What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-09-15 10:00:00 | APIs: Risks and security solutions (lien direct) | This blog was written by an independent guest blogger. APIs have become a vital part of doing business. Organizations increasingly rely on the use of APIs for day-to-day workflows, particularly as cloud applications become something of a mainstay. A recent report found that the average number of APIs per company increased by 221% in 2021. Not only are APIs impossible to ignore, but the need to invest in API security cannot be overlooked. The trend in usage is closely followed by opportunists seeking ways to exploit vulnerabilities for their gain. To ensure adequate security, developers and organizations alike need to understand the risks and design their security strategy to mitigate them. Too often, security approaches are redesigned after a breach or hack occurs. By then, the damage has been done. Being proactive will save organizations time, money, and heartache. API security risks As cybercriminals work tirelessly to develop new ways to steal data and harm organizations, the list of threats is seemingly endless. That should not be cause for despair, however. While it can feel overwhelming, IT departments and financial controllers should not let it stunt them into doing nothing. In this article, we cover the most prominent threats to API security, and ways to employ tactics to protect users, data, and networks. Software bugs At a base level, software bugs are an easy point of exploitation for cybercriminals. Application errors will weaken API security, leaving your organization - and your valuable data - vulnerable to attackers. It’s crucial to have a system in place to regularly check for software updates and patches. Patches function like a software update, plugging potential holes that cyberattackers may use to enter your network or systems. Ensure you conduct regular vulnerability scans and perform security attacks on your implemented APIs. Of course, identifying these vulnerabilities is only the first step. Organizations must ensure they have a workflow in place to address weaknesses swiftly. Broken object-level authorization attacks Another key API security risk is at exposed endpoints that relate to object identifiers. These can be seen as a welcome mat for attackers to enter the endpoints, leaving a wide attack area with access to objects and data. To mitigate this risk, organizations must implement authorization checks at the object level. Checking every function that accesses a data source through input from users will help protect you from criminal activity. Consider using an API gateway, access tokens, object-level authorization checks, and implementing proper authorization credentials to stay protected. Misconfiguration Security misconfigurations are another common threat to API security. This risk is typically enabled through factors such as insecure default configs, misconfigured HTTP headers, unnecessary HTTP methods, or open cloud storage. It is crucial not to rely on default configurations and instead to configure APIs to fit your organization’s specific needs and requirements. Exposed data At times, developers leave object properties exposed, leaving it up to organizations to filter data before availing it to end users. While well intentioned, this unfortunately leaves a large amount of data exposed, luring cybercriminals to attack. Ensure the data exposed through APIs is strictly limited to only the necessary, trusted users. Evaluate access control and ensure you’re deliberate with what is available, and to whom. Injections The threat | Hack Vulnerability Threat | |||
| 2022-09-13 23:34:47 | Breach of software maker used to backdoor as many as 200,000 servers (lien direct) | Hack of FishPig distribution server used to install Rekoobe on customer systems. | Hack | |||
| 2022-09-12 14:24:45 | Lazarus APT Uses Log4j Flaw To Hack US, Canadian Energy Co\'s – Cyber Experts Comment (lien direct) | Researchers have uncovered a new campaign targeting U.S., Canadian and Japanese energy providers to the North Korean Lazarus APT hacking group. The initial vector was the exploitation of the Log4j vulnerability on exposed VMware Horizon servers which was used to gain an initial foothold into targeted organizations https://blog.talosintelligence.com/2022/09/lazarus-three-rats.html | Hack | APT 38 | ||
| 2022-09-12 14:20:48 | Apple fixes eighth zero-day used to hack iPhones and Macs this year (lien direct) | Apple has released security updates to address the eighth zero-day vulnerability used in attacks against iPhones and Macs since the start of the year. [...] | Hack Vulnerability | |||
| 2022-09-12 11:34:17 | Vulnerability in BackupBuddy Plugin Exploited to Hack WordPress Sites (lien direct) | A recently resolved vulnerability in the BackupBuddy WordPress plugin has been exploited in malicious attacks since late August, Defiant's Wordfence team warns. | Hack Vulnerability | |||
| 2022-09-07 15:30:12 | Experts Insight On Holiday Inn Hack (lien direct) | Following the news that: Holiday Inn hotels hit by cyber-attack Holiday Inn hotels hit by cyber-attack – BBC News Cyber security experts reacted below. | Hack | |||
| 2022-09-06 08:10:00 | BlackCat Ransomware Linked to Italy\'s Energy Services Firm Hack (lien direct) | The ransomware group claimed to have downloaded 700GB of data from GSE | Ransomware Hack | |||
| 2022-09-05 16:32:55 | Episode 242: Hacking the Farm (and John Deere) with Sick Codes (lien direct) | In our latest podcast, Paul caught up with Sick Codes (@sickcodes) to talk about his now-legendary presentation at the DEF CON Conference in Las Vegas, in which he demonstrated a hack that ran the Doom first person shooter on a John Deere 4240 touch-screen monitor.
