What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-10-05 18:00:07 | Network Security Monitoring vs Supply Chain Backdoors (lien direct) |  On October 4, 2018, Bloomberg published a story titled “The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies,” with a subtitle “The attack by Chinese spies reached almost 30 U.S. companies, including Amazon and Apple, by compromising America's technology supply chain, according to extensive interviews with government and corporate sources.” From the article:Since the implants were small, the amount of code they contained was small as well. But they were capable of doing two very important things: telling the device to communicate with one of several anonymous computers elsewhere on the internet that were loaded with more complex code; and preparing the device's operating system to accept this new code. The illicit chips could do all this because they were connected to the baseboard management controller, a kind of superchip that administrators use to remotely log in to problematic servers, giving them access to the most sensitive code even on machines that have crashed or are turned off.Companies mentioned in the story deny the details, so this post does not debate the merit of the Bloomberg reporters' claims. Rather, I prefer to discuss how a computer incident response team (CIRT) and a chief information security officer (CISO) should handle such a possibility. What should be done when hardware-level attacks enabling remote access via the network are possible?This is not a new question. I have addressed the architecture and practices needed to mitigate this attack model in previous writings. This scenario is a driving force behind my recommendation for network security monitoring (NSM) for any organization running a network, of any kind. This does not mean endpoint-centric security, or other security models, should be abandoned. Rather, my argument shows why NSM offers unique benefits when facing hardware supply chain attacks.The problem is one of trust and detectability. The problem here is that one loses trust in the integrity of a computing platform when one suspects a compromised hardware environment. One way to validate whether a computing platform is trustworthy is to monitor outside of it, at places where the hardware cannot know it is being monitored, and cannot interfere with that monitoring. Software installed on the hardware is by definition untrustworthy because the hardware backdoor may have the capability to obscure or degrade the visibility and control provided by an endpoint agent.Network security monitoring applied outside the hardware platform does not suffer this limitation, if certain safeguards are implemented. NSM suffers limitations unique to its deployment, of course, and they will be outlined shortly. By watching traffic to and from a suspected computing platform, CIRTs have a chance to identify suspicious and malicious activity, such as contact with remote command and control (C2) infrastructure. NSM data on this C2 activity can be collected and stored in many forms, such as any of the seven NSM data types: 1) full content; 2) extracted content; 3) session data; 4) transaction data; 5) statistical data; 6) metadata; and 7) alert data.Most likely session and transaction data would have been most useful for the case at hand. Once intelligence agencies identified that command and control infrastructure used by the alleged Chinese agents in this example, they could provide that information to the CIRT, who could then query historical NSM data for connectivity between enterprise a On October 4, 2018, Bloomberg published a story titled “The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies,” with a subtitle “The attack by Chinese spies reached almost 30 U.S. companies, including Amazon and Apple, by compromising America's technology supply chain, according to extensive interviews with government and corporate sources.” From the article:Since the implants were small, the amount of code they contained was small as well. But they were capable of doing two very important things: telling the device to communicate with one of several anonymous computers elsewhere on the internet that were loaded with more complex code; and preparing the device's operating system to accept this new code. The illicit chips could do all this because they were connected to the baseboard management controller, a kind of superchip that administrators use to remotely log in to problematic servers, giving them access to the most sensitive code even on machines that have crashed or are turned off.Companies mentioned in the story deny the details, so this post does not debate the merit of the Bloomberg reporters' claims. Rather, I prefer to discuss how a computer incident response team (CIRT) and a chief information security officer (CISO) should handle such a possibility. What should be done when hardware-level attacks enabling remote access via the network are possible?This is not a new question. I have addressed the architecture and practices needed to mitigate this attack model in previous writings. This scenario is a driving force behind my recommendation for network security monitoring (NSM) for any organization running a network, of any kind. This does not mean endpoint-centric security, or other security models, should be abandoned. Rather, my argument shows why NSM offers unique benefits when facing hardware supply chain attacks.The problem is one of trust and detectability. The problem here is that one loses trust in the integrity of a computing platform when one suspects a compromised hardware environment. One way to validate whether a computing platform is trustworthy is to monitor outside of it, at places where the hardware cannot know it is being monitored, and cannot interfere with that monitoring. Software installed on the hardware is by definition untrustworthy because the hardware backdoor may have the capability to obscure or degrade the visibility and control provided by an endpoint agent.Network security monitoring applied outside the hardware platform does not suffer this limitation, if certain safeguards are implemented. NSM suffers limitations unique to its deployment, of course, and they will be outlined shortly. By watching traffic to and from a suspected computing platform, CIRTs have a chance to identify suspicious and malicious activity, such as contact with remote command and control (C2) infrastructure. NSM data on this C2 activity can be collected and stored in many forms, such as any of the seven NSM data types: 1) full content; 2) extracted content; 3) session data; 4) transaction data; 5) statistical data; 6) metadata; and 7) alert data.Most likely session and transaction data would have been most useful for the case at hand. Once intelligence agencies identified that command and control infrastructure used by the alleged Chinese agents in this example, they could provide that information to the CIRT, who could then query historical NSM data for connectivity between enterprise a |
||||
| 2018-09-18 09:48:27 | Firewalls and the Need for Speed (lien direct) | I was looking for resources on campus network design and found these slides (pdf) from a 2011 Network Startup Resource Center presentation. These two caught my attention: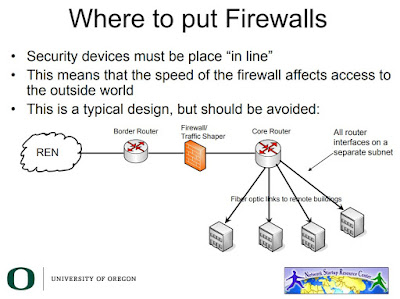  This bothered me, so I Tweeted about it.This started some discussion, and prompted me to see what NSRC suggests for architecture these days. You can find the latest, from April 2018, here. Here is the bottom line for their suggested architecture: This bothered me, so I Tweeted about it.This started some discussion, and prompted me to see what NSRC suggests for architecture these days. You can find the latest, from April 2018, here. Here is the bottom line for their suggested architecture:    What do you think of this architecture?My Tweet has attracted some attention from the high speed network researcher community, some of whom assume I must be a junior security apprentice who equates "firewall" with "security." Long-time blog readers will laugh at that, like I did. So what was my problem with the What do you think of this architecture?My Tweet has attracted some attention from the high speed network researcher community, some of whom assume I must be a junior security apprentice who equates "firewall" with "security." Long-time blog readers will laugh at that, like I did. So what was my problem with the |
Threat | |||
| 2018-09-11 12:07:37 | Twenty Years of Network Security Monitoring: From the AFCERT to Corelight (lien direct) | |||||
| 2018-07-22 10:05:07 | Defining Counterintelligence (lien direct) |  I've written about counterintelligence (CI) before, but I realized today that some of my writing, and the writing of others, may be confused as to exactly what CI means.The authoritative place to find an American definition for CI is the United States National Counterintelligence and Security Center. I am more familiar with the old name of this organization, the Office of the National Counterintelligence Executive (ONCIX).The 2016 National Counterintelligence Strategy cites Executive Order 12333 (as amended) for its definition of CI:Counterintelligence – Information gathered and activities conducted to identify, deceive,exploit, disrupt, or protect against espionage, other intelligence activities, sabotage, or assassinations conducted for or on behalf of foreign powers, organizations, or persons, or their agents, or international terrorist organizations or activities. (emphasis added)The strict interpretation of this definition is countering foreign nation state intelligence activities, such as those conducted by China's Ministry of State Security (MSS), the Foreign Intelligence Service of the Russian Federation (SVR RF), Iran's Ministry of Intelligence, or the military intelligence services of those countries and others.In other words, counterintelligence is countering foreign intelligence. The focus is on the party doing the bad things, and less on what the bad thing is.The definition, however, is loose enough to encompass others; "organizations," "persons," and "international terrorist organizations" are in scope, according to the definition. This is just about everyone, although criminals are explicitly not mentioned.The definition is also slightly unbounded by moving beyond "espionage, or other intelligence activities," to include "sabotage, or assassinations." In those cases, the assumptions is that foreign intelligence agencies and their proxies are the parties likely to be conducting sabotage or assassinations. In the course of their CI work, paying attention to foreign intelligence agents, the CI team may encounter plans for activities beyond collection.The bottom line for this post is a cautionary message. It's not appropriate to call all intelligence activities "counterintelligence." It's more appropriate to call countering adversary intelligence activities counterintelligence.You may use similar or the same approaches as counterintelligence agents when performing your cyber threat intelligence function. For example, you may recruit a source inside a carding forum, or you may plant your own source in a carding forum. This is similar to turning a foreign intelligence agent, or inserting your own agent in a foreign intelligence service. However, activities directing against a carding forum are not counterintelligence. Activities directing against a foreign intelligence service are counterintelligence.The nature and target of your intelligence activities are what determine if it is counterintelligence, not necessarily the methods you use. Again, this is in keeping with the stricter definition, and not becoming a victim of scope creep.Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecurity.b I've written about counterintelligence (CI) before, but I realized today that some of my writing, and the writing of others, may be confused as to exactly what CI means.The authoritative place to find an American definition for CI is the United States National Counterintelligence and Security Center. I am more familiar with the old name of this organization, the Office of the National Counterintelligence Executive (ONCIX).The 2016 National Counterintelligence Strategy cites Executive Order 12333 (as amended) for its definition of CI:Counterintelligence – Information gathered and activities conducted to identify, deceive,exploit, disrupt, or protect against espionage, other intelligence activities, sabotage, or assassinations conducted for or on behalf of foreign powers, organizations, or persons, or their agents, or international terrorist organizations or activities. (emphasis added)The strict interpretation of this definition is countering foreign nation state intelligence activities, such as those conducted by China's Ministry of State Security (MSS), the Foreign Intelligence Service of the Russian Federation (SVR RF), Iran's Ministry of Intelligence, or the military intelligence services of those countries and others.In other words, counterintelligence is countering foreign intelligence. The focus is on the party doing the bad things, and less on what the bad thing is.The definition, however, is loose enough to encompass others; "organizations," "persons," and "international terrorist organizations" are in scope, according to the definition. This is just about everyone, although criminals are explicitly not mentioned.The definition is also slightly unbounded by moving beyond "espionage, or other intelligence activities," to include "sabotage, or assassinations." In those cases, the assumptions is that foreign intelligence agencies and their proxies are the parties likely to be conducting sabotage or assassinations. In the course of their CI work, paying attention to foreign intelligence agents, the CI team may encounter plans for activities beyond collection.The bottom line for this post is a cautionary message. It's not appropriate to call all intelligence activities "counterintelligence." It's more appropriate to call countering adversary intelligence activities counterintelligence.You may use similar or the same approaches as counterintelligence agents when performing your cyber threat intelligence function. For example, you may recruit a source inside a carding forum, or you may plant your own source in a carding forum. This is similar to turning a foreign intelligence agent, or inserting your own agent in a foreign intelligence service. However, activities directing against a carding forum are not counterintelligence. Activities directing against a foreign intelligence service are counterintelligence.The nature and target of your intelligence activities are what determine if it is counterintelligence, not necessarily the methods you use. Again, this is in keeping with the stricter definition, and not becoming a victim of scope creep.Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecurity.b |
