What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-06-27 10:00:00 | Stories from the SOC - Detecting internal reconnaissance (lien direct) | Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Extended Detection and Response customers.
Executive summary
Internal Reconnaissance, step one of the Cyber Kill Chain, is the process of collecting internal information about a target network to identify vulnerabilities that can potentially be exploited. Threat actors use the information gained from this activity to decide the most effective way to compromise the target network. Vulnerable services can be exploited by threat actors and potentially lead to a network breach. A network breach puts the company in the hands of cybercriminals. This can lead to ransomware attacks costing the company millions of dollars to remediate along with a tarnished public image.
The Managed Extended Detection and Response (MXDR) analyst team received two alarms regarding an asset performing network scans within a customer's environment. Further investigation into these alarms revealed that the source asset was able to scan 60 unique IPs within the environment and successfully detected numerous open ports with known vulnerabilities.
Investigation
Initial alarm review
Indicators of Compromise (IOC)
The initial alarm that prompted this investigation was a Darktrace Cyber Intelligence Platform event that was ingested by USM Anywhere. The priority level associated with this alarm was High, one level below the maximum priority of Critical. Network scanning is often one of the first steps a threat actor takes when attempting to compromise a network, so it is a red flag any time an unknown device is scanning the network without permission. From here, the SOC went deeper into associated events to see what activity was taking place in the customer’s environment. The image shown below is the Darktrace alarm that initiated the investigation.
 Expanded investigation
Events search
Utilizing the filters built into USM Anywhere , the events were narrowed down to the specific source asset IP address and Host Name to only query events associated to that specific asset. The following events were found that provide more information about the reconnaissance activity that was being observed.
Expanded investigation
Events search
Utilizing the filters built into USM Anywhere , the events were narrowed down to the specific source asset IP address and Host Name to only query events associated to that specific asset. The following events were found that provide more information about the reconnaissance activity that was being observed.

 Event deep dive
Upon reviewing the logs from the events shown above, the SOC was able to determine that the source asset scanned two separate Classless Inter-Domain Routing (CIDR) blocks, detecting, and scanning 60 unique internal devices for open ports. As shown in the log snippets below, the scans revealed multiple open ports with known vulnerabilities, most notable is Server Message Block (SMB) port 445 which is the key attack vector for the infamous WannaCry malware. Looking at the logs we can also see that the source asset detected port 5985, the port utilized by Windows Remote Management (WinRM). WinRM can be used by threat actors to move laterally in environments by executing remote commands on other assets from the compromised host. These remote commands are typically batch files performing malicious activity or implanting backdoors to maintain persistence in the network. Lastly, we can see the asset scanning for Lightweight Directory Access Protocol (LD
Event deep dive
Upon reviewing the logs from the events shown above, the SOC was able to determine that the source asset scanned two separate Classless Inter-Domain Routing (CIDR) blocks, detecting, and scanning 60 unique internal devices for open ports. As shown in the log snippets below, the scans revealed multiple open ports with known vulnerabilities, most notable is Server Message Block (SMB) port 445 which is the key attack vector for the infamous WannaCry malware. Looking at the logs we can also see that the source asset detected port 5985, the port utilized by Windows Remote Management (WinRM). WinRM can be used by threat actors to move laterally in environments by executing remote commands on other assets from the compromised host. These remote commands are typically batch files performing malicious activity or implanting backdoors to maintain persistence in the network. Lastly, we can see the asset scanning for Lightweight Directory Access Protocol (LD |
Ransomware Malware Threat Guideline | Wannacry | ||
| 2022-05-11 12:57:31 | Wannacry – 5 Years On, 68% Of Enterprises Are Still At Risk (lien direct) | 5 years on from one of the world’s most damaging ransomware attacks, research from network detection and response leader ExtraHop has found that 68% of enterprises are still running insecure protocol that were exploited by the North Korean ransomware. | Ransomware Guideline | Wannacry | ★★★ | |
| 2022-02-01 14:37:29 | CyberheistNews Vol 12 #05 [Heads Up] DHS Sounds Alarm on New Russian Destructive Disk Wiper Attack Potential (lien direct) |
![CyberheistNews Vol 12 #05 [Heads Up] DHS Sounds Alarm on New Russian Destructive Disk Wiper Attack Potential](https://blog.knowbe4.com/hubfs/Stu_Headshot_2021_resize.png)
|
Ransomware Malware Hack Tool Threat Guideline | NotPetya NotPetya Wannacry Wannacry APT 27 APT 27 | ||
| 2021-03-17 18:03:00 | Anomali Cyber Watch: APT, Ransomware, Vulnerabilities and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, AlientBot, Clast82, China, DearCry, RedXOR, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Google: This Spectre proof-of-concept shows how dangerous these attacks can be
(published: March 15, 2021)
Google has released a proof of concept (PoC) code to demonstrate the practicality of Spectre side-channel attacks against a browser's JavaScript engine to leak information from its memory. Spectre targeted the process in modern CPUs called speculative execution to leak secrets such as passwords from one site to another. While the PoC demonstrates the JavaScript Spectre attack against Chrome 88's V8 JavaScript engine on an Intel Core i7-6500U CPU on Linux, Google notes it can easily be tweaked for other CPUs, browser versions and operating systems.
Analyst Comment: As the density of microchip manufacturing continues to increase, side-channel attacks are likely to be found across many architectures and are difficult (and in some cases impossible) to remediate in software. The PoC of the practicality of performing such an attack using javascript emphasises that developers of both software and hardware be aware of these types of attacks and the means by which they can be used to invalidate existing security controls.
Tags: CVE-2017-5753
Threat Assessment: DearCry Ransomware
(published: March 12, 2021)
A new ransomware strain is being used by actors to attack unpatched Microsoft Exchange servers. Microsoft released patches for four vulnerabilities that are being exploited in the wild. The initial round of attacks included installation of web shells onto affected servers that could be used to infect additional computers. While the initial attack appears to have been done by sophisticated actors, the ease and publicity around these vulnerabilities has led to a diverse group of actors all attempting to compromise these servers.
Analyst Comment: Patch and asset management are a critical and often under-resourced aspect of defense in depth. As this particular set of vulnerabilities and attacks are against locally hosted Exchange servers, organization may want to assess whether a hosted solution may make sense from a risk standpoint
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted - T1022 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] File and Directory Discovery - T1083 | [MITRE ATT&CK] Email Collection - T1114 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] System Service Discovery - T1007 | [MITRE ATT&CK] Data Encrypted for Impact - T1486 |
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Google: This Spectre proof-of-concept shows how dangerous these attacks can be
(published: March 15, 2021)
Google has released a proof of concept (PoC) code to demonstrate the practicality of Spectre side-channel attacks against a browser's JavaScript engine to leak information from its memory. Spectre targeted the process in modern CPUs called speculative execution to leak secrets such as passwords from one site to another. While the PoC demonstrates the JavaScript Spectre attack against Chrome 88's V8 JavaScript engine on an Intel Core i7-6500U CPU on Linux, Google notes it can easily be tweaked for other CPUs, browser versions and operating systems.
Analyst Comment: As the density of microchip manufacturing continues to increase, side-channel attacks are likely to be found across many architectures and are difficult (and in some cases impossible) to remediate in software. The PoC of the practicality of performing such an attack using javascript emphasises that developers of both software and hardware be aware of these types of attacks and the means by which they can be used to invalidate existing security controls.
Tags: CVE-2017-5753
Threat Assessment: DearCry Ransomware
(published: March 12, 2021)
A new ransomware strain is being used by actors to attack unpatched Microsoft Exchange servers. Microsoft released patches for four vulnerabilities that are being exploited in the wild. The initial round of attacks included installation of web shells onto affected servers that could be used to infect additional computers. While the initial attack appears to have been done by sophisticated actors, the ease and publicity around these vulnerabilities has led to a diverse group of actors all attempting to compromise these servers.
Analyst Comment: Patch and asset management are a critical and often under-resourced aspect of defense in depth. As this particular set of vulnerabilities and attacks are against locally hosted Exchange servers, organization may want to assess whether a hosted solution may make sense from a risk standpoint
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted - T1022 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] File and Directory Discovery - T1083 | [MITRE ATT&CK] Email Collection - T1114 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] System Service Discovery - T1007 | [MITRE ATT&CK] Data Encrypted for Impact - T1486 | |
Ransomware Tool Vulnerability Threat Guideline | Wannacry APT 41 APT 34 | ||
| 2021-03-03 11:00:00 | Extended threat detection and response (XDR): Filling out cybersecurity gaps (lien direct) |
This blog was written by an independent guest blogger.
|
Tool Threat Guideline | Wannacry | ||
| 2020-05-12 13:08:58 | 30% des attaques visent les professionnels, Kaspersky et INTERPOL appellent les entreprises à se protéger (lien direct) |  A l'occasion de la date anniversaire de WannaCry – cyberattaque massive de 2017 – le leader mondial de la cybersécurité Kaspersky et l'organisation intergouvernementale INTERPOL s'associent pour appeler les professionnels à revoir leur stratégie de sauvegarde et de protection des données. Cette initiative s'inscrit dans le cadre des accords de partenariat conclus entre les deux […] A l'occasion de la date anniversaire de WannaCry – cyberattaque massive de 2017 – le leader mondial de la cybersécurité Kaspersky et l'organisation intergouvernementale INTERPOL s'associent pour appeler les professionnels à revoir leur stratégie de sauvegarde et de protection des données. Cette initiative s'inscrit dans le cadre des accords de partenariat conclus entre les deux […] |
Guideline | Wannacry | ||
| 2019-11-04 17:53:28 | Ransomware hits Spanish companies, sparking WannaCry panic (lien direct) | Two victims reported so far: IT consultancy firm Everis and leading radio network Cadena SER. | Ransomware Guideline | Wannacry | ||
| 2019-09-18 13:00:00 | Does your government take cybersecurity seriously enough? (lien direct) |
 Photo by Katie Moum on Unsplash
Cybercrime is global, but the response isn’t. Governments in the west are slowly waking up to the importance of cybersecurity, and are (equally slowly) helping businesses to safeguard data and home users to protect their homes from cyberattack.
