What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-06-13 13:00:00 | CyberheistNews Vol 13 # 24 [Le biais de l'esprit \\] le prétexage dépasse désormais le phishing dans les attaques d'ingénierie sociale CyberheistNews Vol 13 #24 [The Mind\\'s Bias] Pretexting Now Tops Phishing in Social Engineering Attacks (lien direct) |
 CyberheistNews Vol 13 #24 | June 13th, 2023
[The Mind\'s Bias] Pretexting Now Tops Phishing in Social Engineering Attacks
The New Verizon DBIR is a treasure trove of data. As we will cover a bit below, Verizon reported that 74% of data breaches Involve the "Human Element," so people are one of the most common factors contributing to successful data breaches. Let\'s drill down a bit more in the social engineering section.
They explained: "Now, who has received an email or a direct message on social media from a friend or family member who desperately needs money? Probably fewer of you. This is social engineering (pretexting specifically) and it takes more skill.
"The most convincing social engineers can get into your head and convince you that someone you love is in danger. They use information they have learned about you and your loved ones to trick you into believing the message is truly from someone you know, and they use this invented scenario to play on your emotions and create a sense of urgency. The DBIR Figure 35 shows that Pretexting is now more prevalent than Phishing in Social Engineering incidents. However, when we look at confirmed breaches, Phishing is still on top."
A social attack known as BEC, or business email compromise, can be quite intricate. In this type of attack, the perpetrator uses existing email communications and information to deceive the recipient into carrying out a seemingly ordinary task, like changing a vendor\'s bank account details. But what makes this attack dangerous is that the new bank account provided belongs to the attacker. As a result, any payments the recipient makes to that account will simply disappear.
BEC Attacks Have Nearly Doubled
It can be difficult to spot these attacks as the attackers do a lot of preparation beforehand. They may create a domain doppelganger that looks almost identical to the real one and modify the signature block to show their own number instead of the legitimate vendor.
Attackers can make many subtle changes to trick their targets, especially if they are receiving many similar legitimate requests. This could be one reason why BEC attacks have nearly doubled across the DBIR entire incident dataset, as shown in Figure 36, and now make up over 50% of incidents in this category.
Financially Motivated External Attackers Double Down on Social Engineering
Timely detection and response is crucial when dealing with social engineering attacks, as well as most other attacks. Figure 38 shows a steady increase in the median cost of BECs since 2018, now averaging around $50,000, emphasizing the significance of quick detection.
However, unlike the times we live in, this section isn\'t all doom and
CyberheistNews Vol 13 #24 | June 13th, 2023
[The Mind\'s Bias] Pretexting Now Tops Phishing in Social Engineering Attacks
The New Verizon DBIR is a treasure trove of data. As we will cover a bit below, Verizon reported that 74% of data breaches Involve the "Human Element," so people are one of the most common factors contributing to successful data breaches. Let\'s drill down a bit more in the social engineering section.
They explained: "Now, who has received an email or a direct message on social media from a friend or family member who desperately needs money? Probably fewer of you. This is social engineering (pretexting specifically) and it takes more skill.
"The most convincing social engineers can get into your head and convince you that someone you love is in danger. They use information they have learned about you and your loved ones to trick you into believing the message is truly from someone you know, and they use this invented scenario to play on your emotions and create a sense of urgency. The DBIR Figure 35 shows that Pretexting is now more prevalent than Phishing in Social Engineering incidents. However, when we look at confirmed breaches, Phishing is still on top."
A social attack known as BEC, or business email compromise, can be quite intricate. In this type of attack, the perpetrator uses existing email communications and information to deceive the recipient into carrying out a seemingly ordinary task, like changing a vendor\'s bank account details. But what makes this attack dangerous is that the new bank account provided belongs to the attacker. As a result, any payments the recipient makes to that account will simply disappear.
BEC Attacks Have Nearly Doubled
It can be difficult to spot these attacks as the attackers do a lot of preparation beforehand. They may create a domain doppelganger that looks almost identical to the real one and modify the signature block to show their own number instead of the legitimate vendor.
Attackers can make many subtle changes to trick their targets, especially if they are receiving many similar legitimate requests. This could be one reason why BEC attacks have nearly doubled across the DBIR entire incident dataset, as shown in Figure 36, and now make up over 50% of incidents in this category.
Financially Motivated External Attackers Double Down on Social Engineering
Timely detection and response is crucial when dealing with social engineering attacks, as well as most other attacks. Figure 38 shows a steady increase in the median cost of BECs since 2018, now averaging around $50,000, emphasizing the significance of quick detection.
However, unlike the times we live in, this section isn\'t all doom and |
Spam Malware Vulnerability Threat Patching | Uber APT 37 ChatGPT ChatGPT APT 43 | ★★ | |
| 2023-06-09 10:51:56 | Comment arrêter le spam du calendrier iPhone How to stop iPhone calendar spam (lien direct) |
> comment arrêter le spam du calendrier iPhone Lire la suite "
> How to stop iPhone calendar spam Read More " |
Spam | ★★ | ||
| 2023-06-09 09:55:20 | Comment arrêter les messages texte du spam sur Samsung How to stop spam text messages on Samsung (lien direct) |
> How to stop spam text messages on Samsung Read More " | Spam | ★★ | ||
| 2023-06-09 09:37:33 | Comment arrêter les e-mails de spam dans gmail How to stop spam emails in Gmail (lien direct) |
> comment arrêter les e-mails de spam dans gmail Lire la suite "
> How to stop spam emails in Gmail Read More " |
Spam | ★★ | ||
| 2023-06-07 13:15:09 | CVE-2021-4337 (lien direct) | Seize plugins Add-on XForwooCommerce pour WordPress sont vulnérables au contournement d'autorisation en raison d'une vérification de capacité manquante sur la fonction WP_AJAX_SVX_AJAX_FACTORY dans diverses versions répertoriées ci-dessous.Cela permet aux attaquants authentifiés, avec les autorisations de niveau abonné et au-dessus, de lire, d'éditer ou de supprimer les paramètres WordPress, les paramètres de plugin et de répertorier arbitrairement tous les utilisateurs sur un site Web WordPress.Les plugins touchés sont: Filtre de produit pour WooCommerce | Spam | |||
| 2023-06-07 07:15:08 | CVE-2023-2187 (lien direct) | Sur Triangle Microworks \\ 'SCADA Data Gateway Version | Spam Vulnerability | |||
| 2023-06-07 02:15:13 | CVE-2021-4350 (lien direct) | Le plugin Frontend File Manager pour WordPress est vulnérable à l'injection HTML non authentifiée dans les versions jusqu'à et comprenant 18.2.Cela est dû au manque de protections d'authentification sur l'action AJAX WPFM_SEND_FILE_IN_EMAIL.Cela permet aux attaquants non authentifiés d'envoyer des e-mails à l'aide du site avec un sujet personnalisé, un e-mail du destinataire et un corps avec un contenu HTML non animé.Cela permet à l'attaquant d'utiliser le site comme relais de spam.
The Frontend File Manager plugin for WordPress is vulnerable to Unauthenticated HTML Injection in versions up to, and including, 18.2. This is due to lacking authentication protections on the wpfm_send_file_in_email AJAX action. This makes it possible for unauthenticated attackers to send emails using the site with a custom subject, recipient email, and body with unsanitized HTML content. This effectively lets the attacker use the site as a spam relay. |
Spam | |||
| 2023-06-06 20:09:13 | Les loyers du service ont des adresses e-mail pour les inscriptions de compte Service Rents Email Addresses for Account Signups (lien direct) |
L'un des aspects les plus chers de toutes les opérations cybercriminales est le temps et les efforts nécessaires pour créer un grand nombre de nouveaux comptes de messagerie jetables.Désormais, un nouveau service propose pour aider à réduire considérablement les coûts associés aux campagnes de spam et de création de compte à grande échelle, en payant aux gens de vendre leurs informations d'identification de compte de messagerie et de laisser les clients louer temporairement l'accès à un vaste bassin de comptes établis chez les principaux fournisseurs.
