What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2025-03-27 16:24:42 | Les hacktivistes ciblent de plus en plus la France pour ses efforts diplomatiques Hacktivists Increasingly Target France for Its Diplomatic Efforts (lien direct) |
 According to a Cyble report sent to clients recently, France is increasingly becoming a target of hacktivists for its active role in international diplomacy and in ongoing conflicts in Ukraine and the Middle East.
France\'s role in those conflicts “has drawn the ire of pro-Russian and pro-Palestinian hacktivist groups,” Cyble said, as those hacktivists have found ideological alignment and a common adversary in France.
The attacks have ranged from Distributed Denial-of-Service (DDoS) attacks against French government institutions and other critical infrastructure to attacks against Industrial Control Systems (ICS), with the goal of disrupting essential services, influencing public opinion, and creating political pressure.
Hacktivist Alliance Began with \'Holy League\'
Pro-Russian and pro-Palestinian hacktivists collaborated in the December “Holy League” attacks against French infrastructure and have picked up significantly since January, although Holy League activity against France could also be seen months earlier following the arrest in France of Telegram founder and CEO Pavel Durov.
Cyble
According to a Cyble report sent to clients recently, France is increasingly becoming a target of hacktivists for its active role in international diplomacy and in ongoing conflicts in Ukraine and the Middle East.
France\'s role in those conflicts “has drawn the ire of pro-Russian and pro-Palestinian hacktivist groups,” Cyble said, as those hacktivists have found ideological alignment and a common adversary in France.
The attacks have ranged from Distributed Denial-of-Service (DDoS) attacks against French government institutions and other critical infrastructure to attacks against Industrial Control Systems (ICS), with the goal of disrupting essential services, influencing public opinion, and creating political pressure.
Hacktivist Alliance Began with \'Holy League\'
Pro-Russian and pro-Palestinian hacktivists collaborated in the December “Holy League” attacks against French infrastructure and have picked up significantly since January, although Holy League activity against France could also be seen months earlier following the arrest in France of Telegram founder and CEO Pavel Durov.
Cyble |
Tool Industrial Cloud | APT 15 | ★★★ | |
| 2025-01-09 09:00:00 | Tout savoir sur l\'attribut ping en HTML (lien direct) | Tiens tiens, et si on parlait d’une fonctionnalité HTML plutôt méconnue ? Je veux parler de l’attribut ping, ce petit bout de code qui permet de traquer les clics sur les liens en toute discrétion !
En effet, cette petite merveille issue du HTML5 fait polémique depuis sa création, entre les webmasters qui y voient une aubaine pour l’analyse d’audience et les défenseurs de la vie privée qui tirent la sonnette d’alarme.
Tiens tiens, et si on parlait d’une fonctionnalité HTML plutôt méconnue ? Je veux parler de l’attribut ping, ce petit bout de code qui permet de traquer les clics sur les liens en toute discrétion ! En effet, cette petite merveille issue du HTML5 fait polémique depuis sa création, entre les webmasters qui y voient une aubaine pour l’analyse d’audience et les défenseurs de la vie privée qui tirent la sonnette d’alarme. |
APT 19 | ★★★★ | ||
| 2024-12-24 13:13:55 | Cyberattaque majeure : 40 Go de données clients Peugeot aux mains des hackers de Cicada 3301 (lien direct) | Cyberattaque majeure : 40 Go de données clients Peugeot aux mains des hackers de Cicada 3301
-
Malwares
Cyberattaque majeure : 40 Go de données clients Peugeot aux mains des hackers de Cicada 3301 - Malwares |
APT 10 | ★★★★ | ||
| 2024-12-22 19:03:49 | Les pirates du groupe Cicada 3301 revendiquent une attaque contre les concessions Peugeot (lien direct) | Le groupe de hackers malveillants Cicada 3301 menace Peugeot après avoir prétendument volé 40 Go de données liées à ses concessions. Diffusion prévue : 6 janvier 2025....
Le groupe de hackers malveillants Cicada 3301 menace Peugeot après avoir prétendument volé 40 Go de données liées à ses concessions. Diffusion prévue : 6 janvier 2025.... |
APT 10 | ★★★ | ||
| 2024-12-12 20:36:12 | Lookout Discovers New Chinese Surveillance Tool Used by Public Security Bureaus (lien direct) | ## Snapshot Researchers at Lookout Threat Lab have identified a new surveillance tool called EagleMsgSpy developed by a Chinese software company. ## Description Operational since at least 2017, this spyware has been used by Chinese law enforcement to extract extensive data from mobile devices. It can access third-party chat messages, call logs, device contacts, SMS messages, location data, and network activity. The tool also features screenshot and screen recording capabilities. According to Lookout\'s analysis, EagleMsgSpy includes two key components: an installer APK and a surveillance payload that operates in the background, concealing its activities from the victim. The source code reveals functions that differentiate between device platforms, suggesting the existence of both Android and iOS versions. However, researchers note that physical access to the target device is required to initiate surveillance and EagleMsgSpy has not been found on Google Play or other app stores. Lookout further reports that domain infrastructure linked to EagleMsgSpy overlaps with those associated with public security bureaus in mainland China. This connection indicates widespread use of the tool within the region. Additionally, EagleMsgSpy shares ties with other Chinese surveillance apps, such as PluginPhantom and CarbonSteal, suggesting its role in a broader ecosystem of state-sponsored surveillance targeting various groups in China. ## Microsoft Analysis and Additional OSINT Context Chinese cyber threat actors have been [widely reported](https://www.bloomberg.com/news/articles/2022-11-10/lookout-researchers-say-spyware-tied-to-china-is-targeting-apps-used-by-uyghurs?srnd=technology-vp&sref=E9Urfma4) to employ advanced surveillance tools to conduct targeted espionage against minority groups -- particularly the Uyghurs -- and against activists, journalists, and dissidents both within China and abroad. These tools are designed to quietly infiltrate devices, monitor communications, collect sensitive data, and allow for real-time tracking of individuals. In 2021, [Meta reported](https://about.fb.com/news/2021/03/taking-action-against-hackers-in-china/) that it disrupted a campaign by Earth Empusa which aimed to distribute [PluginPhantom](https://unit42.paloaltonetworks.com/unit42-pluginphantom-new-android-trojan-abuses-droidplugin-framework/) and [ActionSpy](https://www.trendmicro.com/en_us/research/20/f/new-android-spyware-actionspy-revealed-via-phishing-attacks-from-earth-empusa.html) to target Uyghurs living in China and abroad in Turkey, Kazakhstan, the United States, Syria, Australia, and Canada, among other countries. Earlier this year, Lookout Threat Lab detailed [BadBazaar](https://www.lookout.com/threat-intelligence/article/badbazaar-surveillanceware-apt15), a surveillance tool attributed to APT15, tracked by Microsoft as [Nylon Typhoon](https://security.microsoft.com/intel-profiles/6c01b907db21988312af12a7569e4b53eaaeffe1c82c5acd622972735b5c95dc), used to target Tibetan and Uyghur minorities in China. At least one variant of the tool, masquerading as an app called "TibetOne" was distributed via Telegram in a channel named, "tibetanphone." ## Recommendations Microsoft recommends the following mitigations to reduce the impact of this threat. - Only install apps from trusted sources and official stores, like the Google Play Store and Apple App Store. - Never click on unknown links received through ads, SMS messages, emails, or similar untrusted sources. Use mobile solutions such as [Microsoft Defender for Endpoint](https://learn.microsoft.com/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-android?view=o365-worldwide) on Android to detect malicious applications - Always keep Install unknown apps disabled on the Android device to prevent apps from being installed from unknown sources. - Avoid granting SMS permissions, notification listener access, or accessibility access to any applications without a strong unde | Malware Tool Threat Legislation Mobile | APT 15 | ★★★ | |
| 2024-11-25 12:11:18 | Weekly OSINT Highlights, 25 November 2024 (lien direct) | ## Snapshot Last week\'s OSINT reporting reveals a persistent focus on sophisticated attacks targeting diverse sectors, from critical infrastructure to financial services and national defense. Attack types ranged from ransomware and phishing to cyberespionage and supply chain attacks, often leveraging advanced malware like LODEINFO, Asyncshell, and DEEPDATA. Threat vectors predominantly exploit unpatched vulnerabilities, malvertising, supply chain attacks, and credential harvesting, with phishing and social engineering remaining prominent tactics. Notable actors include APT groups such as Gelsemium and BrazenBamboo, alongside cybercriminal collectives like Ignoble Scorpius and Water Barghest, targeting organizations across the US, Europe, and Asia. The findings underscore the growing complexity of cyber threats, emphasizing the need for proactive threat intelligence and robust cybersecurity defenses. ## Description 1. [Helldown Ransomware Campaign](https://sip.security.microsoft.com/intel-explorer/articles/2af97093): Sekoia researchers detailed the Helldown ransomware exploiting a Zyxel firewall vulnerability (CVE-2024-42057) to infiltrate corporate networks. Primarily targeting SMBs in the US and Europe, the attackers deploy Linux and Windows ransomware variants for data extortion and VM encryption. 1. [APT-K-47 Asyncshell Malware](https://sip.security.microsoft.com/intel-explorer/articles/aac966a9): Knownsec reported APT-K-47\'s use of Hajj-themed lures and malicious CHM files to distribute Asyncshell malware. The campaign, targeting South Asian countries, utilizes upgraded stealth tactics and evolving C2 infrastructure for long-term espionage. 