What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-03-25 03:28:07 | L'évolution de la cyberisoire pour perturber au-delà du marché Siem et XDR Cybereason\\'s evolution to disrupt beyond SIEM and XDR market (lien direct) |
 Aujourd'hui, les entreprises accélèrent pour investir dans la numérisation pour rester en avance sur la concurrence.Ils rencontrent de plus en plus un paysage en évolution des menaces et des défis de sécurité complexes - avec plus de charges de travail dans des nuages multiples, plus de main-d'œuvre dans des environnements hybrides et des appareils plus intelligents liés dans les opérations critiques de la mission.Ce parcours de transformation est exacerbé par une augmentation exponentielle des ressources de calcul, des volumes de données et des outils de sécurité, ce qui fait augmenter le coût du stockage, de la gestion et de l'analyse des données à des fins de sécurité.
Aujourd'hui, les entreprises accélèrent pour investir dans la numérisation pour rester en avance sur la concurrence.Ils rencontrent de plus en plus un paysage en évolution des menaces et des défis de sécurité complexes - avec plus de charges de travail dans des nuages multiples, plus de main-d'œuvre dans des environnements hybrides et des appareils plus intelligents liés dans les opérations critiques de la mission.Ce parcours de transformation est exacerbé par une augmentation exponentielle des ressources de calcul, des volumes de données et des outils de sécurité, ce qui fait augmenter le coût du stockage, de la gestion et de l'analyse des données à des fins de sécurité.
 Today enterprises are accelerating to invest into digitalization to stay ahead of competition. They are increasingly encountering an evolving threat landscape and complex security challenges - with more workloads in multi clouds, more workforces in hybrid environments, and more intelligent devices connected in mission critical operations. This transformation journey is exacerbated by exponential increase in compute resources, data volumes and security tooling, driving up the cost of storing, managing and analyzing the data for security purposes.
Today enterprises are accelerating to invest into digitalization to stay ahead of competition. They are increasingly encountering an evolving threat landscape and complex security challenges - with more workloads in multi clouds, more workforces in hybrid environments, and more intelligent devices connected in mission critical operations. This transformation journey is exacerbated by exponential increase in compute resources, data volumes and security tooling, driving up the cost of storing, managing and analyzing the data for security purposes. |
Threat | ★★ | ||
| 2024-03-19 18:33:51 | Podcast de vie malveillante: pouvez-vous bombarder un pirate? Malicious Life Podcast: Can You Bomb a Hacker? (lien direct) |

|
★★ | |||
| 2024-03-13 14:50:52 | Méfiez-vous des messagers, exploitant la vulnérabilité activeMQ Beware of the Messengers, Exploiting ActiveMQ Vulnerability (lien direct) |
Cybearason Security Services Problème des rapports d'analyse des menaces pour informer sur l'impact des menaces.Les rapports d'analyse des menaces étudient ces menaces et fournissent des recommandations pratiques pour se protéger contre eux.
 Cybereason Security Services issues Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them.
Cybereason Security Services issues Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them. |
Vulnerability Threat | ★★ | ||
| 2024-03-06 14:00:00 | Combler l'écart: équilibrer la conformité et l'innovation en matière de sécurité en cybersécurité Bridging the Gap: Balancing Security Compliance and Innovation in Cybersecurity (lien direct) |
 En tant qu'ex-Amazonien (AWS) et Native Native par passion, je n'ai jamais pensé écrire un article de blog comme celui qui suit.Mais je suis aussi un défenseur, un passionné de cybersécurité et surtout obsédé par le client et donc je reconnais que le monde n'est pas en noir et blanc, mais il est coloré avec un large éventail de couleurs et plusieurs nuances.Il en va de même pour les exigences des entreprises.Cela nous amène aux questions:
En tant qu'ex-Amazonien (AWS) et Native Native par passion, je n'ai jamais pensé écrire un article de blog comme celui qui suit.Mais je suis aussi un défenseur, un passionné de cybersécurité et surtout obsédé par le client et donc je reconnais que le monde n'est pas en noir et blanc, mais il est coloré avec un large éventail de couleurs et plusieurs nuances.Il en va de même pour les exigences des entreprises.Cela nous amène aux questions:
 As an Ex-Amazonian (AWS) and cloud-native guy by passion, I never thought I would write a blog post like the following. But I\'m also a Defender, a cyber security enthusiast and most of all customer obsessed and therefore I recognize that the world is not black and white, instead it\'s colorful with a wide range of colors and several nuances. So are the requirements from companies. This leads us to the questions:
As an Ex-Amazonian (AWS) and cloud-native guy by passion, I never thought I would write a blog post like the following. But I\'m also a Defender, a cyber security enthusiast and most of all customer obsessed and therefore I recognize that the world is not black and white, instead it\'s colorful with a wide range of colors and several nuances. So are the requirements from companies. This leads us to the questions: |
★★ | |||
| 2024-03-05 14:41:54 | Débloquer Snake - Python InfostEaler qui se cache à travers les services de messagerie Unboxing Snake - Python Infostealer Lurking Through Messaging Services (lien direct) |
 Les services de sécurité de la cyberison des problèmes d'analyse des menaces pour informer les menaces.Les rapports d'analyse des menaces étudient ces menaces et fournissent des recommandations pratiques pour se protéger contre eux.
Les services de sécurité de la cyberison des problèmes d'analyse des menaces pour informer les menaces.Les rapports d'analyse des menaces étudient ces menaces et fournissent des recommandations pratiques pour se protéger contre eux.
 Cybereason Security Services issues Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them.
Cybereason Security Services issues Threat Analysis reports to inform on impacting threats. The Threat Analysis reports investigate these threats and provide practical recommendations for protecting against them. |
Threat | ★★ | ||
| 2024-03-01 17:40:00 | Podcast de vie malveillante: Kevin Mitnick, partie 2 Malicious Life Podcast: Kevin Mitnick, Part 2 (lien direct) |
★★ | ||||
| 2024-02-21 21:57:49 | Ransomware: véritable coût pour les entreprises 2024 Ransomware: True Cost to Business 2024 (lien direct) |

