What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-01-20 05:03:03 | Deloitte: What to expect with cloud computing, the supply chain and sustainability for 2022 (lien direct) | The report looks at four key areas, including everything from cloud computing to hybrid work environments. | Deloitte | |||
| 2022-01-20 05:03:00 | Deloitte: Some, but not all, chip shortages will ease in the second half of 2022 (lien direct) | The shortage has helped cement semiconductors as an essential industry on par with food and energy production, Deloitte said, but it isn't structured to support that criticality. | Deloitte Deloitte | |||
| 2022-01-19 17:00:02 | Deloitte launches new SaaS cyber threat detection and response platform (lien direct) | AWS, CrowdStrike, Exabeam, and Google Cloud Chronicle are operationalizing the new platform. | Threat | Deloitte | ||
| 2022-01-14 20:26:59 | Deloitte launches Dimension10 Studio to build metaverse experiences with AR, VR, IoT and 5G (lien direct) | Consulting firm will use lessons from running its own virtual space to help customers build training tools, apps and metaverse worlds. | Deloitte | |||
| 2021-12-16 11:00:03 | Deloitte: CFOs\' views on global economic conditions have dimmed (lien direct) | Their top priorities for 2022 are talent/labor, financial performance and growth, according to Deloitte's Q4 survey of Fortune 500 CFOs. | Deloitte | |||
| 2021-12-07 05:03:01 | Another chip shortage is only a matter of time. Here\'s how businesses can prepare (lien direct) | Shortages are more regular than we may realize, and it's time for the businesses making and using semiconductors to implement these five fixes, says Deloitte. | Deloitte | |||
| 2021-12-02 04:02:33 | Let there be light: Ensuring visibility across the entire API lifecycle (lien direct) | The following article is based on a webinar series on enterprise API security by Imvision, featuring expert speakers from IBM, Deloitte, Maersk, and Imvision discussing the importance of centralizing an organization's visibility of its APIs as a way to accelerate remediation efforts and improve the overall security posture. Centralizing security is challenging in today's open ecosystem When | Deloitte | |||
| 2021-12-01 15:28:55 | Fixed wireless access will creep further into broadband\'s territory in 2022 (lien direct) | 5G only makes up a small percentage of those connections now, but a CAGR of 88% by 2026 means it'll be the big driver of FWA's growth, says Deloitte. | Deloitte | |||
| 2021-12-01 15:10:00 | RISC-V\'s open chip processors expected to double in 2022, and double again in 2023 (lien direct) | The open chip standard will go from "one drop in the bucket to two," representing a small fraction of the overall ISA market but showing incredible growth, according to a new report from Deloitte. | Deloitte | |||
| 2021-12-01 05:03:07 | Deloitte\'s take on quantum computing: Great potential but hard to execute (lien direct) | Analysts say that the technology is not relevant for most companies despite millions of dollars of investment from governments and VCs over the last year. | Deloitte | |||
| 2021-12-01 05:03:05 | Deloitte: Don\'t rule out Wi-Fi 6 as a next-generation wireless network (lien direct) | 5G is not the only game in town, according to the firm in a prediction for 2022. | Deloitte | |||
| 2021-12-01 05:03:03 | Deloitte: How sensitive AI data may become more private and secure in 2022 (lien direct) | Technologies are available to better protect the data used in artificial intelligence, but they're not quite ready for prime time, says Deloitte. | Deloitte | |||
| 2021-12-01 05:03:00 | AI to see stricter regulatory scrutiny starting in 2022, predicts Deloitte (lien direct) | Discussions about regulating artificial intelligence will ramp up next year, followed by actual rules the following years, forecasts Deloitte. | Deloitte Deloitte | |||
| 2021-11-17 08:03:01 | Deloitte Fast 500: Medical device company takes the top spot but software continues to dominate the top 10 (lien direct) | Software companies take 7 of the top 10 spots on Deloitte's 2021 North America Technology Fast 500 list, but 3 medical and biotech companies take the other spots, and one of those is the winner. | Deloitte | |||
