What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-11-13 08:00:00 | La sécurité est un processus, pas un outil Security Is a Process, Not a Tool (lien direct) |
Les échecs de processus sont la cause profonde des incidents de cybersécurité les plus graves.Nous devons traiter la sécurité comme un problème de processus, et n'essayez pas de le résoudre avec une collection d'outils.
Process failures are the root cause of most serious cybersecurity incidents. We need to treat security as a process issue, not try to solve it with a collection of tools. |
Tool | ★★★ | ||
| 2023-11-13 07:23:13 | ProofPoint reconnu en 2023 Gartner & Reg;Guide du marché pour la prévention de la perte de données Proofpoint Recognized in 2023 Gartner® Market Guide for Data Loss Prevention (lien direct) |
The risk of data loss increases as your business embraces digital transformation, remote work and cloud computing. Legacy data loss prevention (DLP) solutions weren\'t developed with these new dynamics in mind. In today\'s world, your DLP platform must provide visibility across multiple channels for data loss-email, cloud services, endpoint and web. It must scale with your needs while protecting data without interruption. And since data doesn\'t lose itself, it should be people centric. Part of that means providing insight into user behavior. The Gartner Market Guide for Data Loss Prevention explains that “DLP technology is mature, but today, organizations look for comprehensive solutions that go beyond traditional DLP measures.” It also notes that “Security and risk management leaders should focus on risk-based adaptive data protection techniques to strengthen the data security of their organization.” Let\'s take a look at some other insights from the report. Adaptive DLP: Enhanced with classification and converged with insider threat management The Gartner Market Guide states that “DLP vendors are increasingly converging with insider risk management platforms. This convergence enables better detection of data exfiltration as it enriches DLP events with anomalous user behaviors, improved risk scoring and real-time monitoring capabilities.” This, the report notes, enables an adaptive, risk based DLP approach. It also shares important insights such as: Enterprise DLP (EDLP) solutions offer centralized policy management and reporting functionality Enterprise DLP (EDLP) solutions generally incorporate advanced content inspection techniques to identify complex content and apply remediation Content inspection within IDLP solutions has improved considerably, and many of these solutions can recognize classification tags from more sophisticated classification tools DLP solutions use data classification labels and tags, content inspection techniques and contextual analysis to identify sensitive content and analyze actions related to the use of that content Gartner sees that DLP vendors are increasingly converging with insider risk management platforms. This convergence enables better detection of data exfiltration as it enriches DLP events with anomalous user behaviors, improved risk scoring and real-time monitoring capabilities. Gartner recommends in its Market Guide that a business use enterprise DLP if it has limited resources and its “users are transacting sensitive information through multiple channels.” The report also mentions that consulting and managed services can help “shorten the time to value and augment lean IT and security departments.” Proofpoint delivers adaptive DLP As a key player in the space, we think Proofpoint Enterprise DLP expands on the capabilities that Gartner shares in its report. The following is an overview of how we do that. People-centric insights and risk-based adaptive DLP Proofpoint Enterprise DLP protects against data loss across email, cloud, endpoint and web. Our solution combines content, behavior and threat telemetry from all these channels to address the full spectrum of people-centric data loss scenarios such as: Leavers who feel entitled to take intellectual property with them Compromised users whose data is stolen by threat actors Careless users who accidently email sensitive documents to your partners People-centric information protection is an adaptive, risk-based approach to DLP. Our Enterprise DLP solution uses people and application risk scoring and modeling for dynamic policies. Figure 1. Web security risk-based access rule. In Figure 1, “Leavers Policy 2” applies isolation as a data control when “Risky Leavers” access “Critical Business Cloud Apps.” One console, one agent, one cloud-native platform Proofpoint provides what administrators and analysts need to accurately detect DLP and insider threats: Policy management Workflows Alert management | Tool Threat Cloud | ★ | ||
| 2023-11-13 07:14:17 | Informations exploitables: comprenez votre profil de risque global avec le rapport de résumé exécutif Actionable Insights: Understand Your Overall Risk Profile with the Executive Summary Report (lien direct) |
In this blog series we cover how to improve your company\'s security posture with actionable insights. Actionable insights are a critical tool to help you improve your security posture and stop initial compromise in the attack chain. You can use them to identify and respond to potential risks, enhance your incident response capabilities, and make more informed security decisions. In previous actionable insights blog posts, we covered these topics: People risk Origin risk Business email compromise (BEC) risk Ensuring proper risk context Risk efficacy Telephone-oriented attack delivery (TOAD) risk Threat intelligence In this post, we introduce the new TAP Executive Summary Report-which is available to all Proofpoint Targeted Attack Protection (TAP) customers who use the Proofpoint Aegis threat protection platform. We\'ll show you why the Executive Summary Report is so useful so you can use it effectively to enhance your company\'s security posture. Unlock powerful insights with the Executive Summary Report Email security is more crucial than ever in today\'s fast-evolving threat landscape. To protect your business and users from emerging threats, you need the right tools-like the TAP Dashboard Executive Summary Report. We designed this new report specifically to meet the high-level reporting needs of executives and other decision-makers. It empowers these users by providing quick, easy-to-consume insights on their email security, which helps to accelerate their decision-making. You can find it in the Reports section of the TAP Dashboard as the new first tab. Let\'s explore how this new feature can help your business. Insights: What you can learn from the Executive Summary This report gives you a comprehensive overview of your business\'s email threat landscape. It equips your teams and executives with actionable intelligence. End-to-end threat protection insights Integrating data from the Proofpoint email gateway, the Executive Summary Report offers a holistic view of your company\'s inbound email threat protection effectiveness. This end-to-end visibility helps you understand how your security measures perform across your email stack. Inbound email protection breakdown This new visualization in the TAP Threat Insight Dashboard provides an at-a-glance breakdown of the total number of messages received through your email protection stack. It reveals how and when Proofpoint identified and blocked malicious messages. With this detailed insight, you can identify threats and detect anomalies-and make data-driven decisions to enhance your email security. The inbound email protection breakdown. Exposure insights The Executive Summary Report also provides insight into potentially exposed messages. With drilldowns and actionable items, you can address these threats quickly to minimize the risk of a breach. Exposure insights in the Executive Summary Report. Messages protected This chart offers a trended view of messages protected by advanced threat detection capabilities in Proofpoint TAP. The information presented is broken down by threat type or category. It lets you see the evolving nature of threats over time, so you can conduct a more in-depth analysis of your company\'s email security. The messages protected trend chart-by threat type. Efficacy metrics There are two charts that report on Proofpoint TAP\'s efficacy. The first is the “threat landscape effectiveness” chart. It provides you with a clear understanding of where the most significant threats exist within your email landscape. It displays top objectives, malware families and threat actors by total message volume. The threat landscape effectiveness chart with a breakdown of threat objectives. The second chart is “inbound protection overview.” This donut-style chart combines traditional email security and advanced threat detection (TAP) metrics. This single statistic reflects the overall effectiveness of your Proofpoint inbound email prote | Malware Tool Threat Prediction | ★★ | ||
| 2023-11-12 22:55:15 | Sécuriser vos applications Web et vos API avec Veracode Dast Essentials Securing Your Web Applications and APIs with Veracode DAST Essentials (lien direct) |
Les applications Web sont l'un des vecteurs les plus courants pour les violations, représentant plus de 40% des violations selon le rapport de violation de données de Verizon \'s 2022.S'assurer que vos applications Web sont suffisamment protégées et continuent d'être surveillées une fois qu'elles sont en production est essentielle à la sécurité de vos clients et de votre organisation.
Rester en avance sur la menace
Les attaquants recherchent constamment de nouvelles façons d'exploiter les vulnérabilités et de violer les applications Web, ce qui signifie que à mesure que leurs méthodes mûrissent et deviennent plus agressives, même les applications les plus développées peuvent devenir vulnérables.Les organisations qui effectuent uniquement des tests de pénétration annuelle sur leurs applications Web peuvent se laisser ouvertes à une violation qui pourrait être facilement empêchée par une analyse de production régulière.
La sécurité des applications décrit une collection de processus et d'outils axés sur l'identification, la correction et la prévention des vulnérabilités au niveau des applications tout au long du développement logiciel…
Web applications are one of the most common vector for breaches, accounting for over 40% of breaches according to Verizon\'s 2022 Data Breach Report. Ensuring that your web applications are sufficiently protected and continue to be monitored once they are in production is vital to the security of your customers and your organization. Staying Ahead of the Threat Attackers are constantly looking for new ways to exploit vulnerabilities and to breach web applications, which means that as their methods mature and they become more aggressive, even the most securely developed applications can become vulnerable. Organizations that only perform annual penetration tests on their web applications may be leaving themselves open to a breach that could be easily prevented with regular production scanning. Application security outlines a collection of processes and tools focused on identifying, remediating, and preventing application-level vulnerabilities throughout the entire software development… |
Data Breach Tool Vulnerability Threat | ★★ | ||
| 2023-11-12 08:00:00 | GPT fdisk – L\'outil ultime pour gérer vos disques GPT (lien direct) | Aujourd'hui, je présente GPT fdisk et ses amis (gdisk, cgdisk, sgdisk, fixparts), des outils de partitionnement pour disques GPT, disponibles sur Linux, FreeBSD, macOS et Windows. GPT, successeur du MBR, offre une meilleure gestion des partitions et prise en charge des disques de grande capacité. GPT fdisk permet de convertir MBR en GPT, réparer des structures endommagées et créer un MBR hybride, parmi d'autres fonctionnalités. | Tool | ★★ | ||
| 2023-11-10 19:10:55 | Malvertiser copie le site d'information PC pour livrer un infoster Malvertiser Copies PC News Site to Deliver Infostealer (lien direct) |
#### Description
Dans une nouvelle campagne, MalwareBytes a observé un acteur de menace copiant un portail d'information Windows légitime pour distribuer un installateur malveillant pour l'outil de processeur populaire CPU-Z.Cet incident fait partie d'une plus grande campagne de malvertising qui cible d'autres services publics comme Notepad ++, Citrix et VNC Viewer, comme le montre son infrastructure (noms de domaine) et les modèles de camouflage utilisés pour éviter la détection.MalwareBytes a informé Google des détails pertinents pour le retrait.
