What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-01-08 10:00:00 | Happy 20th Birthday TaoSecurity Blog (lien direct) |  Happy 20th birthday TaoSecurity Blog, born on 8 January 2003. Thank you BloggerBlogger (now part of Google) has continuously hosted this blog for 20 years, for free. I'd like to thank Blogger and Google for providing this platform for two decades. It's tough to find extant self-hosted security content that was born at the same time, or earlier. Bruce Schneier's Schneier on Security is the main one that comes to mind. If not for the wonderful Internet Archive, many blogs from the early days would be lost.StatisticsIn my 15 year post I included some statistics, so here are a few, current as of the evening of 7 January: Happy 20th birthday TaoSecurity Blog, born on 8 January 2003. Thank you BloggerBlogger (now part of Google) has continuously hosted this blog for 20 years, for free. I'd like to thank Blogger and Google for providing this platform for two decades. It's tough to find extant self-hosted security content that was born at the same time, or earlier. Bruce Schneier's Schneier on Security is the main one that comes to mind. If not for the wonderful Internet Archive, many blogs from the early days would be lost.StatisticsIn my 15 year post I included some statistics, so here are a few, current as of the evening of 7 January: I think it's cool to see almost 29 million "all time" views, but that's not the whole story.Here are the so-called "all time" statistics: I think it's cool to see almost 29 million "all time" views, but that's not the whole story.Here are the so-called "all time" statistics: It turns out that Blogger only started capturing these numbers in January 2011. That means I've had almost 29 million views in the last 12 years. I don't know what happened on 20 April 2022, when I had almost 1.5 million views?Top Ten Posts Since January 2011 It turns out that Blogger only started capturing these numbers in January 2011. That means I've had almost 29 million views in the last 12 years. I don't know what happened on 20 April 2022, when I had almost 1.5 million views?Top Ten Posts Since January 2011 |
Ransomware Studies Guideline | Solardwinds | ★★ | |
| 2020-11-09 08:30:17 | New Book! The Best of TaoSecurity Blog, Volume 3 (lien direct) |  Introduction I published a new book!The Best of TaoSecurity Blog, Volume 3: Current Events, Law, Wise People, History, and Appendices is the third title in the TaoSecurity Blog series. It's in the Kindle Store, and if you have an Unlimited account, it's free. I also published a print edition, which is 485 pages. Book DescriptionThe book features the following description on the back cover:Since 2003, cybersecurity author Richard Bejtlich has been publishing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 stories and approximately one million words, he has selected and republished the very best entries from 17 years of writing, along with commentaries and additional material. In the third volume of the TaoSecurity Blog series, Mr. Bejtlich addresses the evolution of his security mindset, influenced by current events and advice from his so-called set of "wise people." He talks about why speed is not the key to John Boyd's OODA loop, and why security strategies designed for and by the "security 1%" may be irrelevant at best, or harmful at worst, for the remaining "99%". His history section explores the origins of the terms threat hunting and indicators of compromise, and reveals who really created the quote "there are two types of companies." His chapter on law highlights traps that might catch security teams, with advice to chief information security officers.This volume contains some of Mr. Bejtlich's favorite posts, such as Marcus Ranum's answer to what happens when security teams confront professionals, or how the Internet continues to function despite constant challenges, or reactions to comments by Dan Geer, Bruce Schneier, Marty Roesch, and other security leaders. Mr. Bejtlich has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Writing the SeriesAlthough I had written and self-published a book in early 2019, I had used Blurb and stayed in print format. Introduction I published a new book!The Best of TaoSecurity Blog, Volume 3: Current Events, Law, Wise People, History, and Appendices is the third title in the TaoSecurity Blog series. It's in the Kindle Store, and if you have an Unlimited account, it's free. I also published a print edition, which is 485 pages. Book DescriptionThe book features the following description on the back cover:Since 2003, cybersecurity author Richard Bejtlich has been publishing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 stories and approximately one million words, he has selected and republished the very best entries from 17 years of writing, along with commentaries and additional material. In the third volume of the TaoSecurity Blog series, Mr. Bejtlich addresses the evolution of his security mindset, influenced by current events and advice from his so-called set of "wise people." He talks about why speed is not the key to John Boyd's OODA loop, and why security strategies designed for and by the "security 1%" may be irrelevant at best, or harmful at worst, for the remaining "99%". His history section explores the origins of the terms threat hunting and indicators of compromise, and reveals who really created the quote "there are two types of companies." His chapter on law highlights traps that might catch security teams, with advice to chief information security officers.This volume contains some of Mr. Bejtlich's favorite posts, such as Marcus Ranum's answer to what happens when security teams confront professionals, or how the Internet continues to function despite constant challenges, or reactions to comments by Dan Geer, Bruce Schneier, Marty Roesch, and other security leaders. Mr. Bejtlich has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Writing the SeriesAlthough I had written and self-published a book in early 2019, I had used Blurb and stayed in print format. |
Threat Guideline | |||
| 2020-10-31 16:11:10 | Security and the One Percent: A Thought Exercise in Estimation and Consequences (lien direct) | There's a good chance that if you're reading this post, you're the member of an exclusive club. I call it the security one percent, or the security 1%. This is shorthand for the assortment of people and organizations who have the personnel, processes, technology, and support to implement somewhat robust digital security programs, especially those with the detection and response capabilities and not just planning and resistance/"prevention" functions. Introduction This post will estimate the size of the security 1% in the United States. It will then briefly explain how the security strategies of the 1% might be irrelevant at best or damaging at worse to the 99%.A First Cut with FIRSTIt's difficult to measure the size of the security 1%, but not impossible. My goal is to ascertain the correct orders of magnitude. One method is to review entities who are members of the Forum of Incident Response and Security Teams, or FIRST. FIRST is an organization to which high-performing computer incident response teams (CIRTs) may apply once their processes and data handling meet standards set by FIRST. I learned of FIRST when the AFCERT was a member in the late 1990s. I also assisted with FIRST duties when Foundstone was a member in the early 2000s. I helped or sponsored membership when I worked at General Electric in the 2000s and Mandiant in the 2010s. I encourage all capable security teams to join FIRST.Being a FIRST member means having a certain degree of incident response and data handling capability, and it signals to the world and to other FIRST teams that the member entity is serious about incident detection and response.As of the writing of this post, there are 540 FIRST teams worldwide. Slightly more than 100 of them are based in the United States. To put that in perspective, there are less than 4,000 publicly traded companies in the US. That means that even if every single US FIRST member represented a publicly traded company -- and that is not the case -- FIRST representation for US publicly traded companies is only 2.5%. Beyond FIRSTSome of you might claim FIRST membership is no big deal. My current employer, Corelight, isn't a member, you might say. Perhaps you could argue that for every US FIRST member, there are 9 others which have equivalent or better security teams. That would increase the cadre of entities with respectable detection and response capabilities from 100 to 1,000. That would still mean an estimate that says 75% of publicly traded US companies have sub-par or non-existent security programs.Remember that we've only been talking about a population of 4,000 publicly traded US companies. The US Small Business and Entrepreneurship Council estimates that there were 5.6 million employer firms in the United States in 2016. Let's sadly reduce that to 4 million to account for the devastation of Covid. | Threat Guideline | |||
