What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2021-04-01 14:00:00 | The Origins of the Names TaoSecurity and the Unit Formerly Known as TAO (lien direct) |  What are the origins of the names TaoSecurity and the unit formerly known as TAO? IntroductionI've been reading Nicole Perlroth's new book This Is How They Tell Me the World Ends. Her discussion of the group formerly known as Tailored Access Operations, or TAO, reminded me of a controversy that arose in the 2000s. I had heard through back channels that some members of that group were upset that I was operating using the name TaoSeurity. In the 2000s and early 2010s I taught classes under the TaoSecurity brand, and even ran TaoSecurity as a single-person consultancy from 2005-2007. The purpose of this post is to explain why, how, and when I chose the TaoSecurity identity, and to show that it is contemporaneous with the formal naming of the TAO group. The most reliable accounts indicate TaoSecurity predates the TAO brand.TaoSecurity Began with Kung Fu and Taoism What are the origins of the names TaoSecurity and the unit formerly known as TAO? IntroductionI've been reading Nicole Perlroth's new book This Is How They Tell Me the World Ends. Her discussion of the group formerly known as Tailored Access Operations, or TAO, reminded me of a controversy that arose in the 2000s. I had heard through back channels that some members of that group were upset that I was operating using the name TaoSeurity. In the 2000s and early 2010s I taught classes under the TaoSecurity brand, and even ran TaoSecurity as a single-person consultancy from 2005-2007. The purpose of this post is to explain why, how, and when I chose the TaoSecurity identity, and to show that it is contemporaneous with the formal naming of the TAO group. The most reliable accounts indicate TaoSecurity predates the TAO brand.TaoSecurity Began with Kung Fu and Taoism With Sifu Michael Macaris, 21 June 1996In the summer of 1994, after graduating from the Air Force Academy and before beginning my graduate program at what is now called the Harvard Kennedy School, I started watching re-runs of the 1970s David Carradine Kung Fu TV series, created by Ed Spielman. I was so motivated by the philosophical message of the program that I joined a kung fu school in Massachusetts. I trained there for two years, and studied what I could about Chinese history and culture. I learned from the show and that it was based on Taoism (for example) so I bought a copy of the Tao Te Ching by Lao Tzu and devoured it. Visiting China With Sifu Michael Macaris, 21 June 1996In the summer of 1994, after graduating from the Air Force Academy and before beginning my graduate program at what is now called the Harvard Kennedy School, I started watching re-runs of the 1970s David Carradine Kung Fu TV series, created by Ed Spielman. I was so motivated by the philosophical message of the program that I joined a kung fu school in Massachusetts. I trained there for two years, and studied what I could about Chinese history and culture. I learned from the show and that it was based on Taoism (for example) so I bought a copy of the Tao Te Ching by Lao Tzu and devoured it. Visiting China Tai Chi on the Yangtze, May 1999In the spring of 1999 my wife and I took a three week trip to Chin Tai Chi on the Yangtze, May 1999In the spring of 1999 my wife and I took a three week trip to Chin |
Malware Threat | |||
| 2021-02-18 10:53:39 | Digital Offense Capabilities Are Currently Net Negative for the Security Ecosystem (lien direct) |  PropositionDigital offense capabilities are currently net negative for the security ecosystem.[0]The costs of improved digital offense currently outweigh the benefits. The legitimate benefits of digital offense accrue primarily to the security one percent (#securityonepercent), and to intelligence, military, and law enforcement agencies. The derived defensive benefits depend on the nature of the defender. The entire security ecosystem bears the costs, and in some cases even those who see tangible benefit may suffer costs exceeding those benefits.The ReasonLimitations of scaling are the reason why digital offense capabilities are currently net negative.Consider the case of an actor developing a digital offense capability, and publishing it to the general public. From the target side, limitations on scaling prevent complete mitigation or remediation of the vulnerability.The situation is much different from the offense perspective.Any actor may leverage the offense capability against any Internet-connected target on the planet. The actor can scale that capability across the entire range of vulnerable or exposed targets.The ThreeOnly three sets of actors are able to possibly leverage an offense capability for defensive purposes.First, the organization responsible for developing and maintaining the vulnerable or exposed asset can determine if there is a remedy for the new offense capability. (This is typically a "vendor," but could be a noncommercial entity. As a shorthand, I will use "vendor.") The vendor can try to develop and deploy a patch or mitigation method.Second, major consumers of the vulnerable or exposed asset can take similar steps, usually by implementing the vendor's patch or mitigation.Third, the security one percent can take some defensive measures, either by implementing the vendor's patch or mitigation, or by developing and acting upon detection and response processes.The combination of the actions by these three sets of actors will not completely remediate the digital offense capability. The gap can be small, or it can be exceptionally large, hence the net negative cost to the digital ecosystem. PropositionDigital offense capabilities are currently net negative for the security ecosystem.