1. [Linux Backdoors by Gelsemium](https://sip.security.microsoft.com/intel-explorer/articles/fc22b3bb): ESET researchers identified WolfsBane and FireWood backdoors used by the China-linked APT group Gelsemium for cyberespionage. These tools enable stealthy, persistent access to Linux systems, targeting sensitive data and emphasizing APT trends toward exploiting Linux environments. 1. [Lottie-Player Supply Chain Attack](https://sip.security.microsoft.com/intel-explorer/articles/86e2a9b6): ReversingLabs discovered a supply chain attack on the npm package @lottiefiles/lottie-player, compromising web3 wallets through malicious code. This incident highlights vulnerabilities in open-source ecosystems and the risk of compromised developer credentials. 1. [VMware Vulnerabilities Exploited](https://sip.security.microsoft.com/intel-explorer/articles/2eda898d): CISA added two VMware vulnerabilities, CVE-2024-38812 and CVE-2024-38813, to the Known Exploited Vulnerabilities Catalog. These flaws, involving heap overflow and privilege escalation, threaten vCenter Server and Cloud Foundation environments, emphasizing the need for immediate patching. 1. [Phishing Campaign Targeting Telecom and Financial Sectors](https://sip.security.microsoft.com/intel-explorer/articles/29972b65): EclecticIQ reported a phishing campaign using Google Docs and Weebly to bypass detection, targeting telecom and financial sectors. Threat actors employed tailored lures, fake MFA prompts, and SIM-swapping tactics to steal sensitive data. 1. [Lumma Stealer Distributed via Telegram](https://sip.security.microsoft.com/intel-explorer/articles/f250caee): McAfee researchers observed Lumma Stealer disguised as cracked software and distributed through Telegram channels. The malware targets users in India, the US, and Europe, stealing cryptocurrency and personal data via sophisticated injection techniques. 1. [Rise of ClickFix Social Engineering](https://sip.security.microsoft.com/intel-explorer/articles/67d03ba9): Proofpoint researchers identified ClickFix, a social engineering tactic that tricks users into executing malicious PowerShell commands, leading to malware infections such as AsyncRAT and DarkGate. Used by groups like TA571 and ClearFake, the method targets Ukrainian entities and employs malvertising, GitHub notifications, and CAPTCHA phishing lures. | Ransomware Malware Tool Vulnerability Threat Patching Industrial Prediction Cloud | APT 10 | ★★ | |
| 2024-11-19 21:54:53 | Spot the Difference: Earth Kasha\'s New LODEINFO Campaign And The Correlation Analysis With The APT10 Umbrella (lien direct) | #### Targeted Geolocations - Japan - India - Taiwan #### Targeted Industries - Government Agencies & Services - Information Technology - Transportation Systems - Aviation - Education ## Snapshot Trend Micro has released a report detailing the activities of Earth Kasha, a cyberespionage group known for leveraging the LODEINFO malware, primarily targeting entities in Japan. While some researchers suggest a connection to APT10, Trend Micro considers Earth Kasha a distinct entity within the "APT10 Umbrella," a term denoting groups linked to APT10\'s operational methods. This distinction arises from shared tactics and malware but insufficient direct evidence to conflate the two groups entirely. APT10 is tracked by Microsoft as [Purple Typhoon](https://security.microsoft.com/intel-profiles/e2ce50467bf60953a8838cf5d054caf7f89a0a7611f65e89a67e0142211a1745?tab=description&). ## Description Since early 2023, Earth Kasha has expanded its operations beyond Japan to include high-profile targets in Taiwan and India, focusing on government agencies and advanced technology industries. Their recent campaigns exhibit a strategic evolution, using vulnerabilities in public-facing enterprise applications, such as FortiOS/FortiProxy and Array AG, to gain initial access. Post-exploitation activities emphasize persistence, lateral movement, and credential theft, deploying backdoors like LODEINFO, NOOPDOOR, and the Cobalt Strike framework. The LODEINFO malware, central to Earth Kasha\'s campaigns, has undergone continuous development, with new versions observed in recent attacks. This malware is used alongside tools like MirrorStealer, which extracts credentials from browsers and email clients, and NOOPDOOR, a sophisticated backdoor with advanced evasion techniques. These tools enable extensive data theft and infiltration of victim networks. Comparative analysis highlights overlaps between Earth Kasha and other APT10-associated campaigns, particularly in tactics like exploiting SSL-VPN vulnerabilities and abusing legitimate tools for credential harvesting. However, toolsets differ, suggesting operational independence while potentially sharing resources or operators.Trend Micro\'s medium-confidence attribution of Earth Kasha underscores its ties to the broader APT10 network but stops short of confirming direct control. The group\'s distinct operational focus and adaptive methods indicate a specialized role within this cyber threat ecosystem. These findings highlight the complexity of attribution in modern cyber warfare and the evolving capabilities of threat actors like Earth Kasha. ## Microsoft Analysis and Additional OSINT Context The threat actor Microsoft tracks as [Purple Typhoon](https://security.microsoft.com/intel-profiles/e2ce50467bf60953a8838cf5d054caf7f89a0a7611f65e89a67e0142211a1745?tab=description&) is a long-running, targeted activity group which has had success in compromising targets from as early as 2009. This activity group has targeted various government entities and industry sectors such as engineering, critical manufacturing, communications infrastructure, and defense. Most of its activity has been spread across a wide geographic area; however, localized targeting using specific malware families has been observed, which suggests possible subgroups are contained within the wider Purple Typhoon group. ## Recommendations Microsoft recommends the following mitigations to reduce the impact of this threat. - Turn on [cloud-delivered protection](https://learn.microsoft.com/en-us/defender-endpoint/linux-preferences) in Microsoft Defender Antivirus or the equivalent for your antivirus product to cover rapidly evolving attacker tools and techniques. Cloud-based machine learning protections block a majority of new and unknown threats. - Run [EDR in block mode](https://learn.microsoft.com/microsoft-365/security/defender-endpoint/edr-in-block-mode?view=o365-worldwide?ocid=magicti_ta_learndoc) so tha | Malware Tool Vulnerability Threat Prediction | APT 10 | ★★ | |
| 2024-11-19 00:00:00 | Spot the Difference: Earth Kasha\\'s New LODEINFO Campaign And The Correlation Analysis With The APT10 Umbrella (lien direct) | LODEINFO is a malware used in attacks targeting mainly Japan since 2019. Trend Micro has been tracking the group as Earth Kasha. We have identified a new campaign connected to this group with significant updates to their strategy, tactics, and arsenals.
LODEINFO is a malware used in attacks targeting mainly Japan since 2019. Trend Micro has been tracking the group as Earth Kasha. We have identified a new campaign connected to this group with significant updates to their strategy, tactics, and arsenals. |
Malware Prediction | APT 10 | ★★ | |
| 2024-10-30 21:14:00 | Le groupe nord-coréen collabore avec les ransomwares de jeu dans une cyberattaque importante North Korean Group Collaborates with Play Ransomware in Significant Cyber Attack (lien direct) |
Les acteurs de menace en Corée du Nord ont été impliqués dans un incident récent qui a déployé une famille de ransomwares connue appelée Play, soulignant leurs motivations financières.
L'activité, observée entre mai et septembre 2024, a été attribuée à un acteur de menace suivi comme des Poissons nerveux, qui est également connu sous le nom d'Andariel, APT45, Darkseoul, Nickel Hyatt, Onyx Sleet (anciennement plutonium), opération Troy,
Threat actors in North Korea have been implicated in a recent incident that deployed a known ransomware family called Play, underscoring their financial motivations. The activity, observed between May and September 2024, has been attributed to a threat actor tracked as Jumpy Pisces, which is also known as Andariel, APT45, DarkSeoul, Nickel Hyatt, Onyx Sleet (formerly Plutonium), Operation Troy, |
Ransomware Threat | APT 15 APT 45 | ★★★ | |
| 2024-10-25 10:30:02 | The Windows Registry Adventure # 4: Hives and the Registry Mayout The Windows Registry Adventure #4: Hives and the registry layout (lien direct) |
Posted by Mateusz Jurczyk, Google Project Zero
To a normal user or even a Win32 application developer, the registry layout may seem simple: there are five root keys that we know from Regedit (abbreviated as HKCR, HKLM, HKCU, HKU and HKCC), and each of them contains a nested tree structure that serves a specific role in the system. But as one tries to dig deeper and understand how the registry really works internally, things may get confusing really fast. What are hives? How do they map or relate to the top-level keys? Why are some HKEY root keys pointing inside of other root keys (e.g. HKCU being located under HKU)? These are all valid questions, but they are difficult to answer without fully understanding the interactions between the user-mode Registry API and the kernel-mode registry interface, so let\'s start there.The high-level view
A simplified diagram of the execution flow taken when an application creates a registry key is shown below:
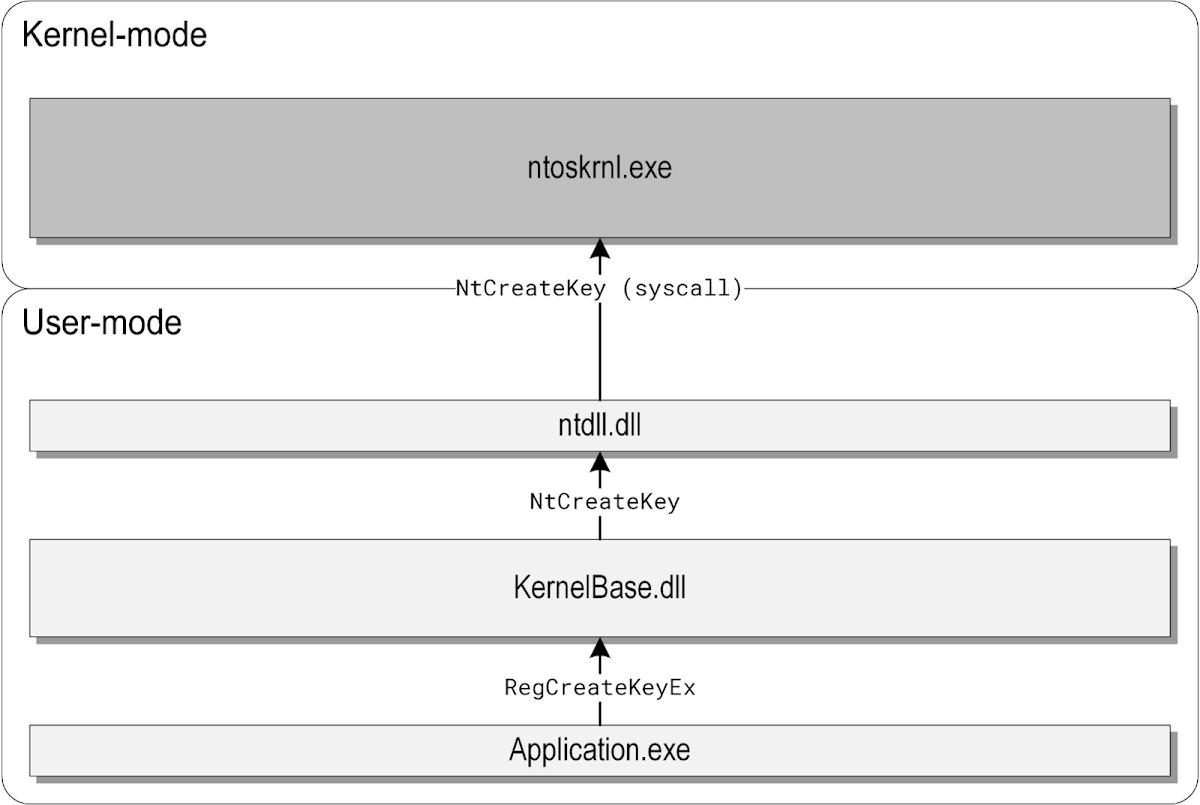 In this example, Application.exe is a desktop program calling the documented RegCreateKeyEx function, which is exported by KernelBase.dll. The KernelBase.dll library implements RegCreateKeyEx by translating the high-level API parameters passed by the caller (paths, flags, etc.) to internal ones understood by the kernel. It then invokes the NtCreateKey system call through a thin wrapper provided by ntdll.dll, and the execution finally reaches the Windows kernel, where all of the actual work on the internal registry representation is performed.
