What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2021-04-16 12:26:02 | Russia-linked APT SVR actively targets these 5 flaws (lien direct) | The US government warned that Russian cyber espionage group SVR is exploiting five known vulnerabilities in enterprise infrastructure products. The U.S. National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI) have published a joint advisory that warns that Russia-linked APT group SVR (aka APT29, Cozy Bear, and The Dukes). […] | APT 29 | |||
| 2021-04-15 22:20:58 | US Gov sanctions Russia and expels 10 diplomats over SolarWinds hack (lien direct) | The U.S. and UK attributed with “high confidence” the recently disclosed supply chain attack on SolarWinds to Russia’s Foreign Intelligence Service (SVR). The U.S. and U.K. attributed with “high confidence” the supply chain attack on SolarWinds to operatives working for Russia’s Foreign Intelligence Service (SVR) (ska APT29, Cozy Bear, and The Dukes). The UK, US […] | Hack | APT 29 | ||
| 2021-03-07 14:54:02 | Russia-linked APT groups exploited Lithuanian infrastructure to launch attacks (lien direct) | Russia-linked APT groups leveraged the Lithuanian nation's technology infrastructure to launch cyber-attacks against targets worldwide. The annual national security threat assessment report released by Lithuania's State Security Department states that Russia-linked APT groups conducted cyber-attacks against top Lithuanian officials and decision-makers last in 2020. APT29 state-sponsored hackers also exploited Lithuania's information technology infrastructure to carry […] | Threat | APT 29 | ||
| 2021-03-02 15:00:00 | Anomali Cyber Watch: APT Groups, Cobalt Strike, Russia, Malware, and More (lien direct) |
We are excited to announce Anomali Cyber Watch, your weekly intelligence digest. Replacing the Anomali Weekly Threat Briefing, Anomali Cyber Watch provides summaries of significant cybersecurity and threat intelligence events, analyst comments, and recommendations from Anomali Threat Research to increase situational awareness, and the associated tactics, techniques, and procedures (TTPs) to empower automated response actions proactively.
We hope you find this version informative and useful. If you haven’t already subscribed get signed up today so you can receive curated and summarized cybersecurity intelligence events weekly.
The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: China, Emotet, Go, Masslogger, Mustang Panda, OilRig, and Vulnerabilities. The IOCs related to these stories are attached to the Weekly Threat Briefing and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Hypervisor Jackpotting: CARBON SPIDER and SPRITE SPIDER Target ESXi Servers With Ransomware to Maximize Impact
(published: February 26, 2021)
Recent reporting indicates that two prolific cybercrime threat groups, CARBON SPIDER and SPRITE SPIDER, have begun targeting ESXi, a hypervisor developed by VMWare to run and manage virtual machines. SPRITE SPIDER uses PyXie's LaZagne module to recover vCenter credentials stored in web browsers and runs Mimikatz to steal credentials from host memory. After authenticating to vCenter, SPRITE SPIDER enables ssh to permit persistent access to ESXi devices. In some cases, they also change the root account password or the host’s ssh keys. Before deploying Defray 777, SPRITE SPIDER’s ransomware of choice, they terminate running VMs to allow the ransomware to encrypt files associated with those VMs. CARBON SPIDER has traditionally targeted companies operating POS devices, with initial access being gained using low-volume phishing campaigns against this sector. But throughout 2020 they were observed shifting focus to “Big Game Hunting” with the introduction of the Darkside Ransomware. CARBON SPIDER gains access to ESXi servers using valid credentials and reportedly also logs in over ssh using the Plink utility to drop the Darkside
Recommendation: Both CARBON SPIDER and SPRITE SPIDER likely intend to use ransomware targeting ESXi to inflict greater harm – and hopefully realize larger profits – than traditional ransomware operations against Windows systems. Should these campaigns continue and prove to be profitable, we would expect more threat actors to imitate these activities.
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE ATT&CK] Hidden Files and Directories - T1158 | [MITRE ATT&CK] Process Discovery - T1057 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Remote Services - T1021 | [MITRE ATT&CK] Scheduled Transfer - T1029 |
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Hypervisor Jackpotting: CARBON SPIDER and SPRITE SPIDER Target ESXi Servers With Ransomware to Maximize Impact
(published: February 26, 2021)
Recent reporting indicates that two prolific cybercrime threat groups, CARBON SPIDER and SPRITE SPIDER, have begun targeting ESXi, a hypervisor developed by VMWare to run and manage virtual machines. SPRITE SPIDER uses PyXie's LaZagne module to recover vCenter credentials stored in web browsers and runs Mimikatz to steal credentials from host memory. After authenticating to vCenter, SPRITE SPIDER enables ssh to permit persistent access to ESXi devices. In some cases, they also change the root account password or the host’s ssh keys. Before deploying Defray 777, SPRITE SPIDER’s ransomware of choice, they terminate running VMs to allow the ransomware to encrypt files associated with those VMs. CARBON SPIDER has traditionally targeted companies operating POS devices, with initial access being gained using low-volume phishing campaigns against this sector. But throughout 2020 they were observed shifting focus to “Big Game Hunting” with the introduction of the Darkside Ransomware. CARBON SPIDER gains access to ESXi servers using valid credentials and reportedly also logs in over ssh using the Plink utility to drop the Darkside
Recommendation: Both CARBON SPIDER and SPRITE SPIDER likely intend to use ransomware targeting ESXi to inflict greater harm – and hopefully realize larger profits – than traditional ransomware operations against Windows systems. Should these campaigns continue and prove to be profitable, we would expect more threat actors to imitate these activities.
