What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-11-03 12:35:00 | \\ 'Campagne sociale en plusieurs étapes \\' Campagne contre Israël lié au groupe basé en Iran \\'Multi-stage social engineering\\' campaign against Israel tied to Iran-based group (lien direct) |
 Un groupe de longue date lié au gouvernement iranien a ciblé au moins deux entités israéliennes avec une campagne de piratage au cours du dernier mois, ont déclaré des chercheurs.Dans un effort continu détecté fin octobre, le groupe connu sous le nom de Muddywater a utilisé des tactiques familières avec de légers modifications à ses outils précédents, selon un Rapport par l'entreprise de cybersécurité
Un groupe de longue date lié au gouvernement iranien a ciblé au moins deux entités israéliennes avec une campagne de piratage au cours du dernier mois, ont déclaré des chercheurs.Dans un effort continu détecté fin octobre, le groupe connu sous le nom de Muddywater a utilisé des tactiques familières avec de légers modifications à ses outils précédents, selon un Rapport par l'entreprise de cybersécurité
 A long-running group connected to the Iranian government targeted at least two Israeli entities with a hacking campaign in the last month, researchers said. In an ongoing effort detected in late October, the group known as MuddyWater used familiar tactics with slight changes to its previous tools, according to a report by the cybersecurity firm
A long-running group connected to the Iranian government targeted at least two Israeli entities with a hacking campaign in the last month, researchers said. In an ongoing effort detected in late October, the group known as MuddyWater used familiar tactics with slight changes to its previous tools, according to a report by the cybersecurity firm |
Tool | ★★ | ||
| 2023-11-03 10:04:59 | Premier combiné avec MTE sur le marché First handset with MTE on the market (lien direct) |
By Mark Brand, Google Project ZeroIntroduction It\'s finally time for me to fulfill a long-standing promise. Since I first heard about ARM\'s Memory Tagging Extensions, I\'ve said (to far too many people at this point to be able to back out…) that I\'d immediately switch to the first available device that supported this feature. It\'s been a long wait (since late 2017) but with the release of the new Pixel 8 / Pixel 8 Pro handsets, there\'s finally a production handset that allows you to enable MTE! The ability of MTE to detect memory corruption exploitation at the first dangerous access is a significant improvement in diagnostic and potential security effectiveness. The availability of MTE on a production handset for the first time is a big step forward, and I think there\'s real potential to use this technology to make 0-day harder. I\'ve been running my Pixel 8 with MTE enabled since release day, and so far I haven\'t found any issues with any of the applications I use on a daily basis1, or any noticeable performance issues. Currently, MTE is only available on the Pixel as a developer option, intended for app developers to test their apps using MTE, but we can configure it to default to synchronous mode for all2 apps and native user mode binaries. This can be done on a stock image, without bootloader unlocking or rooting required - just a couple of debugger commands. We\'ll do that now, but first:Disclaimer This is absolutely not a supported device configuration; and it\'s highly likely that you\'ll encounter issues with at least some applications crashing or failing to run correctly with MTE if you set your device up in this way. This is how I\'ve configured my personal Pixel 8, and so far I\'ve not experienced any issues, but this was somewhat of a surprise to me, and I\'m still waiting to see what the first app that simply won\'t work at all will be...Enabling MTE on Pixel 8/Pixel 8 Pro | Tool Mobile | ★★ | ||
| 2023-11-03 08:15:07 | CVE-2023-42670 (lien direct) | Une faille a été trouvée en samba.Il est sensible à une vulnérabilité où plusieurs auditeurs de RPC incompatibles peuvent être initiés, provoquant des perturbations dans le service AD DC.Lorsque le serveur RPC de Samba \\ connaît une charge élevée ou une non-réponse, les serveurs destinés à des fins de courant continu non AD (par exemple, l'émulation NT4-émulation "DCS") peuvent démarrer et rivaliser à tort pour les mêmes prises de domaine Unix.Ce problème conduit à des réponses de requête partielles de l'AD DC, provoquant des problèmes tels que "le numéro de procédure est hors de portée" lors de l'utilisation d'outils comme les utilisateurs Active Directory.Ce défaut permet à un attaquant de perturber les services AD DC.
A flaw was found in Samba. It is susceptible to a vulnerability where multiple incompatible RPC listeners can be initiated, causing disruptions in the AD DC service. When Samba\'s RPC server experiences a high load or unresponsiveness, servers intended for non-AD DC purposes (for example, NT4-emulation "classic DCs") can erroneously start and compete for the same unix domain sockets. This issue leads to partial query responses from the AD DC, causing issues such as "The procedure number is out of range" when using tools like Active Directory Users. This flaw allows an attacker to disrupt AD DC services. |
Tool Vulnerability | |||
| 2023-11-03 01:00:48 | Top 10 des outils de développement Web Top 10 web development tools (lien direct) |
Commencez-vous simplement votre voyage en tant que développeur Web et recherchez des outils pour rationaliser votre processus de développement?Eh bien, vous & # 8217; Re dans la chance!Ici & # 8217; s a [plus ...]
Are you just beginning your journey as a web developer and hunting for tools to streamline your development process? Well, you’re in luck! Here’s a [more...] |
Tool | ★★ | ||
| 2023-11-02 20:07:38 | Dévoiler le côté obscur: une plongée profonde dans les familles de ransomwares actifs Unveiling the Dark Side: A Deep Dive into Active Ransomware Families (lien direct) |
#### Description
Dans le paysage en constante évolution de la cybersécurité, une tendance constante observée ces dernières années est l'augmentation troublante des attaques de ransomwares.Le groupe NCC partage TTP \\ déployé par quatre familles de ransomwares récemment observées lors des engagements de réponse aux incidents du NCC Group \\.Les familles de ransomwares qui seront explorées sont:
- Blackcat & # 8211;Il est également connu sous le nom d'ALPHV, observé pour la première fois en 2021, un ransomware en tant que service (RAAS) utilisant souvent la méthode d'extorsion à double extorsion pour le gain monétaire.
- Donut & # 8211; Le groupe d'extorsion D0nut a été signalé pour la première fois en août 2022 pour avoir violé les réseaux et exigeant des rançons en échange de ne pas fuiser des données volées.Quelques mois plus tard, les rapports du groupe utilisant le cryptage ainsi que l'exfiltration de données ont été publiés avec des spéculations selon lesquelles le ransomware déployé par le groupe a été lié à des ransomwares Helloxd.Il existe également des liens soupçonnés entre les affiliés D0nut et les opérations de ransomware de casier Hive et Ragnar.
- Medusa & # 8211;À ne pas confondre avec Medusalocker, Medusa a été observée pour la première fois en 2021, est un ransomware en tant que service (RAAS) utilisant souvent la méthode d'extorsion à double extorsion pour le gain monétaire.En 2023, l'activité des groupes \\ 'a augmenté avec le lancement du blog \' Medusa \\ '.Cette plate-forme sert d'outil pour divulguer des données appartenant aux victimes.
- NoEscape & # 8211;Fin mai 2023, un Ransomware nouvellement émergé en tant que service (RAAS) a été observé sur un forum de cybercriminalité nommé NoeScape.
#### URL de référence (s)
1. https://research.nccgroup.com/2023/10/31/unveiling-the-dark-side-a-plongée profonde-inactive-ransomware-families /
#### Date de publication
31 octobre 2023
#### Auteurs)
Alex Jessop
@Thissisfinechief
Molly Dewis
#### Description In the ever-evolving cybersecurity landscape, one consistent trend witnessed in recent years is the unsettling rise in ransomware attacks. NCC Group shares TTP\'s deployed by four ransomware families recently observed during NCC Group\'s incident response engagements. The ransomware families that will be explored are: - BlackCat – Also known as ALPHV, first observed in 2021, is a Ransomware-as-a-Service (Raas) often using the double extortion method for monetary gain. - Donut –The D0nut extortion group was first reported in August 2022 for breaching networks and demanding ransoms in return for not leaking stolen data. A few months later, reports of the group utilizing encryption as well as data exfiltration were released with speculation that the ransomware deployed by the group was linked to HelloXD ransomware. There is also suspected links between D0nut affiliates and both Hive and Ragnar Locker ransomware operations. - Medusa – Not to be confused with MedusaLocker, Medusa was first observed in 2021, is a Ransomware-as-a-Service (RaaS) often using the double extortion method for monetary gain. In 2023 the groups\' activity increased with the launch of the \'Medusa Blog\'. This platform serves as a tool for leaking data belonging to victims. - NoEscape – At the end of May 2023, a newly emerged Ransomware-as-a-Service (RaaS) was observed on a cybercrime forum named NoEscape. #### Reference URL(s) 1. https://research.nccgroup.com/2023/10/31/unveiling-the-dark-side-a-deep-dive-into-active-ransomware-families/ #### Publication Date October 31, 2023 #### Author(s) Alex Jessop @ThisIsFineChief Molly Dewis |
Ransomware Tool Prediction | ★★ | ||
| 2023-11-02 14:54:00 | La sécurité SaaS est désormais accessible et abordable à tous SaaS Security is Now Accessible and Affordable to All (lien direct) |
Ce nouveau produit propose l'évaluation de la découverte et des risques SaaS couplée à une revue gratuite d'accès aux utilisateurs dans un modèle «freemium» unique
La sécurisation des employés \\ 'SaaS devient de plus en plus cruciale pour la plupart des organisations basées sur le cloud.Bien que de nombreux outils soient disponibles pour répondre à ce besoin, ils utilisent souvent différentes approches et technologies, conduisant à une confusion et une complexité inutiles.Entrer
This new product offers SaaS discovery and risk assessment coupled with a free user access review in a unique “freemium” model Securing employees\' SaaS usage is becoming increasingly crucial for most cloud-based organizations. While numerous tools are available to address this need, they often employ different approaches and technologies, leading to unnecessary confusion and complexity. Enter |
Tool Cloud | ★★ | ||
| 2023-11-02 14:51:00 | Muddywater iran Iran\\'s MuddyWater Targets Israel in New Spear-Phishing Cyber Campaign (lien direct) |
L'acteur iranien de l'État-nation connu sous le nom de Muddywater a été lié à une nouvelle campagne de phishing de lance ciblant deux entités israéliennes pour déployer finalement un outil d'administration à distance légitime de Nable appelé agent de surveillance avancée.
