What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-02-20 03:21:02 | How do mail filters work? (lien direct) | Mail filters play a huge role in protecting organizations from cyberattacks. Even though their task is quite small, they are very important for an organization's ability to deter many malicious phishing and spam emails before delivery to a person's inbox. According to the IBM X-Force Threat Intelligence Index, 40% of attacks in the manufacturing industry are phishing attacks, and 1 in 3 employees are most likely to fall for a phishing scam. How do mail filters work? Email SPAM filters use a variety of techniques to protect mail delivery. A mail filter will take action, such as rejecting... | Spam Threat | ★★ | ||
| 2023-02-16 08:00:07 | Spam and phishing in 2022 (lien direct) | Statistics on spam and phishing with the key trends in 2022: two-stage spear phishing, hijacking of social network and instant messaging accounts, import substitution, and survey phishing. | Spam | ★★★ | ||
| 2023-02-14 14:00:00 | CyberheistNews Vol 13 #07 [Scam of the Week] The Turkey-Syria Earthquake (lien direct) |
 CyberheistNews Vol 13 #07 | February 14th, 2023
[Scam of the Week] The Turkey-Syria Earthquake
Just when you think they cannot sink any lower, criminal internet scum is now exploiting the recent earthquake in Turkey and Syria.
Less than 24 hours after two massive earthquakes claimed the lives of tens of thousands of people, cybercrooks are already piggybacking on the horrible humanitarian crisis. You need to alert your employees, friends and family... again.
Just one example are scammers that pose as representatives from a Ukrainian charity foundation that seeks money to help those affected by the natural disasters that struck in the early hours of Monday.
There are going to be a raft of scams varying from blood drives to pleas for charitable contributions for victims and their families. Unfortunately, this type of scam is the worst kind of phishbait, and it is a very good idea to inoculate people before they get suckered into falling for a scam like this.
I suggest you send the following short alert to as many people as you can. As usual, feel free to edit:
[ALERT] "Lowlife internet scum is trying to benefit from the Turkey-Syria earthquake. The first phishing campaigns have already been sent and more will be coming that try to trick you into clicking on a variety of links about blood drives, charitable donations, or "exclusive" videos.
"Don't let them shock you into clicking on anything, or open possibly dangerous attachments you did not ask for! Anything you receive about this recent earthquake, be very suspicious. With this topic, think three times before you click. It is very possible that it is a scam, even though it might look legit or was forwarded to you by a friend -- be especially careful when it seems to come from someone you know through email, a text or social media postings because their account may be hacked.
"In case you want to donate to charity, go to your usual charity by typing their name in the address bar of your browser and do not click on a link in any email. Remember, these precautions are just as important at the house as in the office, so tell your friends and family."
It is unfortunate that we continue to have to warn against the bad actors on the internet that use these tragedies for their own benefit. For KnowBe4 customers, we have a few templates with this topic in the Current Events. It's a good idea to send one to your users this week.
Blog post with links:https://blog.knowbe4.com/scam-of-the-week-the-turkey-syria-earthquake
CyberheistNews Vol 13 #07 | February 14th, 2023
[Scam of the Week] The Turkey-Syria Earthquake
Just when you think they cannot sink any lower, criminal internet scum is now exploiting the recent earthquake in Turkey and Syria.
Less than 24 hours after two massive earthquakes claimed the lives of tens of thousands of people, cybercrooks are already piggybacking on the horrible humanitarian crisis. You need to alert your employees, friends and family... again.
Just one example are scammers that pose as representatives from a Ukrainian charity foundation that seeks money to help those affected by the natural disasters that struck in the early hours of Monday.
There are going to be a raft of scams varying from blood drives to pleas for charitable contributions for victims and their families. Unfortunately, this type of scam is the worst kind of phishbait, and it is a very good idea to inoculate people before they get suckered into falling for a scam like this.
I suggest you send the following short alert to as many people as you can. As usual, feel free to edit:
[ALERT] "Lowlife internet scum is trying to benefit from the Turkey-Syria earthquake. The first phishing campaigns have already been sent and more will be coming that try to trick you into clicking on a variety of links about blood drives, charitable donations, or "exclusive" videos.
"Don't let them shock you into clicking on anything, or open possibly dangerous attachments you did not ask for! Anything you receive about this recent earthquake, be very suspicious. With this topic, think three times before you click. It is very possible that it is a scam, even though it might look legit or was forwarded to you by a friend -- be especially careful when it seems to come from someone you know through email, a text or social media postings because their account may be hacked.
"In case you want to donate to charity, go to your usual charity by typing their name in the address bar of your browser and do not click on a link in any email. Remember, these precautions are just as important at the house as in the office, so tell your friends and family."
It is unfortunate that we continue to have to warn against the bad actors on the internet that use these tragedies for their own benefit. For KnowBe4 customers, we have a few templates with this topic in the Current Events. It's a good idea to send one to your users this week.
Blog post with links:https://blog.knowbe4.com/scam-of-the-week-the-turkey-syria-earthquake
|
Ransomware Spam Threat Guideline | ChatGPT | ★★ | |
| 2023-02-08 21:15:10 | CVE-2023-25163 (lien direct) | Argo CD is a declarative, GitOps continuous delivery tool for Kubernetes. All versions of Argo CD starting with v2.6.0-rc1 have an output sanitization bug which leaks repository access credentials in error messages. These error messages are visible to the user, and they are logged. The error message is visible when a user attempts to create or update an Application via the Argo CD API (and therefor the UI or CLI). The user must have `applications, create` or `applications, update` RBAC access to reach the code which may produce the error. The user is not guaranteed to be able to trigger the error message. They may attempt to spam the API with requests to trigger a rate limit error from the upstream repository. If the user has `repositories, update` access, they may edit an existing repository to introduce a URL typo or otherwise force an error message. But if they have that level of access, they are probably intended to have access to the credentials anyway. A patch for this vulnerability has been released in version 2.6.1. Users are advised to upgrade. There are no known workarounds for this vulnerability. | Spam Tool Vulnerability | Uber | ||
| 2023-02-07 12:23:54 | Malware Delivered through Google Search (lien direct) | Criminals using Google search ads to deliver malware isn’t new, but Ars Technica declared that the problem has become much worse recently. The surge is coming from numerous malware families, including AuroraStealer, IcedID, Meta Stealer, RedLine Stealer, Vidar, Formbook, and XLoader. In the past, these families typically relied on phishing and malicious spam that attached Microsoft Word documents with booby-trapped macros. Over the past month, Google Ads has become the go-to place for criminals to spread their malicious wares that are disguised as legitimate downloads by impersonating brands such as Adobe Reader, Gimp, Microsoft Teams, OBS, Slack, Tor, and Thunderbird... | Spam Malware | ★★ | ||
| 2023-01-20 17:11:49 | Cyberbunker, Part 2 (lien direct) |
 Spamhaus's decision to add Cyberbunker to its list of Spam sources led the Stophaus coalition to initiate a DDoS attack later dubbed “The attack that almost broke the Internet.” The fallout from this attack led to Cyberbunker relocating to a bunker in Germany - but it was the involvement of an Irish drug lord known as 'The Penguin' that led to the bullet-proof hosting company's downfall.