| 2020-10-23 10:12:50 | MITRE ATT&CK Tactics Are Not Tactics (lien direct) |  Just what are "tactics"?IntroductionMITRE ATT&CK is a great resource, but something about it has bothered me since I first heard about it several years ago. It's a minor point, but I wanted to document it in case it confuses anyone else.The MITRE ATT&CK Design and Philosophy document from March 2020 says the following:At a high-level, ATT&CK is a behavioral model that consists of the following core components:• Tactics, denoting short-term, tactical adversary goals during an attack;• Techniques, describing the means by which adversaries achieve tactical goals;• Sub-techniques, describing more specific means by which adversaries achieve tactical goals at a lower level than techniques; and• Documented adversary usage of techniques, their procedures, and other metadata.My concern is with MITRE's definition of "tactics" as "short-term, tactical adversary goals during an attack," which is oddly recursive.The key word in the tactics definition is goals. According to MITRE, "tactics" are "goals."Examples of ATT&CK TacticsATT&CK lists the following as "Enterprise Tactics": Just what are "tactics"?IntroductionMITRE ATT&CK is a great resource, but something about it has bothered me since I first heard about it several years ago. It's a minor point, but I wanted to document it in case it confuses anyone else.The MITRE ATT&CK Design and Philosophy document from March 2020 says the following:At a high-level, ATT&CK is a behavioral model that consists of the following core components:• Tactics, denoting short-term, tactical adversary goals during an attack;• Techniques, describing the means by which adversaries achieve tactical goals;• Sub-techniques, describing more specific means by which adversaries achieve tactical goals at a lower level than techniques; and• Documented adversary usage of techniques, their procedures, and other metadata.My concern is with MITRE's definition of "tactics" as "short-term, tactical adversary goals during an attack," which is oddly recursive.The key word in the tactics definition is goals. According to MITRE, "tactics" are "goals."Examples of ATT&CK TacticsATT&CK lists the following as "Enterprise Tactics": MITRE ATT&CK "Tactics," https://attack.mitre.org/tactics/enterprise/Looking at this list, the first 11 items could indeed be seen as goals. The last item, Impact, is not a goal. That item is an artifact of trying to shoehorn more information into the ATT&CK structure. That's not my primary concern though.Military Theory and DefinitionsAs a service academy graduate who had to sit through many lectures on military theory, and who participated in small unit exercises, the idea of tactics as "goals" does not make any sense. MITRE ATT&CK "Tactics," https://attack.mitre.org/tactics/enterprise/Looking at this list, the first 11 items could indeed be seen as goals. The last item, Impact, is not a goal. That item is an artifact of trying to shoehorn more information into the ATT&CK structure. That's not my primary concern though.Military Theory and DefinitionsAs a service academy graduate who had to sit through many lectures on military theory, and who participated in small unit exercises, the idea of tactics as "goals" does not make any sense. |
Guideline | |||
| 2020-10-10 11:30:12 | Greg Rattray Invented the Term Advanced Persistent Threat (lien direct) | 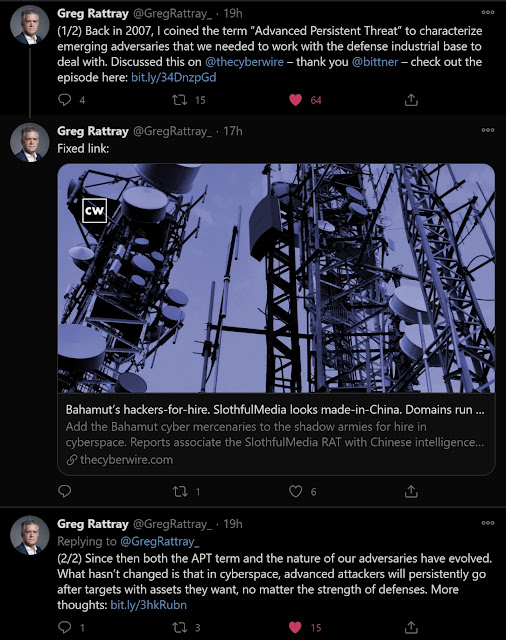 I was so pleased to read this Tweet yesterday from Greg Rattray:"Back in 2007, I coined the term “Advanced Persistent Threat” to characterize emerging adversaries that we needed to work with the defense industrial base to deal with... Since then both the APT term and the nature of our adversaries have evolved. What hasn't changed is that in cyberspace, advanced attackers will persistently go after targets with assets they want, no matter the strength of defenses."BackgroundFirst, some background. Who is Greg Rattray?First, you could call him Colonel or Doctor. I will use Col as that was the last title I used with him, although these days when we chat I call him Greg. Col Rattray served 21 years in the Air Force and also earned his PhD in international security from Tufts University. His thesis formed the content for his 2001 book Strategic Warfare in Cyberspace, which I reviewed in 2002 and rated 4 stars. (Ouch -- I was a bit stingy with the stars back then. I was more of an operator and less of a theorist or historian in those days. Such was my bias I suppose.)Col Rattray is also a 1984 graduate of the Air Force Academy. He studied history and political science there and returned as an assistant professor in the early 1990s. He was one of my instructors when I was a cadet there. (I graduated in 1994 with degrees in history and political science.) Col Rattray then earned a master of public policy degree at Harvard Kennedy School. (I did the same, in 1996.) Do you see a pattern here? He is clearly a role model. Of course, I did not stay in the Air Force as long, earn the same rank, or survive my PhD program!After the Academy, Col Rattray served as commander of the 23rd Information Operations Squadrons on Security Hill in San Antonio, Texas. I was working in the AFCERT at the time. I was so pleased to read this Tweet yesterday from Greg Rattray:"Back in 2007, I coined the term “Advanced Persistent Threat” to characterize emerging adversaries that we needed to work with the defense industrial base to deal with... Since then both the APT term and the nature of our adversaries have evolved. What hasn't changed is that in cyberspace, advanced attackers will persistently go after targets with assets they want, no matter the strength of defenses."BackgroundFirst, some background. Who is Greg Rattray?First, you could call him Colonel or Doctor. I will use Col as that was the last title I used with him, although these days when we chat I call him Greg. Col Rattray served 21 years in the Air Force and also earned his PhD in international security from Tufts University. His thesis formed the content for his 2001 book Strategic Warfare in Cyberspace, which I reviewed in 2002 and rated 4 stars. (Ouch -- I was a bit stingy with the stars back then. I was more of an operator and less of a theorist or historian in those days. Such was my bias I suppose.)Col Rattray is also a 1984 graduate of the Air Force Academy. He studied history and political science there and returned as an assistant professor in the early 1990s. He was one of my instructors when I was a cadet there. (I graduated in 1994 with degrees in history and political science.) Col Rattray then earned a master of public policy degree at Harvard Kennedy School. (I did the same, in 1996.) Do you see a pattern here? He is clearly a role model. Of course, I did not stay in the Air Force as long, earn the same rank, or survive my PhD program!After the Academy, Col Rattray served as commander of the 23rd Information Operations Squadrons on Security Hill in San Antonio, Texas. I was working in the AFCERT at the time. |
Threat Guideline | |||