One of the most expensive aspects of any cybercriminal operation is the time and effort it takes to create large numbers of new throwaway email accounts. Now a new service offers to help dramatically cut costs associated with large-scale spam and account creation campaigns, by paying people to sell their email account credentials and letting customers temporarily rent access to a vast pool of established accounts at major providers. |
Spam | ★★ | ||
| 2023-06-05 14:15:10 | CVE-2023-2489 (lien direct) | L'arrêt Spammers Security |Bloquer les utilisateurs de spam, les commentaires, le plugin WordPress Forms avant 2023 ne désinfectue pas et n'échappe pas à certains de ses paramètres, ce qui pourrait permettre aux utilisateurs de privilèges élevés tels que l'administrateur pour effectuer des attaques de script inter-sites stockées même lorsque la capacité non filtrée_html est interdite (par exemple dans MultiSiteinstallation)
The Stop Spammers Security | Block Spam Users, Comments, Forms WordPress plugin before 2023 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup) |
Spam | |||
| 2023-06-05 14:15:10 | CVE-2023-2488 (lien direct) | L'arrêt Spammers Security |Bloquer les utilisateurs de spam, les commentaires, les formulaires WordPress Plugin avant 2023 ne désinfectue pas et n'échappe pas à divers paramètres avant de les reprendre dans des pages de tableau de bord d'administration, conduisant à un script transversal réfléchi qui pourrait être utilisé contre des utilisateurs de privilèges élevés tels que l'administrateur
The Stop Spammers Security | Block Spam Users, Comments, Forms WordPress plugin before 2023 does not sanitise and escape various parameters before outputting them back in admin dashboard pages, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin |
Spam | |||
| 2023-06-02 18:23:00 | Le botnet brésilien cible les espagnols à travers les Amériques, dit Cisco Brazil-based botnet targets Spanish-speakers across Americas, Cisco says (lien direct) |
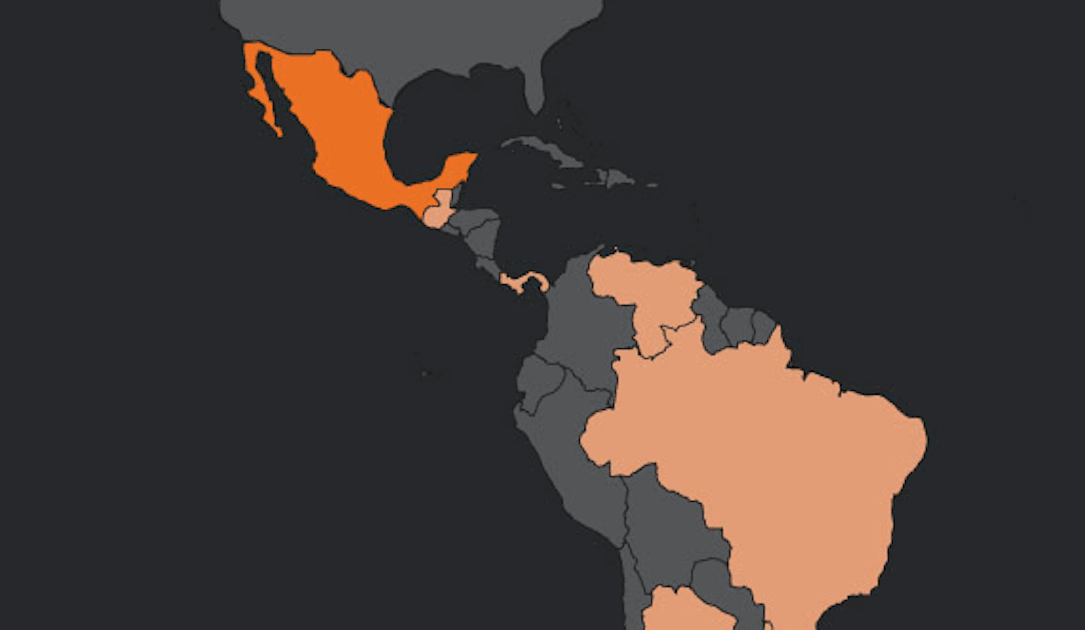 Les pirates soupçonnés de vivre au Brésil utilisent un botnet non identifié auparavant appelé à cibler les boîtes de réception par e-mail des espagnols à travers les Amériques.Des chercheurs de l'équipe de sécurité de Talos de Cisco \\ ont déclaré que le botnet, appelé «Horabot», livre un outil de chevaux de Troie et de spam bancaire sur une campagne qui se déroule depuis
Les pirates soupçonnés de vivre au Brésil utilisent un botnet non identifié auparavant appelé à cibler les boîtes de réception par e-mail des espagnols à travers les Amériques.Des chercheurs de l'équipe de sécurité de Talos de Cisco \\ ont déclaré que le botnet, appelé «Horabot», livre un outil de chevaux de Troie et de spam bancaire sur une campagne qui se déroule depuis
 Hackers suspected to be living in Brazil are using a previously unidentified botnet called to target the email inboxes of Spanish speakers across the Americas. Researchers from Cisco\'s Talos security team said the botnet, called “Horabot,” delivers a banking trojan and spam tool onto victim machines in a campaign that has been running since at
Hackers suspected to be living in Brazil are using a previously unidentified botnet called to target the email inboxes of Spanish speakers across the Americas. Researchers from Cisco\'s Talos security team said the botnet, called “Horabot,” delivers a banking trojan and spam tool onto victim machines in a campaign that has been running since at |
Spam Tool | ★★ | ||
| 2023-06-01 16:54:40 | New Horabot Campaign prend le relais Gmail de la victime, les comptes Outlook New Horabot campaign takes over victim\\'s Gmail, Outlook accounts (lien direct) |
Une campagne auparavant inconnue impliquant le malware de Hotabot Botnet a ciblé les utilisateurs hispanophones en Amérique latine depuis au moins novembre 2020, les infectant avec un troie et un outil de spam bancaires.[...]
A previously unknown campaign involving the Hotabot botnet malware has targeted Spanish-speaking users in Latin America since at least November 2020, infecting them with a banking trojan and spam tool. [...] |
Spam Malware | ★★ | ||
| 2023-05-26 13:15:11 | CVE-2023-24008 (lien direct) | Vulnérabilité de contrefaçon de demande de site croisé (CSRF) dans Yonifre Maspik & acirc; & euro; & ldquo;Spam Blacklist Plugin | Spam Vulnerability | |||
| 2023-05-23 02:30:00 | Strelastealer en cours de distribution aux utilisateurs espagnols StrelaStealer Being Distributed To Spanish Users (lien direct) |
Ahnlab Security Emergency Response Center (ASEC) a récemment confirmé que l'infosaler de Strelastealer est distribué aux utilisateurs espagnols des utilisateurs espagnols.Strelastealer a été initialement découvert vers novembre 2022 et a été distribué en pièce jointe aux e-mails de spam.Dans le passé, les fichiers ISO ont été utilisés comme pièces jointes, mais récemment, les fichiers ZIP ont été utilisés à la place.Figure 1. Email distribué L'e-mail qui est distribué est similaire à celui illustré à la figure 1. Le corps du courrier électronique et le nom du ...
AhnLab Security Emergency response Center (ASEC) analysis team has recently confirmed the StrelaStealer Infostealer being distributed to Spanish users. StrelaStealer was initially discovered around November 2022 and has been distributed as an attachment to spam emails. In the past, ISO files were used as attachments, but recently, ZIP files have been utilized instead. Figure 1. Distributed email The email that is being distributed is similar to the one shown in Figure 1. The email body and the name of the... |
Spam | ★★ | ||
| 2023-05-23 00:30:00 | DarkCloud Infosserner en cours de distribution via des e-mails de spam DarkCloud Infostealer Being Distributed via Spam Emails (lien direct) |
Ahnlab Security Emergency Response Center (ASEC) a récemment découvert que le malware DarkCloud était distribué par e-mail de spam.DarkCloud est un infostecteur qui vole les informations d'identification du compte enregistrées sur les systèmes infectés, et l'acteur de menace a installé Clipbanker aux côtés de DarkCloud.1. Méthode de distribution L'acteur de menace a envoyé l'e-mail suivant pour inciter les utilisateurs à télécharger et à exécuter la pièce jointe.Le contenu de cet e-mail invite les utilisateurs à vérifier la copie jointe de la déclaration de paiement envoyée au compte de la société.Quand l'attachement ...
AhnLab Security Emergency response Center (ASEC) has recently discovered the DarkCloud malware being distributed via spam email. DarkCloud is an Infostealer that steals account credentials saved on infected systems, and the threat actor installed ClipBanker alongside DarkCloud. 1. Distribution Method The threat actor sent the following email to induce users to download and execute the attachment. The contents of this email prompt users to check the attached copy of the payment statement sent to the company account. When the attachment... |
Spam Malware Threat | ★★ | ||
| 2023-05-23 00:15:30 | Entretien avec une crypto Scam Investment Spammez Interview With a Crypto Scam Investment Spammer (lien direct) |
Les réseaux sociaux se battent constamment contre des comptes de bot inauthentiques qui envoient des messages directs aux utilisateurs faisant la promotion des plateformes d'investissement de crypto-monnaie d'escroquerie.Ce qui suit est une interview avec un pirate russe responsable d'une série de campagnes agressives de spam crypto qui ont récemment incité plusieurs grandes communautés de mastodon pour arrêter temporairement de nouvelles inscriptions.Selon le pirate, leur logiciel de spam a été en usage privé jusqu'aux dernières semaines, date à laquelle il a été publié en tant que code open source.
Social networks are constantly battling inauthentic bot accounts that send direct messages to users promoting scam cryptocurrency investment platforms. What follows is an interview with a Russian hacker responsible for a series of aggressive crypto spam campaigns that recently prompted several large Mastodon communities to temporarily halt new registrations. According to the hacker, their spam software has been in private use until the last few weeks, when it was released as open source code. |
Spam | ★★★ | ||
| 2023-05-19 09:59:50 | Comment arrêter les textes de spam sur Android How to stop spam texts on Android (lien direct) |
> comment arrêter les textes de spam sur Android Lire la suite & # 187;
> How to stop spam texts on Android Read More » |
Spam | ★★ | ||
| 2023-05-17 01:21:05 | FAKECALLS: Les appels de spam qui fonctionnent vraiment FakeCalls: the Spam Calls that Really Work (lien direct) |
> Résumé: Pour tous les appels de spam ridicules dans le monde, mais un petit pourcentage d'entre eux sont en fait, légitimement, convaincants.Selon le gouvernement coréen, le «phishing vocal» compromet près de 200 citoyens coréens chaque jour, avec des pertes financières moyennes d'environ 8 500 dollars de coréen a gagné.Si c'est que le succès, les escrocs font quelque chose de bien.[& # 8230;]
>Abstract: For all the ridiculous spam calls in the world, but a small percentage of them are actually, legitimately, convincing. According to the Korean government, “voice phishing” compromises nearly 200 Korean citizens every day, with average financial losses around 8,500 dollars worth of Korean won.If it\'s that successful, surely, the scammers are doing something right. […] |
Spam | ★★ | ||
| 2023-05-16 13:00:00 | CyberheistNews Vol 13 # 20 [pied dans la porte] Les escroqueries de phishing du Q1 2023 \\ |Infographie CyberheistNews Vol 13 #20 [Foot in the Door] The Q1 2023\\'s Top-Clicked Phishing Scams | INFOGRAPHIC (lien direct) |
 CyberheistNews Vol 13 #20 | May 16th, 2023
[Foot in the Door] The Q1 2023\'s Top-Clicked Phishing Scams | INFOGRAPHIC
KnowBe4\'s latest reports on top-clicked phishing email subjects have been released for Q1 2023. We analyze "in the wild" attacks reported via our Phish Alert Button, top subjects globally clicked on in phishing tests, top attack vector types, and holiday email phishing subjects.