[0]The costs of improved digital offense currently outweigh the benefits. The legitimate benefits of digital offense accrue primarily to the security one percent (#securityonepercent), and to intelligence, military, and law enforcement agencies. The derived defensive benefits depend on the nature of the defender. The entire security ecosystem bears the costs, and in some cases even those who see tangible benefit may suffer costs exceeding those benefits.The ReasonLimitations of scaling are the reason why digital offense capabilities are currently net negative.Consider the case of an actor developing a digital offense capability, and publishing it to the general public. From the target side, limitations on scaling prevent complete mitigation or remediation of the vulnerability.The situation is much different from the offense perspective.Any actor may leverage the offense capability against any Internet-connected target on the planet. The actor can scale that capability across the entire range of vulnerable or exposed targets.The ThreeOnly three sets of actors are able to possibly leverage an offense capability for defensive purposes.First, the organization responsible for developing and maintaining the vulnerable or exposed asset can determine if there is a remedy for the new offense capability. (This is typically a "vendor," but could be a noncommercial entity. As a shorthand, I will use "vendor.") The vendor can try to develop and deploy a patch or mitigation method.Second, major consumers of the vulnerable or exposed asset can take similar steps, usually by implementing the vendor's patch or mitigation.Third, the security one percent can take some defensive measures, either by implementing the vendor's patch or mitigation, or by developing and acting upon detection and response processes.The combination of the actions by these three sets of actors will not completely remediate the digital offense capability. The gap can be small, or it can be exceptionally large, hence the net negative cost to the digital ecosystem. |
Ransomware Threat | |||
| 2020-11-09 08:30:17 | New Book! The Best of TaoSecurity Blog, Volume 3 (lien direct) |  Introduction I published a new book!The Best of TaoSecurity Blog, Volume 3: Current Events, Law, Wise People, History, and Appendices is the third title in the TaoSecurity Blog series. It's in the Kindle Store, and if you have an Unlimited account, it's free. I also published a print edition, which is 485 pages. Book DescriptionThe book features the following description on the back cover:Since 2003, cybersecurity author Richard Bejtlich has been publishing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 stories and approximately one million words, he has selected and republished the very best entries from 17 years of writing, along with commentaries and additional material. In the third volume of the TaoSecurity Blog series, Mr. Bejtlich addresses the evolution of his security mindset, influenced by current events and advice from his so-called set of "wise people." He talks about why speed is not the key to John Boyd's OODA loop, and why security strategies designed for and by the "security 1%" may be irrelevant at best, or harmful at worst, for the remaining "99%". His history section explores the origins of the terms threat hunting and indicators of compromise, and reveals who really created the quote "there are two types of companies." His chapter on law highlights traps that might catch security teams, with advice to chief information security officers.This volume contains some of Mr. Bejtlich's favorite posts, such as Marcus Ranum's answer to what happens when security teams confront professionals, or how the Internet continues to function despite constant challenges, or reactions to comments by Dan Geer, Bruce Schneier, Marty Roesch, and other security leaders. Mr. Bejtlich has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Writing the SeriesAlthough I had written and self-published a book in early 2019, I had used Blurb and stayed in print format. Introduction I published a new book!The Best of TaoSecurity Blog, Volume 3: Current Events, Law, Wise People, History, and Appendices is the third title in the TaoSecurity Blog series. It's in the Kindle Store, and if you have an Unlimited account, it's free. I also published a print edition, which is 485 pages. Book DescriptionThe book features the following description on the back cover:Since 2003, cybersecurity author Richard Bejtlich has been publishing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 stories and approximately one million words, he has selected and republished the very best entries from 17 years of writing, along with commentaries and additional material. In the third volume of the TaoSecurity Blog series, Mr. Bejtlich addresses the evolution of his security mindset, influenced by current events and advice from his so-called set of "wise people." He talks about why speed is not the key to John Boyd's OODA loop, and why security strategies designed for and by the "security 1%" may be irrelevant at best, or harmful at worst, for the remaining "99%". His history section explores the origins of the terms threat hunting and indicators of compromise, and reveals who really created the quote "there are two types of companies." His chapter on law highlights traps that might catch security teams, with advice to chief information security officers.This volume contains some of Mr. Bejtlich's favorite posts, such as Marcus Ranum's answer to what happens when security teams confront professionals, or how the Internet continues to function despite constant challenges, or reactions to comments by Dan Geer, Bruce Schneier, Marty Roesch, and other security leaders. Mr. Bejtlich has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Writing the SeriesAlthough I had written and self-published a book in early 2019, I had used Blurb and stayed in print format. |
Threat Guideline | |||
| 2020-10-31 16:11:10 | Security and the One Percent: A Thought Exercise in Estimation and Consequences (lien direct) | There's a good chance that if you're reading this post, you're the member of an exclusive club. I call it the security one percent, or the security 1%. This is shorthand for the assortment of people and organizations who have the personnel, processes, technology, and support to implement somewhat robust digital security programs, especially those with the detection and response capabilities and not just planning and resistance/"prevention" functions. Introduction This post will estimate the size of the security 1% in the United States. It will then briefly explain how the security strategies of the 1% might be irrelevant at best or damaging at worse to the 99%.A First Cut with FIRSTIt's difficult to measure the size of the security 1%, but not impossible. My goal is to ascertain the correct orders of magnitude. One method is to review entities who are members of the Forum of Incident Response and Security Teams, or FIRST. FIRST is an organization to which high-performing computer incident response teams (CIRTs) may apply once their processes and data handling meet standards set by FIRST. I learned of FIRST when the AFCERT was a member in the late 1990s. I also assisted with FIRST duties when Foundstone was a member in the early 2000s. I helped or sponsored membership when I worked at General Electric in the 2000s and Mandiant in the 2010s. I encourage all capable security teams to join FIRST.Being a FIRST member means having a certain