Threat | |||
| 2018-06-28 10:08:22 | Why Do SOCs Look Like This? (lien direct) | When you hear the word "SOC," or the phrase "security operations center," what image comes to mind? Do you think of analyst sitting at desks, all facing forward, towards giant screens? Why is this?The following image is from the outstanding movie Apollo 13, a docudrama about the challenged 1970 mission to the moon. It's a screen capture from the go for launch sequence. It shows mission control in Houston, Texas. If you'd like to see video of the actual center from 1970, check out This Is Mission Control.Mission control looks remarkably like a SOC, doesn't it? When builders of computer security operations centers imagined what their "mission control" rooms would look like, perhaps they had Houston in mind?Or perhaps they thought of the 1983 movie War Games? It's a screen capture from the go for launch sequence. It shows mission control in Houston, Texas. If you'd like to see video of the actual center from 1970, check out This Is Mission Control.Mission control looks remarkably like a SOC, doesn't it? When builders of computer security operations centers imagined what their "mission control" rooms would look like, perhaps they had Houston in mind?Or perhaps they thought of the 1983 movie War Games? Reality was way more boring however: Reality was way more boring however: I visited NORAD under Cheyenne Mountain in 1989, I believe, when visiting the Air Force Academy as a high school senior. I can confirm it did not look like the movie depiction!Let's return to mission control. Look at the resources available to personnel manning the mission control room. The big screens depict two main forms of data: telemetry and video of the rocket. What about the individual screens, where people sit? They are largely customized. Each station presents data or buttons specific to the role of the person sitting there. Listen to Ed Harris' character calling out the stations: booster, retro, vital, etc. For example: I visited NORAD under Cheyenne Mountain in 1989, I believe, when visiting the Air Force Academy as a high school senior. I can confirm it did not look like the movie depiction!Let's return to mission control. Look at the resources available to personnel manning the mission control room. The big screens depict two main forms of data: telemetry and video of the rocket. What about the individual screens, where people sit? They are largely customized. Each station presents data or buttons specific to the role of the person sitting there. Listen to Ed Harris' character calling out the stations: booster, retro, vital, etc. For example: This is one of the key differences between mission control and any modern computerized operations center. In the 1960s and 1970s, workstations (literally, places where people worked) had to be customized. They lacked the technology to have generic workstations where customization was done via screen, keyboard, and mouse. They also lacked the ability to display video on demand, and relied on large televi This is one of the key differences between mission control and any modern computerized operations center. In the 1960s and 1970s, workstations (literally, places where people worked) had to be customized. They lacked the technology to have generic workstations where customization was done via screen, keyboard, and mouse. They also lacked the ability to display video on demand, and relied on large televi |
||||
| 2018-06-25 15:03:20 | Bejtlich on the APT1 Report: No Hack Back (lien direct) |  Before reading the rest of this post, I suggest reading Mandiant/FireEye's statement Doing Our Part -- Without Hacking Back.I would like to add my own color to this situation.First, at no time when I worked for Mandiant or FireEye, or afterwards, was there ever a notion that we would hack into adversary systems. During my six year tenure, we were publicly and privately a "no hack back" company. I never heard anyone talk about hack back operations. No one ever intimated we had imagery of APT1 actors taken with their own laptop cameras. No one even said that would be a good idea.Second, I would never have testified or written, repeatedly, about our company's stance on not hacking back if I knew we secretly did otherwise. I have quit jobs because I had fundamental disagreements with company policy or practice. I worked for Mandiant from 2011 through the end of 2013, when FireEye acquired Mandiant, and stayed until last year (2017). I never considered quitting Mandiant or FireEye due to a disconnect between public statements and private conduct.Third, I was personally involved with briefings to the press, in public and in private, concerning the APT1 report. I provided the voiceover for a 5 minute YouTube video called APT1: Exposing One of China's Cyber Espionage Units. That video was one of the most sensitive, if not the most sensitive, aspects of releasing the report. We showed the world how we could intercept adversary communications and reconstruct it. There was internal debate about whether we should do that. We decided to cover the practice it in the report, as Christopher Glyer Tweeted: Before reading the rest of this post, I suggest reading Mandiant/FireEye's statement Doing Our Part -- Without Hacking Back.I would like to add my own color to this situation.First, at no time when I worked for Mandiant or FireEye, or afterwards, was there ever a notion that we would hack into adversary systems. During my six year tenure, we were publicly and privately a "no hack back" company. I never heard anyone talk about hack back operations. No one ever intimated we had imagery of APT1 actors taken with their own laptop cameras. No one even said that would be a good idea.Second, I would never have testified or written, repeatedly, about our company's stance on not hacking back if I knew we secretly did otherwise. I have quit jobs because I had fundamental disagreements with company policy or practice. I worked for Mandiant from 2011 through the end of 2013, when FireEye acquired Mandiant, and stayed until last year (2017). I never considered quitting Mandiant or FireEye due to a disconnect between public statements and private conduct.Third, I was personally involved with briefings to the press, in public and in private, concerning the APT1 report. I provided the voiceover for a 5 minute YouTube video called APT1: Exposing One of China's Cyber Espionage Units. That video was one of the most sensitive, if not the most sensitive, aspects of releasing the report. We showed the world how we could intercept adversary communications and reconstruct it. There was internal debate about whether we should do that. We decided to cover the practice it in the report, as Christopher Glyer Tweeted:  In none of these briefings to the press did we show pictures or video from adversary laptops. We did show the video that we published to YouTube.Fourth, I privately contacted former Mandiant personnel with whom I worked during the time of the APT1 report creation and distribution. Their reaction to Mr Sanger's allegations ranged from "I've never heard of that" to "completely false." I asked former Mandiant colleagues, like myself, In none of these briefings to the press did we show pictures or video from adversary laptops. We did show the video that we published to YouTube.Fourth, I privately contacted former Mandiant personnel with whom I worked during the time of the APT1 report creation and distribution. Their reaction to Mr Sanger's allegations ranged from "I've never heard of that" to "completely false." I asked former Mandiant colleagues, like myself, |
Hack | APT 1 | ||
| 2018-05-15 14:40:48 | Bejtlich Joining Splunk (lien direct) | Guideline | ||||
| 2018-05-07 14:26:52 | Trying Splunk Cloud (lien direct) |  I first used Splunk over ten years ago, but the first time I blogged about it was in 2008. I described how to install Splunk on Ubuntu 8.04. Today I decided to try the Splunk Cloud.Splunk Cloud is the company's hosted Splunk offering, residing in Amazon Web Services (AWS). You can register for a 15 day free trial of Splunk Cloud that will index 5 GB per day.If you would like to follow along, you will need a computer with a Web browser to interact with Splunk Cloud. (There may be ways to interact via API, but I do not cover that here.)I will collect logs from a virtual machine running Debian 9, inside Oracle VirtualBox.First I registered for the free Splunk Cloud trial online.After I had a Splunk Cloud instance running, I consulted the documentation for Forward data to Splunk Cloud from Linux. I am running a "self-serviced" instance and not a "managed instance," i.e., I am the administrator in this situation.I learned that I needed to install a software package called the Splunk Universal Forwarder on my Linux VM.I downloaded a 64 bit Linux 2.6+ kernel .deb file to the /home/Downloads directory on the Linux VM.richard@debian:~$ cd Downloads/richard@debian:~/Downloads$ lssplunkforwarder-7.1.0-2e75b3406c5b-linux-2.6-amd64.debWith elevation permissions I created a directory for the .deb, changed into the directory, and installed the .deb using dpkg.richard@debian:~/Downloads$ sudo bash[sudo] password for richard: root@debian:/home/richard/Downloads# mkdir /opt/splunkforwarderroot@debian:/home/richard/Downloads# mv splunkforwarder-7.1.0-2e75b3406c5b-linux-2.6-amd64.deb /opt/splunkforwarder/root@debian:/home/richard/Downloads# cd /opt/splunkforwarder/root@debian:/opt/splunkforwarder# ls I first used Splunk over ten years ago, but the first time I blogged about it was in 2008. I described how to install Splunk on Ubuntu 8.04. Today I decided to try the Splunk Cloud.Splunk Cloud is the company's hosted Splunk offering, residing in Amazon Web Services (AWS). You can register for a 15 day free trial of Splunk Cloud that will index 5 GB per day.If you would like to follow along, you will need a computer with a Web browser to interact with Splunk Cloud. (There may be ways to interact via API, but I do not cover that here.)I will collect logs from a virtual machine running Debian 9, inside Oracle VirtualBox.First I registered for the free Splunk Cloud trial online.After I had a Splunk Cloud instance running, I consulted the documentation for Forward data to Splunk Cloud from Linux. I am running a "self-serviced" instance and not a "managed instance," i.e., I am the administrator in this situation.I learned that I needed to install a software package called the Splunk Universal Forwarder on my Linux VM.I downloaded a 64 bit Linux 2.6+ kernel .deb file to the /home/Downloads directory on the Linux VM.richard@debian:~$ cd Downloads/richard@debian:~/Downloads$ lssplunkforwarder-7.1.0-2e75b3406c5b-linux-2.6-amd64.debWith elevation permissions I created a directory for the .deb, changed into the directory, and installed the .deb using dpkg.richard@debian:~/Downloads$ sudo bash[sudo] password for richard: root@debian:/home/richard/Downloads# mkdir /opt/splunkforwarderroot@debian:/home/richard/Downloads# mv splunkforwarder-7.1.0-2e75b3406c5b-linux-2.6-amd64.deb /opt/splunkforwarder/root@debian:/home/richard/Downloads# cd /opt/splunkforwarder/root@debian:/opt/splunkforwarder# ls |
||||
