package ‘arangojs’ vs the hallucinated package ‘arangodb’ as shown in the research done by Vulcan [1].
The trap unfolds:
Artificial intelligence (AI) hallucinations, as described [2], refer to confident responses generated by AI systems that lack justification based on their training data. Similar to human psychological hallucinations, AI hallucinations involve the AI system providing information or responses that are not supported by the available data. However, in the context of AI, hallucinations are associated with unjustified responses or beliefs rather than false percepts. This phenomenon gained attention around 2022 with the introduction of large language models like ChatGPT, where users observed instances of seemingly random but plausible-sounding falsehoods being generated. By 2023, it was acknowledged that frequent hallucinations in AI systems posed a significant challenge for the field of language models.
The exploitative process:
Cybercriminals begin by deliberately publishing malicious packages under commonly hallucinated names produced by large language machines (LLMs) such as ChatGPT within trusted repositories. These package names closely resemble legitimate and widely used libraries or utilities, such as the legitimate package ‘arangojs’ vs the hallucinated package ‘arangodb’ as shown in the research done by Vulcan [1].
The trap unfolds:
 When developers, unaware of the malicious intent, utilize AI-based tools or large language models (LLMs) to generate code snippets for their projects, they inadvertently can fall into a trap. The AI-generated code snippets can include imaginary unpublished libraries, enabling cybercriminals to publish commonly used AI-generated imaginary package names. As a result, developers unknowingly import malicious packages into their projects, introducing vulnerabilities, backdoors, or other malicious functionalities that compromise the security and integrity of the software and possibly other projects.
Implications for developers:
The exploitation of AI-generated hallucinated package names poses significant risks to developers and their projects. Here are some key implications:
Trusting familiar package names: Developers commonly rely on package names they recognize to introduce code snippets into their projects. The presence of malicious packages under commonly hallucinated names makes it increasingly difficult to distinguish between legitimate and malicious options when relying on the trust from AI generated code.
Blind trust in AI-generated code: Many develo
When developers, unaware of the malicious intent, utilize AI-based tools or large language models (LLMs) to generate code snippets for their projects, they inadvertently can fall into a trap. The AI-generated code snippets can include imaginary unpublished libraries, enabling cybercriminals to publish commonly used AI-generated imaginary package names. As a result, developers unknowingly import malicious packages into their projects, introducing vulnerabilities, backdoors, or other malicious functionalities that compromise the security and integrity of the software and possibly other projects.
Implications for developers:
The exploitation of AI-generated hallucinated package names poses significant risks to developers and their projects. Here are some key implications:
Trusting familiar package names: Developers commonly rely on package names they recognize to introduce code snippets into their projects. The presence of malicious packages under commonly hallucinated names makes it increasingly difficult to distinguish between legitimate and malicious options when relying on the trust from AI generated code.
Blind trust in AI-generated code: Many develo |
Tool | APT 15 ChatGPT ChatGPT | ★★★ | |
| 2023-08-01 21:55:00 | Sniffier le parphon sur sa chasse à l'administrateur du domaine Sniffing Out SharpHound on its Hunt for Domain Admin (lien direct) |
Type: Blogs reniflant Sharphound sur sa chasse à l'administrateur de domaine Les graphiques tactiques SecureWorks Taegis XDR recherchent la télémétrie qui peut identifier la présence d'outils malveillants utilisés pour obtenir l'accès administrateur du domaine. Les graphiques tactiques SecureWorks Taegis XDR recherchent une télémétrie qui peut identifier la présence d'outils malveillants utilisés pour obtenir l'accès à l'administrateur de domaine.
Type: BlogsSniffing Out SharpHound on its Hunt for Domain AdminThe Secureworks Taegis XDR Tactic Graphs searches for telemetry that can identify the presence of malicious tools used to gain domain administrator access.The Secureworks Taegis XDR Tactic Graphs searches for telemetry that can identify the presence of malicious tools used to gain domain administrator access. |
Tool | ★★ | ||
| 2023-08-01 20:21:32 | GuardZ identifie les nouveaux logiciels malveillants macOS HVNC, révélant la tendance émergente des outils d'attaque de macOS en tant que service Guardz Identifies New macOS hVNC Malware, Revealing Emerging Trend of macOS Attack-as-a-Service Tools (lien direct) |
Guardz identifie les nouveaux logiciels malveillants MacOS HVNC, révélant la tendance émergente des outils d'attaque macOS en tant que service
Pour la deuxième fois en un mois, l'équipe de recherche GuardZ révèle l'existence d'un autre logiciel malveillant ciblant les appareils MacOS disponibles sur le Web Dark, qui permet aux acteurs malveillants d'obtenir un accès furtif et continu aux systèmes infectés
-
mise à jour malveillant
Guardz Identifies New macOS hVNC Malware, Revealing Emerging Trend of macOS Attack-as-a-Service Tools For the second time in one month, the Guardz research team discloses the existence of another malware targeting macOS devices available on the dark web, which enables malicious actors to obtain stealthy and continuous access to infected systems - Malware Update |
Malware Tool Prediction | ★★ | ||
| 2023-08-01 15:09:45 | Bloodhound réécrit l'outil open source, lance l'édition communautaire BloodHound Rewrites Open Source Tool, Launches Community Edition (lien direct) |
L'écosystème open source pour les technologies de sécurité offensive et défensive est florissante, donnant aux équipes de sécurité l'accès à un large éventail d'outils pour faire leur travail.