degree of incident response and data handling capability, and it signals to the world and to other FIRST teams that the member entity is serious about incident detection and response.As of the writing of this post, there are 540 FIRST teams worldwide. Slightly more than 100 of them are based in the United States. To put that in perspective, there are less than 4,000 publicly traded companies in the US. That means that even if every single US FIRST member represented a publicly traded company -- and that is not the case -- FIRST representation for US publicly traded companies is only 2.5%. Beyond FIRSTSome of you might claim FIRST membership is no big deal. My current employer, Corelight, isn't a member, you might say. Perhaps you could argue that for every US FIRST member, there are 9 others which have equivalent or better security teams. That would increase the cadre of entities with respectable detection and response capabilities from 100 to 1,000. That would still mean an estimate that says 75% of publicly traded US companies have sub-par or non-existent security programs.Remember that we've only been talking about a population of 4,000 publicly traded US companies. The US Small Business and Entrepreneurship Council estimates that there were 5.6 million employer firms in the United States in 2016. Let's sadly reduce that to 4 million to account for the devastation of Covid. | Threat Guideline | |||
| 2020-10-10 11:30:12 | Greg Rattray Invented the Term Advanced Persistent Threat (lien direct) |  I was so pleased to read this Tweet yesterday from Greg Rattray:"Back in 2007, I coined the term “Advanced Persistent Threat” to characterize emerging adversaries that we needed to work with the defense industrial base to deal with... Since then both the APT term and the nature of our adversaries have evolved. What hasn't changed is that in cyberspace, advanced attackers will persistently go after targets with assets they want, no matter the strength of defenses."BackgroundFirst, some background. Who is Greg Rattray?First, you could call him Colonel or Doctor. I will use Col as that was the last title I used with him, although these days when we chat I call him Greg. Col Rattray served 21 years in the Air Force and also earned his PhD in international security from Tufts University. His thesis formed the content for his 2001 book Strategic Warfare in Cyberspace, which I reviewed in 2002 and rated 4 stars. (Ouch -- I was a bit stingy with the stars back then. I was more of an operator and less of a theorist or historian in those days. Such was my bias I suppose.)Col Rattray is also a 1984 graduate of the Air Force Academy. He studied history and political science there and returned as an assistant professor in the early 1990s. He was one of my instructors when I was a cadet there. (I graduated in 1994 with degrees in history and political science.) Col Rattray then earned a master of public policy degree at Harvard Kennedy School. (I did the same, in 1996.) Do you see a pattern here? He is clearly a role model. Of course, I did not stay in the Air Force as long, earn the same rank, or survive my PhD program!After the Academy, Col Rattray served as commander of the 23rd Information Operations Squadrons on Security Hill in San Antonio, Texas. I was working in the AFCERT at the time. I was so pleased to read this Tweet yesterday from Greg Rattray:"Back in 2007, I coined the term “Advanced Persistent Threat” to characterize emerging adversaries that we needed to work with the defense industrial base to deal with... Since then both the APT term and the nature of our adversaries have evolved. What hasn't changed is that in cyberspace, advanced attackers will persistently go after targets with assets they want, no matter the strength of defenses."BackgroundFirst, some background. Who is Greg Rattray?First, you could call him Colonel or Doctor. I will use Col as that was the last title I used with him, although these days when we chat I call him Greg. Col Rattray served 21 years in the Air Force and also earned his PhD in international security from Tufts University. His thesis formed the content for his 2001 book Strategic Warfare in Cyberspace, which I reviewed in 2002 and rated 4 stars. (Ouch -- I was a bit stingy with the stars back then. I was more of an operator and less of a theorist or historian in those days. Such was my bias I suppose.)Col Rattray is also a 1984 graduate of the Air Force Academy. He studied history and political science there and returned as an assistant professor in the early 1990s. He was one of my instructors when I was a cadet there. (I graduated in 1994 with degrees in history and political science.) Col Rattray then earned a master of public policy degree at Harvard Kennedy School. (I did the same, in 1996.) Do you see a pattern here? He is clearly a role model. Of course, I did not stay in the Air Force as long, earn the same rank, or survive my PhD program!After the Academy, Col Rattray served as commander of the 23rd Information Operations Squadrons on Security Hill in San Antonio, Texas. I was working in the AFCERT at the time. |
Threat Guideline | |||
| 2020-09-01 08:30:06 | New Book! The Best of TaoSecurity Blog, Volume 2 (lien direct) |  I published a new book!The Best of TaoSecurity Blog, Volume 2: Network Security Monitoring, Technical Notes, Research, and China and the Advanced Persistent ThreatIt's in the Kindle Store, and if you're Unlimited it's free. Print edition to follow.The book lists as having 413 pages (for the Kindle edition at least) at it's almost 95,000 words. I started working on it in June after finishing Volume 1.Here is the book description:Since 2003, cybersecurity author Richard Bejtlich has been writing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 posts and approximately one million words, he has selected and republished the very best entries from 17 years of writing. In the second volume of the TaoSecurity Blog series, Mr. Bejtlich addresses how to detect and respond to intrusions using third party threat intelligence sources, network data, application and infrastructure data, and endpoint data. He assesses government and private security initiatives and applies counterintelligence and counteradversary mindsets to defend digital assets. He documents the events of the last 20 years of Chinese hacking from the perspective of a defender on the front lines, in the pre- and post-APT era. This volume contains some of Mr. Bejtlich's favorite posts, such as histories of threat hunting, so-called black and white hat budgeting, attribution capabilities and limits, and rating information security incidents. He