La société de cybersécurité Deep Instinct, qui a divulgué les détails des attaques, a déclaré que la campagne "expose les TTP à jour à l'activité de Muddywater précédemment signalée".
The Iranian nation-state actor known as MuddyWater has been linked to a new spear-phishing campaign targeting two Israeli entities to ultimately deploy a legitimate remote administration tool from N-able called Advanced Monitoring Agent. Cybersecurity firm Deep Instinct, which disclosed details of the attacks, said the campaign "exhibits updated TTPs to previously reported MuddyWater activity," |
Tool | ★★★ | ||
| 2023-11-02 13:45:06 | SAST vs. DAST for Security Testing: Unveiling the Differences (lien direct) | Les tests de sécurité des applications (AST) comprennent divers outils, processus et approches pour scanner des applications pour découvrir des problèmes de sécurité potentiels.Les tests de sécurité des applications statiques (SAST) et les tests de sécurité des applications dynamiques (DAST) sont des approches de test de sécurité populairement utilisées qui suivent différentes méthodologies de codes d'application de numérisation à différentes étapes d'un cycle de vie de développement logiciel.
Sast suit une approche de test de boîte blanche pour analyser le code source, le code d'octets et les binaires pour identifier les vulnérabilités exploitables et les erreurs de codage.D'un autre côté, DAST met en œuvre une méthode de test de la boîte noire, où les ingénieurs de sécurité analysent les charges utiles simulées d'attaque via le frontal de l'application sans exposer des informations internes sur la construction interne de l'application \\.
Dans ce blog, nous discuterons des approches de tests de Sast et de Dast, comment ils aident à détecter les vulnérabilités et les défaillances des applications, leurs différences et les meilleurs cas d'utilisation.
Application statique…
Application Security Testing (AST) encompasses various tools, processes, and approaches to scanning applications to uncover potential security issues. Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are popularly used security testing approaches that follow different methodologies of scanning application codes across different stages of a software development lifecycle. SAST follows a white-box testing approach to analyze the source code, byte code, and binaries to identify exploitable vulnerabilities and coding errors. On the other hand, DAST implements a black-box testing method, where security engineers parse simulated attack payloads through the application\'s front end without exposing internal information on the application\'s internal construct. In this blog, we will discuss SAST and DAST testing approaches, how they help detect vulnerabilities and application failures, their differences, and best use cases. Static Application… |
Tool Vulnerability | ★★ | ||
| 2023-11-02 12:00:24 | Plus de moyens pour les utilisateurs d'identifier les applications testées sur la sécurité indépendante sur Google Play More ways for users to identify independently security tested apps on Google Play (lien direct) |
Posted by Nataliya Stanetsky, Android Security and Privacy Team
Keeping Google Play safe for users and developers remains a top priority for Google. As users increasingly prioritize their digital privacy and security, we continue to invest in our Data Safety section and transparency labeling efforts to help users make more informed choices about the apps they use.
Research shows that transparent security labeling plays a crucial role in consumer risk perception, building trust, and influencing product purchasing decisions. We believe the same principles apply for labeling and badging in the Google Play store. The transparency of an app\'s data security and privacy play a key role in a user\'s decision to download, trust, and use an app.
Highlighting Independently Security Tested VPN Apps
Last year, App Defense Alliance (ADA) introduced MASA (Mobile App Security Assessment), which allows developers to have their apps independently validated against a global security standard. This signals to users that an independent third-party has validated that the developers designed their apps to meet these industry mobile security and privacy minimum best practices and the developers are going the extra mile to identify and mitigate vulnerabilities. This, in turn, makes it harder for attackers to reach users\' devices and improves app quality across the ecosystem. Upon completion of the successful validation, Google Play gives developers the option to declare an “Independent security review” badge in its Data Safety section, as shown in the image below. While certification to baseline security standards does not imply that a product is free of vulnerabilities, the badge associated with these validated apps helps users see at-a-glance that a developer has prioritized security and privacy practices and committed to user safety.
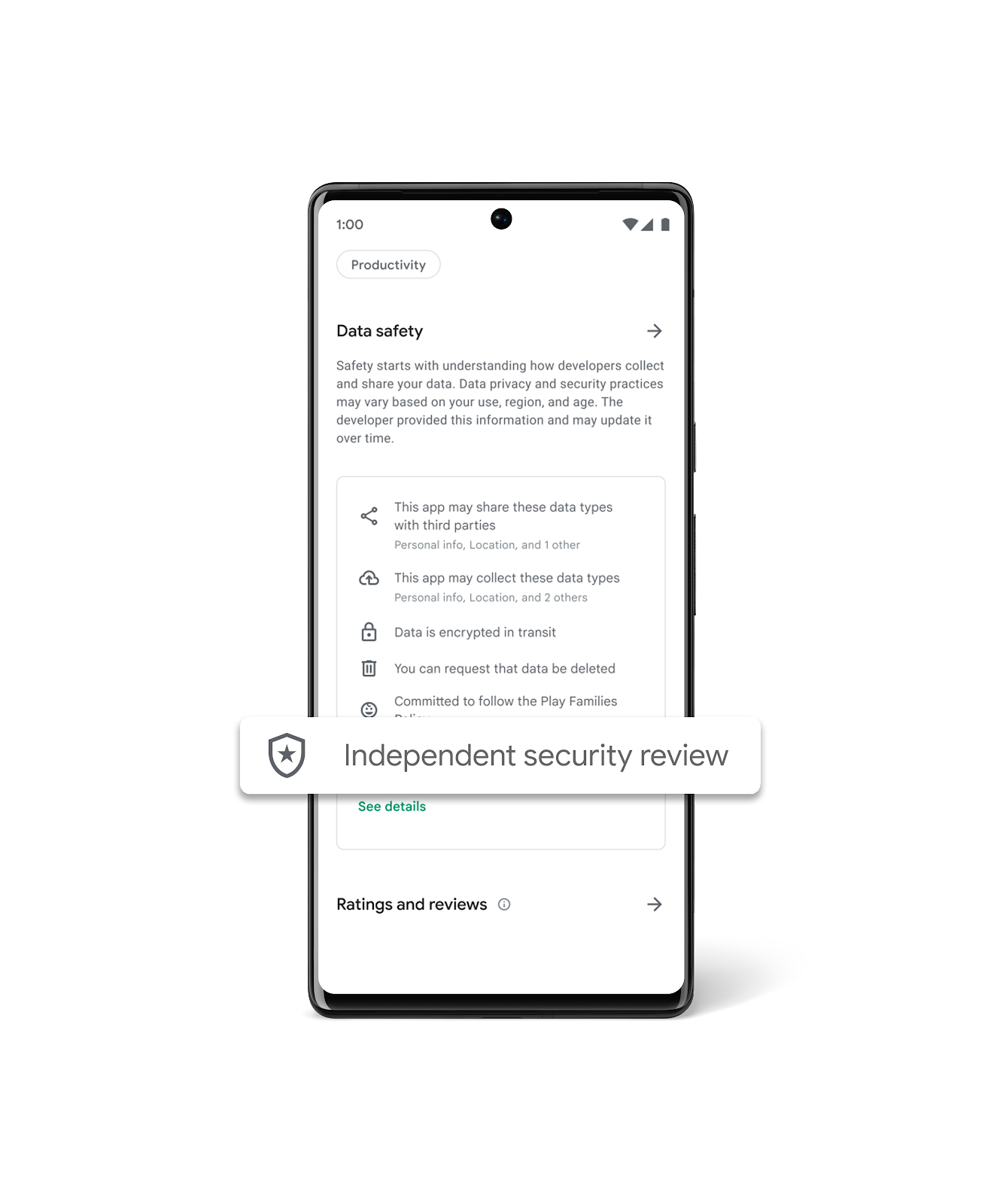 To help give users a simplified view of which apps have undergone an independent security validation, we\'re introducing a new Google Play store banner for specific app types, starting with VPN apps. We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle. When a user searches for VPN apps, they will now see a banner at the top of Google Play that educates them about the “Independent security review” badge in the Data Safety Section. Users also have the ability to “Learn More”, which redirects them to the App Validation Directory, a centralized place to view all VPN apps that have been independently security reviewed. Users can also discover additional technical assessment details in the App Validation Directory, helping them to make more informed decisions about what VPN apps to download, use, and trust with their data.