The open source ecosystem for offensive and defensive security technologies is flourishing, giving security teams access to a wide range of tools to do their jobs. |
Tool | ★★ | ||
| 2023-08-01 14:00:03 | Votre première ligne de défense contre les ransomwares: sase Your First Line of Defense Against Ransomware: SASE (lien direct) |
> Statista dit que 71% des entreprises mondiales ont ressenti l'impact des tendances des ransomwares.Au total, 62,9% des victimes de ransomwares ont payé la rançon.Ils utilisent une myriade de techniques et d'outils pour infiltrer les réseaux, les applications et les ordinateurs car ils jettent les bases de la demande de rançon.C'est pourquoi une solution Secure Access Service Edge (SASE) qui se concentre sur la protection de ces actifs contre les ransomwares est votre première ligne de défense contre les attaquants.Un risque accru avec des ransomwares de travail flexibles peut exploiter l'accès aux ressources des entreprises, y compris les centres de données, les IaaS et les environnements de production cloud pour se propager au sein de votre organisation, vous bloquant de Vital [& # 8230;]
>Statista says that 71% of global businesses felt the impact of ransomware trends. A total of 62.9% of the ransomware victims paid the ransom. They use myriad techniques and tools to infiltrate networks, applications and computers as they lay the groundwork for the ransom demand. This is why a Secure Access Service Edge (SASE) solution that focuses on protecting these assets against ransomware is your first line of defense against attackers. Increased Risk with Flexible Work Ransomware can exploit access to corporate resources, including data centers, IaaS, and cloud production environments to propagate within your organization, blocking you from vital […] |
Ransomware Tool Cloud | ★ | ||
| 2023-08-01 13:00:29 | Investir dans une main-d'œuvre de cybersécurité robuste Investing in a Robust Cybersecurity Workforce (lien direct) |
> Les réseaux de Palo Alto priorisent la sensibilisation à la cybersécurité et l'éducation afin que les individus de tous âges et de tous horizons aient les outils pour rester en sécurité en ligne.
>Palo Alto Networks prioritizes cybersecurity awareness and education so individuals of all ages and backgrounds have the tools to stay safe online. |
Tool | ★★ | ||
| 2023-08-01 12:00:46 | Les outils de cybercriminalité basés sur l'IA Wormgpt et Fraudgpt pourraient être la pointe de l'iceberg AI-Based Cybercrime Tools WormGPT and FraudGPT Could Be The Tip of the Iceberg (lien direct) |
> L'essor des outils de cybercriminalité alimentés par l'IA comme Wormgpt et Fraudgpt a des implications importantes pour la cybersécurité alors que l'avenir de l'IA malveillante se développe rapidement quotidiennement.Découvrez les outils, leurs fonctionnalités et leur impact potentiel sur le paysage numérique.La montée en puissance de la cybercriminalité alimentée par l'IA: Wormgpt & # 38;Fraudgpt le 13 juillet, nous avons rendu compte de l'émergence [& # 8230;]
The Post AI-basé sur l'AILes outils de cybercriminalité Wormgpt et Fraudgpt pourraient être la pointe de l'iceberg apparu pour la première fois sur slashnext .
>The rise of AI-powered cybercrime tools like WormGPT and FraudGPT has significant implications for cybersecurity as the future of malicious AI is rapidly developing daily. Learn about the tools, their features, and their potential impact on the digital landscape. The Rise of AI-Powered Cybercrime: WormGPT & FraudGPT On July 13th, we reported on the emergence […] The post AI-Based Cybercrime Tools WormGPT and FraudGPT Could Be The Tip of the Iceberg first appeared on SlashNext. |
Tool | ★★ | ||
| 2023-08-01 10:08:16 | Les cybercriminels forment des chatbots d'IA pour le phishing, des attaques de logiciels malveillants Cybercriminals train AI chatbots for phishing, malware attacks (lien direct) |
Dans le sillage de Wormgpt, un clone Chatgpt formé sur des données axées sur les logiciels malveillants, un nouvel outil de piratage génératif de l'intelligence artificielle appelée fraudegpt a émergé, et au moins un autre est en cours de développement qui serait basé sur l'expérience de Google \\ S, Bard.[...]