| 2018-02-26 12:02:04 | Importing Pcap into Security Onion (lien direct) |  Within the last week, Doug Burks of Security Onion (SO) added a new script that revolutionizes the use case for his amazing open source network security monitoring platform.I have always used SO in a live production mode, meaning I deploy a SO sensor sniffing a live network interface. As the multitude of SO components observe network traffic, they generate, store, and display various forms of NSM data for use by analysts.The problem with this model is that it could not be used for processing stored network traffic. If one simply replayed the traffic from a .pcap file, the new traffic would be assigned contemporary timestamps by the various tools observing the traffic.While all of the NSM tools in SO have the independent capability to read stored .pcap files, there was no unified way to integrate their output into the SO platform.Therefore, for years, there has not been a way to import .pcap files into SO -- until last week!Here is how I tested the new so-import-pcap script. First, I made sure I was running Security Onion Elastic Stack Release Candidate 2 (14.04.5.8 ISO) or later. Next I downloaded the script using wget from https://github.com/Security-Onion-Solutions/securityonion-elastic/blob/master/usr/sbin/so-import-pcap.I continued as follows:richard@so1:~$ sudo cp so-import-pcap /usr/sbin/richard@so1:~$ sudo chmod 755 /usr/sbin/so-import-pcapI tried running the script against two of the sample files packaged with SO, but ran into issues with both.richard@so1:~$ sudo so-import-pcap /opt/samples/10k.pcapso-import-pcapPlease wait while......creating temp pcap for processing.mergecap: Error reading /opt/samples/10k.pcap: The file appears to be damaged or corrupt(pcap: File has 263718464-byte packet, bigger than maximum of 262144)Error while merging!I checked the file with capinfos.richard@so1:~$ capinfos /opt/samples/10k.pcapcapinfos: An error occurred after reading 17046 packets from "/opt/samples/10k.pcap": The file appears to be damaged or corrupt.(pcap: File has 263718464-byte packet, bigger than maximum of 262144) Within the last week, Doug Burks of Security Onion (SO) added a new script that revolutionizes the use case for his amazing open source network security monitoring platform.I have always used SO in a live production mode, meaning I deploy a SO sensor sniffing a live network interface. As the multitude of SO components observe network traffic, they generate, store, and display various forms of NSM data for use by analysts.The problem with this model is that it could not be used for processing stored network traffic. If one simply replayed the traffic from a .pcap file, the new traffic would be assigned contemporary timestamps by the various tools observing the traffic.While all of the NSM tools in SO have the independent capability to read stored .pcap files, there was no unified way to integrate their output into the SO platform.Therefore, for years, there has not been a way to import .pcap files into SO -- until last week!Here is how I tested the new so-import-pcap script. First, I made sure I was running Security Onion Elastic Stack Release Candidate 2 (14.04.5.8 ISO) or later. Next I downloaded the script using wget from https://github.com/Security-Onion-Solutions/securityonion-elastic/blob/master/usr/sbin/so-import-pcap.I continued as follows:richard@so1:~$ sudo cp so-import-pcap /usr/sbin/richard@so1:~$ sudo chmod 755 /usr/sbin/so-import-pcapI tried running the script against two of the sample files packaged with SO, but ran into issues with both.richard@so1:~$ sudo so-import-pcap /opt/samples/10k.pcapso-import-pcapPlease wait while......creating temp pcap for processing.mergecap: Error reading /opt/samples/10k.pcap: The file appears to be damaged or corrupt(pcap: File has 263718464-byte packet, bigger than maximum of 262144)Error while merging!I checked the file with capinfos.richard@so1:~$ capinfos /opt/samples/10k.pcapcapinfos: An error occurred after reading 17046 packets from "/opt/samples/10k.pcap": The file appears to be damaged or corrupt.(pcap: File has 263718464-byte packet, bigger than maximum of 262144) |
||||
| 2018-01-22 09:30:58 | Lies and More Lies (lien direct) |  Following the release of the Spectre and Meltdown CPU attacks, the security community wondered if other researchers would find related speculative attack problems. When the following appeared, we were concerned:"Skyfall and SolaceMore vulnerabilities in modern computers.Following the recent release of the Meltdown and Spectre vulnerabilities, CVE-2017-5175, CVE-2017-5753 and CVE-2017-5754, there has been considerable speculation as to whether all the issues described can be fully mitigated. Skyfall and Solace are two speculative attacks based on the work highlighted by Meltdown and Spectre.Full details are still under embargo and will be published soon when chip manufacturers and Operating System vendors have prepared patches.Watch this space..."It turns out this was a hoax. The latest version of the site says, in part:"With little more than a couple of quickly registered domain names, thousands of people were hooked...SkyfallThe idea here was to suggest a link to Intel's Skylake processor.SolaceThe idea here was to suggest a link to the Solaris operating system.Copy the styling of the original Meltdown and Spectre sites and add a couple of favicons based loosely on the Intel and Solaris logos and I was nearly done.The final step was to add on https, because if a site's got an SSL certificate it must be legitimate, and the bait was set."The problem with this "explanation" is that it wasn't just a logo, domain name and SSL certificate. The "security professional" who created this site outright lied, as shown at the top of this post. Don't fall for his false narrative.I'm not naming names or linking to the sites here, because the person responsible already thinks he's too clever.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Following the release of the Spectre and Meltdown CPU attacks, the security community wondered if other researchers would find related speculative attack problems. When the following appeared, we were concerned:"Skyfall and SolaceMore vulnerabilities in modern computers.Following the recent release of the Meltdown and Spectre vulnerabilities, CVE-2017-5175, CVE-2017-5753 and CVE-2017-5754, there has been considerable speculation as to whether all the issues described can be fully mitigated. Skyfall and Solace are two speculative attacks based on the work highlighted by Meltdown and Spectre.Full details are still under embargo and will be published soon when chip manufacturers and Operating System vendors have prepared patches.Watch this space..."It turns out this was a hoax. The latest version of the site says, in part:"With little more than a couple of quickly registered domain names, thousands of people were hooked...SkyfallThe idea here was to suggest a link to Intel's Skylake processor.SolaceThe idea here was to suggest a link to the Solaris operating system.Copy the styling of the original Meltdown and Spectre sites and add a couple of favicons based loosely on the Intel and Solaris logos and I was nearly done.The final step was to add on https, because if a site's got an SSL certificate it must be legitimate, and the bait was set."The problem with this "explanation" is that it wasn't just a logo, domain name and SSL certificate. The "security professional" who created this site outright lied, as shown at the top of this post. Don't fall for his false narrative.I'm not naming names or linking to the sites here, because the person responsible already thinks he's too clever.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2018-01-16 12:31:57 | Addressing Innumeracy in Reporting (lien direct) |  Anyone involved in cybersecurity reporting needs a strong sense of numeracy, or mathematical literacy. I see two sorts of examples of innumeracy repeatedly in the media.The first involves the time value of money. Recently CNN claimed Amazon CEO Jeff Bezos was the "richest person in history" and Recode said Bezos was "now worth more than Bill Gates ever was." Thankfully both Richard Steinnon and Noah Kirsch recognized the foolishness of these reports, correctly noting that Bezos would only rank number 17 on a list where wealth was adjusted for inflation.This failure to recognize the time value of money is pervasive. Just today I heard the host of a podcast claim that the 1998 Jackie Chan movie Rush Hour was "the top grossing martial arts film of all time." According to Box Office Mojo, Rush Hour earned $244,386,864 worldwide. Adjusting for inflation, in 2017 dollars that's $367,509,865.67 -- impressive!For comparison, I researched the box office returns for Bruce Lee's Enter the Dragon. Box Office Mojo lacked data, but I found a 2017 article stating his 1973 movie earned "$25 million in the U.S. and $90 million worldwide, excluding Hong Kong." If I adjust the worldwide figure of $90 million for inflation, in 2017 dollars that's $496,864,864.86 -- making Enter the Dragon easily more successful than Rush Hour.If you're wondering about Crouching Tiger, Hidden Dragon, that 2000 movie earned $213,525,736 worldwide. That movie earned less than Rush Hour, and arrived two years later, so it's not worth doing the inflation math.The take-away is that any time you are comparing dollars from different time periods, you must adjust for inflation to have your comparisons have any meaning whatsoever. Anyone involved in cybersecurity reporting needs a strong sense of numeracy, or mathematical literacy. I see two sorts of examples of innumeracy repeatedly in the media.The first involves the time value of money. Recently CNN claimed Amazon CEO Jeff Bezos was the "richest person in history" and Recode said Bezos was "now worth more than Bill Gates ever was." Thankfully both Richard Steinnon and Noah Kirsch recognized the foolishness of these reports, correctly noting that Bezos would only rank number 17 on a list where wealth was adjusted for inflation.This failure to recognize the time value of money is pervasive. Just today I heard the host of a podcast claim that the 1998 Jackie Chan movie Rush Hour was "the top grossing martial arts film of all time." According to Box Office Mojo, Rush Hour earned $244,386,864 worldwide. Adjusting for inflation, in 2017 dollars that's $367,509,865.67 -- impressive!For comparison, I researched the box office returns for Bruce Lee's Enter the Dragon. Box Office Mojo lacked data, but I found a 2017 article stating his 1973 movie earned "$25 million in the U.S. and $90 million worldwide, excluding Hong Kong." If I adjust the worldwide figure of $90 million for inflation, in 2017 dollars that's $496,864,864.86 -- making Enter the Dragon easily more successful than Rush Hour.If you're wondering about Crouching Tiger, Hidden Dragon, that 2000 movie earned $213,525,736 worldwide. That movie earned less than Rush Hour, and arrived two years later, so it's not worth doing the inflation math.The take-away is that any time you are comparing dollars from different time periods, you must adjust for inflation to have your comparisons have any meaning whatsoever. Chart by @CanadianFlagsThe second sort of innumeracy I'd like to highlight today also involves money, but in a slightly different way. This involves changes in values over time.For example, a company may grow revenue from 2015 to 2016, with 2015 revenue being $100,000 and 2016 being $200,000. That's a 100% gain.If the company grows another $100,000 from 2016 to 2017, from $200,000 to $300,000, the growth rate has declined to 50%. To have maintained a 100% growth rate, the comp Chart by @CanadianFlagsThe second sort of innumeracy I'd like to highlight today also involves money, but in a slightly different way. This involves changes in values over time.For example, a company may grow revenue from 2015 to 2016, with 2015 revenue being $100,000 and 2016 being $200,000. That's a 100% gain.If the company grows another $100,000 from 2016 to 2017, from $200,000 to $300,000, the growth rate has declined to 50%. To have maintained a 100% growth rate, the comp |
Guideline | |||
| 2018-01-14 14:08:40 | Remembering When APT Became Public (lien direct) |  Last week I Tweeted the following on the 8th anniversary of Google's blog post about its compromise by Chinese threat actors:This intrusion made the term APT mainstream. I was the first to associate it with Aurora, in this post https://taosecurity.blogspot.com/2010/01/google-v-china.htmlMy first APT post was a careful reference in 2007, when we all feared being accused of "leaking classified" re China: https://taosecurity.blogspot.com/2007/10/air-force-cyberspace-report.htmlI should have added the term "publicly" to my original Tweet. There were consultants with years of APT experience involved in the Google incident response, and they recognized the work of APT17 at that company and others. Those consultants honored their NDAs and have stayed quiet.I wrote my original Tweet as a reminder that "APT" was not a popular, recognized term until the Google announcement on 12 January 2010. In my Google v China blog post I wrote:Welcome to the party, Google. You can use the term "advanced persistent threat" (APT) if you want to give this adversary its proper name.I also Tweeted a similar statement on the same day:This is horrifying: http://bit.ly/7x7vVW Google admits intellectual property theft from China; it's called Advanced Persistent Threat, GOOGI made the explicit link of China and APT because no one had done that publicly.This slide from a 2011 briefing I did in Hawaii captures a few historical points: Last week I Tweeted the following on the 8th anniversary of Google's blog post about its compromise by Chinese threat actors:This intrusion made the term APT mainstream. I was the first to associate it with Aurora, in this post https://taosecurity.blogspot.com/2010/01/google-v-china.htmlMy first APT post was a careful reference in 2007, when we all feared being accused of "leaking classified" re China: https://taosecurity.blogspot.com/2007/10/air-force-cyberspace-report.htmlI should have added the term "publicly" to my original Tweet. There were consultants with years of APT experience involved in the Google incident response, and they recognized the work of APT17 at that company and others. Those consultants honored their NDAs and have stayed quiet.I wrote my original Tweet as a reminder that "APT" was not a popular, recognized term until the Google announcement on 12 January 2010. In my Google v China blog post I wrote:Welcome to the party, Google. You can use the term "advanced persistent threat" (APT) if you want to give this adversary its proper name.I also Tweeted a similar statement on the same day:This is horrifying: http://bit.ly/7x7vVW Google admits intellectual property theft from China; it's called Advanced Persistent Threat, GOOGI made the explicit link of China and APT because no one had done that publicly.This slide from a 2011 briefing I did in Hawaii captures a few historical points: The Google incident was a watershed, for reasons I blogged on 16 January 2010. I remember the SANS DFIR 2008 event as effectively "APTCon," but beyond Mandiant, Northrup Grumman, and NetWitness, no one was really talking publicly about the APT until after Google.As I noted in the July 2009 blog post, You Down With APT? (ugh):Aside from Northrup Grumman, Mandiant, and a few vendors (like NetWitness, one of the full capture vendors out there) mentioning APT, there's not much else available. A Google search for "advanced persistent threat" -netwitness -mandiant -Northrop yields 34 results (prior to this blog post). (emphasis added)Today that search yields 244,000 results.I would argue we're "past APT." APT was the buzzword for The Google incident was a watershed, for reasons I blogged on 16 January 2010. I remember the SANS DFIR 2008 event as effectively "APTCon," but beyond Mandiant, Northrup Grumman, and NetWitness, no one was really talking publicly about the APT until after Google.As I noted in the July 2009 blog post, You Down With APT? (ugh):Aside from Northrup Grumman, Mandiant, and a few vendors (like NetWitness, one of the full capture vendors out there) mentioning APT, there's not much else available. A Google search for "advanced persistent threat" -netwitness -mandiant -Northrop yields 34 results (prior to this blog post). (emphasis added)Today that search yields 244,000 results.I would argue we're "past APT." APT was the buzzword for |