|
Ransomware Studies | ★★★★ | ||
| 2024-02-20 17:29:26 | Annonce de la cyberison sur site Announcing Cybereason On-Prem (lien direct) |
★★ | ||||
| 2024-02-19 21:39:00 | Podcast de vie malveillante: Kevin Mitnick, partie 1 Malicious Life Podcast: Kevin Mitnick, Part 1 (lien direct) |

|
★★★ | |||
| 2024-02-12 16:37:24 | De Cracked à piraté: les logiciels malveillants se propagent via des vidéos YouTube From Cracked to Hacked: Malware Spread via YouTube Videos (lien direct) |
 Ce rapport d'analyse des menaces se plongera dans les comptes YouTube compromis utilisés comme vecteur pour la propagation des logiciels malveillants.Il décrira comment ce vecteur d'attaque est exploité pour les campagnes à faible combustion et à faible coût, mettant en évidence les stratégies utilisées par les acteurs de la menace et comment les défenseurs peuvent détecter et prévenir ces attaques. & NBSP;
Ce rapport d'analyse des menaces se plongera dans les comptes YouTube compromis utilisés comme vecteur pour la propagation des logiciels malveillants.Il décrira comment ce vecteur d'attaque est exploité pour les campagnes à faible combustion et à faible coût, mettant en évidence les stratégies utilisées par les acteurs de la menace et comment les défenseurs peuvent détecter et prévenir ces attaques. & NBSP;
 This Threat Analysis Report will delve into compromised YouTube accounts being used as a vector for the spread of malware. It will outline how this attack vector is exploited for low-burn, low-cost campaigns, highlighting strategies used by threat actors and how defenders can detect and prevent these attacks.
This Threat Analysis Report will delve into compromised YouTube accounts being used as a vector for the spread of malware. It will outline how this attack vector is exploited for low-burn, low-cost campaigns, highlighting strategies used by threat actors and how defenders can detect and prevent these attacks. |
Malware Threat | ★★★ | ||
| 2024-02-06 04:35:35 | Alerte de menace: Ivanti Connect Secure VPN Zero-Day Exploitation THREAT ALERT: Ivanti Connect Secure VPN Zero-Day Exploitation (lien direct) |
 Cybereason Issues Menace Alertes pour informer les clients de l'émergence des menaces impactantes, y compris des vulnérabilités critiques telles que l'exploitation Ivanti Secure VPN Zero-Day.Les alertes de menaces de cyberéasie résument ces menaces et fournissent des recommandations pratiques pour se protéger contre elles.
Cybereason Issues Menace Alertes pour informer les clients de l'émergence des menaces impactantes, y compris des vulnérabilités critiques telles que l'exploitation Ivanti Secure VPN Zero-Day.Les alertes de menaces de cyberéasie résument ces menaces et fournissent des recommandations pratiques pour se protéger contre elles.
 Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including critical vulnerabilities such as the Ivanti Connect Secure VPN Zero-Day exploitation. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including critical vulnerabilities such as the Ivanti Connect Secure VPN Zero-Day exploitation. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them. |
Vulnerability Threat | ★★ | ||
| 2024-02-05 20:53:17 | Podcast de vie malveillante: Enregistrement SIM: Sécurité ou surveillance? Malicious Life Podcast: SIM Registration: Security, or Surveillance? (lien direct) |
★★ | ||||
| 2024-01-29 15:39:52 | THREAT ALERT: DarkGate Loader (lien direct) |
 Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including recently observed DarkGate Loader. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including recently observed DarkGate Loader. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
 Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including recently observed DarkGate Loader. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them.
Cybereason issues Threat Alerts to inform customers of emerging impacting threats, including recently observed DarkGate Loader. Cybereason Threat Alerts summarize these threats and provide practical recommendations for protecting against them. |
Threat | ★★★ | ||
| 2024-01-22 17:58:00 | Podcast de vie malveillante: le botnet Mariposa Malicious Life Podcast: The Mariposa Botnet (lien direct) |
★★★ | ||||
| 2024-01-16 15:14:10 | Qu'est-ce que les esprits les plus intelligents de la cybersécurité pour 2024? What\\'s on the Smartest Cybersecurity Minds for 2024? (lien direct) |