| 2021-10-27 04:02:00 | (Déjà vu) New Deloitte report explains how tech companies have to change to be more ethical (lien direct) | Tech companies have to rethink the software development process and other business practices to make ethics a higher priority. | Deloitte Deloitte | |||
| 2021-10-27 04:02:00 | New Deloitte report explains how Facebook and all tech companies have to change to be more ethical (lien direct) | Tech companies have to rethink the software development process and other business practices to make ethics a higher priority. | Deloitte Deloitte | |||
| 2021-10-26 21:21:10 | AI deployments: Is your organization a transformer, pathseeker, starter or underachiever? (lien direct) | AI-fueled organizations address strategy, operations, culture and change management and ecosystems, according to Deloitte's latest State of AI in the Enterprise report. | Deloitte | |||
| 2021-10-21 04:02:01 | How the semiconductor industry is transforming in the face of disruption and shortages (lien direct) | Change is afoot in the chip manufacturing industry, and COVID-19-induced supply chain shortages aren't the only thing to blame. Deloitte says this is how semiconductor companies can respond. | Deloitte Deloitte | |||
| 2021-10-19 08:00:51 | 5 Cybersecurity Barriers State Organizations Face (lien direct) | Deloitte and NASCIO study found five cybersecurity barriers against state and local government organizations' ability to improve their security posture. | Deloitte | |||
| 2021-09-13 13:27:00 | 5 ways to better prepare your organization for a ransomware attack (lien direct) | Most executives cite ransomware as their biggest security concern but few have run simulated attacks to prepare, says Deloitte. | Ransomware | Deloitte | ||
| 2021-08-30 17:49:52 | Deloitte: The top business use cases for AI in 6 consumer industries (lien direct) | While disparate, all focus on serving customers-and have a common set of current and future business issues, according to a new report from Deloitte AI Institute. | Deloitte Deloitte | |||
| 2021-06-22 13:47:47 | How millennials and Gen Zs were impacted by the pandemic (lien direct) | Stress, mental health, employment, income, climate change and systematic racism are top of mind, according to a Deloitte survey. | Deloitte Deloitte | |||
| 2021-06-16 17:03:00 | Deloitte Acquires Terbium Labs (lien direct) | Baltimore-based digital risk protection company Terbium Labs is acquired by Deloitte | Deloitte Deloitte | |||
| 2021-06-14 15:09:05 | 75% of CFOs are bullish on the North American economy (lien direct) | Tech leaders are optimistic about their companies' financial prospects, and 62% believe they will be better a year out, according to Deloitte's Q2 CFO Signals survey. | Guideline | Deloitte | ||
| 2021-06-09 04:01:03 | Pandemic lockdowns were a beta test for the future of connected tech, says Deloitte (lien direct) | A survey of consumers found that COVID-induced lockdowns tested the limits of our networks, smartphones and services. While largely successful, these forced changes also highlighted some weak spots. | Deloitte Deloitte | |||
| 2021-06-07 16:43:00 | CloudQuest Acquired by Deloitte (lien direct) | Deloitte snaps up Silicon Valley–based security posture management provider | Deloitte Deloitte | |||
| 2021-06-04 05:01:00 | Digital transformation explained (lien direct) |
This article was written by an independent guest author.
No matter what sector your organization does business in, you’ve probably heard the term digital transformation. In every industry, digital transformation is going to be critical to remain competitive and resilient.
But what does digital transformation mean? And how does cybersecurity fit in? Today’s organizations are facing an increasingly complex environment of securing everything attached to the network; applications, data, and endpoints.
What is digital transformation?
At its most basic definition, digital transformation (or DX) is the process of improving your business by leveraging the latest technologies and solutions.
Digital transformation harnesses third platform technologies - think cloud and data analytics, and acceleration technologies - think IoT and mobile apps to transform business operations.
The primary goals of digital transformation are to increase agility for customer responsiveness, flexibility to accommodate new ways of working, and scalability to help your business do more.
What’s driving digital transformation?