IT and Online Services Emails Drive Dangerous Attack Trend
This last quarter\'s results reflect the shift to IT and online service notifications such as laptop refresh or account suspension notifications that can affect your end users\' daily work.
Cybercriminals are constantly increasing the damage they cause to organizations by luring unsuspecting employees into clicking on malicious links or downloading fake attachments that seem realistic. Emails that are disguised as coming from an internal source, such as the IT department, are especially dangerous because they appear to come from a trusted place where an employee would not necessarily question it or be as skeptical.
Building up your organization\'s human firewall by fostering a strong security culture is essential to outsmart bad actors. The report covers the following:
Common "In-The-Wild" Emails for Q1 2023
Top Phishing Email Subjects Globally
Top 5 Attack Vector Types
Top 10 Holiday Phishing Email Subjects in Q1 2023
This post has a full PDF infographic you can download and share with your users:https://blog.knowbe4.com/q1-2023-top-clicked-phishing
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters without ever leaving the PhishER console.
Join us TOMORROW, Wednesday, May 17, @ 2:00 PM (ET) for a l
CyberheistNews Vol 13 #20 | May 16th, 2023
[Foot in the Door] The Q1 2023\'s Top-Clicked Phishing Scams | INFOGRAPHIC
KnowBe4\'s latest reports on top-clicked phishing email subjects have been released for Q1 2023. We analyze "in the wild" attacks reported via our Phish Alert Button, top subjects globally clicked on in phishing tests, top attack vector types, and holiday email phishing subjects.
IT and Online Services Emails Drive Dangerous Attack Trend
This last quarter\'s results reflect the shift to IT and online service notifications such as laptop refresh or account suspension notifications that can affect your end users\' daily work.
Cybercriminals are constantly increasing the damage they cause to organizations by luring unsuspecting employees into clicking on malicious links or downloading fake attachments that seem realistic. Emails that are disguised as coming from an internal source, such as the IT department, are especially dangerous because they appear to come from a trusted place where an employee would not necessarily question it or be as skeptical.
Building up your organization\'s human firewall by fostering a strong security culture is essential to outsmart bad actors. The report covers the following:
Common "In-The-Wild" Emails for Q1 2023
Top Phishing Email Subjects Globally
Top 5 Attack Vector Types
Top 10 Holiday Phishing Email Subjects in Q1 2023
This post has a full PDF infographic you can download and share with your users:https://blog.knowbe4.com/q1-2023-top-clicked-phishing
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters without ever leaving the PhishER console.
Join us TOMORROW, Wednesday, May 17, @ 2:00 PM (ET) for a l |
Ransomware Spam Malware Hack Tool Threat | ★★ | ||
| 2023-05-15 10:00:00 | CISOS: Comment améliorer la cybersécurité dans un paysage de menaces en constante évolution CISOs: How to improve cybersecurity in an ever-changing threat landscape (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. The digital landscape is always changing to keep up with a constantly evolving world, and bad actors are also adapting. For every new development in the digital world, cybercriminals are looking to take advantage of weaknesses, so it is important that those concerned with the security of their organization’s network, data, and other assets stay vigilant and on top of trends. Everybody within an organization should work to establish and maintain good cybersecurity habits and measures, but much of the security burden falls on the chief information security officer (CISO). Below are some key insights for any CISO to take into consideration. Concerns and challenges Since the beginning of the COVID-19 pandemic three years ago, hybrid and remote working solutions have been rising in popularity. This should be a priority area: according to a report from Malwarebytes, 20% of companies reported that a remote worker had caused a security breach. In comparison, 55% cited training employees in security protocols as a major challenge in transitioning to work-from-home infrastructure. Because the shift to hybrid and remote work happened quickly and with an eye for ease of access over security, employees working offsite can pose a great risk to an organization if not provided with adequate cybersecurity training and policies. AI and machine learning are also on the rise, increasingly being utilized by businesses and cybercriminals alike. It is important to recognize that while AI enhancements can provide aid, there is no replacement for the human element in developing a cybersecurity strategy. Understanding and deploying AI and machine learning tools can not only help with fraud detection, spam filtering, and data leak prevention, but it can allow a security officer insight into cybercriminals’ use of the tools. Increasing awareness of the criminal toolkit and operations provides an opportunity to get ahead of threat trends and potentially prevent attacks and breaches. Another major issue is the shortage of qualified cybersecurity professionals leading to a significant struggle with recruitment and retention. In a Fortinet report, 60% of respondents said they were struggling to recruit cybersecurity talent, and 52% said they were struggling to retain qualified people. In the same survey, around two-thirds of organization leaders agreed that the shortage “creates additional risk.” Many factors work in tandem to perpetuate the problem, but the solution doesn’t have to be complicated. Ensuring your employees have a healthy work environment goes a long way, as well as tweaking hiring practices to select “adaptable, highly communicative and curious” people, as these traits make for an employee who will grow and learn with your company. Tips for improving cybersecurity One of the top priorities for CISOs should always be to ensure that all employees are properly trained in cyber hygiene and cybersecurity best practices. Insider threats are a serious issue with no easy solution, and a good number of those (more than half, according to one report) are mistakes due to negligence or ignorance. Traditional threat prevention solutions are often concerned with | Data Breach Spam Threat | ★★ | ||
| 2023-05-15 08:41:56 | Classement Top Malware Check Point avril 2023 : Qbot lance une importante campagne de spam et Mirai fait son grand retour (lien direct) | Classement Top Malware Check Point avril 2023 : Qbot lance une importante campagne de spam et Mirai fait son grand retour Check Point Research a découvert une importante campagne de malspam pour le Trojan Qbot, qui est arrivé en deuxième position dans le classement des menaces du mois dernier. Parallèlement, Mirai, le malware de l'internet des objets (IoT), fait son retour dans le classement pour la première fois depuis un an, tandis que le secteur de la santé devient le deuxième secteur le plus exploité En France, les secteurs les plus touchés par ces Malwares sont les loisirs/hôtellerie, les vendeurs de logiciels et l'éducation/recherche - Malwares | Spam Malware | ★★ | ||
| 2023-05-10 14:59:36 | E / S 2023: Ce qui est nouveau dans la sécurité et la confidentialité d'Android I/O 2023: What\\'s new in Android security and privacy (lien direct) |
Posted by Ronnie Falcon, Product Manager Android is built with multiple layers of security and privacy protections to help keep you, your devices, and your data safe. Most importantly, we are committed to transparency, so you can see your device safety status and know how your data is being used. Android uses the best of Google\'s AI and machine learning expertise to proactively protect you and help keep you out of harm\'s way. We also empower you with tools that help you take control of your privacy. I/O is a great moment to show how we bring these features and protections all together to help you stay safe from threats like phishing attacks and password theft, while remaining in charge of your personal data. Safe Browsing: faster more intelligent protection Android uses Safe Browsing to protect billions of users from web-based threats, like deceptive phishing sites. This happens in the Chrome default browser and also in Android WebView, when you open web content from apps. Safe Browsing is getting a big upgrade with a new real-time API that helps ensure you\'re warned about fast-emerging malicious sites. With the newest version of Safe Browsing, devices will do real-time blocklist checks for low reputation sites. Our internal analysis has found that a significant number of phishing sites only exist for less than ten minutes to try and stay ahead of block-lists. With this real-time detection, we expect we\'ll be able to block an additional 25 percent of phishing attempts every month in Chrome and Android1. Safe Browsing isn\'t just getting faster at warning users. We\'ve also been building in more intelligence, leveraging Google\'s advances in AI. Last year, Chrome browser on Android and desktop started utilizing a new image-based phishing detection machine learning model to visually inspect fake sites that try to pass themselves off as legitimate log-in pages. By leveraging a TensorFlow Lite model, we\'re able to find 3x more2 phishing sites compared to previous machine learning models and help warn you before you get tricked into signing in. This year, we\'re expanding the coverage of the model to detect hundreds of more phishing campaigns and leverage new ML technologies. This is just one example of how we use our AI expertise to keep your data safe. Last year, Android used AI to protect users from 100 billion suspected spam messages and calls.3 Passkeys helps move users beyond passwords For many, passwords are the primary protection for their online life. In reality, they are frustrating to create, remember and are easily hacked. But hackers can\'t phish a password that doesn\'t exist. Which is why we are excited to share another major step forward in our passwordless journey: Passkeys. | Spam Malware Tool | ★★★ | ||
| 2023-05-09 13:00:00 | Cyberheistnews Vol 13 # 19 [Watch Your Back] Nouvelle fausse erreur de mise à jour Chrome Attaque cible vos utilisateurs CyberheistNews Vol 13 #19 [Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users (lien direct) |
 CyberheistNews Vol 13 #19 | May 9th, 2023
[Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users
Compromised websites (legitimate sites that have been successfully compromised to support social engineering) are serving visitors fake Google Chrome update error messages.
"Google Chrome users who use the browser regularly should be wary of a new attack campaign that distributes malware by posing as a Google Chrome update error message," Trend Micro warns. "The attack campaign has been operational since February 2023 and has a large impact area."
The message displayed reads, "UPDATE EXCEPTION. An error occurred in Chrome automatic update. Please install the update package manually later, or wait for the next automatic update." A link is provided at the bottom of the bogus error message that takes the user to what\'s misrepresented as a link that will support a Chrome manual update. In fact the link will download a ZIP file that contains an EXE file. The payload is a cryptojacking Monero miner.
A cryptojacker is bad enough since it will drain power and degrade device performance. This one also carries the potential for compromising sensitive information, particularly credentials, and serving as staging for further attacks.
This campaign may be more effective for its routine, innocent look. There are no spectacular threats, no promises of instant wealth, just a notice about a failed update. Users can become desensitized to the potential risks bogus messages concerning IT issues carry with them.