|
★★★ | |||
| 2024-01-09 17:57:00 | Podcast de vie malveillante: la vraie histoire du piratage de 10 millions de dollars de Citibank \\ Malicious Life Podcast: The Real Story of Citibank\\'s $10M Hack (lien direct) |
 Valdimir Levin est souvent présenté comme "le premier voleur de banque en ligne" et apparaît sur de nombreuses listes des "10 meilleurs pirates de pirates".Mais quelques pirates vétérans russes CLIAM que le tristement célèbre piratage de Levin avait été mutilé par les Journlists qui ont écrit à ce sujet.Quelle est la vérité derrière le hack Citibank de 10,7 millions de dollars en 1994?…
Valdimir Levin est souvent présenté comme "le premier voleur de banque en ligne" et apparaît sur de nombreuses listes des "10 meilleurs pirates de pirates".Mais quelques pirates vétérans russes CLIAM que le tristement célèbre piratage de Levin avait été mutilé par les Journlists qui ont écrit à ce sujet.Quelle est la vérité derrière le hack Citibank de 10,7 millions de dollars en 1994?…
 Valdimir Levin is often presented as "the first online bank robber," and appeares on many lists of the "Top 10 Greatest Hackers." But a few veteran Russian hackers cliam that Levin\'s infamous hack had been mangled by the journlists who wrote about it. What\'s the truth behind the 1994 $10.7 million Citibank hack?…
Valdimir Levin is often presented as "the first online bank robber," and appeares on many lists of the "Top 10 Greatest Hackers." But a few veteran Russian hackers cliam that Levin\'s infamous hack had been mangled by the journlists who wrote about it. What\'s the truth behind the 1994 $10.7 million Citibank hack?… |
Hack | ★★★ | ||
| 2024-01-08 22:01:59 | Podcast de la vie malveillante: NSO est-il mal?Partie 1 Malicious Life Podcast: Is NSO Evil? Part 1 (lien direct) |

|
★★★ | |||
| 2024-01-08 22:01:58 | Podcast de vie malveillante: devriez-vous payer des attaquants de ransomwares?Une approche de théorie des jeux Malicious Life Podcast: Should You Pay Ransomware Attackers? A Game Theory Approach (lien direct) |

|
Ransomware | ★★★ | ||
| 2024-01-08 22:01:56 | Podcast de vie malveillante: Opération Kudo Malicious Life Podcast: Operation Kudo (lien direct) |

|
★★★ | |||
| 2023-12-18 16:09:11 | Alerte de menace: Citriced (CVE-2023-4966) THREAT ALERT: CITRIXBLEED (CVE-2023-4966) (lien direct) |

|
Threat | ★★ | ||
| 2023-11-28 15:41:00 | Alerte de menace: variante DJVU livrée par le chargeur se faisant passer pour un logiciel gratuit THREAT ALERT: DJvu Variant Delivered by Loader Masquerading as Freeware (lien direct) |

|
Threat | ★★★ | ||
| 2023-11-27 16:07:26 | 2024 Prédictions de la cybersécurité - L'IA générative remodèle la cybersécurité 2024 Cybersecurity Predictions - Generative AI Reshapes Cybersecurity (lien direct) |
Prediction Cloud | ★★ | |||
| 2023-11-20 18:11:31 | Alerte de menace: Ransomware INC THREAT ALERT: INC Ransomware (lien direct) |