Spamhaus's decision to add Cyberbunker to its list of Spam sources led the Stophaus coalition to initiate a DDoS attack later dubbed “The attack that almost broke the Internet.” The fallout from this attack led to Cyberbunker relocating to a bunker in Germany - but it was the involvement of an Irish drug lord known as 'The Penguin' that led to the bullet-proof hosting company's downfall.
|
Spam | ★★ | ||
| 2023-01-13 19:15:12 | CVE-2023-22489 (lien direct) | Flarum is a discussion platform for websites. If the first post of a discussion is permanently deleted but the discussion stays visible, any actor who can view the discussion is able to create a new reply via the REST API, no matter the reply permission or lock status. This includes users that don't have a validated email. Guests cannot successfully create a reply because the API will fail with a 500 error when the user ID 0 is inserted into the database. This happens because when the first post of a discussion is permanently deleted, the `first_post_id` attribute of the discussion becomes `null` which causes access control to be skipped for all new replies. Flarum automatically makes discussions with zero comments invisible so an additional condition for this vulnerability is that the discussion must have at least one approved reply so that `discussions.comment_count` is still above zero after the post deletion. This can open the discussion to uncontrolled spam or just unintentional replies if users still had their tab open before the vulnerable discussion was locked and then post a reply when they shouldn't be able to. In combination with the email notification settings, this could also be used as a way to send unsolicited emails. Versions between `v1.3.0` and `v1.6.3` are impacted. The vulnerability has been fixed and published as flarum/core v1.6.3. All communities running Flarum should upgrade as soon as possible. There are no known workarounds. | Spam Vulnerability | |||
| 2022-12-26 13:15:12 | CVE-2022-4120 (lien direct) | The Stop Spammers Security | Block Spam Users, Comments, Forms WordPress plugin before 2022.6 passes base64 encoded user input to the unserialize() PHP function when CAPTCHA are used as second challenge, which could lead to PHP Object injection if a plugin installed on the blog has a suitable gadget chain | Spam Guideline | |||
| 2022-12-12 18:15:11 | CVE-2022-3883 (lien direct) | The Block Bad Bots and Stop Bad Bots Crawlers and Spiders and Anti Spam Protection WordPress plugin before 7.24 does not have proper authorisation and CSRF in an AJAX action, allowing any authenticated users, such as subscriber to call it and install and activate arbitrary plugins from wordpress.org | Spam | |||
| 2022-12-08 13:00:37 | Explorations in the spam folder–Holiday Edition (lien direct) | We explore spam campaigns during this holiday season, demonstrating what can happen if someone actually clicks on links or open attachments in these unsolicited emails. | Spam | ★★★ | ||
| 2022-12-06 17:09:00 | Anomali Cyber Watch: Infected Websites Show Different Headers Depending on Search Engine Fingerprinting, 10 Android Platform Certificates Abused in the Wild, Phishing Group Impersonated Major UAE Oil (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, China, In-memory evasion, Infostealers, North Korea, Phishing, Ransomware, Search engine optimization, and Signed malware. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Chinese Gambling Spam Targets World Cup Keywords
(published: December 2, 2022)
Since 2018, a large-scale website infection campaign was affecting up to over 100,000 sites at a given moment. Infected websites, mostly oriented at audiences in China, were modified with additional scripts. Compromised websites were made to redirect users to Chinese gambling sites. Title and Meta tags on the compromised websites were changed to display keywords that the attackers had chosen to abuse search engine optimization (SEO). At the same time, additional scripts were switching the page titles back to the original if the visitor fingerprinting did not show a Chinese search engine from a preset list (such as Baidu).
Analyst Comment: Website owners should keep their systems updated, use unique strong passwords and introduce MFA for all privileged or internet facing resources, and employ server-side scanning to detect unauthorized malicious content. Implement secure storage for website backups.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Obfuscated Files or Information - T1027
Tags: SEO hack, HTML entities, Black hat SEO, Fraudulent redirects, Visitor fingerprinting, Gambling, Sports betting, World Cup, China, target-country:CN, JavaScript, Baidu, baiduspider, Sogou, 360spider, Yisou
Leaked Android Platform Certificates Create Risks for Users
(published: December 2, 2022)
On November 30, 2022, Google reported 10 different Android platform certificates that were seen actively abused in the wild to sign malware. Rapid7 researchers found that the reported signed samples are adware, so it is possible that these platform certificates may have been widely available. It is not shared how these platform certificates could have been leaked.
Analyst Comment: Malware signed with a platform certificate can enjoy privileged execution with system permissions, including permissions to access user data. Developers should minimize the number of applications requiring a platform certificate signature.
Tags: Android, Google, Platform certificates, Signed malware, malware-type:Adware
Blowing Cobalt Strike Out of the Water With Memory Analysis
(published: December 2, 2022)
The Cobalt Strike attack framework remains difficult to detect as it works mostly in memory and doesn’t touch the disk much after the initial loader stage. Palo Alto researchers analyzed three types of Cobalt Strike loaders: KoboldLoader which loads an SMB beacon, MagnetLoader loading an HTTPS beacon, and LithiumLoader loading a stager beacon. These beacon samples do not execute in normal sandbox environments and utilize in-me
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Chinese Gambling Spam Targets World Cup Keywords
(published: December 2, 2022)
Since 2018, a large-scale website infection campaign was affecting up to over 100,000 sites at a given moment. Infected websites, mostly oriented at audiences in China, were modified with additional scripts. Compromised websites were made to redirect users to Chinese gambling sites. Title and Meta tags on the compromised websites were changed to display keywords that the attackers had chosen to abuse search engine optimization (SEO). At the same time, additional scripts were switching the page titles back to the original if the visitor fingerprinting did not show a Chinese search engine from a preset list (such as Baidu).
Analyst Comment: Website owners should keep their systems updated, use unique strong passwords and introduce MFA for all privileged or internet facing resources, and employ server-side scanning to detect unauthorized malicious content. Implement secure storage for website backups.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Obfuscated Files or Information - T1027
Tags: SEO hack, HTML entities, Black hat SEO, Fraudulent redirects, Visitor fingerprinting, Gambling, Sports betting, World Cup, China, target-country:CN, JavaScript, Baidu, baiduspider, Sogou, 360spider, Yisou
Leaked Android Platform Certificates Create Risks for Users
(published: December 2, 2022)
On November 30, 2022, Google reported 10 different Android platform certificates that were seen actively abused in the wild to sign malware. Rapid7 researchers found that the reported signed samples are adware, so it is possible that these platform certificates may have been widely available. It is not shared how these platform certificates could have been leaked.
Analyst Comment: Malware signed with a platform certificate can enjoy privileged execution with system permissions, including permissions to access user data. Developers should minimize the number of applications requiring a platform certificate signature.
Tags: Android, Google, Platform certificates, Signed malware, malware-type:Adware
Blowing Cobalt Strike Out of the Water With Memory Analysis
(published: December 2, 2022)
The Cobalt Strike attack framework remains difficult to detect as it works mostly in memory and doesn’t touch the disk much after the initial loader stage. Palo Alto researchers analyzed three types of Cobalt Strike loaders: KoboldLoader which loads an SMB beacon, MagnetLoader loading an HTTPS beacon, and LithiumLoader loading a stager beacon. These beacon samples do not execute in normal sandbox environments and utilize in-me |
Spam Malware Tool Threat Medical | APT 38 | ★★★ | |
| 2022-12-06 14:30:00 | CyberheistNews Vol 12 #49 [Keep An Eye Out] Beware of New Holiday Gift Card Scams (lien direct) |
 CyberheistNews Vol 12 #49 | December 6th, 2022
[Keep An Eye Out] Beware of New Holiday Gift Card Scams
By Roger A. Grimes
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, easy to use, easy to gift, usually allow the receiver to pick just what they want, and are often received as a reward for doing something.
The gift card market is estimated in the many hundreds of BILLIONS of dollars. Who doesn't like to get a free gift card? Unfortunately, scammers often use gift cards as a way to steal value from their victims. There are dozens of ways gift cards can be used by scammers to steal money.
Roger covers these three scams in a short [VIDEO] and in detail on the KnowBe4 blog:
You Need to Pay a Bill Using Gift Cards
Maliciously Modified Gift Cards in Stores
Phish You for Information to Supposedly Get a Gift Card
Blog post with 2:13 [VIDEO] and links you can share with your users and family:https://blog.knowbe4.com/beware-of-holiday-gift-card-scams
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, December 7 @ 2:00 PM (ET), for a live demo of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
NEW! KnowBe4 Mobile Learner App - Users Can Now Train Anytime, Anywhere!
