What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2016-11-26 05:06:12 | Il repart au volant d\'une Tesla en utilisant une faille de l\'application mobile (lien direct) | Au fil des différentes tentatives de piratage, les Tesla se sont souvent révélées comme étant plutôt bien sécurisées. Un groupe d'experts en sécurité à pourtant trouvé une faille qui permet même de voler une Model S grâce à un malware.  |
Tesla | |||
| 2016-11-26 02:34:11 | Researchers Show How to Steal Tesla Car by Hacking into Owner\'s Smartphone (lien direct) | New technology is always a little scary, so are Smart Cars. From GPS system and satellite radio to wireless locks, steering, brakes, and accelerator, today vehicles are more connected to networks than ever, and so they are more hackable than ever.
It's not new for security researchers to hack connected cars. Previously they had demonstrated how to hijack a car remotely, and how to disable
|
Tesla | |||
| 2016-11-25 15:14:00 | Researchers Hijack Tesla Car by Hacking Mobile App (lien direct) | Researchers at Norway-based security firm Promon have demonstrated how thieves with the necessary hacking skills can track and steal Tesla vehicles through the carmaker's Android application. | Tesla | |||
| 2016-11-25 06:05:11 | Android Malware Used to Hack and Steal a Tesla Car (lien direct) | By infecting a Tesla owner's phone with Android malware, a car thief can hack and then steal a Tesla car, security researchers have revealed this week. [...] | Tesla | |||
| 2016-11-07 13:07:32 | Oil exec accused of impersonating Elon Musk in an email sues Tesla over Twitter hack (lien direct) | Todd Katz says Tesla illegally accessed his Twitter account in its investigation of a Yahoo email crafted to look like it came from Musk. |
Yahoo Tesla | |||
| 2016-10-14 14:00:00 | Alien Eye in the Sky 14th October 2016 (lien direct) |
 We’ve got the weeks’ news covered for you.
Links to stories in the video
The beginning of the end(point): where we are now and where we’ll be in five years
The strange way people perceive privacy online
Tesla responds to Chinese hack with a major security upgrade
Good cybersecurity can be good marketing
Cyber: Ignore the penetration testers
Other stories of interest
When automated bots were primed to sell the UK Pound
The ethics and morality behind APT reports
Scott Helme went wardriving
Internet of things botnets – SSH just got real!
Lloyds combats call center fraudsters with new tech
F-Secure pens an open letter to businesses that block VPNs on their free WiFi
Sarah Clarke gives a perspective on GDPR, a personal and professional journey
Akamai finds longtime security flaw in 2 million devices.
We’ve got the weeks’ news covered for you.
Links to stories in the video
The beginning of the end(point): where we are now and where we’ll be in five years
The strange way people perceive privacy online
Tesla responds to Chinese hack with a major security upgrade
Good cybersecurity can be good marketing
Cyber: Ignore the penetration testers
Other stories of interest
When automated bots were primed to sell the UK Pound
The ethics and morality behind APT reports
Scott Helme went wardriving
Internet of things botnets – SSH just got real!
Lloyds combats call center fraudsters with new tech
F-Secure pens an open letter to businesses that block VPNs on their free WiFi
Sarah Clarke gives a perspective on GDPR, a personal and professional journey
Akamai finds longtime security flaw in 2 million devices.