|
Ransomware Threat | ★★★ | ||
| 2023-10-25 13:30:00 | Sécurité des informations du réseau de l'UE EU Network Information Security (lien direct) |

|
★★ | |||
| 2023-10-24 13:00:00 | 2023 Détection et réponse prolongée (XDR) Guide de l'acheteur \\ 2023 Extended Detection & Response (XDR) Buyer\\'s Guide (lien direct) |
★★ | ||||
| 2023-10-23 14:03:56 | Toute la sécurité EPP n'est pas la même - changer le garde! NOT all EPP Security is the Same - Changing the Guard! (lien direct) |
 Lorsque j'ai commencé à antivirus en 1991, la solution était simple: trouver un identifiant unique pour détecter les logiciels malveillants, alors vous pouvez le bloquer et si nécessaire, inciter les bonnes étapes programmatiques pour récupérer.Alan Salomon dirait que c'est un problème mathématique, nous avons la solution, et nous pouvons l'étendre infiniment.Cependant, au fil des ans, les menaces, les solutions et les environnements dans lesquels nous les déployons sont devenus de plus en plus complexes.Nous sommes passés à partir de virus de fichiers qui étaient un objet simple à des attaques de ransomwares multiples complexes composées de centaines d'éléments.Tout comme un exemple si vous regardez le Dernier test de mitres , il a utilisé Turla qui est composé de 143objets (indicateurs & amp; comportements liés à l'attaque). & nbsp;
Lorsque j'ai commencé à antivirus en 1991, la solution était simple: trouver un identifiant unique pour détecter les logiciels malveillants, alors vous pouvez le bloquer et si nécessaire, inciter les bonnes étapes programmatiques pour récupérer.Alan Salomon dirait que c'est un problème mathématique, nous avons la solution, et nous pouvons l'étendre infiniment.Cependant, au fil des ans, les menaces, les solutions et les environnements dans lesquels nous les déployons sont devenus de plus en plus complexes.Nous sommes passés à partir de virus de fichiers qui étaient un objet simple à des attaques de ransomwares multiples complexes composées de centaines d'éléments.Tout comme un exemple si vous regardez le Dernier test de mitres , il a utilisé Turla qui est composé de 143objets (indicateurs & amp; comportements liés à l'attaque). & nbsp;
 When I started in anti-virus back in 1991, the solution was simple: find a unique identifier to detect the malware, then you could block it and if needed instigate the right programmatic steps to recover. Alan Solomon would say it\'s a math problem, we have the solution, and we can scale it infinitely. However, over the years threats, the solutions and the environments we deploy them into have become ever more complex. We have moved from file viruses that were one simple object to complex multifaceted ransomware attacks made up of hundreds of elements. Just as an example if you look at the latest MITRE testing, it used Turla which is made up of 143 objects (Indicators & behaviors linked to the attack).
When I started in anti-virus back in 1991, the solution was simple: find a unique identifier to detect the malware, then you could block it and if needed instigate the right programmatic steps to recover. Alan Solomon would say it\'s a math problem, we have the solution, and we can scale it infinitely. However, over the years threats, the solutions and the environments we deploy them into have become ever more complex. We have moved from file viruses that were one simple object to complex multifaceted ransomware attacks made up of hundreds of elements. Just as an example if you look at the latest MITRE testing, it used Turla which is made up of 143 objects (Indicators & behaviors linked to the attack). |
Ransomware | ★★★ | ||
| 2023-10-06 17:53:23 | Analyse des menaces: prendre des raccourcis… en utilisant des fichiers LNK pour l'infection initiale et la persistance THREAT ANALYSIS: Taking Shortcuts… Using LNK Files for Initial Infection and Persistence (lien direct) |