#### URL de référence (s)
1. https://www.malwarebytes.com/blog/thereat-intelligence/2023/11/malvertiste-copies-pc-news-site-to-deliver-infostealer
#### Date de publication
8 novembre 2023
#### Auteurs)
J & eacute; r & ocirc; moi segura
#### Description In a new campaign, Malwarebytes observed a threat actor copying a legitimate Windows news portal to distribute a malicious installer for the popular processor tool CPU-Z. This incident is a part of a larger malvertising campaign that targets other utilities like Notepad++, Citrix and VNC Viewer as seen in its infrastructure (domain names) and cloaking templates used to avoid detection. Malwarebytes have informed Google with the relevant details for takedown. #### Reference URL(s) 1. https://www.malwarebytes.com/blog/threat-intelligence/2023/11/malvertiser-copies-pc-news-site-to-deliver-infostealer #### Publication Date November 8, 2023 #### Author(s) Jérôme Segura |
Tool Threat | ★★ | ||
| 2023-11-10 14:57:04 | Les pirates infligent les orgs de soins de santé via Screenconnect à distance un accès à distance Hackers breach healthcare orgs via ScreenConnect remote access (lien direct) |
Les chercheurs en sécurité avertissent que les pirates ciblent plusieurs organisations de soins de santé aux États-Unis en abusant de l'outil d'accès à distance Screenconnect.[...]
Security researchers are warning that hackers are targeting multiple healthcare organizations in the U.S. by abusing the ScreenConnect remote access tool. [...] |
Tool Vulnerability | ★★ | ||
| 2023-11-10 14:30:00 | La nouvelle règle 80/20 pour SECOPS: Personnaliser là où elle est importante, automatiser le reste The New 80/20 Rule for SecOps: Customize Where it Matters, Automate the Rest (lien direct) |
Il existe une quête apparemment sans fin pour trouver les bons outils de sécurité qui offrent les bonnes capacités pour votre organisation.
Les équipes SOC ont tendance à passer environ un tiers de leur journée à des événements qui ne constituent pas une menace pour leur organisation, ce qui a accéléré l'adoption de solutions automatisées pour remplacer (ou augmenter) des siems inefficaces et encombrants.
Avec environ 80% de
There is a seemingly never-ending quest to find the right security tools that offer the right capabilities for your organization. SOC teams tend to spend about a third of their day on events that don\'t pose any threat to their organization, and this has accelerated the adoption of automated solutions to take the place of (or augment) inefficient and cumbersome SIEMs. With an estimated 80% of |
Tool Threat | ★★ | ||
| 2023-11-10 11:00:00 | Ne vérifiez pas!& # 8211;Activité d'écrémage de la carte de crédit observée Don\\'t check out! – Credit card skimming activity observed (lien direct) |
Our friends at BlackBerry recently released an in-depth blog post on a campaign by threat actors targeting online payment businesses that discusses what happens from initial compromise to the skimmer scripts themselves. You can read their blog here. This blog is focused on what we found across the AT&T Cybersecurity customer base as we looked for the indicators of compromise (IOCs) identified in the BlackBerry blog and on the quick-follow up analysis we performed and provided to our customers.
As a part of the AT&T Managed Threat Detection and Response (MTDR) threat hunter team, we have the unique opportunity to perform threat hunting across our fleet of customers in a very fast and efficient manner. Leveraging the logs across hundreds of data sources, we can come up with our own hunt hypotheses and develop extremely complex searches to find potential prior incidents and compromises.
We can also work with the AT&T Alien Labs team to turn that search syntax into a correlation rule. The Alien Labs team uses this backend data that we gather to create thousands of rules and signatures within the USM Anywhere platform. Threat hunters can also search for specific known tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) as we ingest and process cyber threat intelligence from both open sources (i.e., publicly available data) and closed sources (i.e., government or private data that is not publicly available).
When we looked for the TTPs that the attackers were using to deploy the credit card skimming scripts, our searches yielded no results, but when we searched for IOCs related to where the credit card data was exfiltrated during this campaign, we observed one domain come up across a few customers. Armed with key information such as time frames and which customers and users were impacted, we could now go deeper into USM Anywhere to investigate.
 Figure 1 – Web request for credit card skimming exfiltration domain
Figure 1 shows that the request for the credit card skimming site referred from another website for a well-known food company with an online purchasing option. We observed this to be the case for all the other customers too, with the food site being either the direct referer or being the HTTP request right before the connection to the cdn[.]nightboxcdn[.]com site. One of the other observed impacted customers had a user’s credit information skimmed from a different compromised site (see Figure 2).
Figure 1 – Web request for credit card skimming exfiltration domain
Figure 1 shows that the request for the credit card skimming site referred from another website for a well-known food company with an online purchasing option. We observed this to be the case for all the other customers too, with the food site being either the direct referer or being the HTTP request right before the connection to the cdn[.]nightboxcdn[.]com site. One of the other observed impacted customers had a user’s credit information skimmed from a different compromised site (see Figure 2).
 Figure 2 – Traffic going to shopping site (redacted) followed by traffic to the skim exfiltration and then a legitimate payment site
We can see that the user is on an online shopping site (redacted) followed by traffic to the exfiltration domain as well as to a legitimate payment portal service. We can conclude from the traffic flow that the user went to checkout and that after they input their payment details, this information went to both the exfiltration site and the legitimate payment service, ProPay.
By using the website scanning tool urlscan.io and by looking at a scan of the shopping site from May 23, 2023, we could see the skimming script appended to the jquery.hoverIntent.js file (legitimate script ends after });).
Figure 2 – Traffic going to shopping site (redacted) followed by traffic to the skim exfiltration and then a legitimate payment site
We can see that the user is on an online shopping site (redacted) followed by traffic to the exfiltration domain as well as to a legitimate payment portal service. We can conclude from the traffic flow that the user went to checkout and that after they input their payment details, this information went to both the exfiltration site and the legitimate payment service, ProPay.
By using the website scanning tool urlscan.io and by looking at a scan of the shopping site from May 23, 2023, we could see the skimming script appended to the jquery.hoverIntent.js file (legitimate script ends after });).

