What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2025-01-24 19:56:28 | Android Identity Check Feature Locks Settings Outside Trusted Locations (lien direct) | Google is officially rolling out a new Android security feature that enhances theft protection for supported Pixel and Samsung Galaxy devices.
The “Identity Check” feature provides extra protection to critical account and device settings behind biometric authentication when outside of trusted locations (such as home or workplace). This feature protects the user and their data at every stage-before, during, and after device theft.
“When you turn on Identity Check, your device will require explicit biometric authentication to access certain sensitive resources when you’re outside of trusted locations,” Google wrote in a blog post on Thursday.
To enable Identity Check, you can designate one or more areas as a trusted location. When you are outside of these designated areas, you will need to use biometric authentication to access important account and device settings, such as changing your device PIN or biometrics, disabling theft protection, performing a factory reset, turning off \'Find My Device\', accessing saved passwords or Passkeys, adding or removing a Google Account, or accessing Developer options.
 Identity Check also provides enhanced protection for Google Accounts on all supported devices and adds more security for Samsung Accounts on eligible Galaxy devices with One UI 7. This makes it much more difficult for an unauthorized attacker to access accounts signed in on the device.
The feature is now available on Google Pixel devices running Android 15. It will roll out on Samsung One UI 7 devices in the coming weeks and on supported Android devices from other manufacturers “later this year.”
To turn on the Identity Check feature, you need to go to Settings > Google > All services > Theft Protection, and tap “Identity Check”.
To activate this feature, you must sign in to a Google Account and add a screen lock if you haven\'t.
Then, add biometrics, like Fingerprint or Face Unlock, as well as your trusted places, like Home or Work. After completion, tap Done.
In addition to launching Identity Check, Google announced its Theft Detection Lock feature. This feature uses an AI-powered on-device algorithm to recognize when your phone is forcibly taken and lock the screen.
If the machine learning algorithm detects a possible theft attempt on your unlocked device, it automatically locks the screen to protect it from thieves. This feature has been fully rolled out on devices running Android 10 and later worldwide.
To enable the Theft Detection Lock feature on your device, tap Settings > Google > All services > Theft protection and toggle the “Theft Detection Lock” switch.
Lastly, Google mentioned that it is collaborating with the GSMA and industry experts to tackle mobile device theft by sharing information, tools, and prevention techn
Identity Check also provides enhanced protection for Google Accounts on all supported devices and adds more security for Samsung Accounts on eligible Galaxy devices with One UI 7. This makes it much more difficult for an unauthorized attacker to access accounts signed in on the device.
The feature is now available on Google Pixel devices running Android 15. It will roll out on Samsung One UI 7 devices in the coming weeks and on supported Android devices from other manufacturers “later this year.”
To turn on the Identity Check feature, you need to go to Settings > Google > All services > Theft Protection, and tap “Identity Check”.
To activate this feature, you must sign in to a Google Account and add a screen lock if you haven\'t.
Then, add biometrics, like Fingerprint or Face Unlock, as well as your trusted places, like Home or Work. After completion, tap Done.
In addition to launching Identity Check, Google announced its Theft Detection Lock feature. This feature uses an AI-powered on-device algorithm to recognize when your phone is forcibly taken and lock the screen.
If the machine learning algorithm detects a possible theft attempt on your unlocked device, it automatically locks the screen to protect it from thieves. This feature has been fully rolled out on devices running Android 10 and later worldwide.
To enable the Theft Detection Lock feature on your device, tap Settings > Google > All services > Theft protection and toggle the “Theft Detection Lock” switch.
Lastly, Google mentioned that it is collaborating with the GSMA and industry experts to tackle mobile device theft by sharing information, tools, and prevention techn |
Tool Mobile | ★★ | ||
| 2025-01-24 12:50:00 | Android\\'s New Identity Check Feature Locks Device Settings Outside Trusted Locations (lien direct) | Google has launched a new feature called Identity Check for supported Android devices that locks sensitive settings behind biometric authentication when outside of trusted locations.
"When you turn on Identity Check, your device will require explicit biometric authentication to access certain sensitive resources when you\'re outside of trusted locations," Google said in a post announcing the
Google has launched a new feature called Identity Check for supported Android devices that locks sensitive settings behind biometric authentication when outside of trusted locations. "When you turn on Identity Check, your device will require explicit biometric authentication to access certain sensitive resources when you\'re outside of trusted locations," Google said in a post announcing the |
Mobile | ★★★ | ||
| 2025-01-24 07:31:08 | Android s\'enrichit d\'une sécurité anti-vol sophistiquée (lien direct) | Face à la recrudescence des vols de téléphones et des techniques toujours plus sophistiquées des malfaiteurs, Google contre-attaque encore avec une solution baptisée Identity Check.
Cette nouveauté, qui débarque d’abord sur les Pixel sous Android 15, représente une approche plutôt novatrice de la sécurité mobile. Le principe c’est de mettre en place une double authentification intelligente et contextuelle qui s’active automatiquement lorsque vous n’êtes pas dans un lieu de confiance.
Face à la recrudescence des vols de téléphones et des techniques toujours plus sophistiquées des malfaiteurs, Google contre-attaque encore avec une solution baptisée Identity Check. Cette nouveauté, qui débarque d’abord sur les Pixel sous Android 15, représente une approche plutôt novatrice de la sécurité mobile. Le principe c’est de mettre en place une double authentification intelligente et contextuelle qui s’active automatiquement lorsque vous n’êtes pas dans un lieu de confiance. |
Mobile | ★★★ | ||
| 2025-01-23 16:26:39 | Zimperium\'s Coverage Against Android Malware in Donot APT Operations and Extended Indicators of Compromise (lien direct) | >Take a look at Zimperium\'s coverage against Android malware in Donot APT operations and extended indicators of compromise.
>Take a look at Zimperium\'s coverage against Android malware in Donot APT operations and extended indicators of compromise. |
Malware Mobile | ★★★ | ||
| 2025-01-23 15:54:00 | SonicWall Urges Immediate Patch for Critical CVE-2025-23006 Flaw Amid Likely Exploitation (lien direct) | SonicWall is alerting customers of a critical security flaw impacting its Secure Mobile Access (SMA) 1000 Series appliances that it said has been likely exploited in the wild as a zero-day.
The vulnerability, tracked as CVE-2025-23006, is rated 9.8 out of a maximum of 10.0 on the CVSS scoring system.
"Pre-authentication deserialization of untrusted data vulnerability has been identified in the
SonicWall is alerting customers of a critical security flaw impacting its Secure Mobile Access (SMA) 1000 Series appliances that it said has been likely exploited in the wild as a zero-day. The vulnerability, tracked as CVE-2025-23006, is rated 9.8 out of a maximum of 10.0 on the CVSS scoring system. "Pre-authentication deserialization of untrusted data vulnerability has been identified in the |
Vulnerability Threat Mobile | ★★★ | ||
| 2025-01-23 13:01:21 | Android enhances theft protection with Identity Check and expanded features (lien direct) | Posted by Jianing Sandra Guo, Product Manager, Android, Nataliya Stanetsky, Staff Program Manager, Android
Today, people around the world rely on their mobile devices to help them stay connected with friends and family, manage finances, keep track of healthcare information and more – all from their fingertips. But a stolen device in the wrong hands can expose sensitive data, leaving you vulnerable to identity theft, financial fraud and privacy breaches.
This is why we recently launched Android theft protection, a comprehensive suite of features designed to protect you and your data at every stage – before, during, and after device theft. As part of our commitment to help you stay safe on Android, we\'re expanding and enhancing these features to deliver even more robust protection to more users around the world.
