What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2025-01-21 21:15:18 | DONOT Group Deploys Malicious Android Apps in India (lien direct) | The advanced persistent threat (APT) group is likely India-based and targeting individuals with connections to the country\'s intelligence community.
The advanced persistent threat (APT) group is likely India-based and targeting individuals with connections to the country\'s intelligence community. |
Threat Mobile | ★★★ | ||
| 2025-01-21 17:33:45 | The US Treasury Attack: Key Events and Security Implications (lien direct) | There’s a dark joke in cybersecurity: each year ends with an unwelcome holiday surprise-a major security incident. This timing isn’t random. Threat actors target this timing, knowing security teams operate with skeleton crews that impact...
There’s a dark joke in cybersecurity: each year ends with an unwelcome holiday surprise-a major security incident. This timing isn’t random. Threat actors target this timing, knowing security teams operate with skeleton crews that impact... |
Threat | ★★★ | ||
| 2025-01-21 17:00:00 | New Mirai Malware Variant Targets AVTECH Cameras, Huawei Routers (lien direct) | Murdoc_Botnet used Mirai malware to exploit IoT vulnerabilities, targeting devices globally
Murdoc_Botnet used Mirai malware to exploit IoT vulnerabilities, targeting devices globally |
Malware Vulnerability Threat | ★★★ | ||
| 2025-01-21 15:36:23 | HPE Investigates Hacker’s Claim Of Selling Stolen Source Code (lien direct) | Hewlett Packard Enterprise (HPE) has launched an investigation into a new data breach after a threat actor claimed to have stolen sensitive information from the tech giant\'s systems.
The investigation follows an announcement by the prominent and notorious threat actor “IntelBroker,” who took to BreachForums on January 16th to announce that they are selling files reportedly obtained from HPE’s networks.
For those unaware, IntelBroker is infamous for breaching major organizations like Cisco, Nokia, Europol, and AMD, often stealing and selling sensitive data on cybercrime forums.
Regarding HPE, the compromised data allegedly includes source code for products like Zerto and iLO, private Github repositories, Docker builds, SAP Hybris, Certificates (private and public keys), and even some old user personal identifiable information (PII) used for deliveries.
IntelBroker is also offering selling access to some HPE services, including APIs, WePay, GitHub, GitLab and more.
“Today, I am selling the HPE data breach,” IntelBroker wrote in a BreachForums post. “We have been connecting to some of their services for about 2 days now.”
HPE said it is investigating the breach claims but has found no evidence of a security breach.
It added that there is no operational impact on the company and no evidence that customer information was involved in the cyber incident.
“HPE became aware on January 16 of claims being made by a group called IntelBroker that it was in possession of information belonging to HPE. HPE immediately activated our cyber response protocols, disabled related credentials, and launched an investigation to evaluate the validity of the claims,” an HPE spokesperson said in a statement.
This is not the first time IntelBroker has made such breach claims against HPE. In February 2024, the threat actor claimed to have breached HPE and offered the company\'s stolen data for sale, which reportedly included Continuous Integration/Continuous Deployment (CI/CD) access, system logs, configuration files, access tokens, HPE StoreOnce files (such as serial numbers and warranty information), and access passwords, including email services.
Hewlett Packard Enterprise (HPE) has launched an investigation into a new data breach after a threat actor claimed to have stolen sensitive information from the tech giant\'s systems. The investigation follows an announcement by the prominent and notorious threat actor “IntelBroker,” who took to BreachForums on January 16th to announce that they are selling files reportedly obtained from HPE’s networks. For those unaware, IntelBroker is infamous for breaching major organizations like Cisco, Nokia, Europol, and AMD, often stealing and selling sensitive data on cybercrime forums. Regarding HPE, the compromised data allegedly includes source code for products like Zerto and iLO, private Github repositories, Docker builds, SAP Hybris, Certificates (private and public keys), and even some old user personal identifiable information (PII) used for deliveries. IntelBroker is also offering selling access to some HPE services, including APIs, WePay, GitHub, GitLab and more. “Today, I am selling the HPE data breach,” IntelBroker wrote in a BreachForums post. “We have been connecting to some of their services for about 2 days now.” HPE said it is investigating the breach claims but has found no evidence of a security breach. It added that there is no operational impact on the company and no evidence that customer information was involved in the cyber incident. “HPE became aware on January 16 of claims being made by a group called IntelBroker t |
Data Breach Threat | ★★★ | ||
| 2025-01-21 14:00:00 | Securing Cryptocurrency Organizations (lien direct) | Written by: Joshua Goddard
The Rise of Crypto Heists and the Challenges in Preventing Them Cryptocurrency crime encompasses a wide range of illegal activities, from theft and hacking to fraud, money laundering, and even terrorist financing, all exploiting the unique characteristics of digital currencies. Cryptocurrency heists, specifically, refer to the large-scale theft of cryptocurrencies or digital assets through unauthorized access, exploitation, or deception. Cryptocurrency heists are on the rise due to the lucrative nature of their rewards, the challenges associated with attribution to malicious actors, and the opportunities presented by nascent familiarity with cryptocurrency and Web3 technologies among many organizations. Cofense highlighted that phishing activity targeting Web3 platforms increased by 482% in 2022, Chainalysis reported that $24.2 billion USD was received by illicit addresses in 2023, and Immunefi reported that in Q2 2024, compromises of Web3 organizations resulted in losses of approximately $572 million USD. When threat actors gain access to cryptocurrency organizations, the potential for rapid, high-value financial losses due to unauthorized access is significantly elevated. A single malicious command executed on a vulnerable system can lead to the theft of millions of dollars worth of assets. This starkly contrasts with traditional organizations, where achieving financial gain or extracting value from stolen data often requires prolonged social engineering campaigns, all while facing the risk of detection and apprehension by law enforcement or financial institutions. The prospect of swift and substantial financial gains presents a compelling motivation for threat actors to target cryptocurrency organizations. Cryptocurrency organizations are those whose core operations revolve around the use, management, or exchange of digital currencies, including: Cryptocurrency exchanges that facilitate the buying and selling of cryptocurrencies Financial institutions or payment gateway platforms that provide on or off ramp buying and selling of cryptocurrencies Financial institutions that hold cryptocurrency assets as investment products for their customers DeFi protocol providers that provide financial solutions for interacting with cryptocurrency assets Web3 game creators that use blockchains for their in-game economics Providers of hardware or software cryptocurrency wallets, wallet custodians, and wallet smart contract providers, which facilitate storage solutions for cryptocurrency assets Cryptocurrency mining organizations, which validate transactions to generate |
Malware Tool Vulnerability Threat Studies Legislation Cloud Technical Commercial | ★★★ | ||
| 2025-01-21 10:57:00 | CERT-UA Warns of Cyber Scams Using Fake AnyDesk Requests for Fraudulent Security Audits (lien direct) | The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of ongoing attempts by unknown threat actors to impersonate the cybersecurity agency by sending AnyDesk connection requests.