In this example, Application.exe is a desktop program calling the documented RegCreateKeyEx function, which is exported by KernelBase.dll. The KernelBase.dll library implements RegCreateKeyEx by translating the high-level API parameters passed by the caller (paths, flags, etc.) to internal ones understood by the kernel. It then invokes the NtCreateKey system call through a thin wrapper provided by ntdll.dll, and the execution finally reaches the Windows kernel, where all of the actual work on the internal registry representation is performed.
|
Tool Vulnerability Threat Legislation Technical | APT 17 | ★★★ | |
| 2024-10-14 21:26:20 | Faits saillants hebdomadaires, 14 octobre 2024 Weekly OSINT Highlights, 14 October 2024 (lien direct) |
## Snapshot Last week\'s OSINT reporting highlights a complex landscape of cyber threats with a focus on APT groups, sophisticated malware, and exploitation of vulnerabilities. Many attacks are espionage-focused, with China-aligned groups like CeranaKeeper, Iran\'s Hazel Sandstorm, and Russia\'s Midnight Blizzard (SVR) leveraging spearphishing and vulnerability exploitation for intelligence gathering. Ransomware also remains a dominant attack type, with threat actors leveraging double extortion tactics to maximize pressure on victims. A surge in reporting on malware distribution was also observed, including Lua-based malware in the education sector and Pronsis Loader delivering Lumma Stealer. Additionally, multiple reports detail widespread campaigns leveraging phishing, malvertising, and cryptomining, with key targets being government institutions, financial services, and critical infrastructure. Attackers employ diverse techniques such as DNS tunneling, USB-based malware, and exploit known vulnerabilities like EternalBlue (CVE-2017-0144) and FortiOS (CVE-2024-23113). ## Description Last week\'s OSINT reporting highlights a complex landscape of cyber threats with a focus on APT groups, sophisticated malware, and exploitation of vulnerabilities. Many attacks are espionage-focused, with China-aligned groups like CeranaKeeper, Iran\'s Hazel Sandstorm, and Russia\'s Midnight Blizzard (SVR) leveraging spearphishing and vulnerability exploitation for intelligence gathering. Ransomware also remains a dominant attack type, with threat actors leveraging double extortion tactics to maximize pressure on victims. A surge in reporting on malware distribution was also observed, including Lua-based malware in the education sector and Pronsis Loader delivering Lumma Stealer. Additionally, multiple reports detail widespread campaigns leveraging phishing, malvertising, and cryptomining, with key targets being government institutions, financial services, and critical infrastructure. Attackers employ diverse techniques such as DNS tunneling, USB-based malware, and exploit known vulnerabilities like EternalBlue (CVE-2017-0144) and FortiOS (CVE-2024-23113). 1. [CeranaKeeper Targets Thai Government](https://sip.security.microsoft.com/intel-explorer/articles/b3aa72ef): ESET uncovered a new China-aligned APT, CeranaKeeper, targeting government institutions in Thailand, using unique tools for data exfiltration via cloud services. The group adapts its malware for stealth and has been mistakenly linked to Mustang Panda due to some shared methods. 2. [Largest DDoS Attack Mitigated](https://sip.security.microsoft.com/intel-explorer/articles/74f06d55): Cloudflare mitigated the largest publicly disclosed DDoS attack, peaking at 3.8 Tbps, which targeted financial services, internet, and telecom organizations globally. Akamai also identified a critical vulnerability in CUPS servers, potentially creating a new vector for DDoS amplification. 3. [Cuckoo Spear\'s Sophisticated Tools](https://sip.security.microsoft.com/intel-explorer/articles/d47fc595): Cybereason exposed the Cuckoo Spear campaign by APT10, using NOOPLDR and NOOPDOOR to conduct espionage against Japanese industries and governments. These advanced tools employ anti-detection techniques and facilitate network pivoting for exfiltration. 4. [Mamba 2FA Phishing Campaign](https://sip.security.microsoft.com/intel-explorer/articles/bfcb80ed): Sekoia identified a phishing campaign using Mamba 2FA, a PhaaS platform, to steal credentials and session cookies from Microsoft services. Attackers exploited MFA weaknesses and used Telegram bots for data exfiltration. 5. [Golden Jackal\'s Air-Gapped System Attacks](https://sip.security.microsoft.com/intel-explorer/articles/f0234a25): ESET researchers discovered Golden Jackal targeting European government organizations with tools designed to breach air-gapped systems. The group uses USB-based malware for espionage and data exfiltration. 6. [Awaken Likho Targets Russian Agencies](https://sip.security.microsoft.com/in | Ransomware Malware Tool Vulnerability Threat Patching Industrial Medical Cloud | APT 29 APT 10 GoldenJackal | ★★ | |
| 2024-10-07 19:22:45 | CUCKOO SPEAR PARTIE 2: acteur de menace Arsenal CUCKOO SPEAR Part 2: Threat Actor Arsenal (lien direct) |
## Snapshot Cybereason Security Services Team uncovered sophisticated capabilities of the Cuckoo Spear tools, NOOPLDR and NOOPDOOR. ## Description NOOPLDR variants, including NOOPLDR-DLL and NOOPLDR-C#, establish persistence by registering as services and injecting shellcode into system processes. NOOPLDR-DLL uses code obfuscation, dynamic custom syscalls, and modified legitimate DLLs to evade detection, while NOOPLDR-C# employs heavy obfuscation, time stomping, and executes C# code from XML files using msbuild.exe. Both loaders retrieve and decrypt shellcode from the registry or a .dat file, using AES encryption with keys derived from the machine\'s unique identifiers. NOOPDOOR malware, associated with NOOPLDR, has client and server components designed for stealth and persistence. The client-side features API hashing, anti-debugging, a domain generation algorithm (DGA), and a custom TCP protocol for data exfiltration. The server-side is capable of modifying firewall rules and executing commands for network pivoting. The campaign has ties to the well-known APT10 group, showing clear links between multiple incidents while revealing new tools and strategies employed by the attackers. Cuckoo Spear mainly targeted Japanese companies in the manufacturing, political, and industrial sectors, with cyber espionage as its primary goal. ## Microsoft Analysis Researchers at Cybereason assess the threat actor to be APT10. Microsoft tracks APT10 as [Purple Typhoon](https://security.microsoft.com/intel-profiles/e2ce50467bf60953a8838cf5d054caf7f89a0a7611f65e89a67e0142211a1745) Purple Typhoon (POTASSIUM), the activity group also known as APT 10, Stone Panda, Cloud Hopper, Red Apollo, or menuPass, has been reported to be responsible for global intrusion campaigns from 2006. These campaigns aimed to steal intellectual property and confidential business information from defense contractors and government agencies in the United States. The group was also observed launching attacks against a diverse set of other verticals, including communications, energy, space aviation. Notably, the group targeted managed service providers (MSPs) with presence in Brazil, Canada, Finland, France, Germany, India, Japan, Sweden, Switzerland, United Arab Emirates, and the United Kingdom. Compromising MSPs provided Purple Typhoon a launchpad for infiltrating organizations whose IT infrastructures and/or end-user systems are managed by these MSPs. Known to initially compromise targets via spear-phishing emails that deliver malicious payloads in the form of remote access trojans (RATs), the group steals administrator credentials to move laterally across target systems, maintain persistence, and exfiltrate high-value information. The malicious payloads typically utilized by Purple Typhoon include three main RATs called REDLEAVES, UPPERCUT and CHCHES. On December 17, 2018, the US government indicted two members of Purple Typhoon. On January 2, 2019, the Federal Bureau of Investigation shared indicators of compromise (IOCs) to aid in customer protection. Using these IOCs, which the security community further corroborated, along with Microsoft\'s own IOCs and telemetry, we have put in place enhanced detection mechanisms that can help guard against possible attacks coming from this group. ## Recommendations Apply these mitigations to reduce the impact of this threat. - Apply security updates to vulnerable VPN solutions. - Require multi-factor authentication (MFA) for local device access, RDP access, and remote connections through VPN. Use password-less solutions like [Microsoft Authenticator](https://www.microsoft.com/en-us/account/authenticator/). For further guidance, read about: - [Set up multi-factor authentication for Office 365](https://docs.microsoft.com/en-us/office365/admin/security-and-compliance/set-up-multi-factor-authentication?view=o365-worldwide) - [Use two-step verification with consumer accounts](https://support.microsoft.com/en-us/help/ | Malware Tool Threat Industrial Cloud | APT 10 | ★★★ | |
| 2024-09-23 16:05:03 | Faits saillants hebdomadaires OSINT, 23 septembre 2024 Weekly OSINT Highlights, 23 September 2024 (lien direct) |
## Snapshot Last week\'s OSINT reporting reveals a landscape dominated by complex, multi-layered attacks targeting critical infrastructure, financial sectors, and cloud environments. Nation-state actors, like China\'s Flax Typhoon and Iran\'s UNC1860, leverage botnets, IoT exploits, and sophisticated backdoors to infiltrate government, military, and industrial targets. The emergence of groups such as Earth Baxia highlights the continued exploitation of vulnerabilities like CVE-2024-36401 and spear-phishing tactics in the Asia-Pacific region. Meanwhile, cybercriminals, including SCATTERED SPIDER (Octo Tempest) and those behind the Lumma Stealer campaigns, utilize social engineering, fake CAPTCHA pages, and WebDAV for malware distribution to evade detection and deploy ransomware and infostealers. Exploits underscore the increasing use of open-source vulnerabilities, with attackers targeting a diverse range of industries, including IT, telecommunications, and finance. These attacks highlight evolving tactics, advanced persistence mechanisms, and stealthy malware being used to target sensitive data globally. ## Description 1. [Raptor Train Botnet Operated by Flax Typhoon](https://sip.security.microsoft.com/intel-explorer/articles/9118dcb6): Black Lotus Labs uncovered the massive Raptor Train botnet, operated by Chinese nation-state group Flax Typhoon. This IoT botnet, consisting of compromised routers, cameras, and other devices, has targeted U.S. and Taiwanese entities across sectors like military and government, making it one of the largest Chinese state-sponsored botnets to date. 2. [Exploitation of GeoServer Vulnerability (CVE-2024-36401)](https://sip.security.microsoft.com/intel-explorer/articles/e7a82171): Threat actors are exploiting a remote code execution (RCE) vulnerability in GeoServer to deliver malware such as GOREVERSE, SideWalk, and CoinMiner. Campaigns have targeted IT, telecom, and government sectors across multiple countries, using sophisticated backdoors and botnets to compromise systems. 3. [WebDAV Used to Distribute Emmenthal Loader](https://sip.security.microsoft.com/intel-explorer/articles/6dec4139): Cybercriminals are using WebDAV servers to distribute the Emmenthal loader (aka PeakLight), which delivers infostealers via malicious .lnk files. This infrastructure is likely part of a larger cybercrime operation offering infrastructure as a service (IaaS), and its stealthy, memory-only execution technique poses a significant threat to global cybersecurity. 4. [Iran\'s UNC1860 Targets Middle Eastern Networks](https://sip.security.microsoft.com/intel-explorer/articles/e882507d): Mandiant assesses UNC1860 is likely linked to Iran\'s Ministry of Intelligence and Security (MOIS) and focuses on persistent access to government and telecom organizations in the Middle East. The group leverages sophisticated tools, such as TEMPLEPLAY and VIROGREEN, and exploits internet-facing servers to evade detection. 5. [Cuckoo Spear Campaign Tied to APT10](https://sip.security.microsoft.com/intel-explorer/articles/8f34c36c): Cybereason discovered the "Cuckoo Spear" campaign, attributed to APT10, targeting Japanese manufacturing and political sectors. The attackers used advanced tools like LODEINFO and NOOPLDR to maintain long-term espionage operations, employing tactics like DLL side-loading and phishing. 