The main drivers of digital transformation are:
Skyrocketing data transmission speeds
Increased storage capacities
Expansion of mobile functionality
All these signs point to a rapid decrease of on-premises computing and storage.
With the cloud, the amount of time and resources spent on hardware maintenance and upkeep is drastically reduced because you no longer need to own, maintain, and upgrade these resources in your own data center.
Rebuffing the maintenance mindset, the preference for most IT departments is to spend more on innovation vs. the traditional “keep the lights on” tasks. However, because “turning the lights off” isn’t feasible, the bulk of IT budgets continue to be allocated to maintenance. A 2020 Deloitte Inisights report underscores the reality: the average IT department allocates over half its budget on maintenance but only 19 percent on innovation.
And according to a 2021 State of IT Spiceworks Ziff Davis study, updating outdated IT infrastructure is the number one factor driving IT budget increases — cited by 56% of organizations planning on growing IT spend.
Also driving cloud adoption is the need to address disaster recovery (DR). While DR has not been typically cost-effective for small to mid-sized businesses, many cloud vendors and providers offer DR solutions like DRaaS (Disaster Recovery as a Service) that address those challenges.
But perhaps the greatest driver of cloud adoption today is COVID-19. The pandemic’s disruption to the business landscape forced organizations to consider advanced technologies. The work from home or remote work model is here to stay, and the demand for software-as-a-service (SaaS) applications that allow teams to collaborate from anywhere is steadily increasing.
The main spheres of digital transformation
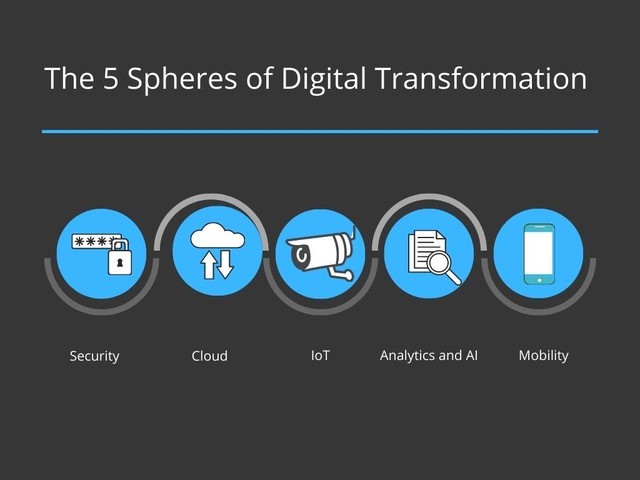 While one can argue that the components of digital transformation are numerous, we are highlighting five important spheres.
Security
As network access moves beyond the office perimeter to meet the demands of a remote workforce, robust security measures are required to maintain the confidentiality, integrity, and availability of corporate and customer data.
While one can argue that the components of digital transformation are numerous, we are highlighting five important spheres.
Security
As network access moves beyond the office perimeter to meet the demands of a remote workforce, robust security measures are required to maintain the confidentiality, integrity, and availability of corporate and customer data. |
Data Breach Threat | Deloitte | ||
| 2021-06-03 10:00:00 | (Déjà vu) Ransomware and Energy and Utilities (lien direct) | This is a blog series focused on providing energy and utility industries with helpful insights and practical, helpful information on cybersecurity. Intro The exponential growth of IoT devices in the energy and utilities industry has greatly increased focus on cybersecurity. Focus on cybersecurity across industries has increased recently, no doubt due to factors like COVID-19 forcing a jump in remote work. In 2020, we saw cybersecurity move from being a technical problem to a business issue. Along with the recognition that businesses really need to lead with a security-first mindset to be resilient, the CISO was elevated to a seat at the proverbial table as a true C-suite leader and trusted board advisor. Energy and utilities face unique challenges compared to other industries. According to McKinsey: “In our experience working with utility companies, we have observed three characteristics that make the sector especially vulnerable to contemporary cyberthreats. First is an increased number of threats and actors targeting utilities: nation-state actors seeking to cause security and economic dislocation, cybercriminals who understand the economic value represented by this sector, and hacktivists out to publicly register their opposition to utilities’ projects or broad agendas. The second vulnerability is utilities’ expansive and increasing attack surface, arising from their geographic and organizational complexity, including the decentralized nature of many organizations’ cybersecurity leadership. Finally the electric-power and gas sector’s unique interdependencies between physical and cyber infrastructure make companies vulnerable to exploitation, including billing fraud with wireless “smart meters,” the commandeering of operational-technology (OT) systems to stop multiple wind turbines, and even physical destruction.” Let’s look at one type of common and profitable attack that