NEW! Security Culture Benchmarking feature lets you compare your organization's security culture with your peers
NEW! AI-Driven phishing and training recommendations for your end users
Did You Know? You can upload your own training video and SCORM modules into your account for home workers
Active Directory or SCIM Integration to easily upload user data, eliminating the need to manually manage user changes
Find out how 50,000+ organizations have mobilized their end-users as their human firewall.
Date/Time: TOMORROW, Wednesday, December 7 @ 2:00 PM (ET)
Save My Spot!https://event.on24.com/wcc/r/3947028/0273119CCBF116DBE42DF81F151FF99F?partnerref=CHN3
CyberheistNews Vol 12 #49 | December 6th, 2022
[Keep An Eye Out] Beware of New Holiday Gift Card Scams
By Roger A. Grimes
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, easy to use, easy to gift, usually allow the receiver to pick just what they want, and are often received as a reward for doing something.
The gift card market is estimated in the many hundreds of BILLIONS of dollars. Who doesn't like to get a free gift card? Unfortunately, scammers often use gift cards as a way to steal value from their victims. There are dozens of ways gift cards can be used by scammers to steal money.
Roger covers these three scams in a short [VIDEO] and in detail on the KnowBe4 blog:
You Need to Pay a Bill Using Gift Cards
Maliciously Modified Gift Cards in Stores
Phish You for Information to Supposedly Get a Gift Card
Blog post with 2:13 [VIDEO] and links you can share with your users and family:https://blog.knowbe4.com/beware-of-holiday-gift-card-scams
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, December 7 @ 2:00 PM (ET), for a live demo of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
NEW! KnowBe4 Mobile Learner App - Users Can Now Train Anytime, Anywhere!
NEW! Security Culture Benchmarking feature lets you compare your organization's security culture with your peers
NEW! AI-Driven phishing and training recommendations for your end users
Did You Know? You can upload your own training video and SCORM modules into your account for home workers
Active Directory or SCIM Integration to easily upload user data, eliminating the need to manually manage user changes
Find out how 50,000+ organizations have mobilized their end-users as their human firewall.
Date/Time: TOMORROW, Wednesday, December 7 @ 2:00 PM (ET)
Save My Spot!https://event.on24.com/wcc/r/3947028/0273119CCBF116DBE42DF81F151FF99F?partnerref=CHN3
|
Ransomware Data Breach Spam Hack Tool Guideline | ★★★ | ||
| 2022-11-28 12:36:18 | Ukraine Themed Twitter Spam Pushing iOS Scareware, (Mon, Nov 28th) (lien direct) | With the expansion of Russia&#;x26;#;39;s invasion of Ukraine in February, Ukraine has made heavy use of social media to demonstrate die ability of the Ukrainian armed forces to repulse the attack. Ukraine often shares video clips showing attacks against Russian troops from drones or action camera footage from the front lines. These videos have been widely distributed, and various social media channels have shared them to build an audience for themselves. | Spam | ★★ | ||
| 2022-11-25 00:42:22 | Auto-Publishing and Auto-Reporting Programs for Blog Posts (lien direct) | Spam programs are illegal programs according to the ACT ON PROMOTION OF INFORMATION AND COMMUNICATIONS NETWORK UTILIZATION AND INFORMATION PROTECTION. The ASEC analysis team previously published a blog post about a spam program sold as a marketing program. Today, we will introduce a program similar to the spam program covered in the past. The file collected under the filename of ‘Naver Blog Report Program.exe’ was developed with C#, just like the spam program covered in the previous blog post. Its... | Spam | |||
| 2022-11-24 00:30:00 | GMX : Black Friday, jusqu\'à 20 % de spam en plus (lien direct) | GMX : Black Friday, jusqu'à 20 % de spam en plus Le fournisseur de messagerie GMX enregistre actuellement une augmentation d'environ 20 % du nombre de spams et d'attaques par hameçonnage pendant la semaine du Black Friday. Le " vendredi noir " et le Cyber Monday sont la haute saison pour les chasseurs de bonnes affaires sur l'internet. La prudence de réagir rapidement aux offres avantageuses diminue. Les criminels en ligne en profitent sans scrupules : l'hameçonnage des services de colis et les faux bons d'achat sont des escroqueries particulièrement fréquentes. - Points de Vue | Spam | |||
| 2022-11-17 14:30:00 | More Than Half of Black Friday Spam Emails Are Scams (lien direct) | New research analyzes email scam techniques in the build-up to this year's Black Friday | Spam | |||
| 2022-11-16 03:26:00 | Anomali Cyber Watch: Amadey Bot Started Delivering LockBit 3.0 Ransomware, StrelaStealer Delivered by a HTML/DLL Polyglot, Spymax RAT Variant Targeted Indian Defense, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, DDoS, Infostealers, Maldocs, Phishing, Ransomware, and Wipers. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
KmsdBot: The Attack and Mine Malware
(published: November 10, 2022)
KmsdBot is a cryptominer written in GO with distributed denial-of-service (DDoS) functionality. This malware was performing DDoS attacks via either Layer 4 TCP/UDP packets or Layer 7 HTTP consisting of GET and POST. KmsdBot was seen performing targeted DDoS attacks against the gaming industry, luxury car manufacturers, and technology industry. The malware spreads by scanning for open SSH ports and trying a list of weak username and password combinations.
Analyst Comment: Network administrators should not use weak or default credentials for servers or deployed applications. Keep your systems up-to-date and use public key authentication for your SSH connections.
MITRE ATT&CK: [MITRE ATT&CK] Network Denial of Service - T1498 | [MITRE ATT&CK] Resource Hijacking - T1496
Tags: detection:KmsdBot, SSH, Winx86, Arm64, mips64, x86_64, malware-type:DDoS, malware-type:Cryptominer, xmrig, Monero, Golang, target-industry:Gaming, target-industry:Car manufacturing, target-industry:Technology, Layer 4, Layer 7
Massive ois[.]is Black Hat Redirect Malware Campaign
(published: November 9, 2022)
Since September 2022, a new WordPress malware redirects website visitors via ois[.]is. To conceal itself from administrators, the redirect will not occur if the wordpress_logged_in cookie is present, or if the current page is wp-login.php. The malware infects .php files it finds – on average over 100 files infected per website. A .png image file is initiating a redirect using the window.location.href function to redirect to a Google search result URL of a spam domain of actors’ choice. Sucuri researchers estimate 15,000 affected websites that were redirecting visitors to fake Q&A sites.
Analyst Comment: WordPress site administrators should keep their systems updated and secure the wp-admin administrator panel with 2FA or other access restrictions. If your site was infected, perform a core file integrity check, query for any files containing the same injection, and check any recently modified or added files.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190
Tags: file-type:PHP, SEO poisoning, WordPress, Google Search, Google Ads
LockBit 3.0 Being Distributed via Amadey Bot
(published: November 8, 2022)
Discovered in 2018, Amadey Bot is a commodity malware that functions as infostealer and loader. Ahnlab researchers detected a new campaign where it is used to deliver the LockBit 3.0 ransomware. It is likely a part of a larger 2022 campaign delivering LockBit to South Korean users. The actors used phishing attachments with two variants of Amadey B
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
KmsdBot: The Attack and Mine Malware
(published: November 10, 2022)
KmsdBot is a cryptominer written in GO with distributed denial-of-service (DDoS) functionality. This malware was performing DDoS attacks via either Layer 4 TCP/UDP packets or Layer 7 HTTP consisting of GET and POST. KmsdBot was seen performing targeted DDoS attacks against the gaming industry, luxury car manufacturers, and technology industry. The malware spreads by scanning for open SSH ports and trying a list of weak username and password combinations.
Analyst Comment: Network administrators should not use weak or default credentials for servers or deployed applications. Keep your systems up-to-date and use public key authentication for your SSH connections.