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE ATT&CK] Hidden Files and Directories - T1158 | [MITRE ATT&CK] Process Discovery - T1057 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Remote Services - T1021 | [MITRE ATT&CK] Scheduled Transfer - T1029 | |
Ransomware Malware Threat | Wannacry Wannacry APT 29 APT 28 APT 31 APT 34 | ||
| 2021-01-19 14:00:00 | Les stratégies de remédiation et de durcissement pour Microsoft 365 pour se défendre contre UNC2452 |Blog Remediation and Hardening Strategies for Microsoft 365 to Defend Against UNC2452 | Blog (lien direct) |
Mise à jour (mai 2022): Nous avons fusionné unc2452 avec apt29 .L'activité UNC2452 décrite dans ce post et ce rapport est désormais attribuée à APT29.
Mise à jour (28 octobre 2021): Mandiant a récemment observé des acteurs de menace ciblés utilisant l'identité EWS (via le rôle de l'impression d'application) pour maintenir un accès persistant aux boîtes aux lettres dans les environnements victimes.Une fois que l'acteur de menace a accès à ce rôle, ses abus sont difficiles à détecter et fournissent le contrôle de l'acteur de menace sur chaque boîte aux lettres d'un locataire victime.Mandiant a également observé des acteurs de menace ciblés abusant de la relation de confiance entre le cloud
UPDATE (May 2022): We have merged UNC2452 with APT29. The UNC2452 activity described in this post and report is now attributed to APT29. UPDATE (Oct. 28, 2021): Mandiant has recently observed targeted threat actors using EWS impersonation (via the ApplicationImpersonation role) to maintain persistent access to mailboxes in victim environments. Once the threat actor has access to this role, its abuse is hard to detect and provides the threat actor control over every mailbox in a victim tenant. Mandiant has also observed targeted threat actors abusing the trust relationship between Cloud |
Threat | APT 29 | ★★★★ | |
| 2020-12-17 18:00:00 | FireEye, SolarWinds Hacks Show that Detection is Key to Solid Defense (lien direct) | Several years back, industry analyst firm Gartner began circulating the idea that almost every major enterprise and government agency was either compromised or would be compromised at some point in time. This week, when we woke up to the news that FireEye and SolarWinds had joined the ranks of the hacked, we learned once again that Gartner was right. Even companies with advanced security expertise and expansive resources can’t escape this inevitable fact of digital life.
Forensic experts and news outlets are now following the trail of digital clues, trying to make sense of how both companies ended up on the hacked side of the equation. At a high level, we know that FireEye was compromised by a state-sponsored adversary. In the case of SolarWinds, it is looking like an adversary was able to dwell in victims’ networks for as long as nine months and that the prime suspect is the Kremlin.
There are undoubtedly many organizations wondering if they are caught up in the attacks, either by design or indirectly. Fortunately, those that have effective threat detection capabilities in place can utilize the information FireEye, SolarWinds, Anomali and other threat research organizations are providing to determine if they’ve been hit.
Anomali customers are already ahead of the game. As soon as the world becomes aware of an attack, Anomali Threat Research immediately front-loads Anomali ThreatStream with a threat bulletin that provides a detailed and concise narrative of the situation along with a comprehensive list of the known indicators of compromise (IOCs). Once added, information relevant to the incident (IOCs, reports from the security community, signatures, etc.) are automatically delivered to customers. This gives them the ability to automate threat detection and blocking across their security controls, including EDR, firewalls, and SIEM. In addition, customers using Anomali Match, our threat detection and response product, are able to use the threat intelligence to do a retrospective search back to when the threat was active, getting real-time results showing whether the threat was seen in their network at that time.
To provide threat intelligence and security operations analysts with a look at what an Anomali threat bulletin looks like, we’ve added the first version of the FireEye threat bulletin to this blog. We are happy to discuss more deeply how Anomali customers are using this information and continual updates to detect the presence of related IOCs in their environments. Reach us at general@anomali.com.
To listen to a more in-depth conversation on the incident and how threat intelligence aids in detection, listen to this week’s Anomali Detect Podcast.
 Key Findings
Unknown, sophisticated actors stole more than 300 FireEye Red Team tools and countermeasures (signatures) on an unspecified date.
An unnamed source for The Washington Post claimed Cozy Bear (APT29), is responsible, but provided no evidence.
Actor(s) were also interested in FireEye customers, specifically, government entities.
