What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-10-17 13:00:00 | Newly Discovered Iranian APT Group Brings State-sponsored Cyber Espionage into Focus (lien direct) | State-sponsored cyber espionage has been rising steadily in recent years. Whether it’s high-profile attacks such as North Korea’s hack of Sony in 2014, China’s alleged hack of the US’s Office of Personnel Management in 2015, or Russia’s alleged hack of the Democratic National Committee in 2016, the stories are mounting. Iran has also been in the cyber espionage news, with major suspected attacks ranging from the Las Vegas Sands attack in 2014 to the DDOS attack on numerous US banks in 2016. Beyond these high-profile attacks, there are also countless examples of low-profile attacks. While these attacks don’t make the major headlines, they may actually be more relevant to your organization. In this blog, we zero in on this lesser-publicized activity, focusing on a recently discovered Iranian hacker group, dubbed APT33, the tools they have developed, and how AlienVault can help you detect this activity in your environment. What is state-sponsored cyber espionage and what are the typical goals? First, a quick primer on state-sponsored cyber espionage. State-sponsored cyber espionage is the act of obtaining secrets and information from individuals, competitors, rivals, groups, governments, and enemies, without the permission and knowledge of the holder of the information, usually for economic, political, or military advantage. The goals of these state-sponsored groups or individuals range from basic theft or sabotage to collecting military and diplomatic information to enabling domestic organizations to compete on a global economic level. Why should you care? Should you be concerned about state-sponsored cyber hacks? In a word, yes. And, it’s really the low-profile attacks from state-sponsored hackers that should be most concerning. This is because the tools and methods that these hackers develop and utilize can be leveraged by other nefarious hackers against your organization. You need to be alerted to and protected against these tools. Who is APT33? This leads us to Iranian group Advanced Persistent Threat 33 (APT33), a group recently chronicled by security firm FireEye. FireEye assessed that APT33 works at the behest of the Iranian government, and they attribute to APT33 many breaches of Saudi Arabian, South Korean, and US organizations ranging from the aviation sector to the energy sector. The primary goals of APT33 appear to be to enhance Iran’s domestic aviation capabilities or to support Iran’s military decision making against Saudi Arabia. Notably, FireEye has found signs of APT33 activity in some of its own clients' networks, but suspects the APT33 intrusions have been on a wider scale. APT33 has unveiled new tools, including a new backdoor. APT33 has developed numerous tools, including a new backdoor called TURNEDUP. TURNEDUP is capable of uploading and downloading files, creating a reverse shell, taking screenshots, and gathering system information. FireEye found that APT33 has also leveraged Dropshot, a drop | Guideline | APT33 APT 33 | ||
| 2017-09-22 13:00:00 | Things I hearted this week - September 22 (lien direct) | It’s been another hectic week in the world of Infosec / IT security / Cyber Security (choose as appropriate). So let’s jump straight into it. APT 33 Iran is building up its cyber capabilities and the emergence of a group of hackers, dubbed APT33, has given rise to concerns the nation's cyberwarfare units are looking to launch destructive attacks on critical infrastructure, energy and military bodies. Meet APT33: A Gnarly Iranian Hacker Crew Threatening Destruction |Forbes Threat data, IOCs and information on APT33, aka greenbug | OTX Data breaches and Class action lawsuits Should individuals whose data has been breached have the right to sue companies? It’s a tricky question, and one that the courts are seemingly having trouble on deciding on. Recently, a judge dismissed two consolidated class actions by more than 21m federal employees who had information breached by the Office of Personnel Management (OPM). The Judge concluded that the federal employees could not establish their threshold right to sue in federal court because they had not shown they faced imminent risk of identity theft, even though nearly two dozen of those named in the class actions claimed their confidential information has already been misused. Hopefully things will change going forward. The problem with identity theft is that it’s not time-dependant. An attacker could hoard details for a long period before committing a crime. And even when an identity is stolen, it is difficult to tie back to where the breach occurred. OPM Data Breach Lawsuit Tossed, Fed Plaintiffs will Appeal | Dark Reading OPM Says Gov't Workers' Data Breach Suit Fails | Law360 In the long run, class actions may not be the best way to redress data breaches | Reuters Somewhat related, My three years in identity theft hell | Bloomberg The Ghost of Windows XP As the lyrics go, “They stab it with their steely knives, but they just can’t kill the beast.” In this case, the beast seems to be Win XP, which, despite being woefully outdated, continues to make its presence felt. The latest announcement being that a fifth of the Manchester police department are running Win XP. Manchester police still relies on Windows XP | BBC Manchester Police are using Windows XP on one in five computers | V3 When insurance goes too far Melina Efthimiadis along with her husband wanted to add personal umbrella liability insurance to their Nationwide homeowner's policy. She says they have been low risk clients so she didn't think it would be a problem. In the application process for Nationwide, Melina says they had to write down the number of dogs they owned and their breeds, wh | Guideline | CCleaner APT33 APT 33 | ||