The post Episode 242: Hacking the Farm (and John Deere) with Sick Codes appeared...Read the whole entry... »Click the icon below to listen. |
Hack | |||
| 2022-09-05 13:50:41 | Cybersecurity Experts Welcome NSA/CISA Best Practices For Software Supply Chain (lien direct) | The U.S NSA and CISA have shared tips to secure the software supply chain. But is this actually a step in the right direction? After the snowball effect of supply-chain attacks like the SolarWinds hack that compromised multiple U.S govt agencies (which brought about President Biden's Executive Order on cybersecurity measures), it's not surprising that […] | Hack | |||
| 2022-09-05 09:52:03 | TikTok denies hack following leak of user data, source code (lien direct) | TikTok denies recent claims it was breached, and source code and user data were stolen, telling BleepingComputer that data posted to a hacking forum is "completely unrelated" to the company. [...] | Hack | |||
| 2022-09-05 08:39:46 | EvilProxy Phishing-As-A-Service With MFA Bypass Emerged In Dark Web (lien direct) | >Resecurity researchers discovered a new Phishing-as-a-Service (PhaaS) called EvilProxy advertised on the Dark Web. Original post: https://resecurity.com/blog/article/evilproxy-phishing-as-a-service-with-mfa-bypass-emerged-in-dark-web Following the recent Twilio hack leading to the leakage of 2FA (OTP) codes, cybercriminals continue to upgrade their attack arsenal to orchestrate advanced phishing campaigns targeting users worldwide. Resecurity has recently identified a new Phishing-as-a-Service (PhaaS) called EvilProxy advertised in the Dark […] | Hack Guideline | |||
| 2022-09-02 13:23:29 | Samsung discloses data breach after July hack (lien direct) | Electronics giant Samsung has confirmed a new data breach today after some of its U.S. systems were hacked to steal customer data. [...] | Data Breach Hack | |||
| 2022-09-02 07:25:46 | Attack infrastructure used in Cisco hack linked to Evil Corp affiliate (lien direct) | >Researchers discovered that the infrastructure used in Cisco hack was the same used to target a Workforce Management Solution firm. Researchers from cybersecurity firm eSentire discovered that the attack infrastructure used in recent Cisco hack was also used to attack a top Workforce Management corporation in in April 2022. The experts also speculate that the […] | Hack | |||
| 2022-09-01 15:33:00 | Infra Used in Cisco Hack Also Targeted Workforce Management Solution (lien direct) | The attack infrastructure used to target Cisco in the May 2022 incident was also employed against an attempted compromise of an unnamed workforce management solutions holding company a month earlier in April 2022. Cybersecurity firm Sentire, which disclosed the findings, raised the possibility that the intrusions could be the work of a criminal actor known as mx1r, who is said to be a member of | Hack | |||
| 2022-09-01 12:59:12 | Ransomware Gang Claims Customer Data Stolen in TAP Air Portugal Hack (lien direct) | The Ragnar Locker ransomware gang says it has exfiltrated customer data in a cyberattack on Portuguese state-owned flag carrier airline TAP Air Portugal. The incident was initially disclosed on August 26, when TAP announced on Twitter that it managed to foil the cyberattack before the threat actor could access any customer data. | Ransomware Hack Threat | |||
| 2022-08-31 14:33:41 | High-School Graduation Prank Hack (lien direct) | This is a fun story, detailing the hack a group of high school students perpetrated against an Illinois school district, hacking 500 screens across a bunch of schools. During the process, the group broke into the school's IT systems; repurposed software used to monitor students' computers; discovered a new vulnerability (and reported it); wrote their own scripts; secretly tested their system at night; and managed to avoid detection in the school's network. Many of the techniques were not sophisticated, but they were pretty much all illegal... | Hack Vulnerability | |||
| 2022-08-30 15:01:00 | Anomali Cyber Watch: First Real-Life Video-Spoofing Attack, MagicWeb Backdoors via Non-Standard Key Identifier, LockBit Ransomware Blames Victim for DDoSing Back, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Authentication, DDoS, Fingerprinting, Iran, North Korea, Ransomware, and Russia. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
LastPass Hackers Stole Source Code
(published: August 26, 2022)
In August 2022, an unidentified threat actor gained access to portions of the password management giant LastPass development environment. LastPass informed that it happened through a single compromised developer account and the attacker took portions of source code and some proprietary LastPass technical information. The company claims that this incident did not affect customer data or encrypted password vaults.