To help give users a simplified view of which apps have undergone an independent security validation, we\'re introducing a new Google Play store banner for specific app types, starting with VPN apps. We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle. When a user searches for VPN apps, they will now see a banner at the top of Google Play that educates them about the “Independent security review” badge in the Data Safety Section. Users also have the ability to “Learn More”, which redirects them to the App Validation Directory, a centralized place to view all VPN apps that have been independently security reviewed. Users can also discover additional technical assessment details in the App Validation Directory, helping them to make more informed decisions about what VPN apps to download, use, and trust with their data.
|
Tool Vulnerability Mobile Technical | ★★ | ||
| 2023-11-02 11:30:00 | Bugy octets # 216 & # 8211;Injections SQL, Android XSS et rédaction de rapports de qualité Bug Bytes #216 – SQL injections, Android XSS and Writing Quality Reports (lien direct) |
> Bug Bytes est une newsletter hebdomadaire organisée par les membres de la communauté Bug Bounty.La deuxième série est organisée par InsiderPhd.Chaque semaine, elle nous tient à jour avec une liste complète des articles, des outils, des tutoriels et des ressources.Ce numéro couvre la semaine du 23 octobre au 29 octobre Intigriti News de mon cahier
>Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by InsiderPhD. Every week, she keeps us up to date with a comprehensive list of write-ups, tools, tutorials and resources. This issue covers the week from October 23rd to October 29th Intigriti News From my notebook |
Tool Mobile Technical | ★★★ | ||
| 2023-11-02 10:00:00 | Un guide de l'acquisition de données numériques en médecine légale avec l'imageur FTK A guide to digital forensics data acquisition with FTK Imager (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In the field of Digital Forensics and Incident Response (DFIR), acquiring a forensic copy of a suspect\'s storage device is a critical first step. This process involves either disk imaging or disk cloning, each with its own distinct purposes and methodologies. In this blog, we\'ll delve into the differences between disk imaging and disk cloning, when to use each method, and provide step-by-step guidance on how to create a forensic disk image using FTK Imager. Disk imaging vs. disk cloning Disk imaging Disk imaging is the process of creating a bit-for-bit copy or snapshot of an entire storage device or a specific partition. In forensic imaging, the goal is to create an exact, bit-for-bit copy of the source disk without making any changes to the original data. The key characteristics of disk imaging include: Non-destructive: Disk imaging is a non-destructive process that doesn\'t alter the original data on the source device. It preserves the integrity of the evidence. File-level access: After imaging, forensic examiners can access and analyze the files and folders within the image using specialized forensic software. This allows for targeted analysis and data recovery. Metadata preservation: Disk imaging retains critical metadata such as file timestamps, permissions, and attributes, which can be crucial in investigations. Flexible storage: Disk images can be stored in various formats (e.g., E01, DD, AFF) and on different media, such as external hard drives or network storage. Disk cloning Disk cloning, on the other hand, involves creating an exact duplicate of the source storage device, including all partitions and unallocated space. Unlike file copying, disk cloning also duplicates the filesystems, partitions, drive meta data and slack space on the drive. The characteristics of disk cloning include: Exact copy: Disk cloning produces an identical copy of the source device. It replicates everything, including empty space and hidden partitions. Quick duplication: Cloning is typically faster than imaging because it doesn\'t involve the creation of a separate image file. It\'s essentially a sector-by-sector copy. Cloning is like making an exact photocopy of a book, smudges and all. It copies everything, even the empty pages. So, if we\'re dealing with a whole computer, it copies the operating system, software, and every file, whether it\'s useful or not. Creating a forensic disk image with FTK Imager FTK Imager is a widely used and trusted tool for creating forensic disk images. Here are the steps to create a disk image using FTK Imager: Download and Install FTK Imager, make sure to use latest stable version available as well mention the version and vendor details in case notes. This is a good practice in digital forensics and incident response (DFIR) as it ensures that you are using the most up-to-date and secure version of the software, and it provides important documentation about the tools and their configurations used in your investigations. Keeping software updated is essential for maintaining the integrity and reliability of your forensic processes. Download and Install FTK Imager on your forensic workstation. It can be downloaded from here. You’ll need to provide some information like name, business email etc., and after you fill in the form the download will start automatically. You can use privacy centric services while filling out the information. Begin the installation. | Tool Tool | ★★★ | ||
| 2023-11-01 20:30:00 | Le Département du commerce promet des garanties pour empêcher les ventes de technologies de surveillance à l'étranger Commerce Department promises safeguards to prevent surveillance tech sales abroad (lien direct) |
 Le Département du commerce a mis en œuvre de nouvelles politiques pour arrêter la promotion des technologies de surveillance aux gouvernements étrangers.Dans un lettre au sénateur Ron (D-or) Wyden, qui a exprimé la préoccupation de l'agence sur le spreadParmi les outils en mai, le Département du commerce a fixé les mesures que son Administration du commerce international (ITA) a prises pour freiner
Le Département du commerce a mis en œuvre de nouvelles politiques pour arrêter la promotion des technologies de surveillance aux gouvernements étrangers.Dans un lettre au sénateur Ron (D-or) Wyden, qui a exprimé la préoccupation de l'agence sur le spreadParmi les outils en mai, le Département du commerce a fixé les mesures que son Administration du commerce international (ITA) a prises pour freiner
 The Commerce Department has implemented new policies to stop the promotion of surveillance technologies to foreign governments. In a letter to Senator Ron (D-OR) Wyden, who expressed concern to the agency about the spread of the tools in May, the Commerce Department laid out the steps its International Trade Administration (ITA) has taken to curb
The Commerce Department has implemented new policies to stop the promotion of surveillance technologies to foreign governments. In a letter to Senator Ron (D-OR) Wyden, who expressed concern to the agency about the spread of the tools in May, the Commerce Department laid out the steps its International Trade Administration (ITA) has taken to curb |
Tool | ★★ | ||
| 2023-11-01 18:08:00 | Une campagne d'informations sur le voleur cible désormais les utilisateurs de Facebook avec des photos révélatrices An info-stealer campaign is now targeting Facebook users with revealing photos (lien direct) |
 Les cybercriminels utilisent des publicités Facebook pour distribuer des logiciels malveillants et des utilisateurs de détournement de logiciels \\ ', des chercheurs ont révélé des chercheurs.Dans la campagne dite de malvertising, les pirates exploitent des outils légitimes pour la distribution d'annonces en ligne et insérer des liens infectés vers des publicités typiques.Pour inciter les utilisateurs à cliquer, la campagne propose des «attracatifs» - dans ce cas, des images obscènes de jeunes
Les cybercriminels utilisent des publicités Facebook pour distribuer des logiciels malveillants et des utilisateurs de détournement de logiciels \\ ', des chercheurs ont révélé des chercheurs.Dans la campagne dite de malvertising, les pirates exploitent des outils légitimes pour la distribution d'annonces en ligne et insérer des liens infectés vers des publicités typiques.Pour inciter les utilisateurs à cliquer, la campagne propose des «attracatifs» - dans ce cas, des images obscènes de jeunes
 Cybercriminals are using Facebook ads to distribute malware and hijack users\' social media accounts, researchers have found. In the so-called malvertising campaign, hackers exploit legitimate tools for online ad distribution and insert infected links into typical advertisements. To entice users into clicking, the campaign offers “provocative enticements” - in this case, lewd images of young
Cybercriminals are using Facebook ads to distribute malware and hijack users\' social media accounts, researchers have found. In the so-called malvertising campaign, hackers exploit legitimate tools for online ad distribution and insert infected links into typical advertisements. To entice users into clicking, the campaign offers “provocative enticements” - in this case, lewd images of young |
Malware Tool Threat | ★★★ | ||
| 2023-11-01 16:45:53 | Docontrol lance l'extension de l'intégration Salesforce DoControl Launches Salesforce Integration Extending (lien direct) |
Docontrol lance l'intégration Salesforce étendant sa plate-forme de sécurité SaaS complète à tous les écosystèmes SaaS de premier plan
Les utilisateurs Salesforce bénéficieront désormais d'une solution consolidée de Docontrol, leur fournissant un éventail complet d'outils pour sauvegarder contre une vaste gamme de menaces
-
revues de produits
DoControl Launches Salesforce Integration Extending Its Comprehensive SaaS Security Platform To All Prominent SaaS Ecosystems Salesforce users will now benefit from DoControl\'s consolidated solution, providing them with a comprehensive array of tools to safeguard against an extensive range of threats - Product Reviews |
Tool Cloud | ★★ | ||
| 2023-11-01 15:10:26 | Outils de premier plan, efficaces et puissants pour identifier les visiteurs du site Leading, effective, and powerful tools for identifying site visitors (lien direct) |
> Par owais sultan
Savoir qui visite votre site Web vous donne des données précieuses que votre équipe de vente peut utiliser ce précieux marketing & # 8230;
Ceci est un article de HackRead.com Lire le post original: Outils de premier plan, efficaces et puissants pour identifier les visiteurs du site
>By Owais Sultan Knowing who visits your website gives you valuable data that your sales team can use this valuable marketing… This is a post from HackRead.com Read the original post: Leading, effective, and powerful tools for identifying site visitors |
Tool | ★★ | ||
| 2023-10-31 19:45:32 | From Albania to the Middle East: The Scarred Manticore is Listening (lien direct) | #### Description
Check Point Research (RCR) surveille une campagne d'espionnage iranienne en cours par Scarred Manticore, un acteur affilié au ministère du renseignement et de la sécurité (MOIS).Les attaques reposent sur Liontail, un cadre de logiciel malveillant passif avancé installé sur les serveurs Windows.À des fins de furtivité, les implants liionnal utilisent les appels directs vers Windows HTTP Stack Driver Http.SYS pour charger les charges utiles des résidents de mémoire.