The AnyDesk requests claim to be for conducting an audit to assess the "level of security," CERT-UA added, cautioning organizations to be on the lookout for such social engineering attempts that seek to
The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of ongoing attempts by unknown threat actors to impersonate the cybersecurity agency by sending AnyDesk connection requests. The AnyDesk requests claim to be for conducting an audit to assess the "level of security," CERT-UA added, cautioning organizations to be on the lookout for such social engineering attempts that seek to |
Threat | ★★★ | ||
| 2025-01-21 08:49:19 | US HC3 warns BEC emerges as one of \\'most financially damaging\\' cybersecurity threat to healthcare sector (lien direct) | The Health Sector Cybersecurity Coordination Center (HC3) within the U.S. Department of Health & Human Services (HHS) identified...
The Health Sector Cybersecurity Coordination Center (HC3) within the U.S. Department of Health & Human Services (HHS) identified... |
Threat Medical | ★★★ | ||
| 2025-01-21 04:25:53 | NASA\\'s Cybersecurity Initiative: What Spacecraft Manufacturers Need to Know (lien direct) | NASA is about to introduce new requirements for its contractors. These requirements will dramatically improve the cybersecurity of spacecraft and the US\' resilience to cyber threats. But what do these requirements mean for spacecraft manufacturers? What challenges will they face? And what will they need to do to comply? Keep reading to find out. Understanding the Cyber Space Threat While NASA has cybersecurity requirements for its spacecraft in operation, these requirements do not extend to the spacecraft acquisition and development lifecycle. Essentially, NASA contractors are not currently...
NASA is about to introduce new requirements for its contractors. These requirements will dramatically improve the cybersecurity of spacecraft and the US\' resilience to cyber threats. But what do these requirements mean for spacecraft manufacturers? What challenges will they face? And what will they need to do to comply? Keep reading to find out. Understanding the Cyber Space Threat While NASA has cybersecurity requirements for its spacecraft in operation, these requirements do not extend to the spacecraft acquisition and development lifecycle. Essentially, NASA contractors are not currently... |
Threat | ★★★ | ||
| 2025-01-20 20:23:00 | DoNot Team Linked to New Tanzeem Android Malware Targeting Intelligence Collection (lien direct) | The Threat actor known as DoNot Team has been linked to a new Android malware as part of highly targeted cyber attacks.
The artifacts in question, named Tanzeem (meaning "organization" in Urdu) and Tanzeem Update, were spotted in October and December 2024 by cybersecurity company Cyfirma. The apps in question have been found to incorporate identical functions, barring minor modifications to the
The Threat actor known as DoNot Team has been linked to a new Android malware as part of highly targeted cyber attacks. The artifacts in question, named Tanzeem (meaning "organization" in Urdu) and Tanzeem Update, were spotted in October and December 2024 by cybersecurity company Cyfirma. The apps in question have been found to incorporate identical functions, barring minor modifications to the |
Malware Threat Mobile | ★★★ | ||
| 2025-01-20 15:03:57 | 20th January– Threat Intelligence Report (lien direct) | >For the latest discoveries in cyber research for the week of 20th January, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Hotel management platform Otelier has suffered a data breach that resulted in extraction of almost eight terabytes of data. The threat actors compromised company\'s Amazon S3 cloud storage, stealing guests’ personal information […]
>For the latest discoveries in cyber research for the week of 20th January, please download our Threat Intelligence Bulletin. TOP ATTACKS AND BREACHES Hotel management platform Otelier has suffered a data breach that resulted in extraction of almost eight terabytes of data. The threat actors compromised company\'s Amazon S3 cloud storage, stealing guests’ personal information […] |
Data Breach Threat Cloud | ★★★ | ||
| 2025-01-20 14:06:38 | HPE investigates breach as hacker claims to steal source code (lien direct) | Hewlett Packard Enterprise (HPE) is investigating claims of a new breach after a threat actor said they stole documents from the company\'s developer environments. [...]
Hewlett Packard Enterprise (HPE) is investigating claims of a new breach after a threat actor said they stole documents from the company\'s developer environments. [...] |
Threat | ★★★ | ||
| 2025-01-20 03:39:35 | Think You Know Tripwire? Think Again (lien direct) | Fortra\'s Tripwire has always been widely known as a File Integrity Monitoring (FIM) solution, and a very good one at that. The good news is that it still is - only when you look closely, it\'s a lot more. And it always has been. Besides its traditionally known role as an integrity and security configuration management tool, Tripwire\'s powerful capabilities make it a comprehensive cybersecurity solution. Did you know that with Tripwire, you could: Detect advanced persistent threats (APTs) Identify ransomware Discover zero-day attacks Implement zero trust policies Far more than facilitating...