Analyst Comment: This incident doesn’t seem to have an immediate impact on LastPass users. Still, organizations relying on LastPass should raise the concern in their risk assessment since “white-box hacking” (when source code of the attacking system is known) is easier for threat actors. Organizations providing public-facing software should take maximum measures to block threat actors from their development environment and establish robust and transparent security protocols and practices with all third parties involved in their code development.
Tags: LastPass, Password manager, Data breach, Source code
Mercury Leveraging Log4j 2 Vulnerabilities in Unpatched Systems to Target Israeli
(published: August 25, 2022)
Starting in July 2022, a new campaign by Iran-sponsored group Static Kitten (Mercury, MuddyWater) was detected targeting Israeli organizations. Microsoft researchers detected that this campaign was leveraging exploitation of Log4j 2 vulnerabilities (CVE-2021-45046 and CVE-2021-44228) in SysAid applications (IT management tools). For persistence Static Kitten was dropping webshells, creating local administrator accounts, stealing credentials, and adding their tools in the startup folders and autostart extensibility point (ASEP) registry keys. Overall the group was heavily using various open-source and built-in operating system tools: eHorus remote management software, Ligolo reverse tunneling tool, Mimikatz credential theft tool, PowerShell programs, RemCom remote service, Venom proxy tool, and Windows Management Instrumentation (WMI).
Analyst Comment: Network defenders should monitor for alerts related to web shell threats, suspicious RDP sessions, ASEP registry anomaly, and suspicious account creation. Similarly, SysAid users can monitor for webshells and abnormal processes related to SysAisServer instance. Even though Static Kitten was observed leveraging the Log4Shell vulnerabilities in the past (targeting VMware apps), most of their attacks still start with spearphishing, often from a compromised email account.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Phishing - T1566 |
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
LastPass Hackers Stole Source Code
(published: August 26, 2022)
In August 2022, an unidentified threat actor gained access to portions of the password management giant LastPass development environment. LastPass informed that it happened through a single compromised developer account and the attacker took portions of source code and some proprietary LastPass technical information. The company claims that this incident did not affect customer data or encrypted password vaults.
Analyst Comment: This incident doesn’t seem to have an immediate impact on LastPass users. Still, organizations relying on LastPass should raise the concern in their risk assessment since “white-box hacking” (when source code of the attacking system is known) is easier for threat actors. Organizations providing public-facing software should take maximum measures to block threat actors from their development environment and establish robust and transparent security protocols and practices with all third parties involved in their code development.
Tags: LastPass, Password manager, Data breach, Source code
Mercury Leveraging Log4j 2 Vulnerabilities in Unpatched Systems to Target Israeli
(published: August 25, 2022)
Starting in July 2022, a new campaign by Iran-sponsored group Static Kitten (Mercury, MuddyWater) was detected targeting Israeli organizations. Microsoft researchers detected that this campaign was leveraging exploitation of Log4j 2 vulnerabilities (CVE-2021-45046 and CVE-2021-44228) in SysAid applications (IT management tools). For persistence Static Kitten was dropping webshells, creating local administrator accounts, stealing credentials, and adding their tools in the startup folders and autostart extensibility point (ASEP) registry keys. Overall the group was heavily using various open-source and built-in operating system tools: eHorus remote management software, Ligolo reverse tunneling tool, Mimikatz credential theft tool, PowerShell programs, RemCom remote service, Venom proxy tool, and Windows Management Instrumentation (WMI).