could impact energy and utility companies – ransomware. What is ransomware? Ransomware is exactly as the name implies – something valuable to your business is being kept from you until a ransom is paid for its return. In simple terms, ransomware is extortion. Ransomware, a form of malicious software, blocks you from accessing your computer systems or files until you pay the cyber adversary to allow you access to your information. The ransom is typically requested in crypto currency because of its anonymity and ease of online payment – this translates to no tracing of the origin or destination of the funds, a common tactic of cyber criminals. Knowingly infecting a system with ransomware and requesting payment to unlock the system is a crime. Law enforcement agencies recommend not paying the ransom associated with ransomware. The thought is that if the ransom is paid, you as the victim of ransomware are then identified as an easy target for further cybercrime and the ransomware attack is perpetuated against others. Who is the target of ransomware? Cyber criminals seek the path of least resistance in their targets and strike against businesses that are easy targets. Ransomware is a business and the perpetrators, like any good businessperson, are looking for a strong ROI. The C | Ransomware Malware Tool Vulnerability Guideline | Deloitte | ||
| 2021-06-03 10:00:00 | Ransomware and energy and utilities (lien direct) | This is a blog series focused on providing energy and utility industries with helpful insights and practical, helpful information on cybersecurity. Intro The exponential growth of IoT devices in the energy and utilities industry has greatly increased focus on cybersecurity. Focus on cybersecurity across industries has increased recently, no doubt due to factors like COVID-19 forcing a jump in remote work. In 2020, we saw cybersecurity move from being a technical problem to a business issue. Along with the recognition that businesses really need to lead with a security-first mindset to be resilient, the CISO was elevated to a seat at the proverbial table as a true C-suite leader and trusted board advisor. Energy and utilities face unique challenges compared to other industries. According to McKinsey: “In our experience working with utility companies, we have observed three characteristics that make the sector especially vulnerable to contemporary cyberthreats. First is an increased number of threats and actors targeting utilities: nation-state actors seeking to cause security and economic dislocation, cybercriminals who understand the economic value represented by this sector, and hacktivists out to publicly register their opposition to utilities’ projects or broad agendas. The second vulnerability is utilities’ expansive and increasing attack surface, arising from their geographic and organizational complexity, including the decentralized nature of many organizations’ cybersecurity leadership. Finally the electric-power and gas sector’s unique interdependencies between physical and cyber infrastructure make companies vulnerable to exploitation, including billing fraud with wireless “smart meters,” the commandeering of operational-technology (OT) systems to stop multiple wind turbines, and even physical destruction.” Let’s look at one type of common and profitable attack that could impact energy and utility companies – ransomware. What is ransomware? Ransomware is exactly as the name implies – something valuable to your business is being kept from you until a ransom is paid for its return. In simple terms, ransomware is extortion. Ransomware, a form of malicious software, blocks you from accessing your computer systems or files until you pay the cyber adversary to allow you access to your information. The ransom is typically requested in crypto currency because of its anonymity and ease of online payment – this translates to no tracing of the origin or destination of the funds, a common tactic of cyber criminals. Knowingly infecting a system with ransomware and requesting payment to unlock the system is a crime. Law enforcement agencies recommend not paying the ransom associated with ransomware. The thought is that if the ransom is paid, you as the victim of ransomware are then identified as an easy target for further cybercrime and the ransomware attack is perpetuated against others. Who is the target of ransomware? Cyber criminals seek the path of least resistance in their targets and strike against businesses that are easy targets. Ransomware is a business and the perpetrators, like any good businessperson, are looking for a strong ROI. The C | Ransomware Malware Tool Vulnerability Guideline | Deloitte | ||