Fortra\'s Tripwire has always been widely known as a File Integrity Monitoring (FIM) solution, and a very good one at that. The good news is that it still is - only when you look closely, it\'s a lot more. And it always has been. Besides its traditionally known role as an integrity and security configuration management tool, Tripwire\'s powerful capabilities make it a comprehensive cybersecurity solution. Did you know that with Tripwire, you could: Detect advanced persistent threats (APTs) Identify ransomware Discover zero-day attacks Implement zero trust policies Far more than facilitating... |
Ransomware Tool Vulnerability Threat | ★★★ | ||
| 2025-01-17 19:43:18 | US Sanctions Chinese Hacker & Firm for Treasury, Critical Infrastructure Breaches (lien direct) | The cyber actor played a role in the Treasury breach as well as attacks on critical infrastructure, linked to China-backed advanced persistent threat (APT) group Salt Typhoon.
The cyber actor played a role in the Treasury breach as well as attacks on critical infrastructure, linked to China-backed advanced persistent threat (APT) group Salt Typhoon. |
Threat | ★★★ | ||
| 2025-01-17 18:36:00 | Python-Based Bots Exploiting PHP Servers Fuel Gambling Platform Proliferation (lien direct) | Cybersecurity researchers have exposed a new campaign that targets web servers running PHP-based applications to promote gambling platforms in Indonesia.
"Over the past two months, a significant volume of attacks from Python-based bots has been observed, suggesting a coordinated effort to exploit thousands of web apps," Imperva researcher Daniel Johnston said in an analysis. "These attacks
Cybersecurity researchers have exposed a new campaign that targets web servers running PHP-based applications to promote gambling platforms in Indonesia. "Over the past two months, a significant volume of attacks from Python-based bots has been observed, suggesting a coordinated effort to exploit thousands of web apps," Imperva researcher Daniel Johnston said in an analysis. "These attacks |
Threat | ★★★ | ||
| 2025-01-17 18:21:00 | Stories from the SOC: Caught in the Trap: Detecting and Defending Against RaccoonO365 Phishing Campaigns (lien direct) | Executive Summary
In September 2024, LevelBlue conducted a comprehensive threat hunt targeting artifacts indicative of Phishing-as-a-Service (PhaaS) activity across our monitored customer fleet. During the investigation, the LevelBlue Managed Detection and Response (MDR) Blue Team discovered a new PhaaS kit, now identified as RaccoonO365. The hunt confirmed true-positive compromises of Office 365 accounts, prompting swift customer notifications and guidance on remediation actions. The initial findings were handed over to the LevelBlue Labs Threat Intelligence team, which further uncovered additional infrastructure and deconstructed the kit’s JavaScript. This analysis provided critical insights into the features and capabilities of the emerging PhaaS kit.
Investigation
An anomalous artifact identified during a customer investigation was escalated to the Threat Hunting team for analysis. Further examination revealed that this artifact was linked to a specific Phishing-as-a-Service (PhaaS) platform known as \'RaccoonO365\'. Promoted as a cutting-edge phishing toolkit, it uses a custom User Agent, domains mimicking Microsoft O365 services, and Cloudflare infrastructure. Including these findings in our threat-hunting queries led to two additional discoveries tallying three total detections across the customer fleet. The two proactive detections identified events received, but no alarms were triggered in the involved customer\'s LevelBlue USM Anywhere instances. The third reactive detection was a confirmed business email compromise (BEC), detected after triggering an alarm. The threat actor utilized the user agent \'RaccoonO365\' prior to the business email compromise detection meaning there was a short period of unauthorized access that went undetected. Each occurrence was triaged individually, and investigations were conducted in all three customer instances referring to the observed activity. Partnering with LevelBlue Labs, a new Correlation Rule was created to search specifically for a RaccoonO365 user agent within associated logs. In addition, the LevelBlue Labs team uncovered additional structural and descriptive features attributed to RaccoonO365, which later was turned into a Pulse Indicator of Compromise (IOC) detection.
Expanded Investigation
Alarm and USMA log review
1. An unrelated potential business email compromise (BEC) alarm was received and triaged by the LevelBlue MDR SOC. The identified user utilized a foreign VPN to successfully log into customer’s Microsoft Office environment. A custom alarm rule was created due to its high probability of being a True Positive. While conducting their investigation, they uncovered a suspicious user agent related to the compromised email address –RaccoonO365.
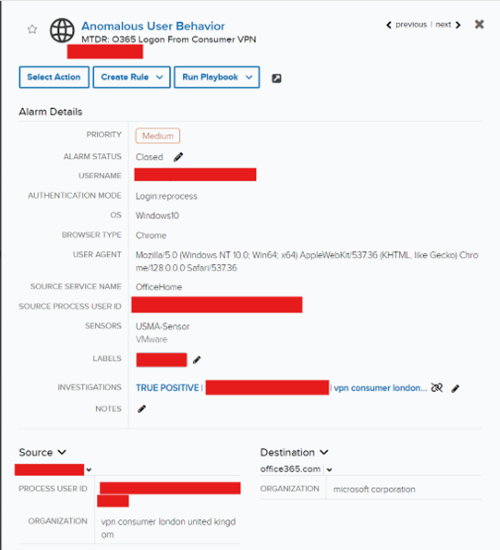 2. Information was passed off to LevelBlue Threat Hunters to conduct further internal and external research for the identified artifact.
2. Information was passed off to LevelBlue Threat Hunters to conduct further internal and external research for the identified artifact.
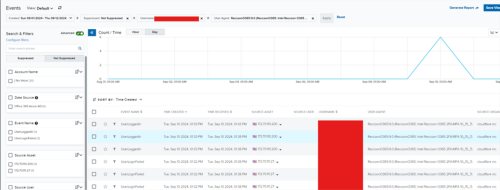 3. A dedicated threat hunter conducted a review of events including the subject user agent. Event logs were compared against each other and the successful logins provided additional key data points.