Analyst Comment: Network defenders should monitor for alerts related to web shell threats, suspicious RDP sessions, ASEP registry anomaly, and suspicious account creation. Similarly, SysAid users can monitor for webshells and abnormal processes related to SysAisServer instance. Even though Static Kitten was observed leveraging the Log4Shell vulnerabilities in the past (targeting VMware apps), most of their attacks still start with spearphishing, often from a compromised email account.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Phishing - T1566 | |
Ransomware Hack Tool Vulnerability Threat Guideline Cloud | APT 37 APT 29 LastPass | ||
| 2022-08-29 21:06:12 | Microsoft 365 Business Users Targeted With New DocuSign Phishing Scam (lien direct) | According IT Pro, a new business email compromise (BEC) campaign has been targeting Microsoft 365 organizations in a bid to hack corporate executives' accounts and maliciously divert business payments. Researchers from cyber security firm Mitiga found that the hackers are leveraging inherent weaknesses in 365's multi-factor authentication (MFA), Microsoft Authenticator, as well as Microsoft 365 Identity […] | Hack | |||
| 2022-08-29 15:25:45 | Twilio breach let attackers access Authy two-factor accounts of 93 users (lien direct) | >Threat actors behind the Twilio hack also gained access to the accounts of 93 individual users of its Authy two-factor authentication (2FA) service. Early August, the communications company Twilio discloses a data breach, threat actors had access to the data of some of its customers. The attackers accessed company systems using employee credentials obtained through […] | Hack Threat | |||
| 2022-08-28 13:15:05 | (Déjà vu) Okta one-time MFA passcodes exposed in Twilio cyberattack (lien direct) | The threat actor behind the Twilio hack used their access to steal one-time passwords (OTPs) delivered over SMS to from customers of Okta identity and access management company. [...] | Hack Threat | |||
| 2022-08-28 13:15:05 | Twilio breach let hackers see Okta\'s one-time MFA passwords (lien direct) | The threat actor behind the Twilio hack used their access to steal one-time passwords (OTPs) delivered over SMS to from customers of Okta identity and access management company. [...] | Hack Threat | |||
| 2022-08-27 16:14:51 | Twilio hackers also breached the food delivery firm DoorDash (lien direct) | >Twilio hackers also compromised the food delivery firm DoorDash, the attackers had access to company data, including customer and employee info. On-demand food delivery service DoorDash disclosed a data breach, the threat actors behind the Twilio hack gained access to the company’s data. DoorDash declared that malicious hackers stole credentials from employees of a third-party vendor, then […] | Hack Threat | |||
| 2022-08-26 19:54:39 | The number of companies caught up in the Twilio hack keeps growing (lien direct) | 2FA provider Authy, password manager LastPass, and DoorDash all experienced breaches. | Hack | LastPass | ||
