What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2021-04-01 14:00:00 | The Origins of the Names TaoSecurity and the Unit Formerly Known as TAO (lien direct) |  What are the origins of the names TaoSecurity and the unit formerly known as TAO? IntroductionI've been reading Nicole Perlroth's new book This Is How They Tell Me the World Ends. Her discussion of the group formerly known as Tailored Access Operations, or TAO, reminded me of a controversy that arose in the 2000s. I had heard through back channels that some members of that group were upset that I was operating using the name TaoSeurity. In the 2000s and early 2010s I taught classes under the TaoSecurity brand, and even ran TaoSecurity as a single-person consultancy from 2005-2007. The purpose of this post is to explain why, how, and when I chose the TaoSecurity identity, and to show that it is contemporaneous with the formal naming of the TAO group. The most reliable accounts indicate TaoSecurity predates the TAO brand.TaoSecurity Began with Kung Fu and Taoism What are the origins of the names TaoSecurity and the unit formerly known as TAO? IntroductionI've been reading Nicole Perlroth's new book This Is How They Tell Me the World Ends. Her discussion of the group formerly known as Tailored Access Operations, or TAO, reminded me of a controversy that arose in the 2000s. I had heard through back channels that some members of that group were upset that I was operating using the name TaoSeurity. In the 2000s and early 2010s I taught classes under the TaoSecurity brand, and even ran TaoSecurity as a single-person consultancy from 2005-2007. The purpose of this post is to explain why, how, and when I chose the TaoSecurity identity, and to show that it is contemporaneous with the formal naming of the TAO group. The most reliable accounts indicate TaoSecurity predates the TAO brand.TaoSecurity Began with Kung Fu and Taoism With Sifu Michael Macaris, 21 June 1996In the summer of 1994, after graduating from the Air Force Academy and before beginning my graduate program at what is now called the Harvard Kennedy School, I started watching re-runs of the 1970s David Carradine Kung Fu TV series, created by Ed Spielman. I was so motivated by the philosophical message of the program that I joined a kung fu school in Massachusetts. I trained there for two years, and studied what I could about Chinese history and culture. I learned from the show and that it was based on Taoism (for example) so I bought a copy of the Tao Te Ching by Lao Tzu and devoured it. Visiting China With Sifu Michael Macaris, 21 June 1996In the summer of 1994, after graduating from the Air Force Academy and before beginning my graduate program at what is now called the Harvard Kennedy School, I started watching re-runs of the 1970s David Carradine Kung Fu TV series, created by Ed Spielman. I was so motivated by the philosophical message of the program that I joined a kung fu school in Massachusetts. I trained there for two years, and studied what I could about Chinese history and culture. I learned from the show and that it was based on Taoism (for example) so I bought a copy of the Tao Te Ching by Lao Tzu and devoured it. Visiting China Tai Chi on the Yangtze, May 1999In the spring of 1999 my wife and I took a three week trip to Chin Tai Chi on the Yangtze, May 1999In the spring of 1999 my wife and I took a three week trip to Chin |
Malware Threat | |||
| 2020-03-12 09:29:36 | COVID-19 Phishing Tests: WRONG (lien direct) | Malware Jake Tweeted a poll last night which asked the following:"I have an interesting ethical quandary. Is it ethically okay to use COVID-19 themed phishing emails for assessments and user awareness training right now? Please read the thread before responding and RT for visibility. 1/"Ultimately he decided:"My gut feeling is to not use COVID-19 themed emails in assessments/training, but to TELL users to expect them, though I understand even that might discourage consumption of legitimate information, endangering public health. 6/"I responded by saying this was the right answer.Thankfully there were many people who agreed, despite the fact that voting itself was skewed towards the "yes" answer.There were an uncomfortable number of responses to the Tweet that said there's nothing wrong with red teams phishing users with COVID-19 emails. For example:"Do criminals abide by ethics? Nope. Neither should testing.""Yes. If it's in scope for the badguys [sic], it's in scope for you.""Attackers will use it. So I think it is fair game."Those are the wrong answers. As a few others outlined well in their responses, the fact that a criminal or intruder employs a tactic does not mean that it's appropriate for an offensive security team to use it too.I could imagine several COVID-19 phishing lures that could target school districts and probably cause high double-digit click-through rates. What's the point of that? For a "community" that supposedly considers fear, uncertainty, and doubt (FUD) to be anathema, why introduce FUD via a phishing test?I've grown increasingly concerned over the past few years that there's a "cult of the offensive" that justifies its activities with the rationale that "intruders do it, so we should too." This is directly observable in the replies to Jake's Tweet. It's a thin veneer that covers bad behavior, outweighing the small benefit accrued to high-end, 1% security shops against the massive costs suffered by the vast majority of networked global organizations.The is a selfish, insular mindset that is reinforced by the echo chamber of the so-called "infosec community." This "tribe" is detached from the concerns and ethics of the larger society. It tells itself that what it is doing is right, oblivious or unconcerned with the costs imposed on the organizations they are supposedly "protecting" with their backwards actions.We need people with feet in both worlds to tell this group that their approach is not welcome in the broader human community, because the costs it imposes vastly outweigh the benefits.I've written here about ethics before, usually in connection with the only real value I saw in the CISSP -- its code of ethics. Reviewing the "code," as it appears now, shows the following:"There are only four mandatory canons in the Code. By necessity, such high-level guidance is not intended to be a substitute for the ethical judgment of the professional.Code of Ethics Preamble:The safety and welfare of society and the common good, duty to our principals, and to each other, requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior.Therefore, strict adherence to this Code is a condition of certification.Code of Ethics Canons:Protect society, the common good, necessary public trust and confidence, and the infrastructure.Act honorably, honestly, justly, responsibly, and legally.Provide diligent and competent service to principals.Advance and protect the profession."This is | Malware | |||