3. A dedicated threat hunter conducted a review of events including the subject user agent. Event logs were compared against each other and the successful logins provided additional key data points.
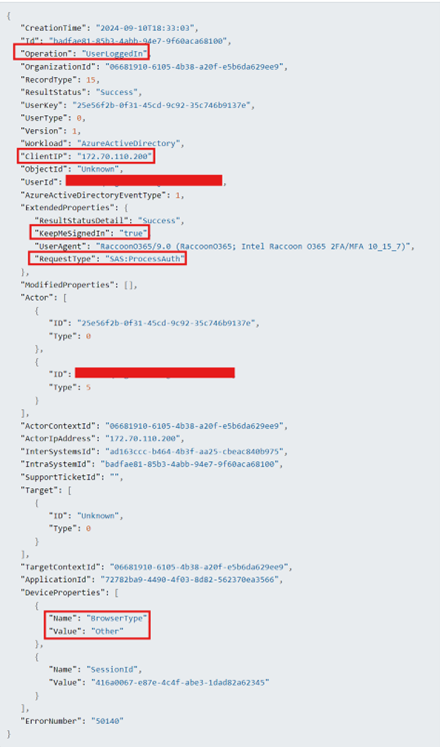 Shared Access Signature (SAS) authentication
"SAS authentication" refers to a method of user access control using a "Shared Access Signature" (SAS) token, which essentially grants temporary, limited access to specific resources within a cloud platform like Azure. This allows users to access data without directly sharing the full account access
Shared Access Signature (SAS) authentication
"SAS authentication" refers to a method of user access control using a "Shared Access Signature" (SAS) token, which essentially grants temporary, limited access to specific resources within a cloud platform like Azure. This allows users to access data without directly sharing the full account access |
Tool Threat Mobile Cloud | ★★★ | ||
| 2025-01-17 17:11:16 | Closing software-understanding gap is critical to national security, CISA says (lien direct) | >In a joint report with DARPA and others, the cyber agency said that knowledge gap “exacerbates” risks posed by threat actors in U.S. critical infrastructure.
>In a joint report with DARPA and others, the cyber agency said that knowledge gap “exacerbates” risks posed by threat actors in U.S. critical infrastructure. |
Threat | ★★★ | ||
| 2025-01-17 15:17:22 | Otelier data breach exposes info, hotel reservations of millions (lien direct) | Hotel management platform Otelier suffered a data breach after threat actors breached its Amazon S3 cloud storage to steal millions of guests\' personal information and reservations for well-known hotel brands like Marriott, Hilton, and Hyatt. [...]
Hotel management platform Otelier suffered a data breach after threat actors breached its Amazon S3 cloud storage to steal millions of guests\' personal information and reservations for well-known hotel brands like Marriott, Hilton, and Hyatt. [...] |
Data Breach Threat Cloud | ★★★ | ||
| 2025-01-17 14:12:31 | Check Point Heads to Davos 2025 to Discuss Advancing Cyber Security and Digital Trust in an Era of GenAI and Disinformation (lien direct) | >Check Point\'s Rupal Hollenbeck, President, and Dorit Dor, CTO, will be attending the World Economic Forum Annual Meeting 2025 next week from January 20-23. Rupal will speak at WEF Agenda sessions including “Democratizing Cybersecurity,” where she will discuss securing the benefits of technological progress for all as the global threat environment grows ever more dangerous. Rupal will articulate the challenges that arise from cyber inequity, and why we should all care about a secure-by-design standard up and down the supply chain. She will also speak on a panel titled “Navigating Disinformation, Division and Equality Moonshot” courtesy of the World Woman […]
>Check Point\'s Rupal Hollenbeck, President, and Dorit Dor, CTO, will be attending the World Economic Forum Annual Meeting 2025 next week from January 20-23. Rupal will speak at WEF Agenda sessions including “Democratizing Cybersecurity,” where she will discuss securing the benefits of technological progress for all as the global threat environment grows ever more dangerous. Rupal will articulate the challenges that arise from cyber inequity, and why we should all care about a secure-by-design standard up and down the supply chain. She will also speak on a panel titled “Navigating Disinformation, Division and Equality Moonshot” courtesy of the World Woman […] |
Threat | ★★★ | ||
| 2025-01-17 13:40:08 | Russian Star Blizzard hackers exploit WhatsApp accounts to spy on nonprofits aiding Ukraine (lien direct) | The Moscow-linked group has been sending phishing messages impersonating U.S. government officials with an invitation to join a fake WhatsApp group for nonprofits supporting Ukraine during the war.
The Moscow-linked group has been sending phishing messages impersonating U.S. government officials with an invitation to join a fake WhatsApp group for nonprofits supporting Ukraine during the war. |
Threat | ★★★ | ||
| 2025-01-17 13:16:57 | Ransomware : 2024, une année marquée par l\'évolution et l\'intensification des menaces (lien direct) | Ransomware :
2024, une année marquée par l\'évolution et l\'intensification des menaces
-
Malwares
Ransomware : 2024, une année marquée par l\'évolution et l\'intensification des menaces - Malwares |
Ransomware Threat | ★★★ | ||
| 2025-01-17 11:57:01 | US sanctions Chinese firm, hacker behind telecom and Treasury hacks (lien direct) | The U.S. Department of the Treasury\'s Office of Foreign Assets Control (OFAC) has sanctioned Yin Kecheng, a Shanghai-based hacker for his role in the recent Treasury breach and a company associated with the Salt Typhoon threat group. [...]
The U.S. Department of the Treasury\'s Office of Foreign Assets Control (OFAC) has sanctioned Yin Kecheng, a Shanghai-based hacker for his role in the recent Treasury breach and a company associated with the Salt Typhoon threat group. [...] |
Threat | ★★★ | ||
| 2025-01-17 07:33:00 | Cyber innovation to address rising regulatory, threat burden (lien direct) | Pas de details / No more details | Threat | ★★★ | ||
| 2025-01-17 01:12:06 | CISA warns of exploited Fortinet bugs as Microsoft issues its biggest Patch Tuesday in years (lien direct) | The federal government and multiple cybersecurity firms warned of a zero-day vulnerability in FortiGate firewalls that hackers are actively exploiting.