MITRE ATT&CK: [MITRE ATT&CK] Network Denial of Service - T1498 | [MITRE ATT&CK] Resource Hijacking - T1496
Tags: detection:KmsdBot, SSH, Winx86, Arm64, mips64, x86_64, malware-type:DDoS, malware-type:Cryptominer, xmrig, Monero, Golang, target-industry:Gaming, target-industry:Car manufacturing, target-industry:Technology, Layer 4, Layer 7
Massive ois[.]is Black Hat Redirect Malware Campaign
(published: November 9, 2022)
Since September 2022, a new WordPress malware redirects website visitors via ois[.]is. To conceal itself from administrators, the redirect will not occur if the wordpress_logged_in cookie is present, or if the current page is wp-login.php. The malware infects .php files it finds – on average over 100 files infected per website. A .png image file is initiating a redirect using the window.location.href function to redirect to a Google search result URL of a spam domain of actors’ choice. Sucuri researchers estimate 15,000 affected websites that were redirecting visitors to fake Q&A sites.
Analyst Comment: WordPress site administrators should keep their systems updated and secure the wp-admin administrator panel with 2FA or other access restrictions. If your site was infected, perform a core file integrity check, query for any files containing the same injection, and check any recently modified or added files.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190
Tags: file-type:PHP, SEO poisoning, WordPress, Google Search, Google Ads
LockBit 3.0 Being Distributed via Amadey Bot
(published: November 8, 2022)
Discovered in 2018, Amadey Bot is a commodity malware that functions as infostealer and loader. Ahnlab researchers detected a new campaign where it is used to deliver the LockBit 3.0 ransomware. It is likely a part of a larger 2022 campaign delivering LockBit to South Korean users. The actors used phishing attachments with two variants of Amadey B |
Ransomware Spam Malware Tool Threat | |||
| 2022-11-14 21:30:35 | Emotet Distributed Through U.S. Election Themed Link Files (lien direct) | FortiGuard Labs has discovered that Emotet was recently delivered through an archive file that has a file name targeting those interested in the U.S. midterm elections. The archive file is "US midterm elections The six races that could decide the US Senate.zip" that has a link file with the same name, which leads to Emotet.Why is this Significant?This is significant because Emotet is trying to leverage the interest of the U.S. midterm elections for infection. While FortiGuard Labs has not observed the infection vector, the file name "US midterm elections The six races that could decide the US Senate.zip" was likely distributed via emails. "The six races" likely refers to Arizona, Georgia, Michigan, Nevada, Pennsylvania, and Wisconsin where Democrats and Republican are expected to have close race in the elections, which gives better chance that recipients will open the archive contents. Emotets' modus operandi includes distribution via malicious spam campaigns and thread hijacking of emails.What's in "US midterm elections The six races that could decide the US Senate.zip"?The zip file contains a link file named "US midterm elections The six races that could decide the US Senate.lnk". When the link file is executed, it drops a further script in %tmp% that will attempt to cycle through several URLs to download a Emotet DLL.The downloaded Emotet connects to C2 server and will likely deliver additional malware.FortiGuard Labs discovered that the same script is present in other link files "New York Election news and updates....lnk" and "Amazon warns of slower sales as economy weakens.lnk" that were submitted to VirusTotal at the end of October and beginning of November respectively.What is the Status of Protection?FortiGuard Labs provides the following AV signatures for the archive and link file involved in the attack:• LNK/Agent.AMY!tr.dldr• PossibleThreat.PALLAS.HC2 address is blocked by FortiGuard Webfiltering Client. | Spam Guideline | |||
| 2022-11-11 11:55:16 | Malware Campaign Redirects 15,000 Sites (lien direct) | It has been reported that security researchers have spotted an intriguing malware campaign designed to increase the search engine rankings of spam websites under the control of threat actors. | Spam Malware Threat | |||
| 2022-10-27 10:00:00 | 11 Cybersecurity investments you can make right now (lien direct) | This blog was written by an independent guest blogger. The average cost of a data breach will continue to rise, which means companies need to start planning accordingly. To protect your business, you need to invest in cybersecurity. Here are 11 areas you should focus on. Cyber insurance Cyber insurance is designed to protect businesses from the financial repercussions of a cyber-attack. It can cover costs such as business interruption, data recovery, legal expenses, and reputational damage. It is increasingly common across industries and at companies of all sizes, even small businesses, which have become a growing target of cybercriminals. Cyber insurance has also become a new compliance requirement in many industries, including healthcare, finance, and retail. In the event of a data breach, companies are often required to notify their customers and partners, which can be costly. Cyber insurance can help cover these expenses. Employee training Employees are often the weakest link in a company's cybersecurity defenses. They may not be aware of the latest cyber threats or how to protect themselves from them. That's why it's important to provide employees with regular training on cybersecurity risks and best practices. There are many different types of employee training programs available, ranging from in-person seminars to online courses. Some companies even offer financial incentives for employees who complete training programs. In the remote work era, employee education also increasingly means arming remote workers with knowledge that will keep company data safe while they are working on networks that might not be well secured. This is especially the case if you know people are connecting via public networks at cafes, co-working spaces, and airports. Endpoint security Endpoints are the devices that connect to a network, such as laptops, smartphones, and tablets. They are also a common entry point for cyber-attacks. That's why it's important to invest in endpoint security, which includes solutions such as antivirus software, firewalls, and encryption. You can invest in endpoint security by purchasing it from a vendor or by implementing it yourself. There are also many free and open-source solutions available. Make sure you test any endpoint security solution before deploying it in your environment. Identity and access management Identity and access management (IAM) is a process for managing user identities and permissions. It can be used to control who has access to what data and resources, and how they can use them. IAM solutions often include features such as Single Sign-On (SSO), which allows users to access multiple applications with one set of credentials, and two-factor authentication (2FA), which adds an extra layer of security. IAM solutions can be deployed on-premises or in the cloud. They can also be integrated with other security solutions, such as firewalls and intrusion detection systems. Intrusion detection and prevention Intrusion detection and prevention systems (IDPS) are designed to detect and prevent cyber-attacks. They work by monitoring network traffic for suspicious activity and blocking or flagging it as needed. IDPS solutions can be deployed on-premises or in the cloud. There are many different types of IDPS solutions available, ranging from simple network-based solutions to more sophisticated host-based ones. Make sure you choose a solution that is right for your environment and needs. Security information and event management Security information and event management (SIEM) solutions are designed to collect and analyze data from a variety of security | Data Breach Spam Malware Vulnerability Patching | |||
| 2022-10-26 23:52:48 | FormBook Malware Being Distributed as .NET (lien direct) | The FormBook malware that was recently detected by a V3 software had been downloaded to the system and executed while the user was using a web browser. FormBook is an info-stealer that aims to steal the user’s web browser login information, keyboard input, clipboard, and screenshots. It targets random individuals, and is usually distributed through spam mails or uploaded to infiltrated websites. FormBook operates by injecting into a running process memory, and the targets of injection are explorer.exe and arbitrary... | Spam Malware | |||
| 2022-10-25 17:15:56 | CVE-2022-3302 (lien direct) | The Spam protection, AntiSpam, FireWall by CleanTalk WordPress plugin before 5.185.1 does not validate ids before using them in a SQL statement, which could lead to SQL injection exploitable by high privilege users such as admin | Spam Guideline | ★★★ | ||