|
Tesla | |||
| 2016-09-28 16:19:35 | Tesla security updates includes code signing feature (lien direct) | Tesla has releases a major firmware update in response to a video posted by a group of Chinese researchers that displayed a series of vulnerabilities the electric car company's vehicles. |
Tesla | |||
| 2016-09-27 11:00:11 | Tesla Responds to Chinese Hack With a Major Security Upgrade (lien direct) |  When researchers at the Chinese firm Tencent hacked a Tesla S, the carmaker pushed out a new security feature known as code signing to millions of vehicles. The post Tesla Responds to Chinese Hack With a Major Security Upgrade When researchers at the Chinese firm Tencent hacked a Tesla S, the carmaker pushed out a new security feature known as code signing to millions of vehicles. The post Tesla Responds to Chinese Hack With a Major Security Upgrade |
Tesla | |||
| 2016-09-27 04:24:00 | After Tesla: why cybersecurity is central to the car industry\'s future (lien direct) | The news that a Tesla car was hacked from 12 miles away tells us that the explosive growth in automotive connectivity may be rapidly outpacing automotive security.This story is illustrative of two persistent problems afflicting many connected industries: the continuing proliferation of vulnerabilities in new software, and the misguided view that cybersecurity is separate from concept, design, engineering and production.This leads to a 'fire brigade approach' to cybersecurity where security is not baked in at the design stage for either hardware or software but added in after vulnerabilities are discovered by cybersecurity specialists once the product is already on the market.To read this article in full or to leave a comment, please click here | Guideline | Tesla | ||
| 2016-09-24 11:00:12 | (Déjà vu) Security News This Week: Hackers Take Control of a Moving Tesla\'s Brakes (lien direct) |  Each weekend we round up the news stories that we didn't break or cover in depth but still deserve your attention. The post Security News This Week: Hackers Take Control of a Moving Tesla's Brakes Each weekend we round up the news stories that we didn't break or cover in depth but still deserve your attention. The post Security News This Week: Hackers Take Control of a Moving Tesla's Brakes |
Tesla | |||
| 2016-09-21 22:27:02 | TEAM CYMRU: Tesla Fixes Critical Remote Hack Vulnerability #cybersecurity http://bit.ly/2cJ9gJt pic.twitter.com/LGRzp33kdr (lien direct) | TEAM CYMRU: Tesla Fixes Critical Remote Hack Vulnerability #cybersecurity http://bit.ly/2cJ9gJt pic.twitter.com/LGRzp33kdr | Tesla | |||
| 2016-09-21 16:16:10 | DarkReading: Chinese Researchers Hack Tesla S Models, Expose Bugshttp://ubm.io/2cCVpyPÂ (lien direct) | DarkReading: Chinese Researchers Hack Tesla S Models, Expose Bugshttp://ubm.io/2cCVpyPÂ | Tesla | |||
| 2016-09-21 16:04:06 | Tesla Model S hacked from 12 miles away (lien direct) | A team of researchers was able to hack the controls of a Tesla Model S from a distance of 12 miles – adjusting the mirrors, locks and even slamming on the brakes. | Tesla | |||
| 2016-09-21 11:16:59 | Hackers take over Tesla Model S while car is moving (lien direct) | First the Jeep Cherokee, now researchers have hacked into the Tesla Model S's in-car web browser to control the car remotely. |
Tesla | |||
| 2016-09-21 09:15:00 | Chinese Researchers Hack Tesla S Models, Expose Bugs (lien direct) | Automaker fixes security risks after Tencent Holdings uncover vulnerabilities in both parking and drive mode. | Tesla | |||
| 2016-09-21 08:03:12 | Tesla Model S : Prise de contrôle à distance possible (lien direct) |  Des chercheurs en sécurité informatique chinois ont découvert une faille de sécurité touchant les Tesla Model S, permettant la prise de contrôle à distance des véhicules. Proof of Concept édifiant. Des chercheurs en sécurité informatique chinois ont découvert une faille de sécurité touchant les Tesla Model S, permettant la prise de contrôle à distance des véhicules. Proof of Concept édifiant. |
Tesla | |||
| 2016-09-20 22:32:27 | Researchers demonstrate how they can remotely attack Tesla Cars (lien direct) | As more and more devices and machines become connected, the world becomes a scarier place. This was shown yesterday, when the Keen Security Lab of Tencent posted a blog post on how they figured out a way to remotely attack Tesla cars. [...] | Tesla | |||
| 2016-09-20 21:15:00 | Researchers wirelessly hit the brakes in a Model S, Tesla patches quickly (lien direct) | Exploiting in-car Web browser, researchers gained access to car's control network. | Tesla | |||
| 2016-09-20 17:10:13 | Hackers crack Tesla CAN Bus, DoT issues policy for securing connected car (lien direct) | Researchers claim they were able to crack into Tesla's CAN Bus to achieve remote control of the electric car and the DoT just issued a new policy concerning automated vehicles. |
Tesla | |||
| 2016-09-20 17:06:22 | Tesla Fixes Critical Remote Hack Vulnerability (lien direct) | Researchers were able to remotely brake Tesla model cars as well as freeze control panels and open the rear hatch while driving. | Tesla | |||
| 2016-09-20 12:22:43 | Watch Teslas being hacked as they drive, from up to 20 km away (lien direct) |  Chinese hackers literally open a backdoor on a Tesla car... Chinese hackers literally open a backdoor on a Tesla car...