Identity Check rolling out to Pixel and Samsung One UI 7 devices
We\'re officially launching Identity Check, first on Pixel and Samsung Galaxy devices eligible for One UI 71, to provide better protection for your critical account and device settings. When you turn on Identity Check, your device will require explicit biometric authentication to access certain sensitive resources when you\'re outside of trusted locations. Identity Check also enables enhanced protection for Google Accounts on all supported devices and additional security for Samsung Accounts on One UI 7 eligible Galaxy devices, making it much more difficult for an unauthorized attacker to take over accounts signed in on the device.
As part of enabling Identity Check, you can designate one or more trusted locations. When you\'re outside of these trusted places, biometric authentication will be required to access critical account and device settings, like changing your device PIN or biometrics, disabling theft protection, or accessing Passkeys.
 Identity Check gives you more peace of mind that your most sensitive device assets are protected against unauthorized access, even if a thief or bad actor manages to learn your device PIN.
Identity Check is rolling out now to Pixel devices with Android 15 and will be available on One UI 7 eligible Galaxy devices in the coming weeks. It will roll out to supported Android devices from other manufacturers later this year.
Theft Detection Lock: expanding AI-powered protection to more users
One of the top theft protection features introduced last year was Theft Detection Lock, which uses an on-device AI-powered algorithm to help detect when your phone may be forcibly taken from you. If the machine learning algorithm detects a potential theft attempt on your unlocked device, it locks your scre
Identity Check gives you more peace of mind that your most sensitive device assets are protected against unauthorized access, even if a thief or bad actor manages to learn your device PIN.
Identity Check is rolling out now to Pixel devices with Android 15 and will be available on One UI 7 eligible Galaxy devices in the coming weeks. It will roll out to supported Android devices from other manufacturers later this year.
Theft Detection Lock: expanding AI-powered protection to more users
One of the top theft protection features introduced last year was Theft Detection Lock, which uses an on-device AI-powered algorithm to help detect when your phone may be forcibly taken from you. If the machine learning algorithm detects a potential theft attempt on your unlocked device, it locks your scre |
Tool Mobile Medical | ★★★ | ||
| 2025-01-23 13:00:00 | New Android Identity Check locks settings outside trusted locations (lien direct) | Google has announced a new Android "Identity Check" security feature that lock sensitive settings behind biometric authentication when outside a trusted location. [...]
Google has announced a new Android "Identity Check" security feature that lock sensitive settings behind biometric authentication when outside a trusted location. [...] |
Mobile | ★★★ | ||
| 2025-01-22 20:05:50 | Appdome Unveils Threat Dynamics™ (lien direct) | Appdome Unveils Threat Dynamics™ to Become Industry\'s First
AI-Native Extended Threat Management Platform
Threat Dynamics Shows How Threats Move and Provides a Benchmark Mobile Risk Index™ to Help Businesses Manage and Stay Ahead of Fraud and Cyber Threats
-
Product Reviews
Appdome Unveils Threat Dynamics™ to Become Industry\'s First AI-Native Extended Threat Management Platform Threat Dynamics Shows How Threats Move and Provides a Benchmark Mobile Risk Index™ to Help Businesses Manage and Stay Ahead of Fraud and Cyber Threats - Product Reviews |
Threat Mobile | ★★★ | ||
| 2025-01-22 18:15:00 | Samsung Says Its Galaxy S25 Is \\'Qi2 Ready.\\' Here\\'s What That Really Means (lien direct) | The company\'s new smartphones do not have Qi2 wireless charging built in natively. Just give me my magnetic Android phone already!
The company\'s new smartphones do not have Qi2 wireless charging built in natively. Just give me my magnetic Android phone already! |
Mobile | ★★★ | ||
| 2025-01-22 18:00:00 | Samsung Galaxy S25 Series: Specs, Release Date, Price, Features (lien direct) | The three flagship Android phones debut new ways to interact with Google\'s Gemini and, yes, Samsung\'s Bixby.
The three flagship Android phones debut new ways to interact with Google\'s Gemini and, yes, Samsung\'s Bixby. |
Mobile | ★★★★ | ||
| 2025-01-21 21:15:18 | DONOT Group Deploys Malicious Android Apps in India (lien direct) | The advanced persistent threat (APT) group is likely India-based and targeting individuals with connections to the country\'s intelligence community.
The advanced persistent threat (APT) group is likely India-based and targeting individuals with connections to the country\'s intelligence community. |
Threat Mobile | ★★★ | ||
| 2025-01-20 20:23:00 | DoNot Team Linked to New Tanzeem Android Malware Targeting Intelligence Collection (lien direct) | The Threat actor known as DoNot Team has been linked to a new Android malware as part of highly targeted cyber attacks.
The artifacts in question, named Tanzeem (meaning "organization" in Urdu) and Tanzeem Update, were spotted in October and December 2024 by cybersecurity company Cyfirma. The apps in question have been found to incorporate identical functions, barring minor modifications to the
The Threat actor known as DoNot Team has been linked to a new Android malware as part of highly targeted cyber attacks. The artifacts in question, named Tanzeem (meaning "organization" in Urdu) and Tanzeem Update, were spotted in October and December 2024 by cybersecurity company Cyfirma. The apps in question have been found to incorporate identical functions, barring minor modifications to the |
Malware Threat Mobile | ★★★ | ||
| 2025-01-20 16:05:00 | Indian APT Group DONOT Misuses App for Intelligence Gathering (lien direct) | Android apps, linked to APT group DONOT, disguised as a chat platform for intelligence gathering
Android apps, linked to APT group DONOT, disguised as a chat platform for intelligence gathering |
Mobile | ★★★ | ||
| 2025-01-17 18:21:00 | Stories from the SOC: Caught in the Trap: Detecting and Defending Against RaccoonO365 Phishing Campaigns (lien direct) | Executive Summary
In September 2024, LevelBlue conducted a comprehensive threat hunt targeting artifacts indicative of Phishing-as-a-Service (PhaaS) activity across our monitored customer fleet. During the investigation, the LevelBlue Managed Detection and Response (MDR) Blue Team discovered a new PhaaS kit, now identified as RaccoonO365. The hunt confirmed true-positive compromises of Office 365 accounts, prompting swift customer notifications and guidance on remediation actions. The initial findings were handed over to the LevelBlue Labs Threat Intelligence team, which further uncovered additional infrastructure and deconstructed the kit’s JavaScript. This analysis provided critical insights into the features and capabilities of the emerging PhaaS kit.
Investigation
An anomalous artifact identified during a customer investigation was escalated to the Threat Hunting team for analysis. Further examination revealed that this artifact was linked to a specific Phishing-as-a-Service (PhaaS) platform known as \'RaccoonO365\'. Promoted as a cutting-edge phishing toolkit, it uses a custom User Agent, domains mimicking Microsoft O365 services, and Cloudflare infrastructure. Including these findings in our threat-hunting queries led to two additional discoveries tallying three total detections across the customer fleet. The two proactive detections identified events received, but no alarms were triggered in the involved customer\'s LevelBlue USM Anywhere instances. The third reactive detection was a confirmed business email compromise (BEC), detected after triggering an alarm. The threat actor utilized the user agent \'RaccoonO365\' prior to the business email compromise detection meaning there was a short period of unauthorized access that went undetected. Each occurrence was triaged individually, and investigations were conducted in all three customer instances referring to the observed activity. Partnering with LevelBlue Labs, a new Correlation Rule was created to search specifically for a RaccoonO365 user agent within associated logs. In addition, the LevelBlue Labs team uncovered additional structural and descriptive features attributed to RaccoonO365, which later was turned into a Pulse Indicator of Compromise (IOC) detection.