Look outside Europe and the US, though, and the picture is radically different. African countries, in particular, are underprepared for the impact of cyberattacks, and lack the governmental expertise to deal with them.
This is an issue for citizens of these countries, but also for us in the west. Poorly prepared countries act as safe havens for cybercriminals, and hackers (some of them state-sponsored) can use these countries to stage cyberattacks that directly impact users in the west.
Cybercrime: a global view
Though you wouldn’t know it from the press coverage, large cyberattacks don’t just affect the west.
Africa, for instance, actually has a huge problem with cybercrime. Recent reports from Botswana, Zimbabwe and Mozambique show that companies are increasingly falling victim to cybercrime. The global WannaCry malware attack of May 2017 hit South Africa hard, and companies in that country typically lose R36 million when they fall victim to an attack.
This situation is mirrored across the global south. It is made worse by the fact that developing nations do not have governmental policies for dealing with cyberattacks. This makes companies and home users in these countries particularly vulnerable. It also means that hackers can route their activities through these countries, which have neither the technical nor the legal expertise to catch them, let alone punish them.
Though government policies on cybercrime vary widely across the globe, many of the largest attacks of recent years rely for their success on their global reach. The Mirai Botnet, for instance, managed to infect IoT devices across a huge range of territories and countries, and this global base made it incredibly difficult to stop. Attacks like this have made the IoT one of the largest concerns among security professionals today.
Given this context, it is time for governments – in all countries and at all levels – to do more when it comes to managing cyber risk.
Managing risk
The approach that governments take to dealing with cyber risk is a critical factor in the success of these programs. Too often, governments take a ‘hands off’ approach, issuing advice to citizens and businesses about how to avoid falling victim to an attack, and then expecting them to protect themselves.
This approach i
Photo by Katie Moum on Unsplash
Cybercrime is global, but the response isn’t. Governments in the west are slowly waking up to the importance of cybersecurity, and are (equally slowly) helping businesses to safeguard data and home users to protect their homes from cyberattack.
Look outside Europe and the US, though, and the picture is radically different. African countries, in particular, are underprepared for the impact of cyberattacks, and lack the governmental expertise to deal with them.
This is an issue for citizens of these countries, but also for us in the west. Poorly prepared countries act as safe havens for cybercriminals, and hackers (some of them state-sponsored) can use these countries to stage cyberattacks that directly impact users in the west.
Cybercrime: a global view
Though you wouldn’t know it from the press coverage, large cyberattacks don’t just affect the west.
Africa, for instance, actually has a huge problem with cybercrime. Recent reports from Botswana, Zimbabwe and Mozambique show that companies are increasingly falling victim to cybercrime. The global WannaCry malware attack of May 2017 hit South Africa hard, and companies in that country typically lose R36 million when they fall victim to an attack.
This situation is mirrored across the global south. It is made worse by the fact that developing nations do not have governmental policies for dealing with cyberattacks. This makes companies and home users in these countries particularly vulnerable. It also means that hackers can route their activities through these countries, which have neither the technical nor the legal expertise to catch them, let alone punish them.
Though government policies on cybercrime vary widely across the globe, many of the largest attacks of recent years rely for their success on their global reach. The Mirai Botnet, for instance, managed to infect IoT devices across a huge range of territories and countries, and this global base made it incredibly difficult to stop. Attacks like this have made the IoT one of the largest concerns among security professionals today.
Given this context, it is time for governments – in all countries and at all levels – to do more when it comes to managing cyber risk.
Managing risk
The approach that governments take to dealing with cyber risk is a critical factor in the success of these programs. Too often, governments take a ‘hands off’ approach, issuing advice to citizens and businesses about how to avoid falling victim to an attack, and then expecting them to protect themselves.
This approach i |
Malware Vulnerability Threat Guideline | Wannacry | ||
| 2019-09-09 13:00:00 | Category 1 cyber threat for UK businesses (lien direct) |
 Julia Solonina
Britain should be prepared for a Category 1 cyber security emergency, according to the National Cyber Security Centre (NCSC). This means that national security, the economy, and even the nation’s lives will be at risk. However, despite this harsh warning, UK businesses still aren’t taking proactive and potentially preventative action to stop these attacks from happening. So just where are UK businesses going wrong and can they turn things around before it’s too late?
How businesses have responded
Since Brexit was announced in June 2016, 53% of UK businesses have increased their cyber security, according to latest statistics. This is as a direct result of industry data being published which revealed that malware, phishing, and ransomware attacks will become the biggest threats once Britain leaves the EU. However, despite these efforts being made, figures reveal that British businesses have the smallest cyber security budget compared to any other country. They typically spend less than £900,000, whereas the average across the world is $1.46 million.
At risk of a Category 1 cyber attack
A Category 1 cyber attack is described by the NCSC as “A cyber attack which causes sustained disruption of UK essential services or affects UK national security, leading to severe economic or social consequences or to loss of life.” To date, the UK has never witnessed such an attack. Although, one of the most severe attacks in recent times was the 2017 NHS cyber attack which was classed as a Category 2 due to there being no imminent threat to life.
The NCSC says that they typically prevent 10 cyber attacks from occurring on a daily basis. However, as the organization believes that hostility from neighbouring nations is what drives these attacks every single day, they say that it’s only a matter of time before a Category 1 attack launches the country into chaos. NCSC's CEO Ciaran Martin states that "I remain in little doubt we will be tested to the full, as a centre, and as a nation, by a major incident at some point in the years ahead, what we would call a Category 1 attack."
UK businesses under attack
The UK government’s ‘Cyber Securi
Julia Solonina
Britain should be prepared for a Category 1 cyber security emergency, according to the National Cyber Security Centre (NCSC). This means that national security, the economy, and even the nation’s lives will be at risk. However, despite this harsh warning, UK businesses still aren’t taking proactive and potentially preventative action to stop these attacks from happening. So just where are UK businesses going wrong and can they turn things around before it’s too late?
How businesses have responded
Since Brexit was announced in June 2016, 53% of UK businesses have increased their cyber security, according to latest statistics. This is as a direct result of industry data being published which revealed that malware, phishing, and ransomware attacks will become the biggest threats once Britain leaves the EU. However, despite these efforts being made, figures reveal that British businesses have the smallest cyber security budget compared to any other country. They typically spend less than £900,000, whereas the average across the world is $1.46 million.
At risk of a Category 1 cyber attack
A Category 1 cyber attack is described by the NCSC as “A cyber attack which causes sustained disruption of UK essential services or affects UK national security, leading to severe economic or social consequences or to loss of life.” To date, the UK has never witnessed such an attack. Although, one of the most severe attacks in recent times was the 2017 NHS cyber attack which was classed as a Category 2 due to there being no imminent threat to life.
The NCSC says that they typically prevent 10 cyber attacks from occurring on a daily basis. However, as the organization believes that hostility from neighbouring nations is what drives these attacks every single day, they say that it’s only a matter of time before a Category 1 attack launches the country into chaos. NCSC's CEO Ciaran Martin states that "I remain in little doubt we will be tested to the full, as a centre, and as a nation, by a major incident at some point in the years ahead, what we would call a Category 1 attack."