6. [PondRAT Campaign Linked to North Korean Group](https://sip.security.microsoft.com/intel-explorer/articles/906408c8): Unit 42 identified the PondRAT campaign, attributed to Gleaming Pisces (Citrine Sleet), which targets Linux and macOS systems through infected PyPI packages. The goal is to compromise the supply chain, particularly in the cryptocurrency sector, by delivering backdoor malware to developers\' machines. 7. [Phishing Campaign Distributes Lumma Stealer](https://sip.security.microsoft.com/intel-explorer/articles/3cb5d189): A phishing campaign abuses GitHub repositories by filing false security vulnerability reports to lure users into downloading the Lumma Stealer malware. The | Ransomware Malware Tool Vulnerability Threat Mobile Industrial Prediction Cloud Conference | APT 10 | ★★ | |
| 2024-09-20 13:20:01 | CUCKOO SPEAR Part 1: Analyzing NOOPDOOR from an IR Perspective (lien direct) | #### Géolocations ciblées - Japon #### Industries ciblées - des groupes politiques et autres - Autres entités commerciales - Installations commerciales ## Instantané Des chercheurs de Cybearon ont découvert une campagne de menaces au niveau de l'État-nation nommée "Cuckoo Spear" qui a persisté sur les réseaux victimes pendant plusieurs années en utilisant des techniques sophistiquées. ## Description La campagne a des liens avec le groupe APT10 bien connu, montrant des liens clairs entre plusieurs incidents tout en révélant de nouveaux outils et stratégies utilisés par les attaquants.Cuckoo Spear a principalement ciblé les entreprises japonaises dans les secteurs de la fabrication, des politiques et industriels, avec le cyber-espionnage comme objectif principal. Les attaquants ont utilisé des logiciels malveillants furtifs, y compris une version mise à jour de Lodeinfo, un outil précédemment associé à l'APT10.Les chercheurs ont également identifié deux nouveaux composants de logiciels malveillants: NOOPLDR, une porte dérobée de persistance, et NOOPDOOR, qui a utilisé un algorithme de génération de domaine (DGA) pour les communications et le relais de réseau interne.Certaines victimes ont accueilli sans le savoir ces acteurs au sein de leurs systèmes jusqu'à deux à trois ans. L'accès initial aux réseaux cibles a été principalement réalisé grâce à des attaques de phishing, bien que la cyber-saison ait également observé que l'exploitation d'applications accessibles au public ait également été observée.Les attaquants ont utilisé des techniques avancées telles que le chargement latéral DLL et l'exploitation MSBuild pour maintenir la persistance. L'infrastructure derrière Cuckoo Spear a exploité les services DNS dynamiques et les domaines enregistrés pour gérerleur campagne.[Strike Cobalt] (https://security.microsoft.com/intel-profiles/fd8511c1d61e93d39411acf36a31130a6795efe186497098fe0c6f2ccfb920fc),Lodeinfo, NOOPLDR et NOOPDOOR ont tous joué des rôles dans le maintien de la persistance et l'activation du mouvement latéral à travers les environnements compromis, permettant aux attaquants de rester non détectés lors de l'exécution d'espionnage à long terme. ## Recommandations Appliquez ces atténuations pour réduire l'impact de cette menace.Vérifiez la carte de recommandations pour l'état de déploiement des atténuations surveillées. - Appliquer des mises à jour de sécurité aux solutions VPN vulnérables. - Exiger l'authentification multi-facteurs (MFA) pour l'accès des périphériques locaux, l'accès RDP et les connexions distantes via VPN.Utilisez des solutions sans mot de passe comme [Microsoft Authenticator] (https://www.microsoft.com/en-us/account/authenticator/).Pour plus de conseils, lisez sur: - [Configurer l'authentification multi-facteurs pour Office 365] (https://docs.microsoft.com/en-us/office365/admin/security-and-compliance/set-up-multi-factor-authentication?view=O365-mondial) - [Utilisez une vérification en deux étapes avec les comptes de consommation] (https://support.microsoft.com/en-us/help/12408/microsoft-account-how-to-use-setwo-tep-verrification) - Utilisez le pare-feu Microsoft Defender et votre pare-feu réseau pour empêcher la communication des appels de procédure distante (RPC) et un bloc de messages (SMB) entre les points de terminaison dans la mesure du possible.Cela limite le mouvement latéral ainsi que d'autres activités d'attaque. - Allumez la protection livrée par le cloud et la soumission automatique des échantillons sur Microsoft Defender Antivirus.Ces capacités utilisent l'IA et l'apprentissage automatique pour identifier et arrêter rapidement les menaces nouvelles et inconnues. - Pratiquez le principe du moindre privile et maintenez l'hygiène des références.Évitez l'utilisation des comptes de service au niveau de l'administration à l'échelle du domaine.Restreindre les privilèges administr | Malware Tool Threat Industrial Commercial | APT 10 | ★★ | |
| 2024-09-07 17:31:39 | 2024-08-30 échantillon de ransomware ESXi Cicada 2024-08-30 Cicada ESXi Ransomware Sample (lien direct) |
& nbsp;  2024 -08 -30 truesec : disséquant la cigale (ransomware ) & nbsp; ESXi ransomware cicada3301, un groupe de ransomware d'abord d'aborddétecté en juin 2024, semble être une version rebaptisée ou dérivée du groupe Ransomware AlphV, utilisant un modèle Ransomware-as-a-Service (RAAS).Le ransomware, écrit en rouille, cible les environnements Windows et Linux / Esxi, en utilisant Chacha20 pour le cryptage.L'analyse technique révèle plusieurs similitudes clés avec AlPHV: les deux utilisent des structures de commande presque identiques pour arrêter les machines virtuelles et supprimer des instantanés, et partager une convention de dénomination de fichiers similaire.Le binaire de Ransomware \\ est un fichier ELF, avec son origine de rouille confirmée par des références de chaîne et une enquête de la section .comment. Les paramètres clés incluent Sleep , qui retarde l'exécution de Ransomware \\, et ui , qui affiche la progression du chiffrement à l'écran.Le paramètre clé est crucial pour le déchiffrement;S'il n'est pas fourni ou incorrect, le ransomware cessera de fonctionner.La fonction principale, linux_enc , démarre le processus de chiffrement en générant une clé aléatoire à l'aide de osrng .Les fichiers supérieurs à 100 Mo sont chiffrés en pièces, tandis que les fichiers plus petits sont chiffrés entièrement à l'aide de Chacha20.La clé chacha20 est ensuite sécurisée avec une clé publique RSA et ajoutée, ainsi qu'une extension de fichier spécifique, à la fin du fichier crypté. L'accès initial semble être facilité par le botnet Brutus, avec des acteurs de menace utilisant des informations d'identification volées ou forcées pour accéder via ScreenConnect.L'adresse IP associée à cette attaque est liée au botnet Brutus, ce qui augmente la possibilité d'une connexion directe entre les opérateurs de botnet et CICADA3301.Le ransomware dispose également d'une routine de vérification de décryptage, où une note de ransomware codée et cryptée stockée dans le binaire est décryptée à l'aide de la clé fournie, validant le décryptage correct. Télécharger Télécharger.(Envoyez-moi un e-mail si vous avez besoin du schéma de mot de passe) 2024 -08 -30 truesec : disséquant la cigale (ransomware ) & nbsp; ESXi ransomware cicada3301, un groupe de ransomware d'abord d'aborddétecté en juin 2024, semble être une version rebaptisée ou dérivée du groupe Ransomware AlphV, utilisant un modèle Ransomware-as-a-Service (RAAS).Le ransomware, écrit en rouille, cible les environnements Windows et Linux / Esxi, en utilisant Chacha20 pour le cryptage.L'analyse technique révèle plusieurs similitudes clés avec AlPHV: les deux utilisent des structures de commande presque identiques pour arrêter les machines virtuelles et supprimer des instantanés, et partager une convention de dénomination de fichiers similaire.Le binaire de Ransomware \\ est un fichier ELF, avec son origine de rouille confirmée par des références de chaîne et une enquête de la section .comment. Les paramètres clés incluent Sleep , qui retarde l'exécution de Ransomware \\, et ui , qui affiche la progression du chiffrement à l'écran.Le paramètre clé est crucial pour le déchiffrement;S'il n'est pas fourni ou incorrect, le ransomware cessera de fonctionner.La fonction principale, linux_enc , démarre le processus de chiffrement en générant une clé aléatoire à l'aide de osrng .Les fichiers supérieurs à 100 Mo sont chiffrés en pièces, tandis que les fichiers plus petits sont chiffrés entièrement à l'aide de Chacha20.La clé chacha20 est ensuite sécurisée avec une clé publique RSA et ajoutée, ainsi qu'une extension de fichier spécifique, à la fin du fichier crypté. L'accès initial semble être facilité par le botnet Brutus, avec des acteurs de menace utilisant des informations d'identification volées ou forcées pour accéder via ScreenConnect.L'adresse IP associée à cette attaque est liée au botnet Brutus, ce qui augmente la possibilité d'une connexion directe entre les opérateurs de botnet et CICADA3301.Le ransomware dispose également d'une routine de vérification de décryptage, où une note de ransomware codée et cryptée stockée dans le binaire est décryptée à l'aide de la clé fournie, validant le décryptage correct. Télécharger Télécharger.(Envoyez-moi un e-mail si vous avez besoin du schéma de mot de passe) |
Ransomware Threat Technical | APT 10 | ★★ | |
| 2024-09-05 09:54:06 | Ransomware Cicada - Ce que vous devez savoir Cicada Ransomware - What You Need To Know (lien direct) |
Qu'est-ce que le ransomware Cicada?La cigale (également connue sous le nom de Cicada3301) est un ransomware sophistiqué écrit en rouille qui a réclamé plus de 20 victimes depuis sa découverte en juin 2024. Pourquoi le ransomware est-il appelé cigale?Les criminels derrière la cigale semblent l'avoir nommé d'après les mystérieux puzzles Cicada 3301 publiés sur Internet entre 2012 et 2014, apparemment pour recruter des individus très intelligents.Bien sûr, il n'y a aucune raison de croire que le ransomware est de quelque manière que ce soit lié aux puzzles énigmatiques qui sont apparus une décennie avant lui - autre que par le nom.Assez juste...
What is the Cicada ransomware? Cicada (also known as Cicada3301) is sophisticated ransomware written in Rust that has claimed more than 20 victims since its discovery in June 2024. Why is the ransomware called Cicada? The criminals behind Cicada appear to have named it after the mysterious Cicada 3301 puzzles posted on the internet between 2012 and 2014, seemingly to recruit highly intelligent individuals. Of course, there is no reason to believe that the ransomware is in any fashion related to the enigmatic puzzles that appeared a decade before it - other than through the name. Fair enough... |
Ransomware | APT 10 | ★★ | |
| 2024-09-04 14:29:06 | Le ransomware CICADA peut être un rebrand et une mise à niveau de BlackCat / AlphV Cicada ransomware may be a BlackCat/ALPHV rebrand and upgrade (lien direct) |
Les chercheurs trouvent de nombreuses similitudes, et de nouvelles personnalisations désagréables telles que les informations d'identification des utilisateurs compromises intégrées Le ransomware Cicada3301, qui a réclamé au moins 20 victimes depuis qu'elle a été repérée en juin, partage "des similitudes frappantes" avec leRansomware notoire Blackcat, selon les chercheurs en sécurité de la tenue de fin de terminaison de tenue de tenue israélienne Morphisec.…
Researchers find many similarities, and nasty new customizations such as embedded compromised user credentials The Cicada3301 ransomware, which has claimed at least 20 victims since it was spotted in June, shares "striking similarities" with the notorious BlackCat ransomware, according to security researchers at Israeli outfit endpoint security outfit Morphisec.… |
Ransomware | APT 10 | ★★ | |
| 2024-07-25 19:38:00 | Les pirates nord-coréens passent du cyber-espionnage aux attaques de ransomwares North Korean Hackers Shift from Cyber Espionage to Ransomware Attacks (lien direct) |
Un acteur de menace en Corée du Nord, connu pour ses opérations de cyber-espionnage, s'est progressivement étendu à des attaques motivées financièrement qui impliquent le déploiement de ransomwares, le distinguant des autres groupes de piratage de l'État-nation liés au pays.