| 2022-08-26 15:30:34 | DoorDash discloses new data breach tied to Twilio hack (lien direct) | Food delivery firm DoorDash has disclosed a data breach exposing customer and employee data that is linked to the recent cyberattack on Twilio. [...] | Data Breach Hack | |||
| 2022-08-26 14:40:34 | DoorDash Data Compromised Following Twilio Hack (lien direct) | Food delivery company DoorDash revealed on Thursday that customer and employee data has been exposed as a result of a recent breach at a third-party vendor. DoorDash said hackers abused a third-party vendor's access to its systems. The attacker abused DoorDash's internal tools and gained access to the information of 'a small percentage of individuals'. | Hack | ★★★★★ | ||
| 2022-08-24 14:56:27 | Plex Confirms Database Breach, Data Theft (lien direct) | Popular streaming media platform Plex is scrambling to reset user passwords after a database hack that included the theft of emails, usernames, and encrypted passwords. | Hack | |||
| 2022-08-24 12:02:07 | CVE-2021-1782, an iOS in-the-wild vulnerability in vouchers (lien direct) | Posted by Ian Beer, Google Project Zero This blog post is my analysis of a vulnerability exploited in the wild and patched in early 2021. Like the writeup published last week looking at an ASN.1 parser bug, this blog post is based on the notes I took as I was analyzing the patch and trying to understand the XNU vouchers subsystem. I hope that this writeup serves as the missing documentation for how some of the internals of the voucher subsystem works and its quirks which lead to this vulnerability. CVE-2021-1782 was fixed in iOS 14.4, as noted by @s1guza on twitter: 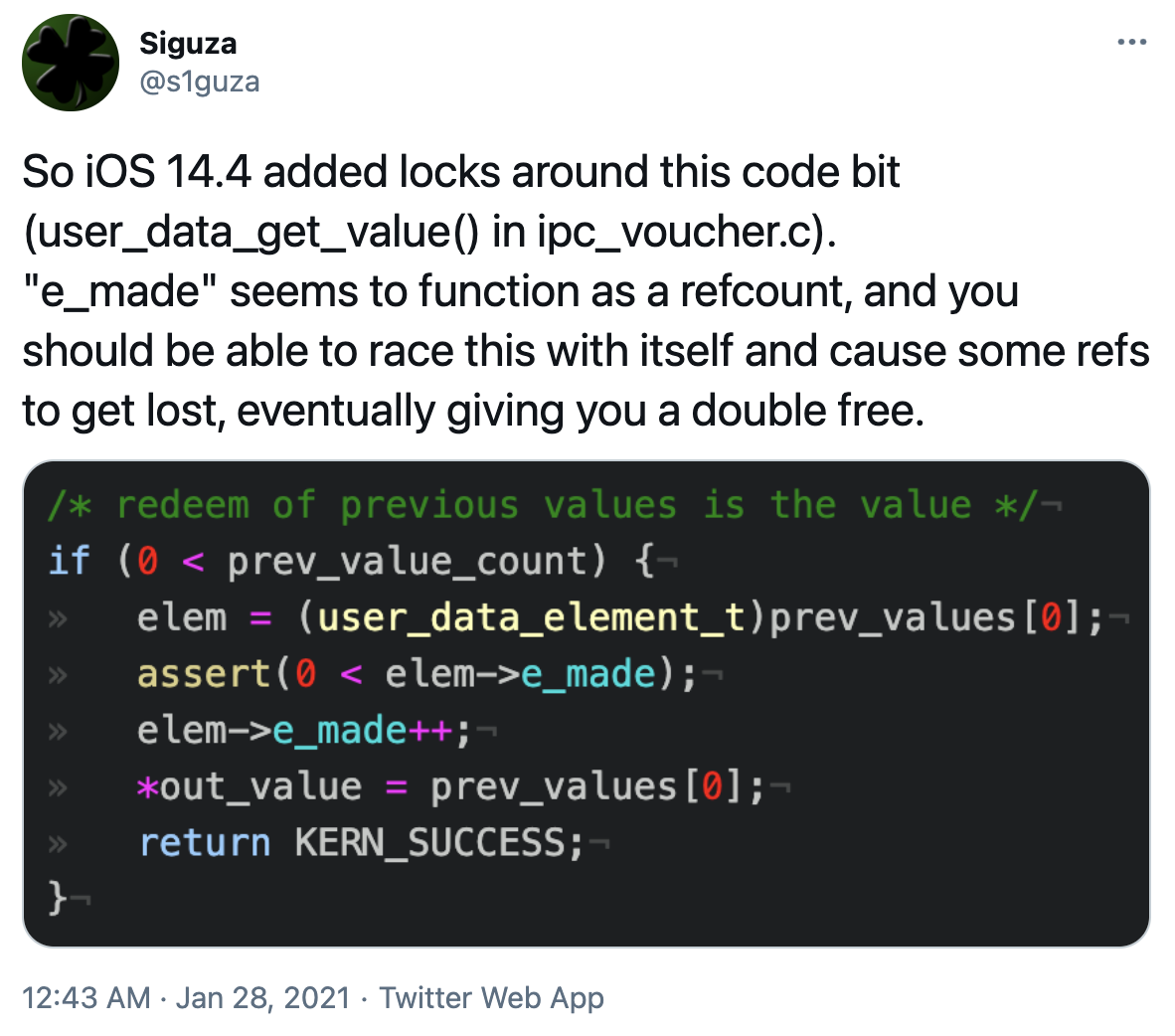 This vulnerability was fixed on January 26th 2021, and Apple updated the iOS 14.4 release notes on May 28th 2021 to indicate that the issue may have been actively exploited: This vulnerability was fixed on January 26th 2021, and Apple updated the iOS 14.4 release notes on May 28th 2021 to indicate that the issue may have been actively exploited: |
Hack Tool Vulnerability Guideline | ★★★ | ||
| 2022-08-24 11:53:36 | Hackers use AiTM attack to monitor Microsoft 365 accounts for BEC scams (lien direct) | A new business email compromise (BEC) campaign has been discovered combining sophisticated spear-phishing with Adversary-in-The-Middle (AiTM) tactics to hack corporate executives' Microsoft 365 accounts, even those protected by MFA. [...] | Hack | |||
| 2022-08-23 14:15:00 | Counterfeit Android Devices Revealed to Contain Backdoor Designed to Hack WhatsApp (lien direct) | At least four different smartphones affected: 'P48pro', 'radmi note 8', 'Note30u' and 'Mate40' | Hack | ★★★★ | ||
| 2022-08-23 13:30:00 | CyberheistNews Vol 12 #34 [Eye Opener] The Cisco Hack Was Caused by Initial Access Broker Phishing (lien direct) |

|
Hack | |||