The federal government and multiple cybersecurity firms warned of a zero-day vulnerability in FortiGate firewalls that hackers are actively exploiting. |
Vulnerability Threat | ★★★ | ||
| 2025-01-17 00:00:00 | DORA is here - are you ready? (lien direct) | Today, January 17, 2025, marks a pivotal moment for the EU financial sector as the Digital Operational Resilience Act (DORA) officially comes into effect. Designed to combat the growing threat of cyberattacks, DORA sets a new standard for cybersecurity resilience across financial institutions and their critical ICT service providers.
With cyberattacks costing the financial sec…
Today, January 17, 2025, marks a pivotal moment for the EU financial sector as the Digital Operational Resilience Act (DORA) officially comes into effect. Designed to combat the growing threat of cyberattacks, DORA sets a new standard for cybersecurity resilience across financial institutions and their critical ICT service providers. With cyberattacks costing the financial sec… |
Threat | ★★★ | ||
| 2025-01-16 23:42:00 | Russian Star Blizzard Shifts Tactics to Exploit WhatsApp QR Codes for Credential Harvesting (lien direct) | The Russian threat actor known as Star Blizzard has been linked to a new spear-phishing campaign that targets victims\' WhatsApp accounts, signaling a departure from its longstanding tradecraft in a likely attempt to evade detection.
"Star Blizzard\'s targets are most commonly related to government or diplomacy (both incumbent and former position holders), defense policy or international relations
The Russian threat actor known as Star Blizzard has been linked to a new spear-phishing campaign that targets victims\' WhatsApp accounts, signaling a departure from its longstanding tradecraft in a likely attempt to evade detection. "Star Blizzard\'s targets are most commonly related to government or diplomacy (both incumbent and former position holders), defense policy or international relations |
Threat | ★★★ | ||
| 2025-01-16 21:35:17 | Reimagining Your SOC: How to Achieve Proactive Network Security (lien direct) | This blog post advises on how security teams can move to autonomous detection and investigation of novel threats, reducing alert fatigue, and enabling tailored, real-time threat response.
This blog post advises on how security teams can move to autonomous detection and investigation of novel threats, reducing alert fatigue, and enabling tailored, real-time threat response. |
Threat | ★★★ | ||
| 2025-01-16 17:45:00 | Middle Eastern Real Estate Fraud Grows with Online Listings (lien direct) | Middle East real estate scams are surging as fraudsters exploit online listings and bypassed due diligence checks
Middle East real estate scams are surging as fraudsters exploit online listings and bypassed due diligence checks |
Threat | ★★ | ||
| 2025-01-16 17:00:00 | The $10 Cyber Threat Responsible for the Biggest Breaches of 2024 (lien direct) | You can tell the story of the current state of stolen credential-based attacks in three numbers:
Stolen credentials were the #1 attacker action in 2023/24, and the breach vector for 80% of web app attacks. (Source: Verizon).
Cybersecurity budgets grew again in 2024, with organizations now spending almost $1,100 per user (Source: Forrester).
Stolen credentials on criminal forums cost as
You can tell the story of the current state of stolen credential-based attacks in three numbers: Stolen credentials were the #1 attacker action in 2023/24, and the breach vector for 80% of web app attacks. (Source: Verizon). Cybersecurity budgets grew again in 2024, with organizations now spending almost $1,100 per user (Source: Forrester). Stolen credentials on criminal forums cost as |
Threat | ★★★ | ||
| 2025-01-16 16:50:00 | Researchers Find Exploit Allowing NTLMv1 Despite Active Directory Restrictions (lien direct) | Cybersecurity researchers have found that the Microsoft Active Directory Group Policy that\'s designed to disable NT LAN Manager (NTLM) v1 can be trivially bypassed by a misconfiguration.
"A simple misconfiguration in on-premise applications can override the Group Policy, effectively negating the Group Policy designed to stop NTLMv1 authentications," Silverfort researcher Dor Segal said in a
Cybersecurity researchers have found that the Microsoft Active Directory Group Policy that\'s designed to disable NT LAN Manager (NTLM) v1 can be trivially bypassed by a misconfiguration. "A simple misconfiguration in on-premise applications can override the Group Policy, effectively negating the Group Policy designed to stop NTLMv1 authentications," Silverfort researcher Dor Segal said in a |
Threat | ★★ | ||
| 2025-01-16 16:49:43 | Exabeam (lien direct) | Contact : Matthieu Potin matthieu.potin@exabeam.com +33 (0)6 08 01 57 37
Année de création : 2013
Activités : Exabeam est un leader mondial en cybersécurité, spécialisé dans les opérations de sécurité basées sur l\'IA. Nous aidons les entreprises à détecter, investiguer et répondre aux menaces en exploitant les logs informatiques et en utilisant le machine learning pour décupler les capacités d\'analyses.
Description du produit ou solution phare pour 2024/2025 : Exabeam propose une solution complète et (...)
-
SOC -GESTION DES LOGS - OUTILS DE SIEM - CONFORMITE - COMPLIANCE - RGPD - FUITE DE DONNEES - DATA ROOM
Contact : Matthieu Potin matthieu.potin@exabeam.com +33 (0)6 08 01 57 37 Année de création : 2013 Activités : Exabeam est un leader mondial en cybersécurité, spécialisé dans les opérations de sécurité basées sur l\'IA. Nous aidons les entreprises à détecter, investiguer et répondre aux menaces en exploitant les logs informatiques et en utilisant le machine learning pour décupler les capacités d\'analyses. Description du produit ou solution phare pour 2024/2025 : Exabeam propose une solution complète et (...) - SOC -GESTION DES LOGS - OUTILS DE SIEM - CONFORMITE - COMPLIANCE - RGPD - FUITE DE DONNEES - DATA ROOM |
Tool Threat | ★★ | ||
| 2025-01-16 16:45:00 | Hackers Hide Malware in Images to Deploy VIP Keylogger and 0bj3ctivity Stealer (lien direct) | Threat actors have been observed concealing malicious code in images to deliver malware such as VIP Keylogger and 0bj3ctivity Stealer as part of separate campaigns.