 Figure 3 – Skimming script appended to legitimate script
Figure 3 – Skimming script appended to legitimate script |
Tool Threat | ★★ | ||
| 2023-11-10 08:04:20 | 2023 Prédictions de l'escroquerie de vacances, si ce que vous devez savoir 2023 Holiday Scam Predictions-Here\\'s What You Should Know (lien direct) |
\'Tis the season for cyberscams. As the holiday season nears, adversaries will try to take advantage of people\'s generosity and holiday spirit. That\'s why it\'s critical to be alert. While it\'s still early to detect and analyze seasonal trends, we anticipate to see several new and emerging techniques in attackers\' creativity and lures, along with tried-and-true tactics from previous holiday seasons. From generative AI that helps telephone-oriented attack delivery (TOAD) to multifactor authentication (MFA) bypass that leans on shipping alerts, here\'s a look at five holiday scam predictions. These are the tricks and trends that you might see evolve in this year\'s winter threat landscape. 1: Generative AI will make threat detection trickier What\'s blown up since last holiday season? A little thing called generative AI. This emerging technology might change the game of crafting emails that include those too-good-to-be-true offers. Phony shipping emails are always favorites for attackers, and they always become more frequent during the holidays. Nobody wants a problem with merchandise they\'ve ordered or packages they\'ve shipped. Last year, many holiday season shipping phishing attempts featured standard red flags, like grammatical errors and non-native language structure. These are easily detectable at a quick glance. But this year, we expect to see many attackers using generative AI to write their emails and texts, potentially reducing easy detection. So go a level deeper when you\'re trying to determine whether a holiday season shipping email is a scam. Take a closer look these emails and ask these questions: Is the message generic or personalized? Are you being asked for unnecessary sensitive information? Does the sender display name match the email address? (This is a safety checklist item that people learn in security awareness training.) Are you being asked to pay a fee to receive a package? (Note: In this case, it\'s best to refuse the delivery until you can confirm the shipment is legitimate.) 2: TOAD scams might get an AI boost TOAD has become part of the threat toolkit, as attackers push victims to take unsafe actions over the phone. Writing with generative AI could increase the believability of TOAD attacks that use a holiday playbook. Need to stop an expensive gift purchase on your credit card or accept a heavily discounted travel offer? Then, contact this (fake) call center! If an AI-generated email successfully imitates a legitimate company, it\'s more likely that the victim will dial the phone number they\'re directed to. Generative AI could also provide opportunities to expand holiday scams globally. For instance, every Christmas and New Year, we see English-language vacation scams that target a Western audience. But there is also a huge volume of travel and celebration for Lunar New Year in China, South Korea, Vietnam and Hong Kong. If attackers previously lacked cultural knowledge or language skills to target these populations, they might now use freely available AI tools to quickly research what experiences might feel meaningful and create holiday lures that are localized and enticing. Luckily, generative AI is unlikely to improve interaction with the fraudulent call center. If you call the TOAD number, red flags should still be detectable. For instance, be wary if the “operator” is: Clearly following a script. Pressuring you to take an action. Speaking in a regional accent that your security awareness training has taught you is where call center fraud often originates. 3: MFA bypass could surface more often MFA bypass surged in popularity last year, and we continue to see an increase in the number of lures that use this technique. The attacker steals account credentials in real time by intercepting the MFA short code when the victim types it into an account login page that is fake or compromised. Since MFA bypass is an ongoing threat trend, we expect to see the techniques applied this year to holiday- | Tool Threat Prediction | FedEx | ★★★ | |
| 2023-11-10 08:00:00 | Dites adieu à Postman grâce à Bruno qui vous aidera à concevoir les meilleurs API de l\'univers (lien direct) | Bruno est un projet open source offrant une alternative légère et polyvalente aux clients API traditionnels. Il facilite la collaboration et la gestion des collections API en intégrant les collections directement dans le dépôt de code source avec le langage Bru. Le Bruno CLI simplifie le test et l'automatisation des API. | Tool | ★★★★ | ||
| 2023-11-10 07:55:46 | New Gartner & Reg;Rapport BEC: les recommandations sont entièrement prises en charge par Proofpoint New Gartner® BEC Report: Recommendations Are Fully Supported by Proofpoint (lien direct) |
Business email compromise (BEC) is costly. The latest Internet Crime Report from the FBI\'s Internet Crime Complaint Center notes that businesses lost more than $2.7 billion due to these scams in 2022. Another staggering statistic that is less reported: BEC losses were almost 80 times that of ransomware last year. The rate of BEC attacks and the average loss per incident are likely to keep climbing, which makes BEC an ongoing concern for businesses. A recent report by Gartner, How to Protect Organizations Against Business Email Compromise Phishing, offers companies several recommendations to help them reduce the risk of these attacks and minimize potential losses. Below, we share five top takeaways and key findings from this 2023 report. We also explain how Proofpoint can help protect your business against BEC attacks by linking what we do to Gartner\'s recommendations. 1. To combat BEC, businesses need to invest in email security rather than relying on endpoint protection Not all BEC scams contain a malicious payload like malware or malicious links. That\'s why endpoint protection and endpoint detection and response platforms are not effective defenses for these types of attacks. Gartner recommends: If you\'re a security and risk management leader who is responsible for infrastructure security, you can maximize your protection against BEC by seeking out and implementing artificial intelligence (AI)-based secure email gateway solutions. Look for solutions that offer: Advanced BEC phishing protection Behavioral analysis Impostor detection Internal email protection Proofpoint protects: Proofpoint believes that Gartner report\'s recommendation stems from the understanding that stopping BEC attacks before they reach a recipient\'s inbox is the best method to minimize risks. This strategy is at the heart of the Proofpoint Aegis threat protection platform. Proofpoint has used machine learning (ML) for more than two decades to detect email threats. We create the highest levels of BEC detection efficacy through our combination of AI/ML-driven behavioral analysis and rich threat intelligence. 2. Supplement email security with additional controls to reduce the risk of ATO Account takeover fraud (ATO) is often a feature in BEC attacks. It occurs when an adversary gains control of a legitimate account. To reduce the risk of ATO, businesses need to be able to recognize whether an email is from a genuine sender. Gartner recommends: Businesses should supplement their existing email security solutions with additional controls to further reduce the risk of BEC attacks like ATO and domain abuse. Proofpoint protects: To protect against account takeover, you need to identify accounts that might be compromised and automate remediation. If you rely solely on behavioral analytics to detect these accounts, you could end up with a high volume of false alerts. Proofpoint combines behavioral analysis with our rich threat intelligence to detect both compromised employee accounts and compromised third-party accounts. How Proofpoint helps when ATO occurs If an internal account has been compromised, a password reset isn\'t enough. Attackers in your environment can still manipulate third-party apps and gain persistent access to the account to wage attacks at will. Proofpoint TAP Account Takeover (TAP ATO) provides insights into what types of threats are targeting your users\' email accounts. And it provides you with the tools you need to take corrective action to protect a compromised account. TAP ATO correlates threat intelligence with artificial intelligence, ML and behavioral analytics to find malicious events across the email attack chain. It helps you see who is being attacked and how, and it provides automated remediation. How Proofpoint helps when supplier accounts are compromised Proofpoint Supplier Threat Protection gives you insight into which third-party and supplier accounts may be compromised. We combine AI/ML-driven behavioral analysis with threat in | Ransomware Malware Tool Threat | ★★ | ||
| 2023-11-09 19:07:00 | Quand les bons programmes de sensibilisation à la sécurité se trompent When Good Security Awareness Programs Go Wrong (lien direct) |
Évitez de faire ces erreurs lors de l'élaboration d'une stratégie de sensibilisation à la sécurité dans votre organisation.
Avoid making these mistakes when crafting a security awareness strategy at your organization. |
Tool | ★★★ | ||
| 2023-11-09 18:56:00 | La nouvelle campagne de malvertising utilise un faux portail d'information Windows pour distribuer des installateurs malveillants New Malvertising Campaign Uses Fake Windows News Portal to Distribute Malicious Installers (lien direct) |
Il a été constaté qu'une nouvelle campagne de malvertising utilise de faux sites qui se faisaient passer pour un portail d'information Windows légitime pour propager un installateur malveillant pour un outil de profilage système populaire appelé CPU-Z.
"Cet incident fait partie d'une plus grande campagne de malvertising qui cible d'autres services publics comme Notepad ++, Citrix et VNC Viewer comme le montre son infrastructure (noms de domaine) et les modèles de camouflage utilisés
A new malvertising campaign has been found to employ fake sites that masquerade as legitimate Windows news portal to propagate a malicious installer for a popular system profiling tool called CPU-Z. "This incident is a part of a larger malvertising campaign that targets other utilities like Notepad++, Citrix, and VNC Viewer as seen in its infrastructure (domain names) and cloaking templates used |
Tool Threat | ★★ | ||
| 2023-11-09 17:45:00 | Un gang de ransomware derrière les attaques de Moevit cible le nouveau jour zéro, dit Microsoft Ransomware gang behind MOEVit attacks are targeting new zero-day, Microsoft says (lien direct) |
 Le gang de ransomes russes derrière l'exploitation de plusieurs outils de transfert de fichiers populaires exploite désormais une nouvelle vulnérabilité dans le logiciel de support informatique SYSAID, selon un nouveau rapport.Mercredi soir, les responsables de la sécurité à Microsoft a déclaré le gang ransomware declop - qu'ils appellent Lance Tempest - vise de nouvelles victimes à travers
Le gang de ransomes russes derrière l'exploitation de plusieurs outils de transfert de fichiers populaires exploite désormais une nouvelle vulnérabilité dans le logiciel de support informatique SYSAID, selon un nouveau rapport.Mercredi soir, les responsables de la sécurité à Microsoft a déclaré le gang ransomware declop - qu'ils appellent Lance Tempest - vise de nouvelles victimes à travers
 The Russian ransomware gang behind the exploitation of several popular file transfer tools is now exploiting a new vulnerability in SysAid IT support software, according to a new report. On Wednesday night, security officials at Microsoft said the Clop ransomware gang - which they refer to as Lance Tempest - is targeting new victims through
The Russian ransomware gang behind the exploitation of several popular file transfer tools is now exploiting a new vulnerability in SysAid IT support software, according to a new report. On Wednesday night, security officials at Microsoft said the Clop ransomware gang - which they refer to as Lance Tempest - is targeting new victims through |
Ransomware Tool Vulnerability | ★★ | ||
| 2023-11-09 16:42:29 | Copilot mais pas que : comment GitHub se nourrit des LLM (lien direct) | Au-delà des éléments proposés sous la bannière GitHub Copilot, les LLM portent, notamment, des fonctionnalités de sécurité. | Tool | ★★ | ||
| 2023-11-09 16:20:00 | MUDDYC2GO: Nouveau cadre C2 Iranian Hackers Utilisation contre Israël MuddyC2Go: New C2 Framework Iranian Hackers Using Against Israel (lien direct) |
Des acteurs iraniens de l'État-nation ont été observés en utilisant un cadre de commandement et de contrôle (C2) sans papiers précédemment appelé Muddyc2go dans le cadre d'attaques ciblant Israël.
"Le composant Web du Framework \\ est rédigé dans le langage de programmation Go", a déclaré Simon Kenin, chercheur en sécurité de Deep Instinct, dans un rapport technique publié mercredi.