In the wake of WormGPT, a ChatGPT clone trained on malware-focused data, a new generative artificial intelligence hacking tool called FraudGPT has emerged, and at least another one is under development that is allegedly based on Google\'s AI experiment, Bard. [...] |
Malware Tool | ChatGPT ChatGPT | ★★★ | |
| 2023-08-01 10:00:00 | Top 15 des plates-formes de gestion de la posture de sécurité des données (DSPM) pour 2023 Top 15 Data Security Posture Management (DSPM) platforms for 2023 (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Data Security Posture Management (DSPM) plays a critical role in identifying security risks, prioritizing misconfigurations, and implementing a zero-trust framework. It is an emerging technology, and there are only a few capable solutions that provide good product offerings. Check out the list of some of the best DSPM platforms that can be considered to streamline data protection, governance, and compliance efforts. Top Data Security Posture Management (DSPM) tools to watch 1. Securiti DSPM Securiti DSPM ranks at the top on Gartner’s list of DSPM platforms in this category. Gartner has given a rating of 4.7 which is the highest amongst other products. The tool is built to protect an organization’s data, especially sensitive data, everywhere. The platform covers data in numerous environments and across various formats, such as structured and unstructured data systems. Users can gain visibility of their data at rest and in motion across public, private, hybrid, and multi-cloud systems. The solution also covers SaaS environments which is a plus since traditionally, DSPM covers only public clouds. The solution leverages AI/ML-powered sensitive data insights to streamline their data governance strategy, data lineage, access policies and controls, and privacy operations, such as cross-border transfer policies. 2. Symmetry DataGuard Symmetry DataGuard comes second to Securiti in ranking and rating as well. The DSPM solution has received a 4.6 rating in the Product Capabilities and Customer Experience categories. It delivers real-time data protection. With visibility of data and advanced analytics, security teams can not only ensure data security but also availability and integrity. Users can leverage that granular information to power their IAM engines to implement effective data controls, access, and permission. Symmetry DataGuard can be an expensive and you’ll need to invest time to understand the product because of its extensive capabilities and features. 3. Sentra Sentra’s DSPM platform is built for speed and efficiency. The platform offers agentless discovery, which means that data doesn’t leave an organization’s secure environment, and hence there’s zero disruption to the productivity of teams. Another important aspect of Sentra’s DSPM solution is that it is easy to implement and scale. It further offers great integration capability and thus enables organizations to integrate with various ecosystems for discovering data. 4. Dig Security Platform Up to 77% of users would recommend Dig Security Platform, suggests Gartner. The DSPM platform has garnered a 4.2 rating on the review platform. The tool can help security and data teams to effectively identify and discover data and perform accurate categorization and classification. The data detection and response capabilities of the solution further ensure robust data protection. Teams can have a complete understanding of their data spread across physical and virtual databases and protect sensitive data from security risks, such as data exfiltration, ransomware, and shadow data. 5. Flow Security Flow Security covers a large set of environments to discover all data of an organization. For instance, the solution can scan through on-prem infrastructure, multiple cloud environments, SaaS applicatio | Tool Vulnerability Cloud | ★★ | ||
| 2023-07-31 20:49:00 | Protéger la propriété intellectuelle lorsqu'elle doit être partagée Protecting Intellectual Property When It Needs to Be Shared (lien direct) |
Les entreprises doivent utiliser une variété d'outils et de stratégies, à la fois techniques et politiques, pour protéger leur IP contre les risques tiers.
Companies should use a variety of tools and strategies, both technical and policy, to protect their IP from third-party risk. |
Tool | ★★★ | ||
| 2023-07-31 19:33:00 | Systèmes ICS à ponction aérienne ciblés par des logiciels malveillants sophistiqués Air-Gapped ICS Systems Targeted by Sophisticated Malware (lien direct) |
Les chercheurs ont découvert de nouveaux outils de deuxième étape de vermidage utilisés pour exfiltrer localement les données des environnements ICS à puits d'air, mettant les acteurs de la menace à un pas de la transmission des informations à un C2.
Researchers uncovered new worming second-stage tools used to locally exfiltrate data from air gapped ICS environments, putting threat actors one step away from transmission of the info to a C2. |
Malware Tool Threat Industrial | ★★ | ||
| 2023-07-31 19:22:00 | \\ 'Worm-like \\' botnet malware ciblant l'outil de stockage redis populaire \\'Worm-like\\' botnet malware targeting popular Redis storage tool (lien direct) |
 Un groupe inconnu de pirates utilise une nouvelle souche de logiciels malveillants pour attaquer les déploiements de redis accessibles publics - un outil de stockage de données populaire utilisé par les grandes sociétés comme Amazon, Hulu et Tinder.Des chercheurs de CADO Security Labs ont expliqué que ce qui se démarquait le plus était le fait que le malware semble être un
Un groupe inconnu de pirates utilise une nouvelle souche de logiciels malveillants pour attaquer les déploiements de redis accessibles publics - un outil de stockage de données populaire utilisé par les grandes sociétés comme Amazon, Hulu et Tinder.Des chercheurs de CADO Security Labs ont expliqué que ce qui se démarquait le plus était le fait que le malware semble être un
 An unknown group of hackers is using a novel strain of malware to attack publicly accessible deployments of Redis - a popular data storage tool used by major companies like Amazon, Hulu and Tinder. Researchers from Cado Security Labs explained that what stood out most was the fact that the malware appears to be a
An unknown group of hackers is using a novel strain of malware to attack publicly accessible deployments of Redis - a popular data storage tool used by major companies like Amazon, Hulu and Tinder. Researchers from Cado Security Labs explained that what stood out most was the fact that the malware appears to be a |
Malware Tool | ★★ | ||
| 2023-07-31 15:09:57 | Les conseillers en renseignement de Biden \\ recommandent de réformer l'accès au FBI à l'outil d'espionnage controversé Biden\\'s intelligence advisers recommend reforming FBI access to controversial spying tool (lien direct) |
Le rapport intervient alors que le Congrès se débarrasse de renouveler l'article 702 de la FISA, qui devrait expirer à la fin de l'année.