Expanded Investigation
Alarm and USMA log review
1. An unrelated potential business email compromise (BEC) alarm was received and triaged by the LevelBlue MDR SOC. The identified user utilized a foreign VPN to successfully log into customer’s Microsoft Office environment. A custom alarm rule was created due to its high probability of being a True Positive. While conducting their investigation, they uncovered a suspicious user agent related to the compromised email address –RaccoonO365.
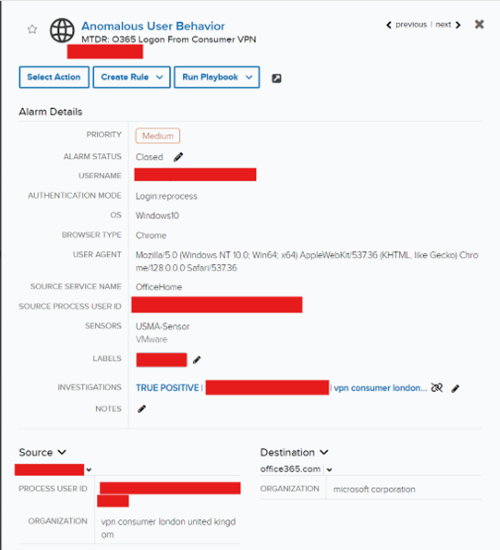 2. Information was passed off to LevelBlue Threat Hunters to conduct further internal and external research for the identified artifact.
2. Information was passed off to LevelBlue Threat Hunters to conduct further internal and external research for the identified artifact.
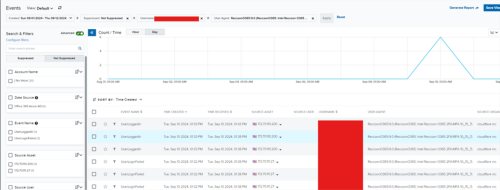 3. A dedicated threat hunter conducted a review of events including the subject user agent. Event logs were compared against each other and the successful logins provided additional key data points.
3. A dedicated threat hunter conducted a review of events including the subject user agent. Event logs were compared against each other and the successful logins provided additional key data points.
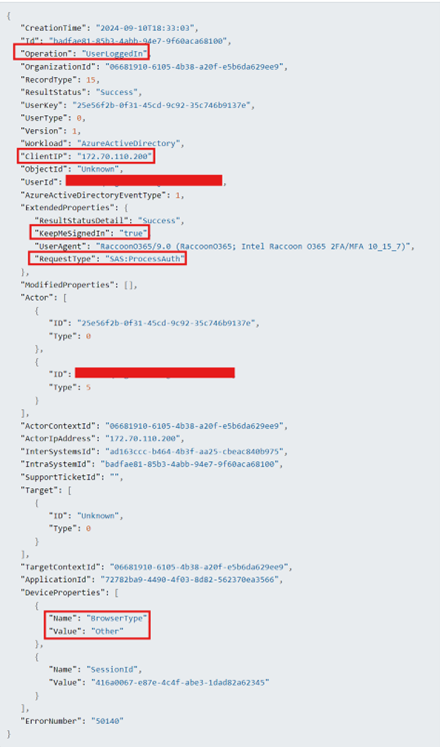 Shared Access Signature (SAS) authentication
"SAS authentication" refers to a method of user access control using a "Shared Access Signature" (SAS) token, which essentially grants temporary, limited access to specific resources within a cloud platform like Azure. This allows users to access data without directly sharing the full account access
Shared Access Signature (SAS) authentication
"SAS authentication" refers to a method of user access control using a "Shared Access Signature" (SAS) token, which essentially grants temporary, limited access to specific resources within a cloud platform like Azure. This allows users to access data without directly sharing the full account access |
Tool Threat Mobile Cloud | ★★★ | ||
| 2025-01-17 14:17:53 | How to delete all emails on your iPhone (lien direct) | […] | Mobile | ★★★ | ||
| 2025-01-17 10:50:12 | How to remove my mobile number from all websites (lien direct) | […] | Mobile | ★★ | ||
| 2025-01-15 18:18:13 | Issue with Amazon WorkSpaces, Amazon AppStream 2.0, and Amazon DCV (CVE-2025-0500 and CVE-2025-0501) (lien direct) | Publication Date: 2025/01/15 10:30AM PST
Description:
AWS identified two issues in specific versions of native clients for Amazon WorkSpaces, Amazon AppStream 2.0, and Amazon DCV. We have proactively communicated with customers regarding the end of support for these impacted versions.
CVE-2025-0500:
This issue applies to specific versions of native clients for Amazon WorkSpaces (when running Amazon DCV protocol), Amazon AppStream 2.0, and Amazon DCV, listed below. If leveraged, this issue could allow a bad actor to perform a man-in-the-middle attack, allowing them to access remote WorkSpaces, AppStream, or DCV sessions. We recommend customers upgrade to the versions with the fix to address this issue.
Affected versions:
Amazon WorkSpaces Windows client 5.20.0 or earlier, macOS client 5.20.0 or earlier, and Linux client 2024.1 or earlier.
Amazon AppStream 2.0 Windows client 1.1.1326 or earlier.
Amazon DCV Windows client 2023.1.8993 or earlier, macOS client 2023.1.6203 or earlier, and Linux client 2023.1.6203 or earlier for all supported Linux distributions.
Resolution:
This issue was fixed in specific versions of the Amazon WorkSpaces, Amazon AppStream 2.0, and Amazon DCV clients listed below. Upgrading to these or later versions remediates the issue.
Versions with the fix:
Amazon WorkSpaces Windows client 5.21.0 or later, macOS client 5.21.0 or later, and Linux client 2024.2 or later.
Amazon AppStream 2.0 Windows client 1.1.1332 or later.
Amazon DCV Windows client 2023.1.9127 or later, macOS client 2023.1.6703 or later, and Linux client 2023.1.6703 or later for all supported Linux distributions.
CVE-2025-0501:
The issue applies to specific versions of native clients for Amazon WorkSpaces (when running Amazon PCoIP protocol), listed below. If leveraged, this issue could allow a bad actor to perform a man-in-the-middle attack, allowing them to access remote WorkSpaces sessions. We recommend customers upgrade to the versions with the fix to address this issue.
Affected versions:
Amazon WorkSpaces Windows client 5.22.0 or earlier, macOS client 5.22.0 or earlier, Linux client 2024.5 or earlier, and Android client 5.0.0 or earlier.
Resolution:
This issue was fixed in specific versions of the Amazon WorkSpaces clients listed below. Upgrading to these or later versions remediates the issue.
Versions with the fix:
Amazon WorkSpaces Windows client 5.22.1 or later, macOS client 5.22.1 or later, Linux client 2024.6 or later, and Android client 5.0.1 or later.
References:
CVE-2025-0500
CVE-2025-0501
Please email aws-security@amazon.com with any security questions or concerns.
Publication Date: 2025/01/15 10:30AM PST Description: AWS identified two issues in specific versions of native clients for Amazon Wor |
Mobile | |||
| 2025-01-15 14:30:00 | The Best Time Management Apps: iOS, Android, and Desktop (lien direct) | Make the most of every 24 hours.