"In both campaigns, attackers hid malicious code in images they uploaded to archive[.]org, a file-hosting website, and used the same .NET loader to install their final payloads," HP Wolf Security said in its Threat Insights Report
Threat actors have been observed concealing malicious code in images to deliver malware such as VIP Keylogger and 0bj3ctivity Stealer as part of separate campaigns. "In both campaigns, attackers hid malicious code in images they uploaded to archive[.]org, a file-hosting website, and used the same .NET loader to install their final payloads," HP Wolf Security said in its Threat Insights Report |
Malware Threat | ★★ | ||
| 2025-01-16 16:08:45 | SentinelOne brings the power of Purple AI to Zscaler, Okta, Palo Alto Networks, Proofpoint, Fortinet and Microsoft Data (lien direct) | SentinelOne brings the power of Purple AI to Zscaler, Okta, Palo Alto Networks, Proofpoint, Fortinet and Microsoft Data
Popular generative AI security analyst can now be used to speed cybersecurity investigations and simplify threat hunting across a growing list of native and third-party sources
-
Product Reviews
SentinelOne brings the power of Purple AI to Zscaler, Okta, Palo Alto Networks, Proofpoint, Fortinet and Microsoft Data Popular generative AI security analyst can now be used to speed cybersecurity investigations and simplify threat hunting across a growing list of native and third-party sources - Product Reviews |
Threat | ★★ | ||
| 2025-01-16 15:00:00 | Strategic Approaches to Threat Detection, Investigation & Response (lien direct) | By staying vigilant, agile, and prepared, organizations can turn TDIR from a defensive strategy into a proactive enabler of security and operational excellence.
By staying vigilant, agile, and prepared, organizations can turn TDIR from a defensive strategy into a proactive enabler of security and operational excellence. |
Threat | ★★★ | ||
| 2025-01-16 14:10:24 | Analysis of Threat Actor Data Posting (lien direct) | This blog analysis regarding a recent threat actor posting, which claims to offer compromised configuration and VPN credentials from FortiGate devices, provides factual information to help our customers better understand the situation and make informed decisions.
This blog analysis regarding a recent threat actor posting, which claims to offer compromised configuration and VPN credentials from FortiGate devices, provides factual information to help our customers better understand the situation and make informed decisions. |
Threat | ★★★ | ||
| 2025-01-16 13:05:06 | FunkSec: The Rising Yet Controversial Ransomware Threat Actor Dominating December 2024 (lien direct) | >As 2024 ended, a new name surged to the top of the cyber threat charts: FunkSec. Emerging as a leading ransomware-as-a-service (RaaS) actor, FunkSec made waves in December by publishing over 85 victim profiles on its Data Leak Site (DLS). However, beneath its apparent dominance lies a more complex and controversial story, as uncovered in Check Point Research\'s (CPR) Global Threat Index for December 2024. FunkSec\'s rapid ascent highlights the evolving tactics of RaaS operators. Utilizing artificial intelligence to scale operations, the group appears to rely heavily on AI-powered tools to generate ransomware and manage its double-extortion campaigns. While this […]
>As 2024 ended, a new name surged to the top of the cyber threat charts: FunkSec. Emerging as a leading ransomware-as-a-service (RaaS) actor, FunkSec made waves in December by publishing over 85 victim profiles on its Data Leak Site (DLS). However, beneath its apparent dominance lies a more complex and controversial story, as uncovered in Check Point Research\'s (CPR) Global Threat Index for December 2024. FunkSec\'s rapid ascent highlights the evolving tactics of RaaS operators. Utilizing artificial intelligence to scale operations, the group appears to rely heavily on AI-powered tools to generate ransomware and manage its double-extortion campaigns. While this […] |
Ransomware Tool Threat | ★★ | ||
| 2025-01-16 12:50:00 | New Hacking Group Leaks Configuration of 15,000 Fortinet Firewalls (lien direct) | The leak likely comes from a zero-day exploit affecting Fortinet\'s products
The leak likely comes from a zero-day exploit affecting Fortinet\'s products |
Vulnerability Threat | ★★ | ||
| 2025-01-16 12:15:00 | Python-Based Malware Powers RansomHub Ransomware to Exploit Network Flaws (lien direct) | Cybersecurity researchers have detailed an attack that involved a threat actor utilizing a Python-based backdoor to maintain persistent access to compromised endpoints and then leveraged this access to deploy the RansomHub ransomware throughout the target network.