|
Tesla | |||
| 2016-09-20 10:42:58 | Tesla Patches Vulnerabilities that Allowed Remote Takeover of Model S Car (lien direct) | Tesla has patched a number of vulnerabilities that allowed attackers to remotely take control over certain features in its Model S car. Researchers at the Keen Security Lab of Tencent, a Chinese tech company, exploited the vulnerabilities to successfully seize control of the CAN bus that operates many vehicle systems in the car. They did […]… Read More | Tesla | |||
| 2016-09-20 08:38:54 | Des hackers ont réussi à pirater une Tesla Model S à distance (lien direct) | Une faille dans le navigateur web de la voiture connectée permettait d'accéder à des fonctions mécaniques comme le freinage ou l'ouverture du coffre. Impressionnant.  |
Tesla | |||
| 2016-09-20 07:55:10 | (Déjà vu) Researchers demonstrate remote attack against Tesla Model S (lien direct) | Tesla Motors is considered one of the most cybersecurity-conscious car manufacturers in the world -- among other things, it has a bug bounty program. But that doesn't mean the software in its cars is free of security flaws.Researchers from Chinese technology company Tencent found a series of vulnerabilities that, when combined, allowed them to remotely take over a Tesla Model S car and control its sunroof, central display, door locks and even the breaking system. The attack allowed the researchers to access the car's controller area network (CAN) bus, which lets the vehicle's specialized computers communicate with each other."As far as we know, this is the first case of remote attack which compromises CAN Bus to achieve remote controls on Tesla cars," the researchers from Tencent's Keen Security Lab said in a blog post Monday. "We have verified the attack vector on multiple varieties of Tesla Model S. It is reasonable to assume that other Tesla models are affected."To read this article in full or to leave a comment, please click here | Tesla | |||
| 2016-09-20 07:54:57 | Chinese Researchers Remotely Hack Tesla Model S (lien direct) | Security researchers from China-based tech company Tencent have identified a series of vulnerabilities that can be exploited to remotely hack an unmodified Tesla Model S while it's parked or on the move. | Tesla | |||
| 2016-09-20 07:12:00 | Researchers remotely hack Tesla Model S while it is being driven (lien direct) | Chinese researchers from Keen Security Lab of Tencent announced that they could chain multiple vulnerabilities together which allowed them to remotely hack the Tesla Model S P85 and 75D from as far as 12 miles away.The researchers said: As far as we know, this is the first case of remote attack which compromises CAN Bus to achieve remote controls on Tesla cars. We have verified the attack vector on multiple varieties of Tesla Model S. It is reasonable to assume that other Tesla models are affected.To read this article in full or to leave a comment, please click here | Tesla | |||
| 2016-09-20 05:39:48 | Hackers take Remote Control of Tesla\'s Brakes and Door locks from 12 Miles Away (lien direct) | Next time when you find yourself hooked up behind the wheel, make sure your car is actually in your control.
Hackers can remotely hijack your car and even control its brakes from 12 miles away.
Car hacking is a hot topic.
Today many automobiles companies have been offering vehicles with the majority of functions electronically controlled, from instrument cluster to steering, brakes, and
|
Tesla | |||
| 2016-09-19 11:17:13 | A Show of (Brute) Force: Crysis Ransomware Found Targeting Australian and New Zealand Businesses (lien direct) | Crysis (detected by Trend Micro as RANSOM_CRYSIS.A), a ransomware family first detected in February this year, has been spotted targeting businesses in Australia in New Zealand through remote desktop protocol (RDP) brute force attacks. Crysis has been reported in early June this year to have set its sights into carving a market share left by TeslaCrypt when the latter's developers decided to shut down their operations, and rivaling Locky's prevalence in the ransomware threat landscape. Post from: Trendlabs Security Intelligence Blog - by Trend Micro A Show of (Brute) Force: Crysis Ransomware Found Targeting Australian and New Zealand Businesses | Tesla | |||