The Red Team countermeasures consisted of custom-versions of known tools, a prioritized Common Vulnerabilities and Exposures (CVE) list, and malware signatures in ClamAV, HXIOC, Snort, and Yara languages.
The stolen tools could be customized by actors, just as the FireEye Red Team did to existing tools.
Key Findings
Unknown, sophisticated actors stole more than 300 FireEye Red Team tools and countermeasures (signatures) on an unspecified date.
An unnamed source for The Washington Post claimed Cozy Bear (APT29), is responsible, but provided no evidence.
Actor(s) were also interested in FireEye customers, specifically, government entities.
The Red Team countermeasures consisted of custom-versions of known tools, a prioritized Common Vulnerabilities and Exposures (CVE) list, and malware signatures in ClamAV, HXIOC, Snort, and Yara languages.
The stolen tools could be customized by actors, just as the FireEye Red Team did to existing tools.
|
Malware Threat Guideline | APT 29 | ||
| 2020-12-15 11:01:00 | 18 000 entreprises et organisations ont téléchargé la backdoor des hackers de Poutine (lien direct) | L'ampleur de l'infection orchestrée par APT19, alias Cozy Bear, est certes énorme, mais cela ne veut pas dire que toutes les victimes ont réellement été piratées.  |
APT 29 APT 19 | |||
| 2020-12-15 03:44:00 | SolarWinds attack explained: And why it was so hard to detect (lien direct) | A group believed to be Russia's Cozy Bear gained access to government and other systems through a compromised update to SolarWinds' Orion software. Most organizations aren't prepared for this sort of software supply chain attack. | APT 29 | |||
| 2020-12-14 21:36:39 | No One Knows How Deep Russia\'s Hacking Rampage Goes (lien direct) | A supply chain attack against IT company SolarWinds has exposed as many as 18,000 companies to Cozy Bear's attacks. | APT 29 | |||
| 2020-12-13 22:00:00 | L'attaquant très évasif exploite la chaîne d'approvisionnement de Solarwinds pour compromettre plusieurs victimes mondiales avec Sunburst Backdoor Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor (lien direct) |
Mise à jour (mai 2022): Nous avons fusionné unc2452 avec apt29 .L'activité UNC2452 décrite dans ce post est désormais attribuée à APT29.
Résumé de l'exécutif
Nous avons découvert une campagne mondiale d'intrusion.Nous suivons les acteurs derrière cette campagne sous le nom de UNC2452.
Fireeye a découvert une attaque de chaîne d'approvisionnement trrojanisant les mises à jour de logiciels commerciaux de Solarwinds Orion afin de distribuer des logiciels malveillants que nous appelons Sunburst.
L'activité post-compromis de l'attaquant exploite plusieurs techniques pour échapper à la détection et obscurcir leur activité, mais ces efforts offrent également quelques opportunités de détection.
le
UPDATE (May 2022): We have merged UNC2452 with APT29. The UNC2452 activity described in this post is now attributed to APT29. Executive Summary We have discovered a global intrusion campaign. We are tracking the actors behind this campaign as UNC2452. FireEye discovered a supply chain attack trojanizing SolarWinds Orion business software updates in order to distribute malware we call SUNBURST. The attacker\'s post compromise activity leverages multiple techniques to evade detection and obscure their activity, but these efforts also offer some opportunities for detection. The |
Malware | Solardwinds APT 29 | ★★★ | |
| 2020-12-13 21:44:40 | US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor (lien direct) | State-sponsored actors allegedly working for Russia have targeted the US Treasury, the Commerce Department's National Telecommunications and Information Administration (NTIA), and other government agencies to monitor internal email traffic as part of a widespread cyberespionage campaign.