The report comes as Congress debates whether to renew Section 702 of FISA, which is set to expire at the end of the year. |
Tool | ★★ | ||
| 2023-07-31 14:08:00 | Fruity Trojan utilise des installateurs de logiciels trompeurs pour diffuser Remcos Rat Fruity Trojan Uses Deceptive Software Installers to Spread Remcos RAT (lien direct) |
Les acteurs de la menace créent de faux sites Web hébergeant des installateurs de logiciels trojanisés pour inciter les utilisateurs sans méfiance à télécharger un logiciel malveillant de téléchargeur appelé Fruity dans le but d'installer des outils de chevaux de Troie distants comme Remcos Rat.
"Parmi les logiciels en question figurent divers instruments pour les processeurs à réglage fin, les cartes graphiques et les bios; outils de surveillance du matériel PC; et certaines autres applications", Cybersecurity
Threat actors are creating fake websites hosting trojanized software installers to trick unsuspecting users into downloading a downloader malware called Fruity with the goal of installing remote trojans tools like Remcos RAT. "Among the software in question are various instruments for fine-tuning CPUs, graphic cards, and BIOS; PC hardware-monitoring tools; and some other apps," cybersecurity |
Malware Tool Threat | ★★ | ||
| 2023-07-31 10:00:00 | Ram Dump: Comprendre son & timide; & timide; RAM dump: Understanding its importance and the process (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In the realm of digital forensics and incident response, the analysis of volatile memory, commonly referred to as RAM (Random Access Memory), plays a pivotal role in extracting crucial evidence and uncovering valuable information. RAM dump - the process of capturing the contents of a computer\'s memory, is a vital step in preserving volatile data for forensic examination. This article aims to shed light on the importance of RAM dump in digital investigations and provide insights into the process involved. The significance of RAM dump Volatile nature of RAM: RAM is a volatile form of memory that holds data temporarily while a computer is powered on. Once the system is shut down, the contents of RAM are lost. Therefore, capturing a RAM dump becomes essential to preserve valuable evidence that may not be available through traditional disk-based analysis. Dynamic and live information: RAM contains real-time information about running processes, active network connections, open files, encryption keys, passwords, and other critical artifacts. Analyzing the RAM dump allows forensic investigators to access this dynamic and live information, providing insights into the state of the system at the time of the incident. Uncovering hidden or encrypted data: RAM often holds data that may not be easily accessible through traditional file system analysis. It can reveal information about active malware, hidden processes, encrypted data in memory, or remnants of deleted files, offering a wealth of evidence that can be crucial to an investigation. The RAM dump process Acquiring a RAM dump: To perform a RAM dump, specialized tools or techniques are used to capture the contents of RAM. Common methods include physical access and utilizing software tools designed for memory acquisition. Physical access allows directly connecting to the computer\'s memory modules, while software tools can acquire RAM remotely or by creating a memory image from a hibernation file. Preserving data integrity: It is essential to ensure the integrity of the RAM dump during acquisition to maintain its evidentiary value. This involves utilizing write-blocking mechanisms, verifying the integrity of the acquired image, and documenting the entire process to establish a proper chain of custody. Analyzing the RAM dump: Once the RAM dump is acquired, it can be analyzed using specialized software tools designed for memory forensics. These tools enable investigators to extract information, identify running processes, recover artifacts, and search for patterns or indicators of compromise. Extracting volatile data: The RAM dump analysis involves extracting volatile data such as active network connections, running processes, loaded drivers, registry information, file handles, and other artifacts. This data can be used to reconstruct the system\'s state, identify malicious activities, or uncover hidden information. Memory carving and artifacts recovery: Memory carving techniques are employed to search for specific file types or artifacts within the RAM dump. This process involves identifying file headers or signatures and reconstructing files from the memory image. This can be particularly useful in recovering deleted or encrypted files. RAM dumps can be acquired using specialised tools like FTK Imager and Magnet Ram Capturer (both of which are available for free) or the analysis can be done using specialised tools or Open source frameworks like Volatility Framew | Tool | ★★ | ||
| 2023-07-31 04:00:00 | L'IA réduit les cycles de vie et les coûts de violation de données AI reduces data breach lifecycles and costs (lien direct) |