| 2022-10-20 13:36:00 | Threat Hunting: Eight Tactics to Accelerating Threat Hunting (lien direct) | One of the more significant headaches in cyber security is the overuse of buzzwords and acronyms and the overlapping mutations of what they mean. Cyber threat Hunting has become one of those phrases, but it has gained clarity over the last few years as organizations strived to become more proactive. So what is threat hunting? Depending on who you ask, you may get somewhat different answers to the same question. Cyber threat hunting is a proactive approach to detecting suspicious activity from known or unknown, remediated, or unaddressed cyber threats within an organization’s networks. It involves finding malware such as viruses, Trojans, adware, spyware, ransomware, worms, bots, and botnets. The goal is for security analysts to find these threats before they cause damage to systems and data. It’s similar to how fire departments respond to fires; they go into buildings to ensure no additional problems before calling the firefighters. There is a vast collection of tools, skill sets, approaches, and processes to help identify advanced threats that could happen within the network. What is an effective hunting process for one organization may be a waste of time for another, depending on each company’s understanding of what threats they might face. Man-hours spent hunting are typically most beneficial for large organizations targeted by the cybercriminal community regularly, but that’s not to say that regular hunts for small/medium-sized enterprises can’t benefit from and identify threats by doing the same. Structured Threat Hunting The structured hunt is based on indicators of compromise (IOCs) and tactics, techniques, and procedures (TTP). IOCs provide information about potential adversaries, such as IP addresses, domain names, operating system versions, etc. TTPs describe how attackers operate and what tools they use. Combining IOCs and TTPs makes it possible to build a picture of the adversary. This approach allows us to detect threats earlier and prevent attacks. In addition, we can quickly identify the threat actors because each activity is described in detail. Unstructured Threat Hunting The concept of unstructured hunting is relatively new. It wasn’t until 2013 that we began seeing the emergence of unstructured hunters. Unstructured hunting is a method of finding malicious software (malware), such as viruses, Trojans, worms, etc., without knowing exactly what type of malware you are looking for. Instead, the hunter relies on behavioral analysis to find these threats. In short, unstructured hunting is investigative work where a cyber threat hunter observes behavior and looks for anomalies. For example, if someone sends out spam emails, a system administrator might notice unusual activity on his network and investigate further. If he finds something suspicious, he could take action immediately or wait a few days to see if the same email addresses start sending again. Traditional Threat Hunting The traditional definition of threat hunting can be defined as a focused and intensive human/machine-assisted process aimed to identify the possibility of something malicious happening within the network or likely about to happen; this is based on abnormal network behavior, artifacts, or identification via active threat research. A good example of this would be: A large bank has team members whose part of their job is to consume threat reports related to activity targeting their vertical and other companies that match their Enterprise profile. > A new threat report is published from an intel provider describing a new variant of malware that has been catastrophic at similar organizations. This report would ideally contain information around the process tree, registry key, etc., to help the cyber threat hunters not just hunt for detection of the associated IOCs but dig deeper to identify patterns that match the behavior of the malware across the network, like abnormal PowerShell executio | Spam Malware Tool Vulnerability Threat | |||
| 2022-10-20 06:00:00 | Attackers switch to self-extracting password-protected archives to distribute email malware (lien direct) | Distributing malware inside password-protected archives has long been one of the main techniques used by attackers to bypass email security filters. More recently, researchers have spotted a variation that uses nested self-extracting archives that no longer require victims to input the password.“This is significant because one of the most difficult obstacles threat actors face when conducting this type of spam campaign is to convince the target to open the archive using the provided password,” researchers from Trustwave SpiderLabs said in a new report.To read this article in full, please click here | Spam Malware Threat | |||
| 2022-10-17 10:00:00 | Stories from the SOC: Feeling so foolish – SocGholish drive by compromise (lien direct) | Executive summary:
SocGholish, also known as FakeUpdate, is a JavaScript framework leveraged in social engineering drive by compromises that has been a thorn in cybersecurity professionals’ and organizations’ sides for at least 5 years now. Upon visiting a compromised website, users are redirected to a page for a browser update and a zip archive file containing a malicious JavaScript file is downloaded and unfortunately often opened and executed by the fooled end user.
An AT&T Managed Extended Detection and Response (MXDR) client with Managed Endpoint Security (MES) powered by SentinelOne (S1) received an alert regarding the detection and mitigation of one of these JavaScript files. The MXDR Threat Hunter assigned to this client walked them through the activity resulting from the execution of the malicious file, as well as provide additional guidance on containment and remediation of the host involved in the incident.
Investigation
Upon detection of the follow up activity of the malicious file executed by the end user, S1 created an Incident within the S1 portal. This in turn creates an Alarm within the USM Anywhere platform, where the MXDR SOC team works, reviews, and creates Investigations for client notification as necessary. Since this activity was observed all within S1, this analysis will be out of there.
 The best way to start looking into a S1 event is to go to the Storyline of the Incident within Deep Visibility.
The best way to start looking into a S1 event is to go to the Storyline of the Incident within Deep Visibility.
 Once we have all the events related to the Incident, we can also create a new Deep Visibility search for all activity related to the affected host from about an hour before right up to the first event for the incident. This will let us try to see what happened on the host that lead to the execution of the malicious JavaScript file.
Reviewing the events from both the overall logs on the host and the events related to the Storyline, we can build out a rough timeline of events. Note there are close to 15k events on the host in the timeframe and 448 events in total in the Storyline; I’m just going over the interesting findings for expediency sake.
12:07:08 The user is surfing on Chrome and using Google search to look up electricity construction related companies; we see two sites being visited, with both sites being powered by WordPress. The SocGholish campaign works by injecting malicious code into vulnerable WordPress websites. While I was unable to find the injected code within the potentially compromised sites, I see that one of the banners on the page contains spam messages; while there are no links or anything specifically malicious with this, it lets us know that this site is unsafe to a degree.
Once we have all the events related to the Incident, we can also create a new Deep Visibility search for all activity related to the affected host from about an hour before right up to the first event for the incident. This will let us try to see what happened on the host that lead to the execution of the malicious JavaScript file.
Reviewing the events from both the overall logs on the host and the events related to the Storyline, we can build out a rough timeline of events. Note there are close to 15k events on the host in the timeframe and 448 events in total in the Storyline; I’m just going over the interesting findings for expediency sake.
12:07:08 The user is surfing on Chrome and using Google search to look up electricity construction related companies; we see two sites being visited, with both sites being powered by WordPress. The SocGholish campaign works by injecting malicious code into vulnerable WordPress websites. While I was unable to find the injected code within the potentially compromised sites, I see that one of the banners on the page contains spam messages; while there are no links or anything specifically malicious with this, it lets us know that this site is unsafe to a degree.
 12:10:46 The user was redirected to a clean[.]godmessagedme[.]com for the initial download. It likely would have looked like this:
12:10:46 The user was redirected to a clean[.]godmessagedme[.]com for the initial download. It likely would have looked like this:
 We can assume the URI for the request looks like the /report as seen in VirusTotal and described in open-source intelligence (OSI). Note that the subdomain “clean” has a different resolution than the root domain; this is domain shadowing performed by the attackers by creating a new A-record within the DNS settings of the legitimate domain:
We can assume the URI for the request looks like the /report as seen in VirusTotal and described in open-source intelligence (OSI). Note that the subdomain “clean” has a different resolution than the root domain; this is domain shadowing performed by the attackers by creating a new A-record within the DNS settings of the legitimate domain:

 12:12:19 Chrome creates on disk: “C:\Users\[redacted]\Downloads\Сhrome.Updаte.zip”.
12:13:11 User has opened the zip
12:12:19 Chrome creates on disk: “C:\Users\[redacted]\Downloads\Сhrome.Updаte.zip”.