L'outil a été attribué à Muddywater, un iranien
Iranian nation-state actors have been observed using a previously undocumented command-and-control (C2) framework called MuddyC2Go as part of attacks targeting Israel. "The framework\'s web component is written in the Go programming language," Deep Instinct security researcher Simon Kenin said in a technical report published Wednesday. The tool has been attributed to MuddyWater, an Iranian |
Tool Technical | ★★★ | ||
| 2023-11-09 14:25:13 | Comment trouver vos identités risquées How to Find Your Risky Identities (lien direct) |
Les acteurs de la menace utilisent de nombreuses techniques pour obtenir des informations d'identification de compte pour la simple raison qu'ils ouvrent la porte à une multitude de tactiques en aval. Lorsqu'ils ont des informations d'identification, les cybercriminels n'ont pas besoin de percer votre périmètre ou de rechercher des vulnérabilités existantes pour entrer. Au lieu de cela, ils peuvent s'attendre sans être détectés, se déplacer dans votre réseau, poser plusieurs charges utiles malveillantes, voler des données et ciblerAutres utilisateurs de grande valeur en cours de route.Toute défense efficace contre ce type d'attaque nécessite que vous compreniez quelle identité risquée est susceptible d'être à la réception de celle-ci. Toute identité unique peut être compromise et doit être protégée en conséquence.Cependant, certains sont plus à risque des attaques que d'autres et d'autres sont plus précieux.Lorsque vous obtenez une visibilité dans les identités les plus à risque, vous pouvez appliquer et améliorer les contrôles où ils sont le plus nécessaires. Voici un aperçu des identités sur lesquelles vous devez concentrer vos efforts ainsi que certains outils qui peuvent vous aider. 3 catégories d'identités risquées Les identités risquées peuvent être regroupées en trois catégories: Identités non gérées Les comptes de service ne sont généralement pas gérés par les outils de gestion de l'accès aux privilèges (PAM) car ils sont souvent non découverts lors de la mise en œuvre.De plus, les identités de la machine peuvent être erronées pour permettre à tort une connexion interactive par les humains. Les administrateurs locaux sont configurés pour faciliter les demandes de support informatique sur les points de terminaison et sont souvent oubliés après leur création. Les comptes privilégiés ne sont souvent pas gérés activement car ils ne sont pas constamment découverts. Identités mal configurées Les administrateurs fantômes sont généralement mal configurés en raison de la complexité des groupes d'identité imbriqués dans Active Directory.Cela peut rendre extrêmement difficile de voir les droits et les droits complets de toutes les identités.En conséquence, les administrateurs fantômes peuvent se voir accorder des privilèges excessifs involontaires. Les identités configurées avec un cryptage faible ou manquant et celles qui n'appliquent pas de mots de passe solides entrent également dans cette catégorie. Identités exposées Les informations d'identification en cache sont généralement stockées sur les points de terminaison, les navigateurs, la mémoire, le registre et le disque.En conséquence, ils peuvent être facilement exploités à l'aide d'outils d'attaquant communs. Les jetons d'accès cloud stockés sur les points de terminaison sont également un moyen courant pour les attaquants d'accéder aux actifs cloud. Les séances d'application à distance, telles que RDP, peuvent être mal fermées.Si cela se produit, les cybercriminels peuvent les utiliser pour compromettre une session ouverte et ses privilèges, sans risque de détection. Ces identités sont risquées. C'est là que vivent des identités risquées. Défense de la menace d'identité de la preuve Plus de 90% des attaques reposent sur des identités compromises.C'est pourquoi vous avez besoin de la défense de la menace d'identité de la preuve.ProofPoint peut vous aider à détecter les menaces actives et à éliminer les lacunes de votre posture d'identité qui peuvent être exploitées par les attaquants. La défense des menaces d'identité est invaincue dans plus de 160 exercices d'équipe rouge (et comptage).Cela peut vous aider: Découvrez et hiérarchisez vos vulnérabilités d'identité Retourner automatiquement les risques sur vos points de terminaison et vos serveurs Détecter les menaces actives au milieu de la chaîne d'attaque au moment de l'escalade des privilèges et du mouvement latéral Proofpoint vous donne les outils pour empêcher les | Tool Vulnerability Threat Cloud | ★★ | ||
| 2023-11-09 14:06:34 | \\ 'BLAZESTEALER \\' MALWORED INDUCTE \\'BlazeStealer\\' Malware Delivered to Python Developers Looking for Obfuscation Tools (lien direct) |
CheckMarx découvre une campagne malveillante ciblant les développeurs Python avec des logiciels malveillants qui prennent le contrôle de leurs systèmes.
Checkmarx uncovers a malicious campaign targeting Python developers with malware that takes over their systems. |
Malware Tool | ★★ | ||
| 2023-11-09 11:09:38 | Google Ads Poussez l'application MALICIEUX CPU-Z à partir du faux site d'information Windows Google ads push malicious CPU-Z app from fake Windows news site (lien direct) |
Un acteur de menace a abusé des publicités Google pour distribuer une version trojanisée de l'outil CPU-Z pour livrer le malware de volet d'informations sur la ligne.[...]
A threat actor has been abusing Google Ads to distribute a trojanized version of the CPU-Z tool to deliver the Redline info-stealing malware. [...] |
Malware Tool Threat | ★★ | ||
| 2023-11-09 08:42:45 | PwC : 72 % des entreprises estiment que l\'Intelligence Artificielle Générative sera génératrice de cyberattaques (lien direct) | 72 % des entreprises estiment que l'Intelligence Artificielle Générative sera génératrice de cyberattaques En France, 60 % des organisations soulignent la modernisation de leur technologie cyber comme principal investissement, surpassant la moyenne mondiale de 49 % La simplification des outils cyber est une priorité, avec 44 % des PDG français optant pour des solutions de cyber technologie intégrées, face à 19 % qui indiquent un besoin de rationalisation La sécurité cloud émerge comme une inquiétude centrale pour 47 % des dirigeants français, reflétant une prise de conscience globale des risques associés L'intelligence artificielle générative (la GenAI) s'annonce comme une révolution en matière de défense cyber, avec 69 % des entreprises françaises projetant son adoption - Investigations | Tool Studies Cloud | ★★★ | ||
| 2023-11-09 08:00:00 | OpenHue – Maitrisez l\'éclairage connecté de vos Philips Hue avec cette API open-source (lien direct) | OpenHue est un projet open-source offrant une spécification OpenAPI pour l'API REST Philips Hue (CLIP API), facilitant l'intégration et le contrôle des systèmes d'éclairage connectés. Sous licence Apache 2.0, il permet de créer des scénarios d'éclairage personnalisés et améliore les expériences utilisateur. | Tool | ★★ | ||
| 2023-11-09 07:02:10 | Le pouvoir de la simplicité: élever votre expérience de sécurité The Power of Simplicity: Elevating Your Security Experience (lien direct) |
Recent research underscores just how challenging the current threat and risk landscape is for businesses and their security and IT teams. Ransomware attacks are up 153% year over year. Business email compromise (BEC) attacks doubled during the same period. Meanwhile, the global deficit of skilled security personnel sits at about 4 million. New threats are emerging and existing ones are growing more sophisticated all the time. Security measures need to keep pace with these dynamics to be effective. Businesses must be proactive and aim to stop threats before they start, but still be able to respond with speed to incidents already in progress. To do that, you must understand how attackers are targeting your business. And you must be able to clearly communicate those risks to executive leadership and peer stakeholders. At Proofpoint, our goal is to protect our customers from advanced threats by streamlining our solutions and processes while also providing easy-to-understand threat visibility. That\'s why we introduced improvements to the usability and reporting of the Proofpoint Aegis threat protection platform. Read on to learn more. 3 Aegis usability enhancements The market spoke, and we listened. Feedback from our customers was key in developing all of the following user interface (UI) enhancements, which we focused around three goals: simplifying access, prioritizing usability and clarifying the threat landscape. 1: Simplifying access Complexity hinders productivity and innovation. With that in mind, Proofpoint launched a new single sign-on (SSO) portal to provide a centralized, frictionless user login experience to Aegis. Customers can now use a single URL and single set of credentials to log in to the platform and switch seamlessly between our products. That\'s a big win for businesses that use multiple Proofpoint solutions. Your business can expect to see improved operational efficiency. By simplifying access to the Aegis platform, we\'re reducing the time admins spend getting to work, navigating their environments and searching for tools. The SSO portal is a significant step forward in improving the usability and user experience of the Proofpoint Aegis platform. 2: Prioritizing usability Proofpoint\'s user-centric design approach means our solutions are becoming more intuitive and easier to use all the time. The new usability updates for Aegis reduce cognitive load by minimizing the mental effort that\'s required to focus on processes. This makes creating natural workflows less complex, which results in fewer errors and less time spent on manual work. Our intuitively designed tools reduce frustration and effort for users by enabling faster onboarding. They also provide better problem-solving and self-troubleshooting capabilities. Our goal of improved usability led us to incorporate new Email Protection modules into the updated cloud administration portal. The modules offer streamlined workflows and quicker response times. This means admins can perform their daily tasks and manage email threats more easily. And they don\'t have to navigate through complicated menus. The Email Protection modules are available now in PPS 8.20; they include the Email Firewall and Spam Configuration UIs. 3: Clarifying the threat landscape Proofpoint has long been at the forefront of bringing clarity to the threat landscape. And we know that when security and IT teams have more visibility, they can make more informed decisions. However, we also know that for actionable decisions to be truly effective, threat landscape visibility needs to be quick and easy for other stakeholders to grasp as well. We\'re striving to minimize information overload through summarized and contextually driven documentation. This helps you to always know and understand the cyberthreats your business is facing. Clear, easy to access data allows administrators to move fast to keep up with evolving threats. It also enhances the ability to communicate risk to nontechnical stakeholders w | Ransomware Spam Tool Threat Cloud | ★★ | ||
| 2023-11-08 19:27:00 | WhatsApp présente une nouvelle fonctionnalité de confidentialité pour protéger l'adresse IP dans les appels WhatsApp Introduces New Privacy Feature to Protect IP Address in Calls (lien direct) |
WhatsApp méta-constitué déploie officiellement une nouvelle fonctionnalité de confidentialité dans son service de messagerie appelé "Protect Adresse IP dans les appels" qui masque les utilisateurs \\ 'IP d'adresses à d'autres parties en relayant les appels via ses serveurs.