| 2020-05-04 11:51:25 | New Book! The Best of TaoSecurity Blog, Volume 1 (lien direct) |  I'm very pleased to announce that I've published a new book!It's The Best of TaoSecurity Blog, Volume 1: Milestones, Philosophy and Strategy, Risk, and Advice. It's available now in the Kindle Store, and if you're a member of Kindle Unlimited, it's currently free. I may also publish a print version. If you're interested, please tell me on Twitter. I'm very pleased to announce that I've published a new book!It's The Best of TaoSecurity Blog, Volume 1: Milestones, Philosophy and Strategy, Risk, and Advice. It's available now in the Kindle Store, and if you're a member of Kindle Unlimited, it's currently free. I may also publish a print version. If you're interested, please tell me on Twitter.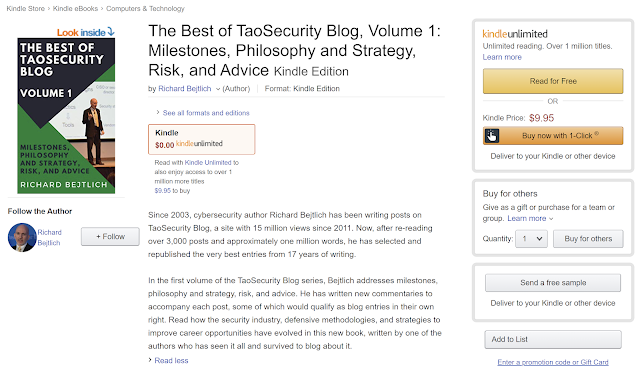 The book lists at 332 pages and is over 83,000 words. I've been working on it since last year, but I've used the time in isolation to carry the first volume over the finish line.The Amazon.com description says:Since 2003, cybersecurity author Richard Bejtlich has been writing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 posts and approximately one million words, he has selected and republished the very best entries from 17 years of writing.In the first volume of the TaoSecurity Blog series, Bejtlich addresses milestones, philosophy and strategy, risk, and advice. Bejtlich shares his thoughts on leadership, the intruder's dilemma, managing burnout, controls versus assessments, insider versus outsider threats, security return on investment, threats versus vulnerabilities, controls and compliance, the post that got him hired at a Fortune 5 company as their first director of incident response, and much more.He has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve career opportunities have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Finally, if you're interested in subsequent volumes, I have two planned. The book lists at 332 pages and is over 83,000 words. I've been working on it since last year, but I've used the time in isolation to carry the first volume over the finish line.The Amazon.com description says:Since 2003, cybersecurity author Richard Bejtlich has been writing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 posts and approximately one million words, he has selected and republished the very best entries from 17 years of writing.In the first volume of the TaoSecurity Blog series, Bejtlich addresses milestones, philosophy and strategy, risk, and advice. Bejtlich shares his thoughts on leadership, the intruder's dilemma, managing burnout, controls versus assessments, insider versus outsider threats, security return on investment, threats versus vulnerabilities, controls and compliance, the post that got him hired at a Fortune 5 company as their first director of incident response, and much more.He has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve career opportunities have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Finally, if you're interested in subsequent volumes, I have two planned. I may also have a few other book projects in the pipeline. I'll have more to say on that in the coming weeks.If you have any questions about the book, let me know. Currently you can see the table of contents via the "Look Inside" function, and ther I may also have a few other book projects in the pipeline. I'll have more to say on that in the coming weeks.If you have any questions about the book, let me know. Currently you can see the table of contents via the "Look Inside" function, and ther |
Guideline | |||
| 2020-03-27 11:15:36 | Skill Levels in Digital Security (lien direct) |  Two posts in one day? These are certainly unusual times.I was thinking about words to describe different skill levels in digital security. Rather than invent something, I decided to review terms that have established meaning. Thanks to Google Books I found this article in a 1922 edition of the Archives of Psychology that mentioned four key terms:The novice is a (person) who has no trade ability whatever, or at least none that could not be paralleled by practically any intelligent (person).An apprentice has acquired some of the elements of the trade but is not sufficiently skilled to be trusted with any important task.The journey(person) is qualified to perform almost any work done by members of the trade.An expert can perform quickly and with superior skill any work done by (people) in the trade.I believe these four categories can apply to some degree to the needs of the digital security profession.At GE-CIRT we had three levels -- event analyst, incident analyst, and incident handler. We did not hire novices, so those three roles map in some ways to apprentice, journeyperson, and expert. One difference with the classical description applies to how we worked with apprentices. We trusted apprentices, or event analysts, with specific tasks. We thought of this work as important, just as every role on a team is important. It may not have been leading an incident response, but without the work of the event and incident analysts, we may not have discovered many incidents!Crucially, we encouraged event analysts, and incident analysts for that matter, to always be looking to exceed the parameters of their assigned duties.However, we stipulated that if a person was working beyond their assigned duties, they had to have their work product reviewed by the next level of analysis. This enabled mentoring among the various groups. It also helped identify people who were candidates for promotion. If a person consistently worked beyond their assigned duties, and eventually reached a near-perfect or perfect ability to do that work, that proved he or she was ready to assume the next level.This ability to access work beyond assigned duties is one reason I have problems with limiting data by role. I think everyone who works in a CIRT should have access to all of the data, assuming there are no classification, privacy, or active investigation constraints.One of my laws is the following:Analysts are good because they have good data. An expert with bad data is helpless. An apprentice with good data has a chance to do good work.I've said it more eloquently elsewhere but this is the main point. For more information on the apprenticeship model, this article might be useful.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Two posts in one day? These are certainly unusual times.I was thinking about words to describe different skill levels in digital security. Rather than invent something, I decided to review terms that have established meaning. Thanks to Google Books I found this article in a 1922 edition of the Archives of Psychology that mentioned four key terms:The novice is a (person) who has no trade ability whatever, or at least none that could not be paralleled by practically any intelligent (person).An apprentice has acquired some of the elements of the trade but is not sufficiently skilled to be trusted with any important task.The journey(person) is qualified to perform almost any work done by members of the trade.An expert can perform quickly and with superior skill any work done by (people) in the trade.I believe these four categories can apply to some degree to the needs of the digital security profession.At GE-CIRT we had three levels -- event analyst, incident analyst, and incident handler. We did not hire novices, so those three roles map in some ways to apprentice, journeyperson, and expert. One difference with the classical description applies to how we worked with apprentices. We trusted apprentices, or event analysts, with specific tasks. We thought of this work as important, just as every role on a team is important. It may not have been leading an incident response, but without the work of the event and incident analysts, we may not have discovered many incidents!Crucially, we encouraged event analysts, and incident analysts for that matter, to always be looking to exceed the parameters of their assigned duties.However, we stipulated that if a person was working beyond their assigned duties, they had to have their work product reviewed by the next level of analysis. This enabled mentoring among the various groups. It also helped identify people who were candidates for promotion. If a person consistently worked beyond their assigned duties, and eventually reached a near-perfect or perfect ability to do that work, that proved he or she was ready to assume the next level.This ability to access work beyond assigned duties is one reason I have problems with limiting data by role. I think everyone who works in a CIRT should have access to all of the data, assuming there are no classification, privacy, or active investigation constraints.One of my laws is the following:Analysts are good because they have good data. An expert with bad data is helpless. An apprentice with good data has a chance to do good work.I've said it more eloquently elsewhere but this is the main point. For more information on the apprenticeship model, this article might be useful.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
Guideline | |||