|
Threat | ★★★ | ||
| 2023-09-20 13:10:48 | La cyberison établit la nouvelle norme de l'industrie en 2023 Évaluations de Mitre ATT & CK: Enterprise Cybereason Sets the New Industry Standard in 2023 MITRE ATT&CK Evaluations: Enterprise (lien direct) |
 Fresh Off the Press: Les résultats de la 2023 MITER ENNÉNUITION ATT & AMP; CK & reg; Évaluations: Entreprise ont été publiés, mettant 30 solutions de sécurité au test dans des scénarios réels qui imitent l'acteur de la menace Turla.
Fresh Off the Press: Les résultats de la 2023 MITER ENNÉNUITION ATT & AMP; CK & reg; Évaluations: Entreprise ont été publiés, mettant 30 solutions de sécurité au test dans des scénarios réels qui imitent l'acteur de la menace Turla.
 Fresh off the press: the results of the 2023 MITRE Engenuity ATT&CK® Evaluations: Enterprise have been published, putting 30 security solutions to the test in real world scenarios that mimic the Turla threat actor.
Fresh off the press: the results of the 2023 MITRE Engenuity ATT&CK® Evaluations: Enterprise have been published, putting 30 security solutions to the test in real world scenarios that mimic the Turla threat actor. |
Threat | ★★ | ||
| 2023-09-13 14:47:38 | La capacité de cybersécurité que l'industrie a presque oublié The Cybersecurity Capability the Industry Nearly Forgot (lien direct) |
 Lorsque j'ai commencé en cybersécurité au début des 90 \\, des capacités de cybersécurité entières n'étaient que quelques Mo de taille et s'adapteraient sur quelques disquettes.Aujourd'hui, de nombreuses capacités de cybersécurité sont si grandes et complexes qu'elles s'appuient sur le cloud computing, soit pour la vitesse de traitement, soit la possibilité de tirer parti de grands ensembles de données utilisés par exemple avec l'apprentissage automatique dans le cadre des capacités de détection et de réponse. & Nbsp; & nbsp;
Lorsque j'ai commencé en cybersécurité au début des 90 \\, des capacités de cybersécurité entières n'étaient que quelques Mo de taille et s'adapteraient sur quelques disquettes.Aujourd'hui, de nombreuses capacités de cybersécurité sont si grandes et complexes qu'elles s'appuient sur le cloud computing, soit pour la vitesse de traitement, soit la possibilité de tirer parti de grands ensembles de données utilisés par exemple avec l'apprentissage automatique dans le cadre des capacités de détection et de réponse. & Nbsp; & nbsp;
 When I started in cybersecurity back in the early 90\'s, entire cyber security capabilities were just a couple of MB in size and would fit on a couple of floppy disks. Today, many cyber security capabilities are so big and complex that they rely on cloud computing, either for processing speed or the ability to leverage large data sets used in for example with Machine Learning as part of the detection and response capabilities.
When I started in cybersecurity back in the early 90\'s, entire cyber security capabilities were just a couple of MB in size and would fit on a couple of floppy disks. Today, many cyber security capabilities are so big and complex that they rely on cloud computing, either for processing speed or the ability to leverage large data sets used in for example with Machine Learning as part of the detection and response capabilities. |
Cloud | ★★ | ||
| 2023-08-22 20:24:00 | Podcast Malicious Life : L’IA générative est-elle dangereuse ? Malicious Life Podcast: Is Generative AI Dangerous? (lien direct) |
 De temps en temps, l'ensemble du paysage de la cybersécurité change d'un seul coup : le dernier changement sismique dans le domaine s'est produit l'année dernière seulement.Ainsi, dans cet épisode de Malicious Life, nous allons nous pencher sur l'avenir de la cybersécurité : comment l'IA générative comme ChatGPT va changer le cyberespace, à travers les yeux de cinq équipes de recherche innovatrices dans le domaine.Nous commencerons par des choses simples, puis nous passerons progressivement à des exemples de plus en plus complexes et futuristes montrant comment cette technologie pourrait bien se retourner contre nous, nous obligeant à résoudre des problèmes que nous n'avions jamais envisagés auparavant. – ;vérifiez-le...
De temps en temps, l'ensemble du paysage de la cybersécurité change d'un seul coup : le dernier changement sismique dans le domaine s'est produit l'année dernière seulement.Ainsi, dans cet épisode de Malicious Life, nous allons nous pencher sur l'avenir de la cybersécurité : comment l'IA générative comme ChatGPT va changer le cyberespace, à travers les yeux de cinq équipes de recherche innovatrices dans le domaine.Nous commencerons par des choses simples, puis nous passerons progressivement à des exemples de plus en plus complexes et futuristes montrant comment cette technologie pourrait bien se retourner contre nous, nous obligeant à résoudre des problèmes que nous n'avions jamais envisagés auparavant. – ;vérifiez-le...
 Every so often, the entire landscape of cybersecurity shifts, all at once: The latest seismic shift in the field occurred just last year. So in this episode of Malicious Life we\'re going to take a look into the future of cybersecurity: at how generative AI like ChatGPT will change cyberspace, through the eyes of five research teams breaking ground in the field. We\'ll start off simple, and gradually build to increasingly more complex, more futuristic examples of how this technology might well turn against us, forcing us to solve problems we\'d never considered before. – check it out...
Every so often, the entire landscape of cybersecurity shifts, all at once: The latest seismic shift in the field occurred just last year. So in this episode of Malicious Life we\'re going to take a look into the future of cybersecurity: at how generative AI like ChatGPT will change cyberspace, through the eyes of five research teams breaking ground in the field. We\'ll start off simple, and gradually build to increasingly more complex, more futuristic examples of how this technology might well turn against us, forcing us to solve problems we\'d never considered before. – check it out... |
ChatGPT ChatGPT | ★★ | ||
| 2023-08-21 20:45:00 | Analyse des menaces: assembler Lockbit 3.0 THREAT ANALYSIS: Assemble LockBit 3.0 (lien direct) |