| 2021-05-25 16:41:37 | 5 reasons organizations should be using enterprise business planning (lien direct) | CFOs who lead transformation efforts need to build resilient, long-term strategies, and EBP unites different functions to help make better decisions, according to Deloitte. | Guideline | Deloitte | ||
| 2021-05-18 15:33:54 | Private companies believe they are well on their way to greater resilience (lien direct) | The pace of digital transformation "exploded" for 69% of privately-held businesses, a new Deloitte survey finds. | Deloitte Deloitte | |||
| 2021-05-04 18:43:13 | After 25 years of trying to close the digital divide, challenges remain (lien direct) | A new report by Deloitte says striving for "broadband for all" would not only provide opportunities for the underserved but also would lead to an overall economic boom in the US. | Guideline | Deloitte Deloitte | ||
| 2021-04-29 20:20:09 | Deloitte and Kellogg School: Chief strategy officer role is evolving to drive digital transformation (lien direct) | In a post-pandemic world, technology is changing how CSOs perform their actual work, a new study finds. | Deloitte | |||
| 2021-04-23 14:30:00 | How Zero Trust Can Help Close the Cybersecurity Skills Gap (lien direct) | Using a zero trust model can help tackle some of the major challenges in cybersecurity today, including the skills gap. In July 2020, Deloitte surveyed webinar attendees about their organizations’ plans to implement a zero trust model. The poll found that four challenges had disrupted the efforts of many employers. A lack of skilled workers […] | Deloitte Deloitte | |||
| 2021-04-22 16:11:29 | Streaming services are a salve during the pandemic (lien direct) | Eighty-two percent of U.S. consumers subscribe to at least one paid streaming video service, Deloitte's 15th annual Digital Media Trends survey finds. | Deloitte | |||
| 2021-04-13 14:12:14 | 87% of global professionals consider contractors to be part of their workforce (lien direct) | A new study from MIT Sloan and Deloitte finds that only 28% are prepared to manage those external workers, and advocates for "workforce ecosystems." | Deloitte Deloitte | |||
| 2021-03-25 15:37:27 | Climate change efforts have stalled during the pandemic (lien direct) | 65% of organizations need to cut back on sustainability efforts-while acknowledging the world's at "a tipping point" to act, a new report from Deloitte finds. | Deloitte Deloitte | |||
| 2021-03-18 12:00:01 | CFOs are bullish on their companies\' financial prospects and the North American economy (lien direct) | While 41% of CFOs don't expect COVID-19 vaccination requirements for the return to work, some will encourage vaccinations, Deloitte's CFO Signals Q1 report found. | Deloitte | |||
| 2021-03-03 16:08:55 | Deloitte partnering with NVIDIA to launch artificial intelligence computing center (lien direct) | The Deloitte Center for AI Computing aims to deliver an accelerated platform to co-innovate with clients and expedite the development of AI applications. | Deloitte Deloitte | |||
| 2021-02-23 15:19:58 | Everything as a service, cloud on the rise to transform enterprise IT (lien direct) | Some 80% of adopters said the pandemic accelerated their organization's shift to XaaS to help them adapt and become nimbler, Deloitte survey finds. | Deloitte Deloitte | |||
| 2021-02-11 16:56:50 | 60% of CXOs are not confident leading through disruption (lien direct) | While 2020 gave some confidence in their organizations' resilience, a majority still don't feel completely ready for the next crisis, a Deloitte study finds. | Deloitte Deloitte | |||
| 2021-01-27 18:34:07 | Three critical tech considerations for 2021 (lien direct) | Upping your digital game, reskilling IT, and revamping supply chains should be on tap, according to a new Deloitte industry outlook report. | Deloitte Deloitte | |||
| 2021-01-25 17:48:00 | Deloitte Acquires Root9B (lien direct) | Assets of cyber-threat-hunting service provider Root9B acquired by Deloitte & Touche | Deloitte Deloitte | |||
| 2020-12-15 16:28:28 | The lines between corporate and tech strategy continue to blur (lien direct) | Strategic platforms with advanced analytics, automation, and AI are on tap for 2021, according to Deloitte. | Deloitte | |||