"Les appels sont cryptés de bout en bout, donc même si un appel est relayé via des serveurs WhatsApp, WhatsApp ne peut pas écouter vos appels", a déclaré la société dans un communiqué partagé avec le
Meta-owned WhatsApp is officially rolling out a new privacy feature in its messaging service called "Protect IP Address in Calls" that masks users\' IP addresses to other parties by relaying the calls through its servers. "Calls are end-to-end encrypted, so even if a call is relayed through WhatsApp servers, WhatsApp cannot listen to your calls," the company said in a statement shared with The |
Tool | ★★★ | ||
| 2023-11-08 18:59:39 | Predator AI | ChatGPT-Powered Infostealer Takes Aim at Cloud Platforms (lien direct) | #### Description
Sentinellabs a identifié un nouvel infosteller basé sur Python et hacktool appelé \\ 'Predator Ai \' conçu pour cibler les services cloud.
Predator AI est annoncé via des canaux télégrammes liés au piratage.L'objectif principal de Predator est de faciliter les attaques d'applications Web contre diverses technologies couramment utilisées, y compris les systèmes de gestion de contenu (CMS) comme WordPress, ainsi que les services de messagerie cloud comme AWS SES.Cependant, Predator est un outil polyvalent, un peu comme les outils de spam de cloud Alienfox et Legion.Ces ensembles d'outils partagent un chevauchement considérable dans le code accessible au public qui réutilise chaque utilisation de leur marque, y compris l'utilisation des modules AndroxGH0st et Greenbot.
Le développeur AI Predator a implémenté une classe axée sur le chatppt dans le script Python, qui est conçue pour rendre l'outil plus facile à utiliser et pour servir d'interface de texte unique entre les fonctionnalités disparates.Il y avait plusieurs projets comme Blackmamba qui étaient finalement plus hype que l'outil ne pouvait livrer.L'IA prédateur est un petit pas en avant dans cet espace: l'acteur travaille activement à la fabrication d'un outil qui peut utiliser l'IA.
#### URL de référence (s)
1. https://www.sentinelone.com/labs/predator-ai-chatgpt-powered-infostealer-takes-aim-at-cloud-platforms/
#### Date de publication
7 novembre 2023
#### Auteurs)
Alex Delamotte
#### Description SentinelLabs has identified a new Python-based infostealer and hacktool called \'Predator AI\' that is designed to target cloud services. Predator AI is advertised through Telegram channels related to hacking. The main purpose of Predator is to facilitate web application attacks against various commonly used technologies, including content management systems (CMS) like WordPress, as well as cloud email services like AWS SES. However, Predator is a multi-purpose tool, much like the AlienFox and Legion cloud spamming toolsets. These toolsets share considerable overlap in publicly available code that each repurposes for their brand\'s own use, including the use of Androxgh0st and Greenbot modules. The Predator AI developer implemented a ChatGPT-driven class into the Python script, which is designed to make the tool easier to use and to serve as a single text-driven interface between disparate features. There were several projects like BlackMamba that ultimately were more hype than the tool could deliver. Predator AI is a small step forward in this space: the actor is actively working on making a tool that can utilize AI. #### Reference URL(s) 1. https://www.sentinelone.com/labs/predator-ai-chatgpt-powered-infostealer-takes-aim-at-cloud-platforms/ #### Publication Date November 7, 2023 #### Author(s) Alex Delamotte |
Tool Cloud | ChatGPT | ★★ | |
| 2023-11-08 18:27:00 | Méfiez-vous, développeurs: logiciels malveillants BlazesEaler découverts dans Python Packages sur PYPI Beware, Developers: BlazeStealer Malware Discovered in Python Packages on PyPI (lien direct) |
Un nouvel ensemble de packages Python malveillants a glissé son chemin vers le référentiel Python Package Index (PYPI) dans le but ultime de voler des informations sensibles à des systèmes de développeurs compromis.
Les forfaits se masquent comme des outils d'obscurcissement apparemment inoffensifs, mais abritent un logiciel malveillant appelé BlazesEaler, a déclaré Checkmarx dans un rapport partagé avec le Hacker News.
"[BLAZESTEALER]
A new set of malicious Python packages has slithered their way to the Python Package Index (PyPI) repository with the ultimate aim of stealing sensitive information from compromised developer systems. The packages masquerade as seemingly innocuous obfuscation tools, but harbor a piece of malware called BlazeStealer, Checkmarx said in a report shared with The Hacker News. "[BlazeStealer] |
Malware Tool | ★★ | ||
| 2023-11-08 16:30:00 | Guide: comment VCISOS, MSPS et MSSP peuvent protéger leurs clients des risques Gen AI Guide: How vCISOs, MSPs and MSSPs Can Keep their Customers Safe from Gen AI Risks (lien direct) |
Téléchargez le guide gratuit, "C'est un monde d'IA génératif: comment VCISO, MSPS et MSSPS peuvent protéger leurs clients des risques Gen Gen AI."
Chatgpt se vante désormais de 1,5 à 2 milliards de visites par mois.D'innombrables ventes, marketing, RH, exécutif informatique, soutien technique, opérations, finances et autres fonctions alimentent les invites de données et les requêtes dans les moteurs d'IA génératifs.Ils utilisent ces outils pour écrire
Download the free guide, "It\'s a Generative AI World: How vCISOs, MSPs and MSSPs Can Keep their Customers Safe from Gen AI Risks." ChatGPT now boasts anywhere from 1.5 to 2 billion visits per month. Countless sales, marketing, HR, IT executive, technical support, operations, finance and other functions are feeding data prompts and queries into generative AI engines. They use these tools to write |
Tool Technical | ChatGPT | ★★ | |
| 2023-11-08 11:44:35 | FBI: Ransomware Gangs Hack Casinos via des vendeurs de jeux tiers FBI: Ransomware gangs hack casinos via 3rd party gaming vendors (lien direct) |
Le Federal Bureau of Investigation avertit que les acteurs des menaces de ransomware ciblent les serveurs de casino et utilisent des outils de gestion des systèmes légitimes pour augmenter leurs autorisations sur le réseau.[...]