UK businesses under attack
The UK government’s ‘Cyber Securi |
Ransomware Threat Guideline | Wannacry | ||
| 2019-06-13 13:00:03 | May 2019\'s Most Wanted Malware: Patch Now to Avoid the BlueKeep Blues (lien direct) | In May, the most significant event in the threat landscape was not a new type of malware: it was a serious vulnerability in older versions of Windows operating systems that – if exploited by criminals – could lead to the type of mega-scale ransomware attacks we saw in 2017 with WannaCry and NotPetya. The… | Ransomware Vulnerability Threat Guideline | NotPetya Wannacry | ★★★ | |
| 2019-05-28 06:20:06 | Almost One Million Vulnerable to BlueKeep Vuln (CVE-2019-0708) (lien direct) | Microsoft announced a vulnerability in it's "Remote Desktop" product that can lead to robust, wormable exploits. I scanned the Internet to assess the danger. I find nearly 1-million devices on the public Internet that are vulnerable to the bug. That means when the worm hits, it'll likely compromise those million devices. This will likely lead to an event as damaging as WannaCry and notPetya from 2017 -- potentially worse, as hackers have since honed their skills exploiting these things for ransomware and other nastiness.To scan the Internet, I started with masscan, my Internet-scale port scanner, looking for port 3389, the one used by Remote Desktop. This takes a couple hours, and lists all the devices running Remote Desktop -- in theory.This returned 7,629,102 results (over 7-million). However, there is a lot of junk out there that'll respond on this port. Only about half are actually Remote Desktop.Masscan only finds the open ports, but is not complex enough to check for the vulnerability. Remote Desktop is a complicated protocol. A project was posted that could connect to an address and test it, to see if it was patched or vulnerable. I took that project and optimized it a bit, rdpscan, then used it to scan the results from masscan. It's a thousand times slower, but it's only scanning the results from masscan instead of the entire Internet.The table of results is as follows:1447579 UNKNOWN - receive timeout1414793 SAFE - Target appears patched1294719 UNKNOWN - connection reset by peer1235448 SAFE - CredSSP/NLA required 923671 VULNERABLE -- got appid 651545 UNKNOWN - FIN received 438480 UNKNOWN - connect timeout 105721 UNKNOWN - connect failed 9 82836 SAFE - not RDP but HTTP 24833 UNKNOWN - connection reset on connect 3098 UNKNOWN - network error 2576 UNKNOWN - connection terminatedThe various UNKNOWN things fail for various reasons. A lot of them are because the protocol isn't actually Remote Desktop and respond weirdly when we try to talk Remote Desktop. A lot of others are Windows machines, sometimes vulnerable and sometimes not, but for some reason return errors sometimes.The important results are those marked VULNERABLE. There are 923,671 vulnerable machines in this result. That means we've confirmed the vulnerability really does exist, though it's possible a small number of these are "honeypots" deliberately pretending to be vulnerable in order to monitor hacker activity on the Internet.The next result are those marked SAFE due to probably being "pached". Actually, it doesn't necessarily mean they are patched Windows boxes. They could instead be non-Windows systems that appear the same as patched Windows boxes. But either way, they are safe from this vulnerability. There are 1,414,793 of them.The next result to look at are those marked SAFE due to CredSSP/NLA failures, of which there are 1,235,448. This doesn't mean they are patched, but only that we can't exploit them. They require "network level authentication" first before we can talk Remote Desktop to them. That means we can't test whether they are patched or vulnerable -- but neither can the hackers. They may still be exploitable via an insider threat who knows a valid username/password, but they aren't exploitable by anonymous hackers or worms.The next category is marked as SAFE because they aren't Remote Desktop at all, but HTTP servers. In other words, in response to o | Ransomware Vulnerability Threat Patching Guideline | NotPetya Wannacry | ||
| 2019-05-27 19:59:38 | A lesson in journalism vs. cybersecurity (lien direct) | A recent NYTimes article blaming the NSA for a ransomware attack on Baltimore is typical bad journalism. It's an op-ed masquerading as a news article. It cites many to support the conclusion the NSA is to be blamed, but only a single quote, from the NSA director, from the opposing side. Yet many experts oppose this conclusion, such as @dave_maynor, @beauwoods, @daveaitel, @riskybusiness, @shpantzer, @todb, @hrbrmst, ... It's not as if these people are hard to find, it's that the story's authors didn't look.The main reason experts disagree is that the NSA's Eternalblue isn't actually responsible for most ransomware infections. It's almost never used to start the initial infection -- that's almost always phishing or website vulns. Once inside, it's almost never used to spread laterally -- that's almost always done with windows networking and stolen credentials. Yes, ransomware increasingly includes Eternalblue as part of their arsenal of attacks, but this doesn't mean Eternalblue is responsible for ransomware.The NYTimes story takes extraordinary effort to jump around this fact, deliberately misleading the reader to conflate one with the other. A good example is this paragraph: That link is a warning from last July about the "Emotet" ransomware and makes no mention of EternalBlue. Instead, the story is citing anonymous researchers claiming that EthernalBlue has been added to Emotet since after that DHS warning.Who are these anonymous researchers? The NYTimes article doesn't say. This is bad journalism. The principles of journalism are that you are supposed to attribute where you got such information, so that the reader can verify for themselves whether the information is true or false, or at least, credible.And in this case, it's probably false. The likely source for that claim is this article from Malwarebytes about Emotet. They have since retracted this claim, as the latest version of their article points out. That link is a warning from last July about the "Emotet" ransomware and makes no mention of EternalBlue. Instead, the story is citing anonymous researchers claiming that EthernalBlue has been added to Emotet since after that DHS warning.Who are these anonymous researchers? The NYTimes article doesn't say. This is bad journalism. The principles of journalism are that you are supposed to attribute where you got such information, so that the reader can verify for themselves whether the information is true or false, or at least, credible.And in this case, it's probably false. The likely source for that claim is this article from Malwarebytes about Emotet. They have since retracted this claim, as the latest version of their article points out. In any event, the NYTimes article claims that Emotet is now "relying" on the NSA's EternalBlue to spread. That's not the same thing as "using", not even close. Yes, lots of ransomware has been updated to also use Eternalblue to spread. However, what ransomware is relying upon is still the Wind In any event, the NYTimes article claims that Emotet is now "relying" on the NSA's EternalBlue to spread. That's not the same thing as "using", not even close. Yes, lots of ransomware has been updated to also use Eternalblue to spread. However, what ransomware is relying upon is still the Wind |
Ransomware Malware Patching Guideline | NotPetya Wannacry | ||
| 2019-04-25 10:43:01 | Smashing Security #125: Pick of the thief! (lien direct) | WannaCry’s “accidental hero” pleads guilty to malware charges, Samsung and Nokia have fingerprint fumbles, the NCSC publishes a list of 100,000 dreadful passwords, and Apple finds itself at the centre of an identity mix-up. All this and much more is discussed in the latest edition of the award-winning “Smashing Security” podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by John Hawes. | Malware Guideline | Wannacry | ||
| 2019-01-10 14:00:00 | Top 12 Blogs of 2018 (lien direct) |
 Time to look back on the top AlienVault blogs of 2018! Here we go:
A North Korean Monero Cryptocurrency Miner by Chris Doman
Crypto-currencies could provide a financial lifeline to a country hit hard by sanctions. Therefore it’s not surprising that universities in North Korea have shown a clear interest in cryptocurrencies. Recently the Pyongyang University of Science and Technology invited foreign experts to lecture on crypto-currencies. The Installer we’ve analysed above may be the most recent product of their endeavours.
VLAN Hopping and Mitigation by Pam
This type of exploit allows an attacker to bypass any layer 2 restrictions built to divide hosts. With proper switch port configuration, an attacker would have to go through a router and any other layer 3 devices to access their target. However, many networks either have poor VLAN implementation or have misconfigurations which will allow for attackers to perform said exploit. In this article, I will go through the two primary methods of VLAN hopping, known as 'switched spoofing', and 'double tagging'. I will then discuss mitigation techniques.
DNS Poisoning and How To Prevent It by Jeff Thompson
The first thing to understand about DNS 'poisoning' is that the purveyors of the Internet were very much aware of the problem. Essentially, DNS requests are "cached", or stored, into a database which can be queried in almost real-time to point names like 'hotmail.com' or 'google.com' to their appropriate IP addresses. Can you imagine having to remember a string of numbers instead of a fancy name to get to your desired WWW (or GOPHER - if that's your thing) resources? 321.652.77.133 or 266.844.11.66 or even 867.53.0.9 would be very hard to remember. [Note: I have obfuscated REAL IP addresses with very fake ones here. Always trying to stay one step ahead of the AI Armageddon. Real IP addresses end with the numerical value of '255' within each octet.]
4 SIEM Use Cases That Will Dramatically Improve Your Enterprise Security by Stephen Roe
Companies both large and small must plan to protect their data. Failing to do so puts you at risk for financial trouble, legal liability, and loss of goodwill.
Make sure to deploy SIEMs to prevent such misfortunes befalling your business. If you know how to put them to use, SIEMs provide value out of the box. Here’s a quick recap on how SIEMs can benefit you with a few clicks.
Prevent SQL injection attacks by keeping an eye on the health of your systems. This will keep you ready if and when attacks do happen.
For handling watering hole intruders, SIEMs make it easy to monitor suspicious communication hinting at an attack in progress.
If you’re worried about malware infection, commun
Time to look back on the top AlienVault blogs of 2018! Here we go:
A North Korean Monero Cryptocurrency Miner by Chris Doman
Crypto-currencies could provide a financial lifeline to a country hit hard by sanctions. Therefore it’s not surprising that universities in North Korea have shown a clear interest in cryptocurrencies. Recently the Pyongyang University of Science and Technology invited foreign experts to lecture on crypto-currencies. The Installer we’ve analysed above may be the most recent product of their endeavours.
VLAN Hopping and Mitigation by Pam
This type of exploit allows an attacker to bypass any layer 2 restrictions built to divide hosts. With proper switch port configuration, an attacker would have to go through a router and any other layer 3 devices to access their target. However, many networks either have poor VLAN implementation or have misconfigurations which will allow for attackers to perform said exploit. In this article, I will go through the two primary methods of VLAN hopping, known as 'switched spoofing', and 'double tagging'. I will then discuss mitigation techniques.
DNS Poisoning and How To Prevent It by Jeff Thompson
The first thing to understand about DNS 'poisoning' is that the purveyors of the Internet were very much aware of the problem. Essentially, DNS requests are "cached", or stored, into a database which can be queried in almost real-time to point names like 'hotmail.com' or 'google.com' to their appropriate IP addresses. Can you imagine having to remember a string of numbers instead of a fancy name to get to your desired WWW (or GOPHER - if that's your thing) resources? 321.652.77.133 or 266.844.11.66 or even 867.53.0.9 would be very hard to remember. [Note: I have obfuscated REAL IP addresses with very fake ones here. Always trying to stay one step ahead of the AI Armageddon. Real IP addresses end with the numerical value of '255' within each octet.]
4 SIEM Use Cases That Will Dramatically Improve Your Enterprise Security by Stephen Roe
Companies both large and small must plan to protect their data. Failing to do so puts you at risk for financial trouble, legal liability, and loss of goodwill.
Make sure to deploy SIEMs to prevent such misfortunes befalling your business. If you know how to put them to use, SIEMs provide value out of the box. Here’s a quick recap on how SIEMs can benefit you with a few clicks.
Prevent SQL injection attacks by keeping an eye on the health of your systems. This will keep you ready if and when attacks do happen.
For handling watering hole intruders, SIEMs make it easy to monitor suspicious communication hinting at an attack in progress.