12:13:11 User has opened the zip |
Spam Threat Guideline | |||
| 2022-10-14 01:24:52 | Guloader Spam Indiscriminately Sent to State Elections Board (lien direct) | Recently, the United States Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint public service announcement - Foreign Actors Likely to Use Information Manipulation Tactics for 2022 Midterm Elections (9I-100622-PSA). The focus of the PSA was to inform the public of the potential manipulation of the midterm election cycle in the United States by foreign agents using social engineering and social media disinformation tactics to influence voters and to sow discord as well.Around the same time of the announcement, FortiGuard Labs observed a Guloader campaign being sent to an elections body in the United States. Although there is no sign that they were specifically targeted, we want to highlight what's involved in these attacks given the 2022 U.S. midterm elections in November. The infection vectors are simple malicious spam that do not rely on exploiting a vulnerability or macros.FortiGuard Labs found a campaign from a purported industrial equipment manufacturer in Indonesia, containing a malicious ISO attachment. Figure 1. Email used in this spam campaignISO email attachments are often used to avoid detection by security solutions. Clicking on the attachment triggers the ISO file. Once mounted, an EXE file-a GuLoader malware variant-becomes visible. The victim then needs to run the "Requisition order-PT. LFC Teknologi,pdf.exe" executable manually to start the infection routine. Figure 2. GuLoader file in the mounted ISO fileThis file is digitally signed via an untrusted root certificate, seen below.Figure 3. Digital signature information for "Requisition order-PT. LFC Teknologi,pdf.exe".The GuLoader payload is a so-called first stage malware that has been seen in the wild for the past few years. It is designed to deliver a second stage payload that can be tailored to the attacker's liking. Some reported second stage payloads include Remote Access Trojans (RATs), infostealers, and ransomware.This particular GuLoader variant reaches out to 195[.]178[.]120[.]184/sMHxAbMCsvl181[.]java, which was no longer available at the time of the investigation. However, we believe the java file to either be a decryption key or a payload download. Another, GuLoader sample (SHA2: 46f8a8cec6bb92708a185cfea876ea1ae0cdef2321dc50f140f23c7cc650b65e) was submitted to VirusTotal on September 14th. This sample accesses 195[.]178[.]120[.]184/uFLBwGvx55[.]java and available OSINT suggests that the payload is the Azorult infostealer. Azorult is capable of exfiltrating data such as passwords from browsers, email, and FTP servers, and harvesting files with extensions specified by an attacker. It can also collect machine information such as user and computer name, installed programs, Windows version, and installed programs. Such stolen information can be a precursor to future attacks.Based on the traits of the GuLoader sample, FortiGuard Labs tracked down additional files involved in the same malicious spam campaign. The attacker mostly used IMG and ISO attachments along with file names in English, German, Spanish, Turkish, and Chinese. Taking a look at VirusTotal, submissions of the attachments are from the US, Czechia, China, Turkey, Germany, UK, Israel, Ireland, and Hungary. The GuLoader variant was also submitted to VirusTotal from the US, Bulgaria, Canada, China, the United Arab Emirates, and Korea. The email delivered to a board of elections in the United States was sent to a publicly available webmaster address. This indicates that the attacker sent these malicious emails to as many recipients as possible in the hope that someone would manually execute the malware. This is the first step to a potential compromise of machines related to the elections board of this United States state, and will allow the attacker to obtain a foothold to obtain unauthorized data for dissemination or simply various angles of disruption (ransomware, wiping, extortion, etc.) and even worse, perhaps sell access to an adversary for financial gain.Fortinet ProtectionsFortinet customers are already protected fr | Spam Malware Vulnerability | |||
| 2022-10-12 10:00:00 | 12 Essential ways to improve your website security (lien direct) | This blog was written by an independent guest blogger. In today's digital age, a business website is essential for success. Not only does it provide potential customers with information about your products or services, but it also allows you to connect and engage with them directly. However, simply having a website is not enough. To ensure that your site is effective and safe, you need to make sure that it has all the necessary security features. In this article, we will discuss twelve security features that every business website must have. 1. Auto-update enabled for plugins and software One of the simplest but most effective security measures you can take, especially if you’re looking to protect your WordPress site, is to ensure that all your plugins and software are up-to-date. Outdated software is one of the most common ways that attackers gain access to websites. By keeping everything up to date, you can help to prevent vulnerabilities from being exploited. You can usually enable auto-updates for most plugins and software from within their setting's menus. For WordPress sites, there is also a plugin called Easy Updates Manager that can help you to keep everything up to date with ease. 2. A strong password policy A strong password policy is the first step to protecting your website from malicious actors. By requiring strong and unique passwords, you can make it significantly more difficult for attackers to gain access to your site. You need to ensure that your website's backend is well protected and that only authorized users have access. To do this, you should consider using a password manager to generate and store strong passwords for your site. You definitely should not be using the same password for multiple sites. 3. Two-factor authentication Two-factor authentication (2FA) is an important security measure that you should consider implementing for your website. 2FA adds an extra layer of security by requiring users to provide two pieces of information before they can access your site. This could include a password and a one-time code that is generated by an app on your phone. 2FA can help to prevent attackers from gaining access to your site, even if they have your password. 4. A secure socket layer (SSL) certificate An SSL certificate is a must-have for any website that wants to protect their users' information. SSL encrypts the communications between your website and your users' web browsers. This means that even if an attacker was able to intercept the communication, they would not be able to read it. SSL also provides authentication, which means you can be sure that your users are communicating with the intended website and not a fake site set up by an attacker. Increasingly, having things like HTTPS and an SSL certificate are part of Google's ranking metrics and will help your website's SEO. If you aren't making an effort to protect your visitors and users (the people who give you their sensitive credit card information), they may take their business elsewhere. 5. A web application firewall (WAF) A web application firewall (WAF) is a piece of software that sits between your website and the internet. It filters traffic to your site and blocks any requests that it considers to be malicious. WAFs can be very effective at stopping attacks such as SQL injection and cross-site scripting (XSS). 6. Intrusion detection and prevention systems (IDPS) Intrusion detection and prevention systems (IDPS) are designed to | Spam Malware Threat | ★★★★ | ||