> Les outils de cybersécurité que vous mettez en œuvre peuvent faire une différence dans l'avenir financier de votre entreprise.Selon le coût IBM 2023 d'un rapport de violation de données, les organisations utilisant l'IA de sécurité et l'automatisation ont engagé moins de coûts de violation de données par rapport aux entreprises n'utilisant pas les outils de cybersécurité basés sur l'IA.Le rapport a révélé que plus une organisation utilise [& # 8230;]
>The cybersecurity tools you implement can make a difference in the financial future of your business. According to the 2023 IBM Cost of a Data Breach report, organizations using security AI and automation incurred fewer data breach costs compared to businesses not using AI-based cybersecurity tools. The report found that the more an organization uses […] |
Data Breach Tool | ★★ | ||
| 2023-07-28 10:00:00 | Gestion des appareils mobiles: sécuriser le lieu de travail moderne Mobile Device Management: Securing the modern workplace (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. More mobile devices, more problems. The business landscape has shifted dramatically, as more endpoints connect to corporate networks from a wider variety of locations and are transmitting massive amounts of data. Economic forces and a lengthy pandemic have caused a decentralization of the workforce and increased adoption of a hybrid workplace model. Today, employees are more mobile than ever. The modern workforce and workplace have experienced a significant increase in endpoints, or devices connecting to the network, and managing these diverse endpoints across various geographic locations has grown in complexity. Here’s an analogy: imagine a bustling city, with its many roads, highways, and intersections. Each road represents a different endpoint, and the city itself symbolizes your corporate network. As the city grows and expands, more roads are built, connecting new neighborhoods and districts. Our corporate networks are like expanding cities. But along with digital transformation and a distributional shift of the workforce, the cybersecurity landscape is evolving at an equal pace. The multitude of endpoints that connect to the network is widening the attack surface that bad actors with malicious intent can exploit. From a cybersecurity perspective, more endpoints represent a significant business risk. Organizations need to understand the importance of managing and securing their endpoints and how these variables are intertwined for a complete endpoint security strategy. The evolution of Mobile Device Management Traditional Mobile Device Management has existed in some form since the early 2000s, when smartphones entered the marketplace. MDM has evolved over the last few decades, and in some way, Unified Endpoint Management (UEM) represents this modern evolution. Today, unified endpoint management has become a prominent solution for modern IT departments looking to secure their expanding attack surfaces. UEM is more than just managing endpoints. The “unified” represents one console for deploying, managing, and helping to secure corporate endpoints and applications. UEM offers provisioning, detection, deployment, troubleshooting, and updating abilities. UEM software gives IT and security departments visibility and control over their devices as well as their end-users, delivered through a centralized management console. For a more detailed discussion of mobile device security, check out this article. What is the difference between MDM and UEM? Unified Endpoint Management (UEM) and Mobile Device Management (MDM) are both solutions used to manage and secure an organization\'s devices, but their scope and capabilities differ. Mobile Device Management (MDM) is a type of security software used by an IT department to monitor, manage, and secure employees\' mobile devices deployed across multiple mobile service providers and across multiple mobile operating systems being used in the organization. MDM is primarily concerned with device security, allowing organizations to enforce policies, manage device settings, monitor device status, and secure devices if lost or stolen. On the other hand, Unified Endpoint Management (UEM) is a more comprehensive solution that manages and secures not just mobile devices but all endpoints within an organization. This includes PCs, laptops, smartphones, tablets, and IoT devices. UEM solutions provide a single management console from which IT can control all these devices, | Tool Vulnerability Threat Medical | ★★★ | ||
| 2023-07-28 08:46:25 | AI dans la nature: applications malveillantes des outils d'IA traditionnels AI in the Wild: Malicious Applications of Mainstream AI Tools (lien direct) |
>  Ce n'est pas tous des limericks drôles, des portraits bizarres et des sketchs viraux hilarants.Chatgpt, Bard, Dall-E, Craiyon, Voice.ai et un hôte entier ...
Ce n'est pas tous des limericks drôles, des portraits bizarres et des sketchs viraux hilarants.Chatgpt, Bard, Dall-E, Craiyon, Voice.ai et un hôte entier ...
>  It\'s not all funny limericks, bizarre portraits, and hilarious viral skits. ChatGPT, Bard, DALL-E, Craiyon, Voice.ai, and a whole host...