Make the most of every 24 hours. |
Mobile | ★★ | ||
| 2025-01-14 18:59:00 | 3 Tips for Eliminating Attack Surface Blind Spots (lien direct) | In today’s rapidly evolving digital landscape, security professionals face many challenges in protecting their organizations from cyber threats. One common problem is the persistence of attack surface blind spots, which can be exploited by attackers and prevent an organization’s ability to stay ahead of threats. For businesses that lack the resources or budget for a full-time, in-house security operations center (SOC) or that struggle to recruit and retain skilled staff, these blind spots can be even more challenging to address. Here are three tips to eliminate attack surface blind spots and strengthen your security posture. 1. Expand Visibility Across Your Attack Surface A common cause of attack surface blind spots is a lack of visibility across an organization’s IT infrastructure. Modern IT environments are diverse and complex, encompassing legacy systems, cloud services, mobile devices, third-party applications, and supply chain touchpoints. Without comprehensive visibility, it’s easy to miss exposures that could lead to significant vulnerabilities. How to Expand Visibility Discover and Categorize Assets: Regularly scanning and monitoring your IT environment with managed vulnerability services paired with managed detection and response (MDR) services ensure new assets are discovered promptly, even as new technology or supply chain touchpoints are added. With these services, you gain comprehensive discovery and categorization of known and unknown assets, applications, and workloads on-premises and in multi-cloud environments for endpoint, OT, IoT, SaaS applications, and other IT infrastructure. With categorization, your data will be enriched with information such as: Criticality of asset to the organization/business, location, maintenance Asset identity, IT address, asset group • Installed software, services that are running, and file integrity Open ports, vulnerabilities, or configuration issues Users and IT or regulatory policy violations Associated alarms and events Fortify Defenses: Using a combination of services, such as MDR with managed endpoint security (MES) and managed vulnerability services significantly expands attack surface visibility. The integration of these services with a centralized technology platform provides a unified view of your attack surface and enriched, extended data collection. You can validate security controls and identify exposures with regular pen testing through managed vulnerability services and complementary consulting services for red/purple team and risk assessments. Leverage Continuous Monitoring: Take advantage of managed security services. Managed services teams that work 24/7 in collaboration across multiple integrated platforms can proactively identify, prioritize, and mitigate or remediate exposures and vulnerabilities, as well as detect and investigate evolving and emerging threats more holistically across your attack surface. By expanding visibility, you’ll not only uncover blind spots but also validate security controls and establish a more proactive approach to identifying threats and managing your cyber risk. 2. Address Vulnerability Overload Through Prioritization Another big challenge for security teams is managing a high volume of vulnerabilities. Without context for prioritization, organizations may be wasting time and resources on vulnerabilities that pose little actual risk while leaving critical exposures unaddressed. How to Overcome Vulnerability Overload Prioritize by Risk and Exploitability: Partner with a security operations team that evaluates vulnerabilities based on their risk of exploitation and potential business impact. For example, LevelBlue integrates threat intelligence and asset criticality into vul | Tool Vulnerability Threat Mobile Industrial Cloud | ★★★ | ||
| 2025-01-14 16:15:06 | Un hacker a réussi à cracker le port USB-C de l\'iPhone (lien direct) | Alors mes petits fanboys d’Apple, vous qui pensiez que votre précieux iPhone était une forteresse imprenable, vous allez devoir racheter des sticks de cristaux de menthe car un chercheur en sécurité vient de réussir à pirater le fameux contrôleur USB-C de l’iPhone 15 et 16. Mais pas de panique, gardez votre iPhone bien au chaud dans votre poche de hipster, car je vais tout vous expliquer.
Pour les néophytes (et les possesseurs d’Android qui se demandent encore pourquoi on parle d’Apple), le contrôleur ACE3, introduit dans la chaîne d’approvisionnement d’Apple en 2023, est un petit composant très smart qui gère toutes les communications via le port USB-C de votre iPhone. C’est un peu comme le videur d’une boîte de nuit très branchouille : C’est lui qui décide qui entre, qui sort, et surtout comment. Plus techniquement, il s’agit d’un microcontrôleur complet qui gère non seulement la charge, mais aussi toute une pile USB connectée aux bus internes de l’appareil.
Alors mes petits fanboys d’Apple, vous qui pensiez que votre précieux iPhone était une forteresse imprenable, vous allez devoir racheter des sticks de cristaux de menthe car un chercheur en sécurité vient de réussir à pirater le fameux contrôleur USB-C de l’iPhone 15 et 16. Mais pas de panique, gardez votre iPhone bien au chaud dans votre poche de hipster, car je vais tout vous expliquer. Pour les néophytes (et les possesseurs d’Android qui se demandent encore pourquoi on parle d’Apple), le contrôleur ACE3, introduit dans la chaîne d’approvisionnement d’Apple en 2023, est un petit composant très smart qui gère toutes les communications via le port USB-C de votre iPhone. C’est un peu comme le videur d’une boîte de nuit très branchouille : C’est lui qui décide qui entre, qui sort, et surtout comment. Plus techniquement, il s’agit d’un microcontrôleur complet qui gère non seulement la charge, mais aussi toute une pile USB connectée aux bus internes de l’appareil. |
Mobile | ★★★★ | ||
| 2025-01-14 11:54:10 | Proofpoint Named a Leader in the 2025 Gartner® Magic Quadrant™ for Digital Communications Governance and Archiving Solutions (lien direct) | When you\'ve got a great thing going, why stop? I\'m pleased to announce that we have been recognized as a Leader. Gartner has named Proofpoint a Leader in the 2025 Magic Quadrant for Digital Communications Governance and Archiving Solutions (DCGA). This recognition by Gartner is exciting. And in our opinion, it gives us momentum as we expand our efforts at helping clients in this space. Two things stand out for me. First, our focus on connectors, which helps customers who are struggling to take control of and manage their diverse communication channels. And second, our focus on customers, which has been part of the Proofpoint DNA for longer than I\'ve been with the company. In this blog post, I want to talk more about why each focus area will help us do even greater things moving forward. Focus on connectors We agree wholeheartedly that the traditional compliance and archiving market has evolved into something much bigger. We even repositioned our Intelligent Compliance portfolio as Proofpoint Digital Communications Governance (DCG) to help us better communicate the discrete value we offer, the use cases we address and the positive outcomes that we help our customers achieve. Digital communications channels-like mobile, SMS, voice, video, virtual meetings, social media and messaging-have rapidly proliferated across organizations everywhere. And this has increased complexity, risk and non-compliance into the business. What you have today is something like a “digital swamp” that introduces more questions than answers for IT, legal and compliance teams. That\'s where Proofpoint can help. We can help you natively capture Microsoft 365 email as well as a wide variety of other digital communications channels including Microsoft Teams, Slack, Zoom and social media platforms like LinkedIn, Facebook and X. We keep a pulse on the market. And at the same time, we continue to listen closely to our customers. That helps us to plan our roadmap and make informed decisions on whether it makes better sense to build, partner or buy. Earlier this year, for example, we launched new native connectors to capture Microsoft OneDrive and SharePoint content in response to customer feedback. But we don\'t just connect all your channels, we also help you capture and store content to various downstream services. To that end, we have signed strategic partnerships that extend our capture capabilities to more than 80 data sources. Have requirements to capture WhatsApp? Text messages? Signal? Webex? NICE? TikTok? Let\'s talk. Today, we can capture content and store to your non-Proofpoint archive. We can improve visibility into your capture stream to reconcile what you believe you\'re storing with what is retained in your non-Proofpoint archive. We can capture and store social media to your non-Proofpoint archive. And we can automatically monitor and remediate non-compliant social profiles and engagement. Plus, we\'re ready whenever you\'re ready to migrate to Proofpoint\'s DCGA solution. Focus on customers I said this in 2022-Proofpoint focuses on driving a world-class customer experience. This was one of our key strategic initiatives in 2024, and it will be moving forward. Our customer-centricity differentiates Proofpoint from other vendors. And our efforts in this area are reflected in many statistics that we\'re proud to share. Year after year, our customer retention rate is more than 90% across all product lines, which is pretty remarkable. We have a 94% customer satisfaction (CSAT) rating (as of July 2024), which is based on surveys completed by customers and conducted by Proofpoint technical support. This further sets us apart from our competitors. In this year\'s report, I was proud to see Gartner recognize us based on our Completeness of Vision and Ability to Execute. We\'re thrilled to hear this and aspire for more recognitions in 2025. Proofpoint offers both depth and breadth I\'ve never been more excited and optimi | Threat Mobile Technical Commercial | ★★★ | ||
| 2025-01-11 21:03:20 | [Zero-day] (lien direct) | Researchers at Google Project Zero on Friday disclosed a now-patched zero-click vulnerability that could allow remote attackers to execute arbitrary code on Samsung devices without any user interaction.