has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.I have a third volume planned. I will publish it by the end of the year. I published a new book!The Best of TaoSecurity Blog, Volume 2: Network Security Monitoring, Technical Notes, Research, and China and the Advanced Persistent ThreatIt's in the Kindle Store, and if you're Unlimited it's free. Print edition to follow.The book lists as having 413 pages (for the Kindle edition at least) at it's almost 95,000 words. I started working on it in June after finishing Volume 1.Here is the book description:Since 2003, cybersecurity author Richard Bejtlich has been writing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 posts and approximately one million words, he has selected and republished the very best entries from 17 years of writing. In the second volume of the TaoSecurity Blog series, Mr. Bejtlich addresses how to detect and respond to intrusions using third party threat intelligence sources, network data, application and infrastructure data, and endpoint data. He assesses government and private security initiatives and applies counterintelligence and counteradversary mindsets to defend digital assets. He documents the events of the last 20 years of Chinese hacking from the perspective of a defender on the front lines, in the pre- and post-APT era. This volume contains some of Mr. Bejtlich's favorite posts, such as histories of threat hunting, so-called black and white hat budgeting, attribution capabilities and limits, and rating information security incidents. He has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.I have a third volume planned. I will publish it by the end of the year.  If you have any questions about the book, let me know. Currently you can see the table of contents via the "Look Inside" function, and there is a sample that lets you download and read some of the book. Enjoy!Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) If you have any questions about the book, let me know. Currently you can see the table of contents via the "Look Inside" function, and there is a sample that lets you download and read some of the book. Enjoy!Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
Threat | |||
| 2019-11-06 16:12:52 | Seven Security Strategies, Summarized (lien direct) | This is the sort of story that starts as a comment on Twitter, then becomes a blog post when I realize I can't fit all the ideas into one or two Tweets. (You know how much I hate Tweet threads, and how I encourage everyone to capture deep thoughts in blog posts!)In the interest of capturing the thought, and not in the interest of thinking too deeply or comprehensively (at least right now), I offer seven security strategies, summarized.When I mention the risk equation, I'm talking about the idea that one can conceptually image the risk of some negative event using this "formula": Risk (of something) is the product of some measurements of Vulnerability X Threat X Asset Value, or R = V x T x A.Denial and/or ignorance. This strategy assumes the risk due to loss is low, because those managing the risk assume that one or more of the elements of the risk equation are zero or almost zero, or they are apathetic to the cost.Loss acceptance. This strategy may assume the risk due to loss is low, or more likely those managing the risk assume that the cost of risk realization is low. In other words, incidents will occur, but the cost of the incident is acceptable to the organization.Loss transferal. This strategy may also assume the risk due to loss is low, but in contrast with risk acceptance, the organization believes it can buy an insurance policy which will cover the cost of an incident, and the cost of the policy is cheaper than alternative strategies.Vulnerability elimination. This strategy focuses on driving the vulnerability element of the risk equation to zero or almost zero, through secure coding, proper configuration, patching, and similar methods.Threat elimination. This strategy focuses on driving the threat element of the risk equation to zero or almost zero, through deterrence, dissuasion, co-option, bribery, conversion, incarceration, incapacitation, or other methods that change the intent and/or capabilities of threat actors. Asset value elimination. This strategy focuses on driving the threat element of the risk equation to zero or almost zero, through minimizing data or resources that might be valued by adversaries.Interdiction. This is a hybrid strategy which welcomes contributions from vulnerability elimination, primarily, but is open to assistance from loss transferal, threat elimination, and asset value elimination. Interdiction assumes that prevention eventually fails, but that security teams can detect and respond to incidents post-compromise and pre-breach. In other words, some classes of intruders will indeed compromise an organization, but it is possible to detect and respond to the attack before the adversary completes his mission.As you might expect, I am most closely associated with the interdiction strategy. I believe the denial and/or ignorance and loss acceptance strategies are irresponsible.I believe the loss transferal strategy continues to gain momentum with the growth of cybersecurity breach insurance policies. I believe the vulnerability elimination strategy is important but ultimately, on its own, ineffective and historically shown to be impossible. When used in concert with other strategies, it is absolutely helpful.I believe the threat elimination strategy is generally beyond the scope of private organizations. As the state retains the monopoly on the use of force, usually only law enforcement, military, and sometimes intelligence agencies can truly eliminate or mitigate threats. (Threats are not vulnerabilities.)I believe asset value elimination is powerful but has not gained the ground I would like to see. This is my " | Vulnerability Threat | |||