If you’re worried about malware infection, commun |
Malware Guideline | Wannacry APT 38 | ||
| 2018-10-14 04:57:46 | How to irregular cyber warfare (lien direct) | Somebody (@thegrugq) pointed me to this article on "Lessons on Irregular Cyber Warfare", citing the masters like Sun Tzu, von Clausewitz, Mao, Che, and the usual characters. It tries to answer:...as an insurgent, which is in a weaker power position vis-a-vis a stronger nation state; how does cyber warfare plays an integral part in the irregular cyber conflicts in the twenty-first century between nation-states and violent non-state actors or insurgenciesI thought I'd write a rebuttal.None of these people provide any value. If you want to figure out cyber insurgency, then you want to focus on the technical "cyber" aspects, not "insurgency". I regularly read military articles about cyber written by those, like in the above article, which demonstrate little experience in cyber.The chief technical lesson for the cyber insurgent is the Birthday Paradox. Let's say, hypothetically, you go to a party with 23 people total. What's the chance that any two people at the party have the same birthday? The answer is 50.7%. With a party of 75 people, the chance rises to 99.9% that two will have the same birthday.The paradox is that your intuitive way of calculating the odds is wrong. You are thinking the odds are like those of somebody having the same birthday as yourself, which is in indeed roughly 23 out of 365. But we aren't talking about you vs. the remainder of the party, we are talking about any possible combination of two people. This dramatically changes how we do the math.In cryptography, this is known as the "Birthday Attack". One crypto task is to uniquely fingerprint documents. Historically, the most popular way of doing his was with an algorithm known as "MD5" which produces 128-bit fingerprints. Given a document, with an MD5 fingerprint, it's impossible to create a second document with the same fingerprint. However, with MD5, it's possible to create two documents with the same fingerprint. In other words, we can't modify only one document to get a match, but we can keep modifying two documents until their fingerprints match. Like a room, finding somebody with your birthday is hard, finding any two people with the same birthday is easier.The same principle works with insurgencies. Accomplishing one specific goal is hard, but accomplishing any goal is easy. Trying to do a narrowly defined task to disrupt the enemy is hard, but it's easy to support a group of motivated hackers and let them do any sort of disruption they can come up with.The above article suggests a means of using cyber to disrupt a carrier attack group. This is an example of something hard, a narrowly defined attack that is unlikely to actually work in the real world.Conversely, consider the attacks attributed to North Korea, like those against Sony or the Wannacry virus. These aren't the careful planning of a small state actor trying to accomplish specific goals. These are the actions of an actor that supports hacker groups, and lets them loose without a lot of oversight and direction. Wannacry in particular is an example of an undirected cyber attack. We know from our experience with network worms that its effects were impossible to predict. Somebody just stuck the newly discovered NSA EternalBlue payload into an existing virus framework and let it run to see what happens. As we worm experts know, nobody could have predicted the results of doing so, not even its creators.Another example is the DNC election hacks. The reason we can attribute them to Russia is because it wasn't their narrow goal. Instead, by looking at things like their URL shortener, we can see that they flailed around broadly all over cyberspace. The DNC was just one of thei | Hack Guideline | Wannacry | ||
| 2018-03-27 17:04:04 | Statistics Say Don\'t Pay the Ransom; but Cleanup and Recovery Remains Costly (lien direct) | Businesses have lost faith in the ability of traditional anti-virus products to detect and prevent ransomware. Fifty-three percent of U.S companies infected by ransomware in 2017 blamed legacy AV for failing to detect the ransomware. Ninety six percent of those are now confident that they can prevent future attacks, and 68% say this is because they have replaced legacy AV with next-gen endpoint protection. Thes details come from a February 2018 survey undertaken by Vanson Bourne for SentinelOne, a next-gen provider, allowing SentinelOne to claim, "This distrust in legacy AV further confirms the required shift to next-gen endpoint protection in defending against today's most prominent information security threats." This is a fair statement, but care should be taken to not automatically confuse 'legacy AV' with all traditional suppliers -- many can also now be called next-gen providers with their own flavors of AI-assisted malware detection. SentinelOne's Global Ransomware Report 2018 (PDF) questioned 500 security and risk professionals (200 in the U.S., and 100 in each of France, Germany and the UK) employed in a range of verticals and different company sizes. The result provides evidence that paying a ransom is not necessarily a solution to ransomware. Forty-five percent of U.S. companies infected with ransomware paid at least one ransom, but only 26% had their files unlocked. Furthermore, 73% of those firms that paid the ransom were targeted at least once again. Noticeably, while defending against ransomware is a security function, responding to it is a business function: 44% of companies that paid up did so without the involvement or sanction of the IT/security teams. The attackers appear to have concluded that U.S. firms are the more likely to pay a ransom, and more likely to pay a higher ransom. While the global average ransom is $49,060, the average paid by U.S. companies was $57,088. "If the cost of paying the ransomware is less than the lost productivity caused by downtime from the attack, they tend to pay," SentinelOne's director of product management, Migo Kedem, told SecurityWeek. "This is not good news, as it means the economics behind ransomware campaigns still make sense, so attacks will continue." This is in stark contrast to the UK, where the average payment is almost $20,000 lower at $38,500. It is tempting to wonder if this is because UK companies just don't pay ransoms. In 2016, 17% of infected UK firms paid up; now it is just 3%. This may reflect the slightly different approaches in law enforcement advice. While LEAs always say it is best not to pay, the UK's NCSC says flatly, 'do not pay', while the FBI admits that it is ultimately the decision of each company. Paying or not paying, is, however, only a small part of the cost equation; and the UK's Office for National Statistics (ONS) provides useful figures. According the SentinelOne, these figures show that in a 12-month period, the average cost of a ransomware infection to a UK business was £329,976 ($466,727). With 40% of businesses with more than 1000 employees being infected, and 2,625 such organizations in the UK, the total cost of ransomware to UK business in 12 months was £346.4 m | Guideline | Wannacry | ||
| 2018-03-27 13:00:00 | Tales from the SOC: The Simulated Attack (lien direct) |
Introduction
In today’s world, understanding threats and how to avoid them are critical to a business’s success. Last year, we saw an evolution in malware and attacks. Ransomwares like WannaCry made their debut; featuring worm-like attributes that allowed ransomware to self-propagate through a network, exploiting vulnerable machines and continuing the damage. We started to see attackers using more advanced automation in their malware and shiftier distribution methods to thwart defenses. In September 2017, we saw a supply chain attack against download servers that added a Trojan virus within versions of the popular CCleaner PC utility software. The download was undetected for almost a month and it is estimated that over 2 million users had installed it.
According to the US government, cyberattacks reportedly cost the US economy a $57-109 billion-dollar loss in 2016. Cisco reported in 2017 that 53% of cyberattacks resulted in damages of over $500k or more; 8% had damage totals over $5 million per incident. While costs are skyrocketing, so is the average timeframe for detecting cyberattacks. Multiple studies over the last several years have found businesses are averaging a three to eight-month time period before even detecting a cyber-attack.
We know the threat is real and the costs of a cyberattack can be exorbitant, so what can we do with all this information? As an MSSP, something we always recommend to our clients and prospects is practicing a multi-layer defense approach within their network. Multiple layers of security are an important part of detecting, preventing, and minimizing a business’s exposure to a cyberattack. So many times, we have heard “I have good anti-virus and an expensive firewall; I don’t need any other defenses.” Unfortunately, that is no longer the case. Preventive security is no longer enough; organizations must build a strong defense and use offensive practices to proactively head off potential intrusions.
In today’s blog, we share with you a real-life experience and what we did to mitigate the threat by building a strong cybersecurity strategy.
Tale from Our SOC
 Several years ago, we helped a client implement managed security services. The client’s priorities were never focused on security, until they had hired a consulting company to perform a simulated cyberattack. The exercise shed light on their security shortcomings. It highlighted how the current controls they had in place failed during the simulated attack and what methods were missing from their environment, including: incident response, security awareness and systems capable of detecting these acts.
The Simulated Attack
When the simulated attack was started, they only used the organization’s name. The first step was reconnaissance about this organization, where common tools like Google and LinkedIn were used to search for user email formats, website, and domain information. As the discovery phase progressed, IPs for VPN server access and email servers were identified. Based off the information they discovered, user lists were built, and a phishing campaign was prepared. The attacker ran vulnerability scans and methodical brute force tests to identify any weaknesses within the external services they had already identified.
Several years ago, we helped a client implement managed security services. The client’s priorities were never focused on security, until they had hired a consulting company to perform a simulated cyberattack. The exercise shed light on their security shortcomings. It highlighted how the current controls they had in place failed during the simulated attack and what methods were missing from their environment, including: incident response, security awareness and systems capable of detecting these acts.
The Simulated Attack
When the simulated attack was started, they only used the organization’s name. The first step was reconnaissance about this organization, where common tools like Google and LinkedIn were used to search for user email formats, website, and domain information. As the discovery phase progressed, IPs for VPN server access and email servers were identified. Based off the information they discovered, user lists were built, and a phishing campaign was prepared. The attacker ran vulnerability scans and methodical brute force tests to identify any weaknesses within the external services they had already identified.