APT 17 APT 1 | |||
| 2018-01-08 14:49:05 | Happy 15th Birthday TaoSecurity Blog (lien direct) |  Today, 8 January 2018, is the 15th birthday of TaoSecurity Blog! This is also my 3,020th blog post.I wrote my first post on 8 January 2003 while working as an incident response consultant for Foundstone.I don't believe I've released statistics for the blog before, so here are a few. Blogger started providing statistics in May 2010, so these apply to roughly the past 8 years only!As of today, since May 2010 the blog has nearly 7.7 million all time page views.Here are the most popular posts as of today: Today, 8 January 2018, is the 15th birthday of TaoSecurity Blog! This is also my 3,020th blog post.I wrote my first post on 8 January 2003 while working as an incident response consultant for Foundstone.I don't believe I've released statistics for the blog before, so here are a few. Blogger started providing statistics in May 2010, so these apply to roughly the past 8 years only!As of today, since May 2010 the blog has nearly 7.7 million all time page views.Here are the most popular posts as of today: Twitter continues to play a role in the way I communicate. When I last reported on a blog birthday two years ago, I said that I had nearly 36,000 Twitter followers for @taosecurity, with roughly 16,000 Tweets. Today I have nearly 49,000 followers with less than 18,000 Tweets. As with most people on social media, blogging has taken a back seat to more instant forms of communication.These days I am active on Instagram as @taosecurity as well. That account is a departure from my social media practice. On Twitter I have separate accounts for cybersecurity and intelligence (@taosecurity), martial arts (@rejoiningthetao), and other purposes. My Instagram @taosecurity account is a unified account, meaning I talk about whatever I feel like. During the last two years I also started another blog to which I regularly contribute -- Rejoining the Tao. I write about my martial arts journey there, usually once a week.Once in a while I post to LinkedIn, but it's usually news of a blog post like this, or other LinkedIn content of interest.What's ahead? You may remember I was working on a PhD and I had left FireEye. I decided to abandon my PhD in the fall of 2016. I realized I was not an academic, although I had written four books.I have also changed all the goals I named in my post-FireEye announcement.For the last year I have been doing limited security consulting, but that has been increasing in recent months. I continue to be involved in martial arts, but I no longer plan to be a Krav Maga instructor nor to open my own school.For several months I've been working with a co-author and subject matter expert on a new book with martial arts applicability. I've been responsible for editing and publishing. I'll say more about that at Rejoining the Tao when the time is right.Thank you to everyone who Twitter continues to play a role in the way I communicate. When I last reported on a blog birthday two years ago, I said that I had nearly 36,000 Twitter followers for @taosecurity, with roughly 16,000 Tweets. Today I have nearly 49,000 followers with less than 18,000 Tweets. As with most people on social media, blogging has taken a back seat to more instant forms of communication.These days I am active on Instagram as @taosecurity as well. That account is a departure from my social media practice. On Twitter I have separate accounts for cybersecurity and intelligence (@taosecurity), martial arts (@rejoiningthetao), and other purposes. My Instagram @taosecurity account is a unified account, meaning I talk about whatever I feel like. During the last two years I also started another blog to which I regularly contribute -- Rejoining the Tao. I write about my martial arts journey there, usually once a week.Once in a while I post to LinkedIn, but it's usually news of a blog post like this, or other LinkedIn content of interest.What's ahead? You may remember I was working on a PhD and I had left FireEye. I decided to abandon my PhD in the fall of 2016. I realized I was not an academic, although I had written four books.I have also changed all the goals I named in my post-FireEye announcement.For the last year I have been doing limited security consulting, but that has been increasing in recent months. I continue to be involved in martial arts, but I no longer plan to be a Krav Maga instructor nor to open my own school.For several months I've been working with a co-author and subject matter expert on a new book with martial arts applicability. I've been responsible for editing and publishing. I'll say more about that at Rejoining the Tao when the time is right.Thank you to everyone who |
||||
| 2018-01-08 14:47:20 | Happy 13th Birthday TaoSecurity Blog (lien direct) | |||||
| 2018-01-05 10:18:35 | Spectre and Meltdown from a CNO Perspective (lien direct) |  Longtime readers know that I have no problem with foreign countries replacing American vendors with local alternatives. For example, see Five Reasons I Want China Running Its Own Software. This is not a universal principle, but as an American I am fine with it. Putting my computer network operations (CNO) hat on, I want to share a few thoughts about the intersection of the anti-American vendor mindset with the recent Spectre and Meltdown attacks.There are probably non-Americans, who, for a variety of reasons, feel that it would be "safer" for them to run their cloud computing workloads on non-American infrastructure. Perhaps they feel that it puts their data beyond the reach of the American Department of Justice. (I personally feel that it's an over-reach by DoJ to try to access data beyond American borders, eg Microsoft Corp. v. United States.)The American intelligence community and computer network operators, however, might prefer to have that data outside American borders. These agencies are still bound by American laws, but those laws generally permit exploitation overseas.Now put this situation in the context of Spectre and Meltdown. Begin with the attack scenario mentioned by Nicole Perlroth, where an attacker rents a few minutes of time on various cloud systems, then leverages Spectre and/or Meltdown to try to gather sensitive data from other virtual machines on the same physical hardware.No lawyer or judge would allow this sort of attack scenario if it were performed in American systems. It would be very difficult, I think, to minimize data in this kind of "fishing expedition." Most of the data returned would belong to US persons and would be subject to protection. Sure, there are conspiracy theorists out there who will never trust that the US government follows its own laws. These people are sure that the USG already knew about Spectre and Meltdown and ravaged every American cloud system already, after doing the same with the "Intel Management Engine backdoors."In reality, US law will prevent computer network operators from running these sorts of missions on US cloud infrastructure. Overseas, it's a different story. Non US-persons do not enjoy the same sorts of privacy protections as US persons. Therefore, the more "domestic" (non-American) the foreign target, the better. For example, if the IC identified a purely Russian cloud provider, it would not be difficult for the USG to authorize a Spectre-Meltdown collection operation against that target.I have no idea if this is happening, but this was one of my first thoughts when I first heard about this new attack vector.Bonus: it's popular to criticize academics who research cybersecurity. They don't seem to find much that is interesting or relevant. However, academics played a big role in discovering Spectre and Meltdown. Wow!Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Longtime readers know that I have no problem with foreign countries replacing American vendors with local alternatives. For example, see Five Reasons I Want China Running Its Own Software. This is not a universal principle, but as an American I am fine with it. Putting my computer network operations (CNO) hat on, I want to share a few thoughts about the intersection of the anti-American vendor mindset with the recent Spectre and Meltdown attacks.There are probably non-Americans, who, for a variety of reasons, feel that it would be "safer" for them to run their cloud computing workloads on non-American infrastructure. Perhaps they feel that it puts their data beyond the reach of the American Department of Justice. (I personally feel that it's an over-reach by DoJ to try to access data beyond American borders, eg Microsoft Corp. v. United States.)The American intelligence community and computer network operators, however, might prefer to have that data outside American borders. These agencies are still bound by American laws, but those laws generally permit exploitation overseas.Now put this situation in the context of Spectre and Meltdown. Begin with the attack scenario mentioned by Nicole Perlroth, where an attacker rents a few minutes of time on various cloud systems, then leverages Spectre and/or Meltdown to try to gather sensitive data from other virtual machines on the same physical hardware.No lawyer or judge would allow this sort of attack scenario if it were performed in American systems. It would be very difficult, I think, to minimize data in this kind of "fishing expedition." Most of the data returned would belong to US persons and would be subject to protection. Sure, there are conspiracy theorists out there who will never trust that the US government follows its own laws. These people are sure that the USG already knew about Spectre and Meltdown and ravaged every American cloud system already, after doing the same with the "Intel Management Engine backdoors."In reality, US law will prevent computer network operators from running these sorts of missions on US cloud infrastructure. Overseas, it's a different story. Non US-persons do not enjoy the same sorts of privacy protections as US persons. Therefore, the more "domestic" (non-American) the foreign target, the better. For example, if the IC identified a purely Russian cloud provider, it would not be difficult for the USG to authorize a Spectre-Meltdown collection operation against that target.I have no idea if this is happening, but this was one of my first thoughts when I first heard about this new attack vector.Bonus: it's popular to criticize academics who research cybersecurity. They don't seem to find much that is interesting or relevant. However, academics played a big role in discovering Spectre and Meltdown. Wow!Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2017-12-04 11:30:48 | On "Advanced" Network Security Monitoring (lien direct) | |||||
| 2017-10-21 15:43:50 | How to Minimize Leaking (lien direct) |  I am hopeful that President Trump will not block release of the remaining classified documents addressing the 1963 assassination of President John F. Kennedy. I grew up a Roman Catholic in Massachusetts, so President Kennedy always fascinated me.The 1991 Oliver Stone movie JFK fueled several years of hobbyist research into the assassination. (It's unfortunate the movie was so loaded with fictional content!) On the 30th anniversary of JFK's death in 1993, I led a moment of silence from the balcony of the Air Force Academy chow hall during noon meal. While stationed at Goodfellow AFB in Texas, Mrs B and I visited Dealey Plaza in Dallas and the Sixth Floor Museum.Many years later, thanks to a 1992 law partially inspired by the Stone movie, the government has a chance to release the last classified assassination records. As a historian and former member of the intelligence community, I hope all of the documents become public. This would be a small but significant step towards minimizing the culture of information leaking in Washington, DC. If prospective leakers were part of a system that was known for releasing classified information prudently, regularly, and efficiently, it would decrease the leakers' motivation to evade the formal declassification process.Many smart people have recommended improvements to the classification system. Check out this 2012 report for details.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) I am hopeful that President Trump will not block release of the remaining classified documents addressing the 1963 assassination of President John F. Kennedy. I grew up a Roman Catholic in Massachusetts, so President Kennedy always fascinated me.The 1991 Oliver Stone movie JFK fueled several years of hobbyist research into the assassination. (It's unfortunate the movie was so loaded with fictional content!) On the 30th anniversary of JFK's death in 1993, I led a moment of silence from the balcony of the Air Force Academy chow hall during noon meal. While stationed at Goodfellow AFB in Texas, Mrs B and I visited Dealey Plaza in Dallas and the Sixth Floor Museum.Many years later, thanks to a 1992 law partially inspired by the Stone movie, the government has a chance to release the last classified assassination records. As a historian and former member of the intelligence community, I hope all of the documents become public. This would be a small but significant step towards minimizing the culture of information leaking in Washington, DC. If prospective leakers were part of a system that was known for releasing classified information prudently, regularly, and efficiently, it would decrease the leakers' motivation to evade the formal declassification process.Many smart people have recommended improvements to the classification system. Check out this 2012 report for details.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2017-05-08 11:20:15 | Latest Book Inducted into Cybersecurity Canon (lien direct) | |||||