Informed users are the last line of defense against attacks like these. New school security awareness training can help any organization sustain that line of defense and create a strong security culture.
Blog post with links:https://blog.knowbe4.com/fake-chrome-update-error-messages
A Master Class on IT Security: Roger A. Grimes Teaches You Phishing Mitigation
Phishing attacks have come a long way from the spray-and-pray emails of just a few decades ago. Now they\'re more targeted, more cunning and more dangerous. And this enormous security gap leaves you open to business email compromise, session hijacking, ransomware and more.
Join Roger A. Grimes, KnowBe4\'s Data-Driven Defense Evangelist,
CyberheistNews Vol 13 #19 | May 9th, 2023
[Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users
Compromised websites (legitimate sites that have been successfully compromised to support social engineering) are serving visitors fake Google Chrome update error messages.
"Google Chrome users who use the browser regularly should be wary of a new attack campaign that distributes malware by posing as a Google Chrome update error message," Trend Micro warns. "The attack campaign has been operational since February 2023 and has a large impact area."
The message displayed reads, "UPDATE EXCEPTION. An error occurred in Chrome automatic update. Please install the update package manually later, or wait for the next automatic update." A link is provided at the bottom of the bogus error message that takes the user to what\'s misrepresented as a link that will support a Chrome manual update. In fact the link will download a ZIP file that contains an EXE file. The payload is a cryptojacking Monero miner.
A cryptojacker is bad enough since it will drain power and degrade device performance. This one also carries the potential for compromising sensitive information, particularly credentials, and serving as staging for further attacks.
This campaign may be more effective for its routine, innocent look. There are no spectacular threats, no promises of instant wealth, just a notice about a failed update. Users can become desensitized to the potential risks bogus messages concerning IT issues carry with them.
Informed users are the last line of defense against attacks like these. New school security awareness training can help any organization sustain that line of defense and create a strong security culture.
Blog post with links:https://blog.knowbe4.com/fake-chrome-update-error-messages
A Master Class on IT Security: Roger A. Grimes Teaches You Phishing Mitigation
Phishing attacks have come a long way from the spray-and-pray emails of just a few decades ago. Now they\'re more targeted, more cunning and more dangerous. And this enormous security gap leaves you open to business email compromise, session hijacking, ransomware and more.
Join Roger A. Grimes, KnowBe4\'s Data-Driven Defense Evangelist, |
Ransomware Data Breach Spam Malware Tool Threat Prediction | NotPetya NotPetya APT 28 ChatGPT ChatGPT | ★★ | |
| 2023-05-08 10:00:00 | Empêcher des attaques de phishing sophistiquées destinées aux employés Preventing sophisticated phishing attacks aimed at employees (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. As technology advances, phishing attempts are becoming more sophisticated. It can be challenging for employees to recognize an email is malicious when it looks normal, so it’s up to their company to properly train workers in prevention and detection. Phishing attacks are becoming more sophisticated Misspellings and poorly formatted text used to be the leading indicators of an email scam, but they’re getting more sophisticated. Today, hackers can spoof email addresses and bots sound like humans. It’s becoming challenging for employees to tell if their emails are real or fake, which puts the company at risk of data breaches. In March 2023, an artificial intelligence chatbot called GPT-4 received an update that lets users give specific instructions about styles and tasks. Attackers can use it to pose as employees and send convincing messages since it sounds intelligent and has general knowledge of any industry. Since classic warning signs of phishing attacks aren’t applicable anymore, companies should train all employees on the new, sophisticated methods. As phishing attacks change, so should businesses. Identify the signs Your company can take preventive action to secure its employees against attacks. You need to make it difficult for hackers to reach them, and your company must train them on warning signs. While blocking spam senders and reinforcing security systems is up to you, they must know how to identify and report themselves. You can prevent data breaches if employees know what to watch out for: Misspellings: While it’s becoming more common for phishing emails to have the correct spelling, employees still need to look for mistakes. For example, they could look for industry-specific language because everyone in their field should know how to spell those words. Irrelevant senders: Workers can identify phishing — even when the email is spoofed to appear as someone they know — by asking themselves if it is relevant. They should flag the email as a potential attack if the sender doesn’t usually reach out to them or is someone in an unrelated department. Attachments: Hackers attempt to install malware through links or downloads. Ensure every employee knows they shouldn\'t click on them. Odd requests: A sophisticated phishing attack has relevant messages and proper language, but it is somewhat vague because it goes to multiple employees at once. For example, they could recognize it if it’s asking them to do something unrelated to their role. It may be harder for people to detect warning signs as attacks evolve, but you can prepare them for those situations as well as possible. It’s unlikely hackers have access to their specific duties or the inner workings of your company, so you must capitalize on those details. Sophisticated attacks will sound intelligent and possibly align with their general duties, so everyone must constantly be aware. Training will help employees identify signs, but you need to take more preventive action to ensure you’re covered. Take preventive action Basic security measures — like regularly updating passwords and running antivirus software — are fundamental to protecting your company. For example, everyone should change their passwords once every three months at minimum to ensur | Spam Malware | ChatGPT | ★★ | |
| 2023-04-28 06:55:57 | (Déjà vu) Comment arrêter les appels de risques de spam How to stop spam risk calls (lien direct) |
> comment arrêter les appels de risque de spam En savoir plus & # 187;
> How to stop spam risk calls Read More » |
Spam | ★★ | ||
| 2023-04-27 15:15:04 | (Déjà vu) Comment arrêter les appels de spam sur la ligne fixe How to stop spam calls on landline (lien direct) |
> comment arrêter les appels de spam surFINDINE En savoir plus & # 187;
> How to stop spam calls on landline Read More » |
Spam | ★★ | ||
| 2023-04-27 14:59:18 | Comment arrêter les textes de spam sur iPhone How to stop spam texts on iPhone (lien direct) |
> comment arrêter les textes de spam suriPhone Lire la suite & # 187;
> How to stop spam texts on iPhone Read More » |
Spam | ★★ | ||
| 2023-04-27 14:22:44 | Comment arrêter les textes de spam sur AT&T How to stop spam texts on AT&T (lien direct) |
Hé, le client AT & # 38; t, êtes-vous inondé par des messages texte de spam?Tu n'es pas le seul.Heureusement, il existe plusieurs façons de lutter contre le spam de texte et vous ne devez pas être un assistant technologique pour le faire.Dans cet article, nous discuterons de cinq méthodes efficaces pour arrêter les textes de spam sur AT & # 38; t.Méthode # 1: Bloquer des messages texte indésirables & # 8230; Comment arrêter les textes de spam sur AT & # 038; t Lire la suite & # 187;
Hey, AT&T customer, are you inundated by spam text messages? You\'re not the only one. Luckily, there are several ways to fight text spam-and you don\'t have to be a tech wizard to do it. In this article, we\'ll discuss five effective methods to stop spam texts on AT&T. Method #1: Blocking unwanted text messages … How to stop spam texts on AT&T Read More » |
Spam | ★★ | ||
| 2023-04-27 14:21:31 | Comment arrêter les appels de spam et les robocaux sur Android How to Stop Spam Calls and Robocalls on Android (lien direct) |
> comment arrêter les appels de spam etRobocalls sur Android en savoir plus & # 187;
> How to Stop Spam Calls and Robocalls on Android Read More » |
Spam | ★★ | ||
| 2023-04-25 18:22:00 | Anomali Cyber Watch: Deux attaques de la chaîne d'approvisionnement enchaînées, leurre de communication DNS furtive de chien, Evilextractor exfiltrates sur le serveur FTP Anomali Cyber Watch: Two Supply-Chain Attacks Chained Together, Decoy Dog Stealthy DNS Communication, EvilExtractor Exfiltrates to FTP Server (lien direct) |
The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Cryptomining, Infostealers, Malvertising, North Korea, Phishing, Ransomware, and Supply-chain attacks. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.  Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
First-Ever Attack Leveraging Kubernetes RBAC to Backdoor Clusters
(published: April 21, 2023)
A new Monero cryptocurrency-mining campaign is the first recorded case of gaining persistence via Kubernetes (K8s) Role-Based Access Control (RBAC), according to Aquasec researchers. The recorded honeypot attack started with exploiting a misconfigured API server. The attackers preceded by gathering information about the cluster, checking if their cluster was already deployed, and deleting some existing deployments. They used RBAC to gain persistence by creating a new ClusterRole and a new ClusterRole binding. The attackers then created a DaemonSet to use a single API request to target all nodes for deployment. The deployed malicious image from the public registry Docker Hub was named to impersonate a legitimate account and a popular legitimate image. It has been pulled 14,399 times and 60 exposed K8s clusters have been found with signs of exploitation by this campaign.
Analyst Comment: Your company should have protocols in place to ensure that all cluster management and cloud storage systems are properly configured and patched. K8s buckets are too often misconfigured and threat actors realize there is potential for malicious activity. A defense-in-depth (layering of security mechanisms, redundancy, fail-safe defense processes) approach is a good mitigation step to help prevent actors from highly-active threat groups.