| 2019-09-13 11:00:00 | Five Thoughts on the Internet Freedom League (lien direct) |  In the September/October issue of Foreign Affairs magazine, Richard Clarke and Rob Knake published an article titled "The Internet Freedom League: How to Push Back Against the Authoritarian Assault on the Web," based on their recent book The Fifth Domain. The article proposes the following:The United States and its allies and partners should stop worrying about the risk of authoritarians splitting the Internet. Instead, they should split it themselves, by creating a digital bloc within which data, services, and products can flow freely, excluding countries that do not respect freedom of expression or privacy rights, engage in disruptive activity, or provide safe havens to cybercriminals...The league would not raise a digital Iron Curtain; at least initially, most Internet traffic would still flow between members and nonmembers, and the league would primarily block companies and organizations that aid and abet cybercrime, rather than entire countries. Governments that fundamentally accept the idea of an open, tolerant, and democratic Internet but that struggle to live up to such a vision would have an incentive to improve their enforcement efforts in order join the league and secure connectivity for their companies and citizens. Of course, authoritarian regimes in China, Russia, and elsewhere will probably continue to reject that vision. Instead of begging and pleading with such governments to play nice, from now on, the United States and its allies should lay down the law: follow the rules, or get cut off.My initial reaction to this line of thought was not encouraging. Rather than continue exchanging Twitter messages, Rob and I had a very pleasant phone conversation to help each other understand our points of view. Rob asked me to document my thoughts in a blog post, so this is the result.Rob explained that the main goal of the IFL is to create leverage to influence those who do not implement an open, tolerant, and democratic Internet (summarized below as OTDI). I agree that leverage is certainly lacking, but I wondered if the IFL would accomplish that goal. My reservations included the following.1. Many countries that currently reject the OTDI might only be too happy to be cut off from the Western Internet. These countries do not want their citizens accessing the OTDI. Currently dissidents and others seeking news beyond their local borders must often use virtual private networks and other means to access the OTDI. If the IFL went live, those dissidents and others would be cut off, thanks to their government's resistance to OTDI principles.2. Elites in anti-OTDI countries would still find ways to access the Western Internet, either for personal, business, political, military, or intelligence reasons. The common person would be mostly likely to suffer.3. Segregating the OTDI would increase the incentives for "network traffic smuggling," whereby anti-OTDI elites would compromise, bribe, or otherwise corrupt Western Internet resources to establish surreptitious methods to access the OTDI. This would increase the intrusion pressure upon o In the September/October issue of Foreign Affairs magazine, Richard Clarke and Rob Knake published an article titled "The Internet Freedom League: How to Push Back Against the Authoritarian Assault on the Web," based on their recent book The Fifth Domain. The article proposes the following:The United States and its allies and partners should stop worrying about the risk of authoritarians splitting the Internet. Instead, they should split it themselves, by creating a digital bloc within which data, services, and products can flow freely, excluding countries that do not respect freedom of expression or privacy rights, engage in disruptive activity, or provide safe havens to cybercriminals...The league would not raise a digital Iron Curtain; at least initially, most Internet traffic would still flow between members and nonmembers, and the league would primarily block companies and organizations that aid and abet cybercrime, rather than entire countries. Governments that fundamentally accept the idea of an open, tolerant, and democratic Internet but that struggle to live up to such a vision would have an incentive to improve their enforcement efforts in order join the league and secure connectivity for their companies and citizens. Of course, authoritarian regimes in China, Russia, and elsewhere will probably continue to reject that vision. Instead of begging and pleading with such governments to play nice, from now on, the United States and its allies should lay down the law: follow the rules, or get cut off.My initial reaction to this line of thought was not encouraging. Rather than continue exchanging Twitter messages, Rob and I had a very pleasant phone conversation to help each other understand our points of view. Rob asked me to document my thoughts in a blog post, so this is the result.Rob explained that the main goal of the IFL is to create leverage to influence those who do not implement an open, tolerant, and democratic Internet (summarized below as OTDI). I agree that leverage is certainly lacking, but I wondered if the IFL would accomplish that goal. My reservations included the following.1. Many countries that currently reject the OTDI might only be too happy to be cut off from the Western Internet. These countries do not want their citizens accessing the OTDI. Currently dissidents and others seeking news beyond their local borders must often use virtual private networks and other means to access the OTDI. If the IFL went live, those dissidents and others would be cut off, thanks to their government's resistance to OTDI principles.2. Elites in anti-OTDI countries would still find ways to access the Western Internet, either for personal, business, political, military, or intelligence reasons. The common person would be mostly likely to suffer.3. Segregating the OTDI would increase the incentives for "network traffic smuggling," whereby anti-OTDI elites would compromise, bribe, or otherwise corrupt Western Internet resources to establish surreptitious methods to access the OTDI. This would increase the intrusion pressure upon o |
Guideline | |||
| 2019-07-01 08:00:07 | Reference: TaoSecurity News (lien direct) | I started speaking publicly about digital security in 2000. I used to provide this information on my Web site, but since I don't keep that page up-to-date anymore, I decided to publish it here. 2017 Mr. Bejtlich led a podcast titled Threat Hunting: Past, Present, and Future, in early July 2017. He interviewed four of the original six GE-CIRT incident handlers. The audio is posted on YouTube. Thank you to Sqrrl for making the reunion possible. Mr. Bejtlich's latest book was inducted into the Cybersecurity Canon. Mr. Bejtlich is doing limited security consulting. See this blog post for details. 2016 Mr. Bejtlich organized and hosted the Management track (now "Executive track") at the 7th annual Mandiant MIRCon (now "FireEye Cyber Defense Summit") on 29-30 November 2016. Mr. Bejtlich delivered the keynote to the 2016 Air Force Senior Leaders Orientation Conference at Joint Base Andrews on 29 July 2016. Mr. Bejtlich delivered the keynote to the FireEye Cyber Defense Live Tokyo event in Tokyo on 12 July 2016. Mr. Bejtlich delivered the keynote to the New Zealand Cyber Security Summit in Auckland on 6 May 2016. Mr. Bejtlich delivered the keynote to the Lexpo Summit in Amsterdam on 21 April 2016. Video posted here. Mr. Bejtlich discussed cyber security campaigns at the 2016 War Studies Cumberland Lodge Conference near London on 30 March 2016. Mr. Bejtlich offered a guest lecture to the Wilson Center Congressional Cybersecurity Lab on 5 February 2016. Mr. Bejtlich delivered the keynote to the SANS Cyber Threat Intelligence Summit on 4 February 2016. Slides and video available. 2015 Mr. Bejtlich spoke on a panel at the DefenseOne Summit on 2 November 2015. Mr. Bejtlich spoke on a panel at the AEI Internet Strategy event on 27 October 2015. Mr. Bejtlich organized and hosted the Management track at the 6th annual Mandiant MIRCon on 13-14 October 2015. Mr. Bejtlich testified to the House Foreign Affairs Committee on 7 October 2015. Mr. Bejtlich testified to the House Armed Services Committee on 30 September 2015. Mr. Bejtlich delivered a keynote at the 2015 Army Cyber Institute Cyber Talks on 22 September 2015 in Washington, DC. Mr. Bejtlich delivered a keynote at the 2015 Security Onion Conference on 11 September 2015 in Augusta, GA. Mr. Bejtlich delivered a keynote at the 2015 World Services Group Conference on 10 S | Guideline | APT 1 | ||