| 2022-08-23 11:30:40 | Signal Phone Numbers Exposed in Twilio Hack (lien direct) | Twilio was hacked earlier this month, and the phone numbers of 1,900 Signal users were exposed: Here’s what our users need to know: All users can rest assured that their message history, contact lists, profile information, whom they’d blocked, and other personal data remain private and secure and were not affected. For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal. This attack has since been shut down by Twilio. 1,900 users is a very small percentage of Signal’s total users, meaning that most were not affected... | Hack | |||
| 2022-08-23 11:12:43 | (Déjà vu) Counterfeit Phones Found to Contain Backdoor to Hack WhatsApp (lien direct) | Budget Android device models that are counterfeit versions associated with popular smartphone brands contain multiple hidden trojans designed to target WhatsApp and WhatsApp Business messaging app. Doctor Web first came across the malware in July 2022. It was discovered in the system partition of at least four different smartphones: radmi note 8, P48pro, Note30u, and […] | Malware Hack | |||
| 2022-08-23 00:02:06 | Lockbit leak sites hit by mysterious DDoS attack after Entrust hack (lien direct) | >LockBit ransomware gang claims to have hacked the IT giant Entrust and started leaking the stolen files. Entrust Corp., provides software and hardware used to issue financial cards, e-passport production, user authentication for those looking to access secure networks or conduct financial transactions, trust certificated for websites, mobile credentials, and connected devices. The Lockbit ransomware […] | Ransomware Hack | |||
| 2022-08-22 07:28:00 | Researchers Find Counterfeit Phones with Backdoor to Hack WhatsApp Accounts (lien direct) | Budget Android device models that are counterfeit versions associated with popular smartphone brands are harboring multiple trojans designed to target WhatsApp and WhatsApp Business messaging apps. The trojans, which Doctor Web first came across in July 2022, were discovered in the system partition of at least four different smartphones: P48pro, radmi note 8, Note30u, and Mate40, was "These | Hack | |||
| 2022-08-20 13:00:00 | Janet Jackson\'s \'Rhythm Nation\' Can Crash Old Hard Drives (lien direct) | Plus: The Twilio hack snags a reporter, a new tool to check for spyware, and the Canadian weed pipeline gets hit by a cyberattack. | Hack Tool | |||
| 2022-08-19 11:10:55 | Russian APT29 hackers abuse Azure services to hack Microsoft 365 users (lien direct) | The state-backed Russian cyberespionage group Cozy Bear has been particularly prolific in 2022, targeting Microsoft 365 accounts in NATO countries and attempting to access foreign policy information. [...] | Hack | APT 29 | ||
| 2022-08-18 21:37:53 | Encrypted Messaging Service Hack Exposes Phone Numbers (lien direct) | > Many people opt for encrypted messaging services because they like the additional layers of privacy they offer. They allow users...