It\'s not all funny limericks, bizarre portraits, and hilarious viral skits. ChatGPT, Bard, DALL-E, Craiyon, Voice.ai, and a whole host...
|
Tool | ChatGPT | ★★★ | |
| 2023-07-28 07:00:00 | SuperImage – L\'application ultime pour améliorer vos photos grâce à l\'IA (lien direct) | En tant qu’amoureux de la technologie et de la photographie, je ne pouvais pas m’empêcher de vous parler de cette nouvelle application révolutionnaire nommée SuperImage. Cette petite app pour Android et Windows 11 utilise un réseau neuronal (deep learning) pour mettre à l’échelle et améliorer la qualité de vos images … Suite | Tool | ★★★ | ||
| 2023-07-28 01:00:00 | Cyclops lance à partir de furtivité avec un outil de recherche basé sur l'IA génératif Cyclops Launches From Stealth With Generative AI-Based Search Tool (lien direct) |
La plate-forme de recherche de cybersécurité contextuelle aide les équipes de sécurité à recueillir des informations sur l'environnement et la posture de sécurité de l'organisation.
The contextual cybersecurity search platform helps security teams gather information about the organization\'s environment and security posture. |
Tool | ★★ | ||
| 2023-07-27 20:10:00 | Le sénateur appelle le DOJ à enquêter sur le prétendu hack chinois de Microsoft Cloud Tools Senator calls on DOJ to investigate alleged China hack of Microsoft cloud tools (lien direct) |
 Un sénateur américain de premier plan a demandé au ministère de la Justice et à plusieurs autres agences d'enquêter sur un récent hack de comptes de messagerie fournis par Microsoft utilisés par les hauts responsables gouvernementaux.Dans une lettre publié jeudi et premier rapporté par le Wall Street Journal , le sénateur américain Ron Wyden (D-ou)Département de la justice, Commission fédérale du commerce et cybersécurité et
Un sénateur américain de premier plan a demandé au ministère de la Justice et à plusieurs autres agences d'enquêter sur un récent hack de comptes de messagerie fournis par Microsoft utilisés par les hauts responsables gouvernementaux.Dans une lettre publié jeudi et premier rapporté par le Wall Street Journal , le sénateur américain Ron Wyden (D-ou)Département de la justice, Commission fédérale du commerce et cybersécurité et
 A leading U.S. senator asked the Justice Department and several other agencies to investigate a recent hack of Microsoft-provided email accounts used by top government officials. In a letter published on Thursday and first reported by the Wall Street Journal, U.S. Senator Ron Wyden (D-OR) asked the Justice Department, Federal Trade Commission and Cybersecurity and
A leading U.S. senator asked the Justice Department and several other agencies to investigate a recent hack of Microsoft-provided email accounts used by top government officials. In a letter published on Thursday and first reported by the Wall Street Journal, U.S. Senator Ron Wyden (D-OR) asked the Justice Department, Federal Trade Commission and Cybersecurity and |
Hack Tool Cloud | ★★ | ||
| 2023-07-27 18:42:00 | Nouvelle campagne de malvertising distribuant des outils informatiques trojanisés via les annonces de recherche Google et Bing New Malvertising Campaign Distributing Trojanized IT Tools via Google and Bing Search Ads (lien direct) |
Une nouvelle campagne de malvertising a été observée en tirant parti des publicités sur Google Search et Bing pour cibler les utilisateurs à la recherche d'outils comme des outils comme AnyDesk, Cisco AnyConnect VPN et WinSCP, et les inciter à télécharger des installateurs trojanisés dans le but de briser les réseaux d'entreprise et de réaliser probablement de futurs ransomwares dans les futurs ransomwaresattaques.
Surnommé d'azote, l'activité "opportuniste" est conçue pour déployer la deuxième étape
A new malvertising campaign has been observed leveraging ads on Google Search and Bing to target users seeking IT tools like AnyDesk, Cisco AnyConnect VPN, and WinSCP, and trick them into downloading trojanized installers with an aim to breach enterprise networks and likely carry out future ransomware attacks. Dubbed Nitrogen, the "opportunistic" activity is designed to deploy second-stage |
Ransomware Tool | ★★ | ||
| 2023-07-27 18:17:09 | Trouver des bogues de sécurité dans les itinéraires d'applications Web avec la détection d'itinéraire Find security bugs in web application routes with route-detect (lien direct) |
Route-Detect est un nouvel outil AppSec de ligne de commande pour trouver des bogues d'authentification et d'autorisation dans les routes d'application Web.
route-detect is a new command-line AppSec tool for finding authentication and authorization bugs in web application routes. |
Tool | ★★ | ||
| 2023-07-27 16:55:00 | Les 4 clés de la création de programmes de sécurité cloud qui peuvent réellement se déplacer à gauche The 4 Keys to Building Cloud Security Programs That Can Actually Shift Left (lien direct) |
Au fur et à mesure que les applications cloud sont construites, testées et mises à jour, elles se frayent un chemin à travers une série toujours complexe de différents outils et équipes.Sur des centaines, voire des milliers de technologies qui composent la courtepointe patchwork des environnements de développement et de cloud, les processus de sécurité sont trop souvent appliqués dans les phases finales du développement logiciel.