The Washington Post, citing unnamed sources, said the latest attacks were the work of APT29 or Cozy Bear, the |
APT 29 | |||
| 2020-07-17 11:55:00 | Experts On Russian Hackers Target Covid-19 Vaccine Research (lien direct) | Following the news that Russian state-sponsored hackers (a group known as “APT29” or “Cozy Bear”) targeted Covid-19 vaccine research, cybersecurity experts commented below. The ISBuzz Post: This Post Experts On Russian Hackers Target Covid-19 Vaccine Research | APT 29 | |||
| 2020-07-17 09:52:24 | Cozy Bear Hackers Target Covid-19 Research Centres in UK, US and Canada (lien direct) | An advisory published by the UK National Cyber Security Centre (NCSC) warns of activity by Russian hacking group APT29 and explicitly calls out efforts to target the US, UK, and Canadian vaccine research, according to CNN. Cyber actors from the Russian hacking group, which also goes by the name “the Dukes” or “Cozy Bear”, are … The ISBuzz Post: This Post Cozy Bear Hackers Target Covid-19 Research Centres in UK, US and Canada | APT 29 | |||
| 2020-07-17 07:54:04 | COVID-19 Researchers Targeted by Russian State-Sponsored Hackers (lien direct) | According to an advisory issued by the National Cyber Security Centre (NCSC) and counterparts in Canada and America, Russian state-sponsored hackers, APT29 or Cozy Bear, have been attacking organisations working towards a coronavirus vaccine. The campaign has been targeting government agencies, diplomatic bodies, healthcare organisations, thinktanks and the energy sector looking to steal intellectual property. […] | APT 29 | |||
| 2020-07-16 14:45:58 | UK NCSC blames Russia-linked APT29 for attacks on COVID-19 vaccine research (lien direct) | The UK National Cyber Security Centre says that Russia-linked APT29 group is attempting to steal research data related to potential COVID-19 vaccines. The British National Cyber Security Centre revealed that Russia-linked group APT29 is conducting cyberespionage campaigns targeting UK, US, and Canadian organizations working of the development of a COVID-19 vaccine. “RUSSIAN cyber actors are targeting organisations […] | APT 29 | |||
| 2019-10-18 10:13:01 | (Déjà vu) Russian hackers noticed after being undetected for years (lien direct) | Cyber-espionage operations from Cozy Bear, a threat actor believed to work for the Russian government, continued undetected for the past years by using malware families previously unknown to security researchers. Relying on stealthy communication techniques between infected systems and the command and control (C2) servers, the group managed to keep their activity under the radar […] | Malware Threat | APT 29 | ||
| 2019-10-17 15:33:16 | Experts Comments: Sophisticated Russian Hacking Group Is back In Action Again (lien direct) | A Russian cyberespionage operation which was one of the groups which hacked into Democratic National Committee in the run-up to the 2016 US Presidential election has been busy with attacks against government departments across Europe and beyond. The Cozy Bear hacking group – also known as APT29 – is believed to be associated with the Russian intelligence … The ISBuzz Post: This Post Experts Comments: Sophisticated Russian Hacking Group Is back In Action Again | APT 29 | |||
| 2019-10-17 10:45:00 | Cozy Bear Emerges from Hibernation to Hack EU Ministries (lien direct) | The cyber-espionage group, linked to Russia and blamed for hacking the Democratic National Committee in 2016, has been using covert communications and other techniques to escape detection for at least two years. | Hack | APT 29 | ||
| 2019-10-17 09:39:47 | Cozy Bear Russian Hackers Spotted After Staying Undetected for Years (lien direct) | Cyber-espionage operations from Cozy Bear, a threat actor believed to work for the Russian government, continued undetected for the past years by using malware families previously unknown to security researchers. [...] | Malware Threat | APT 29 | ||
| 2019-10-17 09:30:46 | Operation Ghost: The Dukes aren\'t back – they never left (lien direct) | ESET researchers describe recent activity of the infamous espionage group, the Dukes, including three new malware families | Malware | APT 29 | ||
| 2019-10-17 09:30:00 | Russia\'s Cozy Bear Hackers Resurface With Clever New Tricks (lien direct) | Largely out of the spotlight since 2016, Cozy Bear hackers have been caught perpetrating a years-long campaign. | APT 29 | |||
| 2019-10-17 01:21:19 | Les cyberespions russes s\'attaquent aux diplomates européens par stéganographie (lien direct) | Des outils assez nouveaux et sophistiqués du groupe The Dukes, alias APT 29, ont été détectés récemment dans le cadre d'une opération d'espionnage qui remonte à 2013.  |
APT 29 | ★★ | ||
| 2019-01-19 00:27:03 | DNC says Russia tried to hack its servers again in November 2018 (lien direct) | Democrats say the spear-phishing attack, which was attributed to Russian group Cozy Bear, was unsuccessful. | Hack | APT 29 | ||
| 2018-11-23 10:38:04 | Exclusive Cybaze ZLab – Yoroi – Hunting Cozy Bear, new campaign, old habits (lien direct) | The experts at Cybaze ZLab – Yoroi continue the analysis of new strain of malware used by the Russia-linked APT29 cyberespionage group (aka Cozy Bear) The experts at Cybaze ZLab – Yoroi continue the analysis of new strain of malware used by the Russia-linked APT29 cyberespionage group (aka The Dukes, Cozy Bear, and Cozy Duke). The researchers of Yoroi ZLab, on […] | Malware | APT 29 | ||
| 2018-11-21 13:15:04 | Cozy Bear Returns With Post-Election Spear-Phishing Campaign (lien direct) | Attackers suspected of working for the Russian government masqueraded as a US State Department official in an attempt to infect dozens of organizations in government, military, defence contracting, media, and other industries, researchers from security firm FireEye have warned. The tactics, techniques and procedures are akin to those used previously by the Russian APT group … The ISBuzz Post: This Post Cozy Bear Returns With Post-Election Spear-Phishing Campaign | APT 29 | |||
| 2018-11-20 18:03:04 | FireEye publie un nouveau rapport sur une activité de phishing probablement liée au groupe APT29 (lien direct) |  FireEye vient de publier un rapport concernant une nouvelle activité de Phishing qui aurait probablement un lien avec le groupe APT29. Ce rapport vient compléter la première découverte de FireEye, datant du 14 novembre 2018, en apportant plus de détails. FireEye vient de publier un rapport concernant une nouvelle activité de Phishing qui aurait probablement un lien avec le groupe APT29. Ce rapport vient compléter la première découverte de FireEye, datant du 14 novembre 2018, en apportant plus de détails. |
APT 29 | |||
| 2018-11-20 18:01:01 | APT29 Re-Emerges After 2 Years with Widespread Espionage Campaign (lien direct) | The group is best-known for hacking the DNC ahead of the 2016 presidential election. | APT 29 | |||
| 2018-11-20 14:16:01 | Russia\'s Fancy Bear and Cozy Bear Hackers May Have New Phishing Tricks (lien direct) | Two new reports show an uptick in sophisticated phishing attacks originating from-where else-Russia. | APT 29 APT 28 | |||
| 2018-11-19 22:00:00 | Pas si confortable: un examen inconfortable d'une campagne de phishing présumée APT29 Not So Cozy: An Uncomfortable Examination of a Suspected APT29 Phishing Campaign (lien direct) |
Introduction
Les appareils Fireeye ont détecté des tentatives d'intrusion contre plusieurs industries, notamment le groupe de réflexion, l'application de la loi, les médias, les militaires américains, l'imagerie, le transport, la pharmaceutique, le gouvernement national et la contraction de défense.