| 2017-03-23 10:26:11 | Five Reasons I Want China Running Its Own Software (lien direct) |  Periodically I read about efforts by China, or Russia, or North Korea, or other countries to replace American software with indigenous or semi-indigenous alternatives. I then reply via Twitter that I love the idea, with a short reason why. This post will list the top five reasons why I want China and other likely targets of American foreign intelligence collection to run their own software.1. Many (most?) non-US software companies write lousy code. The US is by no means perfect, but our developers and processes generally appear to be superior to foreign indigenous efforts. Cisco vs Huawei is a good example. Cisco has plenty of problems, but it has processes in place to manage them, plus secure code development practices. Lousy indigenous code means it is easier for American intelligence agencies to penetrate foreign targets. (An example of a foreign country that excels in writing code is Israel, but thankfully it is not the same sort of priority target like China, Russia, or North Korea.)2. Many (most?) non-US enterprises are 5-10 years behind US security practices. Even if a foreign target runs decent native code, the IT processes maintaining that code are lagging compared to American counterparts. Again, the US has not solved this problem by any stretch of the imagination. However, relatively speaking, American inventory management, patch management, and security operations have the edge over foreign intelligence targets. Because non-US enterprises running indigenous code will not necessarily be able to benefit from American expertise (as they might if they were running American code), these deficiencies will make them easier targets for foreign exploitation.3. Foreign targets running foreign code is win-win for American intel and enterprises. The current vulnerability equities process (VEP) puts American intelligence agencies in a quandary. The IC develops a zero-day exploit for a vulnerability, say for use against Cisco routers. American and Chinese organizations use Cisco routers. Should the IC sit on the vulnerability in order to maintain access to foreign targets, or should it release the vulnerability to Cisco to enable patching and thereby protect American and foreign systems?This dilemma disappears in a world where foreign targets run indigenous software. If the IC identifies a vulnerability in Cisco software, and the majority of its targets run non-Cisco software, then the IC is more likely (or should be pushed to be more likely) to assist with patching the vulnerable software. Meanwhile, the IC continues to exploit Huawei or other products at its leisure.4. Writing and running indigenous code is the fastest way to improve. When foreign countries essentially outsource their IT to vendors, they become program managers. They lose or never develop any ability to write and run quality software. Writing and running your own code will enroll foreign organizations in the security school of hard knocks. American intel will have a field day for 3-5 years against these targets, as they flail around in a perpetual state of compromise. However, if they devote the proper native resources and attention, they will learn from their mistakes. They will write and run better software. Now, this means they will become harder targets for American intel, but American intel will retain the advantage of point 3.5. Trustworthy indigenous code will promote international stability. Countries like China feel especially vulnerable to American exploitation. They have eve Periodically I read about efforts by China, or Russia, or North Korea, or other countries to replace American software with indigenous or semi-indigenous alternatives. I then reply via Twitter that I love the idea, with a short reason why. This post will list the top five reasons why I want China and other likely targets of American foreign intelligence collection to run their own software.1. Many (most?) non-US software companies write lousy code. The US is by no means perfect, but our developers and processes generally appear to be superior to foreign indigenous efforts. Cisco vs Huawei is a good example. Cisco has plenty of problems, but it has processes in place to manage them, plus secure code development practices. Lousy indigenous code means it is easier for American intelligence agencies to penetrate foreign targets. (An example of a foreign country that excels in writing code is Israel, but thankfully it is not the same sort of priority target like China, Russia, or North Korea.)2. Many (most?) non-US enterprises are 5-10 years behind US security practices. Even if a foreign target runs decent native code, the IT processes maintaining that code are lagging compared to American counterparts. Again, the US has not solved this problem by any stretch of the imagination. However, relatively speaking, American inventory management, patch management, and security operations have the edge over foreign intelligence targets. Because non-US enterprises running indigenous code will not necessarily be able to benefit from American expertise (as they might if they were running American code), these deficiencies will make them easier targets for foreign exploitation.3. Foreign targets running foreign code is win-win for American intel and enterprises. The current vulnerability equities process (VEP) puts American intelligence agencies in a quandary. The IC develops a zero-day exploit for a vulnerability, say for use against Cisco routers. American and Chinese organizations use Cisco routers. Should the IC sit on the vulnerability in order to maintain access to foreign targets, or should it release the vulnerability to Cisco to enable patching and thereby protect American and foreign systems?This dilemma disappears in a world where foreign targets run indigenous software. If the IC identifies a vulnerability in Cisco software, and the majority of its targets run non-Cisco software, then the IC is more likely (or should be pushed to be more likely) to assist with patching the vulnerable software. Meanwhile, the IC continues to exploit Huawei or other products at its leisure.4. Writing and running indigenous code is the fastest way to improve. When foreign countries essentially outsource their IT to vendors, they become program managers. They lose or never develop any ability to write and run quality software. Writing and running your own code will enroll foreign organizations in the security school of hard knocks. American intel will have a field day for 3-5 years against these targets, as they flail around in a perpetual state of compromise. However, if they devote the proper native resources and attention, they will learn from their mistakes. They will write and run better software. Now, this means they will become harder targets for American intel, but American intel will retain the advantage of point 3.5. Trustworthy indigenous code will promote international stability. Countries like China feel especially vulnerable to American exploitation. They have eve |
Guideline | |||
| 2017-03-23 08:43:25 | The Missing Trends in M-Trends 2017 (lien direct) |  FireEye released the 2017 edition of the Mandiant M-Trends report yesterday. I've been a fan of this report since the 2010 edition, before I worked at the company.Curiously for a report with the name "trends" in the title, this and all other editions do not publish the sorts of yearly trends I would expect. This post will address that limitation.The report is most famous for its "dwell time" metric, which is the median (not average, or "mean") number of days an intruder spends inside a target company until he is discovered.Each report lists the statistic for the year in consideration, and compares it to the previous year. For example, the 2017 report, covering incidents from 2016, notes the dwell time has dropped from 146 days in 2015, to 99 days in 2016.The second most interesting metric (for me) is the split between internal and external notification. Internal notification means that the target organization found the intrusion on its own. External notification means that someone else informed the target organization. The external party is often a law enforcement or intelligence agency, or a managed security services provider. The 2016 split was 53% internal vs 47% external.How do these numbers look over the years that the M-Trends report has been published? Inquiring minds want to know.The 2012 M-Trends report was the first edition to include these statistics. I have included them for that report and all subsequent editions in the table below. Year Days Internal External 2011 416 6 94 2012 243 37 63 2013 229 33 67 2014 205 31 69 2015 146 47 53 2016 99 53 47 As you can see, all of the numbers are heading in the right direction. We are finally into double digits for dwell time, but over 3 months is still far too long. Internal detection continues to rise as well. This is a proxy for the maturity FireEye released the 2017 edition of the Mandiant M-Trends report yesterday. I've been a fan of this report since the 2010 edition, before I worked at the company.Curiously for a report with the name "trends" in the title, this and all other editions do not publish the sorts of yearly trends I would expect. This post will address that limitation.The report is most famous for its "dwell time" metric, which is the median (not average, or "mean") number of days an intruder spends inside a target company until he is discovered.Each report lists the statistic for the year in consideration, and compares it to the previous year. For example, the 2017 report, covering incidents from 2016, notes the dwell time has dropped from 146 days in 2015, to 99 days in 2016.The second most interesting metric (for me) is the split between internal and external notification. Internal notification means that the target organization found the intrusion on its own. External notification means that someone else informed the target organization. The external party is often a law enforcement or intelligence agency, or a managed security services provider. The 2016 split was 53% internal vs 47% external.How do these numbers look over the years that the M-Trends report has been published? Inquiring minds want to know.The 2012 M-Trends report was the first edition to include these statistics. I have included them for that report and all subsequent editions in the table below. Year Days Internal External 2011 416 6 94 2012 243 37 63 2013 229 33 67 2014 205 31 69 2015 146 47 53 2016 99 53 47 As you can see, all of the numbers are heading in the right direction. We are finally into double digits for dwell time, but over 3 months is still far too long. Internal detection continues to rise as well. This is a proxy for the maturity |
||||
| 2017-03-21 09:17:10 | Cybersecurity Domains Mind Map (lien direct) | 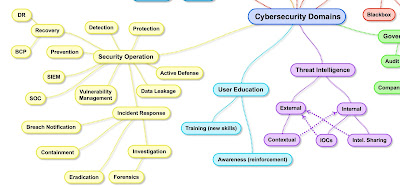 Last month I retweeted an image labelled "The Map of Cybersecurity Domains (v1.0)". I liked the way this graphic divided "security" into various specialties. At the time I did not do any research to identify the originator of the graphic.Last night before my Brazilian Jiu-Jitsu class I heard some of the guys talking about certifications. They were all interested in "cybersecurity" but did not know how to break into the field. The domain image came to mind as I mentioned that I had some experience in the field. I also remembered an article Brian Krebs asked me to write titled "How to Break Into Security, Bejtlich Edition," part of a series on that theme. I wrote:Providing advice on “getting started in digital security†is similar to providing advice on “getting started in medicine.†If you ask a neurosurgeon he or she may propose some sort of experiment with dead frog legs and batteries. If you ask a dermatologist you might get advice on protection from the sun whenever you go outside. Asking a “security person†will likewise result in many different responses, depending on the individual's background and tastes.I offered to help the guys in my BJJ class find the area of security that interests them and get started in that space. I thought the domains graphic might facilitate that conversation, so I decided to identify the originator so as to give proper credit.It turns out that that CISO at Oppenheimer & Co, Henry Jiang, created the domains graphic. Last month at LinkedIn he published an updated Map of Cybersecurity Domains v2.0: Last month I retweeted an image labelled "The Map of Cybersecurity Domains (v1.0)". I liked the way this graphic divided "security" into various specialties. At the time I did not do any research to identify the originator of the graphic.Last night before my Brazilian Jiu-Jitsu class I heard some of the guys talking about certifications. They were all interested in "cybersecurity" but did not know how to break into the field. The domain image came to mind as I mentioned that I had some experience in the field. I also remembered an article Brian Krebs asked me to write titled "How to Break Into Security, Bejtlich Edition," part of a series on that theme. I wrote:Providing advice on “getting started in digital security†is similar to providing advice on “getting started in medicine.