| 2019-05-29 09:55:00 | Know Your Limitations (lien direct) |  At the end of the 1973 Clint Eastwood movie Magnum Force, after Dirty Harry watches his corrupt police captain explode in a car, he says "a man's got to know his limitations."I thought of this quote today as the debate rages about compromising municipalities and other information technology-constrained yet personal information-rich organizations.Several years ago I wrote If You Can't Protect It, Don't Collect It. I argued that if you are unable to defend personal information, then you should not gather and store it.In a similar spirit, here I argue that if you are unable to securely operate information technology that matters, then you should not be supporting that IT.You should outsource it to a trustworthy cloud provider, and concentrate on managing secure access to those services.If you cannot outsource it, and you remain incapable of defending it natively, then you should integrate a capable managed security provider.It's clear to me that a large portion of those running PI-processing IT are simply not capable of doing so in secure manner, and they do not bear the full cost of PI breaches.They have too many assets, with too many vulnerabilities, and are targeted by too many threat actors.These organizations lack sufficient people, processes, and technologies to mitigate the risk.They have successes, but they are generally due to the heroics of individual IT and security professionals, who often feel out-gunned by their adversaries.If you can't patch a two-year-old vulnerability prior to exploitation, or detect an intrusion and respond to the adversary before he completes his mission, then you are demonstrating that you need to change your entire approach to information technology.The security industry seems to think that throwing more people at the problem is the answer, yet year after year we read about several million job openings that remain unfilled. This is a sign that we need to change the way we are doing business. The fact is that those organziations that cannot defend themselves need to recognize their limitations and change their game.I recognize that outsourcing is not a panacea. Note that I emphasized "IT" in my recommendation. I do not see how one could outsource the critical technology running on-premise in the industrial control system (ICS) world, for example. Those operations may need to rely more on outsourced security providers, if they cannot sufficiently detect and respond to intrusions using in-house capabilities.Remember that the vast majority of organizations do not exist to run IT. They run IT to support their lines of business. Many older organizations have indeed been migrating legacy applications to the cloud, and most new organizations are cloud-native. These are hopeful signs, as the older organizations could potentially "age-out" over time.This puts a burden on the cloud providers, who fall into the "managed service provider" category that I wrote about in my recent Corelight blog. However, the more trustworthy providers have the people, proc At the end of the 1973 Clint Eastwood movie Magnum Force, after Dirty Harry watches his corrupt police captain explode in a car, he says "a man's got to know his limitations."I thought of this quote today as the debate rages about compromising municipalities and other information technology-constrained yet personal information-rich organizations.Several years ago I wrote If You Can't Protect It, Don't Collect It. I argued that if you are unable to defend personal information, then you should not gather and store it.In a similar spirit, here I argue that if you are unable to securely operate information technology that matters, then you should not be supporting that IT.You should outsource it to a trustworthy cloud provider, and concentrate on managing secure access to those services.If you cannot outsource it, and you remain incapable of defending it natively, then you should integrate a capable managed security provider.It's clear to me that a large portion of those running PI-processing IT are simply not capable of doing so in secure manner, and they do not bear the full cost of PI breaches.They have too many assets, with too many vulnerabilities, and are targeted by too many threat actors.These organizations lack sufficient people, processes, and technologies to mitigate the risk.They have successes, but they are generally due to the heroics of individual IT and security professionals, who often feel out-gunned by their adversaries.If you can't patch a two-year-old vulnerability prior to exploitation, or detect an intrusion and respond to the adversary before he completes his mission, then you are demonstrating that you need to change your entire approach to information technology.The security industry seems to think that throwing more people at the problem is the answer, yet year after year we read about several million job openings that remain unfilled. This is a sign that we need to change the way we are doing business. The fact is that those organziations that cannot defend themselves need to recognize their limitations and change their game.I recognize that outsourcing is not a panacea. Note that I emphasized "IT" in my recommendation. I do not see how one could outsource the critical technology running on-premise in the industrial control system (ICS) world, for example. Those operations may need to rely more on outsourced security providers, if they cannot sufficiently detect and respond to intrusions using in-house capabilities.Remember that the vast majority of organizations do not exist to run IT. They run IT to support their lines of business. Many older organizations have indeed been migrating legacy applications to the cloud, and most new organizations are cloud-native. These are hopeful signs, as the older organizations could potentially "age-out" over time.This puts a burden on the cloud providers, who fall into the "managed service provider" category that I wrote about in my recent Corelight blog. However, the more trustworthy providers have the people, proc |
Vulnerability Threat | |||
| 2018-12-18 11:22:26 | The Origin of the Quote "There Are Two Types of Companies" (lien direct) |  While listening to a webcast this morning, I heard the speaker mentionThere are two types of companies: those who have been hacked, and those who don't yet know they have been hacked.He credited Cisco CEO John Chambers but didn't provide any source.That didn't sound right to me. I could think of two possible antecedents. so I did some research. I confirmed my memory and would like to present what I found here.John Chambers did indeed offer the previous quote, in a January 2015 post for the World Economic Forum titled What does the Internet of Everything mean for security? Unfortunately, neither Mr Chambers nor the person who likely wrote the article for him decided to credit the author of this quote.Before providing proper credit for this quote, we need to decide what the quote actually says. As noted in this October 2015 article by Frank Johnson titled Are there really only “two kinds of enterprises”?, there are really (at least) two versions of this quote:A popular meme in the information security industry is, “There are only two types of companies: those that know they've been compromised, and those that don't know.”And the second is like unto it: “There