| 2019-07-01 08:00:04 | Reference: TaoSecurity Research (lien direct) | I started publishing my thoughts and findings on digital security in 1999. I used to provide this information on my Web site, but since I don't keep that page up-to-date anymore, I decided to publish it here.2015 and later: Please visit Academia.edu for Mr. Bejtlich's most recent research.2014 and earlier: Seven Tips for Small Business Security, in the Huffington Post, 18 June 2014Strategy, Not Speed: What Today's Digital Defenders Must Learn From Cybersecurity's Early Thinkers, for the Brookings Institution, 7 May 2014What Federal Cyber Breach Notifications Really Mean for Business, for the Brookings Institution, 25 March 2014Don't Underestimate Cyber Spies: How Virtual Espionage Can Lead to Actual Destruction in Foreign Affairs, 2 May 2013Become a Hunter in the targeted-threat-centric Information Security Magzine, July-August 2011 (.pdf) Directions in Incident Detection and Response (.pdf) in the January/February 2011 issue of IEEE Security and Privacy magazineUnderstanding the Advanced Persistent Threat in Information Security Magazine, July 2010Traffic Talk issues 1, 2, 3, 4, 5, 6, 7, 8, 9, 10Snort Report issues 1, 2, 3, 4, 5, 6, | Guideline | |||
| 2019-07-01 08:00:01 | Reference: TaoSecurity Press (lien direct) | I started appearing in media reports in 2000. I used to provide this information on my Web site, but since I don't keep that page up-to-date anymore, I decided to publish it here. As of 2017, Mr. Bejtlich generally denies press inquiries on cybersecurity matters, including those on background.2016Mr. Bejtlich was cited in the Forture story Meet the US's First Ever Cyber Chief, published 8 September 2016.Mr. Bejtlich was interviewed for the NPR story Cybersecurity: Who's Vulnerable To Attack?, aired 30 July 2016.Mr. Bejtlich was interviewed for the Washington Post story It's not just the DNC; we all send emails we probably shouldn't, published 25 July 2016.Mr. Bejtlich was interviewed for the New Scientist story NATO says the internet is now a war zone – what does that mean?, published 22 June 2016.Mr. Bejtlich was interviewed for the Military Times story The Pentagon's controversial plan to hire military leaders off the street, published 19 June 2016.Mr. Bejtlich was interviewed for the Idealog story Idealog talks with a cyber-war expert, published 6 May 2016.Mr. Bejtlich was cited in the New Zealand Herald story Cyber-attacks part of doing business with China - experts, published 5 May 2016.Mr. Bejtlich was cited in the Christian Science Monitor story Iran hacking indictment highlights US naming and shaming strategy, published 30 March 2016.Mr. Bejtlich was cited in the Financial Times story Defence groups take aim at cyber security, published 28 March 2016.Mr. Bejtlich was interviewed for the Security Management story A Chinese New Year, published 4 January 2016.2015Mr. Bejtlich was cited in the AP story US Advised to Examine "Hack Back" Options against China, published 17 November 2015.Mr. Bejtlich was cited in the Reuters story Data from US agency cyber breach not on black market - researcher, published 2 November 2015.Mr. Bejtlich was cited in the NextGov story Creative, Audacious or Destructive: The Different Personalities of Nation-State Hackers, published 2 November 2015.Mr. Bejtlich was cited in the Baltimore Sun story As more devices go online, hackers hunt for vulnerabilities, published 24 October 2015.Mr. Bejtlich was cited in the Atlantic story Can Campus Networks Ever Be Secure?, published 12 October 2015.Mr. Bejtlich was cited in the Info Security story | Guideline | Yahoo | ||
| 2018-12-31 17:46:00 | Notes on Self-Publishing a Book (lien direct) |  In this post I would like to share a few thoughts on self-publishing a book, in case anyone is considering that option.As I mentioned in my post on burnout, one of my goals was to publish a book on a subject other than cyber security. A friend from my Krav Maga school, Anna Wonsley, learned that I had published several books, and asked if we might collaborate on a book about stretching. The timing was right, so I agreed.I published my first book with Pearson and Addison-Wesley in 2004, and my last with No Starch in 2013. 14 years is an eternity in the publishing world, and even in the last 5 years the economics and structure of book publishing have changed quite a bit.To better understand the changes, I had dinner with one of the finest technical authors around, Michael W. Lucas. We met prior to my interest in this book, because I had wondered about publishing books on my own. MWL started in traditional publishing like me, but has since become a full-time author and independent publisher. He explained the pros and cons of going it alone, which I carefully considered.By the end of 2017, Anna and I were ready to begin work on the book. I believe our first "commits" occurred in December 2017.For this stretching book project, I knew my strengths included organization, project management, writing to express another person's message, editing, and access to a skilled lead photographer. I learned that my co-author's strengths included subject matter expertise, a willingness to be photographed for the book's many pictures, and friends who would also be willing to be photographed.None of us was very familiar with the process of transforming a raw manuscript and photos into a finished product. When I had published with Pearson and No Starch, they took care of that process, as well as copy-editing. In this post I would like to share a few thoughts on self-publishing a book, in case anyone is considering that option.As I mentioned in my post on burnout, one of my goals was to publish a book on a subject other than cyber security. A friend from my Krav Maga school, Anna Wonsley, learned that I had published several books, and asked if we might collaborate on a book about stretching. The timing was right, so I agreed.I published my first book with Pearson and Addison-Wesley in 2004, and my last with No Starch in 2013. 14 years is an eternity in the publishing world, and even in the last 5 years the economics and structure of book publishing have changed quite a bit.To better understand the changes, I had dinner with one of the finest technical authors around, Michael W. Lucas. We met prior to my interest in this book, because I had wondered about publishing books on my own. MWL started in traditional publishing like me, but has since become a full-time author and independent publisher. He explained the pros and cons of going it alone, which I carefully considered.By the end of 2017, Anna and I were ready to begin work on the book. I believe our first "commits" occurred in December 2017.For this stretching book project, I knew my strengths included organization, project management, writing to express another person's message, editing, and access to a skilled lead photographer. I learned that my co-author's strengths included subject matter expertise, a willingness to be photographed for the book's many pictures, and friends who would also be willing to be photographed.None of us was very familiar with the process of transforming a raw manuscript and photos into a finished product. When I had published with Pearson and No Starch, they took care of that process, as well as copy-editing. Beyond turning manuscript and photos into a book, I also had to identify a publication platform. Early on we decided to self-publish using one of the many newer companies offering that service. We wanted a company that could get our book into Amazon, and possibly physical book stores as well. We did not want to try working with a traditional publisher, as we felt that we could manage most aspects of the publishing process ourselves, and augment with specialized help where needed.After a lot of research we chose Blurb. One of the most attractive aspects of Blurb was their expert ecosystem. We decided that we would hire one of these experts to handle th Beyond turning manuscript and photos into a book, I also had to identify a publication platform. Early on we decided to self-publish using one of the many newer companies offering that service. We wanted a company that could get our book into Amazon, and possibly physical book stores as well. We did not want to try working with a traditional publisher, as we felt that we could manage most aspects of the publishing process ourselves, and augment with specialized help where needed.After a lot of research we chose Blurb. One of the most attractive aspects of Blurb was their expert ecosystem. We decided that we would hire one of these experts to handle th |
Guideline | |||