Les tentatives concernaient un e-mail de phishing semblant provenir du département d'État américain avec des liens vers des fichiers zip contenant des raccourcis Windows malveillants qui ont livré une frappe de cobalt.
Artefacts techniques partagés;tactiques, techniques et procédures (TTPS);et cibler connectez cette activité à l'activité observée précédemment suspectée d'être APT29.
apt29
Introduction FireEye devices detected intrusion attempts against multiple industries, including think tank, law enforcement, media, U.S. military, imagery, transportation, pharmaceutical, national government, and defense contracting. The attempts involved a phishing email appearing to be from the U.S. Department of State with links to zip files containing malicious Windows shortcuts that delivered Cobalt Strike Beacon. Shared technical artifacts; tactics, techniques, and procedures (TTPs); and targeting connect this activity to previously observed activity suspected to be APT29. APT29 |
APT 29 APT 29 | ★★★★ | ||
| 2018-11-19 13:27:04 | Cybaze ZLab – Yoroi team analyzed malware used in recent attacks on US entities attributed to APT29 (lien direct) | Malware researchers from Cybaze ZLab – Yoroi team have detected a new strain of malware that appears to be associated with a new wave of attacks carries out by Russia linked APT29 group. The researchers of Yoroi ZLab, on 16 November, accessed to a new APT29's dangerous malware which seems to be involved in the recent […] | Malware | APT 29 | ||
| 2018-11-18 09:35:00 | Suspected APT29 hackers behind attacks on US gov agencies, think tanks, and businesses (lien direct) | Last week, security experts reported alleged APT29 hackers impersonating a State Department official in attacks aimed at U.S. government agencies, businesses and think tanks. Cyber security experts are warning of new attacks against U.S. government agencies, think tanks, and businesses. Threat actors carried out spear phishing attacks impersonating a State Department official to attempt compromising targets, […] | Threat | APT 29 | ||
| 2018-11-16 23:40:00 | Russian APT comes back to life with new US spear-phishing campaign (lien direct) | Cozy Bear (APT29) makes a comeback after last year's Dutch and Norwegian hacking campaigns. | APT 29 | |||
| 2018-02-02 21:29:09 | NEWS WRAP-UP: Dutch spies corroborate Russia\'s meddling in U.S. election - and 19 EU nations (lien direct) | Week ending Feb. 2, 2018. Even more substantive corroborating evidence of Russia's proactive interference in the 2016 U.S. presidential election comes from the Netherlands. European news reports detail how a Dutch intelligence agency secretly hacked into the Kremlin's most notorious hacking group, Cozy Bear, and tracked Cozy Bear's election tampering activities. Dutch spies passed all […] | APT 29 | |||
| 2018-01-28 13:23:51 | Les services secrets néerlandais infiltrent Cozy Bear (lien direct) | >Fume, c’est du Cozy Bear ! Les services de renseignement néerlandais auraient fourni des preuves cruciales à leurs homologues américains sur l’ingérence de la Russie lors des élections de 2016. Voilà qui est intéressant. Les services secrets américains ne seraient pas les auteurs des inf... Cet article Les services secrets néerlandais infiltrent Cozy Bear est apparu en premier sur ZATAZ. | APT 29 | |||
| 2018-01-26 17:05:41 | The Dutch were spying on Cozy Bear Hackers as they targeted Democrats (lien direct) | Dutch intelligence is claiming to have observed Russian state-sponsored hackers known as Cozy Bear attacking Democratic Party organizations in the U.S. beginning in 2014. A shocking report from a Dutch website, de Volkskrant, claims that hackers from that country’s intelligence community penetrated the network of a building used by...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/520448790/0/thesecurityledger -->» | APT 29 | |||
| 2018-01-26 14:45:00 | Dutch Intel Agency Reportedly Helped US Attribute DNC Hack to Russia (lien direct) | The General Intelligence and Security Service of the Netherlands broke into Cozy Bear's network in 2014 and spotted the group launching attacks, de Volkskrant says. | APT 29 | |||
| 2018-01-26 11:37:18 | Dutch intelligence agency spied on and took photos of Russia-linked Cozy Bear hackers (lien direct) | >In 2014, Dutch intelligence agency AIVD reportedly managed to locate the hub of the Kremlin-linked hacker group Cozy Bear, also known as APT29. AIVD reportedly gained access to the state-sponsored hacker group’s networks and spied on Cozy Bear’s hacking activities in a cyberespionage campaign that is believed to have lasted between one and two and ... | APT 29 | ★★ | ||