†If you ask a neurosurgeon he or she may propose some sort of experiment with dead frog legs and batteries. If you ask a dermatologist you might get advice on protection from the sun whenever you go outside. Asking a “security person†will likewise result in many different responses, depending on the individual's background and tastes.I offered to help the guys in my BJJ class find the area of security that interests them and get started in that space. I thought the domains graphic might facilitate that conversation, so I decided to identify the originator so as to give proper credit.It turns out that that CISO at Oppenheimer & Co, Henry Jiang, created the domains graphic. Last month at LinkedIn he published an updated Map of Cybersecurity Domains v2.0: Map of Cybersecurity Domains v2.0 by Henry JiangIf I could suggest a few changes for an updated version, I would try to put related disciplines closer to each other. For example, I would put the Threat Intelligence section right next to Security Operations. I would also swap the locations of Risk Assessment and Governance. Governance is closer to the Framework and Standard arena. I would also move User Education to be near Career Development, since both deal with people.On a more substantive level, I am not comfortable with the Risk Assessment section. Blue Team and Red Team are not derivatives of a Penetration test, for example. I'm not sure how to rebuild that section.These are minor issues overall. The main reason I like this graphic is that it largely captures the vario Map of Cybersecurity Domains v2.0 by Henry JiangIf I could suggest a few changes for an updated version, I would try to put related disciplines closer to each other. For example, I would put the Threat Intelligence section right next to Security Operations. I would also swap the locations of Risk Assessment and Governance. Governance is closer to the Framework and Standard arena. I would also move User Education to be near Career Development, since both deal with people.On a more substantive level, I am not comfortable with the Risk Assessment section. Blue Team and Red Team are not derivatives of a Penetration test, for example. I'm not sure how to rebuild that section.These are minor issues overall. The main reason I like this graphic is that it largely captures the vario |
||||
| 2017-03-17 08:00:00 | Bejtlich Moves On (lien direct) |  Exactly six years ago today I announced that I was joining Mandiant to become the company's first CSO. Today is my last day at FireEye, the company that bought Mandiant at the very end of 2013.The highlights of my time at Mandiant involved two sets of responsibilities.First, as CSO, I enjoyed working with my small but superb security team, consisting of Doug Burks, Derek Coulsen, Dani Jackson, and Scott Runnels. They showed that "a small team of A+ players can run circles around a giant team of B and C players."Second, as a company spokesperson, I survived the one-of-a-kind ride that was the APT1 report. I have to credit our intel and consulting teams for the content, and our marketing and government teams for keeping me pointed in the right direction during the weeks of craziness that ensued.At FireEye I transitioned to a strategist role because I was spending so much time talking to legislators and administration officials. I enjoyed working with another small but incredibly effective team: government relations. Back by the combined FireEye-Mandiant intel team, we helped policy makers better understand the digital landscape and, more importantly, what steps to take to mitigate various risks.Where do I go from here?Twenty years ago last month I started my first role in the information warfare arena, as an Air Force intelligence officer assigned to Air Intelligence Agency at Security Hill in San Antonio, Texas. Since that time I've played a small part in the "cyber wars," trying to stop bad guys while empowering good guys.I've known for several years that my life was heading in a new direction. It took me a while, but now I understand that I am not the same person who used to post hundreds of blog entries per year, and review 50 security books per year, and write security books and articles, and speak to reporters, and testify before Congress, and train thousands of students worldwide.That mission is accomplished. I have new missions waiting.My near-term goal is to identify opportunities in the security space which fit with my current interests. These include:Promoting open source software to protect organizations of all sizesAdvising venture capitalists on promising security start-upsHelping companies to write more effective security job descriptions and to interview and select the best candidates availableMy intermediate-term goal is to continue my Krav Maga training, which I started in January 2016. My focus is the General Instructor Course pr Exactly six years ago today I announced that I was joining Mandiant to become the company's first CSO. Today is my last day at FireEye, the company that bought Mandiant at the very end of 2013.The highlights of my time at Mandiant involved two sets of responsibilities.First, as CSO, I enjoyed working with my small but superb security team, consisting of Doug Burks, Derek Coulsen, Dani Jackson, and Scott Runnels. They showed that "a small team of A+ players can run circles around a giant team of B and C players."Second, as a company spokesperson, I survived the one-of-a-kind ride that was the APT1 report. I have to credit our intel and consulting teams for the content, and our marketing and government teams for keeping me pointed in the right direction during the weeks of craziness that ensued.At FireEye I transitioned to a strategist role because I was spending so much time talking to legislators and administration officials. I enjoyed working with another small but incredibly effective team: government relations. Back by the combined FireEye-Mandiant intel team, we helped policy makers better understand the digital landscape and, more importantly, what steps to take to mitigate various risks.Where do I go from here?Twenty years ago last month I started my first role in the information warfare arena, as an Air Force intelligence officer assigned to Air Intelligence Agency at Security Hill in San Antonio, Texas. Since that time I've played a small part in the "cyber wars," trying to stop bad guys while empowering good guys.I've known for several years that my life was heading in a new direction. It took me a while, but now I understand that I am not the same person who used to post hundreds of blog entries per year, and review 50 security books per year, and write security books and articles, and speak to reporters, and testify before Congress, and train thousands of students worldwide.That mission is accomplished. I have new missions waiting.My near-term goal is to identify opportunities in the security space which fit with my current interests. These include:Promoting open source software to protect organizations of all sizesAdvising venture capitalists on promising security start-upsHelping companies to write more effective security job descriptions and to interview and select the best candidates availableMy intermediate-term goal is to continue my Krav Maga training, which I started in January 2016. My focus is the General Instructor Course pr |
APT 1 | |||
| 2017-03-14 10:33:39 | The Origin of Threat Hunting (lien direct) |  2011 Article "Become a Hunter"The term "threat hunting" has been popular with marketers from security companies for about five years. Yesterday Anton Chuvakin asked about the origin of the term.I appear to have written the first article describing threat hunting in any meaningful way. It was published in the July-August 2011 issue of Information Security Magazine and was called "Become a Hunter." I wrote it in the spring of 2011, when I was director of incident response for GE-CIRT. Relevant excerpts include:"To best counter targeted attacks, one must conduct counter-threat operations (CTOps). In other words, defenders must actively hunt intruders in their enterprise. These intruders can take the form of external threats who maintain persistence or internal threats who abuse their privileges. Rather than hoping defenses will repel invaders, or that breaches will be caught by passive alerting mechanisms, CTOps practitioners recognize that defeating intruders requires actively detecting and responding to them. CTOps experts then feed the lessons learned from finding and removing attackers into the software development lifecycle (SDL) and configuration and IT management processes to reduce the likelihood of future incidents...In addition to performing SOC work, CTOps requires more active, unstructured, and creative thoughts and approaches. One way to characterize this more vigorous approach to detecting and responding to threats is the term “hunting.†In the mid-2000s, the Air Force popularized the term “hunter-killer†for a missions whereby teams of security experts performed “friendly force projection†on their networks. They combed through data from systems and in some cases occupied the systems themselves in order to find advanced threats. The concept of “hunting†(without the slightly more aggressive term “killingâ€) is now gaining ground in the civilian world. 2011 Article "Become a Hunter"The term "threat hunting" has been popular with marketers from security companies for about five years. Yesterday Anton Chuvakin asked about the origin of the term.I appear to have written the first article describing threat hunting in any meaningful way. It was published in the July-August 2011 issue of Information Security Magazine and was called "Become a Hunter." I wrote it in the spring of 2011, when I was director of incident response for GE-CIRT. Relevant excerpts include:"To best counter targeted attacks, one must conduct counter-threat operations (CTOps). In other words, defenders must actively hunt intruders in their enterprise. These intruders can take the form of external threats who maintain persistence or internal threats who abuse their privileges. Rather than hoping defenses will repel invaders, or that breaches will be caught by passive alerting mechanisms, CTOps practitioners recognize that defeating intruders requires actively detecting and responding to them. CTOps experts then feed the lessons learned from finding and removing attackers into the software development lifecycle (SDL) and configuration and IT management processes to reduce the likelihood of future incidents...In addition to performing SOC work, CTOps requires more active, unstructured, and creative thoughts and approaches. One way to characterize this more vigorous approach to detecting and responding to threats is the term “hunting.†In the mid-2000s, the Air Force popularized the term “hunter-killer†for a missions whereby teams of security experts performed “friendly force projection†on their networks. They combed through data from systems and in some cases occupied the systems themselves in order to find advanced threats. The concept of “hunting†(without the slightly more aggressive term “killingâ€) is now gaining ground in the civilian world. 2013 Book "The Practice of NSM"If the SOC is characterized by a group that reviews alerts for signs of intruder action, the CIRT is recognized by the likelihood that senior analysts are taking junior analysts on “hunting trips.†A senior investigator who has discovered a novel or clever way to possibly detect intruders guides one or more junior analysts through data and systems looking for signs of the enemy. Upon validating the technique (and responding to any enemy actions), the hunting team should work to incorporate the new detection method in 2013 Book "The Practice of NSM"If the SOC is characterized by a group that reviews alerts for signs of intruder action, the CIRT is recognized by the likelihood that senior analysts are taking junior analysts on “hunting trips.†A senior investigator who has discovered a novel or clever way to possibly detect intruders guides one or more junior analysts through data and systems looking for signs of the enemy. Upon validating the technique (and responding to any enemy actions), the hunting team should work to incorporate the new detection method in |
||||