| 2022-10-11 19:22:42 | Google Pixel 7 and Pixel 7 Pro: The next evolution in mobile security (lien direct) | Dave Kleidermacher, Jesse Seed, Brandon Barbello, Sherif Hanna, Eugene Liderman, Android, Pixel, and Silicon Security Teams Every day, billions of people around the world trust Google products to enrich their lives and provide helpful features – across mobile devices, smart home devices, health and fitness devices, and more. We keep more people safe online than anyone else in the world, with products that are secure by default, private by design and that put you in control. As our advancements in knowledge and computing grow to deliver more help across contexts, locations and languages, our unwavering commitment to protecting your information remains. That's why Pixel phones are designed from the ground up to help protect you and your sensitive data while keeping you in control. We're taking our industry-leading approach to security and privacy to the next level with Google Pixel 7 and Pixel 7 Pro, our most secure and private phones yet, which were recently recognized as the highest rated for security when tested among other smartphones by a third-party global research firm.1 Pixel phones also get better every few months with Feature Drops that provide the latest product updates, tips and tricks from Google. And Pixel 7 and Pixel 7 Pro users will receive at least five years of security updates2, so your Pixel gets even more secure over time. Your protection, built into PixelYour digital life and most sensitive information lives on your phone: financial information, passwords, personal data, photos – you name it. With Google Tensor G2 and our custom Titan M2 security chip, Pixel 7 and Pixel 7 Pro have multiple layers of hardware security to help keep you and your personal information safe. We take a comprehensive, end-to-end approach to security with verifiable protections at each layer - the network, application, operating system and multiple layers on the silicon itself. If you use Pixel for your business, this approach helps protect your company data, too.  Google Tensor G2 is Pixel's newest powerful processor custom built with Google AI, and makes Pixel 7 faster, more efficient and secure3. Every aspect of Tensor G2 was designed to improve Pixel's performance and efficiency for great battery life, amazing photos and videos. Tensor's built-in security core works with our Titan M2 security chip to keep your personal information, PINs and passwords safe. Titan family chips are also used to protect Google Cloud data centers and Chromebooks, so the same hardware that protects Google servers also secures your sensitive information stored on Pixel. And, in a first for Google, Titan M2 hardware has now been certified under Common Criteria PP0084: the international gold standard for hardware security components also used for identity, SIM cards, and bankcard security chips. Google Tensor G2 is Pixel's newest powerful processor custom built with Google AI, and makes Pixel 7 faster, more efficient and secure3. Every aspect of Tensor G2 was designed to improve Pixel's performance and efficiency for great battery life, amazing photos and videos. Tensor's built-in security core works with our Titan M2 security chip to keep your personal information, PINs and passwords safe. Titan family chips are also used to protect Google Cloud data centers and Chromebooks, so the same hardware that protects Google servers also secures your sensitive information stored on Pixel. And, in a first for Google, Titan M2 hardware has now been certified under Common Criteria PP0084: the international gold standard for hardware security components also used for identity, SIM cards, and bankcard security chips. |
Spam Malware Vulnerability Guideline Industrial | APT 40 | ||
| 2022-10-07 09:10:00 | Meta Sues Chinese Devs Over WhatsApp Malware Plot (lien direct) | Fake apps led to account takeovers and spam campaigns | Spam Malware | |||
| 2022-09-28 13:00:00 | FCC moves to block robotexts (lien direct) | >Categories: NewsCategories: ScamsThe Federal Communications Commission wants mobile carriers to block spam texts at the network level. (Read more...) | Spam | |||
| 2022-09-28 03:00:00 | Your Guide to the Latest Email Fraud and Identity Deception Trends (lien direct) | >There's a high chance that you or someone you know has been impacted by email fraud or identity theft. At the very least, you've likely received a variety of spam emails and text messages asking to provide a payment or confirm your identity. The good news is that cybersecurity protection is constantly evolving and improving, […]… Read More | Spam | |||
| 2022-09-27 16:51:00 | Anomali Cyber Watch: Sandworm Uses HTML Smuggling and Commodity RATs, BlackCat Ransomware Adds New Features, Domain Shadowing Is Rarely Detected, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, China, Fraud, Inbound connectors, Phishing, Ransomware, Russia, and Ukraine. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
A Multimillion Dollar Global Online Credit Card Scam Uncovered
(published: September 23, 2022)
ReasonLabs researchers discovered a large network of fake dating and customer support websites involved in credit card fraud operations. The threat actor builds a basic website, registers it with a payment processor (RocketGate), buys credit card data from other threat actors, and subscribes victims to monthly charging plans. The US was the most targeted, and a lower number of sites were targeting France. To pass the processor checks and lower the number of charge-backs the actor avoided test charges, used a generic billing name, charged only a small, typical for the industry payment, and hired a legitimate support center provider, providing effortless canceling and returning of the payment.
Analyst Comment: Users are advised to regularly check their bank statements and dispute fraudulent charges. Researchers can identify a fraudulent website by overwhelming dominance of direct-traffic visitors from a single country, small network of fake profiles, and physical address typed on a picture to avoid indexing.
Tags: Credit card, Fraud, Scam, Chargeback, Payment processor, Fake dating site, USA, target-country:US, France, target-country:FR, target-sector:Finance NAICS 52
Malicious OAuth Applications Used to Compromise Email Servers and Spread Spam
(published: September 22, 2022)
Microsoft researchers described a relatively stealthy abuse of a compromised Exchange server used to send fraud spam emails. After using valid credentials to get access, the actor deployed a malicious OAuth application, gave it admin privileges and used it to change Exchange settings. The first modification created a new inbound connector allowing mails from certain actor IPs to flow through the victim’s Exchange server and look like they originated from the compromised Exchange domain. Second, 12 new transport rules were set to delete certain anti-spam email headers.
Analyst Comment: If you manage an Exchange server, strengthen account credentials and enable multifactor authentication. Investigate if receiving alerts regarding suspicious email sending and removal of antispam header.
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Indicator Removal on Host - T1070
Tags: Exchange, Microsoft, PowerShell, Inbound connector, Transport rule, Fraud, Spam
NFT Malware Gets New Evasion Abilities
(published: September 22, 2022)
Morphisec researchers describe a campaign targeting non-fungible token (NFT) communities since November 2020. A malicious link is being sent via Discord or other forum private phishing message related to an NFT or financial opportunity. If the user
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
A Multimillion Dollar Global Online Credit Card Scam Uncovered
(published: September 23, 2022)
ReasonLabs researchers discovered a large network of fake dating and customer support websites involved in credit card fraud operations. The threat actor builds a basic website, registers it with a payment processor (RocketGate), buys credit card data from other threat actors, and subscribes victims to monthly charging plans. The US was the most targeted, and a lower number of sites were targeting France. To pass the processor checks and lower the number of charge-backs the actor avoided test charges, used a generic billing name, charged only a small, typical for the industry payment, and hired a legitimate support center provider, providing effortless canceling and returning of the payment.
Analyst Comment: Users are advised to regularly check their bank statements and dispute fraudulent charges. Researchers can identify a fraudulent website by overwhelming dominance of direct-traffic visitors from a single country, small network of fake profiles, and physical address typed on a picture to avoid indexing.
Tags: Credit card, Fraud, Scam, Chargeback, Payment processor, Fake dating site, USA, target-country:US, France, target-country:FR, target-sector:Finance NAICS 52
Malicious OAuth Applications Used to Compromise Email Servers and Spread Spam
(published: September 22, 2022)
Microsoft researchers described a relatively stealthy abuse of a compromised Exchange server used to send fraud spam emails. After using valid credentials to get access, the actor deployed a malicious OAuth application, gave it admin privileges and used it to change Exchange settings. The first modification created a new inbound connector allowing mails from certain actor IPs to flow through the victim’s Exchange server and look like they originated from the compromised Exchange domain. Second, 12 new transport rules were set to delete certain anti-spam email headers.
Analyst Comment: If you manage an Exchange server, strengthen account credentials and enable multifactor authentication. Investigate if receiving alerts regarding suspicious email sending and removal of antispam header.