Mandiant appartenant à Google suit le cluster d'activités sous un nouveau surnom APT45, qui chevauche des noms tels que Andariel, Nickel Hyatt,
A North Korea-linked threat actor known for its cyber espionage operations has gradually expanded into financially-motivated attacks that involve the deployment of ransomware, setting it apart from other nation-state hacking groups linked to the country. Google-owned Mandiant is tracking the activity cluster under a new moniker APT45, which overlaps with names such as Andariel, Nickel Hyatt, |
Ransomware Threat | APT 15 | ★★★ | |
| 2024-07-17 14:17:00 | APT17 lié à la Chine cible les sociétés italiennes avec 9002 logiciels malveillants de rat China-linked APT17 Targets Italian Companies with 9002 RAT Malware (lien direct) |
Un acteur de menace lié à la Chine appelée APT17 a été observé ciblant les entreprises italiennes et les entités gouvernementales en utilisant une variante d'un logiciel malveillant connu appelé 9002 rat.
Les deux attaques ciblées ont eu lieu le 24 juin et le 2 juillet 2024, a déclaré TG Soft, la société italienne de cybersécurité, a déclaré dans une analyse publiée la semaine dernière.
"La première campagne le 24 juin 2024 a utilisé un document de bureau, tandis que le second
A China-linked threat actor called APT17 has been observed targeting Italian companies and government entities using a variant of a known malware referred to as 9002 RAT. The two targeted attacks took place on June 24 and July 2, 2024, Italian cybersecurity company TG Soft said in an analysis published last week. "The first campaign on June 24, 2024 used an Office document, while the second |
Malware Threat | APT 17 | ★★★★ | |
| 2024-06-26 00:00:00 | Attaquants dans le profil: Menupass et Alphv / Blackcat Attackers in Profile: menuPass and ALPHV/BlackCat (lien direct) |
Pour tester l'efficacité des services gérés comme notre offre de détection et de réponse à la micro-géré, Mitre Encenuity ™ a combiné les outils, les techniques et les pratiques de deux méchants acteurs mondiaux: Menupass et alphv / blackcat.Ce blog raconte pourquoi ils ont été choisis et ce qui en fait des menaces à compter.
To test the effectiveness of managed services like our Trend Micro managed detection and response offering, MITRE Engenuity™ combined the tools, techniques, and practices of two globally notorious bad actors: menuPass and ALPHV/BlackCat. This blog tells the story of why they were chosen and what makes them threats to be reckoned with. |
Tool Prediction | APT 10 | ★★★ | |
| 2024-06-18 05:00:00 | BlackBerry efficace contre Blackcat / AlphV et Menupass dans les évaluations de Mitre ATT & CK BlackBerry Effective Against BlackCat/ALPHV and menuPass in MITRE ATT&CK Evaluations (lien direct) |
BlackBerry a récemment participé aux évaluations d'atténuité d'Engenuity ATT & CK pour les services gérés.Cette série de tests indépendants a émulé les groupes BlackCat / AlphV et Menupass, soulignant la nécessité de solutions de sécurité robustes et adaptatives face à des adversaires sophistiqués.
BlackBerry recently participated in the MITRE Engenuity ATT&CK Evaluations for Managed Services. This round of independent testing emulated the BlackCat/ALPHV and menuPass threat groups, highlighting the need for robust, adaptive security solutions in the face of sophisticated adversaries. |
Threat | APT 10 | ★★ | |
| 2024-06-18 00:00:00 | Pas juste un autre score de 100%: Mitre Engeniuty ATT & CK Not Just Another 100% Score: MITRE ENGENIUTY ATT&CK (lien direct) |
Les dernières évaluations d'atténuité à mitres ATT & AMP; CK ont opposé les services de détection et de réponse gérés (MDR) de premier plan aux menaces modélisées sur les groupes adversaires MenuPass et BlackCat / AlphV.Trend Micro a atteint une détection de 100% entre les 15 étapes d'attaque majeures avec un taux de 86% exploitable pour ces étapes - équilibrant les détections et priorités commerciales, y compris la continuité opérationnelle et les perturbations minimisées.
The latest MITRE Engenuity ATT&CK Evaluations pitted leading managed detection and response (MDR) services against threats modeled on the menuPass and BlackCat/AlphV adversary groups. Trend Micro achieved 100% detection across all 15 major attack steps with an 86% actionable rate for those steps- balancing detections and business priorities including operational continuity and minimized disruption. |
Prediction | APT 10 | ★★ | |
| 2024-06-05 14:00:00 | Phishing pour l'or: cyber-menaces auxquelles sont confrontés les Jeux olympiques de Paris 2024 Phishing for Gold: Cyber Threats Facing the 2024 Paris Olympics (lien direct) |
Written by: Michelle Cantos, Jamie Collier
Executive Summary Mandiant assesses with high confidence that the Paris Olympics faces an elevated risk of cyber threat activity, including cyber espionage, disruptive and destructive operations, financially-motivated activity, hacktivism, and information operations. Olympics-related cyber threats could realistically impact various targets including event organizers and sponsors, ticketing systems, Paris infrastructure, and athletes and spectators traveling to the event. Mandiant assesses with high confidence that Russian threat groups pose the highest risk to the Olympics. While China, Iran, and North Korea state sponsored actors also pose a moderate to low risk. To reduce the risk of cyber threats associated with the Paris Olympics, organizations should update their threat profiles, conduct security awareness training, and consider travel-related cyber risks. The security community is better prepared for the cyber threats facing the Paris Olympics than it has been for previous Games, thanks to the insights gained from past events. While some entities may face unfamiliar state-sponsored threats, many of the cybercriminal threats will be familiar. While the technical disruption caused by hacktivism and information operations is often temporary, these operations can have an outsized impact during high-profile events with a global audience. Introduction The 2024 Summer Olympics taking place in Paris, France between July and August creates opportunities for a range of cyber threat actors to pursue profit, notoriety, and intelligence. For organizations involved in the event, understanding relevant threats is key to developing a resilient security posture. Defenders should prepare against a variety of threats that will likely be interested in targeting the Games for different reasons: Cyber espionage groups are likely to target the 2024 Olympics for information gathering purposes, due to the volume of government officials and senior decision makers attending. Disruptive and destructive operations could potentially target the Games to cause negative psychological effects and reputational damage. This type of activity could take the form of website defacements, distributed denial of service (DDoS) attacks, the deployment of wiper malware, and operational technology (OT) targeting. As a high profile, large-scale sporting event with a global audience, the Olympics represents an ideal stage for such operations given that the impact of any disruption would be significantly magnified. Information operations will likely leverage interest in the Olympics to spread narratives and disinformation to target audiences. In some cases, threat actors may leverage disruptive and destructive attacks to amplify the spread of particular narratives in hybrid operations. Financially-motivated actors are likely to target the Olympics in v |
Ransomware Malware Threat Studies Mobile Cloud Technical | APT 15 APT 31 APT 42 | ★★ | |
| 2024-06-03 11:06:54 | Voir comme une structure de données Seeing Like a Data Structure (lien direct) |
La technologie était autrefois un outil & # 8212; et un petit à cela & # 8212; utilisé pour Amplifiez l'intention humaine de l'intention humaineet capacité .C'était l'histoire de la révolution industrielle: nous pouvions contrôler la nature et construire de grandes sociétés humaines complexes, et plus nous employons et maîtrisons la technologie, mieux les choses sont devenues.Nous ne vivons plus dans ce monde.Non seulement la technologie est enchevêtrée avec la structure de la société, mais nous ne pouvons plus voir le monde qui nous entoure sans lui.La séparation a disparu et le contrôle que nous pensions que nous avions autrefois révélé comme un mirage.Nous & # 8217; re dans une période de transition de l'histoire en ce moment ...
Technology was once simply a tool—and a small one at that—used to amplify human intent and capacity. That was the story of the industrial revolution: we could control nature and build large, complex human societies, and the more we employed and mastered technology, the better things got. We don’t live in that world anymore. Not only has technology become entangled with the structure of society, but we also can no longer see the world around us without it. The separation is gone, and the control we thought we once had has revealed itself as a mirage. We’re in a transitional period of history right now... |
Industrial | APT 15 | ★★★ | |
| 2024-05-25 03:34:42 | La NASA trouve plus de problèmes avec Starliner de Boeing \\, mais le lancement de l'équipage se déroule pour le 1er juin NASA finds more issues with Boeing\\'s Starliner, but crew launch set for June 1 (lien direct) |
La réparation de la fuite d'hélium retarderait le vol d'essai de l'équipage Starliner pendant des mois.
Fixing the helium leak would delay Starliner crew test flight for months. |
APT 17 | ★★ | ||
| 2024-05-22 15:45:12 | La capsule de calamité de Boeing \\ a glisser la date de lancement dans le futur dans le futur Boeing\\'s Calamity Capsule launch date slides into the future (lien direct) |
Starliner ou Padstayer? Boeing \'s Starliner, alias The Calamity Capsule, a subi un autre revers après que la date de lancement du 25 mai espérée ait été abandonnée alors que les ingénieurs travaillent pour faire face à une héliumfuite dans le système de propulsion du vaisseau spatial.…
Starliner or Padstayer? Boeing\'s Starliner, aka the Calamity Capsule, has suffered another setback after a hoped-for May 25 launch date has been dropped as engineers work to deal with a helium leak in the spacecraft\'s propulsion system.… |
APT 17 | ★★★ | ||
| 2024-05-22 14:00:00 | Extinction de l'IOC?Les acteurs de cyber-espionnage de Chine-Nexus utilisent des réseaux orbes pour augmenter les coûts des défenseurs IOC Extinction? China-Nexus Cyber Espionage Actors Use ORB Networks to Raise Cost on Defenders (lien direct) |
Written by: Michael Raggi
Mandiant Intelligence is tracking a growing trend among China-nexus cyber espionage operations where advanced persistent threat (APT) actors utilize proxy networks known as “ORB networks” (operational relay box networks) to gain an advantage when conducting espionage operations. ORB networks are akin to botnets and are made up of virtual private servers (VPS), as well as compromised Internet of Things (IoT) devices, smart devices, and routers that are often end of life or unsupported by their manufacturers. Building networks of compromised devices allows ORB network administrators to easily grow the size of their ORB network with little effort and create a constantly evolving mesh network that can be used to conceal espionage operations. By using these mesh networks to conduct espionage operations, actors can disguise external traffic between command and control (C2) infrastructure and victim environments including vulnerable edge devices that are being exploited via zero-day vulnerabilities. These networks often use both rented VPS nodes in combination with malware designed to target routers so they can grow the number of devices capable of relaying traffic within compromised networks. Mandiant assesses with moderate confidence that this is an effort to raise the cost of defending an enterprise\'s network and shift the advantage toward espionage operators by evading detection and complicating attribution. Mandiant believes that if network defenders can shift the current enterprise defense paradigm away from treating adversary infrastructure like indicators of compromise (IOCs) and instead toward tracking ORB networks like evolving entities akin to APT groups, enterprises can contend with the rising challenge of ORB networks in the threat landscape. IOC Extinction and the Rise of ORB Networks The cybersecurity industry has reported on the APT practice of ORB network usage in the past as well as on the functional implementation of these networks. Less discussed are the implications of broad ORB network usage by a multitude of China-nexus espionage actors, which has become more common over recent years. The following are three key points and paradigm shifting implications about ORB networks that require enterprise network defenders to adapt the way they think about China-nexus espionage actors: ORB networks undermine the idea of “Actor-Controlled Infrastructure”: ORB networks are infrastructure networks administered by independent entities, contractors, or administrators within the People\'s Republic of China (PRC). They are not controlled by a single APT actor. ORB networks create a network interface, administer a network of compromised nodes, and contract access to those networks to multiple APT actors that will use the ORB networks to carry out their own distinct espionage and reconnaissance. These networks are not controlled by APT actors using them, but rather are temporarily used by these APT actors often to deploy custom tooling more conventionally attributable to known China-nexus adversaries. ORB network infrastructure has a short lifesp |
Malware Tool Vulnerability Threat Prediction Cloud Commercial | APT 15 APT 5 APT 31 | ★★★ | |
| 2024-05-14 19:47:22 | Boeing dépasse une petite fuite d'hélium sur le vaisseau spatial Starliner Boeing is troubleshooting a small helium leak on the Starliner spacecraft (lien direct) |
Le premier lancement des astronautes à bord de la capsule Starliner de Boeing \\ est maintenant fixé pour le 21 mai.