are only two kinds of companies: those that have been hacked, and those that will be.”We see that the first is a version of what Mr Chambers said. Let's call that 2-KNOW. The second is different. Let's call that 2-BE.The first version, 2-KNOW, can be easily traced and credited to Dmitri Alperovitch. He stated this proposition as part of the publicity around his Shady RAT report, written while he worked at McAfee. For example, this 3 August 2011 story by Ars Technica, Operation Shady RAT: five-year hack attack hit 14 countries, quotes Dmitri in the following:So widespread are the attacks that Dmitri Alperovitch, McAfee Vice President of Threat Research, said that the only companies not at risk are those who have nothing worth taking, and that of the world's biggest firms, there are just two kinds: those that know they've been compromised, and those that still haven't realized they've been compromised.Dmitri used slightly different language in this popular Vanity Fair article from September 2011, titled Enter the Cyber-Dragon:Dmitri Alperovitch, who discovered Operation Shady rat, draws a stark lesson: “There are only two types of companies-those that know they've been compromised, and those that don't know. If you have anything that may be valuable to a competitor, you will be targeted, and almost certainly compromised.”No doubt former FBI Director Mueller read this report (and probably spoke with Dmitri). He delivered a speech at RSA on 1 March 2012 that introduced question 2-BE into the lexicon, plus a little more:For it is no longer a question of “if,” but “when” and While listening to a webcast this morning, I heard the speaker mentionThere are two types of companies: those who have been hacked, and those who don't yet know they have been hacked.He credited Cisco CEO John Chambers but didn't provide any source.That didn't sound right to me. I could think of two possible antecedents. so I did some research. I confirmed my memory and would like to present what I found here.John Chambers did indeed offer the previous quote, in a January 2015 post for the World Economic Forum titled What does the Internet of Everything mean for security? Unfortunately, neither Mr Chambers nor the person who likely wrote the article for him decided to credit the author of this quote.Before providing proper credit for this quote, we need to decide what the quote actually says. As noted in this October 2015 article by Frank Johnson titled Are there really only “two kinds of enterprises”?, there are really (at least) two versions of this quote:A popular meme in the information security industry is, “There are only two types of companies: those that know they've been compromised, and those that don't know.”And the second is like unto it: “There are only two kinds of companies: those that have been hacked, and those that will be.”We see that the first is a version of what Mr Chambers said. Let's call that 2-KNOW. The second is different. Let's call that 2-BE.The first version, 2-KNOW, can be easily traced and credited to Dmitri Alperovitch. He stated this proposition as part of the publicity around his Shady RAT report, written while he worked at McAfee. For example, this 3 August 2011 story by Ars Technica, Operation Shady RAT: five-year hack attack hit 14 countries, quotes Dmitri in the following:So widespread are the attacks that Dmitri Alperovitch, McAfee Vice President of Threat Research, said that the only companies not at risk are those who have nothing worth taking, and that of the world's biggest firms, there are just two kinds: those that know they've been compromised, and those that still haven't realized they've been compromised.Dmitri used slightly different language in this popular Vanity Fair article from September 2011, titled Enter the Cyber-Dragon:Dmitri Alperovitch, who discovered Operation Shady rat, draws a stark lesson: “There are only two types of companies-those that know they've been compromised, and those that don't know. If you have anything that may be valuable to a competitor, you will be targeted, and almost certainly compromised.”No doubt former FBI Director Mueller read this report (and probably spoke with Dmitri). He delivered a speech at RSA on 1 March 2012 that introduced question 2-BE into the lexicon, plus a little more:For it is no longer a question of “if,” but “when” and |
Hack Threat | |||
| 2018-11-24 15:23:09 | Even More on Threat Hunting (lien direct) |  In response to my post More on Threat Hunting, Rob Lee asked:[D]o you consider detection through ID'ing/“matching” TTPs not hunting?To answer this question, we must begin by clarifying "TTPs." Most readers know TTPs to mean tactics, techniques and procedures, defined by David Bianco in his Pyramid of Pain post as:How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between.In case you've forgotten David's pyramid, it looks like this. In response to my post More on Threat Hunting, Rob Lee asked:[D]o you consider detection through ID'ing/“matching” TTPs not hunting?To answer this question, we must begin by clarifying "TTPs." Most readers know TTPs to mean tactics, techniques and procedures, defined by David Bianco in his Pyramid of Pain post as:How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between.In case you've forgotten David's pyramid, it looks like this.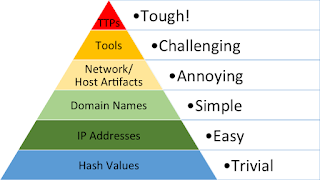 It's important to recognize that the pyramid consists of indicators of compromise (IOCs). David uses the term "indicator" in his original post, but his follow-up post from his time at Sqrrl makes this clear:There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Sqrrl Security Architect, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. At this point it should be clear that I consider TTPs to be one form of IOC.In The Practice of Network Security Monitoring, I included the following workflow: It's important to recognize that the pyramid consists of indicators of compromise (IOCs). David uses the term "indicator" in his original post, but his follow-up post from his time at Sqrrl makes this clear:There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Sqrrl Security Architect, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. At this point it should be clear that I consider TTPs to be one form of IOC.In The Practice of Network Security Monitoring, I included the following workflow: |
Malware Threat | |||