| 2016-09-16 06:38:00 | FBI urges ransomware victims to step forward (lien direct) | The FBI has issued a plea for those who have been hit by ransomware to report this to federal law enforcement so that the country can get a better sense of just how bad this problem really is.Ransomware refers to malware that encrypts files on computers or locks users out of their computers, and requests ransom be paid to set files free or allow users to regain access. Such malware, often going by spooky names like Cryptolocker or TeslaCrypt, can be activated by clicking on a web link or even visiting a compromised website, or opening an file in email. One nasty variant even takes your money and still deletes your files.To read this article in full or to leave a comment, please click here | Tesla | |||
| 2016-08-29 21:55:05 | DarkReading: How to Stay Protected Against Ransomware: @Sophos #Whitepaper details #Cryptowall #TeslaCrypt #Locky & more http://ubm.io/2c0xryRÂ (lien direct) | DarkReading: How to Stay Protected Against Ransomware: @Sophos #Whitepaper details #Cryptowall #TeslaCrypt #Locky & more http://ubm.io/2c0xryRÂ | Tesla | |||
| 2016-08-04 13:00:25 | Hackers Fool Tesla S’s Autopilot to Hide and Spoof Obstacles (lien direct) |  Researchers try out methods of jamming and spoofing the car's radar, ultrasonic sensors, and cameras---with disturbing results. The post Hackers Fool Tesla S's Autopilot to Hide and Spoof Obstacles Researchers try out methods of jamming and spoofing the car's radar, ultrasonic sensors, and cameras---with disturbing results. The post Hackers Fool Tesla S's Autopilot to Hide and Spoof Obstacles |
Tesla | ★★ | ||
| 2016-07-21 16:16:33 | Tesla's Data Collection May Help In Autopilot Defense http://ubm.io/29YmI87 (lien direct) | Tesla's Data Collection May Help In Autopilot Defense http://ubm.io/29YmI87 | Tesla | ★★★★★ | ||
| 2016-06-18 23:17:27 | Tesla review: What you need to know about charging (lien direct) | Before you buy an electric car, you need to understand charging. It's a huge deal. You think it works almost like filling the gas tank. It doesn't. Before going on long trips, you first need to do math and a bit of planning.The MathLike BMW model numbers indicate engine size, Tesla model numbers indicate the size of the battery, so my "Tesla S P90D" has a 90kwh (killowatt-hour) battery, with a 286mile range. Their lowest end model is the “Tesla S 60â€, which has a 60kwh hour battery, or a 208mile advertised range.In the United States, a typical plug is a 120volt circuit with a maximum of 15amps. Doing the math, this is how long it'll take for me to recharge the battery: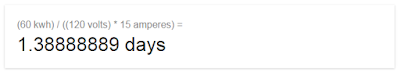 That's right, 1.4 days (or 2.1 days for a 90kwh car). This is the absolute worse case scenario, mind you, but it demonstrates that you have to pay attention to charging. You can't simply drive up to a station, fill up the tank in a couple minutes, and drive away.Let's say you live in Austin, Texas, and you have a meeting in Dallas. You think that you can drive up to Dallas in your new Tesla S 60, let the car charge while you are in the meeting, and then drive home. Or, maybe you have dinner there, letting the car charge longer. Or maybe you even stay overnight.Nope, even 24 hours later, you still might not have enough charge left to get home. At 195 miles, it's at the range of the 60kwh battery, which would take more than a day to recharge using a normal electric circuit. That's right, 1.4 days (or 2.1 days for a 90kwh car). This is the absolute worse case scenario, mind you, but it demonstrates that you have to pay attention to charging. You can't simply drive up to a station, fill up the tank in a couple minutes, and drive away.Let's say you live in Austin, Texas, and you have a meeting in Dallas. You think that you can drive up to Dallas in your new Tesla S 60, let the car charge while you are in the meeting, and then drive home. Or, maybe you have dinner there, letting the car charge longer. Or maybe you even stay overnight.Nope, even 24 hours later, you still might not have enough charge left to get home. At 195 miles, it's at the range of the 60kwh battery, which would take more than a day to recharge using a normal electric circuit.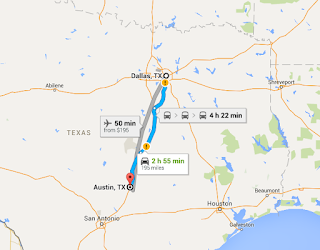 Faster ChargingThat was a worst case scenario. Luckily, you probably won't be charging using a normal 120volt/15amp circuit. That's just the emergency backup if all else fails.In your home, for high-watt devices like ovens, air conditioners, and clothes dryers, you have higher wattage circuits. The typical max in your home will be a 240volt/50amp circuit. It has a different power connector than a normal circuit, thicker wires, and so forth. Doing the math on this sucker, you get: Faster ChargingThat was a worst case scenario. Luckily, you probably won't be charging using a normal 120volt/15amp circuit. That's just the emergency backup if all else fails.In your home, for high-watt devices like ovens, air conditioners, and clothes dryers, you have higher