| 2018-01-26 10:40:29 | The Dutch intelligence service AIVD \'hacked\' Russian Cozy Bear systems for years (lien direct) | Spying on spies – The hackers from the Dutch intelligence service AIVD ‘compromised’ for years the network of the Russian APT Cozy Bear. It’s not a mystery, technology firms that intend to work with Russia need to allow the Government experts to scan their code for backdoors and vulnerabilities. The problem is that this software […] | APT 29 | |||
| 2017-04-05 22:57:33 | Part II. APT29 Russian APT including Fancy Bear (lien direct) |  This is the second part of Russian APT series."APT29 - The Dukes Cozy Bear: APT29 is threat group that has been attributed to the Russian government and has operated since at least 2008.1210 This group reportedly compromised the Democratic National Committee starting in the summer of 2015" (src. Mitre ATT&CK)Please see the first post here: Russian APT - APT28 collection of samples including OSX XAgentI highly recommend reading and studying these resources first:Mitre ATT&CK2017-03 Disinformation. A Primer In Russian Active Measures And Influence Campaigns. Hearings before the Select Committee on Intelligence, March 20172014-08 Mikko Hipponen. Governments as Malware Authors. Presentation ppt.2016. No Easy Breach: Challenges and Lessons from an Epic Investigation. Mandiant. Matthew Dunwoody, Nick Carr. VideoBeyond 'Cyber War': Russia's Use of Strategic Cyber Espionage and Information Operations in Ukraine. NATO Cooperative Cyber Defence Centre of Excellence/ Fireeye - Jen WeedonList of References (and samples mentioned) listed from oldest to newest:2012-02 FSecure. COZYDUKE2013-02_Crysys_Miniduke Indicators2013-04_Bitdefender_A Closer Look at MiniDuke2014-04 FSecure_Targeted Attacks and Ukraine2014-05_FSecure.Miniduke still duking it out2014-07_Kaspersky_Miniduke is back_Nemesis Gemina and the Botgen Studio2014-07_Kaspersky_The MiniDuke Mystery PDF 0-day2014-11_FSecure_OnionDuke APT Attacks Via the Tor Network2014_FSecure_Cosmicduke Cosmu with a twist of MiniDuke2015-04_Kaspersky_CozyDuke-CozyBear This is the second part of Russian APT series."APT29 - The Dukes Cozy Bear: APT29 is threat group that has been attributed to the Russian government and has operated since at least 2008.1210 This group reportedly compromised the Democratic National Committee starting in the summer of 2015" (src. Mitre ATT&CK)Please see the first post here: Russian APT - APT28 collection of samples including OSX XAgentI highly recommend reading and studying these resources first:Mitre ATT&CK2017-03 Disinformation. A Primer In Russian Active Measures And Influence Campaigns. Hearings before the Select Committee on Intelligence, March 20172014-08 Mikko Hipponen. Governments as Malware Authors. Presentation ppt.2016. No Easy Breach: Challenges and Lessons from an Epic Investigation. Mandiant. Matthew Dunwoody, Nick Carr. VideoBeyond 'Cyber War': Russia's Use of Strategic Cyber Espionage and Information Operations in Ukraine. NATO Cooperative Cyber Defence Centre of Excellence/ Fireeye - Jen WeedonList of References (and samples mentioned) listed from oldest to newest:2012-02 FSecure. COZYDUKE2013-02_Crysys_Miniduke Indicators2013-04_Bitdefender_A Closer Look at MiniDuke2014-04 FSecure_Targeted Attacks and Ukraine2014-05_FSecure.Miniduke still duking it out2014-07_Kaspersky_Miniduke is back_Nemesis Gemina and the Botgen Studio2014-07_Kaspersky_The MiniDuke Mystery PDF 0-day2014-11_FSecure_OnionDuke APT Attacks Via the Tor Network2014_FSecure_Cosmicduke Cosmu with a twist of MiniDuke2015-04_Kaspersky_CozyDuke-CozyBear |
APT 29 APT 28 | |||
| 2017-04-03 12:42:42 | APT29 Uses Stealthy Backdoor to Maintain Access to Targets (lien direct) | Researchers at FireEye-owned Mandiant have conducted a detailed analysis of a stealthy backdoor used by the Russia-linked cyberespionage group APT29 to maintain access to targeted systems. | APT 29 | |||
| 2017-04-03 07:00:00 | Dissection de l'une des boursiers WMI et PowerShell sans fichu et PowerShell (Poshspy) Dissecting One of APT29\\'s Fileless WMI and PowerShell Backdoors (POSHSPY) (lien direct) |
Mandiant a observé APT29 en utilisant une porte dérobée furtive que nous appelons poshspy.Poshspy exploite deux des outils que le groupe utilise fréquemment: PowerShell et Windows Management Instrumentation (WMI).Dans les enquêtes que Mandiant a menées, il est apparu qu'APT29 a déployé Poshspy comme porte dérobée secondaire pour une utilisation s'ils perdaient l'accès à leurs possibilités principales.