MITRE ATT&CK: [MITRE ATT&CK] T1190 - Exploit Public-Facing Application | [MITRE ATT&CK] T1496 - Resource Hijacking | [MITRE ATT&CK] T1036 - Masquerading | [MITRE ATT&CK] T1489 - Service Stop
Tags: Monero, malware-type:Cryptominer, detection:PUA.Linux.XMRMiner, file-type:ELF, abused:Docker Hub, technique:RBAC Buster, technique:Create ClusterRoleBinding, technique:Deploy DaemonSet, target-system:Linux, target:K8s, target:Kubernetes RBAC
3CX Software Supply Chain Compromise Initiated by a Prior Software Supply Chain Compromise; Suspected North Korean Actor Responsible
(published: April 20, 2023)
Investigation of the previously-reported 3CX supply chain compromise (March 2023) allowed Mandiant researchers to detect it was a result of prior software supply chain attack using a trojanized installer for X_TRADER, a software package provided by Trading Technologies. The attack involved the publicly-available tool SigFlip decrypting RC4 stream-cipher and starting publicly-available DaveShell shellcode for reflective loading. It led to installation of the custom, modular VeiledSignal backdoor. VeiledSignal additional modules inject the C2 module in a browser process instance, create a Windows named pipe and
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
First-Ever Attack Leveraging Kubernetes RBAC to Backdoor Clusters
(published: April 21, 2023)
A new Monero cryptocurrency-mining campaign is the first recorded case of gaining persistence via Kubernetes (K8s) Role-Based Access Control (RBAC), according to Aquasec researchers. The recorded honeypot attack started with exploiting a misconfigured API server. The attackers preceded by gathering information about the cluster, checking if their cluster was already deployed, and deleting some existing deployments. They used RBAC to gain persistence by creating a new ClusterRole and a new ClusterRole binding. The attackers then created a DaemonSet to use a single API request to target all nodes for deployment. The deployed malicious image from the public registry Docker Hub was named to impersonate a legitimate account and a popular legitimate image. It has been pulled 14,399 times and 60 exposed K8s clusters have been found with signs of exploitation by this campaign.
Analyst Comment: Your company should have protocols in place to ensure that all cluster management and cloud storage systems are properly configured and patched. K8s buckets are too often misconfigured and threat actors realize there is potential for malicious activity. A defense-in-depth (layering of security mechanisms, redundancy, fail-safe defense processes) approach is a good mitigation step to help prevent actors from highly-active threat groups.
MITRE ATT&CK: [MITRE ATT&CK] T1190 - Exploit Public-Facing Application | [MITRE ATT&CK] T1496 - Resource Hijacking | [MITRE ATT&CK] T1036 - Masquerading | [MITRE ATT&CK] T1489 - Service Stop
Tags: Monero, malware-type:Cryptominer, detection:PUA.Linux.XMRMiner, file-type:ELF, abused:Docker Hub, technique:RBAC Buster, technique:Create ClusterRoleBinding, technique:Deploy DaemonSet, target-system:Linux, target:K8s, target:Kubernetes RBAC
3CX Software Supply Chain Compromise Initiated by a Prior Software Supply Chain Compromise; Suspected North Korean Actor Responsible
(published: April 20, 2023)
Investigation of the previously-reported 3CX supply chain compromise (March 2023) allowed Mandiant researchers to detect it was a result of prior software supply chain attack using a trojanized installer for X_TRADER, a software package provided by Trading Technologies. The attack involved the publicly-available tool SigFlip decrypting RC4 stream-cipher and starting publicly-available DaveShell shellcode for reflective loading. It led to installation of the custom, modular VeiledSignal backdoor. VeiledSignal additional modules inject the C2 module in a browser process instance, create a Windows named pipe and |
Ransomware Spam Malware Tool Threat Cloud | Uber APT 38 ChatGPT APT 43 | ★★ | |
| 2023-04-25 13:00:00 | Cyberheistnews Vol 13 # 17 [Head Start] Méthodes efficaces Comment enseigner l'ingénierie sociale à une IA CyberheistNews Vol 13 #17 [Head Start] Effective Methods How To Teach Social Engineering to an AI (lien direct) |
 CyberheistNews Vol 13 #16 | April 18th, 2023
[Finger on the Pulse]: How Phishers Leverage Recent AI Buzz
Curiosity leads people to suspend their better judgment as a new campaign of credential theft exploits a person\'s excitement about the newest AI systems not yet available to the general public. On Tuesday morning, April 11th, Veriti explained that several unknown actors are making false Facebook ads which advertise a free download of AIs like ChatGPT and Google Bard.
Veriti writes "These posts are designed to appear legitimate, using the buzz around OpenAI language models to trick unsuspecting users into downloading the files. However, once the user downloads and extracts the file, the Redline Stealer (aka RedStealer) malware is activated and is capable of stealing passwords and downloading further malware onto the user\'s device."
Veriti describes the capabilities of the Redline Stealer malware which, once downloaded, can take sensitive information like credit card numbers, passwords, and personal information like user location, and hardware. Veriti added "The malware can upload and download files, execute commands, and send back data about the infected computer at regular intervals."
Experts recommend using official Google or OpenAI websites to learn when their products will be available and only downloading files from reputable sources. With the rising use of Google and Facebook ads as attack vectors experts also suggest refraining from clicking on suspicious advertisements promising early access to any product on the Internet.
Employees can be helped to develop sound security habits like these by stepping them through monthly social engineering simulations.
Blog post with links:https://blog.knowbe4.com/ai-hype-used-for-phishbait
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters with
CyberheistNews Vol 13 #16 | April 18th, 2023
[Finger on the Pulse]: How Phishers Leverage Recent AI Buzz
Curiosity leads people to suspend their better judgment as a new campaign of credential theft exploits a person\'s excitement about the newest AI systems not yet available to the general public. On Tuesday morning, April 11th, Veriti explained that several unknown actors are making false Facebook ads which advertise a free download of AIs like ChatGPT and Google Bard.
Veriti writes "These posts are designed to appear legitimate, using the buzz around OpenAI language models to trick unsuspecting users into downloading the files. However, once the user downloads and extracts the file, the Redline Stealer (aka RedStealer) malware is activated and is capable of stealing passwords and downloading further malware onto the user\'s device."
Veriti describes the capabilities of the Redline Stealer malware which, once downloaded, can take sensitive information like credit card numbers, passwords, and personal information like user location, and hardware. Veriti added "The malware can upload and download files, execute commands, and send back data about the infected computer at regular intervals."
Experts recommend using official Google or OpenAI websites to learn when their products will be available and only downloading files from reputable sources. With the rising use of Google and Facebook ads as attack vectors experts also suggest refraining from clicking on suspicious advertisements promising early access to any product on the Internet.
Employees can be helped to develop sound security habits like these by stepping them through monthly social engineering simulations.
Blog post with links:https://blog.knowbe4.com/ai-hype-used-for-phishbait
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters with |
Spam Malware Hack Threat | APT 28 ChatGPT ChatGPT | ★★★ | |
| 2023-04-18 13:00:00 | Cyberheistnews Vol 13 # 16 [doigt sur le pouls]: comment les phishers tirent parti de l'IA récent Buzz CyberheistNews Vol 13 #16 [Finger on the Pulse]: How Phishers Leverage Recent AI Buzz (lien direct) |
 CyberheistNews Vol 13 #16 | April 18th, 2023
[Finger on the Pulse]: How Phishers Leverage Recent AI Buzz
Curiosity leads people to suspend their better judgment as a new campaign of credential theft exploits a person\'s excitement about the newest AI systems not yet available to the general public. On Tuesday morning, April 11th, Veriti explained that several unknown actors are making false Facebook ads which advertise a free download of AIs like ChatGPT and Google Bard.
Veriti writes "These posts are designed to appear legitimate, using the buzz around OpenAI language models to trick unsuspecting users into downloading the files. However, once the user downloads and extracts the file, the Redline Stealer (aka RedStealer) malware is activated and is capable of stealing passwords and downloading further malware onto the user\'s device."
Veriti describes the capabilities of the Redline Stealer malware which, once downloaded, can take sensitive information like credit card numbers, passwords, and personal information like user location, and hardware. Veriti added "The malware can upload and download files, execute commands, and send back data about the infected computer at regular intervals."
Experts recommend using official Google or OpenAI websites to learn when their products will be available and only downloading files from reputable sources. With the rising use of Google and Facebook ads as attack vectors experts also suggest refraining from clicking on suspicious advertisements promising early access to any product on the Internet.
Employees can be helped to develop sound security habits like these by stepping them through monthly social engineering simulations.
Blog post with links:https://blog.knowbe4.com/ai-hype-used-for-phishbait
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters without ever leav
CyberheistNews Vol 13 #16 | April 18th, 2023
[Finger on the Pulse]: How Phishers Leverage Recent AI Buzz
Curiosity leads people to suspend their better judgment as a new campaign of credential theft exploits a person\'s excitement about the newest AI systems not yet available to the general public. On Tuesday morning, April 11th, Veriti explained that several unknown actors are making false Facebook ads which advertise a free download of AIs like ChatGPT and Google Bard.
Veriti writes "These posts are designed to appear legitimate, using the buzz around OpenAI language models to trick unsuspecting users into downloading the files. However, once the user downloads and extracts the file, the Redline Stealer (aka RedStealer) malware is activated and is capable of stealing passwords and downloading further malware onto the user\'s device."
Veriti describes the capabilities of the Redline Stealer malware which, once downloaded, can take sensitive information like credit card numbers, passwords, and personal information like user location, and hardware. Veriti added "The malware can upload and download files, execute commands, and send back data about the infected computer at regular intervals."
Experts recommend using official Google or OpenAI websites to learn when their products will be available and only downloading files from reputable sources. With the rising use of Google and Facebook ads as attack vectors experts also suggest refraining from clicking on suspicious advertisements promising early access to any product on the Internet.
Employees can be helped to develop sound security habits like these by stepping them through monthly social engineering simulations.
Blog post with links:https://blog.knowbe4.com/ai-hype-used-for-phishbait
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters without ever leav |
Spam Malware Hack Threat | APT 28 ChatGPT ChatGPT | ★★★ | |
| 2023-04-13 15:24:00 | Le malware de la Légion marche sur les serveurs Web pour voler des informations d'identification, les utilisateurs de spam mobiles Legion Malware Marches onto Web Servers to Steal Credentials, Spam Mobile Users (lien direct) |
Un nouveau Credential Harvester compromet les services SMTP pour voler des données dans une gamme de services et de fournisseurs hébergés, et peut également lancer des attaques de spam basées sur SMS contre des appareils utilisant des opérateurs mobiles américains.