The first launch of astronauts aboard Boeing\'s Starliner capsule is now set for May 21. |
APT 17 | ★★★ | ||
| 2024-03-14 15:00:00 | La violation de données de l'agence d'emploi française pourrait affecter 43 millions de personnes French Employment Agency Data Breach Could Affect 43 Million People (lien direct) |
L'agence d'emploi de la France a subi une violation massive, exposant les données des utilisateurs qui se sont inscrits au cours des 20 dernières années
France\'s employment agency suffered a massive breach, exposing the data of users who registered over the past 20 years |
Data Breach | APT 19 | ★★★ | |
| 2024-02-13 12:07:03 | Molly White Reviews Blockchain Livre Molly White Reviews Blockchain Book (lien direct) |
Molly White & # 8212; of & # 8220; web3 va bien & # 8221;FAME & # 8212; critiques Chris Dixon & # 8217; s Blockchain Solutions Livre: lisez écrire propre :
En fait, tout au long du livre, Dixon ne parvient pas à identifier un projet de blockchain qui a réussi à fournir un service non spécifique à tout type.Le plus proche qu'il arrive, c'est quand il parle de la façon dont & # 8220; Pendant des décennies, les technologues ont rêvé de construire un fournisseur d'accès Internet de base & # 8221;.Il décrit un projet qui est obtenu plus loin que quiconque & # 8221;: Helium.Il est raisonnable, tant que vous ignorez le fait que l'hélium fournissait à Lorawan, pas Internet, qu'au moment où il écrivait son livre, les hotspots d'hélium avaient depuis longtemps passé la phase où ils pourraient générer encore assez de jetons pour leurs opérateurs pour leurs opérateursPour se casser même, et que le réseau s'arrête dans environ 1 150 $ de frais d'utilisation par mois malgré le fait que l'entreprise soit évaluée à 1,2 milliard de dollars.Oh, et que l'entreprise avait largement menti au public sur ses supposés clients de renom, et que ses dirigeants ont été accusés d'avoir thésaurigeant le jeton du projet pour s'enrichir.Mais bon, A16Z a coulé des millions d'hélium (un fait que Dixon ne mentionne jamais), donc aussi bien essayer de stimuler un nouvel intérêt! ...
Molly White—of “Web3 is Going Just Great” fame—reviews Chris Dixon’s blockchain solutions book: Read Write Own: In fact, throughout the entire book, Dixon fails to identify a single blockchain project that has successfully provided a non-speculative service at any kind of scale. The closest he ever comes is when he speaks of how “for decades, technologists have dreamed of building a grassroots internet access provider”. He describes one project that “got further than anyone else”: Helium. He’s right, as long as you ignore the fact that Helium was providing LoRaWAN, not Internet, that by the time he was writing his book Helium hotspots had long since passed the phase where they might generate even enough tokens for their operators to merely break even, and that the network was pulling in somewhere around $1,150 in usage fees a month despite the company being valued at $1.2 billion. Oh, and that the company had widely lied to the public about its supposed big-name clients, and that its executives have been accused of hoarding the project’s token to enrich themselves. But hey, a16z sunk millions into Helium (a fact Dixon never mentions), so might as well try to drum up some new interest!... |
APT 17 | ★★★ | ||
| 2023-11-28 00:00:00 | Enquêter sur le risque de références compromises et d'actifs exposés à Internet explorez le rapport révélant les industries et les tailles d'entreprise avec les taux les plus élevés d'identification compromises et d'actifs exposés à Internet.En savoir plus Investigating the Risk of Compromised Credentials and Internet-Exposed Assets Explore the report revealing industries and company sizes with the highest rates of compromised credentials and internet-exposed assets. Read More (lien direct) |
IntroductionIn this report, Kovrr collected and analyzed data to better understand one of the most common initial access vectors (1) - the use of compromised credentials (Valid Accounts - T1078) (2) to access internet-exposed assets (External Remote Services - T113) (3). The toxic combination of these two initial access vectors can allow malicious actors to gain a foothold in company networks before moving on to the next stage of their attack, which can be data theft, ransomware, denial of service, or any other action. There are numerous examples of breaches perpetrated by many attack groups that have occurred using this combination, for example, breaches by Lapsus (4) and APT39 (5), among others. âThis report seeks to demonstrate which industries and company sizes have the highest percentage of compromised credentials and number of internet-exposed assets and face a higher risk of having their networks breached by the toxic combination of the initial access vectors mentioned above.âIt should be noted that having an asset exposed to the internet does not inherently pose a risk or indicate that a company has poor security. In our highly digitized world, companies are required to expose services to the internet so their services can be accessed by customers, vendors, and remote employees. These services include VPN servers, SaaS applications developed by the company, databases, and shared storage units. However, there are some common cases when having an asset exposed to the internet can be extremely risky, for example:âWhen a company unintentionally exposes an asset due to misconfiguration.When a malicious third party obtains compromised credentials of a legitimate third party and accesses an exposed asset.  âTo limit unnecessary internet exposure, companies should employ the following possible mitigations:âUse Multi-Factor Authentication (MFA) for any services or assets that require a connection so that compromised credentials on their own will not be enough to breach an exposed asset.Limit access to the asset to only specific accounts, domains, and/or IP ranges.Segment the internal company network and isolate critical areas so that even if a network is breached through access to an external asset, attackers will not be able to use that access to reach wider or more sensitive areas of the company network. âSummaryâThe following are the main findings from the collected data:âThe Services industry is by far the most exposed to attackers. Companies from that industry have the highest percentage of compromised credentials (74%). However, they have a relatively low amount of internet-exposed assets per company (34%). However, given that an average cyber loss in this industry has been shown to be about $45M, this is highly concerning (6). The Services industry (SIC Division I) is followed by Division E (Transportation, Communications, Electric, Gas, and Sanitary Services, with an average loss of around $58M), which is followed by Division D (Manufacturing, with an average loss of around $25M). The revenue range for companies with the highest number of compromised credentials is $1M-$10M, followed by $10M-$50M. A similar trend is also observed when evaluating company size by the number of employees. Indeed, companies with fewer employees have a higher share of compromised credentials. On average, the larger the company (both in terms of revenue and number of employees (7)), the greater the number of internet-exposed assets.There is a correlation between the industries and revenue ranges of companies targeted by ransomware and those with the highest share of compromised credentials.   âMethodologyâThe data for this research was collected as follows:âData regarding compromised credentials was first collected from Hudson Rock, a provider of various cybercrime data. Data was collected for the previous six months, beginning March 2023. This data | Ransomware Threat Studies Prediction Cloud | APT 39 APT 39 APT 17 | ★★★ | |
| 2023-10-24 08:07:41 | Cloud de confiance : la vision environnementale du Cigref (lien direct) | Le Cigref a retravaillé le volet " environnement " de son référentiel du cloud de confiance. Comment se présente-t-il désormais ? | Cloud | APT 15 | ★★ | |
| 2023-10-20 10:19:43 | Métiers IT – Scrum Master : fonction, formation et salaire (lien direct) | Le Scrum Master anime une équipe pluridisciplinaire, composé de développeurs et de product owners, et met en oeuvre les pratiques Scrum pour développer un projet IT. | APT 15 | ★★ | ||
| 2023-10-10 20:05:50 | L'acteur de la triade de la triade saliss Smishing Triad Threat Actor Sets Its Sights on the UAE (lien direct) |
 Resesecurity avertit que l'acteur de la triade de smirage a «largement élargi son empreinte d'attaque» aux Émirats arabes unis (EAU).
Resesecurity avertit que l'acteur de la triade de smirage a «largement élargi son empreinte d'attaque» aux Émirats arabes unis (EAU).
 Resecurity warns that the Smishing Triad threat actor has “vastly expanded its attack footprint” in the United Arab Emirates (UAE).
Resecurity warns that the Smishing Triad threat actor has “vastly expanded its attack footprint” in the United Arab Emirates (UAE). |
Threat | APT 15 | ★★★ | |
| 2023-09-01 13:43:32 | Un groupe d\'espionnage aligné avec les intérêts chinois usurpant Signal et Telegram (lien direct) | Des chercheurs identifient deux campagnes actives ciblant les utilisateurs d’Android. L'acteur opérant ces outils d'espionnage pour Telegram et Signal sont attribués au groupe APT GREF, aligné sur les intérêts de la Chine. Très probablement actives depuis juillet 2020 et depuis juillet 2022, respectivement pour chaque application malveillante, les campagnes ont distribué le code d’espionnage Android … Continue reading Un groupe d'espionnage aligné avec les intérêts chinois usurpant Signal et Telegram | Tool | APT 15 | ★★★ | |
| 2023-08-31 09:18:59 | ESET découvre un groupe d\'espionnage aligné avec les intérêts chinois usurpant les applications Signal et Telegram (lien direct) | ESET découvre un groupe d'espionnage aligné avec les intérêts chinois usurpant les applications Signal et Telegram Télémétrie ESET pour les applications trojanisées. ● ESET Research a découvert des applications Signal et Telegram trojanisées pour Android, nommées Signal Plus Messenger et FlyGram, sur Google Play et Samsung Galaxy Store ; les deux applications ont ensuite été supprimées de Google Play. ● Signal Plus Messenger représente le premier cas documenté d'espionnage des communications Signal en liant secrètement et automatiquement l'appareil compromis à l'appareil Signal de l'attaquant. ● Le code malveillant trouvé dans ces applications est attribué à la famille de logiciels malveillants BadBazaar, qui a été utilisée dans le passé par un groupe APT aligné sur les intérêts de la Chine, nommé GREF. ● Des milliers d'utilisateurs ont téléchargé les applications d'espionnage. La télémétrie d'ESET a signalé des détections sur des appareils Android dans plusieurs pays de l'UE, aux États-Unis, en Ukraine et dans d'autres endroits du monde. ● Le malware BadBazaar a déjà été utilisé pour cibler les Ouïghours et d'autres minorités ethniques turques. Le malware FlyGram a également été vu partagé dans un groupe Telegram ouïghour, ce qui correspond au ciblage précédent de la famille de logiciels malveillants BadBazaar. - Malwares | Malware | APT 15 | ★★ | |
| 2023-08-30 19:13:00 | Les logiciels espions Android BadBazaar liés à la Chine ciblant les utilisateurs de signaux et de télégrammes China-Linked BadBazaar Android Spyware Targeting Signal and Telegram Users (lien direct) |
Des chercheurs en cybersécurité ont découvert des applications Android malveillantes pour Signal et Telegram distribuées via le Google Play Store et le Samsung Galaxy Store, conçues pour diffuser le logiciel espion BadBazaar sur les appareils infectés.