La campagne actuelle a culminé à la mi-2023, passant sous le radar pendant au moins un an.La campagne cible les organisations de haut niveau au Moyen-Orient en mettant l'accent sur les secteurs du gouvernement, des militaires et des télécommunications, en plus des fournisseurs de services informatiques, des organisations financières et des ONG.Scarred Manticore poursuit des objectifs de grande valeur depuis des années, utilisant une variété de déambulations basées sur l'IIS pour attaquer les serveurs Windows.Ceux-ci incluent une variété de shells Web personnalisés, de bornes de dos de DLL personnalisées et d'implants basés sur le pilote.Bien que la principale motivation derrière l'opération de Manticore \\ ne soit que l'espionnage, certains des outils décrits dans ce rapport ont été associés à l'attaque destructrice parrainée par MOIS contre l'infrastructure du gouvernement albanais (appelé Dev-0861).
#### URL de référence (s)
1. https://research.checkpoint.com/2023/from-albania-to-the-middle-East-the-scarred-Manticore-is-Listening/
#### Date de publication
31 octobre 2023
#### Auteurs)
Recherche de point de contrôle
#### Description Check Point Research (CPR) is monitoring an ongoing Iranian espionage campaign by Scarred Manticore, an actor affiliated with the Ministry of Intelligence and Security (MOIS). The attacks rely on LIONTAIL, an advanced passive malware framework installed on Windows servers. For stealth purposes, LIONTIAL implants utilize direct calls to Windows HTTP stack driver HTTP.sys to load memory-residents payloads. The current campaign peaked in mid-2023, going under the radar for at least a year. The campaign targets high-profile organizations in the Middle East with a focus on government, military, and telecommunications sectors, in addition to IT service providers, financial organizations and NGOs. Scarred Manticore has been pursuing high-value targets for years, utilizing a variety of IIS-based backdoors to attack Windows servers. These include a variety of custom web shells, custom DLL backdoors, and driver-based implants. While the main motivation behind Scarred Manticore\'s operation is espionage, some of the tools described in this report have been associated with the MOIS-sponsored destructive attack against Albanian government infrastructure (referred to as DEV-0861). #### Reference URL(s) 1. https://research.checkpoint.com/2023/from-albania-to-the-middle-east-the-scarred-manticore-is-listening/ #### Publication Date October 31, 2023 #### Author(s) Check Point Research |
Malware Tool | APT 34 APT 34 | ★★ | |
| 2023-10-31 19:25:00 | Les États-Unis mènent une alliance de 40 pays pour couper les paiements des ransomwares US Leads 40-Country Alliance to Cut Off Ransomware Payments (lien direct) |
Les parties de l'initiative internationale contre les ransomwares ont l'intention d'utiliser des outils de partage d'informations et une IA pour atteindre leurs objectifs de coupe des ressources financières des acteurs de la menace.
The parties within the International Counter Ransomware Initiative intend to use information-sharing tools and AI to achieve their goals of cutting off the financial resources of threat actors. |
Ransomware Tool Threat | ★★ | ||
| 2023-10-31 18:55:37 | Google prévoit RISC-V Android Tools en 2024, veut que les développeurs «soient prêts» Google plans RISC-V Android tools in 2024, wants developers to “be ready” (lien direct) |
Nous avons un support RISC-V OS, des puces entrantes et bientôt, un écosystème d'applications.
We\'ve got RISC-V OS support, incoming chips, and soon, an app ecosystem. |
Tool | ★★ | ||
| 2023-10-31 10:56:45 | Déstaurer la saga Manticore marquée: une épopée fascinante d'espionnage à enjeux élevés qui se déroule au cœur du Moyen-Orient Unraveling the Scarred Manticore Saga: A Riveting Epic of High-Stakes Espionage Unfolding in the Heart of the Middle East (lien direct) |
> Faits saillants: 1. Intrudeurs silencieux: Manticore marqué, un groupe de cyber-menaces iranien lié à Mois (Ministère des renseignements & # 38; Security), gère tranquillement une opération d'espionnage sophistiquée furtive au Moyen-Orient.En utilisant leur dernier cadre d'outils de logiciels malveillants, Liontail, ils volent sous le radar depuis plus d'un an.2. Secteurs ciblés: La campagne se concentre sur les grands joueurs-gouvernement, militaire, télécommunications, informatique, finance et ONG au Moyen-Orient.Manticore marqué est une question de données systématiquement en train de saisir des données, montrant leur engagement envers les cibles de grande valeur.3. Évolution des tactiques: le livre de jeu de Manticore Scarre est passé des attaques de base de shell sur les serveurs Windows à [& # 8230;]
>Highlights: 1. Silent Intruders: Scarred Manticore, an Iranian cyber threat group linked to MOIS (Ministry of Intelligence & Security), is quietly running a stealthy sophisticated spying operation in the Middle East. Using their latest malware tools framework, LIONTAIL, they have been flying under the radar for over a year. 2. Targeted Sectors: The campaign focuses on big players-government, military, telecom, IT, finance, and NGOs in the Middle East. Scarred Manticore is all about systematically nabbing data, showing their commitment to high-value targets. 3. Evolution of Tactics: Scarred Manticore’s playbook has evolved from basic web shell attacks on Windows Servers to […] |
Malware Tool Threat | APT 34 | ★★ | |
| 2023-10-31 10:37:38 | CISA dévoile la journalisation facilitée: la solution à guichet unique pour les systèmes basés sur Windows CISA Unveils Logging Made Easy: The One-Stop Solution for Windows-Based Systems (lien direct) |
L'Agence de sécurité de la cybersécurité et de l'infrastructure (CISA) a publié la journalisation Made Easy (LME), un outil de gestion de journaux robuste et gratuit conçu pour renforcer les mesures de cybersécurité pour [plus ...]
The Cybersecurity and Infrastructure Security Agency (CISA) has released Logging Made Easy (LME), a robust, cost-free log management tool designed to reinforce cybersecurity measures for [more...] |
Tool | ★★ | ||
| 2023-10-31 08:00:27 | Turbolehe – Un peu d\'OSINT pour trouver des emails cachés (lien direct) | Turbolehe, un outil puissant pour les enquêtes OSINT, facilite la génération et la validation d'adresses e-mail à partir d'un nom et prénom. Basé sur Python, il teste les combinaisons possibles et vérifie leur existence, permettant un gain de temps considérable. Turbolehe offre également des fonctionnalités supplémentaires, telles que le filtrage par domaine, et prévoit des améliorations futures pour optimiser son efficacité. | Tool | ★★★★ | ||
| 2023-10-30 18:30:00 | L'outil de piratage russe inonde les réseaux sociaux avec des robots, disent les chercheurs Russian hacking tool floods social networks with bots, researchers say (lien direct) |
 Les cybercriminels à faible teneur en compétence utilisent un nouvel outil pour créer des centaines de faux comptes de médias sociaux en quelques secondes, ont découvert des chercheurs.Appelé Kopeechka («Penny» en russe), le service aide à contourner deux «obstacles» principaux pour quelqu'un qui essaie de créer un faux compte - une vérification par e-mail et par téléphone.Les cybercriminels pourraient utiliser Kopeechka pour transporter
Les cybercriminels à faible teneur en compétence utilisent un nouvel outil pour créer des centaines de faux comptes de médias sociaux en quelques secondes, ont découvert des chercheurs.Appelé Kopeechka («Penny» en russe), le service aide à contourner deux «obstacles» principaux pour quelqu'un qui essaie de créer un faux compte - une vérification par e-mail et par téléphone.Les cybercriminels pourraient utiliser Kopeechka pour transporter
 Low-skill cybercriminals are using a new tool to create hundreds of fake social media accounts in just a few seconds, researchers have discovered. Called Kopeechka (“penny” in Russian), the service helps to bypass two main “hurdles” for someone trying to create a fake account - email and phone verification. Cybercriminals could use Kopeechka to carry
Low-skill cybercriminals are using a new tool to create hundreds of fake social media accounts in just a few seconds, researchers have discovered. Called Kopeechka (“penny” in Russian), the service helps to bypass two main “hurdles” for someone trying to create a fake account - email and phone verification. Cybercriminals could use Kopeechka to carry |
Tool | ★★★ | ||
| 2023-10-30 15:12:49 | Une augmentation exponentielle de 1265% des e-mails de phishing retracés aux outils d'IA Exponential 1265% Surge in Phishing Emails Traced to AI Tools (lien direct) |
La nouvelle normale: une augmentation de 1265% des e-mails de phishing Le paysage des menaces a subi un changement sismique au cours de la dernière année, et un nouveau rapport [plus ...]