The Federal Bureau of Investigation is warning that ransomware threat actors are targeting casino servers and use legitimate system management tools to increase their permissions on the network. [...] |
Ransomware Hack Tool Threat | ★★★ | ||
| 2023-11-08 11:00:00 | Atténuer les menaces profondes dans le monde de l'entreprise: une approche médico-légale Mitigating deepfake threats in the corporate world: A forensic approach (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In an era where technology advances at breakneck speed, the corporate world finds itself facing an evolving and insidious threat: deepfakes. These synthetic media creations, powered by artificial intelligence (AI) algorithms, can convincingly manipulate audio, video, and even text - posing significant risks to businesses, their reputation, and their security. To safeguard against this emerging menace, a forensic approach is essential. Understanding deepfakes “Deepfake” is a term used to describe a type of synthetic media that is created or manipulated using artificial intelligence (AI) and deep learning algorithms. The term "deepfake" is a combination of "deep learning" and "fake." Deep learning is a subset of machine learning that involves training artificial neural networks to perform specific tasks, such as image or speech recognition. Deepfake technology is primarily associated with the manipulation of audio and video content, although it can also be applied to text. It allows for the creation of highly convincing and often indistinguishable fake content by superimposing one person\'s likeness and voice onto another person\'s image or video. Deepfake technology has been used in various real-world scenarios, raising concerns about its potential for misinformation and deception. For instance, a deepfake video of former President Barack Obama was manipulated to make it seem like he was delivering a speech using synthetic audio and video. In the entertainment industry, deepfake technology has been used to recreate deceased actors for film or commercial purposes. For example, a deepfake version of actor James Dean was used in a Vietnamese commercial. Deepfake content has been circulated on social media and news platforms, contributing to the spread of fake news and disinformation. This can include fabricated speeches, interviews, or events involving public figures. Deepfake technology has been exploited to create explicit content featuring individuals without their consent. This content is often used for harassment, revenge, or extortion. These examples illustrate the versatility of deepfake technology and the potential risks associated with its misuse. As a result, there is growing concern about the need for effective detection and countermeasures to address the potential negative consequences of deepfake manipulation in various contexts. Here are some key aspects of deepfake technology: Face swapping: Deepfake algorithms can replace the face of a person in a video with the face of another individual, making it appear as though the second person is speaking or acting in the video. Voice cloning: Deepfake technology can replicate a person\'s voice by analyzing their speech patterns and using AI to generate new audio recordings in that person\'s voice. Realistic visuals: Deepfake videos are known for their high degree of realism, with facial expressions, movements, and lip-syncing that closely resemble the original subject. Manipulated text: While less common, deepfake technology can also be used to generate fake text content that mimics an individual\'s writing style or produces fictional narratives. Misinformation and deception: Deepfakes have the potential to spread misinformation, deceive people, and create convincing fake content for various purposes, both benign and malicious. Implications for corporations Reputation damage: Corporations invest years in building their brand and reputation. Deepfake videos or audio recordings featuring corporate leaders making controversial statements can have devastating consequences. Financial fraud: Deepfakes can be used to impersonate executives, leading to fraudulent requests for funds, | Tool Vulnerability Threat Commercial | ★★ | ||
| 2023-11-08 07:00:00 | Une seule vitre peut-elle jamais être découverte pour la cybersécurité? Can a Single Pane of Glass Ever be Discovered for Cybersecurity? (lien direct) |
> Dans le paysage en constante évolution de la cybersécurité, le concept d'un «volet unique de verre» a longtemps été le Saint Graal pour de nombreuses organisations.L'idée est simple: consolider tous vos outils et données de cybersécurité sur un seul tableau de bord pour une visibilité et un contrôle améliorés. & # 160;Bien que ce concept contient du mérite, en particulier dans la main-d'œuvre hybride moderne, il \'s [& # 8230;]
>In the ever-evolving landscape of cybersecurity, the concept of a ”single pane of glass” has long been the Holy Grail for many organisations. The idea is simple: consolidate all your cybersecurity tools and data onto a single dashboard for improved visibility and control. While this concept holds merit, particularly in the modern hybrid workforce, it\'s […] |
Tool | ★★ | ||
| 2023-11-08 06:00:00 | Protéger vos chemins, partie 1: comment la gestion du chemin d'attaque peut arrêter les attaquants sur leurs traces Protecting Your Paths, Part 1: How Attack Path Management Can Stop Attackers in Their Tracks (lien direct) |
This blog is the first in a series where we explore attack path management. We\'ll explain what you need to know and give you the tools you need to help you better protect the middle of the attack chain. A big reason that successful cyberattacks are on the rise is that threat actors are shifting their tactics to identity-based attacks. Last year, 84% of businesses fell victim to an identity-related breach. When attackers land on a host, it is rarely their end target. Instead, they look to escalate privilege and move laterally across an environment. Their next step is to exploit more privileged credentials, and they often do this by using shadow admin vulnerabilities. It can be a challenge to stop them. To do so, you need to quickly discover, prioritize and remediate identity vulnerabilities. But first, you need to know what you\'re up against. In this blog post, we explore the multitude of identity vulnerability challenges, and we explain why an attack path management (APM) view is so important. We also specify which identity-centric attack vectors are likely to exist in your environment. Key terms Before we dive into this topic further, let\'s define some key terms that are central to this area of security: Attack path management. This refers to the process of identifying, analyzing, understanding and remediating attack paths within a business. Identities and other system resources are typically spread across multiple on-premises and cloud identity stores. These include Microsoft Active Directory (AD), Entra ID (formerly Azure AD), AWS and Okta. Attack path. Threat actors follow a sequence of steps as they compromise security, which is called an attack path. The typical end result is the compromise of a tier-zero asset (TZA)-or what is generally referred to as a bad breach. TZAs. Tier-zero assets are often referred to as the “crown jewels.” They are a company\'s most critical and sensitive assets. They can include systems, data or other resources (databases, web gateways) that are essential to its operation, reputation and overall resilience. In certain scenarios, AD domain controllers or authentication systems can be considered TZAs given the broad scope of damage that can arise with their breach. The risks of TZA compromise Compromising a tier-zero asset is a high-value objective for attackers because it allows them to achieve their financial or other malicious goals. Here are some common objectives: Data exfiltration TZAs may store or have access to critical and sensitive data or intellectual property. Or they might be critical system resources that, if compromised, could result in a service outage. Attackers aim to steal this information for financial gain, espionage or extortion. Data exfiltration clearly impacts the confidentiality part of the CIA triad. Data manipulation Attackers may alter or manipulate data within TZAs to achieve their goals. For instance, they could modify user account settings, insert malicious code or encrypt data as a step toward operational disruption. Data manipulation impacts the integrity part of the CIA triad. Denial of service (DoS) or disruption Attackers may use compromised tier-zero assets to launch DoS attacks against critical operational services in an enterprise. This can disrupt services and cause operational or financial harm to the business. This exposure category is about impacting the availability portion of the CIA triad. Ransomware Attackers may use their control over TZAs to deploy ransomware across a network. By encrypting critical systems and data, they can demand substantial ransom payments in exchange for the decryption keys. Ultimately ransomware attackers are focused on financial gain. One of their main tactics for extracting a ransom is threatening to directly impact system availability. (See this 2021 breach as an example.) Lateral movement to more TZAs Once attackers compromise a tier-zero asset, they can use it as a launch pad to move laterally to other TZAs. Figure 1. Tier-zero | Ransomware Tool Vulnerability Threat Cloud | ★★ | ||
| 2023-11-07 17:58:00 | La variante de logiciels malveillants de la nouvelle gootloader échappe à la détection et se propage rapidement New GootLoader Malware Variant Evades Detection and Spreads Rapidly (lien direct) |
Il a été constaté qu'une nouvelle variante du logiciel malveillant de gootloader appelé Gootbot facilite les mouvements latéraux sur des systèmes compromis et d'éviter la détection.
"L'introduction de leur propre bot personnalisé par le groupe de chèques dans les stades tardifs de leur chaîne d'attaque est une tentative d'éviter les détections lors de l'utilisation d'outils standard pour C2 tels que CobalTstrike ou RDP", chercheurs IBM X-ForceGolo m & uuml; hr et ole
A new variant of the GootLoader malware called GootBot has been found to facilitate lateral movement on compromised systems and evade detection. "The GootLoader group\'s introduction of their own custom bot into the late stages of their attack chain is an attempt to avoid detections when using off-the-shelf tools for C2 such as CobaltStrike or RDP," IBM X-Force researchers Golo Mühr and Ole |
Malware Tool | ★★★ | ||
| 2023-11-07 17:37:50 | Sécuriser les API: étapes pratiques pour protéger votre logiciel Securing APIs: Practical Steps to Protecting Your Software (lien direct) |
Dans le monde dynamique du développement de logiciels, les interfaces de programmation d'applications (API) servent de conduits essentiels, facilitant l'interaction transparente entre les composants logiciels.Cette interface intermédiaire rationalise non seulement le développement, mais permet également aux équipes logicielles de réutiliser le code.Cependant, la prévalence croissante des API dans les affaires modernes est accompagnée de défis de sécurité.C'est pourquoi nous avons créé ce billet de blog - pour vous fournir des étapes exploitables pour améliorer la sécurité de vos API aujourd'hui.
Comprendre la sécurité de l'API
La sécurité de l'API s'étend au-delà de la protection des services backend d'une application, y compris des éléments tels que des bases de données, des systèmes de gestion des utilisateurs et des composants interagissant avec les magasins de données.Il s'agit d'adopter divers outils et pratiques pour renforcer l'intégrité de votre pile technologique.Une forte stratégie de sécurité des API réduit le risque d'accès non autorisé et d'actions malveillantes, assurant la protection des informations sensibles.
Explorer les vulnérabilités API
Malgré la…
In the dynamic world of software development, Application Programming Interfaces (APIs) serve as essential conduits, facilitating seamless interaction between software components. This intermediary interface not only streamlines development but also empowers software teams to reuse code. However, the increasing prevalence of APIs in modern business comes with security challenges. That\'s why we\'ve created this blog post - to provide you with actionable steps to enhance the security of your APIs today. Understanding API Security API Security extends beyond protecting an application\'s backend services, including elements such as databases, user management systems, and components interacting with data stores. It involves adopting diverse tools and practices to strengthen the integrity of your tech stack. A strong API security strategy reduces the risk of unauthorized access and malicious actions, ensuring the protection of sensitive information. Exploring API Vulnerabilities Despite the… |
Tool Guideline | ★★ | ||
| 2023-11-07 16:30:00 | L'implant de chèvre augmentait le risque de ransomware post-infection GootBot Implant Heightens Risk of Post-Infection Ransomware (lien direct) |
IBM a trouvé un groupe de chèvre-chargeur optant pour des outils de gluant sur le mouvement latéral pour le mouvement latéral
IBM found Gootloader group opting for GootBot over off-the-shelf tools for lateral movement |
Ransomware Tool | ★★ | ||
| 2023-11-07 16:00:00 | Visual Studio Code Security: Deep Dive dans votre éditeur préféré (1/3) Visual Studio Code Security: Deep Dive into Your Favorite Editor (1/3) (lien direct) |
Nous avons examiné la sécurité de l'éditeur de code le plus populaire, Visual Studio Code!Ce billet de blog couvre les risques communs et les surfaces d'attaque afin que vous sachiez à quoi vous attendre lorsque vous l'utilisez.