La société slovaque ESET a attribué la campagne à un acteur lié à la Chine appelé GREF.
"Très probablement actives respectivement depuis juillet 2020 et depuis juillet 2022, les campagnes
Cybersecurity researchers have discovered malicious Android apps for Signal and Telegram distributed via the Google Play Store and Samsung Galaxy Store that are engineered to deliver the BadBazaar spyware on infected devices. Slovakian company ESET attributed the campaign to a China-linked actor called GREF. "Most likely active since July 2020 and since July 2022, respectively, the campaigns |
APT 15 APT 15 | ★★ | ||
| 2023-08-30 16:00:00 | Le groupe chinois APT GREF utilise BadBazaar pour l'espionnage Android Chinese APT Group GREF Use BadBazaar in Android Espionage (lien direct) |
ESET a déclaré que BadBazaar était disponible via le Google Play Store, le Samsung Galaxy Store et divers sites d'applications.
ESET said BadBazaar was available via the Google Play Store, Samsung Galaxy Store and various app sites |
APT 15 APT 15 | ★★★ | ||
| 2023-08-30 11:16:48 | Les applications Trojanized Signal et Telegram sur Google Play ont livré des logiciels espions Trojanized Signal and Telegram apps on Google Play delivered spyware (lien direct) |
Des applications de chevaux de Troie Signal et Telegram contenant le logiciel espion BadBazaar ont été téléchargées sur Google Play et Samsung Galaxy Store par un groupe de piratage APT chinois connu sous le nom de GREF.[...]
Trojanized Signal and Telegram apps containing the BadBazaar spyware were uploaded onto Google Play and Samsung Galaxy Store by a Chinese APT hacking group known as GREF. [...] |
APT 15 | ★★★ | ||
| 2023-08-30 09:30:18 | L'outil d'espionnage Badbazaar cible les utilisateurs d'Android via des applications de signaux et de télégrammes trojanisés BadBazaar espionage tool targets Android users via trojanized Signal and Telegram apps (lien direct) |
Les chercheurs de l'ESET ont découvert des campagnes actives liées au groupe APT aligné par la Chine connu sous le nom de GREF, distribuant un code d'espionnage qui a déjà ciblé les Ouïghours
ESET researchers have discovered active campaigns linked to the China-aligned APT group known as GREF, distributing espionage code that has previously targeted Uyghurs |
Tool | APT 15 | ★★ | |
| 2023-08-19 10:07:14 | Les pirates utilisent le certificat de code VPN Provider \\ pour signer des logiciels malveillants Hackers use VPN provider\\'s code certificate to sign malware (lien direct) |
Le groupe APT (Advanced Advanced Persistance Menace) aligné en Chine connu sous le nom de \\ 'Bronze Starlight \' a été vu ciblant l'industrie du jeu d'Asie du Sud-Est avec des logiciels malveillants signés en utilisant un certificat valide utilisé par le fournisseur IVACY VPN.[...]
The China-aligned APT (advanced persistent threat) group known as \'Bronze Starlight\' was seen targeting the Southeast Asian gambling industry with malware signed using a valid certificate used by the Ivacy VPN provider. [...] |
Malware | APT 10 | ★★★ | |
| 2023-08-16 06:46:45 | Rapport de tendance des menaces sur les groupes APT & # 8211;Juin 2023 Threat Trend Report on APT Groups – June 2023 (lien direct) |
Tendances du groupe APT & # 8211;Juin 2023 1) Andariel 2) APT28 3) Cadet Blizzard (Dev-0586) 4) Camaro Dragon 5) Chicheau charmant (Mint Sandstorm) 6) Gamaredon (Shuckworm) 7) Ke3Chang (Apt15, Nickel) 8) Kimsuky 9) Lazarus 10) Eau boueuse 11) Mustang Panda 12) Oceanlotus 13) Patchwork (éléphant blanc) 14) REd Eyes (APT37) 15) Sharp Panda 16) Sidecopy 17) Soldat Stealth ATIP_2023_JUN_THREAT Rapport de tendance sur les groupes APT
APT Group Trends – June 2023 1) Andariel 2) APT28 3) Cadet Blizzard (DEV-0586) 4) Camaro Dragon 5) Charming Kitten (Mint Sandstorm) 6) Gamaredon (Shuckworm) 7) Ke3chang (APT15, Nickel) 8) Kimsuky 9) Lazarus 10) Muddy Water 11) Mustang Panda 12) OceanLotus 13) Patchwork (White Elephant) 14) Red Eyes (APT37) 15) Sharp Panda 16) SideCopy 17) Stealth Soldier ATIP_2023_Jun_Threat Trend Report on APT Groups |
Threat Prediction | APT 38 APT 37 APT 37 APT 35 APT 35 APT 32 APT 32 APT 28 APT 28 APT 15 APT 15 APT 25 | ★★ | |
| 2023-08-02 10:00:00 | Code Mirage: Comment les cybercriminels exploitent le code halluciné AI pour les machinations malveillantes Code Mirage: How cyber criminals harness AI-hallucinated code for malicious machinations (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article.
Introduction:
The landscape of cybercrime continues to evolve, and cybercriminals are constantly seeking new methods to compromise software projects and systems. In a disconcerting development, cybercriminals are now capitalizing on AI-generated unpublished package names also known as “AI-Hallucinated packages” to publish malicious packages under commonly hallucinated package names. It should be noted that artificial hallucination is not a new phenomenon as discussed in [3]. This article sheds light on this emerging threat, wherein unsuspecting developers inadvertently introduce malicious packages into their projects through the code generated by AI.
 AI-hallucinations:
AI-hallucinations:
 Artificial intelligence (AI) hallucinations, as described [2], refer to confident responses generated by AI systems that lack justification based on their training data. Similar to human psychological hallucinations, AI hallucinations involve the AI system providing information or responses that are not supported by the available data. However, in the context of AI, hallucinations are associated with unjustified responses or beliefs rather than false percepts. This phenomenon gained attention around 2022 with the introduction of large language models like ChatGPT, where users observed instances of seemingly random but plausible-sounding falsehoods being generated. By 2023, it was acknowledged that frequent hallucinations in AI systems posed a significant challenge for the field of language models.
The exploitative process:
Cybercriminals begin by deliberately publishing malicious packages under commonly hallucinated names produced by large language machines (LLMs) such as ChatGPT within trusted repositories. These package names closely resemble legitimate and widely used libraries or utilities, such as the legitimate package ‘arangojs’ vs the hallucinated package ‘arangodb’ as shown in the research done by Vulcan [1].
The trap unfolds:
Artificial intelligence (AI) hallucinations, as described [2], refer to confident responses generated by AI systems that lack justification based on their training data. Similar to human psychological hallucinations, AI hallucinations involve the AI system providing information or responses that are not supported by the available data. However, in the context of AI, hallucinations are associated with unjustified responses or beliefs rather than false percepts. This phenomenon gained attention around 2022 with the introduction of large language models like ChatGPT, where users observed instances of seemingly random but plausible-sounding falsehoods being generated. By 2023, it was acknowledged that frequent hallucinations in AI systems posed a significant challenge for the field of language models.
The exploitative process:
Cybercriminals begin by deliberately publishing malicious packages under commonly hallucinated names produced by large language machines (LLMs) such as ChatGPT within trusted repositories. These package names closely resemble legitimate and widely used libraries or utilities, such as the legitimate package ‘arangojs’ vs the hallucinated package ‘arangodb’ as shown in the research done by Vulcan [1].
The trap unfolds:
 When developers, unaware of the malicious intent, utilize AI-based tools or large language models (LLMs) to generate code snippets for their projects, they inadvertently can fall into a trap. The AI-generated code snippets can include imaginary unpublished libraries, enabling cybercriminals to publish commonly used AI-generated imaginary package names. As a result, developers unknowingly import malicious packages into their projects, introducing vulnerabilities, backdoors, or other malicious functionalities that compromise the security and integrity of the software and possibly other projects.
Implications for developers:
The exploitation of AI-generated hallucinated package names poses significant risks to developers and their projects. Here are some key implications:
Trusting familiar package names: Developers commonly rely on package names they recognize to introduce code snippets into their projects. The presence of malicious packages under commonly hallucinated names makes it increasingly difficult to distinguish between legitimate and malicious options when relying on the trust from AI generated code.
Blind trust in AI-generated code: Many develo
When developers, unaware of the malicious intent, utilize AI-based tools or large language models (LLMs) to generate code snippets for their projects, they inadvertently can fall into a trap. The AI-generated code snippets can include imaginary unpublished libraries, enabling cybercriminals to publish commonly used AI-generated imaginary package names. As a result, developers unknowingly import malicious packages into their projects, introducing vulnerabilities, backdoors, or other malicious functionalities that compromise the security and integrity of the software and possibly other projects.
Implications for developers:
The exploitation of AI-generated hallucinated package names poses significant risks to developers and their projects. Here are some key implications:
Trusting familiar package names: Developers commonly rely on package names they recognize to introduce code snippets into their projects. The presence of malicious packages under commonly hallucinated names makes it increasingly difficult to distinguish between legitimate and malicious options when relying on the trust from AI generated code.