wattage circuits. The typical max in your home will be a 240volt/50amp circuit. It has a different power connector than a normal circuit, thicker wires, and so forth. Doing the math on this sucker, you get: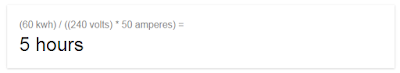 For our 190 mile drive, then, you can except to drive to Dallas, charge during the meeting and dinner for 5 hours, then you'll have enough juice to get back home.When you buy a Tesla, the first thing you'll do is hire and electrician, and for $1000 to $5000, pay them to install this high-end circuit in your garage or car port. Since you garage is usually where the circuit breaker is located anyway, it's usually the low-end of this range. You have to choose either the NEMA 14-50 plug, which can be used to power any electric car, or the Tesla HPWC (“High Power Wall Chargerâ€) that just bundles the cord and everything together, making it easier t For our 190 mile drive, then, you can except to drive to Dallas, charge during the meeting and dinner for 5 hours, then you'll have enough juice to get back home.When you buy a Tesla, the first thing you'll do is hire and electrician, and for $1000 to $5000, pay them to install this high-end circuit in your garage or car port. Since you garage is usually where the circuit breaker is located anyway, it's usually the low-end of this range. You have to choose either the NEMA 14-50 plug, which can be used to power any electric car, or the Tesla HPWC (“High Power Wall Chargerâ€) that just bundles the cord and everything together, making it easier t |
Tesla | ★★★★★ | ||
| 2016-06-10 17:07:20 | The Week in Ransomware - June 10 2016 - Crysis, TeslaCrypt, Nemucod, and More (lien direct) | Lots of ransomware news this week with 3 new infections, 7 new Jigsaw ransomware variants, 3 new decryptors, a new variant to Nemucod, and an interesting article about the Crysis ransomware. I would like to thank everyone who monitors and analyzes new ransomware infections in Twitter and through other sources. [...] | Tesla | |||
| 2016-06-10 16:16:29 | Decryption Utilities Unlock Files Encrypted by All TeslaCrypt Versions (lien direct) | Cisco released a decryption utility that unlocks files encrypted by all four versions of TeslaCrypt; Kaspersky Lab has also published a similar decryptor. | Tesla | |||
| 2016-06-10 15:50:58 | Teslacrypt RIP: Cisco Talos decryptor on the job (lien direct) | Cisco Talos stated today that it has a Teslacrypt decryptor tool up and running and ready for download that will work against any variant of this ransomware. |
Tesla | |||
| 2016-05-27 08:27:43 | DMA Locker 4.0: The Next Threat to Healthcare? (lien direct) | Lately, healthcare has been making headlines due to an onslaught of ransomware attacks from viruses like TeslaCrypt and CryptoWall. As a result of many lucrative successes in extorting ransom payments, the industry has been rightly named the number one target of cyber criminals by several research groups. And it doesn't seem to be slowing down. Cyber criminals are looking to profit off of the traditionally soft target healthcare has presented due to its general lack of highly secure network and data center architectures. According to a malwarebytes... | Tesla | ★★★★★ | ||
| 2016-05-26 10:34:37 | Say No to Ransomware With These Trend Micro Free Tools (lien direct) | Trend Micro has released free tools--Trend Micro Crypto-Ransomware File Decryptor Tool and Trend Micro Lock Screen Ransomware Tool--to help users and organizations fight back against the dangers that ransomware pose. Systems affected with certain crypto-ransomware variants like TeslaCrypt and CryptXXX can use the File Decryptor Tool to retrieve their files that were 'held hostage' by these threats. If your system is infected with ransomware that has a lock-screen feature, our Lock Screen Ransomware Tool will help users gain access to their screen even though the malware is blocking normal and safe mode with networking. One of the primary goals of these tools is to prevent affected users and businesses from succumbing to the pressure and the demands of paying the ransom just to retrieve their confidential data.Post from: Trendlabs Security Intelligence Blog - by Trend MicroSay No to Ransomware With These Trend Micro Free Tools | Guideline | Tesla | ★★★★★ | |
| 2016-05-25 12:30:15 | Expert insight from the author of the ESET TeslaCrypt decryptor (lien direct) | WeLiveSecurity sits down with Igor Kabina, the ESET malware researcher who ultimately created the universal ESET TeslaCrypt decryption tool. | Tesla | |||