 The next step in the simulated attack was the phishing campaign. Now that the attacker had built a list of potential emails, they The next step in the simulated attack was the phishing campaign. Now that the attacker had built a list of potential emails, they |
Guideline | CCleaner Wannacry | ||
| 2018-03-26 13:19:01 | (Déjà vu) Energy Sector Most Impacted by ICS Flaws, Attacks: Study (lien direct) | The energy sector was targeted by cyberattacks more than any other industry, and many of the vulnerabilities disclosed last year impacted products used in this sector, according to a report published on Monday by Kaspersky Lab. The security firm has analyzed a total of 322 flaws disclosed in 2017 by ICS-CERT, vendors and its own researchers, including issues related to industrial control systems (ICS) and general-purpose software and protocols used by industrial organizations. Of the total number of security holes, 178 impact control systems used in the energy sector. Critical manufacturing organizations – this includes manufacturers of primary metals, machinery, electrical equipment, and transportation equipment – were affected by 164 of these vulnerabilities. Other industries hit by a significant number of vulnerabilities are water and wastewater (97), transportation (74), commercial facilities (65), and food and agriculture (61). Many of the vulnerabilities disclosed last year impacted SCADA or HMI components (88), industrial networking devices (66), PLCs (52), and engineering software (52). However, vulnerabilities in general purpose software and protocols have also had an impact on industrial organizations, including the WPA flaws known as KRACK and bugs affecting Intel technology. Learn More at SecurityWeek's ICS Cyber Security Conference As for the types of vulnerabilities, nearly a quarter are web-related and 21 percent are authentication issues. A majority of the flaws have been assigned severity ratings of medium or high, but 60 weaknesses are considered critical based on their CVSS score. Kaspersky pointed out that all vulnerabilities with a CVSS score of 10 are related to authentication and they are all easy to exploit remotely. Kaspersky said 265 of the vulnerabilities can be exploited remotely without authentication and without any special knowledge or skills. It also noted that exploits are publicly available for 17 of the security holes. The company has also shared data on malware infections and other security incidents. In the second half of 2017, Kaspersky security products installed on industrial automation systems detected nearly 18,000 malware variants from roughly 2,400 families. Malware attacks were blocked on almost 38 percent of ICS computers protected by the company, which was slightly less than in the second half of the previous year. Again, the energy sector was the most impacted. According to the security firm, roughly 40 percent of the devices housed by energy organizations were targeted. | Guideline | Wannacry | ★★★★★ | |
| 2018-03-19 12:24:04 | Preventing Business Email Compromise Requires a Human Touch (lien direct) | Human-powered Intelligence Plays a Critical Role in Defending Against Socially Engineered Attacks The FBI's Internet Crime Complaint Center (IC3) declared Business Email Compromise (BEC) the “3.1 billion dollar scam” in 2016, an amount which then grew in the span of one year into a “5 billion dollar scam.” Trend Micro now projects those losses in excess of 9 billion dollars. It's an understatement to say BEC scams and the resulting damages are on the rise. But with cybersecurity spending across all sectors at an all-time high, how is such an unsophisticated threat still costing otherwise well-secured organizations billions of dollars? Unlike the numerous types of attacks that incorporate malware, most BEC scams rely solely on social engineering. In fact, its use of trickery, deception, and psychological manipulation rather than malware is largely why BEC continually inflicts such substantial damages. Since most network defense solutions are designed to detect emails containing malware and malicious links, BEC emails often land directly in users' inboxes. And when this happens, the fate of an attempted BEC scam is in the hands of its recipient. Indeed, BEC underscores why even the most technically sophisticated cyber defenses aren't always a match for low-tech threats. Combating BEC requires more than just advanced technologies and robust perimeter security-it requires humans to understand the threat. Here's why: Human-Powered Intelligence Trumps Automation Since socially engineered attacks such as BEC are designed to exploit human instincts and emotions, human-powered intelligence naturally plays a critical role in defending against these attacks. I've written previously about the limitations of so-called automated intelligence and why human expertise and analysis are irreplaceable. BEC epitomizes this notion. After all, intelligence offerings that rely solely on automation tend to comprise little more than technical indicators of compromise (IoCs). BEC campaigns can have IoCs-but they tend to be less technical and more nuanced, often pertaining to an attacker's syntax, dialect, or other behavioral characteristics. While an IoC for a phishing campaign, for example, might be an email address, an IoC for a BEC campaign could be the phrase an attacker uses to open or sign off the email. Automated intelligence offerings and traditional network security solutions are generally not desig | Guideline | Wannacry | ||
| 2018-03-12 13:00:00 | Countering Crypto-Malware: A Guide to Preventing a Ransomware Infection (lien direct) |
Ransomware had what Malwarebytes describes as a "banner year" in 2017. In the 2017 State of Malware report, telemetry gathered by the anti-malware provider reveals that business and consumer ransomware detections swelled by 90 percent and 93 percent, respectively. The monthly rate of ransomware attacks against businesses grew by approximately 10 times the rate of 2016 over the same period in 2017. A 700 percent increase in ransomware helped drive that surge, with GlobeImposter and WannaCry leading the way.
 Malwarebytes 2017 State of Malware report page 6
Overall, Malwarebytes saw new ransomware development stagnate in the second half of 2017 as digital criminals shifted their focus to bring back old threats like banking Trojans and embrace new techniques, most notably malicious cryptocurrency miners. Those trends notwithstanding, ransomware isn't going away anytime soon. Users should therefore follow these five simple steps that can help them stay safe from a ransomware attack.
Install an Anti-Malware Solution
While some digital attackers are turning to fileless malware, many ransomware strains still come with a digital signature. Anti-malware solutions can use these imprints to detect and block a crypto-malware threat before it has time to execute on a computer. Victims of ransomware can also use these tools to clean their computers of ransomware before they restore their data using a free decryption tool or available backup.
Update Your Systems Regularly
A common delivery vector for ransomware is an exploit kit. It's a type of software package that scans for known vulnerabilities in Adobe Flash Player and other programs. If it finds a match with its hardcoded exploits, the kit launches code that exploits the vulnerability and in turn downloads ransomware onto the vulnerable machine. By staying current with software patches, however, users can block exploit kits from activating on their computers.
Malwarebytes 2017 State of Malware report page 6
Overall, Malwarebytes saw new ransomware development stagnate in the second half of 2017 as digital criminals shifted their focus to bring back old threats like banking Trojans and embrace new techniques, most notably malicious cryptocurrency miners. Those trends notwithstanding, ransomware isn't going away anytime soon. Users should therefore follow these five simple steps that can help them stay safe from a ransomware attack.
Install an Anti-Malware Solution
While some digital attackers are turning to fileless malware, many ransomware strains still come with a digital signature. Anti-malware solutions can use these imprints to detect and block a crypto-malware threat before it has time to execute on a computer. Victims of ransomware can also use these tools to clean their computers of ransomware before they restore their data using a free decryption tool or available backup.
Update Your Systems Regularly
A common delivery vector for ransomware is an exploit kit. It's a type of software package that scans for known vulnerabilities in Adobe Flash Player and other programs. If it finds a match with its hardcoded exploits, the kit launches code that exploits the vulnerability and in turn downloads ransomware onto the vulnerable machine. By staying current with software patches, however, users can block exploit kits from activating on their computers.
 How Exploit Kits Work. (Source: Barkly)
Avoid Suspicious Links and Email Attachments
As seen in the graphic above, one of the most common beginnings of an exploit kit campaign involves a phishing email recipient clicking on a malicious link that redirects them to a compromised website. Users aren't powerless against these tactics. They can make a point of not clicking suspicious links and email attachments, including those that come with messages sent to them from unfamiliar senders.
Disable Macros for Office Documents
Microsoft Office documents come with what's called macros. They are essentially rules that users can craft in order to save time by automating repetitive tasks. Unfortunately, digital attackers often hide ransomware executables within Office macros and attempt to capitalize on users' curiosity by tempting them with an unknown attachment. Users can protect themselves against this trick by disabling macros in Office, by steering clear of unsolicited attachments, and by making it a rule to not enable macros in any document should they receive a prompt to do so.
Install a Pop-Up Blocker
Bad actors don't just rely on ema
How Exploit Kits Work. (Source: Barkly)
Avoid Suspicious Links and Email Attachments
As seen in the graphic above, one of the most common beginnings of an exploit kit campaign involves a phishing email recipient clicking on a malicious link that redirects them to a compromised website. Users aren't powerless against these tactics. They can make a point of not clicking suspicious links and email attachments, including those that come with messages sent to them from unfamiliar senders.
Disable Macros for Office Documents
Microsoft Office documents come with what's called macros. They are essentially rules that users can craft in order to save time by automating repetitive tasks. Unfortunately, digital attackers often hide ransomware executables within Office macros and attempt to capitalize on users' curiosity by tempting them with an unknown attachment. Users can protect themselves against this trick by disabling macros in Office, by steering clear of unsolicited attachments, and by making it a rule to not enable macros in any document should they receive a prompt to do so.
Install a Pop-Up Blocker
Bad actors don't just rely on ema |
Guideline | Wannacry | ||
| 2017-08-17 08:42:28 | Smashing Security #038: Gents! Stop airdropping your pics! (lien direct) |  WannaCry hero Marcus Hutchins (aka MalwareTech) pleads not guilty to malware charges, the Scottish parliament is hit by a brute force attack, IoT smart locks aren't so smart, and.. ahem.. someone is sending intimate pics via AirDrop to unsuspecting commuters.
All this and more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by technology journalist Geoff White. WannaCry hero Marcus Hutchins (aka MalwareTech) pleads not guilty to malware charges, the Scottish parliament is hit by a brute force attack, IoT smart locks aren't so smart, and.. ahem.. someone is sending intimate pics via AirDrop to unsuspecting commuters.
All this and more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by technology journalist Geoff White.
|
Guideline | Wannacry | ||
| 2017-08-15 04:06:33 | WannaCry hero Marcus Hutchins under house arrest (lien direct) | Briton, 23, pleads not guilty to charges of writing and distributing malware | Guideline | Wannacry | ||
| 2017-08-07 20:45:14 | Marcus Hutchins\' Only Certainty is Uncertainty (lien direct) | WannaCry hero Marcus Hutchins pleaded not guilty last week could be freed today on $30,000 bond before the case moves to Wisconsin. | Guideline | Wannacry | ||
| 2017-08-05 03:03:32 | Marcus Hutchins (MalwareTech) Gets $30,000 Bail, But Can\'t Leave United States (lien direct) | Marcus Hutchins, the malware analyst who helped stop global Wannacry menace, has reportedly pleaded not guilty to charges of creating and distributing the infamous Kronos banking malware and is set to release on $30,000 bail on Monday.