Placer la sécurité à la toute fin du
As cloud applications are built, tested and updated, they wind their way through an ever-complex series of different tools and teams. Across hundreds or even thousands of technologies that make up the patchwork quilt of development and cloud environments, security processes are all too often applied in only the final phases of software development. Placing security at the very end of the |
Tool Cloud | ★★ | ||
| 2023-07-27 14:00:00 | Pourquoi les cisos d'aujourd'hui doivent embrasser le changement Why Today\\'s CISOs Must Embrace Change (lien direct) |
Avec le changement plus rapidement que jamais, les outils peuvent aider à combler les lacunes des capacités, ainsi que la formation accélérée de la main-d'œuvre.
With change happening faster than ever before, tools can help bridge capability gaps, along with accelerated workforce training. |
Tool | ★★ | ||
| 2023-07-27 12:01:55 | Les hauts et les bas de 0 jours: une année en revue des 0 jours exploités dans le monde en 2022 The Ups and Downs of 0-days: A Year in Review of 0-days Exploited In-the-Wild in 2022 (lien direct) |
Maddie Stone, Security Researcher, Threat Analysis Group (TAG)This is Google\'s fourth annual year-in-review of 0-days exploited in-the-wild [2021, 2020, 2019] and builds off of the mid-year 2022 review. The goal of this report is not to detail each individual exploit, but instead to analyze the exploits from the year as a whole, looking for trends, gaps, lessons learned, and successes. Executive Summary41 in-the-wild 0-days were detected and disclosed in 2022, the second-most ever recorded since we began tracking in mid-2014, but down from the 69 detected in 2021. Although a 40% drop might seem like a clear-cut win for improving security, the reality is more complicated. Some of our key takeaways from 2022 include:N-days function like 0-days on Android due to long patching times. Across the Android ecosystem there were multiple cases where patches were not available to users for a significant time. Attackers didn\'t need 0-day exploits and instead were able to use n-days that functioned as 0-days. | Tool Vulnerability Threat Prediction Conference | ★★★ | ||
| 2023-07-27 10:00:00 | Ce que vos pairs veulent savoir avant d'acheter un outil DLP What your peers want to know before buying a DLP tool (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Preventing data loss is a concern for almost every organization, regardless of size, especially organizations with sensitive data. Organizations, now more than ever before, rely on voluminous amounts of data to conduct business. When data leakage or a breach occurs, the organization is forced to deal with the negative consequences, such as the high cost associated with data breach fines and remediation and reputational harm to their company and brand. Data loss prevention (DLP) solutions help mitigate the risk of data loss. Losses can occur as a result of insider-related incidents (e.g., employee theft of proprietary information), or due to physical damage to computers, or as a result of human error (e.g., unintentional file deletion or sharing sensitive data in an email). In addition to the various ways an organization might experience data loss, mitigating the risk of loss requires the right people, processes, and technology. Meeting the technology requirement can be a challenge when it comes to selecting the right DLP solution. During the vendor exploration and evaluation phases, there may be questions about whether it makes sense to invest in a solution that protects the network, endpoints, or the cloud or whether it’s better to select a solution that protects the enterprise and takes into account the hybrid nature of many organizations. Data classification and labeling The decision to invest in a DLP solution should be informed by sufficient research and planning with key stakeholders. This blog will discuss three additional things you should consider before making such an investment. Let’s begin with the types of data an organization collects, stores, and analyzes to conduct business. To have a successful data loss prevention program, it’s important to identify all types of data (e.g., financial data, health data, or personally identifiable information) and to classify the data according to its value and the risk to the organization if it is leaked or exfiltrated. Data classification is the process of categorizing data to easily retrieve and store it for business use. It also protects it from loss and theft and enables regulatory compliance activities. Today, systems are more dispersed, and organizations have hybrid and remote workforce models, so it is critical to protect data regardless of where it resides or with whom it is shared. This kind of protection requires properly classified and labeled data. Automated data classification is foundational to preventing data loss. It is the best way for organizations to fully understand what types of data they have, as well as the characteristics of the data and what privacy and security requirements are necessary to protect the data. Properly classifying data also enables the organization to set policies for each data type. Techniques to identify sensitive data DLP solutions detect instances of either intentional or unintentional exfiltration of data. DLP policies describe what happens when a user uses sensitive data in a way the policy does not allow. For example, when a user attempts to print a document containing sensitive data to a home printer, the DLP policy might display a message stating that printing the docu | Data Breach Tool Cloud | ★★★ | ||
| 2023-07-27 02:51:26 | Tripwire Enterprise: réinventer un produit gagnant Tripwire Enterprise: Reimagining a Winning Product (lien direct) |
Combien de produits de sécurité faut-il pour surveiller une organisation?Même une petite entreprise se retrouve souvent à travailler avec plusieurs outils de surveillance pour obtenir une visibilité dans sa posture de sécurité.Cela crée plusieurs angles morts, car un analyste de sécurité doit sauter entre différents outils avec différents formats et configurations pour rechercher un incident de sécurité.L'ajout de ce problème est que les rapports de chaque outil diffère généralement, faisant de la création d'un rapport uniforme une corvée.Les intégrations et Splunk, de nombreuses organisations ont essayé de résoudre leur problème individuel en utilisant Splunk pour ...