We took a look at the security of the most popular code editor, Visual Studio Code! This blog post covers common risks and attack surfaces so you know what to expect when using it. |
Tool Vulnerability | ★★★ | ||
| 2023-11-07 15:59:21 | Eaton lance une plateforme logicielle pour les exploitatants de Data Centers (lien direct) | Eaton lance une plateforme logicielle inédite pour accélérer la transformation digitale et favoriser la durabilité des exploitants de datacenters • Cette nouvelle plateforme rassemble des outils de gestion des équipements, de mesure de la qualité énergétique, de surveillance des appareils informatiques et des technologies opérationnelles (OT), ainsi que d'autres fonctionnalités uniques, réunies en une seule application native • Cet ensemble de solutions digitales permet d'améliorer la durabilité, la résilience et les performances des infrastructures critiques dans les datacenters et les services d'informatique distribuée - Produits | Tool | ★★ | ||
| 2023-11-07 15:51:00 | AI offensif et défensif: le chat (GPT) de \\ Offensive and Defensive AI: Let\\'s Chat(GPT) About It (lien direct) |
Chatgpt: outil de productivité, idéal pour écrire des poèmes et… un risque de sécurité ?!Dans cet article, nous montrons comment les acteurs de la menace peuvent exploiter Chatgpt, mais aussi comment les défenseurs peuvent l'utiliser pour niveler leur jeu.
Chatgpt est l'application de consommation la plus en pleine croissance à ce jour.Le chatbot AI génératif extrêmement populaire a la capacité de générer des réponses humaines, cohérentes et contextuellement pertinentes.
ChatGPT: Productivity tool, great for writing poems, and… a security risk?! In this article, we show how threat actors can exploit ChatGPT, but also how defenders can use it for leveling up their game. ChatGPT is the most swiftly growing consumer application to date. The extremely popular generative AI chatbot has the ability to generate human-like, coherent and contextually relevant responses. |
Tool Threat | ChatGPT | ★★★ | |
| 2023-11-07 15:26:00 | Le projet de loi bipartisan vise à avoir un impact large sur les efforts de surveillance fédérale Bipartisan bill aims to have wide impact on federal surveillance efforts (lien direct) |
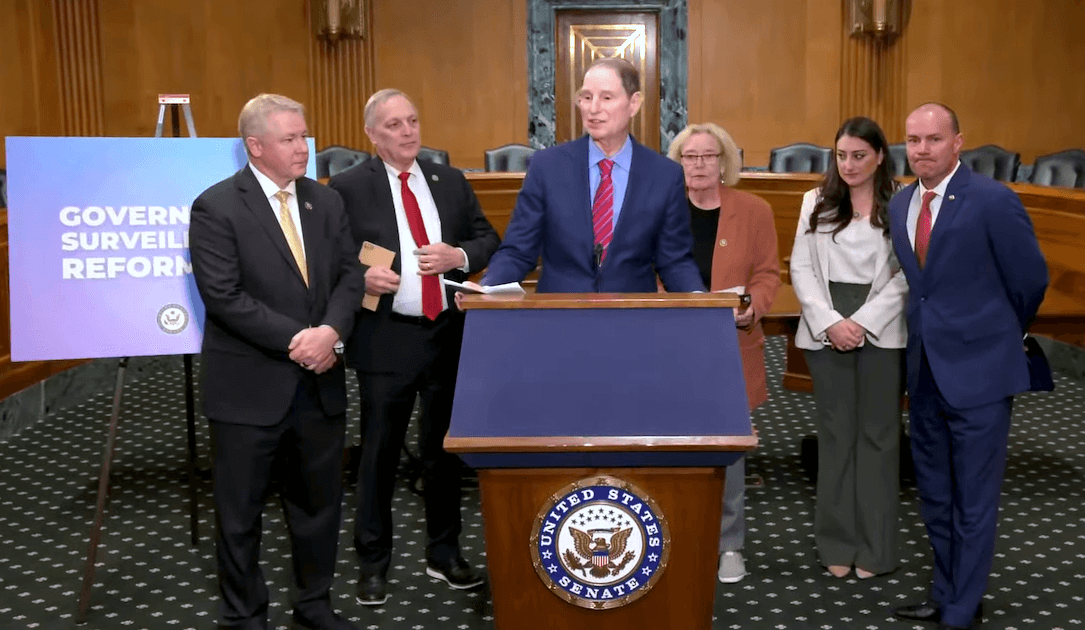 Cette année, la première législation majeure de \\ pour étendre les autorités de surveillance du gouvernement américain expirées est un effort bipartite qui comprendrait certaines des bordures les plus substantielles depuis des années sur ces outils et autres pouvoirs de renseignement.Un groupe de législateurs de la Chambre et du Sénat a introduit la mesure mardi pour renouveler l'article 702 de la Foreign Intelligence Act,
Cette année, la première législation majeure de \\ pour étendre les autorités de surveillance du gouvernement américain expirées est un effort bipartite qui comprendrait certaines des bordures les plus substantielles depuis des années sur ces outils et autres pouvoirs de renseignement.Un groupe de législateurs de la Chambre et du Sénat a introduit la mesure mardi pour renouveler l'article 702 de la Foreign Intelligence Act,
 This year\'s first major legislation to extend expiring U.S. government surveillance authorities is a bipartisan effort that would include some of the most substantial curbs in years on those tools and other intelligence powers. A group of House and Senate lawmakers introduced the measure on Tuesday to renew Section 702 of the Foreign Intelligence Act,
This year\'s first major legislation to extend expiring U.S. government surveillance authorities is a bipartisan effort that would include some of the most substantial curbs in years on those tools and other intelligence powers. A group of House and Senate lawmakers introduced the measure on Tuesday to renew Section 702 of the Foreign Intelligence Act, |
Tool Legislation | ★★ | ||
| 2023-11-07 08:00:00 | Boostez votre PC avec Windows Memory Cleaner ! (lien direct) | Windows Memory Cleaner est un nettoyeur de RAM gratuit et sans installation pour ordinateurs Windows. Il optimise la mémoire en utilisant des fonctionnalités natives et offre plusieurs options telles que l'optimisation automatique et le mode compact. L'outil est multilingue et permet aux utilisateurs de contribuer aux traductions. | Tool | ★★ | ||
| 2023-11-06 21:35:00 | Enlèvement virtuel: les outils d'IA permettent des escroqueries d'extorsion IRL Virtual Kidnapping: AI Tools Are Enabling IRL Extortion Scams (lien direct) |
Avec l'IA et les données accessibles au public, les cybercriminels ont les ressources dont ils ont besoin pour simuler un enlèvement réel et vous faire croire.
With AI and publicly available data, cybercriminals have the resources they need to fake a real-life kidnapping and make you believe it. |
Tool | ★★ | ||
| 2023-11-06 20:15:07 | CVE-2023-5719 (lien direct) | L'outil de configuration Windows Crimson 3.2 permet aux utilisateurs ayant un accès administratif pour définir de nouveaux mots de passe pour les utilisateurs et télécharger la configuration de sécurité résultante sur un appareil.Si un tel mot de passe contient le caractère en pourcentage (%), des valeurs non valides seront incluses, tronquant potentiellement la chaîne si un NUL est rencontré.Si le mot de passe simplifié n'est pas détecté par l'administrateur, l'appareil peut être laissé dans un état vulnérable en raison des informations d'identification plus bien compromises.Notez que les mots de passe entrés via le serveur Web Crimson System ne souffrent pas de cette vulnérabilité.
The Crimson 3.2 Windows-based configuration tool allows users with administrative access to define new passwords for users and to download the resulting security configuration to a device. If such a password contains the percent (%) character, invalid values will be included, potentially truncating the string if a NUL is encountered. If the simplified password is not detected by the administrator, the device might be left in a vulnerable state as a result of more-easily compromised credentials. Note that passwords entered via the Crimson system web server do not suffer from this vulnerability. |
Tool Vulnerability | |||
| 2023-11-06 19:56:48 | Le directeur de contre-terroriste a utilisé l'attaque du Hamas pour justifier le renouvellement du programme de surveillance de masse Counterterror Director Used Hamas Attack to Justify Mass Surveillance Program Renewal (lien direct) |
> La communauté du renseignement américain est confrontée à des appels pour réformer l'outil d'espionnage connu sous le nom de 702, qui devrait expirer à la fin de l'année.
>The U.S. intelligence community is facing calls to reform the spying tool known as 702, which is set to expire at the end of the year. |
Tool | ★★ | ||
| 2023-11-06 16:44:35 | AWS CodeWhisperer reconverti en expert MongoDB (lien direct) | En parallèle du chantier d'adaptation de CodeWhisperer aux codebases internes, AWS l'affine pour des outils spécifiques... dont MongoDB. | Tool | ★★ | ||
| 2023-11-06 13:55:00 | Google avertit comment les pirates pourraient abuser du service de calendrier en tant que canal C2 secret Google Warns How Hackers Could Abuse Calendar Service as a Covert C2 Channel (lien direct) |
Google met en garde contre les acteurs de menaces multiples partageant un exploit de preuve de concept public (POC) qui exploite son service de calendrier pour héberger une infrastructure de commandement et de contrôle (C2).