|
Threat | ★★ | ||
| 2023-08-09 13:00:00 | Étendre la détection et la réponse des nuages avec Sysdig et Cybearon Extend Cloud Detection and Response with Sysdig and Cybereason (lien direct) |
|
Cloud | ★★ | ||
| 2023-08-08 16:36:00 | Podcast de vie malveillant: pourquoi y est-il plus de programmes de primes de bug? Malicious Life Podcast: Why aren\\'t there more bug bounty programs? (lien direct) |

|
★★ | |||
| 2023-07-07 14:20:36 | Le nouveau tableau de bord Unified Malop de Cybereason \\ Cybereason\\'s New Unified MalOp Dashboard (lien direct) |
 Cybearason est ravi d'annoncer un nouveau tableau de bord Unified Malop
Alors que les cybermenaces continuent d'évoluer, les équipes du Centre des opérations de sécurité (SOC) sont confrontées à d'immenses défis dans la protection de leurs organisations.Pour réussir, SOC a besoin non seulement de la bonne technologie, mais aussi un effet de levier efficace des personnes et des processus.Pour aider les équipes SOC à rester en avance sur la courbe, la cyber-saison introduit un tableau de bord unifié conçu pour fournir des informations supplémentaires sur les menaces émergentes, les mesures opérationnelles et fournir des informations pour améliorer continuellement les processus et les procédures du SoC.
Cybearason est ravi d'annoncer un nouveau tableau de bord Unified Malop
Alors que les cybermenaces continuent d'évoluer, les équipes du Centre des opérations de sécurité (SOC) sont confrontées à d'immenses défis dans la protection de leurs organisations.Pour réussir, SOC a besoin non seulement de la bonne technologie, mais aussi un effet de levier efficace des personnes et des processus.Pour aider les équipes SOC à rester en avance sur la courbe, la cyber-saison introduit un tableau de bord unifié conçu pour fournir des informations supplémentaires sur les menaces émergentes, les mesures opérationnelles et fournir des informations pour améliorer continuellement les processus et les procédures du SoC.
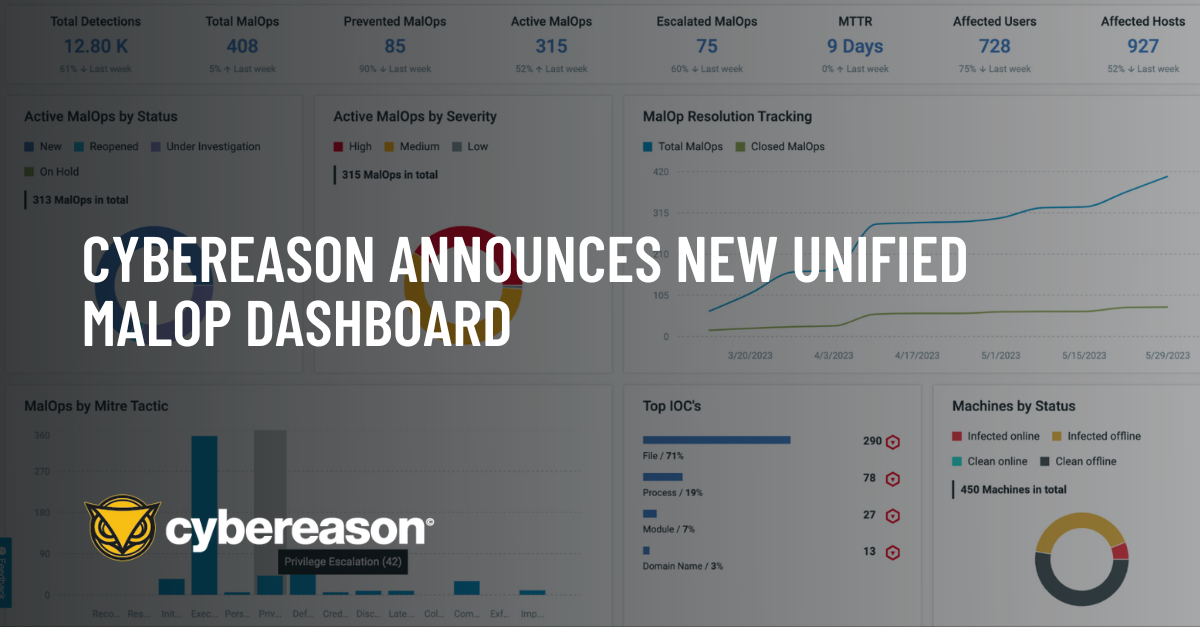 Cybereason is excited to announce a new unified Malop Dashboard
As cyber threats continue to evolve, Security Operations Center (SOC) teams face immense challenges in protecting their organizations. To be successful SOC needs not only the right technology but effective leverage of people and processes. To help SOC teams stay ahead of the curve, Cybereason introduces a unified dashboard designed to provide additional insights into emerging threats, operational metrics and provide insights to continuously improve SOC processes and procedures.
Cybereason is excited to announce a new unified Malop Dashboard
As cyber threats continue to evolve, Security Operations Center (SOC) teams face immense challenges in protecting their organizations. To be successful SOC needs not only the right technology but effective leverage of people and processes. To help SOC teams stay ahead of the curve, Cybereason introduces a unified dashboard designed to provide additional insights into emerging threats, operational metrics and provide insights to continuously improve SOC processes and procedures. |
★★ | |||
| 2023-06-21 13:39:09 | XDR en 2023: Knight de Cybersecurity \\ ou un autre château dans le nuage? XDR in 2023: Cybersecurity\\'s Knight or Another Castle in the Cloud? (lien direct) |