Hutchins, the 23-year-old who operates under the alias MalwareTech on Twitter, stormed to fame and hailed as a hero over two months ago when he stopped a
|
Guideline | Wannacry | ||
| 2017-07-21 20:03:00 | Worried about ransomware? Here are 3 things IT leaders need to know before the next big outbreak (lien direct) | It's only a matter of time before another WannaCry-style ransomware outbreak, but you don't have to be a victim. Here's what IT leaders need to know in order to safeguard themselves and their users. | Guideline | Wannacry | ★★ | |
| 2017-07-19 09:25:52 | WannaCry Fallout: 80% of Brits more worried about how organisations store their data following latest attacks (lien direct) | New research by leading information security company Clearswift shows how attitudes to cyber security have changed in the boardroom and among staff in the wake of the recent WannaCry attack, surveying 600 business decision makers and 1,200 employees across the UK, US, Germany and Australia. Within a day the WannaCry attack, which affected major ... | Guideline | Wannacry | ||
| 2017-07-03 10:22:16 | BCS Launches Bid to Prevent Another NHS WannaCry Epidemic (lien direct) | BCS, The Chartered Institute for IT, is leading a new effort to improve cybersecurity within the NHS in a bid to head off another WannaCry-style incident. View Full Story ORIGINAL SOURCE: Info Security Magazine | Guideline | Wannacry | ||
| 2017-06-30 13:00:00 | Week in Review 30th June 2017 (lien direct) | New Petya Variant Unless you’ve been away for the week on a deserted location with no access to the internet, radio, or television, you’ve likely been bombarded with news of the Petya ransomware variant that took offline most of the Ukraine as well as spreading around to other countries. It echoes the disastrous impact WannaCry had just a few short weeks ago. Our own AlienVault labs team broke down what they saw Microsoft has a nice technical post on how the attack works Lesley Carhart has written a very accessible post explaining the attack and the surrounding issues. Perhaps the biggest victim this time round was Cadbury’s, as it had to shut down its famous chocolate factory in Hobart. How I obtained direct publish access to 13% of npm packages This is a great post on how ChALkeR was able to obtain direct publish access to 13% of npm packages – with an estimated reach of up to 52% once you factor in dependency chains. It’s interesting because it’s relatively straightforward using three basic techniques of bruteforcing, reusing passwords from leaks, and npm credentials on GitHub. The issue has been addressed in an npm blog post. Just in case you need to check your credentials You are not Google Neither are you Amazon, or LinkedIn, or Facebook, or Netflix etc. A great post especially for engineers. This line of thinking can be expanded into security too. Just because a large, well-funded, and highly targeted company is using the latest bleeding edge next generation security products and tools, it doesn’t mean every company needs to adopt the same toolset. Rather, it’s about looking at what matters most, and getting security controls that are appropriate. I really need to find better ways of explaining my thoughts, the paragraph I just wrote throws me back to days of being a consultant. Legal boundaries and privacy The long-running case between the US Department of Justice and Microsoft has taken another turn as the DoJ has petitioned the US supreme court to get involved in allowing the US government access to Microsoft emails stored at its Dublin data centre. As Microsoft president and chief counsel Brad Smith argued in a blog post, if the US government has the right to directly seize internationally-held data, then other countries will of course expect the same right. This in effect would allow international digital raids for American or other nations’ data, in the US or around the worl | Guideline | NotPetya Wannacry | ||
| 2017-06-26 09:52:06 | UK electricity grid cyber-attack risk is \'off the scale\' (lien direct) | Concerns over the threat posed by cyber-attacks on power stations and electricity grids is “off the scale†in the UK energy sector, according to a leading industry figure. No other country in the world has an energy industry as worried about the risk from cyber threats, such as the WannaCry ransomware attack that recently hit ... | Guideline | Wannacry | ★★★★ | |
| 2017-06-09 13:00:00 | Capture The Flag (CTF): What Is It for a Newbie? (lien direct) |
Introduction
This blog is designed for a person that is brand-new to Capture The Flag (CTF) and explains the basics to give you the courage to enter a CTF and see for yourself what’s it’s like to participate. CTFs are events that are usually hosted at information security conferences, including the various BSides events. These events consist of a series of challenges that vary in their degree of difficulty, and that require participants to exercise different skillsets to solve. Once an individual challenge is solved, a “flag” is given to the player and they submit this flag to the CTF server to earn points. Players can be lone wolves who attempt the various challenges by themselves, or they can work with others to attempt to score the highest number of points as a team.
CTF events are usually timed, and the points are totaled once the time has expired. The winning player / team will be the one that solved the most challenges and thus secured the highest score.
Here is a screen shot of a score board from a recent BSides San Francisco CTF event:
 Please note the sentence that I’ve marked with a red box. As you will quickly see, CTF tasks are often based on real world incidents/vulnerabilities that give you a chance to experience how it’s actually done and better prepare you to defend your own systems from these types of attacks. So not only are CTF events fun, they can also be educational and professionally rewarding.
CTF Preparedness
If you’ve never experienced a CTF event before, don’t get frustrated or give up, because the key to any type of hacking is patience. While this is sometimes a difficult thing to have, the only way to learn is to persist and practice on your own (see this post further down on how to practice) and maybe next time you’ll score first place! One thing you can try to do during your first CTF event, if possible, is find a experienced team that’s willing to let you join them. Make sure you’re clear that this is your first CTF event and you’d really love for them to show you the ropes.
In my experience, members of the InfoSec community are usually very willing to share their knowledge with anyone interested in trying to learn and grow in this field. At the same time, however, one common theme you also often hear in the community is that there is a shortage of talent. At times this can be a very real struggle, and many professionals who have worked their way up in the field have spent considerable time to do so, sacrificing much to learn, practice and hone their craft. For this reason, before reaching out for help with basic questions, you should first research the topic and make an effort to figure things out on your own.
Within the InfoSec community, trust isn’t something you can place value on. If your job is to hack into a client’s network, they last thing anyone wants is for that sensitive information to be shared with anyone outside of the team. Trust is a critical component of this relationship and I cannot express enough how important it is to remain ethical during competitions as well. Finally, last but certainly not least: when you go to a CTF event, don’t forget to bring a laptop or another computer that has an operating system with various tools already installed (more on this below) as without that you’re going to be off to a rough start.
In summary, CTF are a great opportunity to learn, so if you’ve never experienced a CTF event or even a BSides event, I strongly encourage you to jump in and join one as soon as you can!
Types of Events
There are usually two different types of CTF events. The two most common types are:
Red Team/Blue Team
In this style of event the red team atte
Please note the sentence that I’ve marked with a red box. As you will quickly see, CTF tasks are often based on real world incidents/vulnerabilities that give you a chance to experience how it’s actually done and better prepare you to defend your own systems from these types of attacks. So not only are CTF events fun, they can also be educational and professionally rewarding.
CTF Preparedness
If you’ve never experienced a CTF event before, don’t get frustrated or give up, because the key to any type of hacking is patience. While this is sometimes a difficult thing to have, the only way to learn is to persist and practice on your own (see this post further down on how to practice) and maybe next time you’ll score first place! One thing you can try to do during your first CTF event, if possible, is find a experienced team that’s willing to let you join them. Make sure you’re clear that this is your first CTF event and you’d really love for them to show you the ropes.
In my experience, members of the InfoSec community are usually very willing to share their knowledge with anyone interested in trying to learn and grow in this field. At the same time, however, one common theme you also often hear in the community is that there is a shortage of talent. At times this can be a very real struggle, and many professionals who have worked their way up in the field have spent considerable time to do so, sacrificing much to learn, practice and hone their craft. For this reason, before reaching out for help with basic questions, you should first research the topic and make an effort to figure things out on your own.
Within the InfoSec community, trust isn’t something you can place value on. If your job is to hack into a client’s network, they last thing anyone wants is for that sensitive information to be shared with anyone outside of the team. Trust is a critical component of this relationship and I cannot express enough how important it is to remain ethical during competitions as well. Finally, last but certainly not least: when you go to a CTF event, don’t forget to bring a laptop or another computer that has an operating system with various tools already installed (more on this below) as without that you’re going to be off to a rough start.
In summary, CTF are a great opportunity to learn, so if you’ve never experienced a CTF event or even a BSides event, I strongly encourage you to jump in and join one as soon as you can!