Many people opt for encrypted messaging services because they like the additional layers of privacy they offer. They allow users...
|
Hack | |||
| 2022-08-18 15:49:45 | Apple releases Safari 15.6.1 to fix zero-day bug used in attacks (lien direct) | Apple has released Safari 15.6.1 for macOS Big Sur and Catalina to fix a zero-day vulnerability exploited in the wild to hack Macs. [...] | Hack Vulnerability | |||
| 2022-08-18 12:00:00 | How a Hacked Tractor Added Fuel to the Right-to-Repair Movement (lien direct) | This week, we discuss the latest John Deere tractor hack and its broader implications for repair rights advocates. | Hack | |||
| 2022-08-18 10:00:00 | (Déjà vu) Urgent update for macOS and iOS! Two actively exploited zero-days fixed (lien direct) | >Categories: Exploits and vulnerabilitiesCategories: NewsTags: macOS Tags: iOS Tags: CVE-2022-32894 Tags: CVE-2022-32893 Tags: kernel privileges Tags: WebKit Tags: actively exploited Tags: watering hole Tags: exploit kit Apple has released emergency security updates to fix two zero-day vulnerabilities previously exploited by attackers to hack iPhones, iPads, or Macs. (Read more...) | Hack | |||
| 2022-08-17 18:35:26 | Apple security updates fix 2 zero-days used to hack iPhones, Macs (lien direct) | Apple has released emergency security updates today to fix two zero-day vulnerabilities previously exploited by attackers to hack iPhones, iPads, or Macs. [...] | Hack | |||
| 2022-08-17 09:33:15 | (Déjà vu) Job Seekers Targeted in Lazarus Group Hack (lien direct) | The North Korea state-backed Lazarus Group has been observed to be targeting job seekers with malware capable of executing on Apple Macs with Intel and M1 chipsets. ESET, a Slovak cybersecurity firm, linked these events to a campaign dubbed “Operation In(ter)ception” that was first disclosed in June 2020 and involved using social engineering tactics to […] | Malware Hack Medical | APT 38 | ||
| 2022-08-16 14:15:00 | New Attack Weaponizes PLCs to Hack Enterprise and OT Networks (lien direct) | The research resulted in proof-of-concept exploits against seven market-leading automation firms | Hack Guideline | |||
| 2022-08-16 13:53:13 | Ransomware Group Claims Access to SCADA in Confusing UK Water Company Hack (lien direct) | A ransomware group has hit at least one water company in the United Kingdom, but there is some confusion over whose systems were actually breached. | Ransomware Hack | |||