 3 questions clés lorsque vous investissez dans des offres XDR
Dans le paysage de la cybersécurité d'aujourd'hui, les équipes de sécurité ont besoin d'une plate-forme de détection et de réponse unifiée.Cependant, même avec l'avènement de XDR, les résultats ne sont souvent pas des attentes.Nous recherchons une prévention efficace, une émulation d'attaque, une amélioration et des rapports positifs sur le retour sur investissement.Sans aucun doute, le domaine de l'ingénierie à distance ajoute de la complexité, ce qui rend crucial pour protéger nos employés, nos données et maintenir la disponibilité.Dans le contexte des pressions commerciales de montage, nous devons comprendre comment XDR peut aider à la consolidation des fournisseurs et à la détection et à la réponse gérées.
3 questions clés lorsque vous investissez dans des offres XDR
Dans le paysage de la cybersécurité d'aujourd'hui, les équipes de sécurité ont besoin d'une plate-forme de détection et de réponse unifiée.Cependant, même avec l'avènement de XDR, les résultats ne sont souvent pas des attentes.Nous recherchons une prévention efficace, une émulation d'attaque, une amélioration et des rapports positifs sur le retour sur investissement.Sans aucun doute, le domaine de l'ingénierie à distance ajoute de la complexité, ce qui rend crucial pour protéger nos employés, nos données et maintenir la disponibilité.Dans le contexte des pressions commerciales de montage, nous devons comprendre comment XDR peut aider à la consolidation des fournisseurs et à la détection et à la réponse gérées.
 3 Key Questions when Investing in XDR offerings
In today\'s cybersecurity landscape, security teams are in dire need of a unified detection and response platform. However, even with the advent of XDR, the outcomes often fall short of expectations. We strive for effective prevention, attack emulation, improvement, and positive ROI reporting. No doubt, the realm of remote engineering adds complexity, making it crucial to protect our employees, data, and maintain uptime. Against a backdrop of mounting business pressures, we need to understand how XDR can help with vendor consolidation and Managed Detection and Response.
3 Key Questions when Investing in XDR offerings
In today\'s cybersecurity landscape, security teams are in dire need of a unified detection and response platform. However, even with the advent of XDR, the outcomes often fall short of expectations. We strive for effective prevention, attack emulation, improvement, and positive ROI reporting. No doubt, the realm of remote engineering adds complexity, making it crucial to protect our employees, data, and maintain uptime. Against a backdrop of mounting business pressures, we need to understand how XDR can help with vendor consolidation and Managed Detection and Response. |
★★★ | |||
| 2023-05-03 16:20:43 | Fondations XDR: éliminer les données de cybersécurité fragmentées XDR Foundations: Eliminating Fragmented Cybersecurity Data (lien direct) |

|
★★ | |||
| 2023-05-01 18:33:48 | Fondations XDR: tirer parti de l'IA là où cela compte le plus XDR Foundations: Leveraging AI Where it Matters Most (lien direct) |