| 2018-11-25 15:48:54 | The Origin of the Term Indicators of Compromise (IOCs) (lien direct) |  I am an historian. I practice digital security, but I earned a bachelor's of science degree in history from the United States Air Force Academy. (1)Historians create products by analyzing artifacts, among which the most significant is the written word.In my last post, I talked about IOCs, or indicators of compromise. Do you know the origin of the term? I thought I did, but I wanted to rely on my historian's methodology to invalidate or confirm my understanding.I became aware of the term "indicator" as an element of indications and warning (I&W), when I attended Air Force Intelligence Officer's school in 1996-1997. I will return to this shortly, but I did not encounter the term "indicator" in a digital security context until I encountered the work of Kevin Mandia.In August 2001, shortly after its publication, I read Incident Response: Investigating Computer Crime, by Kevin Mandia, Chris Prosise, and Matt Pepe (Osborne/McGraw-Hill). I was so impressed by this work that I managed to secure a job with their company, Foundstone, by April 2002. I joined the Foundstone incident response team, which was led by Kevin and consisted of Matt Pepe, Keith Jones, Julie Darmstadt, and me.I Tweeted earlier today that Kevin invented the term "indicator" (in the IR context) in that 2001 edition, but a quick review of the hard copy in my library does not show its usage, at least not prominently. I believe we were using the term in the office but that it had not appeared in the 2001 book. Documentation would seem to confirm that, as Kevin was working on the second edition of the IR book (to which I contributed), and that version, published in 2003, features the term "indicator" in multiple locations.In fact, the earliest use of the term "indicators of compromise," appearing in print in a digital security context, appears on page 280 in Incident Response & Computer Forensics, 2nd Edition. I am an historian. I practice digital security, but I earned a bachelor's of science degree in history from the United States Air Force Academy. (1)Historians create products by analyzing artifacts, among which the most significant is the written word.In my last post, I talked about IOCs, or indicators of compromise. Do you know the origin of the term? I thought I did, but I wanted to rely on my historian's methodology to invalidate or confirm my understanding.I became aware of the term "indicator" as an element of indications and warning (I&W), when I attended Air Force Intelligence Officer's school in 1996-1997. I will return to this shortly, but I did not encounter the term "indicator" in a digital security context until I encountered the work of Kevin Mandia.In August 2001, shortly after its publication, I read Incident Response: Investigating Computer Crime, by Kevin Mandia, Chris Prosise, and Matt Pepe (Osborne/McGraw-Hill). I was so impressed by this work that I managed to secure a job with their company, Foundstone, by April 2002. I joined the Foundstone incident response team, which was led by Kevin and consisted of Matt Pepe, Keith Jones, Julie Darmstadt, and me.I Tweeted earlier today that Kevin invented the term "indicator" (in the IR context) in that 2001 edition, but a quick review of the hard copy in my library does not show its usage, at least not prominently. I believe we were using the term in the office but that it had not appeared in the 2001 book. Documentation would seem to confirm that, as Kevin was working on the second edition of the IR book (to which I contributed), and that version, published in 2003, features the term "indicator" in multiple locations.In fact, the earliest use of the term "indicators of compromise," appearing in print in a digital security context, appears on page 280 in Incident Response & Computer Forensics, 2nd Edition. From other uses of the term "indicators" in that IR book, you can observe that IOC wasn't a formal, independent concept at this point, in 2003. In the same excerpt above you see "indicators of attack" mentioned.The first citation of the term "indicators" in the 2003 book shows it is meant as an investigative lead or tip: From other uses of the term "indicators" in that IR book, you can observe that IOC wasn't a formal, independent concept at this point, in 2003. In the same excerpt above you see "indicators of attack" mentioned.The first citation of the term "indicators" in the 2003 book shows it is meant as an investigative lead or tip: |
Malware Tool Guideline | |||
| 2018-05-15 14:40:48 | Bejtlich Joining Splunk (lien direct) | Guideline | ||||
| 2018-01-16 12:31:57 | Addressing Innumeracy in Reporting (lien direct) | 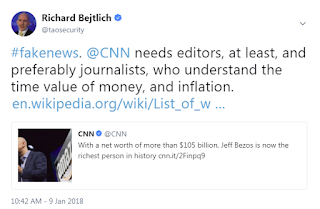 Anyone involved in cybersecurity reporting needs a strong sense of numeracy, or mathematical literacy. I see two sorts of examples of innumeracy repeatedly in the media.The first involves the time value of money. Recently CNN claimed Amazon CEO Jeff Bezos was the "richest person in history" and Recode said Bezos was "now worth more than Bill Gates ever was." Thankfully both Richard Steinnon and Noah Kirsch recognized the foolishness of these reports, correctly noting that Bezos would only rank number 17 on a list where wealth was adjusted for inflation.This failure to recognize the time value of money is pervasive. Just today I heard the host of a podcast claim that the 1998 Jackie Chan movie Rush Hour was "the top grossing martial arts film of all time." According to Box Office Mojo, Rush Hour earned $244,386,864 worldwide. Adjusting for inflation, in 2017 dollars that's $367,509,865.67 -- impressive!For comparison, I researched the box office returns for Bruce Lee's Enter the Dragon. Box Office Mojo lacked data, but I found a 2017 article stating his 1973 movie earned "$25 million in the U.S. and $90 million worldwide, excluding Hong Kong." If I adjust the worldwide figure of $90 million for inflation, in 2017 dollars that's $496,864,864.86 -- making Enter the Dragon easily more successful than Rush Hour.If you're wondering about Crouching Tiger, Hidden Dragon, that 2000 movie earned $213,525,736 worldwide. That movie earned less than Rush Hour, and arrived two years later, so it's not worth doing the inflation math.The take-away is that any time you are comparing dollars from different time periods, you must adjust for inflation to have your comparisons have any meaning whatsoever. Anyone involved in cybersecurity reporting needs a strong sense of numeracy, or mathematical literacy. I see two sorts of examples of innumeracy repeatedly in the media.The first involves the time value of money. Recently CNN claimed Amazon CEO Jeff Bezos was the "richest person in history" and Recode said Bezos was "now worth more than Bill Gates ever was." Thankfully both Richard Steinnon and Noah Kirsch recognized the foolishness of these reports, correctly noting that Bezos would only rank number 17 on a list where wealth was adjusted for inflation.This failure to recognize the time value of money is pervasive. Just today I heard the host of a podcast claim that the 1998 Jackie Chan movie Rush Hour was "the top grossing martial arts film of all time." According to Box Office Mojo, Rush Hour earned $244,386,864 worldwide. Adjusting for inflation, in 2017 dollars that's $367,509,865.67 -- impressive!For comparison, I researched the box office returns for Bruce Lee's Enter the Dragon. Box Office Mojo lacked data, but I found a 2017 article stating his 1973 movie earned "$25 million in the U.S. and $90 million worldwide, excluding Hong Kong." If I adjust the worldwide figure of $90 million for inflation, in 2017 dollars that's $496,864,864.86 -- making Enter the Dragon easily more successful than Rush Hour.If you're wondering about Crouching Tiger, Hidden Dragon, that 2000 movie earned $213,525,736 worldwide. That movie earned less than Rush Hour, and arrived two years later, so it's not worth doing the inflation math.The take-away is that any time you are comparing dollars from different time periods, you must adjust for inflation to have your comparisons have any meaning whatsoever. Chart by @CanadianFlagsThe second sort of innumeracy I'd like to highlight today also involves money, but in a slightly different way. This involves changes in values over time.For example, a company may grow revenue from 2015 to 2016, with 2015 revenue being $100,000 and 2016 being $200,000. That's a 100% gain.If the company grows another $100,000 from 2016 to 2017, from $200,000 to $300,000, the growth rate has declined to 50%. To have maintained a 100% growth rate, the comp Chart by @CanadianFlagsThe second sort of innumeracy I'd like to highlight today also involves money, but in a slightly different way. This involves changes in values over time.For example, a company may grow revenue from 2015 to 2016, with 2015 revenue being $100,000 and 2016 being $200,000. That's a 100% gain.If the company grows another $100,000 from 2016 to 2017, from $200,000 to $300,000, the growth rate has declined to 50%. To have maintained a 100% growth rate, the comp |