The New Normal: A 1265% Increase in Phishing Emails The threat landscape has undergone a seismic shift over the past year, and a new report [more...] |
Tool Threat | ★ | ||
| 2023-10-30 14:15:45 | Outils OSINT qui travaillent pour Facebook Working OSINT Tools for Facebook (lien direct) |
Le paysage numérique est en constante évolution et, avec lui, les méthodes pour extraire des informations précieuses à diverses fins.Les outils de renseignement open source (OSINT) sont devenus indispensables [plus ...]
The digital landscape is ever-evolving, and with it, the methods to extract valuable information for various purposes. Open Source Intelligence (OSINT) tools have become indispensable [more...] |
Tool | ★★★★ | ||
| 2023-10-30 10:41:17 | Métiers IT – Développeur front end : fonction, formation et salaire (lien direct) | Le développeur front end est en charge de la création et du développement de l'interface utilisateur (UI) de pages, applications et sites web. Il maîtrise les principaux outils et les langages du développement web. | Tool | ★★ | ||
| 2023-10-30 10:00:00 | Soins de santé & # 8211;Naviguer sur votre chemin vers le bien-être du bien-être Healthcare – Navigating your path to cyber wellness (lien direct) |
The healthcare industry is progressing towards a more mature cybersecurity posture. However, given it remains a popular attack target, more attention is needed. Results from The Cost of a Data Breach Report 2023 reported that healthcare has had the highest industry cost of breach for 13 consecutive years, to the tune of $10.93M. In 2022, the top 35 global security breaches exposed 1.2 billion records, and 34% of those attacks hit the public sector and healthcare organizations.
 Regulators have responded by requiring more guidance to the healthcare industry. The Cybersecurity Act of 2015 (CSA), Section 405(d), Aligning Health Care Industry Security Approaches, is the government’s response to increase collaboration on healthcare industry security practices. Lead by HHS, the 405(d) Program\'s mission is to provide resources and tools to educate, drive behavioral change, and provide cybersecurity best practices to strengthen the industry\'s cybersecurity posture.
Additionally, Section 13412 of the HITECH Act was amended in January 2022 that requires that HHS take "Recognized Security Practices" into account in specific HIPAA Security Rule enforcement and audit activities when a HIPAA-regulated entity is able to demonstrate Recognized Security Practices have been in place continuously for the 12 months prior to a security incident. This voluntary program is not a safe harbor, but could help mitigate fines and agreement remedies and reduce the time and extent for audits.
The Recognized Security Practices
Recognized Security Practices are standards, guidelines, best practices, methodologies, procedures, and processes developed under:
The National Institute of Standards and Technology (NIST) Cybersecurity Framework
Section 405(d) of the Cybersecurity Act of 2015, or
Other programs that address cybersecurity that are explicitly recognized by statute or regulation
It is apparent that healthcare organizations are being guided and even incentivized to follow a programmatic approach to cybersecurity and adopt a recognized framework.
How can a cybersecurity framework help?
By creating a common language: Adopting a cybersecurity framework and developing a strategy to implement it allows key stakeholders to start speaking a common language to address and manage cybersecurity risks. The strategy will align business, IT, and security objectives. The framework is leveraged as a mechanism in which to implement the cybersecurity strategy across the organization, which will be monitored, progress and budget reported upon to senior leaders and the board, communication, and synergies with control owners and staff. Individual users and senior executives will start to speak a common cybersecurity language, which is the first step to creating a cyber risk-aware culture.
By sustaining compliance: Adherence to a cybersecurity framework ensures that healthcare organizations comply with relevant regulations and industry standards, such as HIPAA. Compliance can help organizations avoid legal penalties, financial losses, and reputational damage.
By improving cybersecurity risk management practices: The core of implementing cybersecurity risk management is understanding the most valuable assets to the organization so that appropriate safeguards can be implemented based upon the threats. A key challenge to the healthcare industry\'s cybersecurity posture is knowing what data needs to be protected and where that data is. Accepted frameworks are built on sound risk management principles.
By increasing resilience: Cyberattacks can disrupt critical he
Regulators have responded by requiring more guidance to the healthcare industry. The Cybersecurity Act of 2015 (CSA), Section 405(d), Aligning Health Care Industry Security Approaches, is the government’s response to increase collaboration on healthcare industry security practices. Lead by HHS, the 405(d) Program\'s mission is to provide resources and tools to educate, drive behavioral change, and provide cybersecurity best practices to strengthen the industry\'s cybersecurity posture.
Additionally, Section 13412 of the HITECH Act was amended in January 2022 that requires that HHS take "Recognized Security Practices" into account in specific HIPAA Security Rule enforcement and audit activities when a HIPAA-regulated entity is able to demonstrate Recognized Security Practices have been in place continuously for the 12 months prior to a security incident. This voluntary program is not a safe harbor, but could help mitigate fines and agreement remedies and reduce the time and extent for audits.
The Recognized Security Practices
Recognized Security Practices are standards, guidelines, best practices, methodologies, procedures, and processes developed under:
The National Institute of Standards and Technology (NIST) Cybersecurity Framework
Section 405(d) of the Cybersecurity Act of 2015, or
Other programs that address cybersecurity that are explicitly recognized by statute or regulation
It is apparent that healthcare organizations are being guided and even incentivized to follow a programmatic approach to cybersecurity and adopt a recognized framework.
How can a cybersecurity framework help?
By creating a common language: Adopting a cybersecurity framework and developing a strategy to implement it allows key stakeholders to start speaking a common language to address and manage cybersecurity risks. The strategy will align business, IT, and security objectives. The framework is leveraged as a mechanism in which to implement the cybersecurity strategy across the organization, which will be monitored, progress and budget reported upon to senior leaders and the board, communication, and synergies with control owners and staff. Individual users and senior executives will start to speak a common cybersecurity language, which is the first step to creating a cyber risk-aware culture.
By sustaining compliance: Adherence to a cybersecurity framework ensures that healthcare organizations comply with relevant regulations and industry standards, such as HIPAA. Compliance can help organizations avoid legal penalties, financial losses, and reputational damage.
By improving cybersecurity risk management practices: The core of implementing cybersecurity risk management is understanding the most valuable assets to the organization so that appropriate safeguards can be implemented based upon the threats. A key challenge to the healthcare industry\'s cybersecurity posture is knowing what data needs to be protected and where that data is. Accepted frameworks are built on sound risk management principles.
By increasing resilience: Cyberattacks can disrupt critical he |
Data Breach Tool Threat Medical | ★★ | ||
| 2023-10-30 09:00:59 | Burpsuite pour Penter: Logger ++ Burpsuite for Pentester: Logger++ (lien direct) |
Dans cet article, nous apprendrons un puissant outil cool d'extension de burp appelé & # 8220; burp logger ++ & # 8221;.C'est comme un super détective pour les sites Web, toujours sur
In this article, we\'ll learn about a powerful Burp Extension cool tool called “Burp Logger++”. It is like a super detective for websites, always on |
Tool | ★★ | ||
| 2023-10-30 01:05:25 | ADAPTATION DE CODE A-AI: Révolution des trackers de ransomwares dans le Darkweb AI-Driven Code Adaptation: Revolutionizing Ransomware Trackers in the Darkweb (lien direct) |
Le Darkweb sert de foyer pour les activités de ransomware.Les trackers de ransomware, souvent créés à l'aide de robots Web codés dans des langages comme Python, sont des outils essentiels qui [Plus ...]
The darkweb serves as a hotbed for ransomware activities. Ransomware trackers, often created using web crawlers coded in languages like Python, are essential tools that [more...] |
Ransomware Tool | ★★ | ||
| 2023-10-27 20:27:00 | Le groupe coréen Lazarus cible le fournisseur de logiciels utilisant des défauts connus N. Korean Lazarus Group Targets Software Vendor Using Known Flaws (lien direct) |
Le groupe de Lazare aligné nord-en Corée a été attribué comme derrière une nouvelle campagne dans laquelle un fournisseur de logiciel sans nom a été compromis par l'exploitation de défauts de sécurité connus dans un autre logiciel de haut niveau.
Selon Kaspersky, les séquences d'attaque ont abouti au déploiement de familles de logiciels malveillants tels que Signbt et Lpeclient, un outil de piratage connu utilisé par l'acteur de menace pour
The North Korea-aligned Lazarus Group has been attributed as behind a new campaign in which an unnamed software vendor was compromised through the exploitation of known security flaws in another high-profile software. The attack sequences, according to Kaspersky, culminated in the deployment of malware families such as SIGNBT and LPEClient, a known hacking tool used by the threat actor for |
Malware Tool Threat | APT 38 APT 38 | ★★★ | |
| 2023-10-27 17:26:21 | Addons de Firefox pour la pentistation Firefox Addons for Pentesting (lien direct) |
Dans cet article, nous apprendrons à personnaliser le navigateur Firefox pour des tests de stylo efficaces ainsi que des extensions que vous pouvez utiliser dans le même but.