| 2018-11-23 12:36:47 | More on Threat Hunting (lien direct) |  Earlier this week hellor00t asked via Twitter:Where would you place your security researchers/hunt team?I replied:For me, "hunt" is just a form of detection. I don't see the need to build a "hunt" team. IR teams detect intruders using two major modes: matching and hunting. Junior people spend more time matching. Senior people spend more time hunting. Both can and should do both functions.This inspired Rob Lee to blog a response, from which I extract his core argument:[Hunting] really isn't, to me, about detecting threats...Hunting is a hypothesis-led approach to testing your environment for threats. The purpose, to me, is not in finding threats but in determining what gaps you have in your ability to detect and respond to them...In short, hunting, to me, is a way to assess your security (people, process, and technology) against threats while extending your automation footprint to better be prepared in the future. Or simply stated, it's incident response without the incident that's done with a purpose and contributes something. As background for my answer, I recommend my March 2017 post The Origin of Threat Hunting, which cites my article "Become a Hunter," published in the July-August 2011 issue of Information Security Magazine. I wrote it in the spring of 2011, when I was director of incident response for GE-CIRT.For the term "hunting," I give credit to briefers from the Air Force and NSA who, in the mid-2000s briefed "hunter-killer" missions to the Red Team/Blue Team Symposium at the Johns Hopkins University Applied Physics Lab in Laurel, MD.As a comment to that post, Tony Sager, who ran NSA VAO at the time I was briefed at ReBl, described hunting thus:[Hunting] was an active and sustained search for Attackers...For us, "Hunt" meant a very planned and sustained search, taking advantage of the existing infrastructure of Red/Blue Teams and COMSEC Monitoring, as well as intelligence information to guide the search. For the practice of hunting, as I experienced it, I give credit to our GE-CIRT incident handlers -- David Bianco, Ken Bradley, Tim Crothers, Tyler Hudak, Bamm Visscher, and Aaron Wade -- who took junior analysts on "hunting trips," starting in 2008-2009.It is very clear, to me, that hunting has always been associated with detecting an adversary, not "determining what gaps you have in your ability to detect and respond to them," as characterized by Rob.For me, Rob is describing the job of an enterprise visibility architect, which I described in a 2007 post:[W]e are stuck with numerous platforms, operating systems, applications, and data (POAD) for which we have zero visibility. I suggest that enterprises consider hiring or assigning a new role -- Enterprise Visibility Architect. The role of the EVA is to identify visibility deficiencies in existing and future POAD and Earlier this week hellor00t asked via Twitter:Where would you place your security researchers/hunt team?I replied:For me, "hunt" is just a form of detection. I don't see the need to build a "hunt" team. IR teams detect intruders using two major modes: matching and hunting. Junior people spend more time matching. Senior people spend more time hunting. Both can and should do both functions.This inspired Rob Lee to blog a response, from which I extract his core argument:[Hunting] really isn't, to me, about detecting threats...Hunting is a hypothesis-led approach to testing your environment for threats. The purpose, to me, is not in finding threats but in determining what gaps you have in your ability to detect and respond to them...In short, hunting, to me, is a way to assess your security (people, process, and technology) against threats while extending your automation footprint to better be prepared in the future. Or simply stated, it's incident response without the incident that's done with a purpose and contributes something. As background for my answer, I recommend my March 2017 post The Origin of Threat Hunting, which cites my article "Become a Hunter," published in the July-August 2011 issue of Information Security Magazine. I wrote it in the spring of 2011, when I was director of incident response for GE-CIRT.For the term "hunting," I give credit to briefers from the Air Force and NSA who, in the mid-2000s briefed "hunter-killer" missions to the Red Team/Blue Team Symposium at the Johns Hopkins University Applied Physics Lab in Laurel, MD.As a comment to that post, Tony Sager, who ran NSA VAO at the time I was briefed at ReBl, described hunting thus:[Hunting] was an active and sustained search for Attackers...For us, "Hunt" meant a very planned and sustained search, taking advantage of the existing infrastructure of Red/Blue Teams and COMSEC Monitoring, as well as intelligence information to guide the search. For the practice of hunting, as I experienced it, I give credit to our GE-CIRT incident handlers -- David Bianco, Ken Bradley, Tim Crothers, Tyler Hudak, Bamm Visscher, and Aaron Wade -- who took junior analysts on "hunting trips," starting in 2008-2009.It is very clear, to me, that hunting has always been associated with detecting an adversary, not "determining what gaps you have in your ability to detect and respond to them," as characterized by Rob.For me, Rob is describing the job of an enterprise visibility architect, which I described in a 2007 post:[W]e are stuck with numerous platforms, operating systems, applications, and data (POAD) for which we have zero visibility. I suggest that enterprises consider hiring or assigning a new role -- Enterprise Visibility Architect. The role of the EVA is to identify visibility deficiencies in existing and future POAD and |
Threat | |||
| 2018-09-18 09:48:27 | Firewalls and the Need for Speed (lien direct) | I was looking for resources on campus network design and found these slides (pdf) from a 2011 Network Startup Resource Center presentation. These two caught my attention: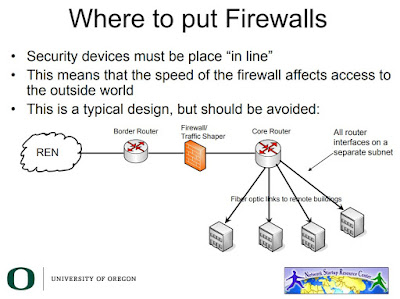  This bothered me, so I Tweeted about it.This started some discussion, and prompted me to see what NSRC suggests for architecture these days. You can find the latest, from April 2018, here. Here is the bottom line for their suggested architecture: This bothered me, so I Tweeted about it.This started some discussion, and prompted me to see what NSRC suggests for architecture these days. You can find the latest, from April 2018, here. Here is the bottom line for their suggested architecture:    What do you think of this architecture?My Tweet has attracted some attention from the high speed network researcher community, some of whom assume I must be a junior security apprentice who equates "firewall" with "security." Long-time blog readers will laugh at that, like I did. So what was my problem with the What do you think of this architecture?My Tweet has attracted some attention from the high speed network researcher community, some of whom assume I must be a junior security apprentice who equates "firewall" with "security." Long-time blog readers will laugh at that, like I did. So what was my problem with the |