| 2020-12-15 11:00:00 | Why application-layer encryption is essential for securing confidential data (lien direct) | This blog was written by an independent guest blogger. Your business is growing at a steady rate, and you have big plans for the future. Then, your organization gets hit by a cyberattack, causing a massive data breach. Suddenly, your company’s focus is shifted to sending out letters to angry customers informing them of the incident - which is required by law in most states - and devising strategies to deal with the backlash. This is an all too common scenario for many businesses, and the unfortunate truth is that most organizations fail to adopt the correct cybersecurity procedures until after an attack. The good news is that with a proactive approach to protecting your data, these kinds of nightmares can be avoided. New technology is constantly providing hackers new opportunities to commit cybercrimes. Most organizations have encrypted their data whether it’s stored on the cloud or in a server provided by their web host, but this isn’t enough. Even properly encrypted disc level encryption is vulnerable to security breaches. In this article, we will discuss the weaknesses found in disc level encryption and why it’s best to ensure your data is encrypted at the application layer. We’ll also discuss the importance of active involvement from a cybersecurity team in the beginning stages of application development, and why developers need to have a renewed focus on cybersecurity in a “security-as-code” culture. The importance of application-layer security Organizations all too often have a piecemeal, siloed approach to security. Increasingly competitive tech environments have pushed developers into building new products at a pace cybersecurity experts sometimes can’t keep up with. This is why it’s becoming more common for vulnerabilities to be detected only after an application launches or a data breach occurs. Application layer encryption reduces surface area and encrypts data at the application level. That means if one application is compromised, the entire system does not become at risk. To reduce attack surfaces, individual users and third parties should not have access to encrypted data or keys. This leaves would-be cybercriminals with only the customer-facing end of the application for finding vulnerabilities, and this can be easily protected and audited for security. Building AI and application-layer security into code Application layer security and building security into the coding itself requires that your DevOps and cybersecurity experts work closely together to form a DevSecOps dream team. Developers are increasingly working hand-in-hand with cybersecurity experts from the very beginning stages of software development to ensure a “security-as-code” culture is upheld. However, there are some very interesting developments in AI that present opportunities to streamline this process. In fact, 78% of data scientists agree that artificial intelligence will have the greatest impact on data protection for the decade. Here are four ways AI is transforming application layer security: 1. Misuse detection or application security breach detection Also referred to as signature-based detection, AI systems alert teams when familiar attack patterns are noticed. | Data Breach Vulnerability Threat | Deloitte | ||
| 2020-12-10 11:30:01 | Deloitte predicts 2021 will feature radical workplace changes around the world (lien direct) | Going from surviving to thriving will be next year's key trend for the enterprise with businesses moving past the pandemic. | Deloitte | ★★★ | ||
| 2020-12-03 19:42:27 | 73% of organizations have embarked on a path to intelligent automation (lien direct) | "It seems that robots-although still bearing the burden of deep-seated human stigmas-have entered the mainstream," says Deloitte in a new report. | Deloitte | |||
| 2020-10-26 15:44:19 | The CFO\'s guide to data management (lien direct) | A new report by Deloitte offers tips for how to use advanced tools to solve data problems when systems don't talk to one another, without large-scale investment. | Deloitte | |||
| 2020-08-27 13:19:14 | 60% of CFOs rate the economy as bad and only 43% expect better conditions in a year (lien direct) | Deloitte's Q3 Signals survey of Fortune 500 CFOs also finds 60% are more optimistic about their own financial prospects than Q2's historic low of 11%. | Deloitte | |||
| 2020-07-20 18:51:34 | AI maturity: Survey details shift from the early-adopter phase into a new era (lien direct) | A new Deloitte report details some of the concerns and market factors influencing the future of AI adoption. | Deloitte |
To see everything:
Our RSS (filtrered)