Types of Events
There are usually two different types of CTF events. The two most common types are:
Red Team/Blue Team
In this style of event the red team atte |
Guideline | Wannacry | ||
| 2017-06-07 05:45:14 | Infosec17: WannaCry could be demise of ransomware (lien direct) | WannaCry could lead to the decline and even demise of ransomware due to its poor implementation and its role in underlining the importance of defending against this threat, says a security expert | Guideline | Wannacry | ||
| 2017-06-05 16:15:45 | Some non-lessons from WannaCry (lien direct) | This piece by Bruce Schneier needs debunking. I thought I'd list the things wrong with it.The NSA 0day debateSchneier's description of the problem is deceptive:When the US government discovers a vulnerability in a piece of software, however, it decides between two competing equities. It can keep it secret and use it offensively, to gather foreign intelligence, help execute search warrants, or deliver malware. Or it can alert the software vendor and see that the vulnerability is patched, protecting the country -- and, for that matter, the world -- from similar attacks by foreign governments and cybercriminals. It's an either-or choice.The government doesn't "discover" vulnerabilities accidentally. Instead, when the NSA has a need for something specific, it acquires the 0day, either through internal research or (more often) buying from independent researchers.The value of something is what you are willing to pay for it. If the NSA comes across a vulnerability accidentally, then the value to them is nearly zero. Obviously such vulns should be disclosed and fixed. Conversely, if the NSA is willing to pay $1 million to acquire a specific vuln for imminent use against a target, the offensive value is much greater than the fix value.What Schneier is doing is deliberately confusing the two, combing the policy for accidentally found vulns with deliberately acquired vulns.The above paragraph should read instead:When the government discovers a vulnerability accidentally, it then decides to alert the software vendor to get it patched. When the government decides it needs as vuln for a specific offensive use, it acquires one that meets its needs, uses it, and keeps it secret. After spending so much money acquiring an offensive vuln, it would obviously be stupid to change this decision and not use it offensively.Hoarding vulnsSchneier also says the NSA is "hoarding" vulns. The word has a couple inaccurate connotations.One connotation is that the NSA is putting them on a heap inside a vault, not using them. The opposite is true: the NSA only acquires vulns it for which it has an active need. It uses pretty much all the vulns it acquires. That can be seen in the ShadowBroker dump, all the vulns listed are extremely useful to attackers, especially ETERNALBLUE. Efficiency is important to the NSA. Your efficiency is your basis for promotion. There are other people who make their careers finding waste in the NSA. If you are hoarding vulns and not using them, you'll quickly get ejected from the NSA.Another connotation is that the NSA is somehow keeping the vulns away from vendors. That's like saying I'm hoarding naked selfies of myself. Yes, technically I'm keeping them away from you, but it's not like they ever belong to you in the first place. The same is true the NSA. Had it never acquired the ETERNALBLUE 0day, it never would've been researched, never found.The VEPSchneier describes the "Vulnerability Equities Process" or "VEP", a process that is supposed to manage the vulnerabilities the government gets.There's no evidence the VEP process has ever been used, at least not with 0days acquired by the NSA. The VEP allows exceptions for important vulns, and all the NSA vulns are important, so all are excepted from the process. Since the NSA is in charge of the VEP, of course, this is at the sole discretion of the NSA. Thus, the entire point of the VEP process goes away.Moreover, it can't work in many cases. The vulns acquired by the NSA often come with clauses that mean they can't be shared.New classes of vulnsOne reason sellers forbid 0days from being shared is because they use new classes of vulnerabilities, such that sha | Guideline | Wannacry | ||
| 2017-05-23 14:59:46 | What did we Learn from WannaCry? - Oh Wait, We Already Knew That!, (Tue, May 23rd) (lien direct) | In the aftermath of last weeks excitement over the WannaCry malware, Ive had a lot of lessons learned meetings with clients. The results are exactly what youd expect, but in some cases came as a surprise to the organizations we met with. There was a whole outcry about not victim shaming during and after this outbreak, and I get that, but in most cases infections were process failures that the IT group didnt know they had, these lessons learned sessions have contributed to improving the situation at many organizations. The short list is below - affected companies had one or more of the issues below: 1/ Patch Plain and simple, when vendor patches come out, apply them. In a lot of cases, Patch Tuesday means Reboot Wednesday for a lot of organizations, or worst case Reboot Saturday. If you dont have a test the patches process, then in a lot of cases simply waiting a day or two (to let all the early birds test them for you) will do the job. If you do have a test process, in todays world it truly needs to take 7 days or less. There are some hosts that you wont be patching. The million dollar MRI machine, the IV pump or the 20 ton punch press in the factory for instance. But you know about those, and youve segmented them away (in an appropriate way) from the internet and your production assets. This outbreak wasnt about those assets, what got hammered by Wannacry was the actual workstations and servers, the hospital stations in admitting and emergency room, the tablet that the nurse enters your stats into and so on. Normal user workstations that either werent patched, or were still running Windows XP. That being said, there are always some hosts that can be patched, but cant be patched regularly. The host thats running active military operations for instance, or the host thats running the callcenter for flood/rescue operations, e-health or suicide hotline. But you cant give just up on those - in most cases there is redundancy in place so that you can update half of those clusters at a time. If there isnt, you do still need to somehow get them updated on a regular schedule. Lesson learned? If your patch cycle is longer than a week, in todays world you need to revisit your process and somehow shorten it up. Document your exceptions, put something in to mitigate that risk (network segmentation is a common one), and get Sr Management to sign off on the risk and the mitigation. 2/ Unknown Assets are waiting to Ambush You A factor in this last attack were hosts that werent in ITs inventory. In my group of clients, what this meant was hosts controlling billboards or TVs running ads in customer service areas (the menu board at the coffee shop, the screen telling you about retirement funds where you wait in line at the bank and so on). If this had been a linux worm, wed be talking about projectors, TVs and access points today. One and all, I pointed those folks back to the Critical Controls list (https://www.cisecurity.org/controls/ ). In plain english, the first item is know whats on your network and the second item is know what is running on whats on your network. If you dont have a complete picture of these two, you will always be exposed to whatever new malware (or old malware) that tests the locks at your organization. 3/ Watch the News. .... And I dont mean the news on TV. Your vendors (in this case Microsoft) have news feeds, and there are a ton of security-related news sites, podcasts and feeds (this site is one of those, our StormCast podcast is another). Folks that watch the news knew about this issue starting back in 2015, when Microsoft started advising us to disable SMB1, then again last year (2016) when Microsoft posted their Were Pleading with you, PLEASE disable SMB1 post. We knew specifically about the vulnerabilities used by Wannacry in January when the Shadowbrokers dump happened, we knew again when the patches were released in March, and we knew (again, much mor | Guideline | Wannacry | ||
| 2017-05-23 09:43:21 | WannaCry? Not really. A report from the 11th Eskenzi PR IT Analyst and CISO Forum (lien direct) | May 16th and 17th 2017 saw Eskenzi PR stage its 11th 2-day IT Security Analyst Forum, as usual, in London. The morning of the second day (which was a Wednesday) was the customary CISO (chief information security officer) roundtable. A coming together of 20 or so IT security leaders from blue chip UK enterprises and ... | Guideline | Wannacry | ||
| 2017-05-22 13:00:54 | Jaya Baloo on WannaCry and Defending Against Advanced Attacks (lien direct) | Jaya Baloo, CISO of KPN, the Netherlands' leading telecommunications provider, talks to Mike Mimoso about the WannaCry ransomware outbreak and how large network providers and enterprises must contend with advanced attacks. | Guideline | Wannacry | ||
| 2017-05-17 16:05:51 | WannaCry : Etat des lieux à J+5 – Commentaire Avast (lien direct) |  Cinq jours après la cyberattaque qui a déjà touché 150 pays dans le monde et fait plus de 250Â 000 victimes, Jakub Kroustek, Threat Lab Team Lead, chez Avast, revient sur les données observées au fil des heures et les questions concrètes qui s'y rapportent. Communiqué de presse – Le vendredi après-midi, plus de 50 000 […] Cinq jours après la cyberattaque qui a déjà touché 150 pays dans le monde et fait plus de 250Â 000 victimes, Jakub Kroustek, Threat Lab Team Lead, chez Avast, revient sur les données observées au fil des heures et les questions concrètes qui s'y rapportent. Communiqué de presse – Le vendredi après-midi, plus de 50 000 […] |
Guideline | Wannacry | ||
| 2017-05-17 03:33:55 | WanaCrypt0r Ransomworm (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDSince the release of the ETERNALBLUE exploit by 'The Shadow Brokers' last month security researchers have been watching for a mass attack on global networks. This came on Friday 12th May when it was bundled with ransomware called WanaCrypt0r and let loose. Initial reports of attacks were highlighted by Telefonica in Spain but the malware quickly spread to networks in the UK where the National Health Service (NHS) was impacted, followed by many other networks across the world.The infographic below illustrates the key components of the WanaCrypt0r ransomware. This is described in further detail in subsequent sections of this report along with initial clues on attribution.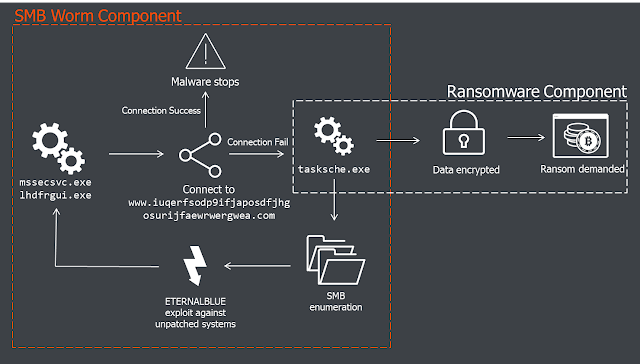 ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs |
Guideline Medical | Wannacry APT 38 | ||
| 2017-05-16 13:00:00 | Innovation for the Sake of Innovation (lien direct) |
“Perfection is finally attained not when there is no longer anything to add, but when there is no longer anything to take away.” - Antoine de Exupery
In today’s world, it feels as if innovation has become the curse of many companies. It forces changes, and wheels being reinvented when not needed, out of fear that lack of innovation will be perceived as stagnation.
In addition, innovation for the sake of innovation can lead to security issues. These issues manifest predominantly in one of two ways:
Scope Creep The first is one of scope creep and the introduction of vulnerabilities through hurried and unplanned changes. For example, adding a new set of fields onto a web application at the last minute often results in an over-worked developer hastily cobbling together code to incorporate functionality. This can lead to inadequate testing and vulnerabilities being introduced.
But not all scope creep is rapid. Sometimes functionality is added slowly over time. What starts off life as a simple workflow ends up being a Frankenstein-esque corporate accounting, inventory, and pricing platform running the entire company.
The fundamental problem is that there is little linking of ideas from a brainstorm with reality. Often times things that are 'nice to have' are just that, only nice to have. There’s no need to invest in a shiny box that will add artificial intelligence to your security team, if you don't already have the basics mapped out.
Because we can The second issue which comes about from ‘innovation for the sake of innovation’ is the introduction of features not out of need, but rather because they are available.
The ever-increasing number of smart-devices are a good example of these. Just because it is possible to connect wirelessly to a kettle, a toaster, or a pillow, it doesn’t necessarily mean that it is a good idea.
In security teams, we often see this manifest in many ways. For example, keeping each and every log generated by every device is a good idea for investigations or to rebuild timelines. But is it really necessary for everything? Why not scope out and only store full logs for critical systems and strip away the noise.
Or why build a fraud detection system when the threat of fraud against your business is low.
 The user experience Anytime there are new features or functionality added, user experience takes a hit. Even ‘good’ updates require users to learn new menu commands, alter their workflow, or simply having to retrain muscle memory to click on a different part of the screen.
But more so, it can disrupt the natural use of a product or technology. For example, an email client should be an email client. When it morphs into an all-singing-all-dancing CRM with context-aware reminders, and bluetooth enabled functionality, one wonders whether the product is actually an email client at all.