A novel credential harvester compromises SMTP services to steal data from a range of hosted services and providers, and can also launch SMS-based spam attacks against devices using US mobile carriers. |
Spam Malware | ★★ | ||
| 2023-04-11 13:16:54 | Cyberheistnews Vol 13 # 15 [Le nouveau visage de la fraude] FTC fait la lumière sur les escroqueries d'urgence familiale améliorées AI-AI CyberheistNews Vol 13 #15 [The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams (lien direct) |
 CyberheistNews Vol 13 #15 | April 11th, 2023
[The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams
The Federal Trade Commission is alerting consumers about a next-level, more sophisticated family emergency scam that uses AI which imitates the voice of a "family member in distress."
They started out with: "You get a call. There\'s a panicked voice on the line. It\'s your grandson. He says he\'s in deep trouble - he wrecked the car and landed in jail. But you can help by sending money. You take a deep breath and think. You\'ve heard about grandparent scams. But darn, it sounds just like him. How could it be a scam? Voice cloning, that\'s how."
"Don\'t Trust The Voice"
The FTC explains: "Artificial intelligence is no longer a far-fetched idea out of a sci-fi movie. We\'re living with it, here and now. A scammer could use AI to clone the voice of your loved one. All he needs is a short audio clip of your family member\'s voice - which he could get from content posted online - and a voice-cloning program. When the scammer calls you, he\'ll sound just like your loved one.
"So how can you tell if a family member is in trouble or if it\'s a scammer using a cloned voice? Don\'t trust the voice. Call the person who supposedly contacted you and verify the story. Use a phone number you know is theirs. If you can\'t reach your loved one, try to get in touch with them through another family member or their friends."
Full text of the alert is at the FTC website. Share with friends, family and co-workers:https://blog.knowbe4.com/the-new-face-of-fraud-ftc-sheds-light-on-ai-enhanced-family-emergency-scams
A Master Class on IT Security: Roger A. Grimes Teaches Ransomware Mitigation
Cybercriminals have become thoughtful about ransomware attacks; taking time to maximize your organization\'s potential damage and their payoff. Protecting your network from this growing threat is more important than ever. And nobody knows this more than Roger A. Grimes, Data-Driven Defense Evangelist at KnowBe4.
With 30+ years of experience as a computer security consultant, instructor, and award-winning author, Roger has dedicated his life to making
CyberheistNews Vol 13 #15 | April 11th, 2023
[The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams
The Federal Trade Commission is alerting consumers about a next-level, more sophisticated family emergency scam that uses AI which imitates the voice of a "family member in distress."
They started out with: "You get a call. There\'s a panicked voice on the line. It\'s your grandson. He says he\'s in deep trouble - he wrecked the car and landed in jail. But you can help by sending money. You take a deep breath and think. You\'ve heard about grandparent scams. But darn, it sounds just like him. How could it be a scam? Voice cloning, that\'s how."
"Don\'t Trust The Voice"
The FTC explains: "Artificial intelligence is no longer a far-fetched idea out of a sci-fi movie. We\'re living with it, here and now. A scammer could use AI to clone the voice of your loved one. All he needs is a short audio clip of your family member\'s voice - which he could get from content posted online - and a voice-cloning program. When the scammer calls you, he\'ll sound just like your loved one.
"So how can you tell if a family member is in trouble or if it\'s a scammer using a cloned voice? Don\'t trust the voice. Call the person who supposedly contacted you and verify the story. Use a phone number you know is theirs. If you can\'t reach your loved one, try to get in touch with them through another family member or their friends."
Full text of the alert is at the FTC website. Share with friends, family and co-workers:https://blog.knowbe4.com/the-new-face-of-fraud-ftc-sheds-light-on-ai-enhanced-family-emergency-scams
A Master Class on IT Security: Roger A. Grimes Teaches Ransomware Mitigation
Cybercriminals have become thoughtful about ransomware attacks; taking time to maximize your organization\'s potential damage and their payoff. Protecting your network from this growing threat is more important than ever. And nobody knows this more than Roger A. Grimes, Data-Driven Defense Evangelist at KnowBe4.
With 30+ years of experience as a computer security consultant, instructor, and award-winning author, Roger has dedicated his life to making |
Ransomware Data Breach Spam Malware Hack Tool Threat | ChatGPT ChatGPT | ★★ | |
| 2023-04-11 09:43:36 | Mars 2023 \\'s Mostware le plus recherché: la nouvelle campagne Emotet contourne les Microsoft Blocks pour distribuer des fichiers OneNote malveillants March 2023\\'s Most Wanted Malware: New Emotet Campaign Bypasses Microsoft Blocks to Distribute Malicious OneNote Files (lien direct) |
mars 2023 \\ est le malware le plus recherché: une nouvelle campagne Emotet contourne les Microsoft Blocks pour distribuer des fichiers Onenote malveillants
Vérifier les rapports de recherche sur les points selon lesquels Emotet Trojan a lancé une nouvelle campagne le mois dernier pour échapper au bloc macro de Microsoft \\, envoyant des e-mails de spam contenant des fichiers onenote malveillants.Pendant ce temps, Ahmyth était le malware mobile le plus répandu et Log4J a de nouveau pris la première place comme la vulnérabilité la plus exploitée
-
mise à jour malveillant
/ /
affiche
March 2023\'s Most Wanted Malware: New Emotet Campaign Bypasses Microsoft Blocks to Distribute Malicious OneNote Files Check Point Research reports that Emotet Trojan launched a new campaign last month to evade Microsoft\'s macro block, sending spam emails containing malicious OneNote files. Meanwhile Ahmyth was the most prevalent mobile malware and Log4j took top spot once again as the most exploited vulnerability - Malware Update / affiche |
Spam Malware | ★★★ | ||
| 2023-04-10 11:23:02 | LLMS et phishing LLMs and Phishing (lien direct) |
Voici une expérience dirigée par des étudiants de premier cycle en informatique partout: demandez à Chatgpt de générer des e-mails de phishing et testez si ceux-ci sont meilleurs pour persuader les victimes de répondre ou de cliquer sur le lien que le spam habituel.C'est une expérience intéressante, et les résultats devraient varier follement basé sur les détails de l'expérience.
Mais bien qu'il soit une expérience facile à exécuter, il manque le risque réel de modèles de grande langue (LLMS) à rédiger des e-mails d'escroquerie.Les escroqueries par l'homme aujourd'hui ne sont pas limitées par le nombre de personnes qui répondent au contact initial par e-mail.Ils sont limitées par le processus à forte intensité de main-d'œuvre de persuader ces personnes d'envoyer de l'argent à l'escroc.Les LLM sont sur le point de changer cela.Il y a dix ans, un type de courriel de spam était devenu une punchline à chaque émission de fin de soirée: & # 8220; Je suis le fils de feu le roi du Nigéria qui a besoin de votre aide & # 8230;. & # 8221;Presque tout le monde avait reçu un ou mille de ces e-mails, au point qu'il semblait que tout le monde devait savoir qu'ils étaient des escroqueries ...
Here’s an experiment being run by undergraduate computer science students everywhere: Ask ChatGPT to generate phishing emails, and test whether these are better at persuading victims to respond or click on the link than the usual spam. It’s an interesting experiment, and the results are likely to vary wildly based on the details of the experiment. But while it’s an easy experiment to run, it misses the real risk of large language models (LLMs) writing scam emails. Today’s human-run scams aren’t limited by the number of people who respond to the initial email contact. They’re limited by the labor-intensive process of persuading those people to send the scammer money. LLMs are about to change that. A decade ago, one type of spam email had become a punchline on every late-night show: “I am the son of the late king of Nigeria in need of your assistance….” Nearly everyone had gotten one or a thousand of those emails, to the point that it seemed everyone must have known they were scams... |
Spam | ChatGPT ChatGPT | ★★★★ | |
| 2023-04-10 11:00:11 | March 2023\'s Most Wanted Malware: New Emotet Campaign Bypasses Microsoft Blocks to Distribute Malicious OneNote Files (lien direct) | > Vérifier les rapports de recherche sur les points selon lesquels Emotet Trojan a lancé une nouvelle campagne le mois dernier pour échapper au bloc macro de Microsoft \\, envoyant des e-mails de spam contenant des fichiers Onenote malveillants.Pendant ce temps, Ahmyth était le logiciel malveillant mobile le plus répandu et Log4j a de nouveau pris la première place comme la vulnérabilité la plus exploitée que notre dernier indice de menace mondial pour mars 2023 a vu les chercheurs découvrir une nouvelle campagne de logiciels malveillants d'Emotet Trojan, qui a augmenté.Comme indiqué plus tôt cette année, les attaquants d'Emotet ont exploré d'autres moyens de distribuer des fichiers malveillants depuis que Microsoft a annoncé qu'ils bloqueraient les macros des fichiers de bureau.[& # 8230;]
>Check Point Research reports that Emotet Trojan launched a new campaign last month to evade Microsoft\'s macro block, sending spam emails containing malicious OneNote files. Meanwhile Ahmyth was the most prevalent mobile malware and Log4j took top spot once again as the most exploited vulnerability Our latest Global Threat Index for March 2023 saw researchers uncover a new malware campaign from Emotet Trojan, which rose to become the second most prevalent malware last month. As reported earlier this year, Emotet attackers have been exploring alternative ways to distribute malicious files since Microsoft announced they will block macros from office files. […] |
Spam Malware Vulnerability Threat | ★★ | ||
| 2023-04-05 08:40:00 | MALIVE SPAM Campaign Downs NPM Registry Malicious Spam Campaign Downs npm Registry (lien direct) |
L'empoisonnement du référencement entraîne une augmentation de la circulation
SEO poisoning drives surge in traffic |
Spam | ★★ | ||
| 2023-04-04 10:00:00 | Fraudeurs chinois: ÉVADER DE DÉTECTION ET MONÉTISATION Chinese fraudsters: evading detection and monetizing stolen credit card information (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article.
Cyber attacks are common occurrences that often make headlines, but the leakage of personal information, particularly credit card data, can have severe consequences for individuals. It is essential to understand the techniques employed by cyber criminals to steal this sensitive information.