In this article, we will learn how to customise the Firefox browser for efficient pen-testing along with extensions you can use for the same purpose. |
Tool | ★★★★ | ||
| 2023-10-27 14:12:11 | Advanced \\ 'stripedfly \\' malware avec 1 million d'infections montrent des similitudes avec les outils liés à la NSA Advanced \\'StripedFly\\' Malware With 1 Million Infections Shows Similarities to NSA-Linked Tools (lien direct) |
Le malware Stripedfly a des capacités de type APT, mais est resté inaperçu pendant cinq ans, se faisant passer pour un mineur de crypto-monnaie.
The StripedFly malware has APT-like capabilities, but remained unnoticed for five years, posing as a cryptocurrency miner. |
Malware Tool | ★★ | ||
| 2023-10-27 14:00:00 | Ce qui se cache dans l'obscurité: prendre le but de Shadow Ai What Lurks in the Dark: Taking Aim at Shadow AI (lien direct) |
Les outils génératifs de l'intelligence artificielle ont déclenché une nouvelle ère de terreur aux cisos qui luttent toujours sur les risques de sécurité informatique de longue date.
Generative artificial intelligence tools have unleashed a new era of terror to CISOs still battling longstanding shadow IT security risks. |
Tool | ★★ | ||
| 2023-10-27 13:51:17 | Outils VMware de haute sévérité et vulnérabilités de serveur VCenter adressées avec des correctifs récents (CVE-2023-34057, CVE-2023-34058, CVE-2023-34048) High-Severity VMware Tools and vCenter Server Vulnerabilities Addressed with Recent Patches (CVE-2023-34057, CVE-2023-34058, CVE-2023-34048) (lien direct) |
VMware a abordé deux vulnérabilités critiques dans les outils VMware, CVE-2023-34057 et CVE-2023-34058, tous deux portant un haut ...
VMware has addressed two critical vulnerabilities in VMware Tools, CVE-2023-34057 and CVE-2023-34058, both carrying high... |
Tool Vulnerability | ★★★ | ||
| 2023-10-27 13:00:00 | L'évolution de 20 ans de conscience de la cybersécurité The evolution of 20 years of cybersecurity awareness (lien direct) |
> Depuis 2004, la Maison Blanche et le Congrès ont désigné le Mois national de sensibilisation à la cybersécurité d'octobre.Cette année marque le 20e anniversaire de cet effort pour sensibiliser à l'importance de la cybersécurité et de la sécurité en ligne.Comment la cybersécurité et les logiciels malveillants ont-ils évolué au cours des deux dernières décennies?Quels types d'outils de gestion des menaces ont fait surface et quand?Le [& # 8230;]
>Since 2004, the White House and Congress have designated October National Cybersecurity Awareness Month. This year marks the 20th anniversary of this effort to raise awareness about the importance of cybersecurity and online safety. How have cybersecurity and malware evolved over the last two decades? What types of threat management tools surfaced and when? The […] |
Malware Tool Threat | ★★ | ||
| 2023-10-27 11:30:00 | # ISC2Congress: Génératif Ai une aubaine pour les organisations malgré les risques, disent les experts #ISC2Congress: Generative AI A Boon for Organizations Despite the Risks, Experts Say (lien direct) |
Les experts ont souligné les façons dont les outils d'IA génératifs peuvent aider les équipes de sécurité et comment atténuer les risques qu'ils posent
Experts highlighted the ways generative AI tools can help security teams, and how to mitigate the risks they pose |
Tool | ★★ | ||
| 2023-10-27 11:01:00 | Service d'écoute électronique Découvert via le certificat TLS expiré Messaging Service Wiretap Discovered through Expired TLS Cert (lien direct) |
fascinant Story d'un écoute secrète qui a été découverte à cause d'un expiréCertificat TLS:
L'attaque suspectée de l'homme au milieu a été identifiée lorsque l'administrateur de Jabber.ru, le plus grand service XMPP russe, a reçu une notification selon laquelle l'un des serveurs \\ '' avait expiré.
Cependant, Jabber.ru n'a trouvé aucun certificat expiré sur le serveur, & timide;Comme expliqué dans un article de blog par Valdikss, un chercheur anti-censurL'enquête.
Le certificat expiré a plutôt été découvert sur un seul port utilisé par le service pour établir une connexion TLS de sécurité de la couche de transport cryptée (TLS) avec les utilisateurs.Avant qu'il ne soit expiré, cela aurait permis à quelqu'un de décrypter le trafic échangé sur le service ...
Fascinating story of a covert wiretap that was discovered because of an expired TLS certificate: The suspected man-in-the-middle attack was identified when the administrator of jabber.ru, the largest Russian XMPP service, received a notification that one of the servers\' certificates had expired. However, jabber.ru found no expired certificates on the server, as explained in a blog post by ValdikSS, a pseudonymous anti-censorship researcher based in Russia who collaborated on the investigation. The expired certificate was instead discovered on a single port being used by the service to establish an encrypted Transport Layer Security (TLS) connection with users. Before it had expired, it would have allowed someone to decrypt the traffic being exchanged over the service... |
Tool | ★★★★ | ||
| 2023-10-27 09:36:08 | Au-delà du statu quo, partie 3: comment réduire les risques humains en changeant les mentalités et les comportements des utilisateurs Beyond the Status Quo, Part 3: How to Reduce Human Risk by Changing Users\\' Mindsets and Behaviors (lien direct) |
This is the final installment in a blog series where we cover topics from our Wisdom 2023 sessions. In each blog, we have explored creative techniques for inspiring engagement in security awareness and building a strong security culture. In the first article, we covered how to personalize and invigorate your curriculum for your users using threat intelligence. Then, last week we learned about impactful ways to keep users and security practitioners engaged in continuous learning. Security teams have long believed that people who take risky actions lack security awareness. So, when users fail trainings or phishing assessments, they assign them more trainings and assessments in the hopes that they will improve. But our recent survey found that the majority of users who took risky action in the past tend to bypass security guidelines on purpose. Given this finding, it would seem that more training alone will do little to help change user behavior. At our annual customer conference, 2023 Proofpoint Protect, our customer panelists delved deep into the top behaviors that increase risk for companies. They also discussed the reasons that training alone is not as effective as people expect it to be. And they shared various ways to motivate employees to prioritize security and take a holistic approach to reducing people risk. Let\'s look at some of their key insights and advice. 3 types of users represent the biggest risk People remain attackers\' primary target. Everyone could pose risk to a business, but some users tend to be a higher risk than others. Our panelists called out the following types of users who require extra attention or could use more help or communication: Click-happy users. Email remains the number one threat vector, and attackers rely heavily on social engineering tactics to target people. So, click-happy users can pose a higher risk to businesses even if they don\'t have access to critical data or systems. Negligent users. These employees believe security has nothing to do with them. They see it as someone else\'s job. And they don\'t think they play a role in securing the business other than to complete mandatory training assigned to them. Frustrated users. These employees view security as a barrier. They overlook the importance of following security best practices and try to go around security controls to meet other objectives. Think outside the box to identify your people risk The most common ways to identify vulnerable users include conducting a phishing simulation and a knowledge assessment. Our customers told us they went beyond phishing tests and used threat intelligence to better identify risky users and quantify people risk. They talked about using Very Attacked People™ (VAPs) insights derived from the Proofpoint Aegis threat protection platform to uncover their most attacked users and top clickers. They also reviewed users who repeatedly failed phishing tests, and those who have business privileges to access sensitive data. Our panelists shared how they factored in the results from gamified training and survey tools to enrich the people risk score. Measuring employees\' attitudes toward security can help security teams get an idea of cultural shift. Nandita Bery, our panelist from Equinix, went above and beyond to connect with the security operations team to track user actions blocked by each security control and factor those security events into individuals\' risk scores. (There are tools in the market to generate user risk scores based on specific user behavior. Social media scraping tools and Proofpoint Nexus People Risk Explorer are examples.) The key is to think outside of the box because there are more effective and meaningful ways to identify and quantify people risk than tracking the training completion rate. Motivate employees by making security easy and personal “It\'s easy for security people to forget that our colleagues have a day job that isn\'t security. If security is perceived as a barrier to that, it\'s going to b | Tool Threat | ★★ | ||
| 2023-10-27 08:15:31 | CVE-2023-46093 (lien direct) | Auth.(Admin +) Vulnérabilité des scripts inter-sites stockés (XSS) dans le plugin d'outils de webmaster lionscripts.com | Tool Vulnerability | |||
| 2023-10-27 05:15:38 | CVE-2023-34058 (lien direct) | VMware Tools contient une vulnérabilité de dérivation de signature de jeton SAML.0e5e-4ccf-9d2a-90948ff643ec.html & acirc; & nbsp; dans une machine virtuelle cible peut être en mesure d'élever leurs privilèges si cette machine virtuelle cible a été affectée à une plus grande partieAlias invité privilégié https://vdc-download.vmware.com/vmwb-repository/dcr-public/d1902b0e-d479-46bf-8ac9-cee0e31e8ec0/07ce8dbd-db48-4261-9b8f-c6d3ad8ba472/vim.vm.ust.uliaster.html.