According to GuidePoint Security, initial access is said to have been facilitated by means of a JavaScript malware downloaded named
Cybersecurity researchers have detailed an attack that involved a threat actor utilizing a Python-based backdoor to maintain persistent access to compromised endpoints and then leveraged this access to deploy the RansomHub ransomware throughout the target network. According to GuidePoint Security, initial access is said to have been facilitated by means of a JavaScript malware downloaded named |
Ransomware Malware Threat | ★★★ | ||
| 2025-01-16 09:20:05 | Menaces liées à l\'IA et fragmentation technologique : selon cette nouvelle étude, tels sont les plus grands défis de cybersécurité pour les organisations en 2025 (lien direct) | Menaces liées à l\'IA et fragmentation technologique : selon cette nouvelle étude, tels sont les plus grands défis de cybersécurité pour les organisations en 2025
74% des cadres dirigeants et professionnels de sécurité interrogés en France se disent préoccupés par les cybermenaces liées à l\'IA, qu\'ils considèrent comme le risque cyber majeur pesant sur leur organisation en 2025, davantage que dans les autres pays d\'Europe interrogés
-
Investigations
Menaces liées à l\'IA et fragmentation technologique : selon cette nouvelle étude, tels sont les plus grands défis de cybersécurité pour les organisations en 2025 74% des cadres dirigeants et professionnels de sécurité interrogés en France se disent préoccupés par les cybermenaces liées à l\'IA, qu\'ils considèrent comme le risque cyber majeur pesant sur leur organisation en 2025, davantage que dans les autres pays d\'Europe interrogés - Investigations |
Threat | ★★★ | ||
| 2025-01-16 09:18:02 | Scammers Exploit California Wildfires, Posing as Fire Relief Services (lien direct) | Cybercriminals are exploiting the California wildfires by launching phishing scams. Learn how hackers are targeting victims with fake domains and deceptive tactics, and how to protect yourself from these cyber threats.
Cybercriminals are exploiting the California wildfires by launching phishing scams. Learn how hackers are targeting victims with fake domains and deceptive tactics, and how to protect yourself from these cyber threats. |
Threat | ★★★ | ||
| 2025-01-16 09:17:00 | Sneaky 2FA: exposing a new AiTM Phishing-as-a-Service (lien direct) | >Introduction In December 2024, during our daily threat hunting routine, we uncovered a new Adversary-in-the-Middle (AiTM) phishing kit targeting Microsoft 365 accounts. These phishing pages have been circulating since at least October 2024, and during that period, we identified potential compromises through the Sekoia.io telemetry. Our analysis showed that this kit is being sold as […]
La publication suivante Sneaky 2FA: exposing a new AiTM Phishing-as-a-Service est un article de Sekoia.io Blog.
>Introduction In December 2024, during our daily threat hunting routine, we uncovered a new Adversary-in-the-Middle (AiTM) phishing kit targeting Microsoft 365 accounts. These phishing pages have been circulating since at least October 2024, and during that period, we identified potential compromises through the Sekoia.io telemetry. Our analysis showed that this kit is being sold as […] La publication suivante Sneaky 2FA: exposing a new AiTM Phishing-as-a-Service est un article de Sekoia.io Blog. |
Threat | ★★★ | ||
| 2025-01-16 08:30:00 | EU To Launch New Support Centre by 2026 to Boost Healthcare Cybersecurity (lien direct) | A new EU action plan will be structured around four pillars: prevention, threat detection and identification, response to cyber-attacks and deterrence
A new EU action plan will be structured around four pillars: prevention, threat detection and identification, response to cyber-attacks and deterrence |
Threat Medical | ★★★ | ||
| 2025-01-16 04:38:40 | DOJ, FBI Dismantle Malware Used by China-Backed Hackers in Global Operation (lien direct) | In an international effort, the US Department of Justice (DOJ) and the Federal Bureau of Investigation (FBI) have successfully eliminated a sophisticated malware threat known as “PlugX” from over 4,200 computers across the United States. The malware, used by bad actors sponsored by the People\'s Republic of China (PRC), has targeted global victims since 2014. [...]
In an international effort, the US Department of Justice (DOJ) and the Federal Bureau of Investigation (FBI) have successfully eliminated a sophisticated malware threat known as “PlugX” from over 4,200 computers across the United States. The malware, used by bad actors sponsored by the People\'s Republic of China (PRC), has targeted global victims since 2014. [...] |
Malware Threat | ★★★ | ||
| 2025-01-16 04:26:38 | RansomHub Affiliates Exploit AI-Generated Python Backdoor in Advanced Cyberattacks (lien direct) | A sophisticated Python-based backdoor, potentially developed using AI, has been identified as a critical tool for RansomHub affiliates to infiltrate and maintain access to compromised networks. The discovery, made by Andrew Nelson, Principal Digital Forensics and Incident Response (DFIR) Consultant at GuidePoint Security, reveals new tactics being used by ransomware gangs. A Lucrative Model RansomHub, [...]
A sophisticated Python-based backdoor, potentially developed using AI, has been identified as a critical tool for RansomHub affiliates to infiltrate and maintain access to compromised networks. The discovery, made by Andrew Nelson, Principal Digital Forensics and Incident Response (DFIR) Consultant at GuidePoint Security, reveals new tactics being used by ransomware gangs. A Lucrative Model RansomHub, [...] |
Ransomware Tool Threat | ★★★ | ||
| 2025-01-16 01:29:55 | CISA director says threat hunters spotted Salt Typhoon on federal networks before telco compromises (lien direct) | >The incident helped the federal government to seize a virtual private server used by the group and more quickly “connect the dots,” Jen Easterly said.
>The incident helped the federal government to seize a virtual private server used by the group and more quickly “connect the dots,” Jen Easterly said. |
Threat | ★★★ | ||
| 2025-01-15 21:07:00 | Lazarus Group Targets Web3 Developers with Fake LinkedIn Profiles in Operation 99 (lien direct) | The North Korea-linked Lazarus Group has been attributed to a new cyber attack campaign dubbed Operation 99 that targeted software developers looking for freelance Web3 and cryptocurrency work to deliver malware.