The vulnerability tracked as CVE-2024-49415 (CVSS score: 8.1) is an out-of-bounds write issue in the saped_rec function of the libsaped.so library, a library of C2 media service responsible for audio playback. It affected the Monkey\'s Audio (APE) decoder used in Samsung\'s flagship Galaxy S23 and S24 devices running Android versions 12, 13, and 14.
“Out-of-bound write in libsaped.so prior to SMR Dec-2024 Release 1 allows remote attackers to execute arbitrary code. The patch adds proper input validation,” read the advisory for the flaw released in December 2024 as part of Samsung\'s monthly security updates.
How the attack could be performed?
Natalie Silvanovich, a Google Project Zero researcher who identified and reported the vulnerability to Samsung on September 21, 2024, said that the attack could be carried out by sending a malicious audio file that does not require any user involvement (zero-click), making it potentially dangerous.
The flaw occurred due to Samsung\'s handling of RCS (rich communication services) messages, specifically in how incoming audio messages are parsed and processed through the Google Messages app in Android. This setting is enabled by default on the Galaxy S23 and S24 models.
“The function saped_rec in libsaped.so writes to a dmabuf allocated by the C2 media service, which always appears to have size 0x120000. While the maximum blocksperframe value extracted by libsapedextractor is also limited to 0x120000, saped_rec can write up to 3 * blocksperframe bytes out, if the bytes per sample of the input is 24. This means that an APE file with a large blocksperframe size can substantially overflow this buffer,” Silvanovich wrote in her bug report.
“Note that this is a fully remote (0-click) bug on the Samsung S24 if Google Messages is configured for RCS (the default configuration on this device), as the transcription service decodes incoming audio before a user interacts with the message for transcription purposes.”
In a hypothetical attack scenario, an attacker can exploit the vulnerability by sending a specially crafted audio message on RCS-enabled devices, causing the device\'s media codec process (“samsung.software.media.c2”) to crash and open a way for further exploitation.
In addition to the above flaw, Samsung’s December 2024 update also fixed another vulnerability: CVE-2024-49413 (CVSS score: 7.1), involving the SmartSwitch app. This flaw allowed local attackers allowed local attackers to install malicious applications by exploiting insufficient cryptographic signature verification.
While Samsung has fixed the flaws, it is recommended that users update their RCS-enabled devices with the latest security updates. Additionally, it is advisable to disable RCS in Google Messages to reduce the risk of zero-click exploits further.
Researchers at Google Project Zero on Friday disclosed a now-patched zero-click vulnerability that could allow remote attackers to execute arbitrary code on Samsung devices without any user interaction. The vulnerability tracked as CVE-2024 |
Vulnerability Threat Mobile | ★★★ | ||
| 2025-01-10 16:27:17 | Apps That Are Spying on Your Location (lien direct) | 404 Media is reporting on all the apps that are spying on your location, based on a hack of the location data company Gravy Analytics:
The thousands of apps, included in hacked files from location data company Gravy Analytics, include everything from games like Candy Crush to dating apps like Tinder, to pregnancy tracking and religious prayer apps across both Android and iOS. Because much of the collection is occurring through the advertising ecosystem—not code developed by the app creators themselves—this data collection is likely happening both without users\' and even app developers\' knowledge...
404 Media is reporting on all the apps that are spying on your location, based on a hack of the location data company Gravy Analytics: The thousands of apps, included in hacked files from location data company Gravy Analytics, include everything from games like Candy Crush to dating apps like Tinder, to pregnancy tracking and religious prayer apps across both Android and iOS. Because much of the collection is occurring through the advertising ecosystem—not code developed by the app creators themselves—this data collection is likely happening both without users\' and even app developers\' knowledge... |
Hack Mobile | ★★★ | ||
| 2025-01-10 15:17:00 | Google Project Zero Researcher Uncovers Zero-Click Exploit Targeting Samsung Devices (lien direct) | Cybersecurity researchers have detailed a now-patched security flaw impacting Monkey\'s Audio (APE) decoder on Samsung smartphones that could lead to code execution.
The high-severity vulnerability, tracked as CVE-2024-49415 (CVSS score: 8.1), affects Samsung devices running Android versions 12, 13, and 14.
"Out-of-bounds write in libsaped.so prior to SMR Dec-2024 Release 1 allows remote
Cybersecurity researchers have detailed a now-patched security flaw impacting Monkey\'s Audio (APE) decoder on Samsung smartphones that could lead to code execution. The high-severity vulnerability, tracked as CVE-2024-49415 (CVSS score: 8.1), affects Samsung devices running Android versions 12, 13, and 14. "Out-of-bounds write in libsaped.so prior to SMR Dec-2024 Release 1 allows remote |
Vulnerability Threat Mobile | ★★★ | ||
| 2025-01-09 10:00:00 | Crypto is soaring, but so are threats: Here\\'s how to keep your wallet safe (lien direct) | As detections of cryptostealers surge across Windows, Android and macOS, it\'s time for a refresher on how to keep your bitcoin or other crypto safe
As detections of cryptostealers surge across Windows, Android and macOS, it\'s time for a refresher on how to keep your bitcoin or other crypto safe |
Mobile | ★★ | ||
| 2025-01-07 15:40:28 | Android patches several vulnerabilities in first security update of 2025 (lien direct) | >The bulletin identifies five critical remote code execution (RCE) vulnerabilities affecting the core components of Android\'s system.
>The bulletin identifies five critical remote code execution (RCE) vulnerabilities affecting the core components of Android\'s system. |
Vulnerability Mobile | ★★★ | ||
| 2025-01-06 21:12:00 | FireScam Android Spyware Campaign Poses \\'Significant Threat Worldwide\\' (lien direct) | A fake Telegram Premium app delivers information-stealing malware, in a prime example of the rising threat of adversaries leveraging everyday applications, researchers say.
A fake Telegram Premium app delivers information-stealing malware, in a prime example of the rising threat of adversaries leveraging everyday applications, researchers say. |
Malware Threat Mobile | ★★ | ||
| 2025-01-06 16:40:00 | FireScam Android Malware Poses as Telegram Premium to Steal Data and Control Devices (lien direct) | An Android information stealing malware named FireScam has been found masquerading as a premium version of the Telegram messaging app to steal data and maintain persistent remote control over compromised devices.
"Disguised as a fake \'Telegram Premium\' app, it is distributed through a GitHub.io-hosted phishing site that impersonates RuStore – a popular app store in the Russian Federation,"
An Android information stealing malware named FireScam has been found masquerading as a premium version of the Telegram messaging app to steal data and maintain persistent remote control over compromised devices. "Disguised as a fake \'Telegram Premium\' app, it is distributed through a GitHub.io-hosted phishing site that impersonates RuStore – a popular app store in the Russian Federation," |
Malware Mobile | ★★★ | ||
| 2025-01-06 16:31:14 | FireScam infostealer poses as Telegram Premium app to surveil Android devices (lien direct) | Once installed, it helps itself to your data like it\'s a free buffet Android malware dubbed FireScam tricks people into thinking they are downloading a Telegram Premium application that stealthily monitors victims\' notifications, text messages, and app activity, while stealing sensitive information via Firebase services.…
Once installed, it helps itself to your data like it\'s a free buffet Android malware dubbed FireScam tricks people into thinking they are downloading a Telegram Premium application that stealthily monitors victims\' notifications, text messages, and app activity, while stealing sensitive information via Firebase services.… |
Malware Mobile | ★★★ | ||
| 2025-01-06 14:10:10 | Vigilance.fr - Google Android | Pixel : multiples vulnérabilités de juillet 2023, analysé le 06/07/2023 (lien direct) | Un attaquant peut employer plusieurs vulnérabilités de Google Android | Pixel.