| 2018-11-25 15:48:54 | The Origin of the Term Indicators of Compromise (IOCs) (lien direct) |  I am an historian. I practice digital security, but I earned a bachelor's of science degree in history from the United States Air Force Academy. (1)Historians create products by analyzing artifacts, among which the most significant is the written word.In my last post, I talked about IOCs, or indicators of compromise. Do you know the origin of the term? I thought I did, but I wanted to rely on my historian's methodology to invalidate or confirm my understanding.I became aware of the term "indicator" as an element of indications and warning (I&W), when I attended Air Force Intelligence Officer's school in 1996-1997. I will return to this shortly, but I did not encounter the term "indicator" in a digital security context until I encountered the work of Kevin Mandia.In August 2001, shortly after its publication, I read Incident Response: Investigating Computer Crime, by Kevin Mandia, Chris Prosise, and Matt Pepe (Osborne/McGraw-Hill). I was so impressed by this work that I managed to secure a job with their company, Foundstone, by April 2002. I joined the Foundstone incident response team, which was led by Kevin and consisted of Matt Pepe, Keith Jones, Julie Darmstadt, and me.I Tweeted earlier today that Kevin invented the term "indicator" (in the IR context) in that 2001 edition, but a quick review of the hard copy in my library does not show its usage, at least not prominently. I believe we were using the term in the office but that it had not appeared in the 2001 book. Documentation would seem to confirm that, as Kevin was working on the second edition of the IR book (to which I contributed), and that version, published in 2003, features the term "indicator" in multiple locations.In fact, the earliest use of the term "indicators of compromise," appearing in print in a digital security context, appears on page 280 in Incident Response & Computer Forensics, 2nd Edition. I am an historian. I practice digital security, but I earned a bachelor's of science degree in history from the United States Air Force Academy. (1)Historians create products by analyzing artifacts, among which the most significant is the written word.In my last post, I talked about IOCs, or indicators of compromise. Do you know the origin of the term? I thought I did, but I wanted to rely on my historian's methodology to invalidate or confirm my understanding.I became aware of the term "indicator" as an element of indications and warning (I&W), when I attended Air Force Intelligence Officer's school in 1996-1997. I will return to this shortly, but I did not encounter the term "indicator" in a digital security context until I encountered the work of Kevin Mandia.In August 2001, shortly after its publication, I read Incident Response: Investigating Computer Crime, by Kevin Mandia, Chris Prosise, and Matt Pepe (Osborne/McGraw-Hill). I was so impressed by this work that I managed to secure a job with their company, Foundstone, by April 2002. I joined the Foundstone incident response team, which was led by Kevin and consisted of Matt Pepe, Keith Jones, Julie Darmstadt, and me.I Tweeted earlier today that Kevin invented the term "indicator" (in the IR context) in that 2001 edition, but a quick review of the hard copy in my library does not show its usage, at least not prominently. I believe we were using the term in the office but that it had not appeared in the 2001 book. Documentation would seem to confirm that, as Kevin was working on the second edition of the IR book (to which I contributed), and that version, published in 2003, features the term "indicator" in multiple locations.In fact, the earliest use of the term "indicators of compromise," appearing in print in a digital security context, appears on page 280 in Incident Response & Computer Forensics, 2nd Edition. From other uses of the term "indicators" in that IR book, you can observe that IOC wasn't a formal, independent concept at this point, in 2003. In the same excerpt above you see "indicators of attack" mentioned.The first citation of the term "indicators" in the 2003 book shows it is meant as an investigative lead or tip: From other uses of the term "indicators" in that IR book, you can observe that IOC wasn't a formal, independent concept at this point, in 2003. In the same excerpt above you see "indicators of attack" mentioned.The first citation of the term "indicators" in the 2003 book shows it is meant as an investigative lead or tip: |
Malware Tool Guideline | |||
| 2018-11-24 15:23:09 | Even More on Threat Hunting (lien direct) |  In response to my post More on Threat Hunting, Rob Lee asked:[D]o you consider detection through ID'ing/“matching” TTPs not hunting?To answer this question, we must begin by clarifying "TTPs." Most readers know TTPs to mean tactics, techniques and procedures, defined by David Bianco in his Pyramid of Pain post as:How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between.In case you've forgotten David's pyramid, it looks like this. In response to my post More on Threat Hunting, Rob Lee asked:[D]o you consider detection through ID'ing/“matching” TTPs not hunting?To answer this question, we must begin by clarifying "TTPs." Most readers know TTPs to mean tactics, techniques and procedures, defined by David Bianco in his Pyramid of Pain post as:How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between.In case you've forgotten David's pyramid, it looks like this.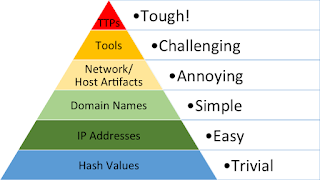 It's important to recognize that the pyramid consists of indicators of compromise (IOCs). David uses the term "indicator" in his original post, but his follow-up post from his time at Sqrrl makes this clear:There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Sqrrl Security Architect, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. At this point it should be clear that I consider TTPs to be one form of IOC.In The Practice of Network Security Monitoring, I included the following workflow: It's important to recognize that the pyramid consists of indicators of compromise (IOCs). David uses the term "indicator" in his original post, but his follow-up post from his time at Sqrrl makes this clear:There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Sqrrl Security Architect, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. At this point it should be clear that I consider TTPs to be one form of IOC.In The Practice of Network Security Monitoring, I included the following workflow: |
Malware Threat |
1
We have: 4 articles.
We have: 4 articles.
To see everything:
Our RSS (filtrered)