L'outil, appelé Google Calendar Rat (GCR), utilise des événements de calendrier Google pour C2 à l'aide d'un compte Gmail.Il a été publié pour la première fois sur Github en juin 2023.
"Le script crée une chaîne \\ 'Covert \' en exploitant l'événement
Google is warning of multiple threat actors sharing a public proof-of-concept (PoC) exploit that leverages its Calendar service to host command-and-control (C2) infrastructure. The tool, called Google Calendar RAT (GCR), employs Google Calendar Events for C2 using a Gmail account. It was first published to GitHub in June 2023. "The script creates a \'Covert Channel\' by exploiting the event |
Tool Threat | ★★★★ | ||
| 2023-11-06 11:00:00 | Appliquer une approche basée sur l'intelligence à la cybersécurité;SIEM et Dark Web Survering Applying an intelligence-based approach to Cybersecurity; SIEM and dark web monitoring (lien direct) |
“History repeatedly has demonstrated that inferior forces can win when leaders are armed with accurate intelligence.” – Central Intelligence Agency; Intelligence in War In the ever-changing landscape of global cybersecurity, the boundaries between traditional military intelligence and cybersecurity are increasingly blurred. At the heart of this convergence lies the science of intelligence analysis—a process fundamental to both realms. Equally important is the recognition of target indicators, which serve as harbingers of impending activities, whether on a battlefield or within the complex circuits of cyberspace. For the modern organization, Security Information and Event Management (SIEM) systems serve as the nexus where the ancient art of intelligence gathering meets the contemporary needs of cybersecurity. This fusion is further enriched by dark web monitoring, a relatively new frontier in information gathering that equips analysts with a fuller understanding of the threat landscape in the darker recesses of the Internet where cybercriminals do their bidding. Traditionally, military intelligence has been the linchpin of strategic and tactical decision-making. It involves complex processes for data collection, analysis, and interpretation. In short, it turns ubiquitous data into actionable intelligence. The types of data used in intelligence analysis range from intercepted radio communications, satellite images, and even information gathered from troops on the ground. Analysts and applications sift through this plethora of information to extract actionable insights, scrutinizing for target indicators—clues that signal the enemy\'s intent or location. For instance, an unusual accumulation of vehicles in a remote area could indicate the staging of troops, thereby serving as a target indicator. Recognizing such cues is crucial for informed decision-making. Likewise, in cybersecurity, intelligence analysis serves as the backbone of protective strategies. Here, data collection is continuous and automated, thanks to SIEM systems and security correlation engines. These systems aggregate logs from various network endpoints, generating alerts based on defined rules that flag anomalies or known indicators of compromise. Just as military analysts look for signs like troop movement or weapons stockpiling, cybersecurity analysts review SIEM logs for target indicators such as repeated failed login attempts or abnormal data transfers, which might indicate a cyber-attack. The enrichment of SIEM data sets through dark web monitoring brings a novel depth to cybersecurity. For the uninitiated, the dark web serves as a haven for cybercriminals, offering a marketplace for anything from hacking tools to stolen data. This space is often the first point of compromise, where stolen data may appear for sale or where impending cyber-attacks might be discussed. Dark web monitoring involves the tracking of these criminal forums and marketplaces for specific keywords, threats, or data sets related to an organization. Information gleaned from the dark web provides that extra layer of intelligence, allowing for a more proactive cybersecurity posture. For example, a company might discover on the dark web that its stolen user credentials or company client lists are being sold. This type of information is a specific target indication that a company has experienced a data breach at some level. The parallels between military intelligence and cybersecurity are not merely conceptual; they have practical implications. Military operations often employ real-ti | Data Breach Tool Threat | ★★ | ||
| 2023-11-06 07:20:56 | 3 erreurs courantes que vous faites avec votre programme de sensibilisation à la sécurité 3 Common Mistakes You\\'re Making with Your Security Awareness Program (lien direct) |
Despite the vast budget and resources invested in cybersecurity, breaches are still commonplace and increasingly impactful. When these incidents are analyzed, there is a common factor-the controlling technology is undermined by human action. This can include staff handing out credentials, facilitating unauthorized requests, falling for spoof emails and running malware at the behest of an attacker. When the World Economic Forum states that 95% of security breaches occur because of human action, it is clear that security awareness throughout your organization is imperative. Yet despite years of activity, more still needs to be done. Here are some things you may be doing that will hinder your security program-and, more importantly, the steps you can take to fix them. Mistake 1: You have named your security program incorrectly As simple as it sounds, you may have chosen a poor name for your security program. We all focus on security awareness and build “security awareness programs” for our businesses, but that isn\'t what we really want. Our true aim is more than just to improve awareness-it is to change behavior. Calling our program “security awareness” encourages us to focus on the wrong outcome. After all, if our real aim is to stop people smoking, we wouldn\'t call our initiative the “be aware of the risks of smoking campaign.” This has an easy fix: Change the name of your program. Decide on the outcome you want and name your program appropriately-such as \'Security Behavior Change Program\' or \'Build Security Culture Program.\' You will be amazed by the difference such a small change can make because the new title will be a constant reminder of what you are actually trying to achieve. Mistake 2: Thinking that \'lots of awareness\' leads to culture The second mistake is related to the first. All too often, programs decide they can change the culture of the organization by increasing the amount of awareness training that staff undertake. That won\'t happen. Culture is not the same as “lots of awareness.” There is an “ABC” maturity model that I use, which stands for awareness, behavior, culture. Each is a step that builds on the previous one. Critically, there is a pivot at each step-a change of focus that\'s required to transition from one level to the next. Let\'s assume we already do awareness. To pivot to behavior, you need to focus on making sure that your staff members understand the consequences of cybersecurity, both personally and professionally. Once they have awareness and motivation, they are much more likely to display the correct behavior. (There is science behind this simplified approach, and I recommend you check out Professor BJ Fogg\'s behavior model.) Once behavior is on the road to achievement, then culture becomes your goal. The pivot for the culture step is the creation of a wide-ranging perception that everyone around the business cares about security. Note that I use the word “perception.” It doesn\'t have to be true initially, as this is a real case of “fake it \'til you make it.” Create that perception by tuning your communications plan to ensure that security messages arrive from across your organization-from executives, from receptionists, and especially from middle and line managers. Indeed, these messages should come from almost everyone except the chief information security officer (CISO). This will build a perception in each staff member that everyone around them cares about security, and that will create peer pressure for them to act in similar ways. This is the crucible of culture. Mistake 3: Using negative consequences as a primary motivator The key step to mature to the behavior level mentioned above is to create a motivation to change behavior. Motivation can be encouraged in various ways. One approach is to create a fear of punishment or embarrassment if staff make an error or fail a security test. Many security professionals have strong opinions on this matter. Some believe that negative c | Malware Tool Vulnerability | ★★ | ||
| 2023-11-05 17:45:05 | Alors, avez-vous entendu parler de Havoc, le nouvel outil du cyber arsenal? So, have you heard about Havoc, the new tool in the cyber arsenal? (lien direct) |
Permettez-moi de vous donner la baisse de ce que le brassage dans le métro numérique avec ce nouveau logiciel appelé Havoc.Maintenant, vous pourriez être [Plus ...]
Let me give you the lowdown on what’s brewing in the digital underground with this fresh piece of software called Havoc. Now, you might be [more...] |
Tool Tool Technical | ★★★★ | ||
| 2023-11-05 14:40:37 | Outils d'étagère supérieurs: les huit meilleurs de Kali Linux Top Shelf Tools: The Best Eight of Kali Linux (lien direct) |
Vous avez soif pour briser les choses en toute sécurité?Soit les tests de stylo de parler et Kali Linux qu'est-ce que ce buzz ce que je continue à entendre?Vous êtes tombé sur [plus ...]
Got a Thirst for Breaking Things Securely? Let’s Talk Pen Testing and Kali Linux What’s this Pen Testing Buzz I Keep Hearing? You’ve stumbled across [more...] |
Tool | ★★★ | ||
| 2023-11-05 13:01:30 | Meilleurs outils logiciels de cybersécurité pour 2024 Best CyberSecurity Software Tools For 2024 (lien direct) |
En 2024, vous souhaitez être équipé des meilleurs outils de cybersécurité.Nous avons créé cette liste d'outils de cybersécurité qui contiennent une collection massive [plus ...]
In 2024, you want to be equipped with the best cybersecurity tools. We have created this list of cybersecurity tools that contain a massive collection [more...] |
Tool | ★★ | ||
| 2023-11-04 17:33:50 | Le partage de données transparente est-il la clé de l'amélioration de la collaboration en cybersécurité? Is Seamless Data Sharing the Key to Enhanced Cybersecurity Collaboration? (lien direct) |
Dans le labyrinthe de la cybersécurité, le partage de l'intelligence rapidement et en toute sécurité entre les outils et les équipes n'est pas critique.Pourquoi?Parce que la vitesse à [plus...]
In the labyrinth of cybersecurity, the sharing of intelligence swiftly and securely among tools and teams isn’t just beneficial-it’s critical. Why? Because the speed at [more...] |
Tool | ★★ |
To see everything:
Our RSS (filtrered)