-
Vulnérabilités
Un attaquant peut employer plusieurs vulnérabilités de Google Android | Pixel. - Vulnérabilités |
Mobile | ★★ | ||
| 2025-01-06 14:10:10 | Vigilance.fr - Google Android | Pixel: multiple vulnerabilities if July 2023, analyzed on 06/07/2023 (lien direct) | An attacker can use several vulnerabilities of Google Android | Pixel.
-
Security Vulnerability
An attacker can use several vulnerabilities of Google Android | Pixel. - Security Vulnerability |
Vulnerability Mobile | ★★ | ||
| 2025-01-06 03:38:52 | FireScam Malware Campaign Highlights Rising Threat to Mobile Users (lien direct) | The ubiquity of mobile applications has created a perfect storm for bad actors, offering ample opportunities to exploit unsuspecting users. One of the latest instances is FireScam, a sophisticated malware that targets Android devices. Disguised as a fake “Telegram Premium” app, FireScam uses phishing websites to lure victims into downloading malware that infects their devices [...]
The ubiquity of mobile applications has created a perfect storm for bad actors, offering ample opportunities to exploit unsuspecting users. One of the latest instances is FireScam, a sophisticated malware that targets Android devices. Disguised as a fake “Telegram Premium” app, FireScam uses phishing websites to lure victims into downloading malware that infects their devices [...] |
Malware Threat Mobile | ★★★ | ||
| 2025-01-04 13:00:00 | New FireScam Infostealer Spyware Hits Android via Fake Telegram Premium (lien direct) | Researchers at Cyfirma have discovered FireScam, an Android malware disguised as \'Telegram Premium\' that steals data, monitors activity, and infiltrates devices. Learn about its distribution, functionality, and the impact on user privacy.
Researchers at Cyfirma have discovered FireScam, an Android malware disguised as \'Telegram Premium\' that steals data, monitors activity, and infiltrates devices. Learn about its distribution, functionality, and the impact on user privacy. |
Malware Mobile | ★★★ | ||
| 2025-01-04 10:16:26 | New FireScam Android data-theft malware poses as Telegram Premium app (lien direct) | A new Android malware named \'FireScam\' is being distributed as a premium version of the Telegram app via phishing websites on GitHub that mimick the RuStore, Russia\'s app market for mobile devices. [...]
A new Android malware named \'FireScam\' is being distributed as a premium version of the Telegram app via phishing websites on GitHub that mimick the RuStore, Russia\'s app market for mobile devices. [...] |
Malware Mobile | ★★★ | ||
| 2025-01-04 01:30:10 | Amazon worker – struck and shot in New Orleans terror attack – initially denied time off (lien direct) | Web giant now pledges full support A warehouse worker at an Amazon facility in Mobile, Alabama, who was struck by a truck and shot in the New Orleans New Year\'s Day deadly terror attack, was initially denied medical leave by the internet mega-giant, possibly due to an HR mix-up.…
Web giant now pledges full support A warehouse worker at an Amazon facility in Mobile, Alabama, who was struck by a truck and shot in the New Orleans New Year\'s Day deadly terror attack, was initially denied medical leave by the internet mega-giant, possibly due to an HR mix-up.… |
Mobile Medical | ★★★ | ||
| 2025-01-03 11:13:00 | Apple to Pay Siri Users $20 Per Device in Settlement Over Accidental Siri Privacy Violations (lien direct) | Apple has agreed to pay $95 million to settle a proposed class action lawsuit that accused the iPhone maker of invading users\' privacy using its voice-activated Siri assistant.
The development was first reported by Reuters.
The settlement applies to U.S.-based individuals current or former owners or purchasers of a Siri-enabled device who had their confidential voice communications with the
Apple has agreed to pay $95 million to settle a proposed class action lawsuit that accused the iPhone maker of invading users\' privacy using its voice-activated Siri assistant. The development was first reported by Reuters. The settlement applies to U.S.-based individuals current or former owners or purchasers of a Siri-enabled device who had their confidential voice communications with the |
Mobile | ★★★★ | ||
| 2025-01-03 11:10:00 | DDoS Disrupts Japanese Mobile Giant Docomo (lien direct) | Docomo has revealed a DDoS attack on Thursday took down key services
Docomo has revealed a DDoS attack on Thursday took down key services |
Mobile | ★★★★ | ||
| 2025-01-02 16:21:26 | Japan\\'s largest mobile carrier says cyberattack disrupted some services (lien direct) | Tokyo-based mobile carrier NTT Docomo said some of its web systems were disrupted by a distributed denial-of-service (DDoS) attack.
Tokyo-based mobile carrier NTT Docomo said some of its web systems were disrupted by a distributed denial-of-service (DDoS) attack. |
Mobile | ★★★ | ||
| 2025-01-01 21:26:40 | Vigilance.fr - Google Android | Pixel : multiples vulnérabilités d\'avril 2024, analysé le 01/04/2024 (lien direct) | Un attaquant peut employer plusieurs vulnérabilités de Google Android | Pixel.
-
Vulnérabilités
Un attaquant peut employer plusieurs vulnérabilités de Google Android | Pixel. - Vulnérabilités |
Mobile | ★★ | ||
| 2025-01-01 21:26:40 | Vigilance.fr - Google Android | Pixel: multiple vulnerabilities of April 2024, analyzed on 01/04/2024 (lien direct) | An attacker can use several vulnerabilities of Google Android | Pixel.
-
Security Vulnerability
An attacker can use several vulnerabilities of Google Android | Pixel. - Security Vulnerability |
Vulnerability Mobile | ★★ | ||
| 2024-12-31 20:28:31 | Inside FireScam: An Information Stealer with Spyware Capabilities (lien direct) | ## Snapshot
FireScam is a sophisticated Android malware distributed via phishing websites hosted on GitHub.io.
## Description
Posing as a “Telegram Premium” app, it mimics the RuStore app store to trick users into downloading a malicious APK dropper. Once installed, FireScam initiates a multi-stage infection process, deploying spyware that surveils the device extensively. It exfiltrates sensitive data, including messages, notifications, and e-commerce transactions, to Firebase Realtime Database endpoints.
Key capabilities of FireScam include monitoring notifications across multiple apps, capturing clipboard content, and logging device activity, such as screen state changes and user engagement. The malware also employs obfuscation techniques and sandbox detection mechanisms to evade security tools, ensuring persistence on compromised devices. Additionally, it utilizes Firebase for command-and-control communication and data exfiltration, further obscuring its malicious activities.
FireScam exploits dynamic broadcast receivers and permissions to gain backdoor access to sensitive device events. Its phishing website delivers a realistic Telegram login page via WebView to steal credentials. Advanced tactics like profiling the device environment and using WebSocket connections enhance its stealth and operational success.
## Recommendations
- Only install applications from trusted sources and official stores.
- If a device is no longer receiving updates, strongly consider replacing it with a new device.