Blind trust in AI-generated code: Many develo |
Tool | APT 15 ChatGPT ChatGPT | ★★★ | |
| 2023-07-19 16:09:41 | IA générative : les tuyaux du Cigref (lien direct) | Fournisseurs, développeurs, sous-traitants, utilisateurs finaux... Le Cigref a compilé quelques observations sur le sujet de l'IA générative. | APT 15 | ★★★ | ||
| 2023-07-13 00:00:00 | Le Ransomware Threat Landscape H1-23 Ce rapport fournit une analyse complète de toutes les attaques de ransomwares connues qui ont été signalées au cours des deux premiers trimestres de 2023. The Ransomware Threat Landscape H1-23This report provides a comprehensive analysis of all known ransomware attacks that were reported during the first two quarters of 2023.Read More (lien direct) |
IntroductionâIn this comprehensive report, Kovrr collected and analyzed data on all known ransomware attacks reported during the first two quarters of 2023. The data was collected from multiple sources, all aggregated and updated regularly in Kovrrâs Threat Intelligence Database. The database includes data on many different types of cyber incidents, but this report includes only data on ransomware attacks, excluding data on any other type of attacks. The ransomware groups covered in this report all operate as a RaaS (Ransomware as a Service), a business model through which the ransomware binary and operation are sold or leased to operators, called affiliates. This means that a ransomware operation is composed of many different individuals, with separate roles, and the extortion profits are divided between them. Some individuals are responsible for initial access to the targets, others to lateral movement to interesting and profitable areas in the victim network, while others are responsible for the ransomware infection itself, and others negotiate with the victim after infection. âSummaryâThese are the main insights from the collected data:There is a 32% drop in attack amounts in H1-23 compared to H2-22. It is important to note that this drop can also be due to delayed reporting of cyber incidents by attacked companies.The top ten most active groups observed during the first half of 2023 are AvosLocker, Bianlian, BlackBasta, BlackCat, Clop, Lockbit 3.0, MedusaLocker, Play, Royal, and ViceSociety. All 10 actors accounted for 87% of attacks during this period, while the top 3 groups (Lockbit 3.0, BlackCat, and Clop) accounted for 53% of all claimed attacks during this period. The average lifespan of a ransomware group is 262 days, while the median is 167 days. In an average month, 18.3 different ransomware groups are active.The most targeted industry is the Services industry, while companies with a revenue of $10M-$50M are the most common targets. âData Collection Methods and Possible BiasesâThe data for this research was collected from Kovrrâs Threat Intelligence Database, that collects data from multiple sources, and includes information on different types of cyber incidents. Specifically for this report, data was collected mainly from ransomware leak sites, public filings of attacked companies, and news reports on ransomware attacks. The data from ransomware leak sites was collected mainly from Double Extortion (https://doubleextortion.com), a data source providing up to date information from ransomware leak sites. The rest of the data was collected using proprietary sources and methods. This data was then combined with additional sources to collect company business information and is limited to ransomware attacks that occurred and were reported in the first two quarters of 2023, between January 1st 2023 and June 31st 2023. There are several possible biases in the data that may affect the results presented in the report. Data collection for this research relied either on a company filing a notification on a ransomware attack, or a ransomware group uploading information about a victim. Therefore, in the case that a company decided not to file a notice of a ransomware attack, for example due to not being legally required to do so, it will not be included in our data. This means that companies located in countries that require data breach notifications, such as companies in the United States or the European Union, are expected to have a higher representation in our data. This is also true for companies in more regulated industries, such as healthcare. Regarding data retrieved from ransom group sites, there may be cases where an attacker did not upload data on the attack victim, as the victim paid the ransom, or for other reasons. This means that some victims that have quickly paid ransoms following an attack might not appear in our data. Additionally,, we have previously researched | Ransomware Data Breach Vulnerability Threat Cloud | APT 17 | ★★★ | |
| 2023-07-07 16:00:00 | L'utilisateur de Twitter expose la fuite de données nickelodeon Twitter User Exposes Nickelodeon Data Leak (lien direct) |
Les rapports sur les réseaux sociaux suggèrent qu'une personne prétendument vide environ 500 Go de fichiers d'animation
Social media reports suggest an individual allegedly dumped approximately 500GB of animation files |
APT 15 | ★★ | ||
| 2023-07-06 22:45:12 | Nickelodeon sonde les affirmations de fuite de données massives alors que les fans de Bob éponge se réjouissent Nickelodeon probes claims of massive data leak as SpongeBob fans rejoice (lien direct) |
TV Network \'s Attorneys \\ 'Sur un Rampage DMCA \' ... êtes-vous sûr que vous êtes prêt, les enfants? Nickelodeon dit qu'il a sondé les affirmations que "Des décennies "Matériel a été volée et a divulgué en ligne.Cela suit des rapports sur les réseaux sociaux selon lesquels quelqu'un avait jeté 500 Go de fichiers d'animation arrachés.L'hilarité, et de nombreux mèmes de squarepants d'éponge, ont suivi.…
TV network\'s attorneys \'on a DMCA rampage\' ... are you sure you\'re ready, kids? Nickelodeon says it is probing claims that "decades old" material was stolen from it and leaked online. This follows reports on social media that someone had dumped 500GB of snatched animation files. Hilarity, and many SpongeBob SquarePants memes, ensued.… |
APT 15 | ★★ | ||
| 2023-07-06 19:11:00 | Nickelodeon dit que certaines des données prétendument volées \\ 'semble avoir des décennies \\' Nickelodeon says some of allegedly stolen data \\'appears to be decades old\\' (lien direct) |
 Le géant de la télévision des enfants, Nickelodeon, a déclaré qu'il enquêtait sur une violation présumée après que les pirates aient prétendu avoir volé 500 Go de données.Pendant des jours, les experts en cybersécurité ont averti que pirates partagent des documents volés du réseau qui comprenait des fuites du département d'animation Nickellodeon.Certaines des informations auraient remonté des décennies.[Captures d'écran du
Le géant de la télévision des enfants, Nickelodeon, a déclaré qu'il enquêtait sur une violation présumée après que les pirates aient prétendu avoir volé 500 Go de données.Pendant des jours, les experts en cybersécurité ont averti que pirates partagent des documents volés du réseau qui comprenait des fuites du département d'animation Nickellodeon.Certaines des informations auraient remonté des décennies.[Captures d'écran du
 Children\'s television giant Nickelodeon said it is investigating an alleged breach after hackers claimed to have stolen 500 GB of data. For days, cybersecurity experts have warned that hackers are sharing stolen documents from the network that included leaks from the Nickelodeon animation department. Some of the information allegedly dates back decades. [Screenshots of the
Children\'s television giant Nickelodeon said it is investigating an alleged breach after hackers claimed to have stolen 500 GB of data. For days, cybersecurity experts have warned that hackers are sharing stolen documents from the network that included leaks from the Nickelodeon animation department. Some of the information allegedly dates back decades. [Screenshots of the |
APT 15 | ★★ | ||
| 2023-07-06 11:03:36 | Nickelodeon enquête sur la violation après la fuite de \\ 'DÉCÉSION \\' DONNÉES Nickelodeon investigates breach after leak of \\'decades old\\' data (lien direct) |
Nickelodeon a confirmé que les données divulguées à partir d'une violation présumée de l'entreprise étaient légitimes, mais elle semble avoir des décennies.[...]
Nickelodeon has confirmed that the data leaked from an alleged breach of the company is legitimate but it appears to be decades old. [...] |
APT 15 | ★★ | ||
| 2023-06-27 13:00:00 | Cyberheistnews Vol 13 # 26 [Eyes Open] La FTC révèle les cinq dernières escroqueries par SMS CyberheistNews Vol 13 #26 [Eyes Open] The FTC Reveals the Latest Top Five Text Message Scams (lien direct) |
 CyberheistNews Vol 13 #26 | June 27th, 2023
[Eyes Open] The FTC Reveals the Latest Top Five Text Message Scams
The U.S. Federal Trade Commission (FTC) has published a data spotlight outlining the most common text message scams. Phony bank fraud prevention alerts were the most common type of text scam last year. "Reports about texts impersonating banks are up nearly tenfold since 2019 with median reported individual losses of $3,000 last year," the report says.
These are the top five text scams reported by the FTC:
Copycat bank fraud prevention alerts
Bogus "gifts" that can cost you
Fake package delivery problems
Phony job offers
Not-really-from-Amazon security alerts
"People get a text supposedly from a bank asking them to call a number ASAP about suspicious activity or to reply YES or NO to verify whether a transaction was authorized. If they reply, they\'ll get a call from a phony \'fraud department\' claiming they want to \'help get your money back.\' What they really want to do is make unauthorized transfers.
"What\'s more, they may ask for personal information like Social Security numbers, setting people up for possible identity theft."
Fake gift card offers took second place, followed by phony package delivery problems. "Scammers understand how our shopping habits have changed and have updated their sleazy tactics accordingly," the FTC says. "People may get a text pretending to be from the U.S. Postal Service, FedEx, or UPS claiming there\'s a problem with a delivery.
"The text links to a convincing-looking – but utterly bogus – website that asks for a credit card number to cover a small \'redelivery fee.\'"
Scammers also target job seekers with bogus job offers in an attempt to steal their money and personal information. "With workplaces in transition, some scammers are using texts to perpetrate old-school forms of fraud – for example, fake \'mystery shopper\' jobs or bogus money-making offers for driving around with cars wrapped in ads," the report says.
"Other texts target people who post their resumes on employment websites. They claim to offer jobs and even send job seekers checks, usually with instructions to send some of the money to a different address for materials, training, or the like. By the time the check bounces, the person\'s money – and the phony \'employer\' – are long gone."
Finally, scammers impersonate Amazon and send fake security alerts to trick victims into sending money. "People may get what looks like a message from \'Amazon,\' asking to verify a big-ticket order they didn\'t place," the FTC says. "Concerned
CyberheistNews Vol 13 #26 | June 27th, 2023
[Eyes Open] The FTC Reveals the Latest Top Five Text Message Scams
The U.S. Federal Trade Commission (FTC) has published a data spotlight outlining the most common text message scams. Phony bank fraud prevention alerts were the most common type of text scam last year. "Reports about texts impersonating banks are up nearly tenfold since 2019 with median reported individual losses of $3,000 last year," the report says.
These are the top five text scams reported by the FTC:
Copycat bank fraud prevention alerts
Bogus "gifts" that can cost you
Fake package delivery problems
Phony job offers
Not-really-from-Amazon security alerts
"People get a text supposedly from a bank asking them to call a number ASAP about suspicious activity or to reply YES or NO to verify whether a transaction was authorized. If they reply, they\'ll get a call from a phony \'fraud department\' claiming they want to \'help get your money back.\' What they really want to do is make unauthorized transfers.
"What\'s more, they may ask for personal information like Social Security numbers, setting people up for possible identity theft."
Fake gift card offers took second place, followed by phony package delivery problems. "Scammers understand how our shopping habits have changed and have updated their sleazy tactics accordingly," the FTC says. "People may get a text pretending to be from the U.S. Postal Service, FedEx, or UPS claiming there\'s a problem with a delivery.
"The text links to a convincing-looking – but utterly bogus – website that asks for a credit card number to cover a small \'redelivery fee.\'"
Scammers also target job seekers with bogus job offers in an attempt to steal their money and personal information. "With workplaces in transition, some scammers are using texts to perpetrate old-school forms of fraud – for example, fake \'mystery shopper\' jobs or bogus money-making offers for driving around with cars wrapped in ads," the report says.
"Other texts target people who post their resumes on employment websites. They claim to offer jobs and even send job seekers checks, usually with instructions to send some of the money to a different address for materials, training, or the like. By the time the check bounces, the person\'s money – and the phony \'employer\' – are long gone."
Finally, scammers impersonate Amazon and send fake security alerts to trick victims into sending money. "People may get what looks like a message from \'Amazon,\' asking to verify a big-ticket order they didn\'t place," the FTC says. "Concerned |
Ransomware Spam Malware Hack Tool Threat | FedEx APT 28 APT 15 ChatGPT ChatGPT | ★★ |
To see everything:
Our RSS (filtrered)