VMware Tools contains a SAML token signature bypass vulnerability. A malicious actor that has been granted Guest Operation Privileges https://docs.vmware.com/en/VMware-vSphere/8.0/vsphere-security/GUID-6A952214-0E5E-4CCF-9D2A-90948FF643EC.html  in a target virtual machine may be able to elevate their privileges if that target virtual machine has been assigned a more privileged Guest Alias https://vdc-download.vmware.com/vmwb-repository/dcr-public/d1902b0e-d479-46bf-8ac9-cee0e31e8ec0/07ce8dbd-db48-4261-9b8f-c6d3ad8ba472/vim.vm.guest.AliasManager.html . |
Tool | |||
| 2023-10-27 05:15:38 | CVE-2023-34057 (lien direct) | VMware Tools contient une vulnérabilité d'escalade locale de privilèges. & Acirc; & nbsp; un acteur malveillant avec un accès utilisateur local à une machine virtuelle invitée peut augmenter les privilèges au sein de la machine virtuelle.
VMware Tools contains a local privilege escalation vulnerability. A malicious actor with local user access to a guest virtual machine may elevate privileges within the virtual machine. |
Tool | |||
| 2023-10-26 10:28:01 | Ransomware : Big Game Hunting, exfiltration… les attaquants se tournent vers le plus rentable et affutent leurs outils (lien direct) | Cette tendance est motivée par l'intérêt persistant à maximiser la monétisation et fait écho à l'adoption massive de la technique de double extorsion, plus rentable, observée ces deux dernières années, et qui se poursuit en 2023. | Ransomware Tool | ★★ | ||
| 2023-10-26 10:00:00 | Ensuring robust security of a containerized environment (lien direct) | The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In today’s rapidly evolving digital landscape, containerized microservices have become the lifeblood of application development and deployment. Resembling miniature virtual machines, these entities enable efficient code execution in any environment, be it an on-premises server, a public cloud, or even a laptop. This paradigm eliminates the criteria of platform compatibility and library dependency from the DevOps equation. As organizations embrace the benefits of scalability and flexibility offered by containerization, they must also take up the security challenges intrinsic to this software architecture approach. This article highlights key threats to container infrastructure, provides insights into relevant security strategies, and emphasizes the shared responsibility of safeguarding containerized applications within a company. Understanding the importance of containers for cloud-native applications Containers play a pivotal role in streamlining and accelerating the development process. Serving as the building blocks of cloud-native applications, they are deeply intertwined with four pillars of software engineering: the DevOps paradigm, CI/CD pipeline, microservice architecture, and frictionless integration with orchestration tools. Orchestration tools form the backbone of container ecosystems, providing vital functionalities such as load balancing, fault tolerance, centralized management, and seamless system scaling. Orchestration can be realized through diverse approaches, including cloud provider services, self-deployed Kubernetes clusters, container management systems tailored for developers, and container management systems prioritizing user-friendliness. The container threat landscape According to recent findings of Sysdig, a company specializing in cloud security, a whopping 87% of container images have high-impact or critical vulnerabilities. While 85% of these flaws have a fix available, they can’t be exploited because the hosting containers aren’t in use. That said, many organizations run into difficulties prioritizing the patches. Rather than harden the protections of the 15% of entities exposed at runtime, security teams waste their time and resources on loopholes that pose no risk. One way or another, addressing these vulnerabilities requires the fortification of the underlying infrastructure. Apart from configuring orchestration systems properly, it’s crucial to establish a well-thought-out set of access permissions for Docker nodes or Kubernetes. Additionally, the security of containers hinges on the integrity of the images used for their construction. Guarding containers throughout the product life cycle A container\'s journey encompasses three principal stages. The initial phase involves constructing the container and subjecting it to comprehensive functional and load tests. Subsequently, the container is stored in the image registry, awaiting its moment of execution. The third stage, container runtime, occurs when the container is launched and operates as intended. Early identification of vulnerabilities is vital, and this is where the shift-left security principle plays a role. It encourages an intensified focus on security from the nascent stages of the product life cycle, encompassing the design and requirements gathering phases. By incorporating automated security checks within the CI/CD pipeline, developers can detect security issues early and minimize the chance of security gap | Tool Vulnerability Threat Cloud | Uber | ★★★ | |
| 2023-10-26 08:49:41 | Increasing transparency in AI security (lien direct) | Mihai Maruseac, Sarah Meiklejohn, Mark Lodato, Google Open Source Security Team (GOSST)New AI innovations and applications are reaching consumers and businesses on an almost-daily basis. Building AI securely is a paramount concern, and we believe that Google\'s Secure AI Framework (SAIF) can help chart a path for creating AI applications that users can trust. Today, we\'re highlighting two new ways to make information about AI supply chain security universally discoverable and verifiable, so that AI can be created and used responsibly. The first principle of SAIF is to ensure that the AI ecosystem has strong security foundations. In particular, the software supply chains for components specific to AI development, such as machine learning models, need to be secured against threats including model tampering, data poisoning, and the production of harmful content. Even as machine learning and artificial intelligence continue to evolve rapidly, some solutions are now within reach of ML creators. We\'re building on our prior work with the Open Source Security Foundation to show how ML model creators can and should protect against ML supply chain attacks by using | Malware Tool Vulnerability Threat Cloud | ★★ | ||
| 2023-10-26 08:00:33 | Google\\'s reward criteria for reporting bugs in AI products (lien direct) | Eduardo Vela, Jan Keller and Ryan Rinaldi, Google Engineering In September, we shared how we are implementing the voluntary AI commitments that we and others in industry made at the White House in July. One of the most important developments involves expanding our existing Bug Hunter Program to foster third-party discovery and reporting of issues and vulnerabilities specific to our AI systems. Today, we\'re publishing more details on these new reward program elements for the first time. Last year we issued over $12 million in rewards to security researchers who tested our products for vulnerabilities, and we expect today\'s announcement to fuel even greater collaboration for years to come. What\'s in scope for rewards In our recent AI Red Team report, we identified common tactics, techniques, and procedures (TTPs) that we consider most relevant and realistic for real-world adversaries to use against AI systems. The following table incorporates shared learnings from | Tool Vulnerability | ★★ | ||
| 2023-10-26 06:00:18 | Break the Attack Chain with Identity Threat Protection (lien direct) | “The attacker only has to be right once. Defenders have to get it right every time.” This well-known saying has shaped countless cybersecurity strategies. The belief is that a single compromise of our defenses can lead to a catastrophic outcome. As new risks emerge and attackers develop tactics to evade controls, defenders face the daunting task of protecting an ever-expanding array of connected identities. Many companies now embrace resilience strategies, accepting that an incident is inevitable - “It\'s not a matter of if, but when.” That\'s because defenders have been fixated on the impossible task of protecting everything within the business. But a new industry approach to cyber defense in recent years has emerged that points the path towards a better way. Instead of protecting everything, defenders should aim to neutralize attackers\' tactics, techniques and procedures (TTPs), which are hard to replace. This disrupts the completion of the attack chain. What is the attack chain? And how does identity threat protection disrupt it? That\'s what we\'re here to discuss. The enduring relevance of the attack chain No other concept has captured the essence of successful cyber attacks like the attack chain (aka the “cyber kill chain”), which was developed by Lockheed Martin in 2011. Even 12 years later, the attack chain remains relevant, while defenders struggle to prevent the most impactful incidents. While cyber criminals don\'t follow the same steps every time, the basic phases of an attack are pretty much always the same: Steps in the cyber attack chain. The challenge of initial compromise The first phase in the attack chain is the initial compromise. Modern cyber criminals use an array of tactics to infiltrate companies and wreak havoc on their systems, from BEC attacks to cloud account takeovers and ransomware incidents. One trend is to exploit trusted third-party relationships to compromise companies through their suppliers. What seems like an innocuous initial email can escalate into a full-scale compromise with great speed. Once attackers gain unrestricted access to a company\'s domain, they can infiltrate email accounts to commit fraudulent activities. One alarming twist to credential phishing emails is that they can evade detection. They leave behind no traces of compromise or malware. Even with the rise of multifactor authentication (MFA), these attacks continue to surge. Once accounts are compromised through a credential phishing email or a vulnerable remote desktop session, businesses face the next phase of the attack chain: privileged escalation and lateral movement within their networks. Next phase: privilege escalation and lateral movement This is the middle of the attack chain. And it\'s where threat actors try to breach a company\'s defenses. Often, they do this by compromising the identities of employees, contractors, service providers or edge devices. Their main goal is to use this initial access to elevate their privileges, typically targeting Active Directory (AD). AD, which many businesses around the world use, is susceptible to compromise. It can provide attackers with unparalleled control over a company\'s computing infrastructure. With this access, they can engage in lateral movement and spread malware across the business, causing more harm. Finally, the risk of data loss Attackers don\'t rely on a single stroke of luck. Their success hinges on a series of precise maneuvers. Monetary gains through data exfiltration are often their objective. And once they have navigated the intricate web of identities, they can target valuable data and orchestrate data theft operations. Defenders must disrupt this chain of events to prevent the loss of sensitive data, like intellectual property or customer identifiable data. Then, they can gain the upper hand and steer the course of cybersecurity in their favor. The three best opportunities to break the attack chain. Building a map of your organizat | Ransomware Malware Tool Threat Prediction Cloud | ★★ | ||
| 2023-10-25 13:00:00 | Blogpost |Changement à droite pour les plates-formes sécurisées et les devops BlogPost | Shifting Right for Secure Platforms and DevOps (lien direct) |
Les outils de développement contribuent non seulement à des problèmes de déplacement, mais les outils aident également à identifier les problèmes qui se produisent plus tard, ou à droite, dans le cycle de vie du développement.Comme la détection des secrets avant de passer à des problèmes de production ou de configuration de la plate-forme.