| 2017-02-13 18:22:47 | Does Reliable Real Time Detection Demand Prevention? (lien direct) |  Chris Sanders started a poll on Twitter asking "Would you rather get a real-time alert with partial context immediately, or a full context alert delayed by 30 mins?" I answered by saying I would prefer full context delayed by 30 minutes. I also replied with the text at left, from my first book The Tao of Network Security Monitoring (2004). It's titled "Real Time Isn't Always the Best Time."Dustin Webber then asked "if you have [indicators of compromise] IOC that merit 'real-time' notification then you should be in the business of prevention. Right?"Long ago I decided to not have extended conversations over Twitter, as well as to not try to compress complex thoughts into 140 characters -- hence this post!There is a difference, in my mind, between high-fidelity matching (using the vernacular from my newest book, The Practice of Network Security Monitoring, 50% off now with code RSAREADING) and prevention.To Dustin's point, I agree that if it is possible to generate a match (or "alert," etc.) with 100% accuracy (or possibly near 100%, depending on the severity of the problematic event), i.e., with no chance or almost no chance of a false positive, then it is certainly worth seeking a preventive action for that problematic event. To use a phrase from the last decade, "if you can detect it, why can't you prevent it?"However, there are likely cases where zero- or low-false positive events do not have corresponding preventive actions. Two come to mind.First, although you can reliably detect a problem, you may not be able to do anything about it. The security team may lack the authority, or technical capability, to implement a preventive action.Second, although you can reliably detect a problem, you may not want to do anything about it. The security team may desire to instead watch an intruder until such time that containment or incident mitigation is required.This, then, is my answer to Dustin's question!Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Chris Sanders started a poll on Twitter asking "Would you rather get a real-time alert with partial context immediately, or a full context alert delayed by 30 mins?" I answered by saying I would prefer full context delayed by 30 minutes. I also replied with the text at left, from my first book The Tao of Network Security Monitoring (2004). It's titled "Real Time Isn't Always the Best Time."Dustin Webber then asked "if you have [indicators of compromise] IOC that merit 'real-time' notification then you should be in the business of prevention. Right?"Long ago I decided to not have extended conversations over Twitter, as well as to not try to compress complex thoughts into 140 characters -- hence this post!There is a difference, in my mind, between high-fidelity matching (using the vernacular from my newest book, The Practice of Network Security Monitoring, 50% off now with code RSAREADING) and prevention.To Dustin's point, I agree that if it is possible to generate a match (or "alert," etc.) with 100% accuracy (or possibly near 100%, depending on the severity of the problematic event), i.e., with no chance or almost no chance of a false positive, then it is certainly worth seeking a preventive action for that problematic event. To use a phrase from the last decade, "if you can detect it, why can't you prevent it?"However, there are likely cases where zero- or low-false positive events do not have corresponding preventive actions. Two come to mind.First, although you can reliably detect a problem, you may not be able to do anything about it. The security team may lack the authority, or technical capability, to implement a preventive action.Second, although you can reliably detect a problem, you may not want to do anything about it. The security team may desire to instead watch an intruder until such time that containment or incident mitigation is required.This, then, is my answer to Dustin's question!Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2017-02-12 07:59:45 | Guest Post: Bamm Visscher on Detection (lien direct) |  Yesterday my friend Bamm Visscher published a series of Tweets on detection. I thought readers might like to digest it as a lightly edited blog post. Here, then, is the first ever (as far as I can remember) guest post on TaoSecurity Blog. Enjoy.When you receive new [threat] intel and apply it in your detection environment, keep in mind all three analysis opportunities: RealTime, Batch, and Hunting.If your initial intelligence analysis produces high context and quality details, it's a ripe candidate for RealTime detection.If analysts can quickly and accurately process events generated by the [RealTime] signature, it's a good sign the indicator should be part of RealTime detection. If an analyst struggles to determine if a [RealTime alert] has detected malicious activity, it's likely NOT appropriate for RealTime detection.If [the threat] intelligence contains limited context and/or details, try leveraging Batch Analysis with scheduled data reports as a better detection technique. Use Batch Analysis to develop better context (both positive and negative hits) to identify better signatures for RealTime detection.Hunting is the soft science of detection, and best done with a team of diverse skills. Intelligence, content development, and detection should all work together. Don't fear getting skunked on your hunting trips. Keep investing time. The rewards are accumulative. Be sure to pass Hunting rewards into Batch Analysis and RealTime detection operations in the form of improved context.The biggest mistake organizations make is not placing emphasis outside of RealTime detection, and "shoe-horning" [threat] intelligence into RealTime operations. So called "Atomic Indicators" tend to be the biggest violator of shoe-horning. Atomic indicators are easy to script into signature driven detection devices, but leave an analyst wondering what he is looking at and for.Do not underestimate the NEGATIVE impact of GOOD [threat] intelligence inappropriately placed into RealTime operations! Mountains of indiscernible events will lead to analyst fatigue and increase the risk of good analyst missing a real incident.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Yesterday my friend Bamm Visscher published a series of Tweets on detection. I thought readers might like to digest it as a lightly edited blog post. Here, then, is the first ever (as far as I can remember) guest post on TaoSecurity Blog. Enjoy.When you receive new [threat] intel and apply it in your detection environment, keep in mind all three analysis opportunities: RealTime, Batch, and Hunting.If your initial intelligence analysis produces high context and quality details, it's a ripe candidate for RealTime detection.If analysts can quickly and accurately process events generated by the [RealTime] signature, it's a good sign the indicator should be part of RealTime detection. If an analyst struggles to determine if a [RealTime alert] has detected malicious activity, it's likely NOT appropriate for RealTime detection.If [the threat] intelligence contains limited context and/or details, try leveraging Batch Analysis with scheduled data reports as a better detection technique. Use Batch Analysis to develop better context (both positive and negative hits) to identify better signatures for RealTime detection.Hunting is the soft science of detection, and best done with a team of diverse skills. Intelligence, content development, and detection should all work together. Don't fear getting skunked on your hunting trips. Keep investing time. The rewards are accumulative. Be sure to pass Hunting rewards into Batch Analysis and RealTime detection operations in the form of improved context.The biggest mistake organizations make is not placing emphasis outside of RealTime detection, and "shoe-horning" [threat] intelligence into RealTime operations. So called "Atomic Indicators" tend to be the biggest violator of shoe-horning. Atomic indicators are easy to script into signature driven detection devices, but leave an analyst wondering what he is looking at and for.Do not underestimate the NEGATIVE impact of GOOD [threat] intelligence inappropriately placed into RealTime operations! Mountains of indiscernible events will lead to analyst fatigue and increase the risk of good analyst missing a real incident.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
Guideline | |||
| 2017-02-09 10:36:49 | Bejtlich Books Explained (lien direct) | A reader asked me to explain the differences between two of my books. I decided to write a public response.If you visit the TaoSecurity Books page, you will see two different types of books. The first type involves books which list me as author or co-author. The second involves books to which I have contributed a chapter, section, or foreword.This post will only discuss books which list me as author or co-author. In July 2004 I published The Tao of Network Security Monitoring: Beyond Intrusion Detection. This book was the result of everything I had learned since 1997-98 regarding detecting and responding to intruders, primarily using network-centric means. It is the most complete examination of NSM philosophy available. I am particularly happy with the NSM history appendix. It cites and summarizes influential computer security papers over the four decade history of NSM to that point.The main problem with the Tao is that certain details of specific software versions are very outdated. Established software like Tcpdump, Argus, and Sguil function much the same way, and the core NSM data types remain timeless. You would not be able to use the Bro chapter with modern Bro versions, for example. Still, I recommend anyone serious about NSM read the Tao.The introduction describes the Tao using these words:Part I offers an introduction to Network Security Monitoring, an operational framework for the collection, analysis, and escalation of indications and warnings (I&W) to detect and respond to intrusions. Part I begins with an analysis of the terms and theory held by NSM practitioners. The first chapter discusses the security process and defines words like security, risk, and threat. It also makes assumptions about the intruder and his prey that set the stage for NSM operations. The second chapter addresses NSM directly, explaining why NSM is not implemented by modern NIDS' alone. The third chapter focuses on deployment considerations, such as how to access traffic using hubs, taps, SPAN ports, or inline devices. Part II begins an exploration of the NSM “product, process, people†triad. Chapter 4 is a case study called the “reference intrusion model.†This is an incident explained from the point of view of an omniscient observer. During this intrusion, the victim collected full content data in two locations. We will use those two trace files while explaining the tools discussed in Part II. Following the reference intrusion model, I devote chapters to each of the four types of data which must be collected to perform network security monitoring – full content, session, statistical, and alert data. Each chapter describes open source tools tested on the FreeBSD operating system and available on other UNIX derivatives. Part II also includes a look at tools to ma In July 2004 I published The Tao of Network Security Monitoring: Beyond Intrusion Detection. This book was the result of everything I had learned since 1997-98 regarding detecting and responding to intruders, primarily using network-centric means. It is the most complete examination of NSM philosophy available. I am particularly happy with the NSM history appendix. It cites and summarizes influential computer security papers over the four decade history of NSM to that point.The main problem with the Tao is that certain details of specific software versions are very outdated. Established software like Tcpdump, Argus, and Sguil function much the same way, and the core NSM data types remain timeless. You would not be able to use the Bro chapter with modern Bro versions, for example. Still, I recommend anyone serious about NSM read the Tao.The introduction describes the Tao using these words:Part I offers an introduction to Network Security Monitoring, an operational framework for the collection, analysis, and escalation of indications and warnings (I&W) to detect and respond to intrusions. Part I begins with an analysis of the terms and theory held by NSM practitioners. The first chapter discusses the security process and defines words like security, risk, and threat. It also makes assumptions about the intruder and his prey that set the stage for NSM operations. The second chapter addresses NSM directly, explaining why NSM is not implemented by modern NIDS' alone. The third chapter focuses on deployment considerations, such as how to access traffic using hubs, taps, SPAN ports, or inline devices. Part II begins an exploration of the NSM “product, process, people†triad. Chapter 4 is a case study called the “reference intrusion model.†This is an incident explained from the point of view of an omniscient observer. During this intrusion, the victim collected full content data in two locations. We will use those two trace files while explaining the tools discussed in Part II. Following the reference intrusion model, I devote chapters to each of the four types of data which must be collected to perform network security monitoring – full content, session, statistical, and alert data. Each chapter describes open source tools tested on the FreeBSD operating system and available on other UNIX derivatives. Part II also includes a look at tools to ma |
Guideline | |||
| 2017-02-01 09:19:15 | Meeting Cliff Stoll (lien direct) | |||||