Security is not immune to these problems. Whether these be in-house scripts that evolve into a homegrown SOC, or enabling of additional capabilities - it adds unnecessary complexity and confusion.
The impact of such security changes is amplified when they impact the end user. Password reset policies, multi-factor authentication, phishing exercises, etc. all add to the mental workload of the users.
Technology, and by extension security, shouldn’t need to go through innovation for the sake of innovation. While arguments can be made for the progress such innovation brings, the risks often-times outweigh the pros.
Instead, I propose technology be put on an ‘Atkins diet’ of decluttering. While there are many intricacies to decluttering, they can be broken down into two broad steps:
The user experience Anytime there are new features or functionality added, user experience takes a hit. Even ‘good’ updates require users to learn new menu commands, alter their workflow, or simply having to retrain muscle memory to click on a different part of the screen.
But more so, it can disrupt the natural use of a product or technology. For example, an email client should be an email client. When it morphs into an all-singing-all-dancing CRM with context-aware reminders, and bluetooth enabled functionality, one wonders whether the product is actually an email client at all.
Security is not immune to these problems. Whether these be in-house scripts that evolve into a homegrown SOC, or enabling of additional capabilities - it adds unnecessary complexity and confusion.
The impact of such security changes is amplified when they impact the end user. Password reset policies, multi-factor authentication, phishing exercises, etc. all add to the mental workload of the users.
Technology, and by extension security, shouldn’t need to go through innovation for the sake of innovation. While arguments can be made for the progress such innovation brings, the risks often-times outweigh the pros.
Instead, I propose technology be put on an ‘Atkins diet’ of decluttering. While there are many intricacies to decluttering, they can be broken down into two broad steps:
 Simplify When looking at your
Simplify When looking at your |
Guideline | Wannacry | ||
| 2017-05-16 07:21:56 | WannaCry? Do your own data analysis., (Tue, May 16th) (lien direct) | In God we trust. All others must bring data. ~Bob Rudis With endless amounts of data, technical detail, and insights on WannaCrypt/WannaCry, and even more FUD, speculation, and even downright trolling, herein is a proposal for you to do your own data-driven security analysis. My favorite book to help you scratch that itch? Data Driven Security: Analysis, Visualization and Dashboards, by Jay Jacobs Bob Rudis. A few quick samples, using WannaCry data and R, the open source programming language and software environment for statistical computing and graphics. If ever you wanted to pick up a bit of immediately useful programming, R is for you. Our good friends over at Team Cymru tweeted out a great GitHubGist WannaCry factsheet, therein are a number of useful resources, many leading to other good reads. I easily tracked down a list of malicious IPs associated with WannaCry. width:686px" /> You can always learn interesting insights from IPs and this situation is no different. In very few lines of R, we can identify and visualize the data for further insight. Ill walk you through it. First, lets pull in the libraries we need to do some IP geolocation, create a word cloud, and make said word cloud more color rich, and make a nice plot. library(rgeolocate) library(wordcloud) library(RColorBrewer) library(plotrix) We need to then read in Maxmind data (GeoLite2-Country) and call Oliver Key and @hrbrmstrs rgeolocate package file - system.file(extdata,GeoLite2-Country.mmdb, package = rgeolocate) Follow that with our malicious WannaCry IP addresses. ips - c(188.166.23.127,91.219.236.222,46.101.166.19,193.23.244.244,62.210.124.124,2.3.69.209, 144.76.92.176,91.121.65.179,146.0.32.144,148.244.38.101,91.219.237.229,50.7.161.218, 149.202.160.69,217.79.179.177,87.7.10.93,163.172.149.155,212.47.232.237,192.42.115.101, 171.25.193.9,81.30.158.223,178.62.197.82,195.22.26.248,79.172.193.32,212.47.244.98, 197.231.221.221,38.229.72.16,5.35.251.247,198.96.155.3,46.101.166.19,128.31.0.39, 213.61.66.117,23.254.167.231) Finally, we pull it all together and receive our first results file. results - maxmind(ips, file, c(continent_name, country_code, country_name width:328px" /> And in one fell swoop, we create a word cloud from our data. wordcloud(results$country_name, max.words = 100, min.freq = 1, random.order = FALSE, rot.per=0.35, colors=brewer.pal(8, Dark2 width:267px" /> Hmm, looks like most of the malicious IPs are in Germany. :-) Prefer to visualize that a different way? No problem, well run a quick count and use plotH to create a scatterplot with histogram-like bars. ct - count(results$country_name) plotH(freq~x,data=ct,ylab=Frequency,xlab=Country,col=blue width:434px" /> Give it a try for yourself. When events such as WannaCry have you frustrated and down, you can at least take data-driven security analysis in your own hands. Resources for this article: WannaCry font-size:15px">|">@holisticinfosec (c) SANS | Guideline | Wannacry | ||
| 2017-05-13 17:17:00 | Making Sense of WannaCry (lien direct) |
 Whenever a calamity befalls, it's only natural for people to try and rationalise and identify the problem.
As is now happening with the WannaCry ransomware outbreak that affected the UK's NHS service, and other services in over 100 countries. People are discussing what should have been done to prevent it.
On one hand, there’s a debate ongoing about responsible disclosure practices. Should the NSA have "sat on" vulnerabilities for so long? Because when Shadowbrokers released the details it left a small window for enterprises to upgrade their systems.
On the other hand, there are several so-called “simple” steps the NHS or other similar organisations could have taken to protect themselves, these would include:
Upgrading systems
Patching systems
Maintaining support contracts for out of date operating systems
Architecting infrastructure to be more secure
Acquiring and implementing additional security tools.
The reality is that while any of these defensive measures could have prevented or minimised the attack, none of these are easy for many enterprises to implement.
Also, none of these are new discussions or challenges. Most security professionals have witnessed these same occurrences, albeit not as wide scale, for many years.
Sometimes the infrastructure or endpoint devices aren’t all controlled by IT. Also, patching or updating a system can sometimes lead to other dependent applications breaking or having other issues. For example, the operating system can’t be updated until another vendor updates their software, which in turn can’t be updated until an in-house custom application is updated.
There are many other technical nuances; but it boils down to risk management. And often times if systems are working as desired with no issues, then they will be kept running as such, especially where the costs of upgrading is a taxpayer expense.
That’s not to say security measures shouldn’t be implemented. In an ideal world it would be good to see no legacy systems, regular patching, and securely architected infrastructure. Unfortunately, that is the exception for most companies; not the rule. So while its easy to simply say that the government should have put more money into systems; it’s more a case of the senior decision-makers and purse string holders weighing risks - understanding the exposure they have, the pros and cons, and the potential impact.
Only then can decisions be made that can result in meaningful change. This should include addressing the root causes for the Wannacry outbreak and other threats. It’s inevitable there will be copy-cats soon, with it being trivial to replace the transport mechanism (the SMB worm) with a new payload (variant of ransomware).
But more could be done. Australia is notable for their success in enforcing higher than average security across government. Departments are mandated to enforce four technical controls. The first attacks would have been limited by the first two controls - application whitelisting and regular patching. Enforcing these controls on legacy systems requires a significant investment in personnel.
That’s not to say stricter legislation is the answer. However, blaming companies for not patching, or running legacy systems, or asking that intelligence agencies cease cyber activities is not going to fix the issues.
Here's the video!
Whenever a calamity befalls, it's only natural for people to try and rationalise and identify the problem.
As is now happening with the WannaCry ransomware outbreak that affected the UK's NHS service, and other services in over 100 countries. People are discussing what should have been done to prevent it.
On one hand, there’s a debate ongoing about responsible disclosure practices. Should the NSA have "sat on" vulnerabilities for so long? Because when Shadowbrokers released the details it left a small window for enterprises to upgrade their systems.
On the other hand, there are several so-called “simple” steps the NHS or other similar organisations could have taken to protect themselves, these would include:
Upgrading systems
Patching systems
Maintaining support contracts for out of date operating systems
Architecting infrastructure to be more secure
Acquiring and implementing additional security tools.
The reality is that while any of these defensive measures could have prevented or minimised the attack, none of these are easy for many enterprises to implement.
Also, none of these are new discussions or challenges. Most security professionals have witnessed these same occurrences, albeit not as wide scale, for many years.
Sometimes the infrastructure or endpoint devices aren’t all controlled by IT. Also, patching or updating a system can sometimes lead to other dependent applications breaking or having other issues. For example, the operating system can’t be updated until another vendor updates their software, which in turn can’t be updated until an in-house custom application is updated.
There are many other technical nuances; but it boils down to risk management. And often times if systems are working as desired with no issues, then they will be kept running as such, especially where the costs of upgrading is a taxpayer expense.
That’s not to say security measures shouldn’t be implemented. In an ideal world it would be good to see no legacy systems, regular patching, and securely architected infrastructure. Unfortunately, that is the exception for most companies; not the rule. So while its easy to simply say that the government should have put more money into systems; it’s more a case of the senior decision-makers and purse string holders weighing risks - understanding the exposure they have, the pros and cons, and the potential impact.
Only then can decisions be made that can result in meaningful change. This should include addressing the root causes for the Wannacry outbreak and other threats. It’s inevitable there will be copy-cats soon, with it being trivial to replace the transport mechanism (the SMB worm) with a new payload (variant of ransomware).
But more could be done. Australia is notable for their success in enforcing higher than average security across government. Departments are mandated to enforce four technical controls. The first attacks would have been limited by the first two controls - application whitelisting and regular patching. Enforcing these controls on legacy systems requires a significant investment in personnel.
That’s not to say stricter legislation is the answer. However, blaming companies for not patching, or running legacy systems, or asking that intelligence agencies cease cyber activities is not going to fix the issues.
Here's the video!
|
Guideline | Wannacry |
1
We have: 40 articles.
We have: 40 articles.
To see everything:
Our RSS (filtrered)