Poshspy tire le meilleur parti des fonctionnalités Windows intégrées & # 8211;Ce que l'on appelle «vivre du terrain» & # 8211;pour faire une porte dérobée particulièrement furtive.L'utilisation de WMI de Poshspy \\ pour stocker et persister le code de porte dérobée le rend presque invisible pour quiconque
Mandiant has observed APT29 using a stealthy backdoor that we call POSHSPY. POSHSPY leverages two of the tools the group frequently uses: PowerShell and Windows Management Instrumentation (WMI). In the investigations Mandiant has conducted, it appeared that APT29 deployed POSHSPY as a secondary backdoor for use if they lost access to their primary backdoors. POSHSPY makes the most of using built-in Windows features – so-called “living off the land” – to make an especially stealthy backdoor. POSHSPY\'s use of WMI to both store and persist the backdoor code makes it nearly invisible to anyone |
Tool Technical | APT 29 | ★★★★ | |
| 2017-03-31 02:03:28 | Part I. Russian APT - APT28 collection of samples including OSX XAgent (lien direct) |  This post is for all of you, Russian malware lovers/haters. Analyze it all to your heart's content. Prove or disprove Russian hacking in general or DNC hacking in particular, or find that "400 lb hacker" or nail another country altogether. You can also have fun and exercise your malware analysis skills without any political agenda.The post contains malware samples analyzed in the APT28 reports linked below. I will post APT29 and others later.Read about groups and types of targeted threats here: Mitre ATT&CKList of References (and samples mentioned) listed from oldest to newest:APT28_2011-09_Telus_Trojan.Win32.Sofacy.AAPT28_2014-08_MhtMS12-27_PrevenityAPT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.OperationsAPT28_2014-10_Telus_Coreshell.AAPT28_2014-10_TrendMicro Operation Pawn Storm. Using Decoys to Evade DetectionAPT28_2015-07_Digital Attack on German ParliamentAPT28_2015-07_ESET_Sednit_meet_HackingAPT28_2015-07_Telus_Trojan-Downloader.Win32.Sofacy.BAPT28_2015-09_Root9_APT28_Technical_FollowupAPT28_2015-09_SFecure_Sofacy-recycles-carberp-and-metasploit-codeAPT28_2015-10_New Adobe Flash Zero-Day Used in Pawn StormAPT28_2015-10_Root9_APT28_targets Financial MarketsAPT28_2015-12_Bitdefender_In-depth_anal This post is for all of you, Russian malware lovers/haters. Analyze it all to your heart's content. Prove or disprove Russian hacking in general or DNC hacking in particular, or find that "400 lb hacker" or nail another country altogether. You can also have fun and exercise your malware analysis skills without any political agenda.The post contains malware samples analyzed in the APT28 reports linked below. I will post APT29 and others later.Read about groups and types of targeted threats here: Mitre ATT&CKList of References (and samples mentioned) listed from oldest to newest:APT28_2011-09_Telus_Trojan.Win32.Sofacy.AAPT28_2014-08_MhtMS12-27_PrevenityAPT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.OperationsAPT28_2014-10_Telus_Coreshell.AAPT28_2014-10_TrendMicro Operation Pawn Storm. Using Decoys to Evade DetectionAPT28_2015-07_Digital Attack on German ParliamentAPT28_2015-07_ESET_Sednit_meet_HackingAPT28_2015-07_Telus_Trojan-Downloader.Win32.Sofacy.BAPT28_2015-09_Root9_APT28_Technical_FollowupAPT28_2015-09_SFecure_Sofacy-recycles-carberp-and-metasploit-codeAPT28_2015-10_New Adobe Flash Zero-Day Used in Pawn StormAPT28_2015-10_Root9_APT28_targets Financial MarketsAPT28_2015-12_Bitdefender_In-depth_anal |
APT 29 APT 28 | |||
| 2017-03-27 20:14:12 | APT29 Used Domain Fronting, Tor to Execute Backdoor (lien direct) | APT29, a/k/a Cozy Bear, has used Tor and a technique called domain fronting in order to secure backdoor access to targets for nearly two years running. | APT 29 | |||
| 2017-03-27 14:56:43 | APT29 Cyberspies Use Domain Fronting to Evade Detection (lien direct) | The Russia-linked cyber espionage group known as APT29 has been using a technique called “domain fronting†in an effort to make it more difficult for targeted organizations to identify malicious traffic, FireEye reported on Monday. | APT 29 | |||
| 2017-03-27 07:00:00 | Domaine APT29 Fonctionner avec Tor APT29 Domain Fronting With TOR (lien direct) |
Mandiant a observé que les attaquants de l'État-nation russe APT29 employant des techniques de façade de domaine pour l'accès de porte dérobée furtif aux environnements victimes pendant au moins deux ans.Il y a eu des discussions considérables sur le fronoisement du domaine après la publication d'un document détaillant ces techniques .Domain Fronting fournit des connexions de réseau sortant qui ne se distinguent pas des demandes légitimes de sites Web populaires.