| 2016-12-28 11:50:45 | Check Out My TeePublic Designs (lien direct) |  Over the years fans of this blog have asked if I would consider selling merchandise with the TaoSecurity logo. When I taught classes for TaoSecurity from 2005-2007 I designed T-shirts for my students and provided them as part of the registration package. This weekend I decided to exercise my creative side by uploading some designs to TeePublic.TeePublic offers clothing along with mugs, phone cases, notebooks, and other items.Two are based on the TaoSecurity logo. One includes the entire logo, along with the company motto of "The Way of Digital Security." The second is a close-up of the TaoSecurity S, which is a modified yin-yang symbol.Two other designs are inspired by network security monitoring. One is a 1989-era map of MilNet, the United States' military network. This image is found in many places on the Internet, and I used it previously in my classes. The second is a close-up of a switch and router from the TaoSecurity labs. I used this equipment to create packet captures for teaching network security monitoring. Over the years fans of this blog have asked if I would consider selling merchandise with the TaoSecurity logo. When I taught classes for TaoSecurity from 2005-2007 I designed T-shirts for my students and provided them as part of the registration package. This weekend I decided to exercise my creative side by uploading some designs to TeePublic.TeePublic offers clothing along with mugs, phone cases, notebooks, and other items.Two are based on the TaoSecurity logo. One includes the entire logo, along with the company motto of "The Way of Digital Security." The second is a close-up of the TaoSecurity S, which is a modified yin-yang symbol.Two other designs are inspired by network security monitoring. One is a 1989-era map of MilNet, the United States' military network. This image is found in many places on the Internet, and I used it previously in my classes. The second is a close-up of a switch and router from the TaoSecurity labs. I used this equipment to create packet captures for teaching network security monitoring. I hope you like these designs. I am particularly partial to the TaoSecurity Logo mug, the TaoSecurity S Logo Mug, and TaoSecurity S Logo t-shirt.Let me know what you think via comments here.Update 28 Dec 2016:Check out the MilNet mug! I hope you like these designs. I am particularly partial to the TaoSecurity Logo mug, the TaoSecurity S Logo Mug, and TaoSecurity S Logo t-shirt.Let me know what you think via comments here.Update 28 Dec 2016:Check out the MilNet mug! Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2016-10-18 11:17:49 | Five Ways That Good Guys Share More Than Bad Guys (lien direct) | It takes a lot for me to write a cybersecurity blog post these days. I spend most of my writing time working on my PhD. Articles like Nothing Brings Banks Together Like A Good Hack drive me up the wall, however, and a Tweet rant is insufficient. What fired me up, you might ask? Please read the following excerpt:[Troels] Oerting, with no small dose of grudging admiration, says his adversaries excel at something that can't be addressed with deep pockets or killer software: They're superb networkers. “The organized crime groups in cyber are sharing much better than we are at the moment,†says Oerting, a Dane with a square jaw and the watchful eyes of a cop who's investigated the underworld for 35 years. “They are sharing methodologies, knowledge, tools, practices-what works and what doesn't.â€Statements like these are regularly submitted without evidence. In response, I provide five sources of evidence why organized crime groups do not share more than defenders.1. Solution providers share. Both commercial and not-for-profit solution providers share enormous amounts of information on the security landscape. Some of it is free, and some of it is sold as products or consulting. Thousands of security companies and not-for-profit providers compete for your attention, producing white papers, Webinars, and other resources. You might argue that all of them claim to be the answer to your problem. However, this situation is infinitely better than the 1980s and early 1990s. Back then, hardly any solutions, or even security companies and organizations, existed at all.Criminal solution providers share, but they do so by selling their wares. This is true for the open world as well, but the volume of the open world is orders of magnitude greater.2. Government agencies share. My fellow Americans, has your organization you been visited by the FBI? Federal agents notified more than 3,000 U.S. companies [in 2013] that their computer systems had been hacked. The agents didn't just walk in, drop a letter, and leave. If a relationship did not exist previously, it will now be developed.Beyond third party breach notifications, agencies such as NIST, DHS, and others regularly share information with organizations. They may not share as much as we would like, but again, historical perspective reveals great progress.3. Books, articles, and social media share. The amount of readable material on security is astounding. Again, in the late 1980s and early 1990s hardly any books or articles were available. Now, thousands of resources exist, with new material from publishers like No Starch arriving monthly. Where are the books written by the underground?4. Security conferences share. You could spend every week of the year at a security conference. If you happen to miss a talk, it's likely the incomparable Iron Geek recorded it. Does the underground offer similar opportunities?5. Private groups and limited information exchange groups share. A final category of defender sharing takes place in more controlled settings. These involve well-established Information Sharing and Analysis Centers (ISACs), developing Information Sharing and Analysis Organizations (ISAOs), and private mailing lists and forums with limited membership. These could possibly be the closest analogue to the much-esteemed underground. Even if you disregard points 1-4 above, the quality of information shared in this final category a | ||||
| 2016-06-28 09:42:23 | Latest PhD Thesis Title and Abstract (lien direct) |  In January I posted Why a War Studies PhD? I recently decided to revise my title and abstract to include attention to both offensive and defensive aspects of intrusion campaigns.I thought some readers might be interested in reading about my current plans for the thesis, which I plan to finish and defend in early 2018.The following offers the title and abstract for the thesis.Network Intrusion Campaigns: Operational Art in Cyberspace Campaigns, Not Duels: The Operational Art of Cyber Intrusions*Intruders appear to have the upper hand in cyberspace, eroding users' trust in networked organizations and the data that is their lifeblood. Three assumptions prevail in the literature and mainstream discussion of digital intrusions. Distilled, these assumptions are that attacks occur at blinding speed with immediate consequences, that victims are essentially negligent, and that offensive initiative dominates defensive reaction. This thesis examines these assumptions through two research questions. First, what characterizes network intrusions at different levels of war? Second, what role does operational art play in network intrusion campaigns? By analyzing incident reports and public cases, the thesis refutes the assumptions and leverages the results to improve strategy. The thesis reveals that strategically significant attacks are generally not "speed-of-light" events, offering little chance for recovery. Digital defenders are hampered by a range of constraints that reduce their effectiveness while simultaneously confronting intruders who lack such restrictions. Offense does not necessarily overpower defense, constraints notwithstanding, so long as the defenders conduct proper counter-intrusion campaigns. The thesis structure offers an introduction to the subject, and an understanding of cybersecurity challenges and trade-offs. It reviews the nature of digital intrusions and the levels of war, analyzing the interactions at the levels of tools/tactics/technical details, operations and campaigns, and strategy and policy. The thesis continues by introducing historical operational art, applying lessons from operational art to network intrusions, and applying lessons from network intrusions to operational art. The thesis concludes by analyzing the limitations of operational art in evolving digital environments.*See the post Updated PhD Thesis Title for details on the new title.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) In January I posted Why a War Studies PhD? I recently decided to revise my title and abstract to include attention to both offensive and defensive aspects of intrusion campaigns.I thought some readers might be interested in reading about my current plans for the thesis, which I plan to finish and defend in early 2018.The following offers the title and abstract for the thesis.Network Intrusion Campaigns: Operational Art in Cyberspace Campaigns, Not Duels: The Operational Art of Cyber Intrusions*Intruders appear to have the upper hand in cyberspace, eroding users' trust in networked organizations and the data that is their lifeblood. Three assumptions prevail in the literature and mainstream discussion of digital intrusions. Distilled, these assumptions are that attacks occur at blinding speed with immediate consequences, that victims are essentially negligent, and that offensive initiative dominates defensive reaction. This thesis examines these assumptions through two research questions. First, what characterizes network intrusions at different levels of war? Second, what role does operational art play in network intrusion campaigns? By analyzing incident reports and public cases, the thesis refutes the assumptions and leverages the results to improve strategy. The thesis reveals that strategically significant attacks are generally not "speed-of-light" events, offering little chance for recovery. Digital defenders are hampered by a range of constraints that reduce their effectiveness while simultaneously confronting intruders who lack such restrictions. Offense does not necessarily overpower defense, constraints notwithstanding, so long as the defenders conduct proper counter-intrusion campaigns. The thesis structure offers an introduction to the subject, and an understanding of cybersecurity challenges and trade-offs. It reviews the nature of digital intrusions and the levels of war, analyzing the interactions at the levels of tools/tactics/technical details, operations and campaigns, and strategy and policy. The thesis continues by introducing historical operational art, applying lessons from operational art to network intrusions, and applying lessons from network intrusions to operational art. The thesis concludes by analyzing the limitations of operational art in evolving digital environments.*See the post Updated PhD Thesis Title for details on the new title.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2016-06-27 11:24:15 | Updated PhD Thesis Title (lien direct) |  Yesterday I posted Latest PhD Thesis Title and Abstract. One of my colleagues Ben Buchanan subsequently contacted me via Twitter and we exchanged a few messages. He prompted me to think about the title.Later I ruminated on the title of a recent book by my advisor, Dr. Thomas Rid. He wrote Cyber War Will Not Take Place. One of the best parts of the book is the title. In six words you get his argument as succinctly as possible. (It could be five words if you pushed "cyber" and "war" together, but the thought alone makes me cringe, in the age of cyber-everything.)I wondered if I could transform my latest attempt at a thesis title into something that captured my argument in a succinct form.I thought about the obsession of the majority of the information security community on the tool and tactics level of war. Too many technicians think about security as a single-exchange contest between an attacker and a defender, like a duel.That reminded me of a problem I have with Carl von Clausewitz's definition of war.We shall not enter into any of the abstruse definitions of war used by publicists. We shall keep to the element of the thing itself, to a duel. War is nothing but a duel on an extensive scale.- On War, Chapter 1Clausewitz continues by mentioning "the countless number of duels which make up a war," and then makes his famous statement that "War therefore is an act of violence to compel our opponent to fulfill our will." However, I've never liked the tactically-minded idea that war is a "duel."This concept, plus the goal to deliver a compact argument, inspired me to revise my thesis title and subtitle to the following:Campaigns, Not Duels: The Operational Art of Cyber IntrusionsIn the first three words I deliver my argument, and in the subtitle I provide context by including my key perspective ("operational art"), environment ("cyber," yes, a little part of me is dying, but it's a keyword), and "intrusions."When I publish the thesis as a book in 2018, I hope to use the same words in the book title.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Yesterday I posted Latest PhD Thesis Title and Abstract. One of my colleagues Ben Buchanan subsequently contacted me via Twitter and we exchanged a few messages. He prompted me to think about the title.Later I ruminated on the title of a recent book by my advisor, Dr. Thomas Rid. He wrote Cyber War Will Not Take Place. One of the best parts of the book is the title. In six words you get his argument as succinctly as possible. (It could be five words if you pushed "cyber" and "war" together, but the thought alone makes me cringe, in the age of cyber-everything.)I wondered if I could transform my latest attempt at a thesis title into something that captured my argument in a succinct form.I thought about the obsession of the majority of the information security community on the tool and tactics level of war. Too many technicians think about security as a single-exchange contest between an attacker and a defender, like a duel.That reminded me of a problem I have with Carl von Clausewitz's definition of war.We shall not enter into any of the abstruse definitions of war used by publicists. We shall keep to the element of the thing itself, to a duel. War is nothing but a duel on an extensive scale.- On War, Chapter 1Clausewitz continues by mentioning "the countless number of duels which make up a war," and then makes his famous statement that "War therefore is an act of violence to compel our opponent to fulfill our will." However, I've never liked the tactically-minded idea that war is a "duel."This concept, plus the goal to deliver a compact argument, inspired me to revise my thesis title and subtitle to the following:Campaigns, Not Duels: The Operational Art of Cyber IntrusionsIn the first three words I deliver my argument, and in the subtitle I provide context by including my key perspective ("operational art"), environment ("cyber," yes, a little part of me is dying, but it's a keyword), and "intrusions."When I publish the thesis as a book in 2018, I hope to use the same words in the book title.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
To see everything:
Our RSS (filtrered)