Guideline | |||
| 2017-03-23 10:26:11 | Five Reasons I Want China Running Its Own Software (lien direct) |  Periodically I read about efforts by China, or Russia, or North Korea, or other countries to replace American software with indigenous or semi-indigenous alternatives. I then reply via Twitter that I love the idea, with a short reason why. This post will list the top five reasons why I want China and other likely targets of American foreign intelligence collection to run their own software.1. Many (most?) non-US software companies write lousy code. The US is by no means perfect, but our developers and processes generally appear to be superior to foreign indigenous efforts. Cisco vs Huawei is a good example. Cisco has plenty of problems, but it has processes in place to manage them, plus secure code development practices. Lousy indigenous code means it is easier for American intelligence agencies to penetrate foreign targets. (An example of a foreign country that excels in writing code is Israel, but thankfully it is not the same sort of priority target like China, Russia, or North Korea.)2. Many (most?) non-US enterprises are 5-10 years behind US security practices. Even if a foreign target runs decent native code, the IT processes maintaining that code are lagging compared to American counterparts. Again, the US has not solved this problem by any stretch of the imagination. However, relatively speaking, American inventory management, patch management, and security operations have the edge over foreign intelligence targets. Because non-US enterprises running indigenous code will not necessarily be able to benefit from American expertise (as they might if they were running American code), these deficiencies will make them easier targets for foreign exploitation.3. Foreign targets running foreign code is win-win for American intel and enterprises. The current vulnerability equities process (VEP) puts American intelligence agencies in a quandary. The IC develops a zero-day exploit for a vulnerability, say for use against Cisco routers. American and Chinese organizations use Cisco routers. Should the IC sit on the vulnerability in order to maintain access to foreign targets, or should it release the vulnerability to Cisco to enable patching and thereby protect American and foreign systems?This dilemma disappears in a world where foreign targets run indigenous software. If the IC identifies a vulnerability in Cisco software, and the majority of its targets run non-Cisco software, then the IC is more likely (or should be pushed to be more likely) to assist with patching the vulnerable software. Meanwhile, the IC continues to exploit Huawei or other products at its leisure.4. Writing and running indigenous code is the fastest way to improve. When foreign countries essentially outsource their IT to vendors, they become program managers. They lose or never develop any ability to write and run quality software. Writing and running your own code will enroll foreign organizations in the security school of hard knocks. American intel will have a field day for 3-5 years against these targets, as they flail around in a perpetual state of compromise. However, if they devote the proper native resources and attention, they will learn from their mistakes. They will write and run better software. Now, this means they will become harder targets for American intel, but American intel will retain the advantage of point 3.5. Trustworthy indigenous code will promote international stability. Countries like China feel especially vulnerable to American exploitation. They have eve Periodically I read about efforts by China, or Russia, or North Korea, or other countries to replace American software with indigenous or semi-indigenous alternatives. I then reply via Twitter that I love the idea, with a short reason why. This post will list the top five reasons why I want China and other likely targets of American foreign intelligence collection to run their own software.1. Many (most?) non-US software companies write lousy code. The US is by no means perfect, but our developers and processes generally appear to be superior to foreign indigenous efforts. Cisco vs Huawei is a good example. Cisco has plenty of problems, but it has processes in place to manage them, plus secure code development practices. Lousy indigenous code means it is easier for American intelligence agencies to penetrate foreign targets. (An example of a foreign country that excels in writing code is Israel, but thankfully it is not the same sort of priority target like China, Russia, or North Korea.)2. Many (most?) non-US enterprises are 5-10 years behind US security practices. Even if a foreign target runs decent native code, the IT processes maintaining that code are lagging compared to American counterparts. Again, the US has not solved this problem by any stretch of the imagination. However, relatively speaking, American inventory management, patch management, and security operations have the edge over foreign intelligence targets. Because non-US enterprises running indigenous code will not necessarily be able to benefit from American expertise (as they might if they were running American code), these deficiencies will make them easier targets for foreign exploitation.3. Foreign targets running foreign code is win-win for American intel and enterprises. The current vulnerability equities process (VEP) puts American intelligence agencies in a quandary. The IC develops a zero-day exploit for a vulnerability, say for use against Cisco routers. American and Chinese organizations use Cisco routers. Should the IC sit on the vulnerability in order to maintain access to foreign targets, or should it release the vulnerability to Cisco to enable patching and thereby protect American and foreign systems?This dilemma disappears in a world where foreign targets run indigenous software. If the IC identifies a vulnerability in Cisco software, and the majority of its targets run non-Cisco software, then the IC is more likely (or should be pushed to be more likely) to assist with patching the vulnerable software. Meanwhile, the IC continues to exploit Huawei or other products at its leisure.4. Writing and running indigenous code is the fastest way to improve. When foreign countries essentially outsource their IT to vendors, they become program managers. They lose or never develop any ability to write and run quality software. Writing and running your own code will enroll foreign organizations in the security school of hard knocks. American intel will have a field day for 3-5 years against these targets, as they flail around in a perpetual state of compromise. However, if they devote the proper native resources and attention, they will learn from their mistakes. They will write and run better software. Now, this means they will become harder targets for American intel, but American intel will retain the advantage of point 3.5. Trustworthy indigenous code will promote international stability. Countries like China feel especially vulnerable to American exploitation. They have eve |
Guideline | |||