| 2022-08-16 13:34:25 | (Déjà vu) CyberheistNews Vol 12 #33 [Eye Opener] Recent Cisco Hack by Ransomware Group Started Because of a Phishing Attack (lien direct) |

|
Ransomware Hack | |||
| 2022-08-16 13:30:00 | #DEFCON: How US Teen RickRolled His High School District (lien direct) | American teenager explains how he was able to hack his local high school district | Hack | |||
| 2022-08-16 11:30:27 | Il a hacké un tracteur John Deere… et a installé Doom (lien direct) | >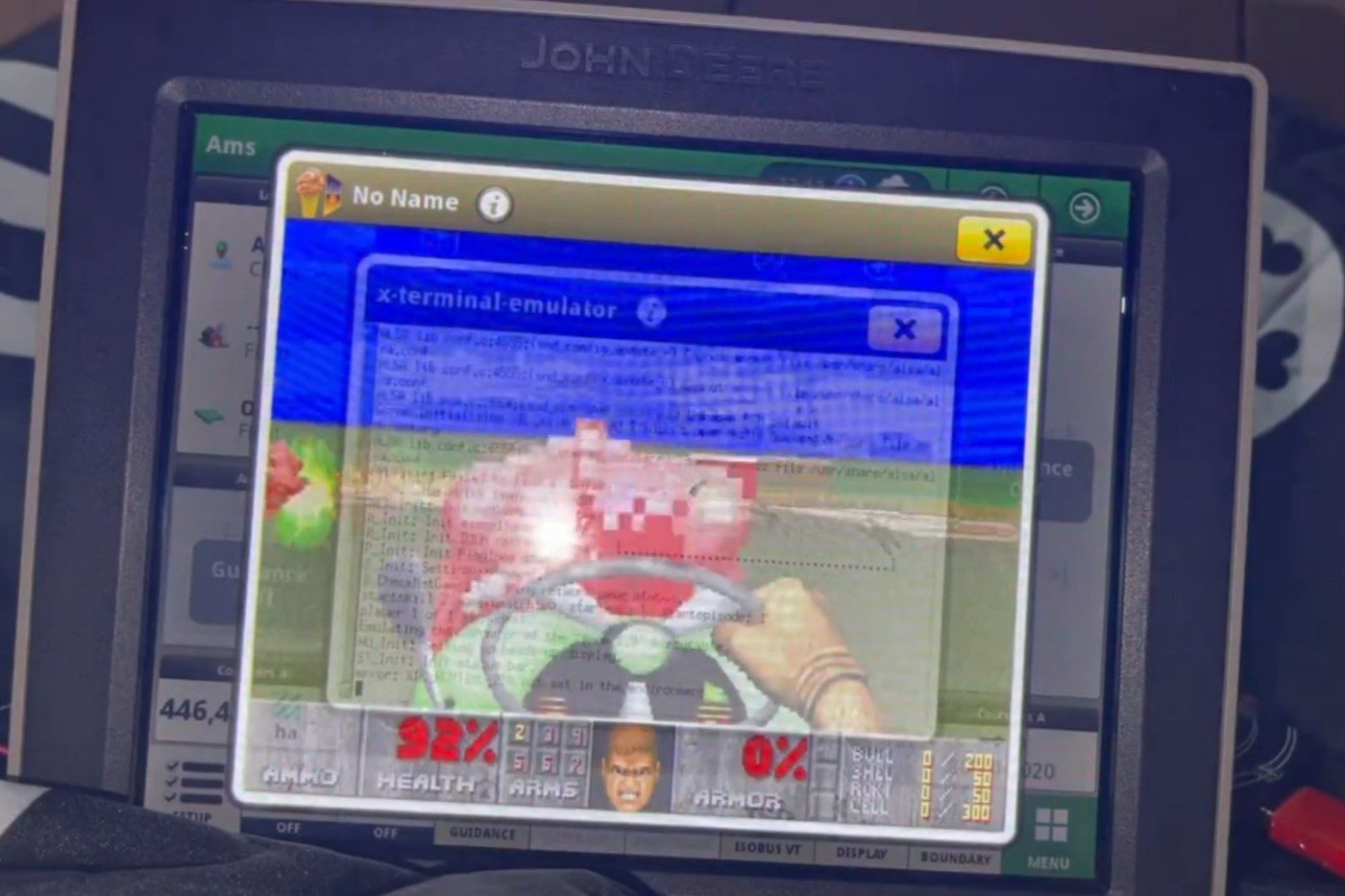 Au delà du jeu vidéo, ce hack permettrait aux utilisateurs de regagner le contrôle des équipements agricoles qu'ils possèdent et de ne plus être obligés de passer par un concessionnaire pour les mises à jour.
L'article Il a hacké un tracteur John Deere… et a installé Doom est à retrouver sur 01net.com.
Au delà du jeu vidéo, ce hack permettrait aux utilisateurs de regagner le contrôle des équipements agricoles qu'ils possèdent et de ne plus être obligés de passer par un concessionnaire pour les mises à jour.
L'article Il a hacké un tracteur John Deere… et a installé Doom est à retrouver sur 01net.com. |
Hack | |||
| 2022-08-16 11:09:42 | Signal Discloses Impact From Twilio Hack (lien direct) | Secure communications services provider Signal on Monday disclosed impact from the recent Twilio hack, after threat actors attempted to re-register the phone numbers of some of its users to new devices. | Hack Threat | |||
| 2022-08-15 22:42:11 | Nearly 1,900 Signal Messenger Accounts Potentially Compromised in Twilio Hack (lien direct) | Popular end-to-end encrypted messaging service Signal on Monday disclosed the cyberattack aimed at Twilio earlier this month may have exposed the phone numbers of roughly 1,900 users. "For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal," the company said. "All users can rest assured that | Hack | |||
| 2022-08-15 17:46:24 | Twilio hack exposed Signal phone numbers of 1,900 users (lien direct) | Phone numbers of close to 1,900 Signal users were exposed in the data breach Twilio cloud communications company suffered at the beginning of the month. [...] | Data Breach Hack |
To see everything:
Our RSS (filtrered)