|
★★ | |||
| 2023-04-26 14:16:20 | La cyberréason annonce la chasse et l'enquête unifiées aux menaces Cybereason Announces Unified Threat Hunting and Investigation (lien direct) |
 La cyberréasie est ravie d'annoncer un développement significatif dans son approche pour stocker des données de chasse à long terme (télémétrie collectée par nos capteurs pas \\ 'Données bénignes \' détectées par et liées à un malveillantOpération, ou
La cyberréasie est ravie d'annoncer un développement significatif dans son approche pour stocker des données de chasse à long terme (télémétrie collectée par nos capteurs pas \\ 'Données bénignes \' détectées par et liées à un malveillantOpération, ou |
Threat | ★★ | ||
| 2023-04-18 14:58:36 | All Things Cybereason à la conférence RSA 2023 All Things Cybereason at 2023 RSA Conference (lien direct) |

|
Conference | ★★ | ||
| 2023-04-03 13:40:01 | Cybearason obtient un financement de 100 millions de dollars, nomme un nouveau PDG Cybereason Secures $100M Funding, Appoints New CEO (lien direct) |
★★ | ||||
| 2023-03-31 15:08:17 | La cyberison détecte et empêche l'attaque de la chaîne d'approvisionnement du 3CXDESKTOPAPPAPPAPPAP [Cybereason Detects and Prevents 3CXDesktopApp Supply Chain Attack] (lien direct) |

|
★★ | |||
| 2023-03-15 11:30:00 | 5 Steps to More Effective Ransomware Response (lien direct) |

|
Ransomware Ransomware | ★★★ | ||
| 2023-03-14 10:00:00 | New Study: Ransomware Driving SOC Modernization Requirements (lien direct) |

|
Ransomware | ★★★ | ||
| 2023-03-09 15:20:53 | Visibility, Response, and Private Infrastructure Protection: Why Cybereason is a 2022 Gartner® Magic Quadrant™ Leader (lien direct) |

|
Guideline | ★★ | ||
| 2023-03-08 12:58:50 | U.S. National Cybersecurity: Strategy at an Inflection Point (lien direct) |
 The Biden administration issued a new cybersecurity strategy last week that has many observers applauding its emphasis on regulating minimum cybersecurity standards and enforcing so-called secure by design development practices, among other things.
The Biden administration issued a new cybersecurity strategy last week that has many observers applauding its emphasis on regulating minimum cybersecurity standards and enforcing so-called secure by design development practices, among other things. |
General Information | ★★ | ||
| 2023-03-03 13:00:00 | Variant Payload Prevention: Applying Data Science to Stop the Stealthiest Threats (lien direct) |

|
★★ | |||
| 2023-02-28 13:04:02 | Cybereason Named a Leader in 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms (lien direct) |

|
Guideline | ★★ | ||
| 2023-02-23 21:33:59 | New Studies Paint Bleak Picture of Future SOC Effectiveness (lien direct) |

|
Studies | ★★★ | ||
| 2023-02-14 19:20:18 | Ransomware Shifting to the Cloud (lien direct) |
 In the last few years, ransomware attacks have grown considerably. With 75% of organizations being attacked, it seems likely that we'll see a saturation point soon. And attackers have not been resting on their laurels. On the contrary, they have continued to evolve ransomware and are already in the fourth generation of this malicious software.
In the last few years, ransomware attacks have grown considerably. With 75% of organizations being attacked, it seems likely that we'll see a saturation point soon. And attackers have not been resting on their laurels. On the contrary, they have continued to evolve ransomware and are already in the fourth generation of this malicious software. |
Ransomware | ★★ | ||
| 2023-02-07 18:17:40 | THREAT ALERT: GootLoader - SEO Poisoning and Large Payloads Leading to Compromise (lien direct) |
 The Cybereason Incident Response (IR) team investigated an incident which involved new deployment methods of GootLoader through heavily-obfuscated JavaScript files. In addition to the new techniques used to load GootLoader, Cybereason also observed Cobalt Strike deployment, which leveraged DLL Hijacking, on top of a VLC MediaPlayer executable.
The Cybereason Incident Response (IR) team investigated an incident which involved new deployment methods of GootLoader through heavily-obfuscated JavaScript files. In addition to the new techniques used to load GootLoader, Cybereason also observed Cobalt Strike deployment, which leveraged DLL Hijacking, on top of a VLC MediaPlayer executable.
|
Threat Guideline | ★★★ |
To see everything:
Our RSS (filtrered)