- Use mobile solutions such as [Microsoft Defender for Endpoint on Android](https://learn.microsoft.com/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-android?view=o365-worldwide)to detect malicious applications
- Always keep Install unknown apps disabled on the Android device to prevent apps from being installed from unknown sources.
- Evaluate whether [Microsoft Defender for Internet of Things (IoT)](https://learn.microsoft.com/en-us/azure/defender-for-iot/organizations/overview) services are applicable to your IoT environment.
## Detections/Hunting Queries
### Microsoft Defender Antivirus
Microsoft Defender Antivirus detects threat components as the following malware:
- [Trojan:AndroidOS/Multiverze](https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Trojan:AndroidOS/Multiverze)
## References
[Inside FireScam: An Information Stealer with Spyware Capabilities](https://www.cyfirma.com/research/inside-firescam-an-information-stealer-with-spyware-capabilities/). CYFIRMA (accessed 2024-12-30)
## Copyright
**© Microsoft 2024**. All rights reserved. Reproduction or distribution of the content of this site, or any part thereof, without written permission of Microsoft is prohibited.
## Snapshot FireScam is a sophisticated Android malware distributed via phishing websites hosted on GitHub.io. ## Description Posing as a “Telegram Premium” app, it mimics the RuStore app store to trick users into downloading a malicious APK dropper. Once installed, FireScam initiates a multi-stage infection process, deploying spyware that surveils the device extensively. It exfiltrates sensitive data, including messages, notifications, and e-commerce transactions, to Firebase Realtime Database endpoints. Key capabilities of FireScam include monitoring notifications across multiple apps, capturing clipboard content, and logging device activity, such as screen state changes and user engagement. The malware also employs obfuscation techniques and sandbox detection mechanisms to evade security tools, ensuring persistence on compromised devices. Additionally, it utilizes Firebase for command-and-control communication and data exfiltration, further obscuring its malicious activities. FireScam exploits dynamic broadcast receivers and permissions to gain backdoor access to sensitive device events. Its phishing website delivers a realistic Tel |
Malware Tool Threat Mobile | ★★★ | ||
| 2024-12-30 13:22:42 | Why MFA is Good, but Not Good Enough: The Need for Defense-in-Depth to Combat MFA Bypass (lien direct) | Over the past decade multifactor authentication (MFA) has risen to become a cornerstone of modern cybersecurity. However, during that time as user authentication sophistication has improved, so have cybercriminal tactics. Just look at the rise of MFA bypass techniques. Despite the ability of attackers to get past MFA, beliefs about its near perfection persist. Recent Proofpoint research shows that almost half of all accounts that were taken over by bad actors had MFA configured. Yet 89% of security professionals consider MFA a complete protection against account takeover. Clearly, there\'s a disconnect. That\'s why a robust defense-in-depth approach is needed now more than ever. Layered security can help mitigate MFA bypass and reduce the likelihood of a significant breach that stems from an account takeover. In this blog post, we\'ll explore why MFA is not enough and give you some tips to better protect your organization. MFA bypass techniques MFA is effective because it requires users to authenticate with multiple factors. It combines something they know (typically their password) with something they have (an authenticator app or token) or with something they are (like a face scan). While this sounds very secure, threat actors have found multiple ways to bypass MFA. Many of these tactics are highly sophisticated: Phishing attacks. In these attacks, users are tricked by cybercriminals into entering MFA codes or their login credentials into websites that are controlled by the attackers. MFA fatigue attacks. After threat actors steal a user\'s password, they initiate a barrage of MFA push notifications. This can confuse users, leading them to approve the access request just to make the notifications stop. Session hijacking. With this technique, attackers steal session cookies post-authentication. This makes the preceding MFA-based authentication moot. SIM-swapping. This technique compromises SMS-based MFA by transferring the targets phone number to the attacker. To accomplish this, the threat actor needs to socially engineer the mobile carrier or have an insider at the organization. Pure social engineering. Most organizations have a way for remote workers to reset their passwords and MFA configurations without having to show up in person. However, without proper online identity verification the IT helpdesk can be socially engineered to hand over a spoofed employees\' credentials to the threat actor. Adversary-in-the-middle attacks. Attacker tools, like the specialized phishing kit Evilginx, intercepts session tokens. Those tokens are then relayed to legitimate services, which grant attackers access. Check out this demo of an adversary-in-the-middle attack enabled by Evilginx, which Proofpoint Account Takeover Protection can detect and stop. Why MFA alone is not enough No doubt, MFA adds a valuable layer of user authentication security. And this makes it harder for threat actors to break in. But the bypass techniques that are described above show why it\'s so risky to rely on any single security defense mechanism. The increasing prevalence of successful MFA bypass attacks just shows that determined attackers can adapt to overcome broadly deployed protections. While it might seem obvious, it\'s still important to always keep in mind that MFA should only be part of a larger security program. It\'s not a definitive defense. The whole point of defense-in-depth means that implementing additional layers of security reduces the likelihood of a successful attack, even if one layer is breached. Implementing a defense-in-depth strategy A defense-in-depth approach involves multiple, overlapping security measures. This creates redundancies and reduces an attacker\'s ability to exploit any vulnerabilities. Here\'s how organizations can bolster their defenses against MFA bypass: Strengthen endpoint protection. Deploy endpoint detection and response (EDR) tools to identify and mitig | Tool Vulnerability Threat Mobile Cloud | ★★ | ||
| 2024-12-23 09:30:00 | ICO Warns of Mobile Phone Festive Privacy Snafu (lien direct) | The Information Commissioner\'s Office has warned that millions of Brits don\'t know how to erase personal data from their old devices
The Information Commissioner\'s Office has warned that millions of Brits don\'t know how to erase personal data from their old devices |
Mobile | ★★★ | ||
| 2024-12-20 18:52:43 | (Déjà vu) WikiKit AiTM Phishing Kit: Where Links Tell Lies (lien direct) | #### Targeted Industries - Critical Manufacturing - Healthcare & Public Health ## Snapshot Researchers from TRAC Labs recently uncovered a phishing kit dubbed "WikiKit," which received its name for redirecting to Wikipedia pages when JavaScript is disabled or the phishing link is invalid. ## Description Launched in October 2024, WikiKit campaigns have been observed impacting multiple industries, including automotive, manufacturing, and healthcare. The phishing kit uses Jimdosite-hosted landing pages that mimic corporate branding and prompt users to click on a link labeled "Review Document Here," redirecting them to credential harvesting pages. Attackers exploit compromised corporate email accounts to distribute phishing links, sometimes disguising them as legitimate Salesforce redirects to increase user trust. Victims who interact with these phishing links encounter CAPTCHA checks before entering credentials, which are then validated and sent to the attackers\' servers. The phishing kit dynamically customizes pages with the victim\'s company logo and background, enhancing its legitimacy. WikiKit employs advanced techniques to evade detection, including tamper-proof JavaScript code that disrupts debugging attempts and hides non-default authentication methods. The attackers leverage stolen credentials to bypass multi-factor authentication and redirect victims to what appear to be legitimate Microsoft 365 or Outlook error pages. As of December 2024, the campaign continues to operate with consistent infrastructure and evasion tactics. ## Recommendations - Invest in advanced anti-phishing solutions that monitor incoming emails and visited websites. [Microsoft Defender for Office 365](https://learn.microsoft.com/microsoft-365/security/defender/microsoft-365-security-center-mdo) merges incident and alert management across email, devices, and identities, centralizing investigations for email-based threats. Organizations can also leverage web browsers that automatically [identify and block](https://learn.microsoft.com/deployedge/microsoft-edge-security-smartscreen) malicious websites, including those used in this phishing campaign. - [Require multifactor authentication (MFA).](https://learn.microsoft.com/microsoft-365/admin/security-and-compliance/set-up-multi-factor-authentication)While AiTM phishing attempts to circumvent MFA, implementation of MFA remains an essential pillar in identity security and is highly effective at stopping a variety of threats. - Leverage more secure implementations such as FIDO Tokens, or [Microsoft Authenticator](https://www.microsoft.com/security/mobile-authenticator-app) with passkey. Avoid telephony-based MFA methods to avoid risks associated with SIM-jacking. - For more granular control, enable conditional access policies. [Conditional access](https://learn.microsoft.com/entra/identity/conditional-access/overview) policies evaluate sign-in requests using additional identity driven signals like user or group membership, IP location information, and device status, among others, and are enforced for suspicious sign-ins. Organizations can protect themselves from attacks that leverage stolen credentials by enabling policies such as compliant devices or trusted IP address requirements. - Implement [continuous access evaluation](https://learn.microsoft.com/entra/identity/conditional-access/concept-continuous-access-evaluation). - Turn on [Safe Links](https://learn.microsoft.com/defender-office-365/safe-links-about) and [Safe Attachments](https://learn.microsoft.com/defender-office-365/safe-attachments-about) for Office 365. - Enable [Zero-hour auto purge (ZAP)](https://learn.microsoft.com/defender-office-365/zero-hour-auto-purge) in Office 365 to quarantine sent mail in response to newly acquired threat intelligence and retroactively neutralize malicious phishing, spam, or malware messages that have already been delivered to mailboxes. - Run endpoint detection and response [(EDR) in block mode](https://l | Spam Malware Tool Threat Mobile Medical | ★★★ | ||
| 2024-12-20 10:00:00 | Use the \\'Anti-AI\\' Camera Apps Zerocam and Hallide to Keep Your Photos Looking More Natural (lien direct) | It\'s still possible to just take normal-looking photos. Use these apps for Android and iOS to give your phone\'s camera a more natural eye.