APT29 a utilisé le routeur d'oignon (TOR) et le plugin de façade du domaine Tor Mode pour créer un tunnel réseau crypté caché qui semblait se connecter aux services Google sur TLS
Mandiant has observed Russian nation-state attackers APT29 employing domain fronting techniques for stealthy backdoor access to victim environments for at least two years. There has been considerable discussion about domain fronting following the release of a paper detailing these techniques. Domain fronting provides outbound network connections that are indistinguishable from legitimate requests for popular websites. APT29 has used The Onion Router (TOR) and the TOR domain fronting plugin meek to create a hidden, encrypted network tunnel that appeared to connect to Google services over TLS |
APT 29 APT 29 | ★★★★ | ||
| 2017-02-13 16:52:34 | DHS Uses Cyber Kill Chain to Analyze Russia-Linked Election Hacks (lien direct) | DHS Publishes Enhanced Analysis Report on GRIZZLY STEPPE Activity | APT 29 APT 28 | |||
| 2017-01-11 04:00:46 | 10 Questions that Need to Be Asked about Every Cybersecurity Story (lien direct) | The Russian hacking fiasco we’ve been following over the past weeks – hysteria, which is due to the flawed Grizzly Steppe report and subsequent haphazard news reporting – has done a grave disservice to the serious issue of national cybersecurity. If the world is going to ever turn the corner from its current state of […]… Read More | APT 29 APT 28 | |||
| 2017-01-04 17:40:00 | DHS-FBI Report Shows Russian Attribution\'s A Bear (lien direct) | Political and technical fallout from the DHS-FBI joint 'Grizzly Steppe' report on Russia's role in the recent election-related hacks causes more chaos than closure. | APT 29 APT 28 | |||
| 2017-01-03 21:33:01 | Dear Obama, From Infosec (lien direct) | Dear President Obama:We are more than willing to believe Russia was responsible for the hacked emails/records that influenced our election. We believe Russian hackers were involved. Even if these hackers weren't under the direct command of Putin, we know he could put a stop to such hacking if he chose. It's like harassment of journalists and diplomats. Putin encourages a culture of thuggery that attacks opposition, without his personal direction, but with his tacit approval.Your lame attempts to convince us of what we already agree with has irretrievably damaged your message.Instead of communicating with the America people, you worked through your typical system of propaganda, such as stories in the New York Times quoting unnamed "senior government officials". We don't want "unnamed" officials -- we want named officials (namely you) who we can pin down and question. When you work through this system of official leaks, we believe you have something to hide, that the evidence won't stand on its own.We still don't believe the CIA's conclusions because we don't know, precisely, what those conclusions are. Are they derived purely from companies like FireEye and CloudStrike based on digital forensics? Or do you have spies in Russian hacker communities that give better information? This is such an important issue that it's worth degrading sources of information in order to tell us, the American public, the truth.You had the DHS and US-CERT issue the "GRIZZLY-STEPPE" report "attributing those compromises to Russian malicious cyber activity". It does nothing of the sort. It's full of garbage. It contains signatures of viruses that are publicly available, used by hackers around the world, not just Russia. It contains a long list of IP addresses from perfectly normal services, like Tor, Google, Dropbox, Yahoo, and so forth.Yes, hackers use Yahoo for phishing and malvertising. It doesn't mean every access of Yahoo is an "Indicator of Compromise".For example, I checked my web browser [chrome://net-internals/#dns] and found that last year on November 20th, it accessed two IP addresses that are on the Grizzley-Steppe list: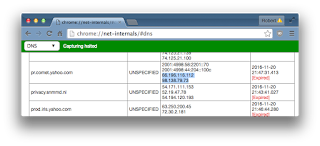 No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati |
Yahoo APT 29 APT 28 | |||
| 2017-01-02 16:29:22 | U.S. Gov\'s "GRIZZLY STEPPE" Report Fails to Achieve Purpose: Experts (lien direct) | The recently released Joint Analysis Report (JAR) published by the Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) to detail tools used by Russian hackers in cyber attacks against the United States election didn't deliver on its promise, security experts argue. | APT 29 APT 28 |
To see everything:
Our RSS (filtrered)