Threat | |||
| 2018-07-22 10:05:07 | Defining Counterintelligence (lien direct) |  I've written about counterintelligence (CI) before, but I realized today that some of my writing, and the writing of others, may be confused as to exactly what CI means.The authoritative place to find an American definition for CI is the United States National Counterintelligence and Security Center. I am more familiar with the old name of this organization, the Office of the National Counterintelligence Executive (ONCIX).The 2016 National Counterintelligence Strategy cites Executive Order 12333 (as amended) for its definition of CI:Counterintelligence – Information gathered and activities conducted to identify, deceive,exploit, disrupt, or protect against espionage, other intelligence activities, sabotage, or assassinations conducted for or on behalf of foreign powers, organizations, or persons, or their agents, or international terrorist organizations or activities. (emphasis added)The strict interpretation of this definition is countering foreign nation state intelligence activities, such as those conducted by China's Ministry of State Security (MSS), the Foreign Intelligence Service of the Russian Federation (SVR RF), Iran's Ministry of Intelligence, or the military intelligence services of those countries and others.In other words, counterintelligence is countering foreign intelligence. The focus is on the party doing the bad things, and less on what the bad thing is.The definition, however, is loose enough to encompass others; "organizations," "persons," and "international terrorist organizations" are in scope, according to the definition. This is just about everyone, although criminals are explicitly not mentioned.The definition is also slightly unbounded by moving beyond "espionage, or other intelligence activities," to include "sabotage, or assassinations." In those cases, the assumptions is that foreign intelligence agencies and their proxies are the parties likely to be conducting sabotage or assassinations. In the course of their CI work, paying attention to foreign intelligence agents, the CI team may encounter plans for activities beyond collection.The bottom line for this post is a cautionary message. It's not appropriate to call all intelligence activities "counterintelligence." It's more appropriate to call countering adversary intelligence activities counterintelligence.You may use similar or the same approaches as counterintelligence agents when performing your cyber threat intelligence function. For example, you may recruit a source inside a carding forum, or you may plant your own source in a carding forum. This is similar to turning a foreign intelligence agent, or inserting your own agent in a foreign intelligence service. However, activities directing against a carding forum are not counterintelligence. Activities directing against a foreign intelligence service are counterintelligence.The nature and target of your intelligence activities are what determine if it is counterintelligence, not necessarily the methods you use. Again, this is in keeping with the stricter definition, and not becoming a victim of scope creep.Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecurity.b I've written about counterintelligence (CI) before, but I realized today that some of my writing, and the writing of others, may be confused as to exactly what CI means.The authoritative place to find an American definition for CI is the United States National Counterintelligence and Security Center. I am more familiar with the old name of this organization, the Office of the National Counterintelligence Executive (ONCIX).The 2016 National Counterintelligence Strategy cites Executive Order 12333 (as amended) for its definition of CI:Counterintelligence – Information gathered and activities conducted to identify, deceive,exploit, disrupt, or protect against espionage, other intelligence activities, sabotage, or assassinations conducted for or on behalf of foreign powers, organizations, or persons, or their agents, or international terrorist organizations or activities. (emphasis added)The strict interpretation of this definition is countering foreign nation state intelligence activities, such as those conducted by China's Ministry of State Security (MSS), the Foreign Intelligence Service of the Russian Federation (SVR RF), Iran's Ministry of Intelligence, or the military intelligence services of those countries and others.In other words, counterintelligence is countering foreign intelligence. The focus is on the party doing the bad things, and less on what the bad thing is.The definition, however, is loose enough to encompass others; "organizations," "persons," and "international terrorist organizations" are in scope, according to the definition. This is just about everyone, although criminals are explicitly not mentioned.The definition is also slightly unbounded by moving beyond "espionage, or other intelligence activities," to include "sabotage, or assassinations." In those cases, the assumptions is that foreign intelligence agencies and their proxies are the parties likely to be conducting sabotage or assassinations. In the course of their CI work, paying attention to foreign intelligence agents, the CI team may encounter plans for activities beyond collection.The bottom line for this post is a cautionary message. It's not appropriate to call all intelligence activities "counterintelligence." It's more appropriate to call countering adversary intelligence activities counterintelligence.You may use similar or the same approaches as counterintelligence agents when performing your cyber threat intelligence function. For example, you may recruit a source inside a carding forum, or you may plant your own source in a carding forum. This is similar to turning a foreign intelligence agent, or inserting your own agent in a foreign intelligence service. However, activities directing against a carding forum are not counterintelligence. Activities directing against a foreign intelligence service are counterintelligence.The nature and target of your intelligence activities are what determine if it is counterintelligence, not necessarily the methods you use. Again, this is in keeping with the stricter definition, and not becoming a victim of scope creep.Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecurity.b |
Threat |
1
We have: 13 articles.
We have: 13 articles.
To see everything:
Our RSS (filtrered)