It\'s still possible to just take normal-looking photos. Use these apps for Android and iOS to give your phone\'s camera a more natural eye. |
Mobile | ★★★ | ||
| 2024-12-20 01:01:31 | Phishing platform Rockstar 2FA trips, and “FlowerStorm” picks up the pieces (lien direct) | #### Targeted Geolocations - United States - Canada - United Kingdom #### Targeted Industries - Consumer Retail - Critical Manufacturing - Financial Services - Other business entities - Consulting Services ## Snapshot Researchers from Sophos released a report detailing the disruption of the prolific phishing-as-a-service (PaaS) platform Rockstar2FA and the surge from a similar PaaS platform, dubbed FlowerStorm. ## Description According to Sophos, Rockstar2FA\'s infrastructure suffered a significant technical failure in November 2024, with phishing pages and command-and-control Telegram channels going offline. This disruption was not due to a takedown but appears to stem from backend issues. Following Rockstar2FA\'s collapse, Sophos researchers began to observe an increase in activity from FlowerStorm. FlowerStorm shares many features with Rockstar2FA, such as the format of its phishing portal pages and the connection to its backend server. Both platforms show similarities in their HTML structure and domain registration patterns, suggesting a shared ancestry or operational overlap. However, FlowerStorm has introduced minor variations in its phishing methods, such as unique subdomain names and field responses. FlowerStorm users have primarily impacted users in North America and Europe, with the US accounting for 60% of observed attacks. The service industry, particularly organizations that offer engineering, construction, real estate, and legal services, have been heavily impacted. Despite its rapid adoption, FlowerStorm\'s operations have been marred by technical errors, providing researchers with valuable insights into its backend infrastructure. While direct links between Rockstar2FA and FlowerStorm remain unconfirmed by Sophos, their shared characteristics and operational trends hint at a potential connection. The decline of Rockstar2FA and the rise of FlowerStorm may reflect a strategic pivot, personnel changes, or disruptions in shared infrastructure. ## Recommendations - Invest in advanced anti-phishing solutions that monitor incoming emails and visited websites. [Microsoft Defender for Office 365](https://learn.microsoft.com/microsoft-365/security/defender/microsoft-365-security-center-mdo) merges incident and alert management across email, devices, and identities, centralizing investigations for email-based threats. Organizations can also leverage web browsers that automatically [identify and block](https://learn.microsoft.com/deployedge/microsoft-edge-security-smartscreen) malicious websites, including those used in this phishing campaign. - [Require multifactor authentication (MFA).](https://learn.microsoft.com/microsoft-365/admin/security-and-compliance/set-up-multi-factor-authentication)While AiTM phishing attempts to circumvent MFA, implementation of MFA remains an essential pillar in identity security and is highly effective at stopping a variety of threats. - Leverage more secure implementations such as FIDO Tokens, or [Microsoft Authenticator](https://www.microsoft.com/security/mobile-authenticator-app) with passkey. Avoid telephony-based MFA methods to avoid risks associated with SIM-jacking. - For more granular control, enable conditional access policies. [Conditional access](https://learn.microsoft.com/entra/identity/conditional-access/overview) policies evaluate sign-in requests using additional identity driven signals like user or group membership, IP location information, and device status, among others, and are enforced for suspicious sign-ins. Organizations can protect themselves from attacks that leverage stolen credentials by enabling policies such as compliant devices or trusted IP address requirements. - Implement [continuous access evaluation](https://learn.microsoft.com/entra/identity/conditional-access/concept-continuous-access-evaluation). - Turn on [Safe Links](https://learn.microsoft.com/defender-office-365/safe-links-about) and [Safe Attachment | Spam Malware Tool Threat Mobile Cloud Technical | ★★ | ||
| 2024-12-19 17:01:58 | BadBox malware botnet infects 192,000 Android devices despite disruption (lien direct) | The BadBox Android malware botnet has grown to over 192,000 infected devices worldwide despite a recent sinkhole operation that attempted to disrupt the operation in Germany. [...]
The BadBox Android malware botnet has grown to over 192,000 infected devices worldwide despite a recent sinkhole operation that attempted to disrupt the operation in Germany. [...] |
Malware Mobile | ★★ | ||
| 2024-12-19 14:10:00 | UAC-0125 Abuses Cloudflare Workers to Distribute Malware Disguised as Army+ App (lien direct) | The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed that a threat actor it tracks as UAC-0125 is leveraging Cloudflare Workers service to trick military personnel in the country into downloading malware disguised as Army+, a mobile app that was introduced by the Ministry of Defence back in August 2024 in an effort to make the armed forces go paperless.
Users who visit the
The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed that a threat actor it tracks as UAC-0125 is leveraging Cloudflare Workers service to trick military personnel in the country into downloading malware disguised as Army+, a mobile app that was introduced by the Ministry of Defence back in August 2024 in an effort to make the armed forces go paperless. Users who visit the |
Malware Threat Mobile | ★★ | ||
| 2024-12-19 13:59:26 | Android malware found on Amazon Appstore disguised as health app (lien direct) | A malicious Android spyware application named \'BMI CalculationVsn\' was discovered on the Amazon Appstore, masquerading as a simple health tool but stealing data from infected devices in the background. [...]
A malicious Android spyware application named \'BMI CalculationVsn\' was discovered on the Amazon Appstore, masquerading as a simple health tool but stealing data from infected devices in the background. [...] |
Malware Tool Mobile | ★★ | ||
| 2024-12-19 12:48:17 | New Mobile Phishing Targets Executives with Fake DocuSign Links (lien direct) | Cybercriminals are using advanced techniques to target executives with mobile-specific phishing attacks.
Cybercriminals are using advanced techniques to target executives with mobile-specific phishing attacks. |
Mobile | ★★ |
To see everything:
Our RSS (filtrered)