| 2017-05-17 03:33:55 | WanaCrypt0r Ransomworm (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDSince the release of the ETERNALBLUE exploit by 'The Shadow Brokers' last month security researchers have been watching for a mass attack on global networks. This came on Friday 12th May when it was bundled with ransomware called WanaCrypt0r and let loose. Initial reports of attacks were highlighted by Telefonica in Spain but the malware quickly spread to networks in the UK where the National Health Service (NHS) was impacted, followed by many other networks across the world.The infographic below illustrates the key components of the WanaCrypt0r ransomware. This is described in further detail in subsequent sections of this report along with initial clues on attribution.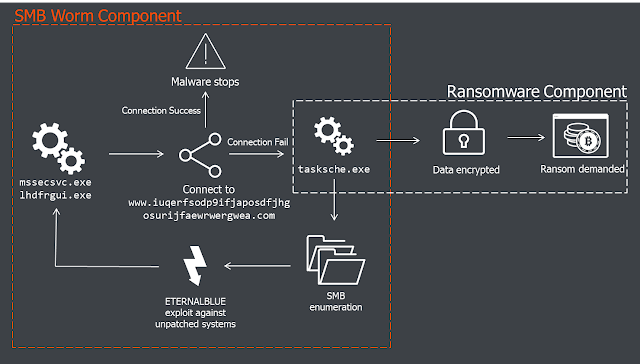 ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs |
Guideline Medical | Wannacry APT 38 | ||
| 2017-03-06 12:13:22 | Lazarus & Watering-hole attacks (lien direct) | On 3rd February 2017, researchers at badcyber.com released an article that detailed a series of attacks directed at Polish financial institutions. The article is brief, but states that "This is – by far – the most serious information security incident we have seen in Poland" followed by a claim that over 20 commercial banks had been confirmed as victims.This report provides an outline of the attacks based on what was shared in the article, and our own additional findings. ANALYSISAs stated in the blog, the attacks are suspected of originating from the website of the Polish Financial Supervision Authority (knf.gov[.]pl), shown below: From at least 2016-10-07 to late January the website code had been modified to cause visitors to download malicious JavaScript files from the following locations: hxxp://sap.misapor[.]ch/vishop/view.jsp?pagenum=1hxxps://www.eye-watch[.]in/design/fancybox/Pnf.action Both of these appear to be compromised domains given they are also hosting legitimate content and have done for some time. The malicious JavaScript leads to the download of malware to the victim's device. Some hashes of the backdoor have been provided in BadCyber's technical analysis: 85d316590edfb4212049c4490db08c4bc1364bbf63b3617b25b58209e4529d8c1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae The C&Cs given in the BadCyber analysis were the following IP addresses: 125.214.195.17196.29.166.218 LAZARUS MALWAREOnly one of the samples referenced by BadCyber is available in public malware repositories. At the moment we cannot verify that it originated from the watering-hole on the KNF website – but we have no reason to doubt this either. MD5 hash Filename File Info First seen From at least 2016-10-07 to late January the website code had been modified to cause visitors to download malicious JavaScript files from the following locations: hxxp://sap.misapor[.]ch/vishop/view.jsp?pagenum=1hxxps://www.eye-watch[.]in/design/fancybox/Pnf.action Both of these appear to be compromised domains given they are also hosting legitimate content and have done for some time. The malicious JavaScript leads to the download of malware to the victim's device. Some hashes of the backdoor have been provided in BadCyber's technical analysis: 85d316590edfb4212049c4490db08c4bc1364bbf63b3617b25b58209e4529d8c1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae The C&Cs given in the BadCyber analysis were the following IP addresses: 125.214.195.17196.29.166.218 LAZARUS MALWAREOnly one of the samples referenced by BadCyber is available in public malware repositories. At the moment we cannot verify that it originated from the watering-hole on the KNF website – but we have no reason to doubt this either. MD5 hash Filename File Info First seen |
Guideline Medical | APT 38 | ||
| 2017-03-06 12:13:03 | Lazarus\' False Flag Malware (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDWe continue to investigate the recent wave of attacks on banks using watering-holes on at least two financial regulator websites as well as others. Our initial analysis of malware disclosed in the BadCyber blog hinted at the involvement of the 'Lazarus' threat actor. Since the release of our report, more samples have come to light, most notably those described in the Polish language niebezpiecznik.pl blog on 7 February 2017. MD5 hash Filename Compile Time File Info Submitted 9216b29114fb6713ef228370cbfe4045 srservice.chm N/A N/A N/A 8e32fccd70cec634d13795bcb1da85ff srservice.hlp N/A N/A N/A e29fe3c181ac9ddb | Guideline Medical | APT 38 | ||
| 2016-09-30 09:07:00 | IDG Contributor Network: Treasures attackers look for in the sea of email (lien direct) | As we dive into October, cybersecurity awareness month, there are lots of strategies to help us all become stronger swimmers in the digital waters. Given that there are 112 billion business emails sent around the world every day, that is one huge ocean that everyone can learn how to better navigate.Since its inception, email has become mission critical, and so many necessities beyond mail service have grown up along with it. Enterprises have become burdened by the complexities of email, which additionally requires the added protections of encryption gateways, spam filters, phishing protections, and much more.In order to attack all of the issues of email security in the age of digital disruption, you first have to know what is beneath the rough seas.To read this article in full or to leave a comment, please click here | Guideline | APT 32 |
To see everything:
Our RSS (filtrered)