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Indicator Removal on Host - T1070
Tags: Exchange, Microsoft, PowerShell, Inbound connector, Transport rule, Fraud, Spam
NFT Malware Gets New Evasion Abilities
(published: September 22, 2022)
Morphisec researchers describe a campaign targeting non-fungible token (NFT) communities since November 2020. A malicious link is being sent via Discord or other forum private phishing message related to an NFT or financial opportunity. If the user |
Ransomware Spam Malware Tool Threat | |||
| 2022-09-27 15:40:27 | Malicious Oauth app enables attackers to send spam through corporate cloud tenants (lien direct) | >Microsoft investigated a new kind of attack where malicious OAuth applications were deployed on compromised cloud tenants before being used for mass spamming. | Spam | |||
| 2022-09-27 11:00:00 | Exchange servers abused for spam through malicious OAuth applications (lien direct) | >Categories: NewsTags: Exchange Tags: OAuth Tags: spam Tags: MFA Tags: Transport rules Tags: connector Threat actors have been using malicious OAuth applications to abuse Microsoft Exchange servers for their spam campaign. (Read more...) | Spam | |||
| 2022-09-23 16:00:00 | Hackers Deploy Malicious OAuth Apps to Compromise Email Servers, Spread Spam (lien direct) | The spam emails were sent to trick recipients into signing up for fake paid subscriptions | Spam | |||
| 2022-09-23 15:22:53 | Cyberattackers Compromise Microsoft Exchange Servers Via Malicious OAuth Apps (lien direct) | Cybercriminals took control of enterprise Exchange Servers to spread large amounts of spam aimed at signing people up for bogus subscriptions. | Spam | |||
| 2022-09-23 08:00:13 | Mass email campaign with a pinch of targeted spam (lien direct) | Mass spam mailing posing as customer email delivers the Agent Tesla stealer disguised as a document to corporate users. | Spam | |||
| 2022-09-07 09:40:00 | UK Privacy Regulator Fines Halfords for Spam Deluge (lien direct) | Retailer sent half a million emails to people without their consent | Spam | |||
| 2022-08-29 18:15:08 | CVE-2022-1663 (lien direct) | The Stop Spam Comments WordPress plugin through 0.2.1.2 does not properly generate the Javascript access token for preventing abuse of comment section, allowing threat authors to easily collect the value and add it to the request. | Spam Threat | |||
| 2022-08-26 05:31:39 | Paypal Phishing/Coinbase in One Image, (Fri, Aug 26th) (lien direct) | There is a current wave of Paypal phishing emails ongoing. I already received a few of them. This time, the spam is based on a simple JPEG image. The subject has always this format (with the date changing): | Spam | |||
| 2022-08-23 00:00:00 | Emotet Resurgence: Cross-Industry Campaign Analysis (lien direct) | This blog aims to provide background and technical discoveries from the recent Emotet resurgence detected in early 2022 across multiple Darktrace client environments in multiple regions and industries. Predominantly in March and April 2022, Darktrace DETECT provided visibility over network activities associated with Emotet compromises using initial staged payload downloads involving algorithmically generated DLLs and subsequent outbound command and control, as well as spam activities. | Spam | ★★★★ | ||
| 2022-08-16 09:30:17 | How a spoofed email passed the SPF check and landed in my inbox (lien direct) | >The Sender Policy Framework can't help prevent spam and phishing if you allow billions of IP addresses to send as your domain | Spam | |||
| 2022-08-15 11:21:39 | CVE-2022-35958 (lien direct) | Discourse is a 100% open source discussion platform. A malicious user can use the invitation system to spam arbitrary email addresses by sending them invitation emails in some cases. This issue is patched in the latest stable, beta and tests-passed versions of Discourse. There are currently no known workarounds. | Spam | ★★★ | ||
| 2022-08-08 15:11:18 | LogoKit update – The phishing kit leveraging Open Redirect Vulnerabilities (lien direct) | >LogoKit – Threat actors leveraging Open Redirect Vulnerabilities popular in online services and apps to bypass spam filters in phishing campaigns. Resecurity, Inc. (USA), a Los Angeles-based cybersecurity company providing managed threat detection and response for Fortune 500’s, identified threat actors leveraging Open Redirect Vulnerabilities popular in online services and apps to bypass spam filters […] | Spam Threat | |||
| 2022-08-08 14:15:10 | CVE-2022-35488 (lien direct) | In Zammad 5.2.0, an attacker could manipulate the rate limiting in the 'forgot password' feature of Zammad, and thereby send many requests for a known account to cause Denial Of Service by many generated emails which would also spam the victim. | Spam | |||
| 2022-08-05 12:39:42 | FCC warns of steep rise in phishing over SMS (lien direct) | >Smishing attacks, or phishing attempts via SMS, are on the rise, and Americans are fighting off billions of spam messages each month. | Spam | |||
| 2022-08-04 08:00:13 | Attackers leveraging Dark Utilities "C2aaS" platform in malware campaigns (lien direct) |  By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform. By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform.  Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo |
Spam Malware Hack Tool Threat Guideline | APT 19 | ||
| 2022-08-01 20:15:08 | CVE-2022-31184 (lien direct) | Discourse is the an open source discussion platform. In affected versions an email activation route can be abused to send mass spam emails. A fix has been included in the latest stable, beta and tests-passed versions of Discourse which rate limits emails. Users are advised to upgrade. Users unable to upgrade should manually rate limit email. | Spam | ★★★★★ | ||
| 2022-07-26 10:11:15 | Quarterly Report: Incident Response Trends in Q2 2022 (lien direct) | Commodity malware usage surpasses ransomware by narrow margin  By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. 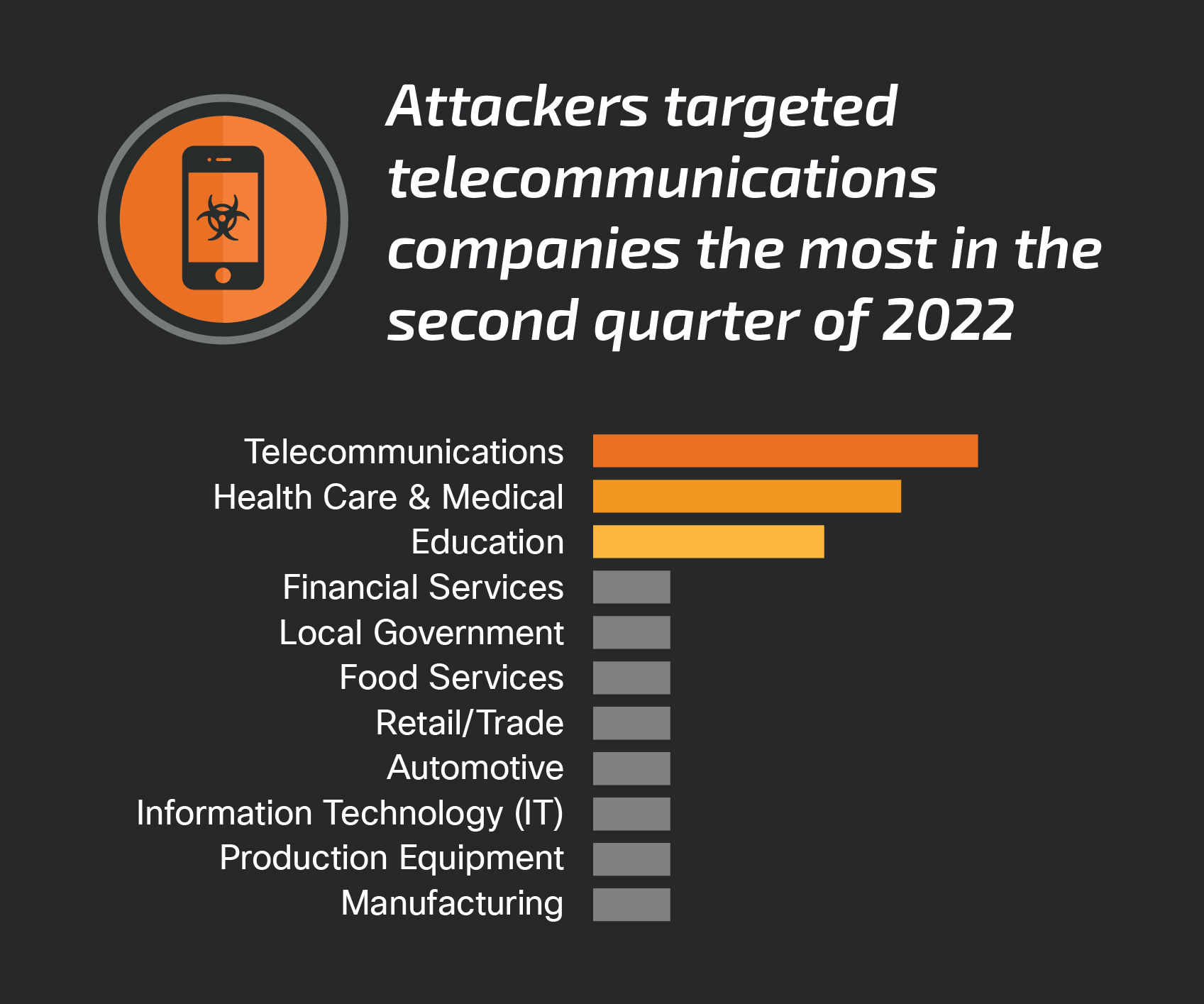 Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity |
Ransomware Spam Malware Threat | |||
| 2022-07-19 15:13:21 | Who on earth would be trying to promote EC-Council University via comment spam on my website? (lien direct) | I can't tell you not to seek ethical hacking certification from EC-Council. But I can suggest that if you are looking for an online university to boost your cybersecurity career, you don't settle for an outfit that has proven itself to be of questionable ethics and utterly clueless. | Spam | ★★★ |
To see everything:
Our RSS (filtrered)