Credit card fraud in the United States has been on the rise, with total losses reaching approximately $12.16 billion in 2021, according to Insider Intelligence. Card-Not-Present (CNP) fraud constituted 72% of these losses, with a substantial portion attributed to Chinese fraudsters.
This article discusses the tactics employed by Chinese cyber actors in committing CNP fraud and their value chain.
Chinese fraudsters primarily target the United States for two reasons: the large population makes phishing attacks more effective, and credit card limits in the country are higher compared to other nations. These factors make the US an attractive market for card fraudsters.
Common methods for acquiring card information include phishing, JavaScript injection through website tampering, and stealing data via Trojan horse infections. Phishing is the most prevalent method, and this analysis will focus on phishing tactics and the monetization value chain of stolen credit card information.
 Chinese fraudsters have developed extensive ecosystems for their operations. In a card fraud community targeting Japan and the US, over 96,000 users have joined. For 3,000 Chinese yuan in Bitcoin, individuals can enroll in a bootcamp to learn phishing techniques through recorded videos and access resources for creating phishing sites and profiting from stolen credit cards.
According to the community leader, more than 500 students enrolled in the first half of 2022 alone. This leader has made significant profits, receiving 56 BTC over the past three years.
Chinese fraudster ecosystem: actor’s value chain
The value chain of Card Non-present fraud is shown as the following picture.
Chinese fraudsters have developed extensive ecosystems for their operations. In a card fraud community targeting Japan and the US, over 96,000 users have joined. For 3,000 Chinese yuan in Bitcoin, individuals can enroll in a bootcamp to learn phishing techniques through recorded videos and access resources for creating phishing sites and profiting from stolen credit cards.
According to the community leader, more than 500 students enrolled in the first half of 2022 alone. This leader has made significant profits, receiving 56 BTC over the past three years.
Chinese fraudster ecosystem: actor’s value chain
The value chain of Card Non-present fraud is shown as the following picture.
 To carry out these activities, Chinese fraudsters establish a value chain for CNP fraud, starting with setting up a secure environment. They anonymize IDs, falsify IP addresses, change time zones and language settings, alter MAC addresses and device IDs, modify user agents, and clear cookies to evade detection by security researchers and bypass various security measures.
To carry out these activities, Chinese fraudsters establish a value chain for CNP fraud, starting with setting up a secure environment. They anonymize IDs, falsify IP addresses, change time zones and language settings, alter MAC addresses and device IDs, modify user agents, and clear cookies to evade detection by security researchers and bypass various security measures.
 Fraudsters also use residential proxies, which are infected domestic devices, to access targeted websites indirectly and avoid tracking. These proxies can be purchased from online providers, with payments made via stolen credit cards or bitcoin. By selecting the desired IP address, users can access the target site with a fake IP address, making it difficult to trace their activities.
One residential proxy service popular among Chinese fraudsters is "911," which is built using software distributed under the guise of a free VPN service. Once installed, users are unknowingly transformed into valuable residential proxies for fraudsters without their consent. The service offers locations at city granularity to match the target user\'s geographic location.
Fraudsters also use residential proxies, which are infected domestic devices, to access targeted websites indirectly and avoid tracking. These proxies can be purchased from online providers, with payments made via stolen credit cards or bitcoin. By selecting the desired IP address, users can access the target site with a fake IP address, making it difficult to trace their activities.
One residential proxy service popular among Chinese fraudsters is "911," which is built using software distributed under the guise of a free VPN service. Once installed, users are unknowingly transformed into valuable residential proxies for fraudsters without their consent. The service offers locations at city granularity to match the target user\'s geographic location.
 Additionally, fraudsters can select ISP and device fingerprints, such as browser version, operating system, and screen size. This information is usually acquired through phishing, and fraudsters select the ones used by the victims t
Additionally, fraudsters can select ISP and device fingerprints, such as browser version, operating system, and screen size. This information is usually acquired through phishing, and fraudsters select the ones used by the victims t |
Spam | ★★ | ||
| 2023-03-28 10:00:00 | Dridex Malware, le Troie bancaire [Dridex malware, the banking trojan] (lien direct) | The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Introduction: Dridex, also known as Cridex or Bugat, is a banking Trojan that has been active since 2011. The malware is primarily used to steal sensitive information, such as login credentials and financial information, from victims. Dridex is known for its ability to evade detection by using dynamic configuration files and hiding its servers behind proxy layers. The Dridex malware typically spreads through spam email campaigns, with the emails containing a malicious attachment or link that, when clicked, will install the malware on the victim\'s computer. The malware then uses web injections to steal financial information from the victim. One of the interesting features of Dridex is its use of a peer-to-peer (P2P) network for command and control (C&C) communication. This allows the attackers to evade detection by security researchers and law enforcement, as the C&C servers can be quickly changed if one is discovered. In terms of atomic techniques, Dridex uses a variety of methods to evade detection and maintain persistence on an infected system. Some of these techniques include: Fileless infection: Dridex can infect a system without leaving any trace of a malicious file on the hard drive. Process hollowing: Dridex can inject its code into a legitimate process in order to evade detection by security software. Anti-debugging and anti-virtualization: Dridex can detect if it is running in a virtualized environment or if it is being debugged, and will terminate itself if it is. Dridex is a well-known and sophisticated banking trojan that has been active for more than a decade, the malware has been known to target financial institutions, businesses, and individuals. Despite the arrest of one of its administrators in 2015, the malware continues to be active and evolve. Recent infection on Macs: The recent variant of Dridex malware that targets MacOS systems delivers malicious macros via documents in a new way. The malware typically spreads through spam email campaigns, with the emails containing a malicious attachment or link that, when clicked, will install the malware on the victim\'s computer. The variant overwrites document files to carry Dridex\'s malicious macros, but currently, the payload it delivers is a Microsoft exe file, which won\'t run on a MacOS environment. This suggests that the variant may still be in the testing stages and not yet fully converted to work on MacOS machines. However, it\'s possible that the attackers will make further modifications to make it compatible with MacOS in the future. Once the malware is installed on the system, it searches for files with .doc extensions and overwrites them with the malicious code. The overwritten code has a D0CF file format signature, implying it is a Microsoft document file. This means that the malicious macros are delivered via document files, which makes it harder for the user to determine if the file is malicious or not. The malware also uses basic string encryption to hide the malicious URL it connects to in order to retrieve a file. This method of delivery is different from the traditional method of delivery, which is through email attachments. This shows that the attackers behind Dridex are trying to find new targets and more efficient methods of entry. How it works: Dridex is a banking Trojan that is typically distributed through phishing email campaigns. The malware is delivered as an attachment, often in the form of a Word or Excel document, that contains a malicious macro. Once the macro is enabled, it will download and execute the Dridex payload on the victim\'s system. Once installed, Dridex can perform a variety of malicious actions, including keylogging, capturing scre | Spam Malware Guideline | ★★★ | ||
| 2023-03-27 08:56:44 | Zoominfo opt et supprimez vos informations [ZoomInfo Opt Out & Remove Your Info] (lien direct) | Obtenir des appels de télémarketing plus ennuyeux et des e-mails spams ces derniers temps?Cela pourrait être Zoominfo faire son truc, en vous assurant que vos informations personnelles sont à jour et facilement accessibles à tous.Heureusement, le processus d'opt-out de Zoominfo \\ est assez rapide et facile, surtout si vous suivez notre guide étape par étape.Tout ce que vous avez à faire est de «vérifier» votre e-mail de travail (après avoir fait & # 8230; zoominfo opt out & # 038; supprimer vos informations en savoir plus & # 187;
Getting more annoying telemarketing calls and spam emails lately? Could be ZoomInfo doing its thing, making sure your personal information is up-to-date and easily accessible to all. Luckily, ZoomInfo\'s opt-out process is fairly quick and easy, especially if you follow our step-by-step guide. All you have to do is “verify” your work email (after making … ZoomInfo Opt Out & Remove Your Info Read More » |
Spam Guideline | ★★★★ | ||
| 2023-03-27 07:25:54 | Sophos montre comment faire du chatppt un copilote de cybersécurité [Sophos Demonstrates How to Make ChatGPT a Cybersecurity Co-Pilot] (lien direct) | Sophos montre comment faire du chatppt un co-pilot de cybersécurité
Le modèle d'IA peut filtrer plus facilement l'activité malveillante dans la télémétrie XDR, améliorer les filtres de spam et simplifier l'analyse de la vie des binaires terrestres
-
rapports spéciaux
Sophos Demonstrates How to Make ChatGPT a Cybersecurity Co-Pilot The AI Model Can More Easily Filter Malicious Activity in XDR Telemetry, Improve Spam Filters, and Simplify the Analysis of Living Off the Land Binaries - Special Reports |
Spam | ChatGPT ChatGPT | ★★ | |
| 2023-03-27 04:15:09 | CVE-2023-24835 (lien direct) | SoftNext Technologies Corp. & aLilde; & cent; & acirc; & sbquo; & not; & acirc; & bdquo; & cent; s spam sqr a une vulnérabilité de l'injection de code dans sa fonction spécifique.Un attaquant distant authentifié avec privilège administrateur peut exploiter cette vulnérabilité pour exécuter la commande arbitraire du système pour effectuer un fonctionnement du système arbitraire ou un service de perturbation.
Softnext Technologies Corp.’s SPAM SQR has a vulnerability of Code Injection within its specific function. An authenticated remote attacker with administrator privilege can exploit this vulnerability to execute arbitrary system command to perform arbitrary system operation or disrupt service. |
Spam Vulnerability | |||
| 2023-03-23 14:18:54 | Seulement 1% des domaines à but non lucratif ont des protections de sécurité par e-mail DMARC de base [Just 1% of Nonprofit Domains Have Basic DMARC Email Security Protections] (lien direct) | DMARC bloque le spam et les e-mails de phishing envoyés à partir de domaines usurpés, et il est largement sous-utilisé, indique un nouveau rapport.