| 2017-02-12 07:59:45 | Guest Post: Bamm Visscher on Detection (lien direct) |  Yesterday my friend Bamm Visscher published a series of Tweets on detection. I thought readers might like to digest it as a lightly edited blog post. Here, then, is the first ever (as far as I can remember) guest post on TaoSecurity Blog. Enjoy.When you receive new [threat] intel and apply it in your detection environment, keep in mind all three analysis opportunities: RealTime, Batch, and Hunting.If your initial intelligence analysis produces high context and quality details, it's a ripe candidate for RealTime detection.If analysts can quickly and accurately process events generated by the [RealTime] signature, it's a good sign the indicator should be part of RealTime detection. If an analyst struggles to determine if a [RealTime alert] has detected malicious activity, it's likely NOT appropriate for RealTime detection.If [the threat] intelligence contains limited context and/or details, try leveraging Batch Analysis with scheduled data reports as a better detection technique. Use Batch Analysis to develop better context (both positive and negative hits) to identify better signatures for RealTime detection.Hunting is the soft science of detection, and best done with a team of diverse skills. Intelligence, content development, and detection should all work together. Don't fear getting skunked on your hunting trips. Keep investing time. The rewards are accumulative. Be sure to pass Hunting rewards into Batch Analysis and RealTime detection operations in the form of improved context.The biggest mistake organizations make is not placing emphasis outside of RealTime detection, and "shoe-horning" [threat] intelligence into RealTime operations. So called "Atomic Indicators" tend to be the biggest violator of shoe-horning. Atomic indicators are easy to script into signature driven detection devices, but leave an analyst wondering what he is looking at and for.Do not underestimate the NEGATIVE impact of GOOD [threat] intelligence inappropriately placed into RealTime operations! Mountains of indiscernible events will lead to analyst fatigue and increase the risk of good analyst missing a real incident.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Yesterday my friend Bamm Visscher published a series of Tweets on detection. I thought readers might like to digest it as a lightly edited blog post. Here, then, is the first ever (as far as I can remember) guest post on TaoSecurity Blog. Enjoy.When you receive new [threat] intel and apply it in your detection environment, keep in mind all three analysis opportunities: RealTime, Batch, and Hunting.If your initial intelligence analysis produces high context and quality details, it's a ripe candidate for RealTime detection.If analysts can quickly and accurately process events generated by the [RealTime] signature, it's a good sign the indicator should be part of RealTime detection. If an analyst struggles to determine if a [RealTime alert] has detected malicious activity, it's likely NOT appropriate for RealTime detection.If [the threat] intelligence contains limited context and/or details, try leveraging Batch Analysis with scheduled data reports as a better detection technique. Use Batch Analysis to develop better context (both positive and negative hits) to identify better signatures for RealTime detection.Hunting is the soft science of detection, and best done with a team of diverse skills. Intelligence, content development, and detection should all work together. Don't fear getting skunked on your hunting trips. Keep investing time. The rewards are accumulative. Be sure to pass Hunting rewards into Batch Analysis and RealTime detection operations in the form of improved context.The biggest mistake organizations make is not placing emphasis outside of RealTime detection, and "shoe-horning" [threat] intelligence into RealTime operations. So called "Atomic Indicators" tend to be the biggest violator of shoe-horning. Atomic indicators are easy to script into signature driven detection devices, but leave an analyst wondering what he is looking at and for.Do not underestimate the NEGATIVE impact of GOOD [threat] intelligence inappropriately placed into RealTime operations! Mountains of indiscernible events will lead to analyst fatigue and increase the risk of good analyst missing a real incident.Copyright 2003-2016 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
Guideline | |||
| 2017-02-09 10:36:49 | Bejtlich Books Explained (lien direct) | A reader asked me to explain the differences between two of my books. I decided to write a public response.If you visit the TaoSecurity Books page, you will see two different types of books. The first type involves books which list me as author or co-author. The second involves books to which I have contributed a chapter, section, or foreword.This post will only discuss books which list me as author or co-author. In July 2004 I published The Tao of Network Security Monitoring: Beyond Intrusion Detection. This book was the result of everything I had learned since 1997-98 regarding detecting and responding to intruders, primarily using network-centric means. It is the most complete examination of NSM philosophy available. I am particularly happy with the NSM history appendix. It cites and summarizes influential computer security papers over the four decade history of NSM to that point.The main problem with the Tao is that certain details of specific software versions are very outdated. Established software like Tcpdump, Argus, and Sguil function much the same way, and the core NSM data types remain timeless. You would not be able to use the Bro chapter with modern Bro versions, for example. Still, I recommend anyone serious about NSM read the Tao.The introduction describes the Tao using these words:Part I offers an introduction to Network Security Monitoring, an operational framework for the collection, analysis, and escalation of indications and warnings (I&W) to detect and respond to intrusions. Part I begins with an analysis of the terms and theory held by NSM practitioners. The first chapter discusses the security process and defines words like security, risk, and threat. It also makes assumptions about the intruder and his prey that set the stage for NSM operations. The second chapter addresses NSM directly, explaining why NSM is not implemented by modern NIDS' alone. The third chapter focuses on deployment considerations, such as how to access traffic using hubs, taps, SPAN ports, or inline devices. Part II begins an exploration of the NSM “product, process, people†triad. Chapter 4 is a case study called the “reference intrusion model.†This is an incident explained from the point of view of an omniscient observer. During this intrusion, the victim collected full content data in two locations. We will use those two trace files while explaining the tools discussed in Part II. Following the reference intrusion model, I devote chapters to each of the four types of data which must be collected to perform network security monitoring – full content, session, statistical, and alert data. Each chapter describes open source tools tested on the FreeBSD operating system and available on other UNIX derivatives. Part II also includes a look at tools to ma In July 2004 I published The Tao of Network Security Monitoring: Beyond Intrusion Detection. This book was the result of everything I had learned since 1997-98 regarding detecting and responding to intruders, primarily using network-centric means. It is the most complete examination of NSM philosophy available. I am particularly happy with the NSM history appendix. It cites and summarizes influential computer security papers over the four decade history of NSM to that point.The main problem with the Tao is that certain details of specific software versions are very outdated. Established software like Tcpdump, Argus, and Sguil function much the same way, and the core NSM data types remain timeless. You would not be able to use the Bro chapter with modern Bro versions, for example. Still, I recommend anyone serious about NSM read the Tao.The introduction describes the Tao using these words:Part I offers an introduction to Network Security Monitoring, an operational framework for the collection, analysis, and escalation of indications and warnings (I&W) to detect and respond to intrusions. Part I begins with an analysis of the terms and theory held by NSM practitioners. The first chapter discusses the security process and defines words like security, risk, and threat. It also makes assumptions about the intruder and his prey that set the stage for NSM operations. The second chapter addresses NSM directly, explaining why NSM is not implemented by modern NIDS' alone. The third chapter focuses on deployment considerations, such as how to access traffic using hubs, taps, SPAN ports, or inline devices. Part II begins an exploration of the NSM “product, process, people†triad. Chapter 4 is a case study called the “reference intrusion model.†This is an incident explained from the point of view of an omniscient observer. During this intrusion, the victim collected full content data in two locations. We will use those two trace files while explaining the tools discussed in Part II. Following the reference intrusion model, I devote chapters to each of the four types of data which must be collected to perform network security monitoring – full content, session, statistical, and alert data. Each chapter describes open source tools tested on the FreeBSD operating system and available on other UNIX derivatives. Part II also includes a look at tools to ma |
Guideline |
1
We have: 18 articles.
We have: 18 articles.
To see everything:
Our RSS (filtrered)