Dev tooling is not only helping shift issues left, but the tools also help identify issues that happen later, or to the right, in the development lifecycle. Like detecting secrets before they go into production or platform configuration issues. |
Tool | ★★ | ||
| 2023-10-25 08:35:31 | Hausse des sinistres cyber : les outils de détection et de réponse, de plus en plus importants (lien direct) | Hausse des sinistres cyber : les outils de détection et de réponse, de plus en plus importants • Les incidents de ransomware repartent à la hausse, les pirates utilisant les exfiltrations de données et les attaques contre les chaînes d'approvisionnement pour maximiser leur efficacité. • L'analyse des grands sinistres cyber effectuée par Allianz Commercial met en évidence l'augmentation des exfiltrations de données, mais aussi des incidents rendus publics. • Les violations de données peuvent devenir 1 000 fois plus coûteuses si elles ne sont pas détectées et contenues rapidement. • En matière de cybersécurité, les entreprises doivent notamment s'attacher à renforcer leurs capacités de détection et de réponse. - Investigations | Ransomware Tool | ★★ | ||
| 2023-10-24 19:50:31 | Technique de téléchargement à double DLL de Quasar Rat \\ Quasar RAT\\'s Dual DLL Sideloading Technique (lien direct) |
#### Description
Quasarrat, également connu sous le nom de Cinarat ou Yggdrasil, est un outil d'administration à distance léger écrit en C #.Cet outil est ouvertement accessible en tant que projet GitHub.Cet outil est capable de diverses fonctions telles que la collecte de données système, l'exécution d'applications, le transfert de fichiers, l'enregistrement des touches, la prise de captures d'écran ou les captures de caméra, la récupération de mots de passe du système et la supervision des opérations comme le gestionnaire de fichiers, le gestionnaire de startup, le bureau distant et l'exécution de commandes de shell.
Dans la phase initiale, l'attaquant exploite "ctfmon.exe", qui est un fichier Microsoft authentique.Ce faisant, ils chargent une DLL malveillante qui, à l'œil non formé, semblerait bénin en raison de son nom déguisé.Lors de l'exécution du binaire "ctfmon.exe", l'étape est définie lorsque l'attaquant acquiert une charge utile de stade 1 \\ '.Cette charge utile initiale est cruciale, agissant comme la passerelle pour les actions malveillantes suivantes.À ce stade, l'acteur de menace met en jeu le fichier "calcc.exe" qui, dans ce contexte, n'est pas juste une application de calculatrice simple.Parallèlement à "Calc.exe", la DLL malveillante est également mise en mouvement.Lors de l'exécution de «calcc.exe», la DLL malveillante est déclenchée.Cette action se termine dans l'infiltration de la charge utile "quasarrat" dans la mémoire de l'ordinateur, reflétant la sensibilité de l'attaquant à contourner les mécanismes de sécurité.
#### URL de référence (s)
1.Hets: //www.uptcs.kum/blag/koker-rut
#### Date de publication
Octobre ౨౪, ౨౦౨౩
#### థ థ థ థ థ థ థ థ థ థ థ థ థ థ
Tejaswini Sandapolla
#### Description QuasarRAT, also known as CinaRAT or Yggdrasil, is a lightweight remote administration tool written in C#. This tool is openly accessible as a GitHub project. This tool is capable of various functions such as gathering system data, running applications, transferring files, recording keystrokes, taking screenshots or camera captures, recovering system passwords, and overseeing operations like File Manager, Startup Manager, Remote Desktop, and executing shell commands. In the initial phase, the attacker harnesses "ctfmon.exe," which is an authentic Microsoft file. By doing so, they load a malicious DLL which, to the untrained eye, would seem benign because of its disguised name. Upon execution of the "ctfmon.exe" binary, the stage is set as the attacker acquires a \'stage 1\' payload. This initial payload is crucial, acting as the gateway for the subsequent malicious actions. At this juncture, the threat actor brings into play the "calc.exe" file, which in this context, isn\'t just a simple calculator application. Alongside "calc.exe," the malicious DLL is also set into motion. On executing "calc.exe," the malicious DLL is triggered. This action culminates in the infiltration of the "QuasarRAT" payload into the computer\'s memory, reflecting the attacker\'s adeptness at circumventing security mechanisms. #### Reference URL(s) 1. https://www.uptycs.com/blog/quasar-rat #### Publication Date October 24, 2023 #### Author(s) Tejaswini Sandapolla |
Tool Threat | ★★★ | ||
| 2023-10-24 14:12:30 | Cinq raisons pour lesquelles les outils de prévention des pertes de données hérités ne parviennent pas à livrer Five Reasons Why Legacy Data Loss Prevention Tools Fail to Deliver (lien direct) |
Comme tant de technologies héritées, les outils de prévention de la perte de données (DLP) hérités ne parviennent pas à offrir la protection aujourd'hui que les organisations ont besoin.Les défis de mise en œuvre, les lacunes de visibilité et les politiques incohérentes ont un impact négatif sur les clients et rendent les violations de données beaucoup trop faciles aux adversaires.Les coûts de violation des données américains sont en moyenne de 4,45 millions de dollars l'année dernière, les organisations ont besoin d'un moyen de [& # 8230;]
Like so many legacy technologies, legacy data loss prevention (DLP) tools fail to deliver the protection today\'s organizations need. Implementation challenges, visibility gaps and inconsistent policies negatively impact customers and make data breaches far too easy for adversaries. With U.S. data breach costs averaging a staggering $4.45 million last year, organizations need a way to […] |
Data Breach Tool Guideline | ★★★ | ||
| 2023-10-24 10:00:00 | Comment établir une grande culture de sensibilisation à la sécurité How to establish a great security awareness culture (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. As we mark another Cybersecurity Awareness Month, it\'s essential to recognize that this is more than a calendar event; it\'s a wake-up call for proactive vigilance in the digital age. In an environment rife with technological threats, the cornerstone of robust cybersecurity isn\'t just advanced systems and firewalls—it\'s informed and empowered individuals. There are three most important insights organizations can learn before implementing any cybersecurity awareness-raising campaign: More than a reminder: Each October, organizations and individuals worldwide pause to reflect on the ever-evolving digital cybersecurity. But it’s not just about ticking off a box or recognizing threats. The month serves as an empowering signal, urging everyone, from top-tier management to the newest intern, to equip themselves with knowledge and best practices. The central role of individuals: While the technological landscape continually shifts, one factor remains constant—the human element. Properly informed individuals stand as the first and often most crucial line of defense against a myriad of cyber threats. From awareness to action: True cybersecurity is about transitioning from passive recognition to active defense. Cybersecurity Awareness Month lays the foundation, but the responsibility is on each of us to translate that knowledge into tangible actions. This involves understanding the risks inherent in the digital space and cultivating a culture of security within our spheres of influence. When diving deeper into the various digital vulnerabilities in this article, always remember that every individual, armed with awareness - can make a difference. Cultivating a culture of cybersecurity awareness Creating a culture where security awareness is a top priority demands actionable steps, consistent reinforcement, and collective responsibility. Here\'s how: Security-first leadership—Leading by example Leaders play a pivotal role in shaping organizational culture. When top management emphasizes cybersecurity, it cascades down the ranks, instilling a security-first mindset across all tiers. Security as a shared responsibility—Beyond the IT department Security isn\'t a realm exclusive to the IT department. Every employee, irrespective of their role, has a stake in maintaining a secure digital environment. Promoting this understanding can foster collective ownership, ensuring that everyone feels responsible for and participates in the company\'s security efforts. Feedback-driven fortifications—Sharpening defense with dialogue Open channels of communication can be powerful tools for refining security strategies. A two-way dialogue encourages employees to voice concerns and observations, resulting in a dynamic defense system that\'s constantly refined based on ground realities. Learning from the landscape—Stay updated, stay safe The cyber landscape is in flux, shaped by emerging technologies and evolving threats. Organizations can preemptively adjust strategies by actively monitoring global trends and incidents, ensuring they\'re always a step ahead. Architecting a bespoke security culture—Beyond templates Organizations are as unique as fingerprints. A one-size-fits-all approach may not capture the specific needs of a particular enterprise. Tailoring security measures to an organization\'s unique characteristics ensures precision protection, leaving no blind spots. Maintaining awareness—The marathon mindset Cybersecurity isn\'t about sprinting through a checklist; it\'s a marathon of maintaining awareness. With | Tool Vulnerability | ★★★ |
To see everything:
Our RSS (filtrered)