| 2016-05-24 19:00:26 | TeslaCrypt Ransomware Shuts Down: One Down, Plenty to Go (lien direct) | In a surprising turn of events, the creators of the notorious TeslaCrypt ransomware shut down their operation and revealed the master key for decrypting all files. They even said they are sorry, as displayed in the image below. Figure 1: TeslaCrypt Shut Down Message The motive behind this step remains unclear. The attackers could […] | Tesla | |||
| 2016-05-23 21:01:06 | Will CryptXXX Replace TeslaCrypt After Ransomware Shakeup? #cybersecurity http://bit.ly/1TtR5QG pic.twitter.com/xmyagcQlo2 (lien direct) | Will CryptXXX Replace TeslaCrypt After Ransomware Shakeup? #cybersecurity http://bit.ly/1TtR5QG pic.twitter.com/xmyagcQlo2 |
Tesla | |||
| 2016-05-23 10:00:56 | The security review: ESET release decryptor for TeslaCrypt ransomware (lien direct) | Welcome to this week's security review, which includes ESET releasing a new decryptor for TeslaCrypt ransomware, new revelations about a 2012 LinkedIn data breach and expert insight into Operation Groundbait. | Tesla | |||
| 2016-05-23 07:16:38 | Ransomware TeslaCrypt – Le déchiffrement est enfin possible (lien direct) | La société ESET ayant remarqué que le ransomware TeslaCrypt était en fin de vie, ils se sont connectés sur le chat du site de paiement de TeslaCrypt pour demander avec culot aux cybercriminels, la clé universelle (master key) de déchiffrement du malware. Et c'est avec surprise que ces derniers ont accepté de la donner à ESET, > Lire la suiteCet article merveilleux et sans aucun égal intitulé : Ransomware TeslaCrypt – Le déchiffrement est enfin possible ; a été publié sur Korben, le seul site qui t'aime plus fort que tes parents. | Tesla | |||
| 2016-05-22 19:02:59 | TeslaCrypt Developers recommend TeslaDecoder to Decrypt Files (lien direct) | Today, Mikko Hypponen discovered that the TeslaCrypt ransomware developers have changed the message on their last functioning TOR site. According to Mikko, as of a few hours ago a new message appeared on the TOR TeslaCrypt site that now recommends BloodDolly's TeslaDecoder application to decrypt your files. [...] | Tesla | |||
| 2016-05-20 19:00:00 | (Déjà vu) TeslaCrypt authors release master keys, Ransomware Info Day held 19 May (lien direct) | The authors of the TeslaCrypt ransomware have publicly released the master decryption key that unlocks files encrypted by the malware in efforts to close up shop and go home for good. |
Tesla | ★★★★★ | ||
| 2016-05-20 16:19:45 | Will CryptXXX Replace TeslaCrypt After Ransomware Shakedown? (lien direct) | The departure of TeslaCrypt from the ransomware circle has gone and made waves in the cybercriminal world. Bad guys appear to be jumping ships in hopes of getting a chunk out of the share that was previously owned by TeslaCrypt. In line with this recent event, indicators are pointing to a new strong man in the ransomware game: CryptXXX.Post from: Trendlabs Security Intelligence Blog - by Trend MicroWill CryptXXX Replace TeslaCrypt After Ransomware Shakedown? | Tesla | |||
| 2016-05-20 15:46:37 | Threatpost News Wrap, May 20, 2016 (lien direct) | Mike Mimoso and Chris Brook discuss the news of the week, including a big LinkedIn breach, TeslaCrypt closing up shop, and a breakthrough in random number generation. The two also recap this week's Source Conference in Boston. | Tesla | ★★★★ | ||
| 2016-05-20 15:04:28 | The Week in Ransomware - May 20 2016 (lien direct) | The ransomware keep on coming! Since the last article we have had 6 new ransomware infections released, and to weight it out, 6 decryptors. Included in the new ransomware is one that is targeting Drupal web sites. By far, the biggest news, though, was the closing of TeslaCrypt and their release of the master decryption key. [...] | Tesla | |||
| 2016-05-19 19:50:00 | (Déjà vu) TeslaCrypt closes down...Releases master decryption key, (Thu, May 19th) (lien direct) | In a surprising move...The TeslaCrypt ransomware developers have have stopped distributing TeslaCrypt and released their master decryption keyto the public. Various TeslaCrypt decryptor tools have been updated to include this key permitting anyone who gets compromised with TeslaCrypt a way of decrypting their data without paying the ransom.Further information can be found in the EMET blog post.-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected) (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License. | Tesla | |||
| 2016-05-19 13:41:37 | Master Decryption Key Released for TeslaCrypt Ransomware (lien direct) | The criminals behind the TeslaCrypt ransomware have closed up shop and publicly released the master decryption key that unlocks files encrypted by the malware. | Tesla |
To see everything:
Our RSS (filtrered)