"The campaign begins with fake recruiters, posing on platforms like LinkedIn, luring developers with project tests and code reviews," Ryan Sherstobitoff, senior vice president of Threat
The North Korea-linked Lazarus Group has been attributed to a new cyber attack campaign dubbed Operation 99 that targeted software developers looking for freelance Web3 and cryptocurrency work to deliver malware. "The campaign begins with fake recruiters, posing on platforms like LinkedIn, luring developers with project tests and code reviews," Ryan Sherstobitoff, senior vice president of Threat |
Malware Threat | APT 38 | ★★ | |
| 2025-01-15 21:03:35 | Microsoft Fixes 8 Zero-Days In January 2025 Patch Tuesday (lien direct) | Microsoft recently released its January 2025 Patch Tuesday cumulative update, which included security updates for 159 flaws across Windows OS, Microsoft Office, .NET, Azure, Kerberos, and Windows Hyper-V. These included eight zero-day vulnerabilities, of which three are under active exploitation and five are publicly known flaws. “Of the patches released today, 11 are rated Critical, and the other 148 are rated Important in severity. This is the largest number of CVEs addressed in any single month since at least 2017 and is more than double the usual amount of CVEs fixed in January,” Trend Micro\'s Zero Day Initiative (ZDI) program researchers wrote in an analysis. The three zero-day vulnerabilities under active exploitation in the wild are tracked as CVE-2025-21333, CVE-2025-21334, and CVE-2025-21335. These are elevation of privilege (EoP) vulnerabilities in the Windows Hyper-V NT Kernel Integration Virtualization Service Provider (VSP), with a CVSS score of 7.8 (important). According to Microsoft, successfully exploiting the vulnerability could allow an authenticated user to execute code with SYSTEM privileges. As usual, the Redmond giant has provided no information about how these flaws are being exploited, the attackers involved, or the scale of the attacks. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added these flaws to its Known Exploited Vulnerabilities (KEV) catalog, mandating federal agencies to implement fixes by February 4, 2025. Further, let\'s have a look at the five publicly disclosed zero-days that were not exploited by the attackers and have been patched in the January 2025 Patch Tuesday cumulative update: CVE-2025-21186, CVE-2025-21366, and CVE-2025-21395: These three vulnerabilities, each rated 7.8 on the CVSS scale (important), are Remote Code Execution (RCE) flaws in Microsoft Access that are triggered when opening maliciously crafted Access documents. The company has addressed these vulnerabilities by blocking access to the following extensions: accdb accde accdw accdt accda accdr accdu Microsoft credited Unpatched.ai, an AI-assisted vulnerability hunting platform, for finding all three Microsoft Access issues. The other two publicly disclosed and unexploited zero-da | Vulnerability Threat Prediction Cloud | ★★★ | ||
| 2025-01-15 19:02:00 | North Korean IT Worker Fraud Linked to 2016 Crowdfunding Scam and Fake Domains (lien direct) | Cybersecurity researchers have identified infrastructure links between the North Korean threat actors behind the fraudulent IT worker schemes and a 2016 crowdfunding scam.
The new evidence suggests that Pyongyang-based threamoret groups may have pulled off illicit money-making scams that predate the use of IT workers, SecureWorks Counter Threat Unit (CTU) said in a report shared with The Hacker
Cybersecurity researchers have identified infrastructure links between the North Korean threat actors behind the fraudulent IT worker schemes and a 2016 crowdfunding scam. The new evidence suggests that Pyongyang-based threamoret groups may have pulled off illicit money-making scams that predate the use of IT workers, SecureWorks Counter Threat Unit (CTU) said in a report shared with The Hacker |
Threat | ★★ | ||
| 2025-01-15 15:34:45 | Japan Attributes More Than 200 Cyberattacks to China Threat Actor "MirrorFace" (lien direct) |
 Japan\'s National Police Agency (NPA) has attributed more than 200 cyber incidents over the past five years to the China-aligned threat actor “MirrorFace,” Infosecurity Magazine reports.
Japan\'s National Police Agency (NPA) has attributed more than 200 cyber incidents over the past five years to the China-aligned threat actor “MirrorFace,” Infosecurity Magazine reports.
 Japan\'s National Police Agency (NPA) has attributed more than 200 cyber incidents over the past five years to the China-aligned threat actor “MirrorFace,” Infosecurity Magazine reports.
Japan\'s National Police Agency (NPA) has attributed more than 200 cyber incidents over the past five years to the China-aligned threat actor “MirrorFace,” Infosecurity Magazine reports. |
Threat Legislation | ★★ | ||
| 2025-01-15 13:47:31 | Phishing and Persistence: Darktrace\\'s Role in Defending Against a Sophisticated Account Takeover (lien direct) | In a recent incident, Darktrace uncovered a M365 account takeover attempt targeting a company in the manufacturing industry. The attacker executed a sophisticated phishing attack, gaining access through the organization\'s SaaS platform. This allowed the threat actor to create a new inbox rule, potentially setting the stage for future compromises.
In a recent incident, Darktrace uncovered a M365 account takeover attempt targeting a company in the manufacturing industry. The attacker executed a sophisticated phishing attack, gaining access through the organization\'s SaaS platform. This allowed the threat actor to create a new inbox rule, potentially setting the stage for future compromises. |
Threat Cloud | ★★★ | ||
| 2025-01-15 13:00:11 | 5 Reasons You Won\\'t Want to Miss CPX 2025 (lien direct) | >As CPX 2025 approaches, the excitement is undeniable-and so is the opportunity. If you’re a security leader, cyber enthusiast, or someone who wants to stay current on the very latest in cyber threat prevention, CPX is the event you should heavily consider penciling into your calendar in 2025. From actionable insights by industry experts to exclusive networking opportunities, here are the top 5 reasons why this year\'s event is shaping up to be our best ever! Focus on AI Artificial intelligence is making waves across our world, and cyber security is no exception. As we see AI used to create […]
>As CPX 2025 approaches, the excitement is undeniable-and so is the opportunity. If you’re a security leader, cyber enthusiast, or someone who wants to stay current on the very latest in cyber threat prevention, CPX is the event you should heavily consider penciling into your calendar in 2025. From actionable insights by industry experts to exclusive networking opportunities, here are the top 5 reasons why this year\'s event is shaping up to be our best ever! Focus on AI Artificial intelligence is making waves across our world, and cyber security is no exception. As we see AI used to create […] |
Threat | ★★ |
To see everything:
Our RSS (filtrered)