How many security products does it take to monitor an organization? Even a small company often finds itself working with multiple monitoring tools to gain visibility into its security posture. This creates multiple blind spots, as a security analyst needs to jump between different tools with different formats and configurations to research a security incident. Adding to this problem is that the reporting from each tool usually differs, making the creation of a uniform report a chore. Integrations and Splunk Many organizations have tried to solve their individual problem by using Splunk to... |
Tool | ★★ | ||
| 2023-07-26 15:32:00 | Nouvel outil AI \\ 'fraudegpt \\' émerge, adapté à des attaques sophistiquées New AI Tool \\'FraudGPT\\' Emerges, Tailored for Sophisticated Attacks (lien direct) |
Suite aux traces de Wormpt, les acteurs de la menace font de la publicité pour un autre outil d'intelligence artificielle générative (IA) de cybercriminalité (IA) surnommé Fraudgpt sur diverses marchés Web sombres et canaux télégrammes.
"Il s'agit d'un bot IA, exclusivement ciblé à des fins offensives, telles que la fabrication de courriels de phishing de lance, la création d'outils de craquage, le cardage, etc.
Following the footsteps of WormGPT, threat actors are advertising yet another cybercrime generative artificial intelligence (AI) tool dubbed FraudGPT on various dark web marketplaces and Telegram channels. "This is an AI bot, exclusively targeted for offensive purposes, such as crafting spear phishing emails, creating cracking tools, carding, etc.," Netenrich security researcher Rakesh Krishnan |
Tool Tool Threat | ★★ | ||
| 2023-07-26 15:05:00 | Les marchés Web sombres offrent un nouvel outil Fraudegpt AI Dark Web Markets Offer New FraudGPT AI Tool (lien direct) |
L'outil peut élaborer des e-mails de phishing, créer des logiciels malveillants indétectables et identifier les sites vulnérables
The tool can craft phishing emails, create undetectable malware and identify vulnerable sites |
Malware Tool | ★ | ||
| 2023-07-26 10:00:00 | Comment améliorer la sensibilisation au phishing des employés How to improve employee phishing awareness (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Social engineering has long been a popular tactic among cybercriminals. Relying exclusively on information security tools does not guarantee the safety of an IT infrastructure these days. It is critically important to enhance the knowledge of employees regarding information security threats. Specifically, there is often a pressing need to educate employees about phishing. But how could phishing awareness training go wrong, and what can be done about it? Let\'s delve deeper and unravel the potential issues and solutions. In recent years, we have seen an uptick in the delivery of malware via phishing attacks. Compounding the problem is the rising volume of email fatigue, which can lead to less vigilance and increased vulnerability. Regrettably, email protection software does not fully safeguard against phishing due to the inevitable human factor involved. Indeed, there is a reason why social engineering continues to be a preferred strategy for cybercriminals - its effectiveness is exceptional. Many organizations are already conducting training sessions and rolling out specialized programs to enhance employee awareness about phishing. These programs are not just theoretical but also offer hands-on experience, allowing employees to interact with possible threats in real-world scenarios. For this, companies often use simulated phishing attacks, which are a vital part of their awareness programs. Some businesses manage these cyber exercises internally through their information security teams, while others enlist the help of service providers. However, these training sessions and mock phishing exercises are not without their flaws. At times, technical issues can disrupt the process. In other instances, the problem lies with the employees who may exhibit apathy, failing to fully engage in the process. There are indeed numerous ways in which problems can arise during the implementation of these programs. Email messages caught by technical means of protection It is standard practice for most companies to operate various email security systems, like Secure Email Gateway, DMARC, SPF, DKIM tools, sandboxes, and various antivirus software. However, the goal of simulated phishing within security awareness training is to test people, not the effectiveness of technical protective tools. Consequently, when initiating any project, it is crucial to adjust the protection settings so your simulated phishing emails can get through. Do not forget to tweak all tools of email protection at all levels. It is important to establish appropriate rules across all areas. By tweaking the settings, I am certainly not suggesting a total shutdown of the information security system - that would be unnecessary. When sending out simulated phishing emails, it is important to create exceptions for the IP addresses and domains that these messages come from, adding them to an allowlist. After making these adjustments, conduct a test run to ensure the emails are not delayed in a sandbox, diverted to junk folders, or flagged as spam in the Inbox. For the training sessions to be effective and yield accurate statistics, there should be no issues with receiving these training emails, such as blocking, delays, or labeling them as spam. Reporting phishing Untrained employees often become victims of phishing, but those who are prepared, do more than just skip and delete suspicious messages; they report them to their company\'s | Spam Malware Tool | ★★★ |
To see everything:
Our RSS (filtrered)