DMARC blocks spam and phishing emails sent from spoofed domains, and it\'s vastly underutilized, a new report says. |
Spam Studies | ★★ | ||
| 2023-03-20 17:56:00 | Mispadu Banking Trojan Targets Latin America: 90,000+ Credentials Stolen (lien direct) | A banking trojan dubbed Mispadu has been linked to multiple spam campaigns targeting countries like Bolivia, Chile, Mexico, Peru, and Portugal with the goal of stealing credentials and delivering other payloads. The activity, which commenced in August 2022, is currently ongoing, Ocelot Team from Latin American cybersecurity firm Metabase Q said in a report shared with The Hacker News. Mispadu ( | Spam | ★★ | ||
| 2023-03-14 13:00:00 | CyberheistNews Vol 13 #11 [Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears (lien direct) |
 CyberheistNews Vol 13 #11 | March 14th, 2023
[Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information. Yikes.
I'm giving you a short extract of the story and the link to the whole article is below.
"Employees are submitting sensitive business data and privacy-protected information to large language models (LLMs) such as ChatGPT, raising concerns that artificial intelligence (AI) services could be incorporating the data into their models, and that information could be retrieved at a later date if proper data security isn't in place for the service.
"In a recent report, data security service Cyberhaven detected and blocked requests to input data into ChatGPT from 4.2% of the 1.6 million workers at its client companies because of the risk of leaking confidential info, client data, source code, or regulated information to the LLM.
"In one case, an executive cut and pasted the firm's 2023 strategy document into ChatGPT and asked it to create a PowerPoint deck. In another case, a doctor input his patient's name and their medical condition and asked ChatGPT to craft a letter to the patient's insurance company.
"And as more employees use ChatGPT and other AI-based services as productivity tools, the risk will grow, says Howard Ting, CEO of Cyberhaven.
"'There was this big migration of data from on-prem to cloud, and the next big shift is going to be the migration of data into these generative apps," he says. "And how that plays out [remains to be seen] - I think, we're in pregame; we're not even in the first inning.'"
Your employees need to be stepped through new-school security awareness training so that they understand the risks of doing things like this.
Blog post with links:https://blog.knowbe4.com/employees-are-feeding-sensitive-biz-data-to-chatgpt-raising-security-fears
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blockl
CyberheistNews Vol 13 #11 | March 14th, 2023
[Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information. Yikes.
I'm giving you a short extract of the story and the link to the whole article is below.
"Employees are submitting sensitive business data and privacy-protected information to large language models (LLMs) such as ChatGPT, raising concerns that artificial intelligence (AI) services could be incorporating the data into their models, and that information could be retrieved at a later date if proper data security isn't in place for the service.
"In a recent report, data security service Cyberhaven detected and blocked requests to input data into ChatGPT from 4.2% of the 1.6 million workers at its client companies because of the risk of leaking confidential info, client data, source code, or regulated information to the LLM.
"In one case, an executive cut and pasted the firm's 2023 strategy document into ChatGPT and asked it to create a PowerPoint deck. In another case, a doctor input his patient's name and their medical condition and asked ChatGPT to craft a letter to the patient's insurance company.
"And as more employees use ChatGPT and other AI-based services as productivity tools, the risk will grow, says Howard Ting, CEO of Cyberhaven.
"'There was this big migration of data from on-prem to cloud, and the next big shift is going to be the migration of data into these generative apps," he says. "And how that plays out [remains to be seen] - I think, we're in pregame; we're not even in the first inning.'"
Your employees need to be stepped through new-school security awareness training so that they understand the risks of doing things like this.
Blog post with links:https://blog.knowbe4.com/employees-are-feeding-sensitive-biz-data-to-chatgpt-raising-security-fears
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blockl |
Ransomware Data Breach Spam Malware Threat Guideline Medical | ChatGPT ChatGPT | ★★ | |
| 2023-03-14 10:30:00 | NCSC warns over AI language models but rejects cyber alarmism (lien direct) |
 CyberheistNews Vol 13 #11 | March 14th, 2023
[Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information. Yikes.
I'm giving you a short extract of the story and the link to the whole article is below.
"Employees are submitting sensitive business data and privacy-protected information to large language models (LLMs) such as ChatGPT, raising concerns that artificial intelligence (AI) services could be incorporating the data into their models, and that information could be retrieved at a later date if proper data security isn't in place for the service.
"In a recent report, data security service Cyberhaven detected and blocked requests to input data into ChatGPT from 4.2% of the 1.6 million workers at its client companies because of the risk of leaking confidential info, client data, source code, or regulated information to the LLM.
"In one case, an executive cut and pasted the firm's 2023 strategy document into ChatGPT and asked it to create a PowerPoint deck. In another case, a doctor input his patient's name and their medical condition and asked ChatGPT to craft a letter to the patient's insurance company.
"And as more employees use ChatGPT and other AI-based services as productivity tools, the risk will grow, says Howard Ting, CEO of Cyberhaven.
"'There was this big migration of data from on-prem to cloud, and the next big shift is going to be the migration of data into these generative apps," he says. "And how that plays out [remains to be seen] - I think, we're in pregame; we're not even in the first inning.'"
Your employees need to be stepped through new-school security awareness training so that they understand the risks of doing things like this.
Blog post with links:https://blog.knowbe4.com/employees-are-feeding-sensitive-biz-data-to-chatgpt-raising-security-fears
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blockl
CyberheistNews Vol 13 #11 | March 14th, 2023
[Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information. Yikes.
I'm giving you a short extract of the story and the link to the whole article is below.
"Employees are submitting sensitive business data and privacy-protected information to large language models (LLMs) such as ChatGPT, raising concerns that artificial intelligence (AI) services could be incorporating the data into their models, and that information could be retrieved at a later date if proper data security isn't in place for the service.
"In a recent report, data security service Cyberhaven detected and blocked requests to input data into ChatGPT from 4.2% of the 1.6 million workers at its client companies because of the risk of leaking confidential info, client data, source code, or regulated information to the LLM.
"In one case, an executive cut and pasted the firm's 2023 strategy document into ChatGPT and asked it to create a PowerPoint deck. In another case, a doctor input his patient's name and their medical condition and asked ChatGPT to craft a letter to the patient's insurance company.
"And as more employees use ChatGPT and other AI-based services as productivity tools, the risk will grow, says Howard Ting, CEO of Cyberhaven.
"'There was this big migration of data from on-prem to cloud, and the next big shift is going to be the migration of data into these generative apps," he says. "And how that plays out [remains to be seen] - I think, we're in pregame; we're not even in the first inning.'"
Your employees need to be stepped through new-school security awareness training so that they understand the risks of doing things like this.
Blog post with links:https://blog.knowbe4.com/employees-are-feeding-sensitive-biz-data-to-chatgpt-raising-security-fears
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blockl |
Spam | ★★ | ||
| 2023-03-13 10:00:00 | Insights from an external incident response team: Strategies to reduce the impact of cybersecurity attacks (lien direct) | The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. "Why are you here if you cannot decrypt our data?" This is how people sometimes react to the arrival of the external incident response team. In this article, I will try to answer this question, but at the same time, I am going to describe the stages of incident response, list the main mistakes that play into the hands of hackers, and give basic advice on how to respond. Let's start by defining what a security incident is. Although the concept is straightforward, various companies may interpret it differently. For instance, some companies may consider incidents to include situations such as a power supply failure or a hard drive malfunction, while others may only classify malicious actions as incidents. In theory, an incident is a moment when some kind of undesirable event occurs. In practice, the definition of an "undesirable event" is determined by each company's own interpretation and perspective. For one organization, the discovery of a phishing email is what requires investigation. Other companies may not see the point in worrying about such incidents. For instance, they may not be concerned about a phishing email being opened on an employee device in a remote location not connected to the main infrastructure since it poses no immediate threat. There are also interesting cases here. For example, online traders consider a drop in the speed of interaction with the online exchange by 1% to be a serious incident. In many industries, proper incident response steps and cybersecurity in general, cannot be overestimated. But if we are talking about serious incidents, then most often, these are events related to the penetration of an attacker into the corporate network. This annoys the vast majority of business leaders. Incident response stages While the interpretation of certain events as security incidents may vary depending on various factors such as context and threat model, the response steps are often the same. These response steps are primarily based on the old SANS standard, which is widely used by many security professionals. SANS identifies six stages of incident response: Preparation Identification Containment Eradication Recovery Lessons learned It is important to note that the external response team is not immediately involved in this process. Preparation Preparation involves properly aligning organizational and technical processes. These are universal measures that should be implemented effectively across all areas: Inventory networks Build subnets correctly Use correct security controls and tools Hire the right people All this is not directly related to the external response team and, at the same time, affects its work significantly. The response is based on preparatory steps. For example, it relies heavily on the log retention policy. Each attack has its own dwell time - the time from an attacker entering the network until their activity is detected. If the attack has an extended dwell time (three-four months) and the logs are kept for seven days, it will be much more difficult for the investigation team to fin | Spam Malware Vulnerability Threat Guideline | ★★★ | ||
| 2023-03-13 00:00:00 | Emotet Returns, Now Adopts Binary Padding for Evasion (lien direct) | Following a three-month hiatus, Emotet spam activities resumed in March 2023, when a botnet known as Epoch 4 began delivering malicious documents embedded in Zip files that were attached to the emails. | Spam | ★★★ | ||
| 2023-02-22 16:47:00 | Attackers Flood NPM Repository with Over 15,000 Spam Packages Containing Phishing Links (lien direct) | In what's a continuing assault on the open source ecosystem, over 15,000 spam packages have flooded the npm repository in an attempt to distribute phishing links. "The packages were created using automated processes, with project descriptions and auto-generated names that closely resembled one another," Checkmarx researcher Yehuda Gelb said in a Tuesday report. "The attackers referred to retail | Spam | ★★ |
To see everything:
Our RSS (filtrered)
